STANDARDS GROUPS, PROPOSALS, AND TECHNOLOGIES
Copy Protection Technical Working Group (CPTWG)
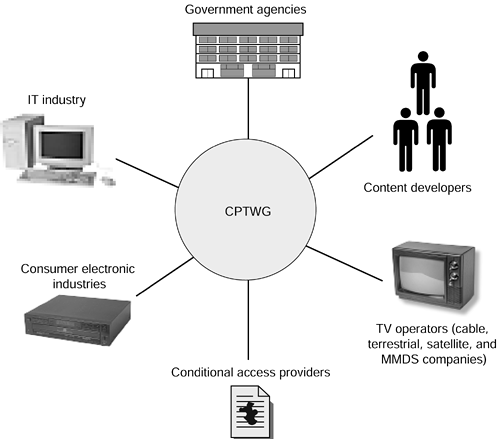
The CPTWG is an ad hoc group of experts from computer, consumer-electronics, and movie-studio industries that was formed in 1996 to assess the technical merits of competing copy-protection proposals for movies, video, and other content on digital media. Figure 18.1 is an illustration of the major industries and organizations that are working with CPTWG to stop the unauthorized copying of digital content.
CPTWG is the frontrunner in developing standards for the protection of digital content. One of its main accomplishments was the launching of an encryption approach called Content Scrambling System (CSS) in 1997. CSS is a technology that prevents unauthorized copying from prerecorded DVD disks.
Digital Watermarking
Current read-only DVD systems prevent unauthorized copying from prerecorded DVD disks by using licensed technologies, such as the digital content scrambling system (CSS) from CPTWG. The content scrambling system is a form of data encryption to discourage reading media files directly from DVD disks. But with the advent of digital recording equipment such as recordable DVDs, digital tape recorders, and personal computers with large disk storage capacities, additional copy-protection features are needed to prevent unauthorized copies of the copyrighted digital content. The solution is the creation of invisible electronic watermarks for digital movies and video. The use of watermarking technologies is becoming a popular method of protecting video content from unauthorized copying and/or playback.
These watermarks are embedded in the video content during the processing and digital compression of the content. For this method of content protection to be effective, the watermark must always be added to the content before the content is distributed via DVD, cable, satellite, broadcast, or MMDS. Watermarking technologies make life difficult for counterfeiters because they are difficult to erase or alter. Although invisible to the user, electronic watermarks contain information that can be recognized, for example, by a detector chip in consumer digital set-top boxes, or special detection software running on compliant PC systems as instructions for enabling or disabling its ability to make a copy. In addition to being invisible to users, electronic watermarks must survive through normal processes such as digital-to-analog conversion and repeated digital compression/decompression cycles while still remaining detectable by the digital recorder system. The addition of a watermark to video/audio material does not interfere with the quality of service for home networking users.
Figure 18.1. Principal players in the content protection industry
In theory, the idea of having detection built into the PC or player sounds really good. However there are two problems. There is no reason why anyone needs to include watermark detection in equipment that they manufacture or software that they develop. Given that absence of copy protection technology is a big selling feature for any equipment, one can only guess that there will be no rush to include the technology from equipment providers and software developers. Second, if you know how to detect a watermark, you know how to remove it. If the watermark algorithm is in every player and piece of software it will be very quickly reverse-engineered, and before long there will be watermark removal utilities.
A subgroup of the CPTWG called the Data Hiding Subgroup (DHSG) was formed in May 1997 to assess the technical merits of competing copy-protection proposals for movies, video, and other content on digital media. In July of the same year, the DHSG issued a call for proposals (CFP) for a data-hiding system that could be used to protect high-value content from unauthorized copying and recopying.
The CFP defined a set of requirements, ranked as either essential or desirable. The essential requirements are as follows.
Transparency—The presence of watermark should not affect the quality of the digital signal.
Low-cost method for digital detection.
Digital detection domain—The digital detection can be made at source data (uncompressed digital video), MPEG-2 compressed elementary data, a multiplexed stream (program/transport), and/or logical sector data.
Generational copy control for one copy.
Reliable detection of piracy.
Watermark will survive normal video processing in consumer use.
Licensable under reasonable terms.
No restriction in export/import.
Technical maturity (proven technology).
Data payload—Three states ("never-copy," "no-more-copy," or "one-copy").
Minimum impact on content preparation.
Data rate of at least 11.08 Mbps
In September 1997, eleven proposals were submitted in response to the CFP. In May 1998, DHSG issued the interim report on the results of its analysis of the eleven proposals. Following the release of this report, several companies sought to strengthen their independent proposals by joining forces. IBM and NEC combined their efforts to jointly develop a powerful method for automatically creating and embedding robust watermarks that are invisible to viewers. At about the same time, Hitachi, Pioneer, and Sony focused their extensive expertise in consumer products and watermarking technologies behind a separate proposal that featured critical technical elements for maintaining the high visual quality of authorized copies and for meeting the more demanding requirements of future high-definition television (HDTV) content. Macrovision, Digimarc, and Philips also joined forces to develop their own proposal on how to deter unauthorized copying of digital content.
At the end of 1998, the IBM-NEC group and the Pioneer-Hitachi-Sony group held a series of meetings to evaluate the possibility of merging their two proposals together. As a result of these meetings, IBM, NEC, Pioneer, Hitachi, and Sony announced the formation of the Galaxy team. The Galaxy team merged watermarking proposals for DVD copy protection and submitted a unified proposal of video watermarking to the DVD Watermark Review Panel (WaRP) on March 2, 1999. WaRP was formed at the December 1998 meeting of the CSS licensees to define and execute the final evaluations of the remaining proposals for video watermarking.
