High Tech Interview
Information in this chapter:
![]() A main goal of questioning a suspect
A main goal of questioning a suspect
![]() The line of questioning for suspects
The line of questioning for suspects
Introduction
There are investigators with an uncanny knack for obtaining admissions and confessions during their interrogations. Other investigators avoid interrogations because of a pattern of only being able to get requests for an attorney from suspects. Reading books on interview techniques, taking course work in interviews and interrogations, and experience can each contribute to becoming a more effective interrogator. This chapter is not designed to teach interrogations. It will give you the questions needed for interrogations that are related to computer-related investigations. Each investigator must choose the timing and the delivery of the questions to elicit the truth from the suspect based on her own training, experience, and specific knowledge of the investigation.
Some of the most successful interrogations appear more like interviews or conversations, which many times could be the best description of the activity when speaking to suspects. Although an interview is an exchange of information and an interrogation is mainly a one-way road of information, the use of the terms “interrogation” and “interview” are used interchangeably throughout this chapter. The intention, regardless of definition, is eliciting truthful statements from suspects.
In cases where a suspect has been identified and arrested with enough evidence to charge them with a crime, the interview phase can solidify details, but only if the right questions are asked which elicit truthful answers. As with any suspect interview, some questions are asked to which the investigator already knows the answer, intermingled with questions to which answers are sought. Although not a foolproof method of guaranteeing all answers are truthful, it does provide a means of corroborating known and truthful information.
The Main Goal of Questioning a Suspect
The timing of contact with a suspect in any given case is not entirely dependent on the investigator. Sometimes, a suspect may not be identified until late in the case and the interview may only be used to corroborate evidence discovered previously. Other times, suspects may be contacted early in the case, during which time the evidence may be minimal.
Either situation still requires specific questions to be asked concerning technology involved. The listing of questions in this chapter gives the interviewer a foundation of evidence-gathering questions related to technology involved in the investigation. The questions do not depend upon whether or not the suspect is interviewed early in the case or prior to submitting charges.
The best case scenario is where the suspect freely admits guilt and confesses all details of the act. The sooner, the better for everyone involved. Sometimes that happens. Most times, it does not. For these investigations, it takes a person (the interrogator) to ask another person (the suspect) questions that elicit the truth. Unlike technology, there are no physical buttons to push, no debug program to determine why a question doesn’t work. It is purely human-to-human interaction.
Non-criminal cases employ many of the same interviewing techniques as criminal investigations, although confessions and admissions won’t necessarily result in criminal convictions more so than civil penalties or internal employee discipline. With many investigations, a computer system is only a part of the crime, either by use to facilitate a crime or maybe containing evidence of a crime. Therefore, not every crime has a digital forensics examiner assigned as the lead case agent. Additionally, since the digital forensics examiner in many organizations may be a rare breed, the non-digital forensics investigator conducts high-tech interviews, sometimes to the detriment of the case when necessary questions are not asked.
The information obtained by a suspect willing to be interviewed will be beneficial whether the suspect lies, tells the truth, stretches the truth, or omits facts. Everything admitted by the suspect needs independent verification to confirm the veracity of the statements. If the statements were true, then verification goes to show credibility. Conversely, if any statements were false or misleading and further investigation can show the inconsistencies and untruthfulness, those statements then lead to the suspect’s lack of credibility. Either way, statements made are statements that, if possible, need to be fact checked through independent means.
The suggested questions listed in this chapter can be used as a guide of questioning, in any order best suited to the investigator, the suspect, and the case. The particular manner of speaking, specific words used, and interviewing methods are up to the investigator to use with these. Technical information, for which the interrogator does not understand during the questioning, may even sometimes be best left to elaborate by the suspect. This not only educates the interrogator of the suspect’s mindset, but also allows the suspect to give even more information about the alleged crime.
To assist in the corroboration of suspect statements, any alleged suspect activity on computer devices should be detailed in order for forensic examiners to more quickly prove or disprove the statements. As an example, if a suspect denies ever using a peer-to-peer networking program or downloading files with such a program, a forensic examination may find information on the system that could counter the denial, thereby, discrediting that statement and suspect’s credibility. Other information given by a suspect, especially those statements made against a penal interest, could save hours or days of an examiner’s time in looking for electronic evidence that could have been identified by the suspect.
Investigators should keep an open mind as to the number and type of electronic devices that any suspect may have access at home, work, or public locations. For practical experience, an investigator can conduct a simple walkthrough of her own home and workplace, taking note of electronic devices and the interconnectivity to each other as well as to the Internet. Even with experienced investigators, conducting an informal visual survey of the home will most times be a surprise realization of the high number of devices used by family members on a regular basis. The actual devices used by cybercriminals will not be much different than the average computer user.
As can be seen in Figure 2.1, a multitude of devices exists outside the basic desktop computer. Some of the devices have specific uses but interconnected with each other. Modems, wireless routers, external storage devices, multiple computers, multiple cellular devices, and even Internet connected game stations may contain electronic evidence as single points of analysis or as obtaining corroborating evidence for a whole picture of user activity across a spectrum of devices.
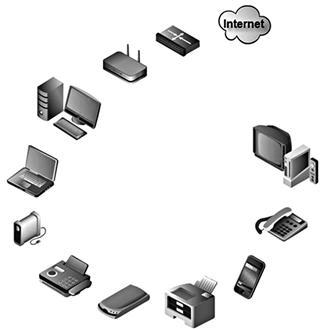
Figure 2.1 Commonly used electronic devices, any or all, may be interconnected through wired or wireless networks at home or the workplace.
The Line of Questions for Suspects
The rule of not asking any question for which you don’t know the answer works, but only if you knew the answer beforehand. In every other instance, you are asking questions to get answers. As the interviewer, it really doesn’t matter if the answers are true, half true, or lies. The goal is to corroborate the answers with other facts, regardless of what you hear in an interview.
