Chapter 4. Low tech wireless hacking
Information in this chapter
• Wireless 101: The Electromagnetic Spectrum
• 802.11 and Bluetooth Low Tech Hacks
• DoS and Availability
• Backdoors and Cracks
• Going Rogue
• Assault by Defaults
• Bypassing Specific Security Tools
It does no good to hermetically seal the windows in an organization if the doors are left wide open. But that is precisely what many organizations are doing today when they neglect to secure their wireless communications systems. Organizations habitually overlook the security of their wireless communications because they cannot see it. If they cannot see it, then they presume that no one else can either, and it is safe. However, that presumption cannot be farther from the truth. This chapter is dedicated to thwarting wireless systems of all types, armed with everything from a bobby pin to a yagi antenna. The goal of this chapter is to enable readers to “see” wireless, by explaining how it works, describing different types of devices that share common mediums and functionality, and offering clear explanations of security vulnerabilities using real-world examples. The attacks included are part of the low tech hacking subgenre of wireless assaults.
Key Words: 802.11, Access point, Bluetooth, Denial of service, Electromagnetic radiation, Farewell attack, ISM band, Jammer, Queensland attack, Radio frequency, Wireless communications system, Wireless Local Area Network, Wireless Personal Area Network, Yagi antenna
We interrupt this Low Tech Hacking title to bring you a little slice of slightly higher (but still low tech) hacking technique. Nestled among the physical security and locks, we bring you low tech wireless hacking; a chapter dedicated to thwarting wireless systems of all types, armed with everything from a bobby pin to a yagi antenna.
Although I'm probably better known in the security social circles (if there are such things) for dissecting the more complex protocols and vulnerabilities in wireless, general networking, and 802.1X technologies, I'm excited about the opportunity to contribute low tech material. Every day I see network administrators who have painstakingly figuratively hermetically sealed the windows in their castle, only to leave the doors wide open. As Jack says, “Don't hit your head on the low-hanging fruit!”1
Wireless is a pretty broad topic. The term wireless was first used to refer to radio transceivers. As homage to this ancient wireless terminology, I'm including a variety of technologies in this chapter, centered around the more traditional 802.11 wireless LANs (Local Area Networks) and similar wireless systems that afflict—I mean, simplify—our lives.
Wireless 101: the electromagnetic spectrum
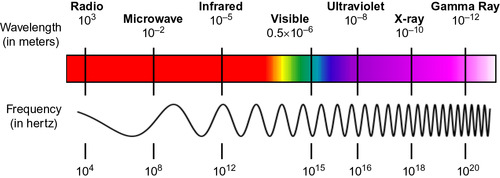
At a very broad level, the wireless technologies we're covering in this chapter use EMR (electromagnetic radiation). EMR of various wavelengths give us light, colors, AM and FM radio, and electronic devices in the electromagnetic spectrum. In order of longest to shortest wavelengths, we have radio, microwave, infrared, visible light, ultraviolet, X-rays, and gamma rays. Figure 4.1 below is a graphical representation of the EMR space, with wavelengths and frequency noted for key subsets of EMR ranges. As part of my research for this book, I was hoping to construct and analyze attacks for a gamma ray laser, but that was frowned upon by several parties and turned out to be cost-prohibitive. In lieu of that, I narrowed the scope of our happy little wireless chapter to cover more specific types of EMR, such as radio waves and devices in the industrial, scientific, and medical (ISM) band.
 |
| Figure 4.1 |
The radio spectrum of EMR is used for transmission of data via modulation, meaning it conveys the message by modifying properties of the wave such as frequency, phase, and amplitude. Television, mobile phones, wireless networking, and amateur radio all use radio waves. The use of the radio spectrum is regulated by most governments through frequency allocation. One such designation is the ISM band.
The ISM band is a subset of radio bands reserved internationally for industrial, scientific, and a variety of medical purposes. Many of the technologies that first pop in our head when we hear “wireless” live in this band. The lines of RF are blurry, at best, with quite a bit of exception and overlap, making it difficult to present technologies in order of frequency. Instead, below is a list of some popular ISM applications, in a relatively random order. The units of measure in the ISM band are GHz (gigahertz) and MHz (megahertz). To put those in perspective of one another, 1 MHz = 106 (1,000,000) Hz, and 1 GHz = 109 (1,000,000,000) Hz. Looking at Figure 4.1, the ISM band would be in the general area of the EMR spectrum where microwaves and long wave radios live.
• Home and Office
• Microwave Oven
2.45 GHz
• Car Alarm
2.45 GHz (between channels 8 and 9 which interferes with WLAN channels 6 and 11)
• Cordless Phones
915 MHz, 2.450 GHz, and 5.800 GHz bands. DECT phones are outside ISM.
• WiFi/Wireless LAN (IEEE 802.11)
2.450 GHz and 5.800 GHz bands
• RFID
13.56 MHz (used by biometric passports and contactless smart cards)
• RC Equipment
2.4 GHz (used by toys, from gas powered cars to miniature aircraft)
• Video, CCTV, Security Systems
2.4 GHz and other various
• Phones and Broadband
• Mobile Broadband Wireless Access (MBWA) (IEEE 802.20)
1.6 to 2.3 GHz
• Wireless Sensor Networks
868 MHz, 915 MHz, and 2.450 GHz bands (to monitor temperature, sound, vibration, pressure, motion, or pollutants)
• Metro Area Network (MAN)/WiMax (IEEE 802.16)
2 to 11 GHz band
• Wireless Personal Area Networks (PANs)
• Bluetooth (IEEE 802.15.1)
2.4 to 2.4835 GHz (used by iPod Touch, PlayStation 3, telephones and headsets, Nintendo Wii)
• ZigBee (IEEE 802.15.4)
2.45 to 2.4835 GHz band (used by wireless light switches with lamps, electrical meters with in-home-displays, consumer electronics equipment)
If we were to collapse some of these more common wireless network technologies into four broad use cases, as in Table 4.1, it becomes apparent that these systems are implemented with very different standards and technologies but that all live in the same general frequency of 6 GHz, plus or minus 4 GHz.
Why securing wireless is hard
Throughout my years working in various aspects of technology and security, I've come to realize one simple concept; out of sight is out of mind. Organizations habitually overlook security of wireless communications because they can't see it. If they can't see it, then I suppose their logic is that no one else can either, and it's safe. If you come across my Mom, you can ask her about the many times, as a toddler, I glided through the living room, one hand up to my head acting as a blinder. I was told, “I don't want to see you come out of your room.” I figured if I couldn't see them, they couldn't see me, and I was following the instructions given perfectly. When you're 4 years old, it seems logical. Apparently a faction of network administrators never outgrew that mindset. It's a little less excusable when you have 5 or 10 years of network management under your belt.
People have been looking for ways to visualize or materialize wireless for many decades, as evidenced by the extensive development and use of frequency monitoring tools from the early 1900s. Figure 4.2 is an example of a WWII-era frequency analyzer used by the U.S. military. We've come a long way since then, with devices like this small enough to fit in the palm of a hand and affordable enough for hobbyists. My goal in this chapter is to let everyone “see” wireless, by explaining how it works, describing types of devices that share common mediums and functionality, and offering plain English explanations of security vulnerabilities using real-world examples. The attacks included are part of the low tech hacking subgenre of wireless assaults. If, in reading these scenarios, you grasp just one new concept or think of one new way to attack (and therefore secure) a system, then I've accomplished my task.
802.11 and bluetooth low tech hacks
When someone hears the word wireless, two of the most common initial associations are first with traditional wireless LANS for home and enterprise networks, and second with wireless PANs (personal area networks) such as Bluetooth. This section is dedicated to the variety of low tech hacking techniques for these popular wireless structures.
Since we're dealing with a slightly higher low tech topic than other low tech tricks in this book, I've decided to rate each hack on a scale of one to five, with five being the most technical of the low tech hacks.
DoS and availability
Attacks on service quality and availability of wireless are probably some of the easiest and least technical and have the most impact. Denial of service (DoS) can result from some of the most cleverly architected technical attacks and, conversely, from some of the most Neanderthal-style physical tampering.
When discussing wireless security, we often talk about layer 1 and layer 2 attacks. Specifically here, we're looking at DoS attacks, broken down by layers.
Layer 1 DoS attacks
Layer 1 in wired networking is the physical connection layer. And so too, in wireless, layer 1 is the physical (albeit unseen) layer of RF. For extra credit, I threw in a couple of extra physical, non-RF attacks here too.
Archetypal antennas
• Removing, replacing, and tampering with antennas
Low Tech Level 1
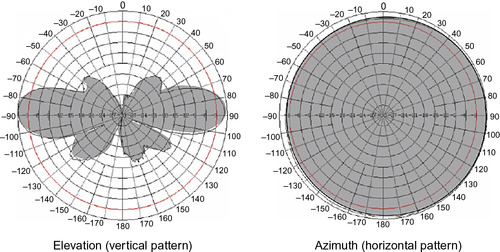
The simplest and most fun thing you can do to disrupt a wireless system is muck around with the antennas. This low tech hack earns a respectable Low Tech Level 1. What many network administrators and wireless users don't understand is that the integrity and strength of wireless signals have everything to do with the antenna, the antenna type, direction, and connectivity to the access point (AP). Figure 4.3 shows samples of three different access point types from a common wireless vendor. Note the six external antennas on one model. Other APs shown have integrated or internal antennas. The number of antennas used and the placement of each greatly affect coverage and performance of the wireless network.
 |
| Figure 4.3 |
To extensively disrupt a wireless system, one needs only to tamper with the antenna system enough to throw off the expected RF pattern. This type of tampering can be easily achieved by simply removing, replacing, or adjusting the angle of the antenna(s). As we'll see in other sections, antenna placement and direction are key to maintaining wireless coverage.
