Chapter 14: Constant Learning and Community Contribution
Thank you for taking the time to read this book and gain a thorough understanding of this new solution. In this final chapter, we want to provide some useful resources that you can use to continue your learning journey and get involved with community-based efforts to share knowledge. You can also find resources to directly provide feedback to Microsoft, ensuring the continual improvement of this solution.
This chapter will explore the official resources from Microsoft, additional resources for Security Operations Center (SOC) operations, and other resources made available by GitHub.
In this chapter, we will cover the following topics:
- Official resources from Microsoft
- Resources for SOC operations
- Using GitHub
- Specific components and supporting technologies
Official resources from Microsoft
In this section, we will cover resources that are made available by Microsoft to support the design, implementation, and operation of Azure Sentinel as a core security platform. This will include links to official documentation, blogs and technical forums, feature requests, and groups on LinkedIn.
Official documentation
Microsoft Docs (https://docs.microsoft.com/en-us/) is a great resource for documentation on every Microsoft solution. The following list provides some specific links to relevant documents you should start with:
- There is a comprehensive section on Azure Sentinel that will provide the latest official release of information about products, and product-specific guidance for the design and implementation of solutions: https://docs.microsoft.com/en-us/azure/sentinel/.
- Azure Monitor, and Log Analytics specifically, has a separate section that can be used to further study the information we provided in Chapter 2, Azure Monitor – Log Analytics. Visit this site for more details: https://docs.microsoft.com/en-us/azure/azure-monitor/.
- Azure Active Directory (AD) is another key component that is worth studying in more depth to ensure you can properly secure access to the Azure Sentinel subscription and critical resources. Guidance for Azure AD can be found here: https://docs.microsoft.com/en-us/azure/active-directory/.
Tech community – blogs
Microsoft has built a tech community for many different areas of its solutions offerings, each offering a blog to allow expert articles to be shared via specific focused blog posts. The one dedicated to Azure Sentinel can be found here: https://techcommunity.microsoft.com/t5/azure-sentinel/bg-p/AzureSentinelBlog.
You can join this site to keep up to date on announcements and new product features, or to ask questions that will be answered by members of the community and experts from Microsoft. The Microsoft team provides links to future training and webinars, and to previously recorded sessions and their associated resources, such as presentation slides.
You may also want to subscribe to the Really Simple Syndication (RSS) feed to ensure the latest information is instantly available and easy to find.
Here are some additional blogs and related material available:
- Microsoft blog for Chief Information Security Officers (CISOs): https://www.microsoft.com/security/blog/ciso-series
- Blog for all Microsoft security initiatives: https://www.microsoft.com/security/blog
- Microsoft Azure security blog: https://azure.microsoft.com/en-us/blog/topics/security
- Microsoft Graph Security API blog: https://www.microsoft.com/security/blog/microsoft-graph-security-api-4
- Azure Sentinel questions on Reddit: https://www.reddit.com/r/AzureSentinel/
Tech community – forum