The sets of questions in this chapter are divided by topic and purpose. Not every question needs to be asked in every interview, but having a list of possible questions will help you guide the interview with a goal to accomplish.
Computer skills, ability, and knowledge
Obtaining a foundation of computer knowledge of the suspect helps counter arguments of ignorance of technology skills at some point in the case. Most questions are benign and innocent without any inference of guilt; yet could be vitally important to the investigation. Depending upon the position of the interviewer (whether the interviewer is the forensic examiner or the case agent), certain questions may seem unimportant. It is vital for the interviewer to understand that an unimportant question asked now may be extremely important for her counterpart in the investigation later.
Questions an interviewer may not understand can still be asked, as long as the interviewer is aware of the types of answers expected from each question. The assistance of a forensic examiner, or someone more versed in technology than the interviewer, would benefit the interviewer in obtaining accurate information from the suspect. Of course, one of the best questions to ask is simply, “Did you do it and how did you do it?” and take notes!
![]() Do you have any computer training or education?
Do you have any computer training or education?
![]() What did the training and education consist of?
What did the training and education consist of?
![]() Have you ever taught computer subjects? When and where?
Have you ever taught computer subjects? When and where?
![]() Have you ever written software?
Have you ever written software?
![]() Have you ever built a computer?
Have you ever built a computer?
![]() Have you ever replaced parts of a computer?
Have you ever replaced parts of a computer?
![]() Have you ever installed software?
Have you ever installed software?
![]() What operating systems have you used?
What operating systems have you used?
![]() Are you comfortable using computers for basic tasks, such as Internet and word processing?
Are you comfortable using computers for basic tasks, such as Internet and word processing?
![]() How often do you use computers each week? How many hours per day?
How often do you use computers each week? How many hours per day?
![]() Do you have antivirus programs installed on your devices?
Do you have antivirus programs installed on your devices?
![]() Have you ever had a virus on your device?
Have you ever had a virus on your device?
![]() Did you clean the virus with any software?
Did you clean the virus with any software?
![]() Do you know what a virus or Trojan is? Do you have any on your devices?
Do you know what a virus or Trojan is? Do you have any on your devices?
![]() Have you ever defragmented your hard drives?
Have you ever defragmented your hard drives?
![]() Have you ever reformatted your hard drives?
Have you ever reformatted your hard drives?
![]() Why did you reformat your hard drives?
Why did you reformat your hard drives?
![]() Do you maintain or own any websites? Blogs? Forums? Lists?
Do you maintain or own any websites? Blogs? Forums? Lists?
![]() What are the website Internet addresses?
What are the website Internet addresses?
![]() When did you start maintaining or create the websites?
When did you start maintaining or create the websites?
![]() What content is on the websites? Blogs? Forums? Lists?
What content is on the websites? Blogs? Forums? Lists?
Password, encryption, steganography, and deletion
The presence of encryption plays an important aspect of any digital forensics examination. Considering that many current operating systems include encryption features by default and Internet users can easily download any one of dozens of encryption programs, the odds of approaching encrypted systems or encrypted data increase. Depending upon the encryption scheme used coupled with a complex passphrase, it may be literally impossible to access certain files, folders, or entire storage devices that have been encrypted. The quickest method to obtain passphrases is usually just politely “ask” to be given the password by the suspect. And many times, it may be the only method to gain access.
As many electronic devices also have encryption or password protection features, such as smartphones and USB flash drives, interviewers should remember to obtain passphrase information to all devices. Assuming computer users have ill intent using encryption would be a risky assumption to make, especially as many devices and programs require a password to log into the system or program. Rather than assume data has been encrypted for nefarious purposes, let the suspect describe the intentions behind using encryption. Perhaps the use is innocent and unavoidable, but perhaps the suspect will detail intentional attempts to hide criminal evidence through the means of encryption.
An uncommon use of computers involves steganography. Steganography as it relates to electronic data simply means that data is hidden from view as to not be seen. The presence of data hidden using applications designed for steganography is significant to show intention of the suspect in knowingly concealing evidence. Forensic examiners will never know how many times they encounter steganography, other than the times they actually discovered steganography.
Given the high likelihood that properly hidden electronic evidence may never be found, it is crucial to obtain this information from the suspects through interrogations. Figure 2.2 shows a freeware utility capable of easily hiding files within files through a few clicks of the mouse. As the ease of hiding data increases, the odds that data will be hidden by suspects also increase.
![]() Do you use encryption for files or computers?
Do you use encryption for files or computers?
![]() What software do you use to encrypt?
What software do you use to encrypt?
![]() What are your current passwords?
What are your current passwords?
![]() What are past passwords you have used in the past?
What are past passwords you have used in the past?
![]() Do you have hidden files? How are they hidden?
Do you have hidden files? How are they hidden?
![]() Do you have hidden partitions or volumes? How are they hidden?
Do you have hidden partitions or volumes? How are they hidden?
![]() Do you have any hidden volumes or partitions hidden within encrypted containers?
Do you have any hidden volumes or partitions hidden within encrypted containers?
![]() Does anyone else know or use any of your passwords?
Does anyone else know or use any of your passwords?
![]() When do others use your passwords?
When do others use your passwords?
![]() Do you have a written or printed list of your passwords?
Do you have a written or printed list of your passwords?
![]() What is your login information to each of your devices?
What is your login information to each of your devices?
![]() Do you empty the Recycle Bin/Recycler/Trash Bin? How often?
Do you empty the Recycle Bin/Recycler/Trash Bin? How often?
![]() Have you ever wiped an entire hard drive?
Have you ever wiped an entire hard drive?
![]() How did you wipe the hard drive?
How did you wipe the hard drive?
![]() Do you use steganography or data hiding programs?
Do you use steganography or data hiding programs?