Whether an AP has a built-in omnidirectional antenna or an external directional antenna, every antenna has its own unique RF radiation pattern. The proper terms for these patterns are beamwidth, azimuth, and elevation. Beamwidth is a simple concept: it tells us how broad or directed the overall power is, so we'd use this to describe whether we want to cover a wide localized area or fire a signal down a narrow directed path (e.g., between rows of racks in a manufacturing warehouse). Azimuth (a term borrowed from navigation and astronomy) and elevation give a better picture of the actual coverage area by showing the full propagation pattern. Azimuth is the view you'd get if you could see RF and you were looking down on the antenna from a birds-eye view. The elevation is the view you'd get seeing RF from the side.
As shown in Figure 4.4, external antennas can take on many shapes, sizes, and forms. Antenna manufacturers include specific information in their product datasheets, detailing the beamwidths and coverage patterns, as shown in Table 4.2 and Figure 4.5, but without this information the shape and size of the antenna is a good enough indicator of the antenna type, coverage, and purpose.
 |
| Figure 4.4 |
Omnidirectional antennas, if you couldn't deduce this from the name, are designed to radiate, for the most part, in all directions in a semi-flat vertical plane. The coverage pattern for these is most often likened to a doughnut. Patch antennas are designed to radiate along two planes, typically in front, behind, or below, which is why they're most often found on sides of buildings or other vertical walls. Yagi antennas, usually long and narrow, have a radiation pattern that mimics their shape, and these are used to provide strong directional signals such as is needed for point-to-point wireless. These are usually found high, on top of buildings, poles, or towers, and will likely have a matching antenna on the other end.
Directional dangers
• Sending wireless bridges off course
Low Tech Level 1
A network administrator would be hard-pressed to troubleshoot this type of attack remotely. If the wireless team has a good monitoring system or WIPS, they're more likely to spot the RF changes picked up if sensors and monitoring APs are in the immediate area. Full remediation would probably involve a visual survey of the APs and antennas, and possibly a physical RF site survey using a laptop and wireless survey application. Since hunting down this issue may be nearly impossible after the fact, the best mitigation is preventing it in the first place. Organizations with external APs or antennas should carefully select their mounting locations and ensure there's appropriate physical security protection for the devices. Mounting on rooftops, maintenance areas, and tall poles or using secured enclosures is strongly recommended. For more on physical security, be sure to read the guidance provided by Jack in Chapters 1 and 2.
Scattered, reflected, and diffracted, please! You may like your hash browns served fancy style, but scattered, smattered, reflected, or in any way distorted is no way to take your RF. Aside from tampering with antennas, forced reflection is probably the simplest and most effective wireless disturbance. As you can probably construe from the word, reflection happens when RF signals bounce off something. Think of it as completely rerouting the path of the RF signal, away from its intended users, and off into some black hole of space (or other unintended users).
Meet evil Doctor Reflecto
• Shielding and deflecting RF signal
Low Tech Level 1
An evil Doctor Reflecto could easily disrupt wireless availability by positioning a metal sheet, enclosure, or even just some aluminum around the antennas or between the AP and the designated service area. Depending on how much of an evil genius he is, Reflecto may have an extraordinarily good grasp of antenna patterns and may be able to strategically insert a reflecting item outside the immediate area of the AP antenna, but in a spot that will greatly disrupt service to wireless clients. Places where APs may be hard to reach, such as airports and warehouses, would be prime targets for this type of attack.
As with antenna security, preventing direct shielding at an AP can be accomplished with good physical security by way of smart mounting and appropriate locked or hidden enclosures. Enclosures usually run around $50 to $300, depending on requirements for security, power, mounting, and conditioning. Figure 4.6 shows a popular style of ceiling tile enclosures, designed to house an AP out of sight and install easily in standard drop ceiling grids.
There are a variety of enclosures designed to conceal access points and prevent tampering. Products like the ceiling tile enclosure shown in Figure 4.6 will protect APs installed throughout a mid- to large-sized organization with many APs, while lockable racks and cabinets (see Figure 4.7) help prevent physical access to APs and other network equipment that may be more centrally located in smaller offices. Also be sure to refer to Chapter 3, where Jack provides some invaluable information on lock mechanisms and guidance on picking trustworthy locks.
Foiled!? How effective is Evil Doctor Reflecto's power?
How effective is this low tech hack against modern enterprise APs? That's exactly what I set out to answer. To test this onslaught of RF, we staged the setup in our office labs at Carolina Advanced Digital. We started with a baseline site survey to document the ambient RF and signal strengths and then we piled on the heavy metal. I enlisted the assistance of one of my colleagues.
The first test was simply to place an enterprise 802.11b/g/n dual-radio AP inside a standard metal enclosure. With no visible reduction in RF strength, we layered on a couple of steel doors and shelves taken from some of our equipment racks. I wasn't too happy with the selection, since they were all textured and coated metals. Remember, when we channel our inner hacker, we know our most effective materials will be very smooth and reflective.
Figure 4.8 shows the pretamper setup with a commonly used metal enclosure and one of the more advanced 802.11b/g/n multi-radio access points currently available. It's worth noting that the AP is of the newer variety, since the radios and power options on this unit are far superior to basic 802.11a or b/g radios from several years back.
Convinced the textured steel doors wouldn't do the trick, I moved on to the next metallic test: aluminum foil. I carefully crafted a few sheets with 90 degree angles and placed them strategically to cover most of the enclosure, shown in Figure 4.9. Upon measuring, we found the RF signal took a hit, but not a big enough one for me to put my Low Tech Hack stamp of approval on Doctor Reflecto.
Back to the drawing board. Before our first test, I didn't bother researching the best distances to use in separating the foil to create an RF trap, I was just layering it in thin sheets. For our second attempt, I still didn't get mathematical with it – after all, this is supposed to be a low tech hack, not a get-your-calculator-out-and-properly-space-the-foil attack, right? I decided to rather indiscriminately throw on a few added layers of foil. Luckily, my Dad was in the office. Upon seeing my crazy shenanigans, he suggested we ground the foil just as a final blow. Five minutes and some wire strippers later, we were all set with a grounding wire, complete with plug. Figure 4.10 shows the result of our rigging.
If this didn't do it, then I was ready to declare this Low Tech Hack myth BUSTED. With fingers crossed, I foiled a bit more, rigged a hemostat to clip the ground on, and went back to my cohort to see what our RF readings were showing.
The results were promising, we effected more than a 10 dB loss, even at close range (less than 50 feet). The hit in signal quality would certainly be enough to interrupt the operation of latency-sensitive devices like Voice over WiFi phones and specialized medical and manufacturing equipment. In larger buildings with more distance between the AP and clients, we could also affect a sizable RF loss that would hamper connectivity of laptops as well. Our little hack was redeemed!
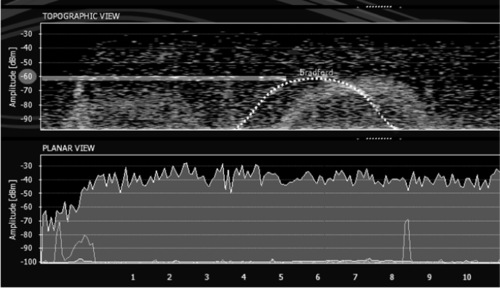
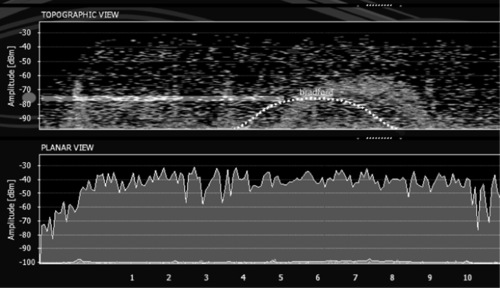
If you compare Figures 4.11 and 4.12, you'll see the signal degradation affected with the grounded foil. Figure 4.11 shows the normal signal strength. Pay attention to the white dotted line labeled “Bradford” (which happened to be the SSID name used in the lab that day). Now look at Figure 4.12, showing the Bradford SSID signal post-tampering. You'll see the dotted white line there is lower than it was in Figure 4.11. In fact, Figure 4.11 shows a signal at −60 dB, while the signal in Figure 4.12 hits −75 dB, meaning we affected a 15 dB signal loss with our grounded foil, tested from less than 50 feet away.
After the testing, we ended up with quite a pile of aluminum foil. Figure 4.13 shows a shot of the aftermath. Not wanting to waste the foil, I neglected to throw it away. I think pieces of it floated through the office for a few days, some reincarnated as hats, while others were used as creative wall hangings.
The John attack
• Using electrical engineering smarts to short an antenna
Low Tech Level 0.5
In true MacGyver style, we're back to hacking with aluminum foil, paperclips, or anything conductive and malleable.
Placing a piece of foil, or anything conductive that you can shape a bit, around the base of the antenna connector (as in Figure 4.14) and reconnecting to the AP will cause an immediate short. This ridiculously simple hack will create a huge impedance mismatch in the connectors and reduce the antenna power to almost nothing. In fact, it's quite possible this little manipulation will cause permanent damage to the antenna.
Securing the APs and antennas, as suggested earlier, will thwart this attack. If your physical security doesn't hold up, this attack will prove difficult for network staff to troubleshoot remotely. Frankly, it would be difficult for them to pinpoint the problem even with a visual survey of the AP, since the hacker would likely have left the antenna in place after his assault on the system. The AP and antennas will appear normal upon physical inspection, but one or both antennas would be destroyed by the electrical short.
One of the worst things an ill-intentioned hacker can do is get someone else in trouble with The Law, as they call it here in the South. The most trouble an attacker can cause (short of launching a threat to the White House from a wireless network they're not authorized to use) is to get the FCC involved. The Federal Communications Commission (FCC) regulates interstate and international wireless and wired communications, including radio, television, satellite, wire, and cable.
The wireless communications we mere mortals use are in unlicensed bands set aside for that purpose. We're not radio or television stations. We're just trying to surf the Internet without a wire tether. The FCC takes their job very seriously and once an unlicensed system starts to interfere with a licensed one the RF Cops will surely come a knockin'. Keep reading to see how illegal gain can be used to cause trouble with the FCC.
