Web surfing is all fine and good, but it’s a decidedly solo activity. When we need to communicate with others, we turn to other methods. Though the younger generation has embraced texting for person-to-person communications, e-mail is still the go-to method for communications in the world of work and for many people who grew up before the era of cell phones and SMS (Short Message Service, the original and official name for “texting”). Instant messaging’s popularity has waned with the advent of smartphones, replaced by more mobile-oriented messenger apps. Let’s dig into these technologies a little deeper. To understand how to protect ourselves, we need to have a basic idea of how they work. Let’s start with e-mail.
When you visit a web site with your web browser, you are creating a connection between your computer and a distant server such as your bank, an online retailer, or whatever. This connection may or may not be encrypted. If it is encrypted, then you can be sure that no one else will be able to peek at your messages.

E-mail communication within a single service
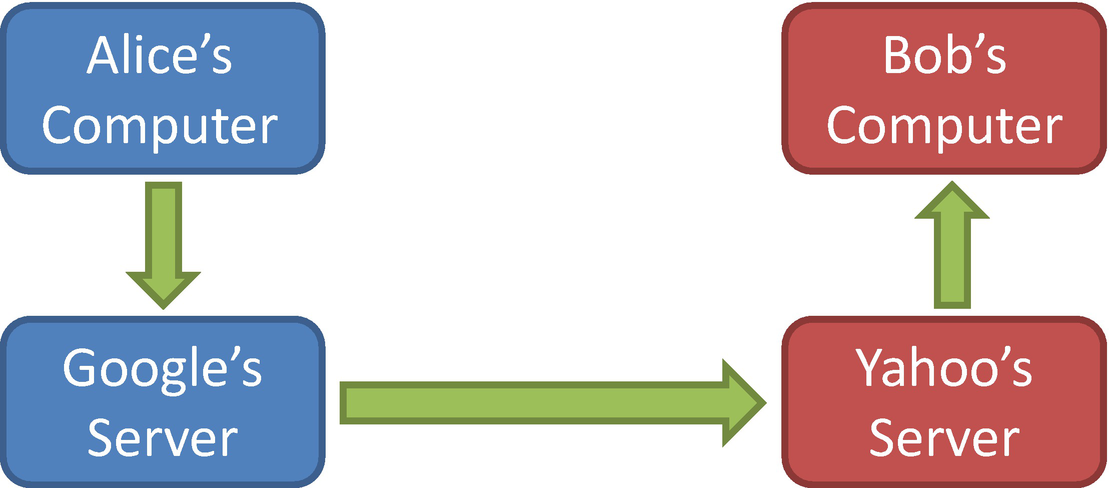
E-mail communication between two services
When we talked about encryption used for surfing the Web, all of the communications were point-to-point and short-lived. With e-mail, the message is often encrypted only in transit (the arrows in the diagram). The messages themselves are rarely encrypted, meaning that anyone with access to the computers or servers could potentially read the e-mails. E-mails are really more like postcards than sealed letters because anyone involved in transporting the message can read it. Also, while the connection between Alice and Google’s e-mail server may be encrypted, she has no way to know or control whether the link between Google’s server and Yahoo’s server is encrypted or whether the link between Yahoo’s server and Bob’s computer is encrypted. In fact, until recently, many of these server-to-server links were known to be unencrypted.
So, what can we do about this? The best answer is to encrypt the e-mail message itself, before it ever leaves Alice’s computer. Bob would then decrypt it when it arrives, and no one in between would be able to see the contents. Unfortunately, this is not easy for the average person to do, at least not yet. Google and other mainstream e-mail service providers are working hard on providing solutions that will work without a lot of user interaction, but as of the writing of this book, they are not yet available. The process involves generating a public/private key pair using a passphrase, publishing these keys to one or more public key servers, and…I’ve already given up. Regular people will never do this. We need something that just works. It may be something entirely new, relegating e-mail to an old technology you’ll tell your grandkids about. E-mail just wasn’t built for end-to-end encryption. Nevertheless, there are some viable options now, and I’ll tell you about them at the end of this chapter.