Figure 2.2 Steganography programs can easily hide electronic data within electronic data. Xiao Steganography, http://www.nakasoft.net.
Control of the device(s) in question
A claim from a suspect that no other person had access to the computer device used in a crime is a powerful statement. However, specific questions asked about the control of the devices should still be asked to ensure no details, alibis, or failure to recollect details accurately occur later by the suspect. These specific questions clarify any doubts as to the person or persons that had access or control of an evidence device.
![]() Is this device (computer, phone, etc.) yours?
Is this device (computer, phone, etc.) yours?
![]() Do you have the owner’s permission?
Do you have the owner’s permission?
![]() Does anyone else have permission to use it?
Does anyone else have permission to use it?
![]() Does anyone else have access to it?
Does anyone else have access to it?
![]() Does anyone else have the login information?
Does anyone else have the login information?
![]() What is the name of their account?
What is the name of their account?
![]() Does anyone else use your account? Who? Why? When?
Does anyone else use your account? Who? Why? When?
![]() Did you ever have other devices?
Did you ever have other devices?
![]() Does anyone else have access to them? Who?
Does anyone else have access to them? Who?
![]() When was the last time you used the device?
When was the last time you used the device?
![]() When was the last time someone else used the device?
When was the last time someone else used the device?
![]() Did they have your permission?
Did they have your permission?
![]() What do you use the device for?
What do you use the device for?
![]() Where do you normally use the device?
Where do you normally use the device?
![]() Where else have you used the device? Home? Work? Public places?
Where else have you used the device? Home? Work? Public places?
![]() Is the room secured where the device is stored?
Is the room secured where the device is stored?
![]() Is there a key to enter the room/office/home?
Is there a key to enter the room/office/home?
![]() Who has access to the key or spare keys?
Who has access to the key or spare keys?
![]() Is there a keycard access to the room/building/office?
Is there a keycard access to the room/building/office?
![]() Have you allowed use of your keycard to anyone?
Have you allowed use of your keycard to anyone?
- Why did you allow someone to use your keycard?
![]() Do you have remote access configured for any computer?
Do you have remote access configured for any computer?
![]() From where do you remotely access your computer?
From where do you remotely access your computer?
![]() What activity do you usually conduct when connected remotely?
What activity do you usually conduct when connected remotely?
![]() Does anyone else connect to your computer remotely?
Does anyone else connect to your computer remotely?
- Who do you allow to do this?
- Why do you allow others to connect remotely to your computer?
Other devices used by suspect
![]() What other devices do you own? (Laptops, PDA, smartphones, external hard drives, etc.)
What other devices do you own? (Laptops, PDA, smartphones, external hard drives, etc.)
![]() How many cell phones do you have?
How many cell phones do you have?
- Have you taken photos or videos with the cell phones?
- Where are the photos and videos saved?
![]() How many desktop and laptop computers do you have?
How many desktop and laptop computers do you have?
![]() Do you have other types of computer systems?
Do you have other types of computer systems?
![]() When did you last use each device?
When did you last use each device?
![]() What did you use the devices for?
What did you use the devices for?
![]() Does anyone else have access to them?
Does anyone else have access to them?
![]() When were the devices used by someone else?
When were the devices used by someone else?
![]() Do you use your computers at your work for personal use?
Do you use your computers at your work for personal use?
![]() How many work computers have you used for personal use?
How many work computers have you used for personal use?
![]() Do you have an assigned computer?
Do you have an assigned computer?
![]() Have you downloaded personal files with work computers?
Have you downloaded personal files with work computers?
![]() How else do you use work computers for personal business?
How else do you use work computers for personal business?
Software used by suspect
![]() What operating systems do you use?
What operating systems do you use?
![]() What types of programs do you use?
What types of programs do you use?
![]() Do you use any password or encryption programs?
Do you use any password or encryption programs?
![]() Do you use any programs that hide your identity?
Do you use any programs that hide your identity?
![]() Do you install the programs yourself?
Do you install the programs yourself?
![]() Do you download programs from the Internet?
Do you download programs from the Internet?
![]() What kind of programs have you downloaded?
What kind of programs have you downloaded?
![]() Have you ever written any programs or code?
Have you ever written any programs or code?
![]() Have you modified the code of any programs?
Have you modified the code of any programs?
![]() Have you ever used cracked or pirated software?
Have you ever used cracked or pirated software?
![]() Have you ever shared a copy of it?
Have you ever shared a copy of it?
![]() Did you install “name of software?”
Did you install “name of software?”
![]() When did you last use this software?
When did you last use this software?
![]() How did you use this software?
How did you use this software?
Internet use by suspect
![]() Do you have Internet access at home?
Do you have Internet access at home?
![]() What is your Internet Service Provider (ISP)?
What is your Internet Service Provider (ISP)?
![]() Do you have wireless Internet in your home?
Do you have wireless Internet in your home?
![]() How long have you had this ISP?
How long have you had this ISP?
![]() Is your wireless encrypted or open access?
Is your wireless encrypted or open access?
![]() Does anyone else have access to your Internet account?
Does anyone else have access to your Internet account?
![]() Does anyone else have access to your Internet?
Does anyone else have access to your Internet?
![]() Who else has access? When was the last time used by someone else?
Who else has access? When was the last time used by someone else?
![]() Do you have other means to access the Internet?
Do you have other means to access the Internet?
- Why do you have other Internet access accounts?
![]() Which Internet browsers do you use?
Which Internet browsers do you use?
![]() Do you clear your Internet history?
Do you clear your Internet history?
![]() How often do you clear the history?
How often do you clear the history?
![]() Do you use any method of concealing your IP address?
Do you use any method of concealing your IP address?
![]() Which search engines do you use?
Which search engines do you use?
![]() Do you bookmark favorite websites?
Do you bookmark favorite websites?