Your debut on COPS
• Getting ousted with illegal gain
Low-Tech Level 2
Although this attack requires minimal technology to physically execute (an antenna change), I'm giving this hack a slightly higher Low Tech Level 2 since the attacker will have to be familiar with FCC regulations and procure the illegal antenna to carry out this attack. Instead of providing the specific calculations, I'll just say that there are many online retailers that are more than happy to sell antennas that would be (in almost all circumstances) illegal to use in the United States. Perhaps the antenna is okay in other countries.…You see where I'm going with that one.
As with the other antenna attacks, mitigation can be accomplished with good physical security by way of smart mounting and appropriate locked or hidden enclosures. In addition, in an enterprise environment with wireless sensors, monitoring APs and RF management tools would catch sudden spikes in signal or power changes.
To discuss these next low tech hacks, we have to have a little bit of background on some of the more fundamental nuances of the technology. Wireless, because of the physical properties of RF, is a half-duplex system. Wireless things are listening and then either sending or receiving, not both simultaneously. Without getting into too much of the boring stuff, 802.11 systems use a combination of detection methods to determine whether it's okay to transmit. When one station wants to talk to an AP or another station, CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) kicks in to see if the airwaves are clear. If they're not, the station (and any others in range) will hold off until the RF medium isn't busy. The severity and footprint of a collision avoidance attack depend on how it was initiated. We'll look at a couple of specific scenarios, each with different methodologies and effective reaches.
Contraptions of mass disruption
• Jammers, noise makers, and homemade interference
Low Tech Level 2
The most popular jammers of this type were all the buzz just a few years ago as techies wrote articles on cell phone jamming. But that takes some calculations and adjustments to be effective. For our low tech hacks, the two easiest ways to jam up wireless are by raising the noise floor of the wireless and by exploiting the collision-avoidance mechanism used by wireless. Here we'll examine the former, which is what most people consider to be jamming, or intentional interference. Even without the frequency-matching requirement, I'm giving this attack a Low Tech Level 2. It does require some electronics, but can be pulled off with unadulterated off-the-shelf products or a small pile of household electronics cobbled together.
Jammers can be easily built from homemade electronic components or by repurposing another device that's designed to transmit on the frequency you're attacking. At the time of writing, even with the fast adoption of 802.11n, the most prevalent wireless is still 802.11b/g operating in the 2.4 GHz band. With that little piece of info, an attacker could look for transmitters using 2.4 GHz and have quite a bit of fun. I've seen everything from cordless phones to audio-video (AV) wireless transmitters used to demonstrate DoS on 802.11b/g networks. Ah, the possibilities are limitless.
Aside from homemade contraptions of mass disruption, there are a few purpose-built jammers and testing equipment that could be dangerous in the wrong hands. The attack is basically the same, but these devices are likely to be higher-powered than homemade ones and therefore have a much more effective attack range. There are legitimate uses for such devices, such as enforcement of no Wi-Fi zones on private property and by law enforcement and military to block communications or stop remote detonation. It's worth noting these jamming devices are illegal in most countries, including the United States, under the Communications Act of 1934. Remember those RF Cops mentioned earlier? Yeah, they'll find you!
Off with her head!
• The Queensland attack, continuous transmit endpoints
Low Tech Level 1
This is a comparably effortless attack. A hacker only needs this (free) tool and a laptop for a localized attack. If an attacker wanted to scale this to mastermind levels, he might take the tools and launch a distributed DoS (DDoS) by distributing a malicious payload that would execute this attack without the users' interaction. This type of attack could be targeted at a location, an organization, or even the entire Internet.
There's not much that can be done to stop this hack from occurring. The best defense against the Queensland attack for an organization is a WIPS system or an integrated security option built in to the wireless, both of which could contain an unruly endpoint via RF. Without control over the endpoint launching the attack, the best recommendation is mitigation and containment. Since this attack affects 802.11b, another option may be to standardize on 802.11n in the environment. Of course, for every attack you dodge by changing technology, you introduce a new one! Read below for more on why the Queensland attack targets 802.11b.
The Queensland attack is isolated to 802.11b networks, since 802.11a/g/n standards use orthogonal frequency-division multiplexing (OFDM) to help cope with RF medium issues. It's worth noting here because 802.11b and 802.11b/g systems are affected and in common use as organizations are still transitioning to newer and higher-bandwidth technologies like 802.11n.
Layer 2 DoS attacks
Layer 2 DoS attacks occur when an evil-doer messes around with the 802.11 frames versus the RF as in layer 1. However, akin to the Queensland attack and other exploits at layer 1, most layer 2 strikes are aimed at vulnerabilities within the documented processes required for wireless networking to operate. What that means for wireless network managers is that many attacks can't be completely prevented but can be mitigated, monitored, or secured in other ways.
It's probably fair to generalize that as we move up the stack, our technical difficulty will also increase. So, as we move into our first layer 2 attacks, you may notice the Low Tech Levels hovering around 3 and 4 versus 1 and 2 found in the previous sections. Many of these attacks can be easily launched by someone only vaguely familiar with wireless technologies, using open source applications readily available on the Internet. Even though the underlying processes may be slightly higher tech, the execution is pretty low tech.
Farewell attack
• Forcing deauthentication and disassociation
Low Tech Level 5
Here's the foundation for understanding these farewell attacks. The management messages sent between APs and wireless stations are unencrypted, unauthenticated, and unacknowledged, which means that neither side has to decode them to read them, and neither side can be certain the apparent sender is the actual sender. Also, these frames are notifications, not requests, so the recipient doesn't have the opportunity to give an acknowledgment or say okay. Think of it as the equivalent to a person announcing “I'll be back in ten minutes” and then walking out the door, versus asking “May I be excused?” and waiting for a reply. And so we have the farewell attacks, which allow hackers to leverage this behavior to force other stations to disassociate or deauthenticate from the AP.
I'm assigning this attack a Low Tech Level 5, the highest technical designation of the low tech hacks. As you'll see, the concept is extremely simple, but it does require that the attacker have a more capable wireless NIC (usually an after-market install) and enough know-how to download the right tool or driver.
If you don't spend your free time sniffing wireless packets, you may not be privy to all the goings-on that happen when a station connects to an AP.
Here are the four stages a client may go through while connecting to an AP:
1. Unauthenticated and unassociated
2. Authenticated and unassociated
3. Authenticated and associated
4. Authenticated, associated, and 802.1X authenticated
There are different types of key exchanges and authentication in wireless (WEP, WPA PSK, WPA Enterprise, 802.1X), the succession of which is inserted at different points along this procedure of connection.
Armed with an NIC and driver that support wireless packet injection, an attacker can easily spoof either a station or AP MAC address for a successful attack, and can take aim at a single device by using a unicast or all devices by using a broadcast address. Most hacker types will opt to automate the process with popular tools like Aireplay-ng (part of the Aircrack-ng suite), Nemesis, AirJack, and Winsock Packet Editor.
The order of the connection stages above is important because there are two very similar attacks to discuss: a forged disassociation and a forged deauthentication. The attacker may opt to send either type of spoofed messages. Association depends on authentication as a requisite, so by default, a deauthentication will force a disassociation also. If we pretend this is a board game, the disassociation will knock them back a space or two, while the deauthentication will put them back at the start line.
Besides a few obscure proprietary solutions, there's no standard-based answer for the farewell attacks. But wait: there is hope. In 2009 IEEE approved a standard designed to protect certain types of 802.11 management frames. Aside from this new(er) 802.11w standard, network administrators are best served using WIPS (wireless IPS) and monitoring systems to pinpoint and identify trouble areas in the wireless networks.
IEEE's new 802.11w standard for management frame protection is coming. The IEEE 802.11w standard aims to mitigate certain types of WLAN DoS attacks. 802.11w extends strong cryptographic protection to specific management frames, thereby mitigating certain classes of DoS attacks on WLANs, such as deauthentication and disassociation attacks. However, there are limitations of 802.11w's ability to thwart certain DoS attacks:
• 802.11w provides protection for certain specific 802.11 management frames only, specifically, deauthentication frames, disassociation frames, and action management frames. Hence, DoS attacks based on management frames not protected by 802.11w are still possible (e.g., association-based attacks, beacon-based attacks).
• DoS attacks based on 802.11 data and control frames are outside the scope of 802.11w.
• RF jamming-based DoS attacks cannot be mitigated via 802.11w.
I know what you're going to ask. “If this standard was passed in 2009, why aren't we using it?” The answer is pretty simple. 802.11w will require a code change/firmware upgrade on both APs and clients and that just takes time to plan and roll out. Manufacturers have to have their firmware tested and certified and organizations have to do extensive testing on clients in controlled environments to verify proper operation.
Rogue on rogue
• Using rogue mitigation from a rogue AP to attack wireless
Low Tech Level 3
Rogue detection and rogue mitigation are features on many autonomous APs, wireless controllers, and a variety of integrated and overlay wireless IPS (WIPS) systems. Rogue detection just tells the network administrator, “Hey we see these other SSIDs and MACs” and may let the administrator manually adopt them as part of the managed network or leave them as rogue devices.
Rogue mitigation takes detection one step farther, by letting the network administrator configure the AP or controller to take action against anything determined to be a rogue. Vendors may label their rogue mitigation with various sugar-coated branding efforts, but when it comes down to the ones and zeros, it's usually the same technique: a farewell attack. Yep, all our fancy wireless security systems leverage the vulnerability in management frame exchanges to launch a widespread disassociation attack against the rogue AP and any stations connected to it. If used properly in an organization, it's a good and effective security measure to protect the integrity of the wired and wireless networks. In the hands of a hacker, it's just a simplified nasty DoS attack that can be executed with a power outlet and a few clicks in a web GUI.
The best recommendation for network administrators is two-fold:
1. Monitor the wireless environment effectively with a WIPS system, and
2. Implement some controls on the wired side to prevent an attacker (or a dangerously misinformed user) from connecting a hazardous device to your network.
The latter is possible through the use of device registration, NAC solutions, wired 802.1X or MAC-auth port security, and monitoring the wire for new management traffic such as SNMP traffic.