At the time of writing, only two proposals remain for evaluation by WaRP: the unified Galaxy proposal and the one submitted by Philips, Macrovision, and Digimarc.
Protecting Digital Content
As mentioned previously, high-speed digital interfaces allow consumer A/V electronic devices to interoperate with PCs. This is very exciting for home network users; however, it poses some serious challenges to industries that are worried about the pirating of digital content. To confront these challenges, copy protection systems are being developed to:
Protect content in transmission from one A/V device to another
Protect content that is stored on digital tapes, DVDs, CD-ROMs, and hard disks
At the time of writing, digital video sources such as DVD players, set-top boxes, and PCs were not permitted to exchange digital entertainment content with CE devices such as TVs and VCRs through any external digital bus. In an effort to overcome the legal and technical restrictions associated with the transfer of digital data within our homes, the consumer electronics industry has developed the following protection systems.
Digital Transmission Content Protection (DTCP)
The CPTWG formed a subgroup in April 1997 called Digital Transmission Discussion Group (DTDG) to work on the standardization of copy protection tools for digital interfaces (IEEE 1394). A number of companies submitted proposals to the subgroup over a twelve-month period. Figure 18.2 shows the companies that are involved in the protection of 1394-based content.
From the diagram we can see five of the companies (Sony, Hitachi, Toshiba, Matsushita, and Intel) merged their proposals into one, referred to as 5C. The proposal uses a cryptographic protocol called digital transmission content protection, commonly called DTCP, to protect A/V entertainment content from illegal copying, interception, and tampering as the content traverses such high-performance digital buses as IEEE 1394. The technology is available for licensing in two forms. The "use license" is for system OEMs and the "development intellectual-property license" is for semiconductor companies. Semiconductor divisions of Japan's two consumer electronics giants—Sony and Matsushita—have each launched their own DTCP-enabled IEEE-1394 chips. Designed for use in digital set-top boxes and other home networking appliances, these chips support the secure, two-way transmission of digital content across the IEEE interface at speeds of up to 200 Mbps. Both chips encrypt and decrypt digital content in real-time with no load on the consumer appliance's microprocessor. In August of 1998, NDS announced an initiative to broaden the approach of 5C. The new initiative was called *C.
Figure 18.2. Timescales of DTDG proposals
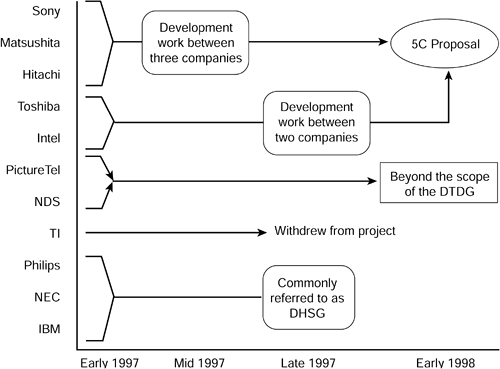
The *C title is fashioned after the 5C, replacing the number 5 with a wildcard. *C covers all the areas covered by 5C and goes beyond. The *C proposal has been submitted to various standards bodies, including CPTWG.
*C is fair, open, secure, flexible, extendable, and involves no nondisclosure agreements (NDAs). To content owners and distributors, *C architecture offers ultimate security as well as powerful and secure support for a wide range of distribution and business models. *C allows consumer electronics manufacturers to shift the bulk of security burden and associated responsibilities to the security provider companies. It also allows them to offer/support a number of consumer features, such as anti-theft protection, flexible and secure parental control and customization and others. Consumers would enjoy the benefits above—the more convenient and attractive distribution options, anti-theft protection and parental control.
Extended Conditional Access (XCA) Approach
Original copyrighted content is delivered to a home network from a number of sources. Under the XCA approach, content can be identified as "never-copy," "copy-once," and "free-copy." These three states are represented using the Copy Generation Management System (CGMS) bits. The A/V devices on your home network should obey "playback control," "record control," and "one-generation control" rules, as summarized in Table 18.2.
Zenith Electronics and Thomson Consumer Electronics are heading a group of manufacturers that favors a smart-card-based renewable encryption scheme called XCA. There are several reasons why this was seen as being advantageous.
First, it decouples the security system from the manufacture of the player. This is important as player manufacturers can come under market pressure to short-cut security as the lack of it is a selling point. (One consumer electronics manufacturer received significant pressure from its distributors to make the ability to remove country codes and macrovision from its DVD players easier. The competition had done so and this had helped their sales).
Second, security is never static. Security systems have a significantly shorter life span than consumer equipment. The breach in the CSS system has become unrecoverable because there is a large base of DVD players that cannot be upgraded. Every security system gets broken. Good system design means that you can recover from the breach. The use of security models goes some way to achieve this.
XCA protection involves two steps:
Content scrambling—Different parts of the content are scrambled with a symmetric algorithm under different keys. For robustness, the key is changed every few seconds.
Key protection—The scrambling keys are derived in a number of ways. They can be generated randomly or derived from Entitlement Control Messages (ECMs). Randomly generated keys are protected using a public-key algorithm or any other method.
Scrambling and key protection take place at the source (i.e., broadcaster headend or publishing house). MPEG-2 defines Entitlement Control Messages (ECMs) for carrying the scrambling keys (control words) together with A/V content. ECMs are then used by the smart card to decrypt the relevant program. In XCA, the ECMs are extended to contain the CGMS bits and access rights as well as control words. Every time copyrighted content (e.g., a movie) is recorded, the extended ECMs (XECMs) are modified through a one-way, irreversible transformation to distinguish copies from the original.
Further information about current XCA activities can be obtained through NDS's Web site at http://www.ndsworld.com/cmp/cmp_docs/xcav5.doc.