![]() Which websites have your bookmarked as favorites?
Which websites have your bookmarked as favorites?
![]() How often do you revisit these websites?
How often do you revisit these websites?
![]() What are some of your favorite bookmarked websites?
What are some of your favorite bookmarked websites?
![]() What search terms do you usually search?
What search terms do you usually search?
![]() How often do you search for these terms?
How often do you search for these terms?
![]() When was the last time you searched for these terms?
When was the last time you searched for these terms?
![]() What were the most recent words you searched?
What were the most recent words you searched?
![]() Do you use any method to clear your search history?
Do you use any method to clear your search history?
- Why do you clear your search history?
- When was the last time you cleared your search history?
![]() Do you search for pictures on the Internet?
Do you search for pictures on the Internet?
![]() What words do you search for pictures?
What words do you search for pictures?
![]() What kinds of pictures show in the search results?
What kinds of pictures show in the search results?
![]() Do you download these pictures? When? How many? How often?
Do you download these pictures? When? How many? How often?
![]() Do you view pornography on the Internet?
Do you view pornography on the Internet?
- Do you download pornography? How much? How often?
![]() Are they posted online or shared with anyone?
Are they posted online or shared with anyone?
![]() Do you search for movies or videos on the Internet?
Do you search for movies or videos on the Internet?
![]() What kind of movies or videos?
What kind of movies or videos?
![]() What search terms have you used?
What search terms have you used?
![]() When was the last time you searched for movies or videos?
When was the last time you searched for movies or videos?
![]() Did you download the movies or videos?
Did you download the movies or videos?
![]() Did you watch any of the movies or videos?
Did you watch any of the movies or videos?
![]() Did you share any movies or videos with anyone?
Did you share any movies or videos with anyone?
![]() Have you sold any of the videos or movies you downloaded?
Have you sold any of the videos or movies you downloaded?
- Did you sell them online or in person?
![]() Have you ever used Virtual Private Networks?
Have you ever used Virtual Private Networks?
![]() What is your login information?
What is your login information?
Online chat, email, forums, boards, online social networking
Few persons are not connected through any number of social networking Internet services. Information posted in these accounts by the users can assist in obtaining investigative leads or evidence from the services directly. Most social networking services keep logs of a user’s access to their websites which can include Internet protocol (IP) addresses, date/time of login, and information posted.
Alibis may be proven or disproven depending upon the totality of the alibi with other corroborating information, such as obtaining the IP address of specific logins to place a person at a location during a specific time. Also, other related victims and suspects may be identified through the review of information obtained from these online services.
![]() What program do you use to chat?
What program do you use to chat?
![]() What are your nicknames/user names/screen names?
What are your nicknames/user names/screen names?
- How did you pick these names?
- Do you use these names on multiple chat system?
- What are your passwords to access chat?
![]() When was the last time you chatted online?
When was the last time you chatted online?
![]() What did you/do you chat about?
What did you/do you chat about?
![]() Have you ever transferred files while chatting?
Have you ever transferred files while chatting?
- Who did you transfer the files to/who did you receive files from?
![]() Do you play games in chat rooms?
Do you play games in chat rooms?
![]() How often do you play these games?
How often do you play these games?
![]() Do you play games online to meet children?
Do you play games online to meet children?
![]() Have you ever met anyone in person that you met online?
Have you ever met anyone in person that you met online?
![]() Have you met more than one person?
Have you met more than one person?
![]() Who were these people you met?
Who were these people you met?
![]() What type of email do you use?
What type of email do you use?
![]() What are your email addresses?
What are your email addresses?
![]() Do you save or delete your email?
Do you save or delete your email?
![]() Does anyone have access to your email accounts or passwords?
Does anyone have access to your email accounts or passwords?
![]() Why do you allow access to your email?
Why do you allow access to your email?
![]() Do you send attachments in emails?
Do you send attachments in emails?
- What kinds of attachments do you send?
- Who do you send attachment to?
![]() When was the last time you used your email accounts?
When was the last time you used your email accounts?
![]() What are other email accounts you have used in the past?
What are other email accounts you have used in the past?
- Did anyone else have access to these accounts?
![]() Do you visit forums or Internet boards?
Do you visit forums or Internet boards?
![]() Have you commented or shared files on these forums/boards?
Have you commented or shared files on these forums/boards?
![]() Have you received files from any of these forums/boards?
Have you received files from any of these forums/boards?
![]() How often do you visit these forums/boards?
How often do you visit these forums/boards?
![]() What are your user names/screen names/login for these forums/boards?
What are your user names/screen names/login for these forums/boards?
![]() What user groups do you belong?
What user groups do you belong?
![]() Who is on your “buddy” or “friend” lists?
Who is on your “buddy” or “friend” lists?
![]() Have you met any face to face?
Have you met any face to face?
![]() Do you have a Facebook account?
Do you have a Facebook account?
![]() What is your user name and login information?
What is your user name and login information?
![]() Does anyone else have access to your account?
Does anyone else have access to your account?
![]() How often do you log into the account?
How often do you log into the account?
- Do you play games on Facebook?
![]() What other social websites do you visit or have accounts?
What other social websites do you visit or have accounts?
![]() Do you use dating websites? What is your user information?
Do you use dating websites? What is your user information?
Suspects that browse the Internet with applications configured to allow for anonymity on the Internet have the ability to interact with others, such as victims of their harassment without being tracked by their true IP address. Some methods of anonymous browsing configurations include using virtual private networks (VPN) and The Tor Project (Tor) browser. With each of these methods, the IP address of the suspect is hidden through a series of random global nodes.
Figure 2.3 shows the Tor Network Map, in which the suspect’s originating IP address is hidden behind dozens of anonymous relays, preventing detection. The IP address will only be from a Tor exit node, not the actual IP address of the suspect. Although these methods of remaining anonymous online are not illegal, questioning the intentions of use of these applications by suspects builds evidence in their knowledge of attempting to thwart investigative efforts.
