Some Things Will Become Easier, Others Not So Much
Information in this chapter:
![]() It will become easier to place a suspect behind the keyboard
It will become easier to place a suspect behind the keyboard
![]() It will become more difficult to place a suspect behind the keyboard
It will become more difficult to place a suspect behind the keyboard
Introduction
The digital forensics field evolves faster than most other fields simply because technology changes rapidly. With each new operating system or new version of an operating system, digital forensics must keep up with the advances. Not only must digital forensic examiners try to keep up with each technological advance in computing, but also keep up with ever changing laws.
Sometimes, these changes make it easier for digital forensics and the investigator’s ability to place a suspect behind a keyboard. Other times, these changes can make it difficult or impossible. Expecting which changes will occur in the future is anyone’s guess, but no matter the changes, the digital forensics field must be flexible to stay abreast.
It Will Become Easier to Place a Suspect Behind the Keyboard
With each new version of operating systems, many in the community of digital forensics examiners discover innovative methods that more easily help place the suspect behind the keyboard. This is made possible due to advancements in operating systems and forensic software capable of exploiting forensic artifacts created by computer users.
Investigations where computer systems are involved also create changes in laws that can benefit digital forensics examiners. Combined with a number of these advances and legal changes, placing a suspect behind a keyboard becomes easier as time passes. Knowing which aspects make it easier to accomplish this goal should be a priority for every examiner.
Operating systems will make it easier
With each new version of an operating system, more electronic evidence artifacts are created by the operating system and subsequently discovered by forensic examiners. It is highly unlikely that for any new feature of an operating system, no new forensic artifact will be related to it. More features simply mean more artifacts, each of which may by itself or in relation to other artifacts, help place the suspect behind the keyboard with more circumstantial electronic evidence.
One example is that of the Volume Shadow Copy Service (VSS) found in Microsoft Windows. The Volume Shadow Copy Service was introduced in Windows Server 2003 through the current version of Windows 8. The VSS creates a series of incremental backup of modified files, known as shadow copies. The VSS process operates in the background, without the need for user intervention to create the shadow copies. In many cases, computer users are completely unaware that their files are being backed up and will not be deleted if they delete only the current version of any file.
Computer users can restore multiple revisions of one single word processing file from multiple shadow copies, even if the current file has been deleted or wiped from the system. Although earlier versions of Windows, such as Windows XP, have a similar function, it is much more limited in scope and persistence. Figure 9.1 shows the ease to access a previous version of a file through a simple GUI interface. A list of previous versions of the file is given, which the user can select and restore.
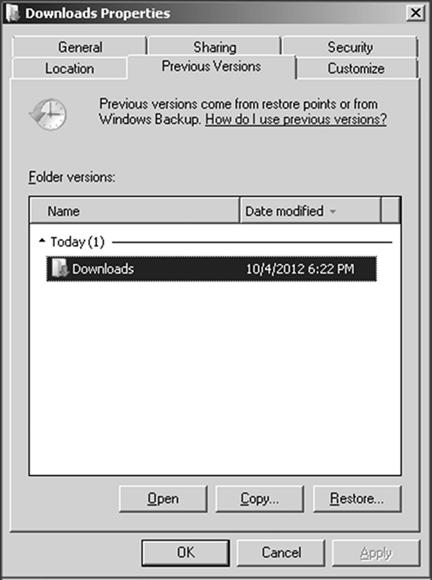
Figure 9.1 “Right clicking” on a file or folder allows easily restoring a previous version of a file or folder from one or more shadow copies.
Each version of a file recovered from a shadow copy gives the examiner additional metadata, such as file creation or modification dates and times, that contributes to user activity evidence. As this is a background service in the operating system, the average computer user is unaware of the evidence that is continually created with computer use.
For evidence collection, shadow copies contain a wealth of information, much more so than previous operating systems. As the average computer user may be unaware of these incremental backups, more evidence can be recovered. Suspects unaware of shadow copies are mistaken in their beliefs of security when deleting or wiping their evidence when they ignore shadow copy files.
The Volume Shadow Copy Service is only one example from one operating system, in which improvements by an operating system for an enhancement to the computer user experience, result in additional troves of electronic evidence. More features in operating systems equates to more user-related forensic artifacts.
