Online Investigations
Information in this chapter
Introduction
Online investigations are one of the most powerful tools you have available in your objective of placing the suspect at a keyboard or location, identifying your suspect, and identifying co-conspirators of your suspect. You can even identify the victims and witnesses in investigations.
This chapter is not about online undercover investigations. Primarily, this chapter will give you advanced techniques to search for information beyond simply using a search engine. Social networking sites, forums, blogs, and the deep web contain much more information that any one search engine. The goal of this chapter is to show how to find your suspect online so you can eventually find him in person.
Online Investigations
As you can see in the Case Studies chapter, several high-profile investigations involved searching the Internet for information to identify suspects. As a corporate investigator, you may have access to public databases on a subscription basis. Law enforcement investigators have access to government databases, such as those containing criminal history information, including non-conviction data.
These databases have an advantage over information found online, in that the information can be considered very credible. An arrest record is not needed to be verified with the arresting agency, but if it were, documents would be found such as fingerprint cards, mug shots, and arrest reports. But generally, a record of an arrest is taken at face value as being credible.
Information found online is not as credible and in fact, may be completely and intentionally falsified. Anything that is posted on a website, blog, or forum has no requirement that it be backed by physical proof. With this type of free-for-all wild west of publishing information on the Internet, why would any investigator consider using it at all? The answer lies in the source of the information.
Unlike a criminal or public records database where the information is entered by a third party, information found online offers something you can’t get anywhere else. The information is published by the suspect, personally, by the suspect’s own hands. Whether the information is factual or false bears little weight as the content is not always the factor needed in your investigation. Any character typed on a keyboard by the suspect that is posted on any webpage is a breadcrumb for you to follow to his doorstep. The best part is that the information posted online may be as close to real-time information on your suspect you can find. In most cases, the data posted online is stored by third parties that have nothing to do with your suspect, nor may even allow your suspect to remove from their systems. That’s the power of online investigations.
Why the internet?
The Internet as it relates to investigations is much more than commercials for products. It is a means of communication with email, chatting, social networking, forums, and blogs. Internet users can share information and ideas or give their opinions in publicly viewable forums.
With the interconnectivity of mobile devices in which photos and messages can be instantly uploaded to the Internet, more people are online, all of the time. Those that wish to share every detail online can do so uninhibited. This includes those that wish to brag about their exploits, which could be your suspect anonymously bragging about his criminal acts.
Again, the content of a posting may not be important to your case compared to the timing of when a comment was posted. Potentially, an IP address may lead to a physical location that has not been obscured through an anonymous means. And most important, the Internet might be your only chance of identifying your suspect.
What can be found online?
Just about everything can be found on the Internet and for the most part, online content stays online. If the content is interesting enough it will multiply through mirrored webpages. At a certain point, it is difficult if not impossible to remove information on the Internet.
The difficulty is weeding through millions of webpages to find only the information you need without having to spend days at a computer screen. Without a plan or the knowledge of how to search for information, you will miss important clues a suspect has left for you to find.
Some of the most pertinent areas to look for information on your suspect are comments to articles that your suspect finds interesting. Forums that relate to his need to brag, express anger, or simply communicate with others like him. Your suspect may not have his own webpage or domain, but may have any number of personal social networking pages such as a Facebook page. He may have one or many usernames in different forums. Your goal is to find the first clue and typically you already have it.
If your case involves harassing emails, you have one or more email addresses. If the case involves the posting of threatening comments on a blog, you have the usernames of your suspect. Even if your suspect has given a false name, you have the false name at least to start your online search.
How to build your “super” browser
Before you get started with an intensive manhunt online, there are tools you can configure that will greatly reduce the amount of time spent searching. Your primary tool will be the web browser. With a few tweaks to the browser, online research can be more effectively accomplished.
A web browser allows you to read webpages, watch videos, and interact with others online. Search engines, such as Google, allow you to search the Internet for webpages on the search terms you choose. Tweaking your web browser to accomplish searches automatically, systematically, and thoroughly will make your online time much more efficient.