Whack-a-rogue
• Exploiting rogue containment to launch a DoS
Low Tech Level 3
Many wireless security systems take advantage of the controllers and access points already installed throughout the environment. Using these existing devices, instead of overlaying an additional WIPS system, to help monitor and secure the wireless can be a great cost-saver, but it comes at some other expense. An AP can't be time-slicing and channel-hopping to serve wireless clients and monitor the airwaves at the same time. It can't contain a rogue AP while clients are attached, and it can't service clients when it's trying to contain a rogue.
Think of it in terms of a tractor beam. If the Enterprise is locked onto an object and containing it within a subspace/graviton interference pattern, the ship's movement and ability to perform other starship duties is hampered.
You can probably imagine, in an enterprise (lowercase enterprise, not the Starship Enterprise; we're past that) using this type of wireless security, an attacker can simply light up one or more rogue APs for the explicit purpose of causing the legitimate wireless controllers with WIPS to move APs from servicing endpoints to rogue containment mode. If the attacker places these APs strategically and times it well, he could affect a widespread DoS on the wireless. Even if some APs maintain their client connections, the additional load from clients that would normally attach to the affected APs (the ones containing the rogues) will likely overload the rest of the APs in the area and cause a domino effect of availability loss. In short, this hack can attack specific APs, but will have a domino effect and overload neighboring APs for as far as the wireless eye can see.
As with the rogue-on-rogue attack, proper monitoring systems with some manual verification and alerting is key to managing this risk. If your organization's daily operations revolve around wireless and you can't afford down time, I'd recommend a well-developed autonomous WIPS or monitoring system of your choice.
Bogus beacons
• Vulnerabilities in channel assignments
Low Tech Level 4
The attack is more properly known as illegal channel beaconing, and here's how it works. Your friendly neighborhood hacker sends a spoofed beacon to a station; it contains the same SSID the client is currently using, but the channel field has been manipulated with a bogus channel. As a point of reference, standard 802.11b/g wireless has 14 channels available. The hacked bogus beacon might tell the station to look for the AP on channel 0, 123, 456, or some other nonexistent channel. Many wireless NICs can't process the bogus channel field and they just croak and die.
This attack is relatively easy to prevent with updated firmware and NIC drivers. What am I saying? All your laptops are patched, updated, and in no way vulnerable, right? Organizations with WIPS can also leverage the RF monitoring feature and investigate suspect new devices or APs that have suddenly moved.
Flooding
• Attacks on capacity
Low Tech Level 3
Decoy SSID
• Confusion and distraction with nonexisting wireless LANs
Low Tech Level 3
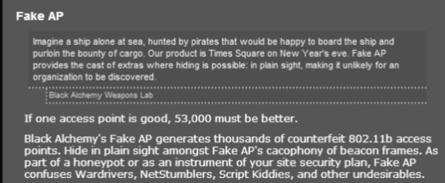 |
| Figure 4.16 A screenshot from the official website of the Fake AP project, www.blackalchemy.to/project/fakeap/, describes how their utility works |
Imagine an attacker using Fake AP, or a similar tool, that creates and advertises phony SSIDs that were remarkably similar, or perhaps even the same, as your corporate environment used. Or maybe it's a set of SSIDs chosen to specifically mimic a popular retail area with a Starbucks, Barnes and Noble, or other stores that love to advertise their free Wi-Fi. A hotel would be a smashing place to try this little trick. The attacker wouldn't need 53,000 phony APs and traffic; all that would be required is just a handful of strategically named ones.
If corporate users or hospitality guests opened their laptop and saw 12 to 15 different SSIDs, all named to appropriately reflect the native wireless they're expecting, your one or two legitimate SSIDs would be buried in the chaos and probably only a small percentage of users would make it to a real SSID and AP. If the SSID is the same, and the hacker's signal is stronger, guess which network the laptop will latch on to. Any users connecting to the hacker's Fake AP would be DoS victims, connected to decoy SSIDs that lead to nowhere.
This attack is easier to prevent in enterprise environments with managed endpoints, where the wireless network is authenticated and encrypted. In these environments, the endpoints are generally preconfigured for the enterprise network, including the appropriate security settings. The good news is, if an attacker tries this little hack on your network, someone is very likely to notice the sudden surge in SSIDs and sudden loss of service and the help desk will get some nasty calls that would alert you to the disturbance in the force.
Dead-end hijacking
• Man-in-the-middle attacks for DoS
Low Tech Level 3
In a real wireless hijacking, or evil twin attack, here's what would happen: Eager Ed (that's our hacker) would have software on a laptop that would let the laptop NIC look and act like an AP. He'd also have it configured to serve DHCP and maybe DNS. Ed would then plop down for a Hoffacino at the local coffee shop (yes, even the bad hackers like their tasty coffee beverages). He would tell his laptop to assume the identity of another legitimate SSID seen there. (If he's using some of the newer tools like Karma, the process is automated.) Eager Ed would use the farewell attack to send a disassociation to the other station(s) around. His honeypot of a signal would be stronger, so the victim laptops will immediately reconnect, but they'd unknowingly attach to his laptop instead of the real AP. At this point, Ed has all the access he needs to violate the victim laptops, deliver payloads, sniff traffic, or perform other malicious tasks. Voilà. And all before he finishes his coffee.
One of the best real-world examples of the attack described above was Rich Mogull's demonstration of a man-in-the-middle attack on a Starbuck's wireless users. In his demonstration during Defcon Security Jam in 2008, Rich showed how he was able to package Eager Ed's attack (above) into a self-contained, automated package.
Among other tricks, several of the exploits used in this setup included:
• Exploitation of browser on splash screen
• Installation of a Trojan for later access
• Sniffing traffic and man-in-the-middle attack
• Injection of HTML
• Uploading of all traffic captures to a remote server
Overall this attack is clever and relatively simple in execution and would pose an extreme danger to users were it used in the wild. The fake coffee shop book contains everything needed to compromise laptops of unsuspecting guests. The rig inserts itself in the environment and appears to be the legitimate wireless network, broadcasting the local SSID (wireless service set identifier), but with a much stronger signal to entice the laptops to attach to the rogue stack instead of the legitimate coffee shop network. Once the users are attached to attack network, the possibilities are limitless. In Rich's attack, he sends users to a browser page (such as a captive portal) that he manages and uses it to deliver an attack payload to compromise the browser. A Trojan is also installed, allowing for remote access to the system later. This attack captures all the data going to and from the endpoint and sends it up to a remote server on the Internet.
Figure 4.17 shows just how unassuming the system is, cleverly disguised as a book that looks just as normal as a cup of Joe in the shop. When opened, as in Figure 4.18, you see the equipment concealed in the book, including an AP and router.
 |
| Figure 4.17 Image courtesy of Rich Mogull |
Now, let's look at my lazy low tech hijacking. We have a similar scenario but a much less motivated hacker and the singular goal of a DoS. Lazy Lenny takes his laptop, and depending on how much Mountain Dew he's had, he may choose to just use the wireless management tools that came with his operating system or he may install the same free software Ed was using. He's okay downloading and installing the software maybe, but he doesn't feel like configuring anything. Lenny's not going to launch a payload attack and he doesn't care if the victims actually have Internet or not. He don't need no stinkin' DHCP server here. Lenny just tells his laptop to broadcast the same SSID as the coffee shop's and he sits, waits, and watches as the unsuspecting little lambs of coffee shop clientele pass in and out, befuddled as to why the wireless isn't working.
It's not the sexiest attack in the world, and I sure hate to ugly-up a perfectly beautiful automated attack, but sometimes we make sacrifices in the name of low tech. This attack could be pulled off with any device that can broadcast an SSID and has a stronger signal than the resident AP.
Attacks like this would probably be caught first by complaining users and second by your wireless monitoring system. Half-hearted attempts at an evil twin attack may be a little more obvious. If Lenny was so lazy he set up an ad hoc network with a spoofed SSID, the victim laptops would certainly identify and display it as an ad hoc (versus AP), but that doesn't necessarily keep anyone from connecting to it.
Backdoors and cracks
There are a variety of attacks that take aim at passwords and encryption keys. Some of these attacks require a little more packet savvy than others, but almost every type of cipher or key attack has an automated tool available online. Other backdoor attacks make use of the wired infrastructure or additional wireless networks that may be more easily accessible to an attacker. Access to one less secured network is usually a nice backdoor to the juicy stuff.
Crack attack
• Sniffers and automated online tools for preshared key (PSK) cracks
Low Tech Level 4
Retract that last sentence; I just realized Chapter 5 is the Surveillance chapter. In any event, there have been a flurry of tools circulating that allow hackers to passively sniff wireless traffic, collect the data, and perform a traditional encryption crack. As we learned in WWII, the more times a password is used, the more vulnerable it is. These encryption cracking tools gather as many packets as they can from the wireless traffic passing around them to and from legitimate stations and analyze the initialization vector (IV) of each. It's estimated a hacker would need to collect about 500,000 IVs to crack a WEP key. While that may sound like a lot, remember those IVs are on every packet being sent. Still, in an enterprise environment, that could translate to days' worth of packet captures.
Hackers are not too keen on waiting, so they devise a better plan. Newer encryption cracking tools use injection attacks, usually in the form of ARP flooding, to force devices to generate more packets with more IVs, in a much shorter time. This catalyst allows hackers to capture enough IVs for a crack in a matter of minutes.
But, wait. It gets better. About a year and a half ago (at the time of writing), researcher Moxie Marlinspike launched WPA Cracker, a palpably named cloud-based service that offers a pay-per-use powerhouse of hacking. The online service has at its disposal 400 processors to check a WPA or WPA2 key against a sizable 135-million-word dictionary tailored for WPA cracking. How is it tailored? Read the side note on rainbow tables and WPA encryption. The hosted service costs just $17 and $34 per use, for use of half or all CPUs, respectively, and guarantees a response time of 40 or 20 minutes.
What is a rainbow table? Most descriptions of rainbow tables reference a lot of crypto terminology, but it's really a simple concept. Many passwords are stored as hashes of the plaintext. Hashes are just one-way functions to turn legible plaintext into a fixed-length unintelligible string of characters. See the example in Table 4.3. The process is virtually irreversible, so the best way to crack a hashed code is to create a list of all possible plaintexts and their respective hashed output. If we just stop there, we're doing a dictionary attack. With a bit of cryptographic magic fairy dust, we have rainbow tables, which are like dictionary attack files, but instead include complete chains of possible hash strings that a hashed password can be dropped into and traced back to its original plaintext.