Computer hardware and software applications will make it easier
The manufacturers and developers of digital forensic tools, both software and hardware, continue to make great strides in making forensic examinations easier and quicker. Forensic software maximizes computing power to recover deleted files, create indexes of data, and search for keywords and files across enormous amounts of data. Password bypassing applications can access protected files in seconds whereas only a few years ago, these same files could be considered inaccessible.
Even the selection of software applications specific to a certain need has given forensic examiners the ability to provide intensity on an aspect with greater depth than ever before. Early forensic software was neither intuitive nor easy to operate, whereas today, current forensic software can be almost described as point and click applications.
The speed of electronic evidence collection, which can have an effect on an investigation that is time sensitive, is simply incredible as compared to any previous year. An example is the collection of specific information from a computer system in order to help determine initial investigative steps to take. Although a fully featured forensic suite can be used to collect massive amounts of data, smaller and more focused applications may be more efficient.
Figure 9.2 shows the interface of Forensic Scanner, an open source forensic software application developed to collect targeted information from a computer system in less than one minute. By browsing to a mounted target folder and selecting a directory for the output report, user account information is pulled from the system and placed into a text file in seconds. Not more than a half a decade ago, this type of ability was unheard of and impossible without spending an hour or more to collect the same information.
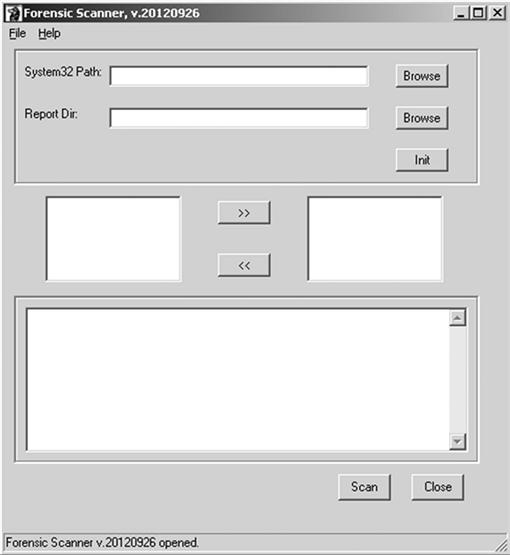
Figure 9.2 Forensic Scanner, developed by Harlan Carvey http://code.google.com/p/forensicscanner/.
The continued development of forensic software designed to accomplish specific tasks quickly, such as the Forensic Scanner, will only increase the ease of use, speed of data collection, and simplicity of the analysis. As computing power increases, the increased processing speeds allow for even faster case processing of data. These factors effectively make the interpretation of computer user data clearer through massive amounts of circumstantial evidence to make your case.
New and innovative computing devices will make it easier
Human ingenuity continues to create some of the most creative and useful computing devices. The cellular phone, once the size of a small gym bag carried by an elite few, has now been shrunk to fit in the palm of a hand, and carried everywhere by adults and teenagers alike.
Figure 9.3 shows an iPhone by Apple (http://www.apple.com), which continues to store more information with more features, with a compact design. As these devices continue to be developed and used as everyday activities, the data trail of evidence will also continue to grow. Smartphones can be considered one of the best sources of evidence to place a suspect not only behind a keyboard, but at any location the device has traveled.

Figure 9.3 An iPhone with gigabytes of storage capacity, GPS tracking, text messaging, Internet, and email. All of this data is useful in the investigation of cybercriminals.
Data storage and access will make it easier
Just as computing power increases, data storage capacity also increases. As the price for data storage decreases, there is almost a direct relation in an increase of data storage capacity. With the ease and capacity to store massive amounts of data created by computer users, there is simply more electronic evidence to be collected and analyzed. Since any one case can consist of thousands upon thousands of individual evidence files and artifacts, circumstantial evidence of computer use and the amount of electronic contraband becomes extensive with just one hard drive.
Today’s storage devices are not only measured in terabytes, but also measured by their small size. Portable external hard drives that can fit in the pocket of trousers can hold terabytes of data. These inexpensive and commonly used storage devices encourage the collection of data by any computer user. Smaller storage devices allow for extreme amount of data storage and a risk of misplacing these small items. A misplaced storage device by a suspect may be a goldmine of evidence if found by an investigator. Figure 9.4 shows an example of a 16 Gbyte USB flash drive compared to the size of a penny.

Figure 9.4 Data storage devices increase in capacity, decrease in size, and decrease in cost, such as this 16 Gbyte USB flash drive.