Using Mozilla’s Firefox as an example, there are a few changes to the browser you can accomplish in a few minutes. From the Mozilla website (http://www.mozilla.org), Firefox can be downloaded freely and installed. From the same website, “Add-ons” can be downloaded and installed to the browser.
Add-ons are additional features that add push button efficiency to your online searches. For example, in Figure 10.1, an Add-on that searches multiple social networking sites at one time can be added with the click of a button. As many Add-ons you see fit for use can be added to the Firefox browser. The time saving feature for this one example will allow searching over 40 social networking sites at once rather than searching individually.

Figure 10.1 An Add-on for the Firefox web browser from http://www.mozilla.org that allows searching social networking sites.
With each Add-on giving your browser combinations of searches to be conducted at once, the amount of data specific to your searches will be produced faster. Another additional feature for the Firefox browser is from SEARCH. SEARCH is an online resource for investigations. From SEARCH, you can download and install the SEARCH Investigative Community Toolbar, which installs directly to Firefox. The SEARCH toolbar adds bookmarks to the browser specific to areas of an online research, such as IP address information, cell phone information, and social networking websites.
Other web browsers also offer Add-ons type features, such as Google’s Chrome browser which allows for extensions for the browser. Some toolbar Add-ons, like the SEARCH Investigative Toolbar are compatible across several browsers. Regardless of the browser you choose, set it up from the start and you will quickly have a systematic method of online searching that will save you more days of research than you would have liked to endure.
Internet search engines and directories
All search engines are not created equal. In the world of search engines, there are catagories of search engines that are specific to a topic, which are helpful to narrow your results. All-purpose category search engines, such as Google or Bing, search across the Internet for any hits on your search term, if the website has been indexed by that search engine. As each search engine has been developed by different organizations, using different indexing methods, their results may differ slightly. That means that many times you may need to try the same search term using different search engines.
One example of a category-specific search engine is Icerocket, which is a search engine for blogs. Figure 10.2 shows the search dialog box for Icerocket. Other category search engines are developed for catagories such as searching for books, businesses, email, forums, games, people, and news. If there is a specific search topic you need to accomplish, there may be a search engine designed for your search. One website that maintains a list of search engines separated by category is The Search Engine List at http://www.thesearchenginelist.com.

Figure 10.2 A blog search engine, Icerocket, http://www.icerocket.com.
Another source of online information is directories. A directory, like a phonebook, is a listing of information, which includes online phonebooks. Some of these online directories may not be indexed with a search engine and as such, a general-purpose search engine may completely miss any results in a directory.
Usernames
Usernames may be the only lead you have in a case. Besides attempting to determine the meaning of a username, it is probably more important to find if the username has been used in other online services. There are a few websites that allow searching across many social networking sites by username. Figure10.3 shows one example, NameChk, which can search for matches across a wide range of websites.
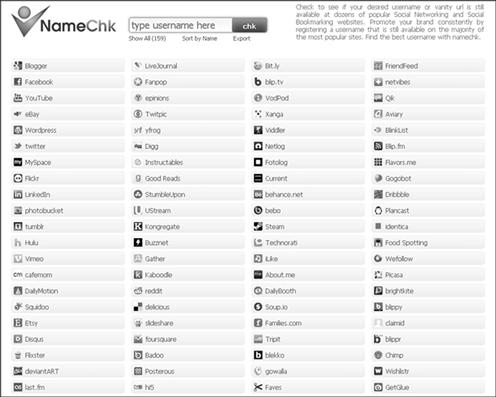
Figure 10.3 NameChk (http://www.namechk.com) allows searching for a username across many social networking websites.
However, if the same username is found on more than one website as a comment or blog post, it does not necessarily mean it is the same person. Usernames are specific to an account on the Internet, not to the Internet as a whole. Finding the same username in more than one location means time is needed to investigate if the owner of the username is the same person.
