One of the interesting experiments we can do with TCP socket programming is to set up a TCP port forwarding. This has very good use cases. Say, for example, if you are running an insecure program like FTP in a public server that doesn't have any SSL capability to do secure communication (FTP passwords can be seen clear-text over the wires). Since this server is accessible from Internet, you must not login with your password to the server without ensuring that the passwords are encrypted. One way of doing this is to use Secure FTP or SFTP. We can use a simple SSH tunnel in order to show how this approach works. So, any communication between your local FTP client and remote FTP server will happen via this encrypted channel.
Let us run the FTP program to the same SSH server host. But create an SSH tunnel from your local machine that will give you a local port number and will directly connect you to the remote FTP server daemon.
Python has a third party sshtunnel module that is a wrapper around the Paramiko's SSH library. The following is a code snippet of TCP port forwarding that shows how the concept can be realized:
import sshtunnel
from getpass import getpass
ssh_host = '192.168.56.101'
ssh_port = 22
ssh_user = 'YOUR_SSH_USERNAME'
REMOTE_HOST = '192.168.56.101'
REMOTE_PORT = 21
from sshtunnel import SSHTunnelForwarder
ssh_password = getpass('Enter YOUR_SSH_PASSWORD: ')
server = SSHTunnelForwarder(
ssh_address=(ssh_host, ssh_port),
ssh_username=ssh_user,
ssh_password=ssh_password,
remote_bind_address=(REMOTE_HOST, REMOTE_PORT))
server.start()
print('Connect the remote service via local port: %s' %server.local_bind_port)
# work with FTP SERVICE via the `server.local_bind_port.
try:
while True:
pass
except KeyboardInterrupt:
print("Exiting user user request.
")
server.stop()Let us capture the packet transfer from the local machine 192.168.0.102 to the remote machine 192.168.0.101. You will see all network traffic is encrypted. When you run the preceding script, you will get a local port number. Use the ftp command to connect to that local port number:
$ ftp <localhost> <local_bind_port>
If you run the preceding command, then you will get the following screenshot:
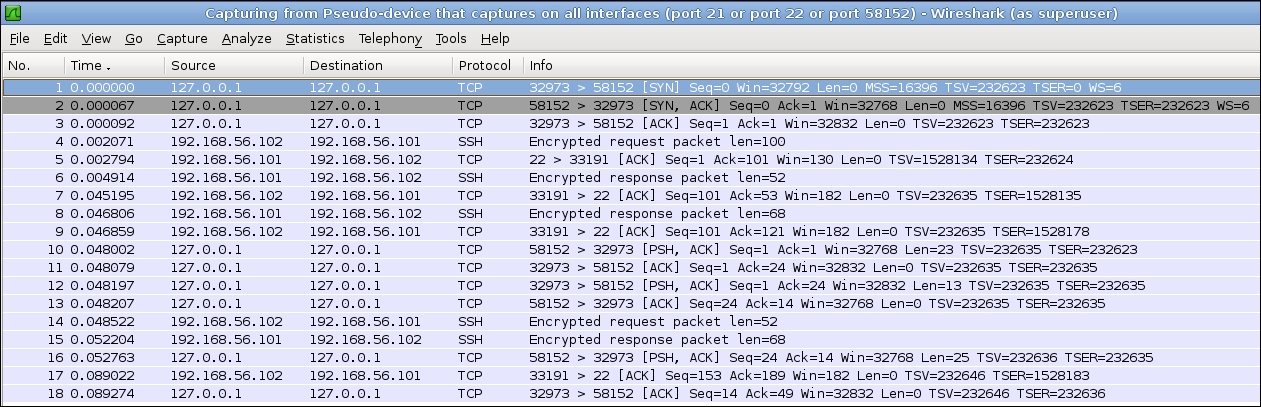
In the preceding screenshot, you cannot see any FTP traffic. As you can see, first we connect to local port 5815 (see the first three packets) and suddenly an encrypted session started with the remote host. You can continue watching the remote traffic, but there is no trace of FTP.
If you can also capture packets on your remote machine (192.168.56.101), you could see FTP traffic, as shown in the following screenshot:
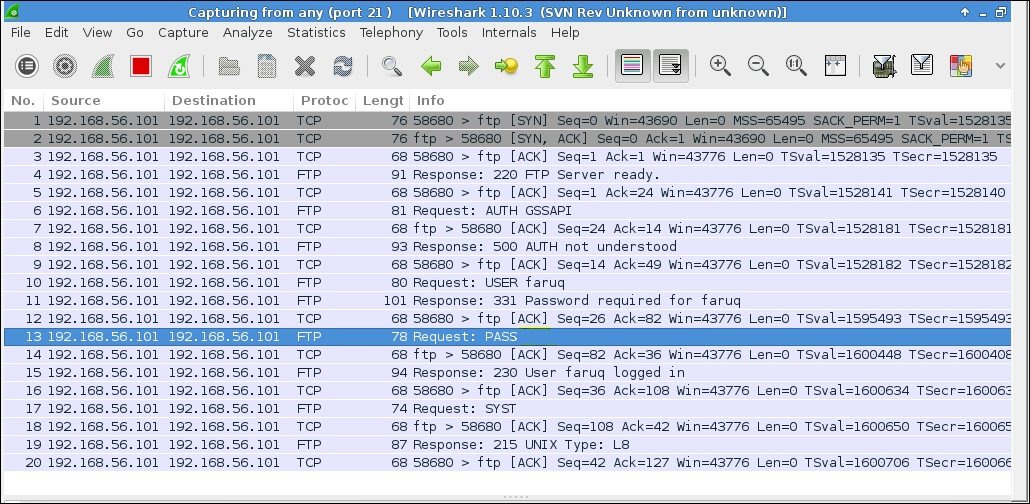
Interestingly, you can see your FTP password sent from the local machine (over SSH tunnel) as clear-text only on your remote box, not over the network, as shown in the following screenshot:
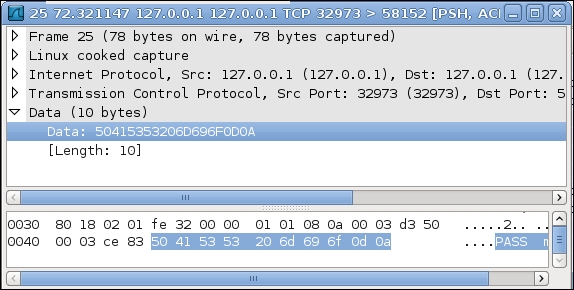
So, in this way, you can hide any sensitive network traffic in an SSL tunnel. Not only the FTP, you can also pass remote desktop session encrypted over an SSH channel.