Data is created, copied, stored, backed up, modified, and backed up numerous more times across multiple hard drives by computer users, including cybercriminals. All of this massive data duplication and storage aids investigators by increasing the chances of finding electronic evidence that a suspect may have destroyed on any other hard drive. Rather than focusing on a single hard drive from a suspect’s computer, there is usually a potpourri of associated storage devices containing pertinent electronic evidence.
Online storage, a convenient method to store and back up user data, contributes to potential evidence sources. Whether the services are provided by commercial sources or freely available, each file stored online offers an investigator the opportunity to find and attribute evidence to a suspect.
Public awareness and education will make it easier
Cybercrime has become a common term with regular media attention. The public has been inundated with high profile media cases of hacking, intrusions, and identity theft broadcast across printed and televised media. This results in victims self-identifying themselves as victims faster. This faster identification of victims gives investigators more time to identify electronic evidence before it is destroyed.
Education of forensic examiners continues to increase in quality, depth, and opportunities. Just within the last half decade, many universities have created certificate and degree programs either specific to digital forensics or Information Technology Programs with an emphasis on digital forensics. US Government agencies faced with exploding cybercrime issue further support educational institutions by providing partially and fully funded cybercrime scholarships.
Digital forensics has entered the forefront of desirable careers and impact on the security of infrastructure across a broad spectrum of businesses and government entities. This education, public knowledge, and even entertainment references of digital forensics in popular television programs have contributed to a frontline of examiners ready to identify cybercriminals.
The suspect will make it easier
For basic computer use, cybercriminals use computers just like everyone else. Passwords are still written down and taped to the bottom of the keyboard, by everyday computer users and cybercriminals, such as seen in Figure 9.5. Weak passwords are used for logins, and communicating online is conducted in a manner as if no one will ever read the chats or comments made in social networking websites. Cybercriminals will still continue to brag about their crimes in online public forums and chats as if immune to detection.

Figure 9.5 Commonly used methods by all computer users are used by cybercriminals, such as writing passwords for reminders.
Cybercriminals also backup their systems, using the same programs that everyone else uses. Some cybercriminals are unaware of evidence they create as they commit crimes, such as illegally accessing a network when using their home computer and IP address. Harassing emails and text messages are sent and deleted without thought of investigators tracing each email and message.
Basic human nature has always helped investigators in all criminal investigations, not just cybercrime investigations. In many cases, breaks in an investigation are solely due to a mistake or laziness on the part of the cybercriminal, which most likely will never change. These mistakes by cybercriminals turn a seemingly impossible case into an easy, open, and shut case.
Pre-placed surveillance systems will make it easier
As it stands in major cities now, it is virtually impossible for any person to conduct daily business or travels without being under video surveillance at some point. The majority of these video surveillance systems are in place by private businesses for the prevention and detection of crime on their premises. Any of these can be sources of information to place the suspect at a location, given legal authority to demand the information from private businesses.
Additionally, surveillance systems are being placed in public by government agencies at a faster rate than ever before. High crime areas in some cities already have surveillance systems in place; however, many cities are now installing more video cameras in high pedestrian traffic areas in addition to traffic cameras. As with private business security systems, any of these can place a person at a location, to either prove or disprove alibis. If lucky enough, an investigator may even place a suspect at a publicly available computer such as at a computer store, while the suspect committed any number of online crimes through store surveillance cameras.
New laws and employer rights will make it easier
As terrorism breeds risk to national security, laws are continually created or updated to include increased surveillance on citizens. Since terrorism also includes cyber-terrorism, this will result in more data collected which is beneficial to investigations.
In the private sector, laws and employer rights generally include the right to monitor employees in the workplace. This can be through video surveillance or computer monitoring software. Already, employee use of business equipment is under the explicit approval of and monitoring by the employer. The monitoring of computer use, including emails and Internet history is considered to be part of employee monitoring in the workplace.
This reduction of privacy in public and private businesses generates a massive amount of information of all persons being monitored, which hopefully includes those engaged in cybercrimes.
It Will Become More Difficult to Place a Suspect Behind the Keyboard
Just as the future holds more ease in placing suspects at a keyboard, it is also a fair statement that as it becomes easy in some aspects, it becomes difficult in others. At times, investigations may be impossible to complete successfully depending upon the effort undertaken by a suspect and technology hinderances.
The following topics give a broad overview of increased difficulty that is currently faced by investigators. Many of these obstacles will continue in complexity, but at any point, a breakthrough in technology can make the impossible, possible.