As with blogs, there are many forums available to cover each Microsoft product. Forums allow you to read questions from other members, learn more about potential challenges and resolutions, then raise your own questions if you can’t find answers elsewhere. Some of them are as follows:
- Forum for Azure Sentinel: https://techcommunity.microsoft.com/t5/azure-sentinel/bd-p/AzureSentinel
- Forum for Azure Log Analytics: https://techcommunity.microsoft.com/t5/azure-log-analytics/bd-p/AzureLogAnalytics
- Forum for Azure Security community: https://techcommunity.microsoft.com/t5/security-identity/bd-p/Azure-Security
Feature requests
If you have a good idea to improve Azure Sentinel, or you find a gap in any of the Microsoft security solutions that needs to be addressed, you can provide your ideas via the feedback option within the Azure portal. The feedback option appears in the top right-hand corner of the screen, and looks like the following screenshot. You can select the smiley face to provide positive feedback, or the sad face to explain any issues you may have with the functionality, as shown in the following screenshot:
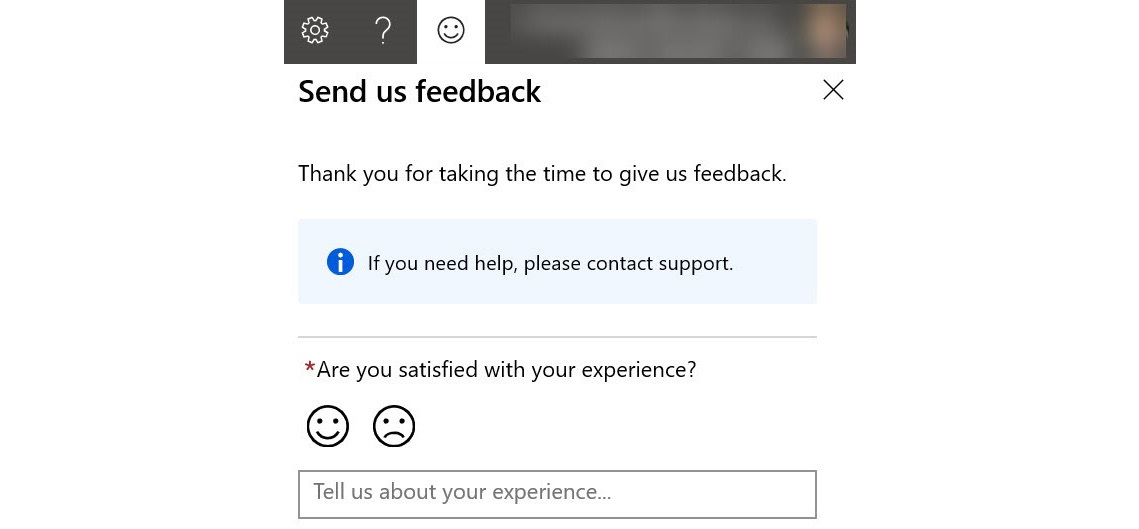
Figure 14.1 – Azure feedback options
While blogs and forums are a good resource for research and to ask questions, you should not rely on them for problems that are having an immediate effect and may need specific technical expertise to resolve. If you need immediate assistance with your implementation of Azure Sentinel, you should reach out to Microsoft Support, using one of the official channels:
If you do not have a support plan, you can sign up for one here: https://azure.microsoft.com/en-us/support/plans.
If you have a PREMIER agreement, you will be provided with direct contact details for your dedicated support team.
In the Azure portal, navigate to the Azure Sentinel home page, then select the question mark icon from the menu at the top right of the screen, as shown in the following screenshot:
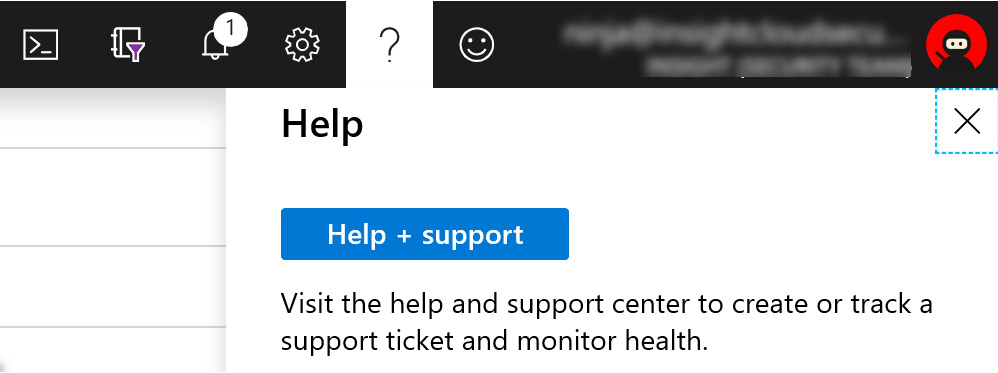
Figure 14.2 – Help and support
Select the Help + support button, then follow the instructions to create a new support request.
LinkedIn groups
LinkedIn can be used to build your professional network and gain access to other experts in your field. Groups are for general discussion on topics of interest and usually anyone can join. Microsoft moderates its own LinkedIn group dedicated to the security community. To join, use the following link to get to the group, then ask to join:
https://aka.ms/AzureSentinelLinkedIn.
Other resources
Microsoft also provides resources on Facebook and Twitter. The following links are shortcut links you can use to get directly to these resources:
- Facebook: https://aka.ms/AzureSentinelFacebook
- Twitter: https://aka.ms/AzureSentinelTwitter
Resources for SOC operations
The following study resources are available for improving SOC capabilities, such as advanced threat-hunting procedures, incident response tactics, and adopting a strategic Zero Trust approach to implementing technology:
MITRE ATT&CK® framework
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. The MITRE ATT&CK® framework was developed to ensure documentation of these behaviors and that they are applicable to real environments. The framework provides a common taxonomy to promote comparison across different types of adversary groups using the same terminology.
The MITRE ATT&CK® framework contains four common use cases:
- Detections and Analytics
- Threat Intelligence
- Adversary Emulation and Red Teaming
- Assessment and Engineering
This framework has been embedded across Azure Sentinel to ensure ease of reference. To learn more about this framework, and to gain access to relevant resources, start by reading the guide to the MITRE ATT&CK® framework at : https://attack.mitre.org/resources/getting-started.