Now, if you're curious how WPA Cracker is tuned for WPA/WPA2, those two algorithms take the ESSID and salt the pre-shared key with it. What that means is the hash will be a hashed value of the combination of ESSID and PSK, instead of just the PSK. The WPA Cracker rainbow tables take this into consideration and have included this variable in their lookups.
Table 4.4 demonstrates the combination of the two individual elements used in WPA/WPA2 to create the hash. This table shows sample MD5 output using individual plaintext “myPSKcode” representing the pre-shared key and “linksys” representing the ESSID. The bottom row then shows the MD5 hash created in a WPA/WPA2 scenario where the two components (pre-shared key and ESSID) are used together to create a MD5 hash output. Notice the hash of the combined output cannot be derived from the MD5 output from the individual components.
How do you protect against these types of attacks? First of all, don't use WEP. I don't really encourage anyone to use static (or even rotating) PSKs if it's at all avoidable. If the wireless should be secured in an enterprise, then 802.1X should be used for authentication and key rotation. At this time, the keys in 802.1X and the rotation have not been exploited.
It's worth noting here that there has been an attack named Hole 196 that exploits the use of shared keys, but it is the implementation that's vulnerable and not the keys themselves.
If an organization needs to support legacy devices that can't participate in 802.1X exchanges, it should use the strongest encryption algorithm supported and isolate that usage from the rest of the network with VLANs (Virtual LANs) that terminate at a firewall or a routing switch with ACLs (access control lists) that restrict those devices only to the resources they need. A great example is a handheld scanner. If the best it can do is WPA2 with a PSK, then use that, and put them on their own VLAN that only has access to the server they communicate with.
The third piece of advice is not to use default SSIDs, even if it's not YOUR default SSID. I've seen a lot of organizations with enterprise APs that use “linksys” as the SSID to trick would-be hackers into thinking it's a different type of wireless, with a different set of default passwords etc. This will make you more vulnerable to the WPA Cracker attack, which uses thousands (maybe tens of thousands) of popular and default SSIDs in their rainbow tables.
Tap, tap. Mirror, mirror…on the wallplate
• Using mirror/monitor switch functions to grab wireless traffic
Low Tech Level 3
An attacker could also use this handy little switch feature to duplicate all traffic from an AP and send it to a laptop or other wicked hacker storage device. “But wireless traffic is encrypted,” you might argue. It's true, but most wireless, if encrypted at all, is decrypted at the AP and passed in cleartext over the wire.
There are exceptions to this rule. Some wireless vendors offer encrypted tunneling from wireless stations all the way to the controller, and extremely security-conscious organizations may implement an IPSec tunnel for their wireless clients. To address the former, a strategically placed tap could be outside the controller and catch traffic after it's been decrypted by the controller but before it leaves the network. An attacker would more than likely get a deluge of other random traffic with this placement, but that's not necessarily a deterrent. To address the latter, there's little a low tech hacker can do to break your IPSec tunnel. The more affluent hackers might go after SSL certificates and trustpoints, but evil Dopey is unlikely to get into your tunnels.
As a network administrator, it's important to understand how your wireless system works, how the APs communicate to the controller, and how it integrates into the wired network. There are many types of wireless in terms of these variables. Some authenticate and then drop traffic locally on the designated VLAN at the switch. Others tunnel (but don't encrypt) traffic from the AP to the controller so you don't have to provision all the extra wireless VLANs throughout the infrastructure. A few wireless solutions offer an option to tunnel and encrypt from the APs to the controller, and those usually also offer wireless station to controller encryption.
Modifying switch configurations isn't as difficult as you may think. I'd say 90 percent of the time, I find some hole in the wired infrastructure management, whether it's a default SNMP read/write string or a web management interface left open. In this scenario, a hacker would have an easier time with physical access to the network, but this attack can certainly be executed remotely, should he or she successfully infiltrate the network.
Taps and unauthorized monitoring can be prevented with port access controls and mitigated with strict network monitoring. Network administrators should be aware of sudden traffic spikes on previously low-volume ports, and any configuration changes.
Guesssst who got in
• Infiltrating the network via guest wireless
Low Tech Level 2
You're lucky Gary isn't a hacker, because he would have just scored complete and total network domination. I know this little trick works, because I've channeled my inner Gary on more than one occasion.
You're sure the guest network is the guest network and only has Internet access. But what you don't know is your network administrators didn't put ACLs on the routing switch. Or maybe they did, but they didn't add them to the new one installed last month. Maybe the ACLs were written for a specific guest scope and the DHCP scope was expanded and now serving addresses outside the IP range in the ACL rule. It's possible the guest VLAN terminated at the firewall and someone made an update or replaced it. Maybe the CFO came in and his daughter was having problems getting to some game she liked to play online, so the IT department temporarily removed the ACLs and forgot to reinstate them. Who knows how it happened, but the end result is your curious guests have unfettered access to your production network.
This attack gets a Low Tech Level 2 because it requires only a simple free GUI-based tool and minimal knowledge to execute. So easy, even a Gary could do it.
These types of attacks are easy to prevent but hard to maintain. A simple ACL on a switch would have prevented the attack, but keeping up with the maintenance and management of routing switches can be difficult for an IT team strapped for time. Everyone's putting out fires, and no one's teaching fire safety.
I encourage organizations to perform their own light pen tests internally from time to time. There are many tools out there that are easy to use, free or inexpensive, and that provide a wealth of information about vulnerabilities and misconfigurations on your network. I also strongly encourage network administrators and IT staff of all types to attend conferences, webcasts, and demonstrations of pen testing and hacking techniques so they can be familiar with the tools and methodologies.
There are quite a few white papers and best practice notes floating around the Internet, instructing people to use cloaked, or hidden, SSIDs as a layer of security for their wireless networks. Unfortunately, this practice does not increase security at all. To the contrary, it may even create an additional vulnerability.
Before we talk about why SSID cloaking is bad, let's take a moment to talk about what it really means. On the client side, the SSID is what users see in the list of available wireless networks that their laptop (or other wireless device) provides. On the network side, the SSID is a wireless network, with specific attributes tied to it – such as the authentication method, the encryption type, the name, and probably the VLAN (virtual LAN) it's associated with on the wired side.
When a network admin cloaks or hides an SSID, he's telling the access point not to broadcast the SSID. Broadcasting just means the AP is letting nearby clients know, “Hey, I have this wireless network.” If the AP isn't broadcasting that the wireless network is available, then the clients are forced to ask for it. This happens by configuring the laptop's preferred networks manually or by pushing those settings via a management tool. Either way, to connect to a non-broadcast network, each client must know the SSID name and its associated security settings and be configured to look for that particular network, even if it's not being broadcast. In this configuration, the wireless client, regardless of where it is, will keep looking for that network.
As an example, let's say there's an ACME Corp. that has their secured internal network configured to not let APs broadcast (cloaked SSID). The secured SSID is named “ACME-Secured” and it's using a pretty strong PSK. ACME's corporate office has close to 1,000 users, approximately 40 wireless APs, 800 laptops, and an estimated 500 other wireless devices, such as wireless-enabled phones, iPads, or Kindles. Most of the employees use the ACME-Secured network, but a few may hop on a guest network instead. With this scenario, each of the 800 laptops and 500 other devices that have used the ACME-Secured network will be looking for that network wherever they go. Outside the walls of ACME Corp., each device will be sending a beacon of “Hello, ACME-Secured network, are you there?” The devices will do this everywhere — at coffee shops, in airports, malls, and even security conferences.
The vulnerability is twofold. First, the corporate network is at risk, because each of these devices is very publicly broadcasting key information about the network. The details broadcast by the endpoints are meaningless to most but pure gold for a hacker. Second, this beaconing puts the client at risk, because someone wishing to launch a MITM (man in the middle) attack has all the information they needs to spoof the client's preferred wireless network and lure the device in to a malicious rogue connection. For more on this attack, flip back a few pages to the WARNING on Mogull's MITM attack from Defcon.
Peer-to-peer-to-hack
• Attacking peers on the wireless LAN
Low Tech Level 3
In terms of malicious activity, it means a hacker on the same network could easily get to, attack, and even deliver a dangerous payload (virus, rootkit) to any other vulnerable device within that broadcast domain. As we saw in Mogull's man in the middle attack earlier, access to the host device serves as a gateway for a variety of attacks. Viruses attack the applications and may spread to other devices on wireless (and possibly wired) networks. Rootkits provide attackers with back doors to the system. The bottom line is, once an attacker has access to the host system, many types of attacks can be launched, and the severity of the attack varies with the tools and intent. The only way to segment the traffic at layer 2 is to further VLAN the network or to physically separate the devices. There is simply no other control on a wired medium.
However, on wireless networks, we have the option of layer 2 protection not available on the wire. Here's the hitch: it's probably not enabled. Cisco calls the option PSPF (Public Secure Packet Forwarding), other manufacturers call it inter-station blocking, peer filtering, station isolation, and other similar terms. Regardless of the name, it keeps wireless stations attached to the same network from being able to see and directly communicate with one another.
Many network administrators assume this feature is enabled by default, and while I think it probably should be, the fact is even in many enterprise wireless systems, it's not. Someone has to research that vendor's moniker for this feature, find out how to enable it, and configure each controller or AP accordingly. From a hacker's perspective, I give this one a Low Tech Level 3. It's pretty simple to execute and doesn't require any special tools or applications.
There are times when using interstation blocking is not appropriate. Networks supporting medical equipment, wireless phones, handheld scanners, and proprietary systems should check with their vendor before enabling this security feature. As an example, voice over wireless (VoWiFi) phones that have push-to-talk (walkie-talkie style) features need direct communication among the devices because the protocol uses multicasting. If a wireless system needs this type of communication, just make sure those devices are on their own SSID and segmented from the other wireless data.