Text Messaging
Short Message Service (SMS), or texting, came around with the advent of mobile phones. It’s still the lower common denominator today for mobile messaging—all cell phones and cellular service providers support this technology. Texting is similar to sending an e-mail. It supports the store-and-forward function, meaning that the intended recipient doesn’t need to be online to get your message—you can send it whenever you want, and whenever they turn on their phone, the message will be delivered. Also, the phone companies have managed to work out the technical stuff to allow someone on Verizon to send text messages to someone using AT&T or T-Mobile. Apple has even integrated SMS with its instant message system (Messages or iMessage) so that you can use Apple’s proprietary system if all parties are using an Apple product (in which case the messages are blue) or fall back to regular text messaging otherwise (where message bubbles will be green).
Instant messaging (IM) has been around for about as long as e-mail, believe it or not. They both date back to the early 1960s. IM is similar to e-mail in terms of the communications pathways shown in the diagrams for e-mail, but there are two main differences. First, there’s usually no store-and-forward ability. Second, instant messaging is mostly proprietary, so there is usually only one service provider involved. That is, if you’re using Google’s IM service, you generally can’t communicate with someone using Yahoo Messenger or AOL’s AIM service.
This is similar to the newer, mobile-oriented messenger apps: WhatsApp, Facebook Messenger, Telegram, WeChat, Discord, and so on. To chat with others, all users must have the same app installed. Unlike older instant messaging , most modern messenger apps will allow messages to be stored and forwarded if the intended recipient isn’t currently online.
Spam and Spoofed Messages
Junk e-mails and messages—usually unsolicited advertisements—are referred to generally as spam. Many of our most-used messaging platforms are open by default. That is, if you know someone’s e-mail address, messaging handle, or cell number, you can send them a message—no permission required. Some messaging systems have implemented a check mechanism whereby you have to first allow the other person to “follow” or “friend” you before they can send you a message; however, this support isn’t ubiquitous.
If you’re lucky, the spammers will only send you advertisements. However, spam is also a favored delivery mechanism for malware—either with links to bad web sites or with malicious code embedded in attachments. These links and attachments can be sent using e-mail, text messages, and messenger apps.
It’s important to realize that it’s easy for the sender of a message to be spoofed. That is, just because the “from” on the e-mail or text message is someone or some company you know and trust, you can’t assume that it’s really coming from them. Also, e-mail accounts are often hacked, so even if a message truly is from where it says it’s from, you still have to be very wary of any links or attachments given to you. While antivirus and other safety utilities do an okay job of blocking these things, you can’t assume that they are 100 percent effective.
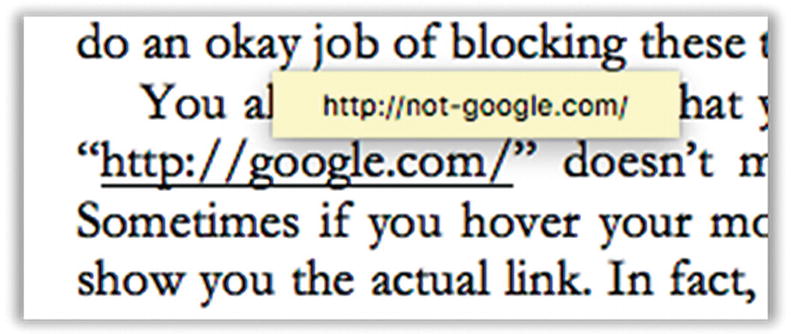
Misleading web links in text
Sometimes the bad guys will try to trick you with web sites that are slightly misspelled, often in a way that is hard to catch like out1ook.com or tvvitter.com.