Encryption will make it more difficult
Encryption, in the most basic definition, makes electronic data unreadable without supplying a key, or password. Encryption can be bypassed with sophisticated software and hardware which can try thousands of potential passwords per second in the attempt to guess the password. However, the stronger the encryption algorithm and the more complex of a password used, the less likely an encrypted file or computer system will be accessed.
By any standards, the use of encryption does not automatically imply that criminal evidence is being hidden. It is quite the opposite in that encryption is commonly used to protect sensitive personal, corporate, or government data. In a forensic examination of encrypted data, the only method to know if the encrypted data is evidence is to bypass the encryption protection.
As more operating systems are being sold with encryption built into the operating system, the odds of encountering encryption are increasing. As seen in Figure 9.6, several Microsoft Windows Operating Systems offer the option of encrypting the entire hard drive and other attached hard drives with Bitlocker Drive Encryption by simply clicking “Turn On BitLocker.”
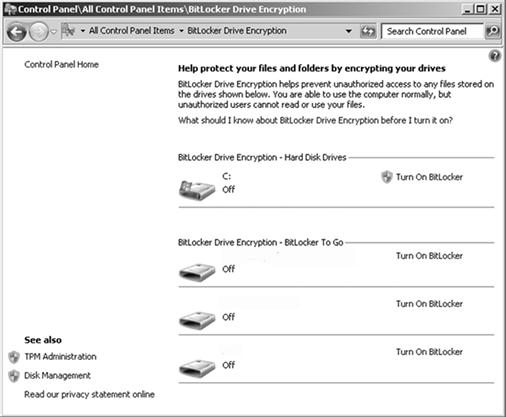
Figure 9.6 The Control Panel of Microsoft Windows 7 Ultimate, hard drive encryption with BitLocker Drive Encryption. (http://www.microsoft.com).
Operating systems that do not include encryption features can still be encrypted with third party software applications. Many of these encryption applications are open source and freeware, such as TrueCrypt and by being freely available, increase the chances that more users will install these types of programs. Figure 9.7 shows the dialog box of TrueCrypt, giving the user options of encrypting the entire partition or drive and creating hidden volumes.
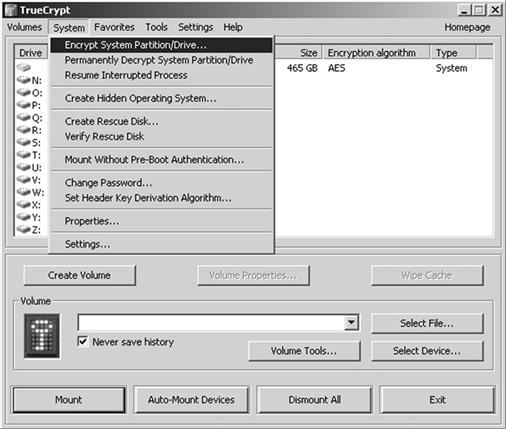
Figure 9.7 TrueCrypt dialog for encrypting data. (http://www.truecrypt.org).
Full disk encryption, such as BitLocker Drive Encryption, requires possession of the key, which may be an alphanumeric phrase or any number of additional protections such as a physical USB device containing a startup key. Without the key, access to the hard drive and any information on the hard drive is virtually inaccessible.
Other uses of encryption also render data useless, such as encrypting files, folders, and electronic communication. Emails can be encrypted prior to and during transit. Internet use can also be encrypted or obscured through Internet proxies. Cellular calls are also capable of encryption. Any of these uses of encryption can render electronic storage devices uses as a source of evidence, unless the key is available or the encryption can be broken.
Public awareness will make it more difficult
Just as public awareness may prevent and detect cybercrime, this same awareness may also contribute to creating difficulties in forensic examinations. The average computer user has become aware of encryption to protect personal data, creating complex passwords to prevent someone guessing their password, and generally being aware of the potential hazards of computer use. And just as the average user has become more aware, so has the cybercriminals.
Although television crime dramas are not completely accurate with investigative methods, these dramas and crime novels do create to a broader perception of what examiners may be able to find on computers. This perception includes both accurate and false beliefs as to the abilities of investigative methods. Also known as the “CSI Effect,” where television dramas solve crimes within an hour, public perception may falsely believe the impossible is possible. This belief negatively affects law enforcement examiners in the courtroom just as much as it effects private sector examiners in the boardroom. The paranoia created through the entertainment world inspires cybercriminals to be even more cautious than they would have been otherwise, making investigative efforts that much more difficult.