Securing from this attack is pretty simple. To make sure your organization doesn't fall victim to a peer hack that uses this gateway, network administrators should clearly inventory all (read: ALL) wireless, including controller-based systems and any autonomous APs, no matter how inconsequential. Once they can determine which SSIDs are being used for what and determine that interstation blocking can be enabled on one or more SSIDs, that security can be pushed throughout the wireless infrastructure. As an added layer of security, it's always recommended that organizations use endpoint security tools that offer firewall protection at the host, thwarting attacks from peers, viruses, and spyware. Most modern antivirus providers offer standalone and enterprise-managed tools with this type of protection.
We anticipate a pretty monumental shift in wireless technology over the next few years as manufacturers realize the value of virtualized technologies. At the time of writing, Meru is the only enterprise vendor I'm familiar with that is offering solutions built on virtual AP technology. In this case, virtual AP means the wireless clients see just one set of SSIDs, from what appears to be one really big AP. When this setting is enabled and a client connects, all it's aware of is itself and the virtual AP. The technology lets organizations provision a single-channel wireless infrastructure without interference, so all APs could be on Channel 11, for example, alleviating the need for extensive maintenance, channel staggering, and reduced power so channels don't overlap.
This same technology also prevents attacks like the one mentioned above from happening. Because the client and AP are in their own virtual world, clients aren't susceptible to peer attacks or even the Hole 196 vulnerability released at Defcon in 2010. Hole 196 is an insider attack that leveraged group keys in 802.1X.
With the added security and ease of manageability, I think more wireless vendors will follow suit, moving to more virtualized technologies in wireless.
Ad hoc, ad finem
• Independent basic service sets (IBSS) and ad hoc networks
Low Tech Level 2
Without an AP, everything connected in an ad hoc network is a peer; there's no master and therefore no one to regulate the chaos. Because of this, ad hocs are dangerous networks to have floating in an enterprise. You don't know who's connected to whom, what they're accessing, and you can't see or control the traffic or access. These unhampered connections cause less heartburn in homes and home offices where users are looking for the convenience of connectivity without the hassle of architecting a true network.
I've given this scenario a Low Tech Level 2 because it can be performed with a variety of wireless devices and only requires a small configuration change to implement. An ad hoc network gives a hacker surreptitious access to its peers, allowing the same type of attacks seen in the previous peer-to-peer hacks.
There are some obvious limitations to exploiting an ad hoc network, since a hacker would need to get close to your other wireless clients, as the antennas in laptops aren't as strong as those in APs. The warning to heed here: this attack is a great approach for an insider attack. The data he or she acquires, either wirelessly or via a wired bridge, is virtually untraceable. Your switches, routers, firewalls, IDS/IPS, and data leakage prevention (DLP) tools at the gateway will not see data stolen in this manner.
Organizations, especially larger ones, are strongly encouraged to use a variety of tools to protect against these types of attacks and possible data theft. Settings on laptops and forced configurations through group policy or endpoint security tools can prevent endpoints from participating in ad hoc networks. In addition, the protocol analyzer or WIPS can be used to look for IBSS traffic, which would alert you to an ad hoc network in the environment.
Acronym descramble: SSID, ESSID, BSS, IBSS. Here's how to decode the various acronyms used in 802.11 wireless.
• SSID (Service Set Identifier)
The wireless network name. It should be unique to each AP and can/should be used on multiple APs if users are roaming between APs. The SSID is what shows up in the wireless network list on your laptop.
• BSS (Basic Service Set)
A term used to describe basic 802.11 services and the standard mode for enterprises; wireless connectivity using an AP and stations. The AP controls the stations in its BSS. Think of each AP as a BSS.
• IBSS (Independent Basic Service Set)
An ad hoc network with no APs, only stations that communicate directly to one another as peers.
• ESS (Extended Service Set)
The set of interconnected BSSs with the same SSID (network name). When you add the same SSID to all APs in a building, they have the same SSID (network name) but are physically located on different access devices (BSS). The SSID that's extended across those APs is part of an ESS.
• BSSID (Basic Service Set Identifier)
Unique ID for each BSS, includes the MAC address of the AP. In ad hoc (IBSS) networks, BSSIDs are per peer devices and are made-up MAC addresses based on a random number.
Going rogue
Just a few months ago, in the first quarter of 2011, AirTight Networks (www.AirTightNetworks.com) released a report with findings gathered through extensive research on wireless security and vulnerabilities in the enterprise. The research was based on analysis of more than 200 cardholder data environments, all of which fall under regulations by Payment Card Industry Data Security Standard (PCI DSS).
One of the most significant findings from the data is that 24 percent of enterprises had rogue access points in their environments. 5 That number should be shocking to most. It's not to me, because out of the hundreds of sites I've worked with, I can count on one hand the number that I've encountered without rogue devices of some kind. The sites with zero rogues tend to be secured high risk facilities.
Almost one quarter of these organizations had rogue access points. Rogue APs are just one type of rogue device; rogue wired devices such as switches and routers may have been present, as well as rogue clients or wireless endpoints. With the recent consumerization of technology, enterprises are struggling to keep up with the latest wireless gadgets and strike a balance between productivity, employees' desire to bring new toys – I mean, tools—to the office, and an acceptable level of risk and assurance for the organization. There's a full gamut of rogue devices and vulnerabilities that pose security risks.
Following are low tech hacks involving rogue devices and rogue networks integrated into the existing enterprise network.
Marveling at the gambit of rogues
• Introducing rogue access devices on the network
Low Tech Level 2
A rogue device is any device—client or infrastructure—that attaches to your infrastructure without knowledge or consent by the organization. Rogue devices are a huge security risk in an enterprise. They open unknown and therefore unmonitored paths to data and critical resources. Someone could be siphoning data from your network at this very moment via a rogue access point, and you may never know it happened.
Should a hacker decide there are juicy tidbits on your network, he may not even need bother with breaking in to the authorized production network. Chances are, he can find an employee who's thrown a wireless AP in the office so he can move around more freely, get better signal or let his kids play online with their Internet-enabled games. I've assigned this hack a Low Tech Level 2, because our happy little hacker doesn't even need to hack much; your employee did the work for him.
In this scenario, a nefarious individual can attach to a rogue AP and 99% of the time he'll get right on the production network, instead of a guest network. Why? Because when the IT department adds wireless, it provisions the proper VLANs, networks, and settings to offer secured wireless for the organization, whereas the ignorant employee will simply plug an unconfigured AP in the most convenient wall plate (on the production network) and go on about his business. He may not even intend to leave it in place; perhaps there was some immediate and sudden need.
The key takeaway here is these rogue devices added haphazardly by non-IT employees won't have the appropriate configuration, security, and management controls. If you don't know about them, you can't manage or secure them. If you can't manage or secure them, they're at risk.
Mitigating rogue access devices, such as APs, is a daunting task. There are a variety of ways to prevent new devices from being inserted into the network or to monitor for devices after they're added. My preference is to be proactive and inhibit rogues, but if you can't do that because of logistics or budget, monitoring and reactive mitigation are acceptable. Organizations can:
• Use network access control (NAC) technologies to prevent new devices from attaching to the network
• Use dynamic VLAN assignments to force devices to authenticate before a wired port offers a production VLAN
• Use switch configurations to learn and lock to specific registered MAC addresses
• Monitor for SNMP and new devices on the wired network, matching OUIs or MAC addresses
• Monitor for new RF or SSIDs with a WIPS tool or with the existing wireless infrastructure
New SSID on the street
• Adding new networks to the production wireless
Low Tech Level 3
Regardless of the specific vulnerability, nine times out of ten, there's SOME way to access the management interface of a switch or access point. And if a hacker can get to the management interface, they can pull many underhanded tricks. Unless the hacker affects the services, for example, launching a DoS attack, the changes he or she makes may go unnoticed for an extensive period of time.
One such sly trick is to add a new SSID on a wireless AP or controller. With this, the hacker has two options, depending on the culture of the IT staff. He can add an SSID with a completely different name (something that would appear to be a neighbor's wireless, if someone were to view the list of local SSIDs from a laptop), or he can add something very similar to a current enterprise SSID that might seem like a legitimate corporate network. The former works in a smaller organization that doesn't regularly manage, maintain or audit the wireless systems. The latter works in a larger organization with a more segmented network management team. With divided responsibilities, one management team might not question a configuration change that could have been affected by another team. There also tend to be more turnover and movement of personnel within larger organizations, versus a small IT shop, with one or two folks who have built and maintained the networks for years. This hack gets a Low Tech Level 3 designation. It doesn't require special equipment, and it uses a relatively simple attack on device management, followed up with the extremely easy-to-execute process of adding an SSID.
If an attacker were to gain access to the management of an AP or controller (I've already explained why this is not farfetched at all), he could add an SSID that would be the least obvious to the users and IT team. By setting his own security options on the SSID, he wouldn't need to bypass any other security to get network access. The network wouldn't show a rogue device, because the SSID would appear to be rightly configured on an enterprise AP.
The rogue SSID would allow a hacker to access the network, possibly directly to the wired production network. You know, if I were performing this attack, I'd definitely put my rogue SSID on the production or management VLAN, depending on what my goal was. This type of access would give him entrée to the wired network, to other network devices or network users and to whatever data he configured the SSID to give him access to – servers, credit card info, HR records, etc. He'd have this access until someone noticed the additional SSID; it could be days, weeks, months, or even years.
How do you combat this attack? Handling this vulnerability is actually pretty easy, but most organizations don't think about it. I've worked with many enterprises and government offices that had a mish-mash of wireless equipment, layered with both controller-based and autonomous APs. With such a random jumble of equipment and usually a short-handed network team, these organizations rarely revisit or audit the wireless. It gets set up, it works, and it gets left alone until something breaks. Here are ways to combat this attack:
• Regular monitoring of the RF environment for new SSIDs
• Secured management interfaces for the APs, controllers, chassis hosting controllers
• Strict change management policies
• Monitoring and auditing configuration changes and alerts on changes
• Annual or semi-annual review of all wireless configurations
When reviewing wireless networks, I frequently find legacy SSIDs accidentally left in place after testing and after a migration to a different SSID. For example, an organization may have been using WEP or WPA2 with pre-shared keys (PSKs). They're moving to 802.1X, but they leave the PSK SSID up while they transition the endpoints and test, but no one goes back to de-provision the original SSID. I see it almost daily, and it becomes a risk in an enterprise. As noted above, regular reviews of the wireless configurations will help stifle these issues before they're a problem.