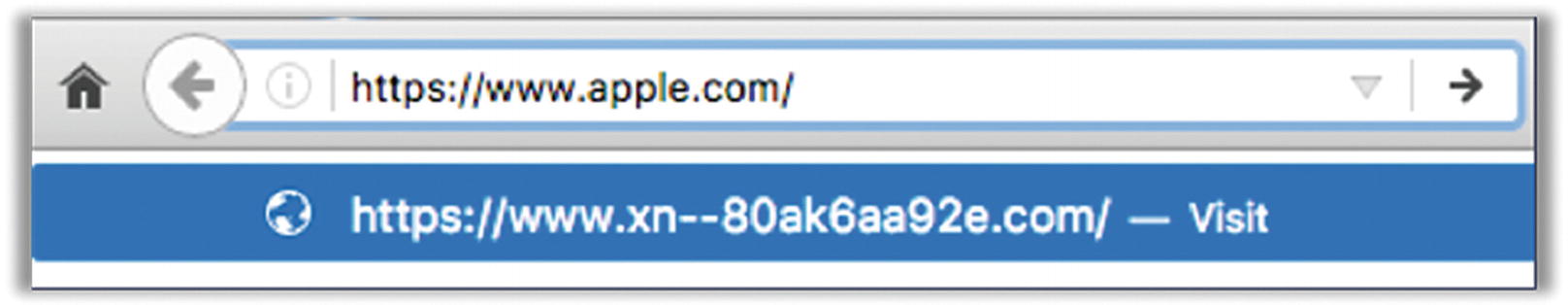
Example of Punycode misleading web address
The top value is what you would normally see, but the unencoded version (the real web site) is what you see at the bottom. While this appears to be the English alphabet characters a-p-p-l-e, the web address here is actually using characters from the Cyrillic alphabet that happen to look just like a-p-p-l-e in the font used by Chrome and Firefox browsers.
Thankfully, web browser password manager plugins like LastPass will not be fooled by either of these tricks. If you go to a web site that should be familiar but LastPass isn’t offering to fill in your username and password, then you might not be looking at the web site you think you are.
Many web links today just immediately redirect you to another web site, so you can’t be certain that what you see is what you’ll get. There are link-shortening services that will take long, obnoxious web addresses and shorten them to something much easier to type and/or remember. These services perform a redirect from the short link to the real destination. So, for many reasons, you simply cannot judge a link by its text.
Finally, some images and links that come in e-mails can be used to track your movements on the Web and will also help spammers to mark you as a viable target. This is why many e-mail clients will refuse to load the images contained in an e-mail until you say it’s okay. For example, a spammer may get a list of a million e-mail addresses from someone who hacked into some databases. The spammer has no way of knowing whether all of these addresses are real and still active. They will also not know if a particular e-mail was able to get through all the various spam filters that are between them and the recipient. But if they put an image in that e-mail with a unique identifier and your e-mail client downloads that image from the bad guy’s server, then they will immediately know that the e-mail address works and that it got through to you... in which case you should expect to receive more junk mail.
Many solutions have been proposed for stopping spam, but because the Internet is so driven by marketing and advertising, the key players have been loath to adopt them. It comes down to this: who gets to determine what’s junk? We’ve had the same struggle with regular junk mail delivered by the postal service. The postal office makes a lot of money delivering those ad flyers to you. However, the risks of malware I believe will eventually drive the industry to offer some sort of solution.
One option would be to charge a small amount of money to transmit more than, say, 100 e-mails in a 1-hour period or maybe 500 per day—something that would not affect most people but would cause spammers some grief. Right now, e-mail is essentially free, which leaves it open for abuse. The problem here is that this could hurt small, legitimate businesses and still allow massive, wealthy corporations to continue sending gobs of unwanted e-mails.
The most draconian option would probably be moving to a whitelist system where you cannot send e-mail to someone unless they first approve you as a sender. This could be automated to a certain degree. When you first e-mail someone, you will get a canned response from the service provider saying something like “I only accept e-mail from people I know. Please contact me by some other mechanism first or answer these few questions to prove you know me.” Spammers deal with millions of e-mails, so they wouldn’t have time to bother with this. This would still allow legitimate companies with which you actually have some relationship to contact you. The process of registering on their web site could automatically add them to your whitelist of approved senders. My gut tells me that this is where we’ll end up, unless we come up with a completely new scheme for sending electronic messages .