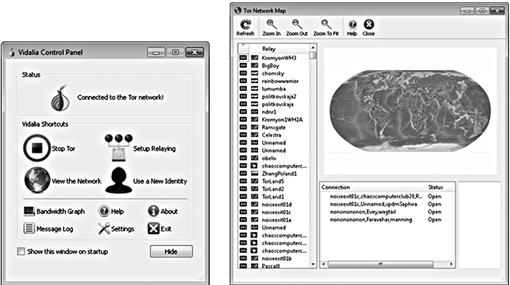
Figure 2.3 The Tor Project (Tor) application allows for anonymous Internet surfing. http://www.torproject.org.
Identifying each uncommon use of a computer system gives the investigator insight into the mindset of the suspect. The average computer user does not typically hide data under other data, encrypt data, wipe data, and cloak IP addresses while surfing the Internet on a regular basis. The combination of all of these types of activity gives the impression that not only was the suspect well versed in computer technology, but also took advantage of uncommonly used technology to facilitate crimes. This is not to say use of these applications is illegal, but coupled with criminal activity, their use can show facilitation of the criminal activity.
Another key component in questioning suspects about their use of programs includes discovering their intention and knowledge of using file sharing programs. File sharing programs, such as Frostwire seen in Figure 2.4, allow for files to be downloaded from many sources, globally. Several file sharing applications can be configured to search and download files automatically and be left virtually unattended by a computer user.
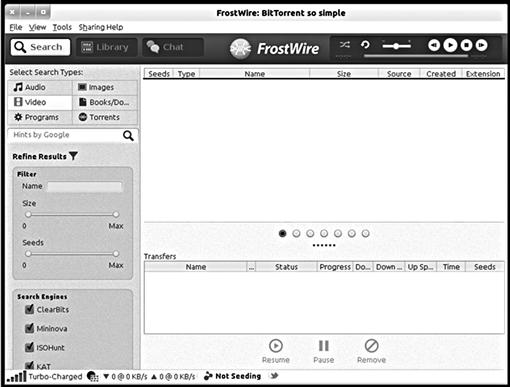
Figure 2.4 Frostwire is one of many “Peer-to-Peer” file sharing applications. http://www.frostwire.com.
Claiming ignorance as to the types of files downloaded may be plausible if enough information is not obtained to prove or disprove knowledge and intention. Digital forensics most likely will show the use of file sharing programs to include the files searched, downloaded, and shared. For example, downloaded files that have been renamed, placed into a folder other than the default download folder, or copied onto removable media show the suspect’s intent to view and save the files.
Peer-to-Peer Networking
![]() Do you use Peer-to-Peer Networking software?
Do you use Peer-to-Peer Networking software?
![]() What is the name of the software?
What is the name of the software?
![]() Do you search for files with the software?
Do you search for files with the software?
![]() Have you downloaded files with the P2P programs?
Have you downloaded files with the P2P programs?
![]() Have you shared files or folders with the software?
Have you shared files or folders with the software?
![]() What kind of files have you downloaded?
What kind of files have you downloaded?
![]() What kind of files have you shared?
What kind of files have you shared?
![]() Is your software installed by default or did you make changes?
Is your software installed by default or did you make changes?
![]() What other changes did you make?
What other changes did you make?
![]() Why did you make those changes?
Why did you make those changes?
Duplicating and storing data on a local media, such as desktops, laptops, and external storage devices, has quickly become common practice in homes and businesses. Forensic examinations of storage media can find all files that have been backed up or copied and sometimes deleted. However, forensic examinations of storage media will not be able to recover data that has been stored online. Finding traces of information leading to believe data may be stored online is important, but more important is being able to access that data.
Online data storage services, otherwise known as the “Cloud,” range from freely available to paid services. Configurations of online storage can be set to backup specific folders or an entire system, automatically and incrementally. Online data storage services usually encrypt the customer’s data and may not be able to decrypt the data that exists on their storage servers without the customer’s credentials. Without having access to any notes containing login credentials, it is critical to obtain them from the suspect through the interview process.
Investigators should also be aware that data stored in the Cloud may be shared with other users. Having shared access allows for the users to upload and delete files as well as potentially cancel accounts. If electronic evidence is suspected of being stored in the Cloud, precautions need to be taken immediately, such as sending preservation orders to the providers in preparation of obtaining search warrants to prevent destruction of the evidence.
There are a number of services currently available at no charge, such as ADrive seen in Figure 2.5. ADrive offers a free online storage capacity of 50 GB for every account. Paid accounts allow for even more online storage. Those investigators tasked with investigating child pornography cases may want to remember the potential evidence cache of online storage. Offenders using these types of freely available systems can share illicit images directly with other offenders, without the need of peer-to-peer networking applications.
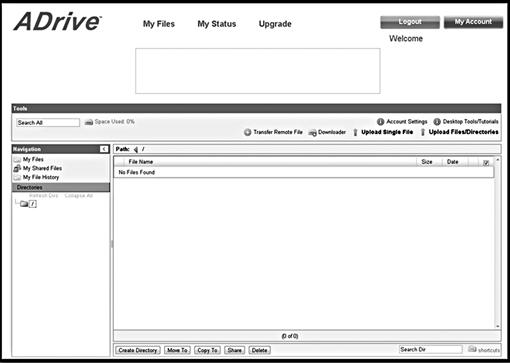
Figure 2.5 ADrive online storage, http://www.adrive.com.
File storage
![]() Do you store files on your computer hard drive?
Do you store files on your computer hard drive?
![]() Where do you store them on your hard drive?
Where do you store them on your hard drive?
![]() Do you organize your saved files?
Do you organize your saved files?