Additionally, the education available for potential and future cybercriminals not only consists of the same colleges and universities offering cybersecurity degrees, but there also exists an entire network of online hackers which share information among each other. The information on how to commit cybercrimes is as readily available as information on how to combat cybercrime.
Remote control of systems will make it more difficult
Almost every computer on the planet is practically connected to every other computer, as long as the computer is connected to the Internet. Networks are protected with firewalls and computers are generally configured to not accept remote connections without approval of the computer user.
But as with any security system, methods to gain entry exist through electronic means, such as hacking into a system, or being allowed into a system through social engineering. Social engineering, which consists of a suspect gaining trust of a person through false pretenses, is just as dangerous for security as any malware. If a victim willingly gives remote access or information leading to remote access to a social engineer, the victim’s computer could be used to facilitate a crime.
The difficulty in placing a suspect behind a keyboard arises when the keyboard at the evidence computer is actually a different location than the computer. A suspect who can access a victim computer system or even his own computer system from another location might not be able to be traced to the suspect’s physical location. The act of remotely accessing multiple systems further complicates an investigation, particularly if the actual physical location of the suspect has been obscured through proxies and the use of public wireless access points.
The examination of a suspect’s computer system, which was suspected used in a cybercrime, will most likely show the exact dates and times the criminal activity occurred. But your investigation could show that the most likely suspects were at work, on vacation, or on the other side of the world. With remote access potential, this does not eliminate the likely suspects if the analysis shows remote connections on the system.
Open wi-fi hotspots will make it more difficult
Wireless Internet is perhaps the most convenient technology creation for anyone who travels with mobile devices. The ability to instantly connect to the Internet and access email, surf the web, and conduct business cannot be overstated. Private businesses draw patrons to their business by offering free wireless. Coffee shops, grocery stores, and hotels each offer free wireless services.
Besides private business, many government entities offer free wireless for their citizens. Also, private households inadvertently or intentionally offer free wireless access through their home networks. A single apartment building can literally have dozens of open wireless access points where any computer in range will be able to access without restriction.
The difficulty arises as a traveling cybercriminal may access a number of open wireless networks and commits any number of online crimes. The owners of the wireless networks are then at risk of being accused of these crimes. This not only causes investigators to wrongly assume the identity of a suspect, but also causes unnecessary resources to be spent on chasing the wrong leads.
Massive and duplicate data will make it more difficult
I stated that the massive amounts of data, stored across multiple storage devices, can be helpful to an investigation, as evidence can exist on any of the devices. By the same token, because of the massive amount of data, much of which may be duplicative, the time necessary to cull and analyze the data contributes to the difficulty of an investigation. As an example, hundreds of compact disks, or several external hard drives containing hundreds of gigabytes of data, not only take time to analyze, but the analysis may end with a negative result for evidence.
It is the time involved to adequately search and analyze mountains of electronic data that add to the complexity of investigations. Particularly where time is of the essence, not knowing which hard drive contains the most pertinent and important evidence means that every hard drive may have to be examined. That which would have taken days may now take weeks or months, during which time, victims are being further victimized and suspects continuing to roam free. This includes the data stored online through any means of online storage providers needing to be sought after, found, collected, and examined.
Virtual machines will make it more difficult
Any way you look at it, a virtual machine is just as much a complete operating system and contains just as much system and user created files as any “real” operating system. On a suspect’s computer, where a virtual machine exists, two forensic examinations are needed: one of the actual physical machine and another on the virtual machine.
Technically, the issues of examining a virtual machine are not unlike those of the physical system. The virtual machine can be imaged, data carved, indexed, and analyzed. But technically, the same issues of complications can arise, such as encryption, along with a other roadblocks to any forensic analysis.
Making matters worse, a single physical computer can host multiple virtual machines. An example seen in Figure 9.8, five separate virtual machines are seen existing on one physical machine. This figure does not show the virtual machines that may have been deleted, nor does it show any virtual machine that was run from a portable USB device. But at a minimum, Figure 9.8 shows that for a complete forensic examination, there are six operating systems to exam (five virtual systems and one physical system).