National Institute of Standards for Technology (NIST)
NIST provides a rich source of materials that have been developed for the advancement of security across a range of industries, government, and critical infrastructure. If you are not based in the US, you can still use this information as a guide to secure your own operations and infrastructure.
One of the key articles to review is the Cybersecurity Framework (CSF), aimed primarily at private sector organizations to assess and improve their ability to prevent, detect, and respond to cyberattacks. You can view this here: https://www.nist.gov/cyberframework.
If you are working in government, or looking for the strongest guidance for security controls, we recommend reviewing the information provided by NIST specifically for risk management in government, NIST 800-53 – Security and Privacy Controls for Federal Information Systems and Organizations: https://csrc.nist.gov/publications/detail/sp/800-53/rev-4/final.
Using GitHub
GitHub is the largest, and one of the best, platforms for sharing content and securely storing your code. The platform is primarily used for software development version control, using a distributed version control system called Git. When you start to use GitHub, you create a new project. This contains the code repository and allows for secure collaboration between different authors and contributors. The repository can be set to Private, ensuring only specific people can view the contents, or you can allow others to view and contribute by making it Public.
GitHub is available for free and offers plans for professional and enterprise accounts. To learn how to get started with GitHub, sign up for the tutorial. If you get stuck at any time, there is also a help site dedicated to getting the most out of this unique solution. You can choose between the Learning Lab or the Help site, which can be accessed at the following links:
- GitHub Learning Lab: https://lab.github.com
- GitHub Help site: https://help.github.com
GitHub for Azure Sentinel
Microsoft created and maintains a specific GitHub repository for Azure Sentinel. You can use this repo to find sample queries for Hunting to aid in the development of techniques for threat hunting, by leveraging logs from multiple sources. With these sample queries, you can get a head start in learning the Kusto Query Language (KQL) and understanding different data sources. To get started, simply paste a sample query into the user interface and run the query. To view Azure Sentinel Hunting queries on GitHub, go to the following link: https://github.com/Azure/Azure-Sentinel/tree/master/Hunting%20Queries.
GitHub for community contribution
One of the great benefits of adopting Azure Sentinel as your SOC platform is access to a community of like-minded security professionals who want to help make the world a more secure place. If you have a great idea for a hunting, investigation, or detection query that can be shared with the Sentinel community, you can submit it to the repository and it will be brought directly into the Azure Sentinel service for direct customer use. To learn how to do this, use one of the following resources:
- Azure Sentinel Wiki pages: https://github.com/Azure/Azure-Sentinel /wiki
- Send an email with questions or feedback to:
Specific components and supporting technologies
As we have covered in this book, Azure Sentinel is built upon the Log Analytics platform, as part of Azure Monitor, which uses KQL for queries; Jupyter Notebook; Flow; and Logic Apps, and has machine learning capabilities. Mastering Azure Sentinel requires growing your skills in each of these areas. The following are some of our top picks for resources available today. You may find many more by joining the communities or developing your own groups of special interests.
Kusto Query Language (KQL)
In Chapter 5, Using Kusto Query Language (KQL), we introduced KQL, and in Chapter 6, Azure Sentinel Logs and Writing Queries, we showed how to use it to query logs within Azure Sentinel. However, you will likely need to continue learning this technology in order to write more useful queries and use advanced techniques to fine-tune the results.
For the official KCL documentation, go to the following link: https://docs.microsoft.com/en-us/azure/kusto/.
Pluralsight (https://pluralsight.com) is another great resource for many types of training course across the IT landscape. Specifically, we found the Pluralsight KQL course, which may be of interest to you: https://www.pluralsight.com/courses/kusto-query-language-kql-from-scratch.
Jupyter Notebook
Jupyter Notebook is an open source application used to create and share documents that contain notes, visualizations, live code, and other resources you can share between SOC analysts to improve threat-hunting and response capabilities.
Find more resources for Jupyter Notebook at the following link: https://jupyter.org/.
Machine learning with Fusion
Fusion is a Microsoft technology based on machine learning that helps Azure Sentinel automatically detect multistage attacks. By encasing two or more alert activities, such as anomalous behavior and suspicious activities, Azure Sentinel can produce accurate high-fidelity incidents, reducing false positives and detecting attacks that may otherwise go unseen.