![]() What kind of files do you save?
What kind of files do you save?
![]() Do you make backups of your computer hard drive?
Do you make backups of your computer hard drive?
![]() What do you store the backups on?
What do you store the backups on?
![]() Are they encrypted? What are the passwords?
Are they encrypted? What are the passwords?
![]() Does anyone else have access to your backups?
Does anyone else have access to your backups?
![]() How many flash drives do you own?
How many flash drives do you own?
![]() What is stored on the flash drives?
What is stored on the flash drives?
![]() Do you use external hard drives?
Do you use external hard drives?
![]() How many external hard drives do you own?
How many external hard drives do you own?
![]() What is stored on the external hard drives?
What is stored on the external hard drives?
![]() Do you encrypt these hard drives?
Do you encrypt these hard drives?
![]() Have you ever replaced a hard drive on your computer/s?
Have you ever replaced a hard drive on your computer/s?
![]() What did you do with the previous hard drive?
What did you do with the previous hard drive?
![]() What service do you use to store files online?
What service do you use to store files online?
![]() How often do you use online storage?
How often do you use online storage?
![]() What is you login information?
What is you login information?
![]() Are the online files encrypted?
Are the online files encrypted?
![]() Are the files accessible by anyone else? Who else? Why?
Are the files accessible by anyone else? Who else? Why?
![]() Do you share files with others with these services?
Do you share files with others with these services?
![]() Does anyone else have access to your online storage?
Does anyone else have access to your online storage?
![]() When did they last access your files?
When did they last access your files?
![]() Has anyone else uploaded files to your storage? Who? When? What files?
Has anyone else uploaded files to your storage? Who? When? What files?
Crime specific—child pornography
Child pornography investigations sometimes involve hundreds of thousands of images with most of the images leaving no question that the subjects in the images are children. Other times, the subjects may not be clearly identified as children. As the mere possession of child pornography is a crime, these investigations could be considered easier than other computer-related crime.
However, that would be an incorrect assumption. If not simply for the benefit of other past and future victims, questioning suspects involved in this crime could not be more important, to not only prove a case, but to also find unreported cases of exploited and missing children. The following list of questions for Child Pornography is not all inclusive but is specific to computer use. Other questions, such as asking specific details related to the crime and victims, should also be asked.
![]() Can you tell me what you believe child pornography to be?
Can you tell me what you believe child pornography to be?
![]() How do you know it was child porn?
How do you know it was child porn?
![]() Have you searched online for child pornography?
Have you searched online for child pornography?
![]() What search engine did you use?
What search engine did you use?
![]() What search terms did you use?
What search terms did you use?
![]() Did you find child porn through searching online?
Did you find child porn through searching online?
![]() Did you download any child porn from searches?
Did you download any child porn from searches?
![]() Have you ever uploaded child porn to the Internet?
Have you ever uploaded child porn to the Internet?
![]() Have you used Peer-to-Peer Networking programs to access child porn?
Have you used Peer-to-Peer Networking programs to access child porn?
![]() Have you downloaded child porn using P2P?
Have you downloaded child porn using P2P?
![]() Have you shared child porn using P2P?
Have you shared child porn using P2P?
![]() Have you ever encountered child porn on the Internet unintentionally?
Have you ever encountered child porn on the Internet unintentionally?
![]() Is there child pornography on your computer/s?
Is there child pornography on your computer/s?
![]() Describe the child pornography on the computer.
Describe the child pornography on the computer.
![]() What file formats do you use? JPG? AVI?
What file formats do you use? JPG? AVI?
![]() Did you rename any child porn files?
Did you rename any child porn files?
![]() Did you organize any child porn files? By age group? By sex? By act?
Did you organize any child porn files? By age group? By sex? By act?
![]() Did you copy any child porn to compact disks or other devices or media?
Did you copy any child porn to compact disks or other devices or media?
![]() Have you ever deleted child pornography from your computer?
Have you ever deleted child pornography from your computer?
![]() How many images and videos of child porn do you estimate to have?
How many images and videos of child porn do you estimate to have?
![]() Have you ever sent or received child porn in an email?
Have you ever sent or received child porn in an email?
![]() How else do you trade/buy/sell child porn?
How else do you trade/buy/sell child porn?
![]() Have you ever received spam that was child porn?
Have you ever received spam that was child porn?
![]() Have you printed child pornography from your computers?
Have you printed child pornography from your computers?
![]() Where are those printed photos?
Where are those printed photos?
![]() What printer or printers did you use?
What printer or printers did you use?
![]() Have you shared those printed photos with anyone?
Have you shared those printed photos with anyone?
![]() Who have you shared them with?
Who have you shared them with?
![]() Have you ever copied printed pages of child porn?
Have you ever copied printed pages of child porn?
![]() What copy machine did you use?
What copy machine did you use?
![]() What did you do with the copies?
What did you do with the copies?
![]() Do you keep any photos of children?
Do you keep any photos of children?
![]() Do you search for “pre-teen” images or “Lolita” websites?
Do you search for “pre-teen” images or “Lolita” websites?
![]() Do any of your friends or family know you have child pornography?
Do any of your friends or family know you have child pornography?
![]() Do they also have child pornography?
Do they also have child pornography?
![]() Have you shared child pornography with them?
Have you shared child pornography with them?
![]() How old do you think the children are in the images?
How old do you think the children are in the images?
![]() Are you sexually aroused by the child porn images?
Are you sexually aroused by the child porn images?
![]() Have you taken photos of children…
Have you taken photos of children…
![]() Where did you meet these children?
Where did you meet these children?
![]() How did you meet these children?
How did you meet these children?
![]() Have you communicated with minors online?
Have you communicated with minors online?
![]() Have you sent photos to the minor? What kind of photos?
Have you sent photos to the minor? What kind of photos?
![]() What were the screen names of the minors?