The benefit to you in searching usernames is that if your suspect chooses a username for criminal activity, it is possible that he may use the same username for legitimate activity, even though the email addresses associated with the username may be different.
Social networking websites
Searching for your suspect online obviously includes searching social networking websites. By this time in your searching, you should have installed several Add-ons or extensions to your browser to help. In addition to the added features, there are several search engines developed for searching these websites. One example is seen in Figure 10.4 with SocialMention, which can search a user specified selection of social networking websites or all at once.
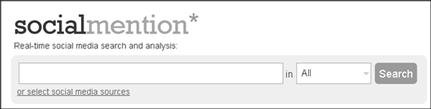
Figure 10.4 SocialMention is one of many search engines designed for searching social networking websites. http://www.socialmention.com.
Recent privacy concerns have resulted in many people setting their personal social networking websites to private only settings, where only friends and family can view. Without legal authority, you cannot view these pages directly. A workaround may be the friends of your suspect who may keep their pages open for public view. Once a friend or family member has been identified, if they allow open public view, you too can see the page and possibly information posted by your suspect.
I would not get caught up with only the most popular social networking sites. There are literally thousands of social networking sites on the Internet, any of which may hold the key to your suspect’s identification. Many of these sites are created by category, unlike a general social networking site. If your suspect is involved in hacking, there is a possibility he may have an account with a hacking networking site along with others like him. Or maybe he enjoys knitting and belongs to both a hacking and knitting social networking site. Either way, it doesn’t matter which social networking topic the suspect belongs, as long as you can find it.
Blogs, forums, and wikis
Blogs, forums, and wikis require a separate discussion apart from social networking sites. Generally, a social networking site is administered by a third party, such as Facebook. Users with Facebook accounts do not control their data on the service, nor does a user have control over data retention of the service. For information posted by a user on some of these sites, it will remain and the user may not have the means to alter or delete it.
This does not always hold true for the blogs, forums, and wikis. For the blogs, forums, and wikis, the control of the information may or may not be in a third party’s hand and the user can alter or delete their information as desired. Many times, your suspect may be the administrator of the blog or forum, in which case, sending a legal demand for information may not be in the investigation’s best interest. Even a blog that resides with a third party, but created by a user, you may not be able to locate a post by the suspect if the suspect deletes it. The deleted post may still be available from the third party, but you won’t know that it ever existed if it were deleted.
An example would be a blog service provided by Google, Blogger, seen in Figure 10.5. A suspect can create a blog using Blogger, and post incriminating or identifying information, but at any point, the suspect can simply delete the blog. Without finding the information before deletion, you’ll never know it was there. A wiki, which is like an online encyclopedia, also allows for users to access, create, and modify content. These changes are usually logged by the wiki, listing the changes by username. Since a suspect could delete their own information on a wiki, it may be missed. Potentially, if discovered after a deletion, the information may still exist and be able for production upon legal request, such as a search warrant.
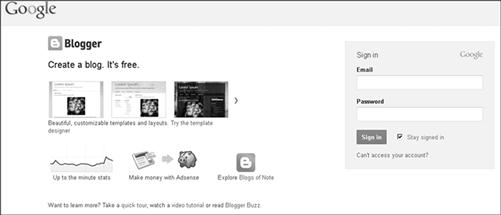
Figure 10.5 Blogger, by Google. http://www.google.com.
Forums pose some of the same issues as a blog if the forum administrator is your suspect. Forums also offer more opportunities for information about your suspect. Given any forum on any topic, users can post to a threaded topic, like replying to an email, only that these are usually in public view.
Since most forums require a username and profile, there may be information specific to your suspect in the profile, especially since the profile is self-identifying. One example of a pertinent piece of information can be seen in Figure 10.6. In this example, the user’s profile photo is a handgun. Although this is just a photo of a handgun, it gives rise to officer safety concerns when the suspect is eventually contacted or arrested. As the saying goes, a picture is worth a thousand words.