It's a bird…it's a plane…it's a ROGUE?
• Adding legitimate-looking rogue APs
Low Tech Level 4
The systems vulnerable to this attack are light-AP-based controllers that are configured to use a single provisioning VLAN. A provisioning VLAN is used between the controller and APs to communicate, and usually all wireless traffic is encapsulated in it. It's great for large organizations, because the IT department can add a wireless AP with different SSIDs without having to pipe through all the wireless VLANs. I'm going to use the HP WESM solution as an example. By default, it uses VLAN 2100 to communicate between the controller (HP WESM) and AP (HP Radio Port). If our guest VLAN is 99 and production wireless is VLAN 5, we still only have to extend the provisioning VLAN 2100 out to the AP. Traffic from VLANs 5 and 99 will be tunneled over VLAN 2100 with no additional VLANs on the switches along the way.
To make life even easier, many of these systems offer an auto-provisioning feature. I'm picking on HP here, because I know their VLAN assignments off the top of my head, but many other vendors do the same thing, and network administrators love it. The auto-provision lets the organization add an AP. The switch says “Hey, you're an AP, you get VLAN 2100.” The controller then sees the AP pretty immediately and auto-adopts the AP. When it auto-adopts, the configuration is pushed out, with SSIDs and security settings, and the AP is ready to use in no time!
Sounds fabulous, right? It is. It lends to a more plug-and-play-style operation and saves the IT teams from the daunting tasks of having to identify every single interswitch link and add two or more VLANs.
There's a downside to all this auto-provisioning plug-and-play. If an outside attacker or mischievous employee wanted to extend the corporate wireless network to an area that was intended to have no access, the most inconspicuous way to do so would be to use the same equipment already in place, and simply add to it. The AP would most likely be auto-adopted by the controller, and the IT staff wouldn't think anything of it. If the network staff even noticed the new addition, it would seem innocuous – just an extension of the corporate wireless. If the IT staff didn't have alerting set for new APs, they might not even notice until they performed some type of refresh or coverage survey.
Extending wireless outside the intended boundaries can be troublesome; the SSIDs and access served may be intended only for specific groups of users, in specific locations. In some instances, they're provisioned for equipment in healthcare and manufacturing and not intended for general data use. Adding APs can disrupt RF planning, compromise security containment areas, and create a quality-of-service issue if the new users cut into bandwidth for the intended users of the system.
Preventing this type of attack is straightforward. In an environment where wireless containment is critical, network managers should turn off auto-adopt and auto-provision of APs and VLANs. All organizations should set alerts that report on new APs and keep a detailed inventory of where every AP is, with its MAC address and physical location. In addition, regulated businesses may also use WIPS and RF sensors throughout their facilities or locations to alert for the presence of new RF in the environment. PCI DSS standards require this, and it's a good practice if a location shouldn't have wireless, to offer assurance that there is, in fact, no wireless:
• Disable AP auto-adoption on the controllers.
• Disable auto-provisioned VLANs on switches.
• Set specific alerts to notify a network admin of new APs.
• Use WIPS or RF sensors to monitor for new RF in protected areas.
There are organizations that may have a business case for auto-adopt and auto-provisioning, so I wouldn't make the blanket statement that these features should never be used. The IT staff just needs to be aware of the possibility and keep a closer watch on the wireless network.
Bridge bereavement
• Abuse of bridged interfaces in ad hoc clients, printers, and cameras
Low Tech Level 3
Wireless ad hoc networks aren't only menacing due to the lack of control of wireless access; they can also become gateways to the wired infrastructure in an enterprise. We've already seen how hackers can exploit ad hoc networks; think of the possibilities if they used that access to penetrate the wired infrastructure as well.
Users can bridge the wireless and Ethernet NICs, either deliberately or accidentally, through the use of self-configuring applications. In this scenario, an attacker would get immediate and probably undetectable access to your wired infrastructure, via an ad hoc network.
This attack doesn't stop at vulnerable laptops. Newer wireless-enabled printers, cameras, and other networked headless devices can also become gateways for destruction. These devices are designed with easy plug-and-play functionality, so without configuration they'll advertise and participate in ad hoc wireless networks. The other end of that printer or camera is attached somewhere to the wired network. With an 802.11-enabled printer as our example, an attacker can easily access the management interface via a web GUI, upload vulnerable firmware, and/or simply modify the settings so the wired and wireless interfaces are bridged. The same attack works on some camera and security systems as well.
Securing the network from hazardous bridged configurations requires a bit of tenacity and attention to detail. As suggested earlier, group policies and forced settings will protect laptops from misconfigurations and configuration tampering. Disallowing the use of ad hoc networks and forbidding interface bridging is a good start for laptops.
The headless devices, such as printers, are a bit more troublesome because they're so often overlooked and undocumented. The IT department should have an accurate inventory of ALL network devices and maintain an accounting of what it is, when it was added, where it is, why it's there, and who's responsible for it. Strength in enforcement can come from technology but will be more effective with organizational policy and strict regulation. To do this, the IT department must be monitoring the network regularly for new devices. The organization should have very clearly documented policies on adding networked devices, and those policies should be communicated clearly and often to all employees. If someone is discovered to have added a switch, AP, or even printer without permission, he or she should be reprimanded appropriately.
The technological difficulty for many organizations is not having the mechanism to be alerted on new devices. To this end, port access security, NAC, and MAC-based management systems offer the only enterprise-level solution. Other more manual techniques for smaller organizations may include switch-configured MAC-learn and MAC-lockdown features. These tell a switch to learn the MAC address (or addresses) of what's plugged in, and not allow anything else to be connected. Another manual option would be for the IT department to run a light network mapping scan every so often to identify devices that have been added. Free scanning tools such as NMAP can report on findings from scans to target networks. More advanced network management tools (usually paid) include advanced reporting, archival data, and comparative tools that are better at notifying the network team of changes. Just remember: knowing something has changed does no good if the organization's management team doesn't act on it and enforce policies.
• Create and communicate a clear policy on adding networked devices.
• Use directory group policy to enforce settings that protect computers from ad hoc networks and interface bridging.
• Enforce the policies by monitoring the network closely.
• Use tools to scan the network manually and look for new devices.
• Use network management applications that will monitor and alert on new devices.
Assault by defaults
I vacillated on whether or not to include this section. Avoiding susceptibilities of default configurations seems like such a no-brainer. That was my original thought, at least. Then I reconsidered. It's a problem often disregarded as being too mundane, yet I habitually see organizations fall victim to it. Besides, exploiting default configurations has to be a paramount low tech hack.
Open sesame
• Breaking in with default passwords
Low Tech Level 1
Within the realm of wireless, there are many default settings that are of interest to a hacker, including:
• Default management usernames and passwords for APs, controllers, and WIPS
• Default management usernames and passwords for wired devices servicing wireless access
• Default read/write network management strings
• Default management IP addresses
• Default serial terminal settings
• Default database accounts and passwords
• Default directory service accounts and passwords
• Default Bluetooth PINs, both on laptops and accessory devices
• Default RADIUS policies and common RADIUS shared secrets
• Default management access and absence of certificates out-of-the-box
Armed with one or more of these little gems, a hacker has the potential to modify management settings, lock out legitimate admin users, reconfigure devices, launch man-in-the-middle attacks on authentication, participate in 802.1X and other authentications without an account, attach to a device, and/or engage in out-of-band device management. These are more general assertions of possible hacks using default settings, but the list is really limitless.
I don't have to tell you what the appropriate steps are to prevent this manner of attack. (I will anyway, but I don't need to.) Always, always, always change default settings and default accounts that are provisioned within any part of a wireless system. This includes, but is not limited to, the controllers, APs, switches, endpoints, authentication and directory servers and any management hardware or software.
As seen in Figure 4.19, simple Google searches can yield a wealth of information, including default management passwords for just about any type of hardware (or software) you can imagine.
Default WPA keys
• Default PSK lookup for ISP-provided WLAN
Low Tech Level 2
The algorithm used by  to determine both the default SSID and corresponding WEP/WPA-PSK/WPA2-PSK passwords has been published on GNUcitizen.org. If you have a wireless router from
to determine both the default SSID and corresponding WEP/WPA-PSK/WPA2-PSK passwords has been published on GNUcitizen.org. If you have a wireless router from  /
/ please use the tool below to determine if you are vulnerable. Though WPA and WPA2 are by itself pretty secure,
please use the tool below to determine if you are vulnerable. Though WPA and WPA2 are by itself pretty secure,  s implementation of generating default values has proven to be flawed. Unfortunately, some ISPs like
s implementation of generating default values has proven to be flawed. Unfortunately, some ISPs like  are still distributing this router and allowing their customers to use the default (insecure) settings…. 6
are still distributing this router and allowing their customers to use the default (insecure) settings…. 6
This hack is assigned a Low Tech Level 2, because there's really not much to hack. If a hacker uses a simple wireless network scanning tool, knows the system is vulnerable to this attack, and simply uses a search engine to look up the algorithm converter, then bingo! He's in.
The obvious fix for this low tech hack is not to use default SSIDs and/or default PSKs. Most important, don't use the default PSK, but if you read the section, Crack Attack, you'll know why you shouldn't use the default SSID either.