What were the screen names of the minors?
![]() Have you ever meet a minor face-to-face that you met online?
Have you ever meet a minor face-to-face that you met online?
![]() What took place during the meeting and any subsequent meetings?
What took place during the meeting and any subsequent meetings?
![]() How far did you have to travel?
How far did you have to travel?
![]() Did you have sex with the minor?
Did you have sex with the minor?
![]() What percentage of your pornography collection are minors?
What percentage of your pornography collection are minors?
![]() Do you know anyone that has taken photos of minors engaged in sex acts?
Do you know anyone that has taken photos of minors engaged in sex acts?
![]() Do you have or have you seen those photos or videos?
Do you have or have you seen those photos or videos?
![]() Who took the photos or videos?
Who took the photos or videos?
![]() Where the children were first met?
Where the children were first met?
![]() Have you had sexual fantasies about children you have seen in photos/videos?
Have you had sexual fantasies about children you have seen in photos/videos?
![]() Do you know what NAMBLA refers to?
Do you know what NAMBLA refers to?
![]() Do you know what Lolita refers to?
Do you know what Lolita refers to?
![]() Do you know what “pre-teen” refers to?
Do you know what “pre-teen” refers to?
![]() What percentage of your pornography collection are adults only?
What percentage of your pornography collection are adults only?
Crime specific—identity theft
![]() Have you ever purchased ID cards fraudulently?
Have you ever purchased ID cards fraudulently?
![]() Have you ever used a stolen ID to purchase items or obtain credit?
Have you ever used a stolen ID to purchase items or obtain credit?
![]() Have you ever sold a person’s personal information?
Have you ever sold a person’s personal information?
![]() Have you used scanners to scan stolen ID cards or ID cards you created?
Have you used scanners to scan stolen ID cards or ID cards you created?
![]() Have you ever portrayed yourself with another’s personal information to obtain items or credit?
Have you ever portrayed yourself with another’s personal information to obtain items or credit?
![]() Have you ever searched for methods of obtaining personal information to create fraudulent ID card?
Have you ever searched for methods of obtaining personal information to create fraudulent ID card?
![]() What search engine did you use?
What search engine did you use?
![]() What search terms did you use?
What search terms did you use?
![]() Have you used software programs to create and alter ID cards?
Have you used software programs to create and alter ID cards?
![]() What are the names you have used that were obtained through theft or fraud?
What are the names you have used that were obtained through theft or fraud?
![]() What items have you purchased using fraudulent ID and credit cards?
What items have you purchased using fraudulent ID and credit cards?
![]() Do you know any persons that create fraudulent ID cards and credit cards?
Do you know any persons that create fraudulent ID cards and credit cards?
![]() Have you provided them with someone’s personal information?
Have you provided them with someone’s personal information?
![]() Have you paid for services from them? When?
Have you paid for services from them? When?
![]() Where did you get personal information used to obtain credit in someone else’s name?
Where did you get personal information used to obtain credit in someone else’s name?
![]() Do you have personal information about other persons on your device?
Do you have personal information about other persons on your device?
![]() What information do you have on other people?
What information do you have on other people?
![]() Where did you get this information?
Where did you get this information?
![]() Have any of the names been used to create credit cards or ID cards?
Have any of the names been used to create credit cards or ID cards?
![]() Have any of the names been used in any manner by you or others?
Have any of the names been used in any manner by you or others?
Other alleged crimes
Creating an atmosphere where suspects admit their guilt with graphicaly details helps any investigation. But it may be also helpful for other investigations to not only obtain information about their involvement in the criminal acts under investigation, but also about other yet to be detected crimes.
At times, asking questions about criminal activity, other than the crime in question, can lead to information beneficial to other cases. Suspects may also be more apt to give information on others and their crimes rather than personally admit guilt.
![]() Do you know why you are arrested/investigated/questioned?
Do you know why you are arrested/investigated/questioned?
![]() Have you ever been questioned about this sort of thing before? When? By whom?
Have you ever been questioned about this sort of thing before? When? By whom?
![]() Have you ever been charged or arrested for this type of crime before? When? Where?
Have you ever been charged or arrested for this type of crime before? When? Where?
![]() Do you know what this alleged act consists of?
Do you know what this alleged act consists of?
![]() Do you know why someone would accuse you of any crime or this crime? Who?
Do you know why someone would accuse you of any crime or this crime? Who?
![]() Do you know the identity of anyone that may have committed this crime?
Do you know the identity of anyone that may have committed this crime?
![]() Do you know of any others that may be involved in any aspect of this crime?
Do you know of any others that may be involved in any aspect of this crime?
![]() How do you know they are involved?
How do you know they are involved?
![]() Do you know any others involved in any other crimes?
Do you know any others involved in any other crimes?
Questions for Victims
Computer-related questions for victims are not intended to prove or disprove their knowledge of computer systems, but rather to help determine the role of those systems in a crime. Victims may not be as well versed with computer systems as their victimizers, which can make them easy prey to scammers, phishing attacks, and hacking.
The questions posed to the victims will hopefully lead to information as to how they were victimized in order to determine the identity of the suspect. The questions also will help prevent overlooking physical evidence to be collected, such as recorded voicemails or printed pages of emails and websites.
Computer crime victim questions—identity theft
![]() How often do you use your computer?
How often do you use your computer?
![]() Do you have anti-virus software installed? Is it up to date?
Do you have anti-virus software installed? Is it up to date?
![]() Have you had viruses on your computer before?
Have you had viruses on your computer before?
![]() Have you given your name, date of birth, social security number to anyone in any email?
Have you given your name, date of birth, social security number to anyone in any email?
![]() Did you speak to anyone on the telephone too?
Did you speak to anyone on the telephone too?
![]() Do you have any contact information or name of the person?
Do you have any contact information or name of the person?