Figure 10.6 Profile photos in forums give some information of importance about a suspect.
The trust users lend to forums most always leads to a compromise in personal information, which benefits an investigation. One example where forum postings were instrumental in a case involved a pursuit by police officers where the suspect eluded officers and the suspect’s license plate was not identified.
One of the officers involved in the pursuit searched online and found a forum discussing the same pursuit that occurred a few days earlier. In this forum, the anonymous suspect admitted to getting away from the police and bragged about it, however, the suspect was not using a real name in the forum.
Looking further, the same username was found in another forum topic selling motorcycle parts, giving away the city where he lived, but still, not quite enough information for identification.
Eventually, a different forum was found with the same suspect bragging about beating a speeding ticket. This suspect was so proud of beating the system, that he scanned a copy of a check received from the court as a refund for bail when he won his case. The suspect redacted his name on the check and posted the scanned image to the forum in an attempt to protect his identity.
It took one phone call to the court listed on the check to get the full name, date of birth, and home address of the suspect. Five minutes later, having the suspect’s real name, his photo was found online in yet another forum where he was standing next to the same motorcycle he was riding when he eluded the police. This online search took less than an hour.
The Dark Web
There are places on the Internet that few venture into. In this place known as the Dark Web, or The Onion Web, you can find anything. Drugs, sex, child pornography, hackers for hire, hit men for hire. Literally anything that you would ever want to see exists in the Dark Web. Perhaps your suspect visits the Dark Web and you want to check. Let’s take a quick look at some of the problems you’ll have.
First, to access the Dark Web, you must use Tor, as you can’t get in otherwise. When you run Tor, your IP address is hidden through a number of anonymous relays, worldwide. That means your suspect’s IP address is also hidden.
Once you have accessed the Dark Web, website addresses take a new meaning. Instead of webpages with understandable characters, like the name of a company, the address appear like this: http://silkroadvb5piz3r.onion/index.php.
This particular example of an address is for the “Silk Road Anonymous Market”. The Silk Road offers visitors anything they want, mostly illegal items and substances. A screenshot of the Silk Road website can be seen in Figure 10.7. As you can see, marijuana, heroin, hash, and other drugs are openly sold online, all from sellers hiding behind the same system as the buyers.
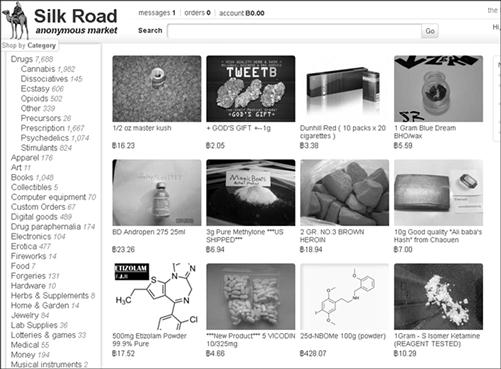
Figure 10.7 The Silk Road Anonymous Market website, http://silkroadvb5piz3r.onion/index.php.
I can assume that many of the items and services in this Dark Web are scams and cons from anonymous criminals selling to anonymous buyers through electronic payments. None being the wiser of the other or being able to track each other, surely results in problems for the buyers being ripped off in some manner. The black market is the black market, even if it is online.
Your obstacles in identifying your suspect in the Dark Web start with IP addresses. If your suspect is in there, using forums or participating in the black market, chasing the IP address will waste valuable time. Another problem is that websites and forums in the Dark Web are extremely transitory. Probably the biggest problem is that if you could identify the owner of a website or forum, you may not have any luck with cooperation.
Following the bread crumbs
Perhaps the biggest question to this chapter is “so what does this do to help put a suspect behind a keyboard?” Besides identifying your suspect, which can be a major break in your case by itself, there is a ton of evidence waiting for you to grab online. For every comment posted to news articles, or comments to blogs, or continued forum posts, exist one or more IP addresses and email addresses. Behind each email address there are more even IP addresses for when the account was created and each time accessed.