This feature is enabled by default and currently supports several scenarios:
- Impossible travel to atypical location, followed by anomalous Office 365 activity
- Sign-in activity for unfamiliar location, followed by anomalous Office 365 activity
- Sign-in activity from infected device, followed by anomalous Office 365 activity
- Sign-in activity from anonymous IP address, followed by anomalous Office 365 activity
- Sign-in activity from a user with leaked credentials, followed by anomalous Office 365 activity
To learn more about this technology and keep up with the latest developments, visit the following site: https://docs.microsoft.com/en-us/azure/sentinel/fusion.
Azure Logic Apps
Azure Logic Apps can be used for a wide variety of automation tasks, including the following:
- Schedule-based workflow: Creating a task to automatically carry out actions on a frequent basis, such as gathering data, then comparing that value to the last time it was gathered, and raising an alert if the value exceeds a threshold.
- Approval-based workflow: Creating a task to monitor for a given trigger, then sending an approval request (such as an email), and continuing the requested action once the approval is received.
- Azure Functions: This can be integrated with Azure Logic Apps to carry out additional tasks and integrations, such as:
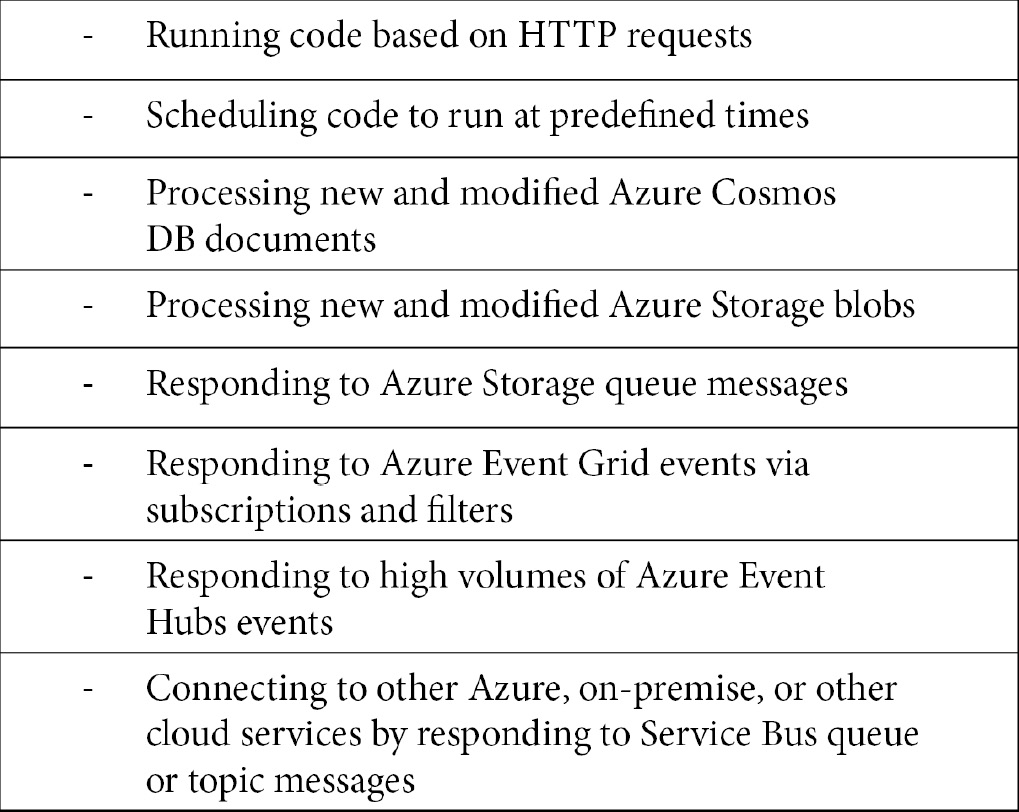
- Storage workflow: Enables integration with Azure Storage to enable the automated collection and retrieval of data.
To enable this automation, Azure Logic Apps is able to use connectors to provide quick access to events, data, and actions across other apps, services, systems, protocols, and platforms. This integration works for on-premise workloads, Azure, and other cloud platforms. Learn more about connectors at the following link: https://docs.microsoft.com/en-us/connectors/.
We recommend studying these capabilities further, to ensure you can automatically trigger actions when alerts and incidents are raised in Azure Sentinel:
Azure Logic Apps: https://azure.microsoft.com/en-us/services/logic-apps/
Summary
As you can see, there are plenty of opportunities for extended learning and contributing your own expertise to benefit others. As Microsoft adds new features to Azure Sentinel, read about the improvements from their blogs and official documentation, then apply the most appropriate changes to your own implementation.
We encourage you to engage and pass on your experience and expertise with others, as we have learned from writing this book; it is only by sharing your knowledge and listening to others’ feedback that you will truly master the topic and appreciate how much more there is to learn!