Until then, we have limited methods of dealing with junk messages. We’ll cover those in the checklist.
“So How Do I Communicate Securely?”
Most of the time, you will probably be satisfied knowing that your e-mails and text messages are encrypted in transit, even if the message itself is not. You’ll need to realize that your e-mail and messaging service providers are almost surely scanning your messages so they can improve their marketing profiles on you. Most of this is automated (it’s not a human reading your stuff), but nevertheless, you’re trading your privacy to use these free services.
But there will come a time when something you want to send needs to be really private. Maybe you’re discussing something deeply personal, or maybe you’re just trying to send financial information to your tax preparer. Remember that copies of whatever you send will likely remain on the servers of your messaging provider, possibly even after both you and the recipient delete the messages.
So, how can you do this? You have at least two options (and to be super secure, you can do them both simultaneously). We’re talking about data at rest versus data in motion, that is, encrypting the content of the message versus encrypting the channel that the data will pass through. Think about it this way. You can put your money in a safe—that’s security at rest. If you want to then send that money across town, you could hire an armored car—that’s security in motion. If you want to be really secure, you would have the armored car transport the money in the safe—that’s using both mechanisms at once. If someone hijacks the armored car or follows it to its destination, they’d still have to break into the safe to get the money.
Let’s talk first about securing your messages as they traverse the Internet. As we’ve said, most modern messaging systems will encrypt your message as it travels but will not encrypt the message itself. There are some notable exceptions that offer end-to-end encryption . That is, the message contents are actually encrypted at the sender’s device and are capable of being decrypted only by the recipient’s device. These systems use a form of asymmetric encryption like we discussed earlier in the book—using a public key to encrypt the message and a private key to decrypt it. Apple’s iMessage service offers full end-to-end encryption, as do the Telegram and WhatsApp messenger.1 There are secure e-mail services, as well, including a wonderful service called ProtonMail. Unfortunately, in all of these cases, you’ll need your intended recipient to use the same service.
One way around this is to separately encrypt the contents of your message, and then you can theoretically send it using any communications mechanism you want. This would be like driving your safe full of money across town in the back of your pickup truck. Everyone can see the safe—and may well assume that it contains something valuable—but the contents are perfectly secure, assuming you bought a decent safe.
So, how does one go about encrypting a message or a file? The simplest way is to zip the file or files using a compression utility. These utilities are usually used to shrink the size of a file and/or bundle several files together into a single file. You select the file or files and tell the utility to zip them up, resulting in a single output file that should be smaller than the original(s). In fact, the most common such utility creates a file ending in .zip.
But these zip utilities also often have the option of adding a password to the bundle, meaning that the recipient won’t be able to unzip the file without knowing the password. Adding the password encrypts the entire bundle.
If what you’re sending could be sent as a Portable Document Format (PDF) file, you can also usually create PDF files with passwords. So, if you’re sending a single file, you could export that file to PDF format and add a password to that file. (This may require opening “advanced” options when exporting the file.)
Of course, if you have the option, you could combine both techniques: encrypt the contents and send them using an encrypted communications mechanism. But at a bare minimum, you need to encrypt the contents itself. Remember that whatever you send could be saved on a server somewhere for a very long time, possibly unencrypted, just waiting to be found. Encrypting the file is more important than sending the file using an encrypted communications channel.
Note
When sending a password-protected (encrypted) file, you must find a way to securely communicate the password to the recipient. Specifically, you can’t just send the password using the same mechanism that you used to send the file. For example, if I were to e-mail my tax docs to my CPA in a password-protected zip file, I should not then send him the password in another e-mail. I should either call him on the phone and tell him the password or send the password using a secure messenger application.
Summary
E-mail and text messaging add a new dimension to the problem of secure communications. Instead of just having to secure a single channel between you and a web server (as with web surfing), you also need to secure the channel from the server to the intended recipient—and perhaps between your service provider’s server and their service provider’s server. That is, communication between two or more people is almost never point-to-point—there could be other “legs” along the way that are not secure.