Some of these accesses by the suspect may be obscured by using virtual private networks, if the suspect takes the time to use a VPN all the time. All you need is to find that one time that the suspect made a mistake. Once you tie the suspect to a physical address, you have half the obstacles in your investigation solved. Surveillance operations can be planned and executed, a background conducted on the newly identified suspect, and you will no longer be investigating John Doe.
The other benefit to following bread crumbs of evidence and logging each item found online is that of suspect activity, by date and time. Each bit of activity online shows the suspect was at a computer at that date and time. There are exceptions to this, such as configuring a blog post to upload at a later time, but generally, you will have dates and times consist to actually being at a computer.
Capturing Webpages as Evidence
One thing about the draw to the Internet is that it is dynamic and changing. Dynamic websites change constantly with ads, comments, or other content. Information that exists at 1:00 pm may not exist at 1:01 pm. Sometimes this information can be critical to your case. So how do you save it?
One general rule to save a webpage of interest is to immediately print it when you find it. Don’t bother reading the entirety of the website first, or grab your partner to brag what you just discovered. Print it. Make sure it printed. Then treat that printed page as if it is the only copy in the world because it just could end up being the only copy if the webpage changes.
At that point, you can take several measures to preserve the webpage or website. You can create a PDF file of the entire website or single pages with Adobe Acrobat or you can download the entire site with a program designed for saving websites. One example is the free software, HTTrack Website Copier, seen in Figure 10.8. This program can download an entire website to a local folder in native files, meaning the html code used. It also downloads the files associated with the website such as videos, graphics, and documents.
Figure 10.8 HTTrack Website Copier, http://www.httrack.com.
Commercial products exist for capturing Internet pages with more features designed for evidence control, but printing the pages, creating a PDF of the website, and downloading the website with a program such as HTTrack Website Copier can accomplish the goal of saving your evidence locally. For court admissibility, documents of website captures only require that they be entered as evidence if they accurately reflect what was seen on your monitor. A printed webpage fills that need if all else fails.
Be careful of your visits online
A very important consideration before you go online to find your suspect is to prevent being discovered by the suspect. If your suspect is technology savvy, runs their own websites, writes malicious scripts, or otherwise examines their website logs, be prepared for your IP address to show up in front of him and for the suspect to take advantage of the information.
Also be prepared that a website run by your suspect could be a honeypot of sorts to infect machines through malicious links, in particular, infect those that are intent on finding him. This applies to any website run by any criminal element. It may be an idea to use a method to hide your IP address, such as Tor or a VPN and like you’ve heard on every police drama, be careful out there.
Summary
Prepare for your online investigation before you actually start searching. There are steps you can take now that will save hours of work and narrow your search results to a manageable amount. Online investigations do not mean solely using a general purpose search engine to look for your suspect. An online investigation exploits the Internet using every tool available to find exactly what you need. It would be a rare cybercriminal that is not on the Internet in some form or fashion.
For some, the Internet holds all the answers to life. For you, the Internet may hold the identity of your suspect. It can also hold the eventual physical address of your suspect, his contacts and co-conspirators, admissions and confessions, and maybe even a photo posted of him and his motorcycle.
Bibliography
1. Adobe Acrobat. <http://www.adobe.com>.
2. Bing. <http://www.bing.com>.
3. Facebook. <http://www.facebook.com>.
4. Google. <http://www.google.com>.
5. HTTrack Website Copier. <http://www.httrack.com>.
6. Icerocket. <http://www.icerocket.com>.
7. Mozilla Firefox. <http://www.mozilla.org>.
8. NameChk. <http://www.namechk.com>.
9. SEARCH Investigative Community Toolbar. <http://www.search.org>.
10. Silk Road Anonymous Market. <http://silkroadvb5piz3r.onion/index.php>.
11. SocialMention. <http://www.socialmention.com>.