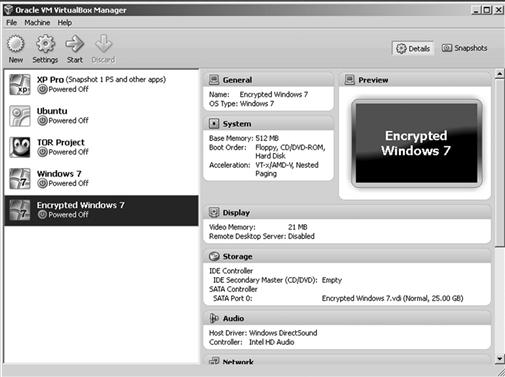
Figure 9.8 VirtualBox interface showing five virtual machines. (http://www.virtualbox.org).
The difficulty caused by virtual machines goes beyond the time involved for an analysis of each virtual machine. As a virtual machine can be run from a USB flashdrive, the evidence stored in the virtual machine may not even exist on the physical computer hard drive. The evidence would exist on the USB flashdrive, which, in a difficult scenario, could also be encrypted or thrown away by the suspect.
Another aspect of difficulty with virtual machines is the feature of virtual Snapshots. Figure 9.9 shows an example of a virtual machine with Snapshots. A Snapshot stores the current state of a virtual machine which at any time may be used to revert back in time. By referring to a Snapshot, electronic evidence created on the virtual after the chosen Snapshot is effectively destroyed. In this manner, a virtual machine can be reused often for any cybercrime, yet the evidence destroyed after reverting back to a Snapshot.
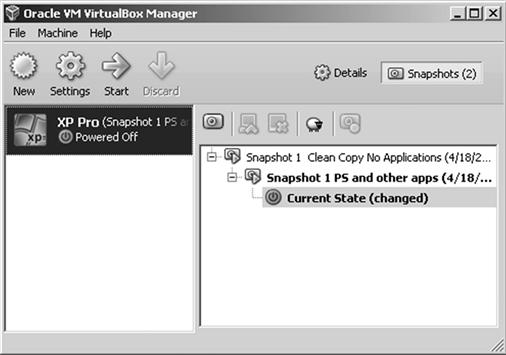
Figure 9.9 VirtualBox allows for Snapshots to be stored of the current state of a virtual machine. These can be used to revert previous states, eliminating electronic evidence.
The use of a virtual machine to facilitate cybercrimes strongly benefits the suspect and is a detriment to the investigator. Internet access through the virtual machine can still be conducted through open wireless access points or through the use of proxies to obscure the suspect’s actual IP address. Crime committed within a virtual machine stays within that virtual machine, which is really just a file on a computer or USB drive. This single file or storage device can be wiped beyond recovery or simply tossed on a freeway to prevent discovery.
Even more techniques will make it difficult
Counter-forensics, or anti-forensics techniques, is any method to make forensics difficult or impossible. Some of these discussed already include encryption and the use of virtual machines. Other methods that are just as easy and effect are data wiping and data hiding, where evidence is either overwritten with random data or hidden behind other data. Employing a combination of these techniques can effectively render forensic analysis on a storage medium useless.
Perhaps the most effective means of disrupting a forensic examination is that of the complete destruction and disposal of the suspect’s computer system. Because storage devices drop continue to decrease in price as they increase in storage capacity, the disposal of these containers of evidence by suspects is of small consequence compared to prosecution. Desktop computers and laptops also have become so inexpensive, that the destruction and disposal may be commonplace. Computer systems can even be purchased solely for the facilitation of a crime and quickly disposed after its use.
Summary
Without a confession from a suspect, placing the suspect behind the keyboard requires effort, ingenuity, patience, and more than one Eureka! moment. Even with a confession, reliance upon one piece of evidence is a risky decision when a confession can be suppressed, recanted, or proven to be inaccurate.
The future holds easier solutions to placing the suspect behind the keyboard, just as it will provide obstacles to that end. It is up to the investigator, the examiner, and the investigator-examiner to be a problem solver and think beyond traditional means of investigations. A forensic analysis can stand on its own regarding only the interpretation of the data recovered. It cannot, however, be the sole piece of evidence to place a suspect at the computer without further investigative methods and other circumstantial evidence.
Bibliography
1. BitLocker Drive Encryption. <http://windows.microsoft.com/>.
2. Forensic Scanner. <http://code.google.com/p/forensicscanner/>.
3. TrueCrypt. <http://www.truecrypt.org>.
4. VirtualBox. <http://www.virtualbox.org>.