![]() Did you fax or mail any information?
Did you fax or mail any information?
![]() Have you received emails from a bank or other institution asking to provide your account information?
Have you received emails from a bank or other institution asking to provide your account information?
![]() Did you provide any information?
Did you provide any information?
![]() Have any friends told you that they received spam from your email account?
Have any friends told you that they received spam from your email account?
![]() Have you seen unauthorized banking activity in any of your accounts?
Have you seen unauthorized banking activity in any of your accounts?
![]() Does anyone else have access to your online banking information?
Does anyone else have access to your online banking information?
- Why would they access your account?
- Do they have permission to access your account?
![]() Do you have a Facebook (or other) page?
Do you have a Facebook (or other) page?
![]() Have you “friended” any strangers?
Have you “friended” any strangers?
![]() Have you posted personal information online, such as your date of birth?
Have you posted personal information online, such as your date of birth?
![]() Have you applied for credit cards online?
Have you applied for credit cards online?
![]() Did you bookmark the website address?
Did you bookmark the website address?
Computer crime victim questions—harassment via email/text/online postings
![]() Did you save all emails that you consider harassing?
Did you save all emails that you consider harassing?
![]() Do you know the person that may have sent the emails?
Do you know the person that may have sent the emails?
![]() Did you reply to any of the emails?
Did you reply to any of the emails?
![]() Did you give permission to post your personal photos online?
Did you give permission to post your personal photos online?
![]() Did you share these photos with anyone?
Did you share these photos with anyone?
![]() How often are you receiving harassing emails/texts?
How often are you receiving harassing emails/texts?
![]() Have you printed or saved harassing webpages that have been uploaded by others?
Have you printed or saved harassing webpages that have been uploaded by others?
![]() Has anyone posted information online using your name?
Has anyone posted information online using your name?
![]() Why do you think someone is harassing you?
Why do you think someone is harassing you?
![]() Have you received phone calls that are harassing?
Have you received phone calls that are harassing?
Questions for Network Administrators
Network administrators are needed many times to obtain information necessary for search warrants when they are third-party hosts to electronic evidence stored by their customers. These questions will help the investigator draft affidavits that specifically request information sought in support of their investigations. The customer referenced in these questions refers to the alleged suspect in a crime. Any computer-related crime requires sensitivity to timeliness of evidence identification and collection. The Order of Volatility applies to data that naturally becomes unavailable in time due to natural processes such as shutting off a computer. It also applies to data that is intentionally deleted through normal business operations or computer use.
Document retention policies are not written with the purpose of preserving evidence as it is more so written to support business operations. Questioning network administrators as soon as each is identified will reduce the risk that relevant evidence will be destroyed through normal business operations.
Customer accounts—Internet Service Provider, online data hosting, other online services
![]() Who is the system administrator or contact?
Who is the system administrator or contact?
![]() What log files are kept of customer logins?
What log files are kept of customer logins?
![]() How far in the past are they kept?
How far in the past are they kept?
![]() What information is contained in the log file?
What information is contained in the log file?
![]() Are incorrect attempts logged?
Are incorrect attempts logged?
![]() Are backup copies made of customer data?
Are backup copies made of customer data?
![]() How far back in time do backups exist?
How far back in time do backups exist?
![]() Does customer “x” currently have an account?
Does customer “x” currently have an account?
![]() What is the email address of customer “x?”
What is the email address of customer “x?”
![]() Is communication tracked with customers?
Is communication tracked with customers?
![]() Is this communication able to be produced?
Is this communication able to be produced?
![]() Does it include phone calls and emails?
Does it include phone calls and emails?
![]() Where does the data physically reside for customer “x?”
Where does the data physically reside for customer “x?”
![]() Is any customer identifying information needed for verification to create an account?
Is any customer identifying information needed for verification to create an account?
![]() What customer information is maintained?
What customer information is maintained?
![]() What Internet addresses do customers use to access their accounts?
What Internet addresses do customers use to access their accounts?
![]() Can customers share files with their accounts?
Can customers share files with their accounts?
![]() Is information maintained by all users included shared users, on accounts?
Is information maintained by all users included shared users, on accounts?
![]() Can you describe how data is saved onto customer accounts?
Can you describe how data is saved onto customer accounts?
![]() What is the document retention policy of cancelled accounts?
What is the document retention policy of cancelled accounts?
![]() Is encryption employed on customer accounts?
Is encryption employed on customer accounts?
![]() Are payment records maintained? For how long?
Are payment records maintained? For how long?
![]() Can you immediately preserve the account of customer “x” in preparation of a search warrant?
Can you immediately preserve the account of customer “x” in preparation of a search warrant?
Summary
The suggested questions are crucial in a computer-related criminal investigation. Answers may be truthful, untruthful, or portions of answers willfully omitted. Having the suspect commit to answers in one or more interviews will benefit the case regardless if the suspect was entirely truthful. Either the suspect tells the truth, providing incriminating statements, or the suspect is untruthful, which potentially discredits statements of innocence.
The investigator should intermingle questions with known answers to help determine the truthfulness of the questioning and to lead to additional questions. The suspect should not know which answers to questions are known as control questions. As the investigator, it is not only the confession that is sought, but also the admissions that will bolster physical and circumstantial evidence.
Confessions and admissions are only part of the investigative process and cannot solely be relied upon. Statements can be retracted, restated, or disproven. If evidence is weak in other areas of the investigation, the case can begin to be disrupted and torn apart, even if the suspect is guilty. Yet, confessions can be the most powerful evidence as the statements are made against the suspect’s penal interest.
Bibliography
1. ADrive. <http://www.adrive.com>.
2. Frostwire. <http://www.frostwire.com>.
3. The Onion Router (Tor). <http://www.torproject.org>.
4. Xiao Steganography. <http://www.nakasoft.net>.