Furthermore, even if all of these separate channels are encrypted, the messages themselves are almost surely not, meaning that the servers between you and the intended recipient will have copies of your messages that they can read whenever they like. Those copies can remain long after you and the recipient delete them.
We have to be careful when clicking links and opening attachments we receive, even if they appear to be from someone we know and trust. E-mail in particular can be used to send dangerous, malware-laden files or links to web sites that will attempt to infect your computer.
If we want truly secure and private communications, we need to encrypt the message itself as well as the channel by which it’s sent.
Checklist
Tip 8-1. Create E-mail Accounts for Public and Private Uses
E-mail accounts are free and easy to create. Having one e-mail address for people you actually care about and another “throwaway” address for retailers, web forums, contests, etc., will at least allow you to quickly segregate important e-mails from ones that can wait (possibly forever). If your current e-mail account is already swamped with junk, you should consider creating a new e-mail address that you will give out only to friends and family.
Tip 8-2. Use an Encrypted E-mail Service
The desire for truly private e-mail communications is definitely increasing as we learn more and more about mass surveillance and hackers liberating embarrassing conversations from poorly secured servers. The marketplace is starting to respond with new offerings that provide true end-to-end encryption.
Tip 8-3. Send Sensitive Info Securely
You should never send sensitive or highly personal information via e-mail or text message. Again, most of these messages should be thought of as postcards, not sealed envelopes. And copies of these messages may remain on servers long after you and the recipient delete the message. Sensitive info would include Social Security numbers, credit card numbers, passwords, medical or financial data, and anything else that you wouldn’t want someone else to see.
Regardless of how you plan to send this information, you should take the precaution of encrypting the data before you send it. This means somehow locking that data with a password. The gold standard for this is a system called Pretty Good Privacy (PGP) , but it’s hard to set up. An easier and more universally accessible method is to create a password-protected zip file. While you will need some special tools to create this encrypted zip file, your recipient should be able to open this file without needing a special application. (Even if they do, the applications are free and easy to use.)
Your first step is to pick your password. Since this is something you’ll need to be able to communicate to someone else (your recipient will need this to open the file), consider how you will send it. You can’t use the same mechanism for sending the zip file and sending the password. Will you have to call them on the phone? Can you send them a secure text message? Will they be able to copy and paste it, or will they have to type it by hand? You want something they can handle without too much trouble, but it can’t be easy to guess. Once you have your password, proceed with the following steps to create your file.
Once you’ve created your file, you can send it via e-mail. You might also use a cloud storage service like Dropbox , which allows you to create a “share link”—a unique download link. Once the file has been downloaded by the recipient, you should remove the file from your cloud service (or at least disable the share link).
If this whole process is too complicated, you might try the next tip.
Tip 8-3a. Windows
- 1.
Download and install 7-Zip (you probably want the 64-bit version unless you have a very old computer): https://www.7-zip.org/ .
- 2.Put all of the files you want to encrypt into a single folder, say My Private Files. Then right-click this folder and select 7-Zip ➤ Add to archive (Figure 8-5).
 Figure 8-5
Figure 8-57-Zip archive creation
- 3.Don’t let all the options scare you. In the window that pops up (Figure 8-6), you only have to check three things.
- a.
Set “Archive format” to 7z (upper left).
- b.
Set “Encryption method” to AES-256 (lower right).
- c.
Enter your chosen password.
- a.
- 4.Click OK to create your password-protected file (it will end in .7z). Send this file to your recipient. If they have trouble opening it, have them download 7-Zip (Windows) or Keka (Mac).