More Google hacking
• Google hacking for wireless device mgmt interface
Low Tech Level 3
For wireless, there are a few specific Google techniques that can serve as a launching pad to many of the other low tech attacks in this chapter. One of my favorite Google hacks is searching for configuration files stored on Internet-accessible servers. If you look into Chapter 4 of Google Hacking, you'll see specific examples for using the Google inurl operator with key phrases like “conf” or “config.” Expanding on that search, you could also look for specific filename strings and file extensions, .txt, .pcc, .ini, and many others. Finding this information will give a hacker information about the organization (based on the IP or server found) and configuration of various network devices, including wireless APs, controllers, switches, routers, and more. Important information such as management configurations, SNMP strings, IP schema, routes, and VLANs could be gleaned from these configuration documents. I've also been successful in finding backup archives containing this information online. Along the same lines, you can Google foo to find log files, including Putty log files. Putty is a tool used to connect to CLI interfaces of devices, via SSH, telnet, or serial. They frequently contain technical troubleshooting output and therefore may be even more interesting and telling than just a configuration file alone.
Chapter 8 of Google Hacking details specific strings for finding Internet-accessible network hardware. With Johnny's search strings, an attacker can easily find devices such as switches, routers, wireless hardware, printers, firewalls, cameras, monitoring systems, and more. Examples include searches for “intitle:DEFAULT_CONFIG –HP” to find HP Networking switches and “intitle:”switch home page,” “cisco systems,” “ Telent–to,” for Cisco switches. The list spans seven pages and includes juicy search tidbits for all types of devices. Clearly, finding live production network devices on the Internet opens up a host of attack possibilities that can be executed remotely.
Google hacks create a field day for hackers. Save yourself from Internet-launched attacks by making sure critical systems, backups, and configurations aren't accessible from the Internet, and perform your own Google hacking every 3 to 9 months to ensure you're not a search result. Google Hacking for Penetration Testers, the cover of which is shown in Figure 4.21, is one of the best, if not the best, resources I've seen on this topic.
Bypassing specific security tools
In the great world of wireless hacking, there are even a few low tech hacks that can bypass very specific higher tech security mechanisms. In the examples below, we'll see how to bypass MAC filtering, port security, and even some of the newer NAC-based controls.
Going static
• Setting a static IP to avoid DHCP-enforced security
Low Tech Level 2
In some instances, a static IP won't be enough to bypass the system; for example, NAC solutions that use a layer 2 (VLAN) enforcement may appear to be containing clients via IPs and routing, but in reality the system is flipping VLANs at edge ports or wireless SSIDs. Setting a static IP on these will just further isolate you from the network, since you'll have assigned an IP associated to the wrong VLAN and, therefore, have no way to access any default gateway.
It's hard to say how often this hack will be successful. It's so easy to test, it would be more of a trial-and-error attack than one heavily researched by a hacker.
You'll know if this attack works on your network. Even if you don't understand the operation of your access security enough to deduce whether it's layer 2 or layer 3, you can (like the hacker) just give it a whirl and see where you get (or where you don't get). You have the added benefit of knowing your IP schema, so you can be precise in your self-pen test and know for sure whether a hacker would also be successful.
Protecting the network from statically addressed devices is multifaceted. Believe it or not, there are many organizations that are still (intentionally) using all or partially statically configured devices. Each has its own reason for doing so, and many are trying to transition, but it's important to note that some of the protection against static rogues isn't suitable for environments with intentionally static-assigned devices. For DHCP environments, there are numerous options. Most name-brand enterprise switches have DHCP protection features, some of which look for MAC addresses that appear on the switch but don't match to the DHCP requests seen going through. That gives a very high level of assurance that the device was statically configured. Other solutions are software-based and plug in to DHCP servers and/or directory services to correlate data between network devices and switches.
Organizations may also choose to provision different networks and access types for managed and unmanaged endpoints. The managed production network might offer access only to corporate assets, which can be more strictly controlled via group policy. Meaning, the IT department could set a policy to disallow employees from setting static IP addresses on any network interface. The guest, or unmanaged, devices would use another network that is perhaps less restrictive but doesn't offer access to internal resources that would pose a security risk.
Counterfeit MACs
• Basic MAC spoofing (and why it works)
Low Tech Level 3
For systems that use layer 2 enforcement on a wired or wireless network, the system uses a device's MAC address to uniquely identify it, and access is then allowed or denied to that particular MAC address. At the time of this writing, the majority of access solutions out today use MAC addresses to control access. Some more advanced solutions (like NAC) use a combination of criteria to identify and authenticate combinations of users and devices, but the vast majority of solutions aren't there yet.
MAC addresses can be changed on most devices with a few clicks of the mouse, making it an easy option for even nontechnical users. Traditionally, MAC filtering has been used more often in wireless networks than wired. There's some debate in the industry over whether or not MAC spoofing is a hack or not. Spoofing a MAC is an action usually affected on the attacker's own machine in an effort to subvert or circumvent security.
There's a current federal indictment against a programmer, Aaron Swartz, in Massachusetts, who is charged with illegally accessing the Massachusetts Institute of Technology (MIT) network in order to steal electronic documents from a non-profit who hosted archives and provided access to colleges and their students for a fee. Over the course of many weeks, Swartz subverted the security mechanisms in place at MIT with basic MAC spoofing. The college would identify the bad behavior and block the MAC address of his computer(s). Swartz would then change the MAC address, as described above, to circumvent the filter. This process repeated several times and allowed him to successfully access the network and steal millions of pages of content. The full indictment from the U.S. Courts can be found at http://web.mit.edu/bitbucket/Swartz,%20Aaron%20Indictment.pdf.
MAC switcharoo
• Using a legitimate device to get past a profiler
Low Tech Level 4
As mentioned in Going Static earlier, some network access solutions (NAC and endpoint security) use DHCP fingerprinting to identify and validate a type of device. I'm going to try to describe the behavior succinctly, but I think it's important to understand what happens so you know why this attack works.
In this incident, let's say there's a NAC solution in place, and it's configured to identify any iPads (current or new) on the network, register them in the NAC controller, and then allow them access to the production VLAN. DHCP fingerprinting is one of the most common methods for identifying common commercial network devices, such as printers, phones, handhelds, and even for identifying types of laptops and the operating systems they're running. I'm using iPads as my example because they connect wirelessly, and we're trying to hack the wireless in this scenario.
Here's how the attack plays out. George the hacker, through observation, social engineering, or good guessing, knows that iPads are allowed on the network without additional user authentication. George gets an iPad and connects to the wireless, and the iPad requests an IP address. The NAC system sees the DHCP request, knows it's an iPad, and follows its normal process of registering the device in the system using its MAC address. It's now considered a known device. George then fires up his laptop, spoofs the MAC address of the iPad, and BAZINGA: immediate access for George. Now, if George thought he was going to be abusing this wireless quite often, he could make a small adjustment to his hack and spoof his laptop's MAC address on the iPad before connecting the iPad to the wireless for the first time. This technique will work if only DHCP fingerprinting is in use to identify devices, but it may fail if the NAC is also inspecting the MAC address for the OUI (Organizationally Unique Identifier), which would divulge the manufacturer. If both are inspected and there's a mismatch between the results of the DHCP fingerprint and the OUI, then the attack variation would fail.
There's a key recommendation in network security that would save an organization from this type of attack. That recommendation is to secure appropriately and differently any portions of the network that are provisioned differently. So in this case, if iPads are allowed on the network without user authentication, then they should be segmented from the primary network, secured differently, and only allowed access to what they must have. An iPad may only need Internet access, for example, and a printer may only need to talk to a print server. With this design, an attacker could still bypass the system, but they'd have limited access to the network and likely give up and find an easier target.
<html>Free Wi-Fi</html>
• Pay for free: Hotel wireless captive portal HTML modifications and MAC duplication
Low Tech Level 2.5
The second attack is a bit more work, and so is a Low Tech Level 3, slightly higher tech than the first HTML hack. In this attack, a corrupt user approaches the task a bit differently. Perhaps this fellow is more comfortable with his free sniffer tools than with the HTML editor. In many paid wireless portals, the back-end system keeps inventory of paid devices by MAC address. This is why connecting to a paid system via wireless and moving to wired may trigger a recharge.
This stingy hacker knows how to abuse the system, so he uses a wireless protocol analyzer to look at wireless traffic and find another wireless client already paid and registered with the system. That's the hard part, if there was one. All the hacker needs to do now is spoof one of the registered MAC addresses he sniffed out, apply that to his device(s), and hop right on. It's highly unlikely he'll get any type of captive portal page or notice of charge because the wireless system thinks he's a device that's already paid.
Summary
As you can imagine, even with the breadth of low tech hacks described in this chapter, we're just hitting the tip of the iceberg. Wireless is a broad topic, with a variety of implementations throughout the world and in every facet of life. These technologies are found in at least one item, and probably dozens, in our daily activities; cell phones and hands-free calling tools, enterprise and hotspot Wi-Fi access, satellite communications, traffic and highway monitoring, wire-free audio and video technologies such as baby monitors and security cameras, RFID tagging and tracking in retail stores, and even medical devices in hospitals.
Now armed with a little technical know-how and the street smarts to protect against physical intrusions and social engineering attacks, you're well on your way to increasing the security of your wireless systems at home, in the office, and anywhere you travel along the way.
Endnotes
1.
Wiles J, personal communication
2.
Nguyen T, Nguyen D, Tran B, Vu H, Mittal N. A lightweight solution for defending against deauthentication/disassociation attacks on 802.11 networks [Internet]. 2008 [cited 2011 Sept 10]. Available from: http://www.utdallas.edu/~neerajm/publications/conferences/attacks.pdf
3.
Black Alchemy Enterprises. Fake AP [Internet]. 2001-2002 [cited 2011 Sept 01]. Available from: http://www.blackalchemy.to/project/fakeap/
4.
Merriam-Webster Dictionary [Internet]. M-W digital online edition. 2011. ad hoc [cited 2011 Sept 10]. Available from: http://www.merriam-webster.com/
5.
Is Your Wireless Safe? QSR Magazine [Internet]. 2011 Apr [cited 2011 Sept 10]. Available from: http://www.qsrmagazine.com/outside-insights/your-wireless-safe
6.
SpeedTouch default wireless/wpa/wep password security checker [Internet]. 2009 [Updated 2010 Nov 11; cited 2011 Sept 10]. Available from: http://www.mentalpitstop.com/touchspeedcalc/calculate_speedtouch_default_wep_wpa_wpa2_password_by_ssid.html
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.