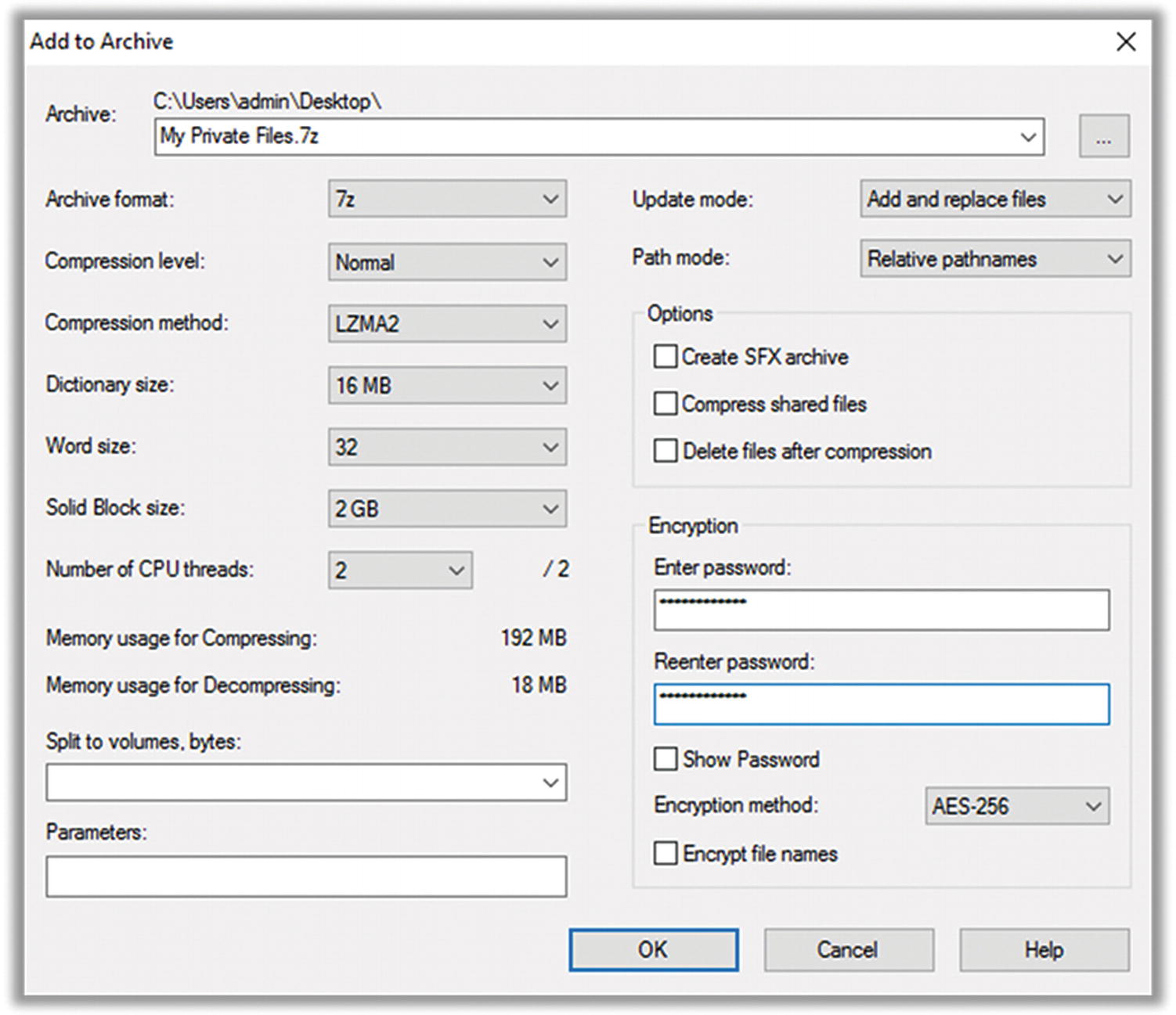 Figure 8-6
Figure 8-67-Zip password-protected archive settings
Tip 8-3b. Mac OS
- 1.
Download and install Keka. Ideally, you would do this via the Mac App Store. But you can also find it here: https://www.kekaosx.com/en/ .
- 2.Keka is handy but a little odd to work with. Launch Keka (Figure 8-7). If not already selected by default, choose the tab for 7z. Fill in your chosen password. I usually also select “Exclude Mac resource forks” (harmless and invisible to Mac users but confusing for Windows users).
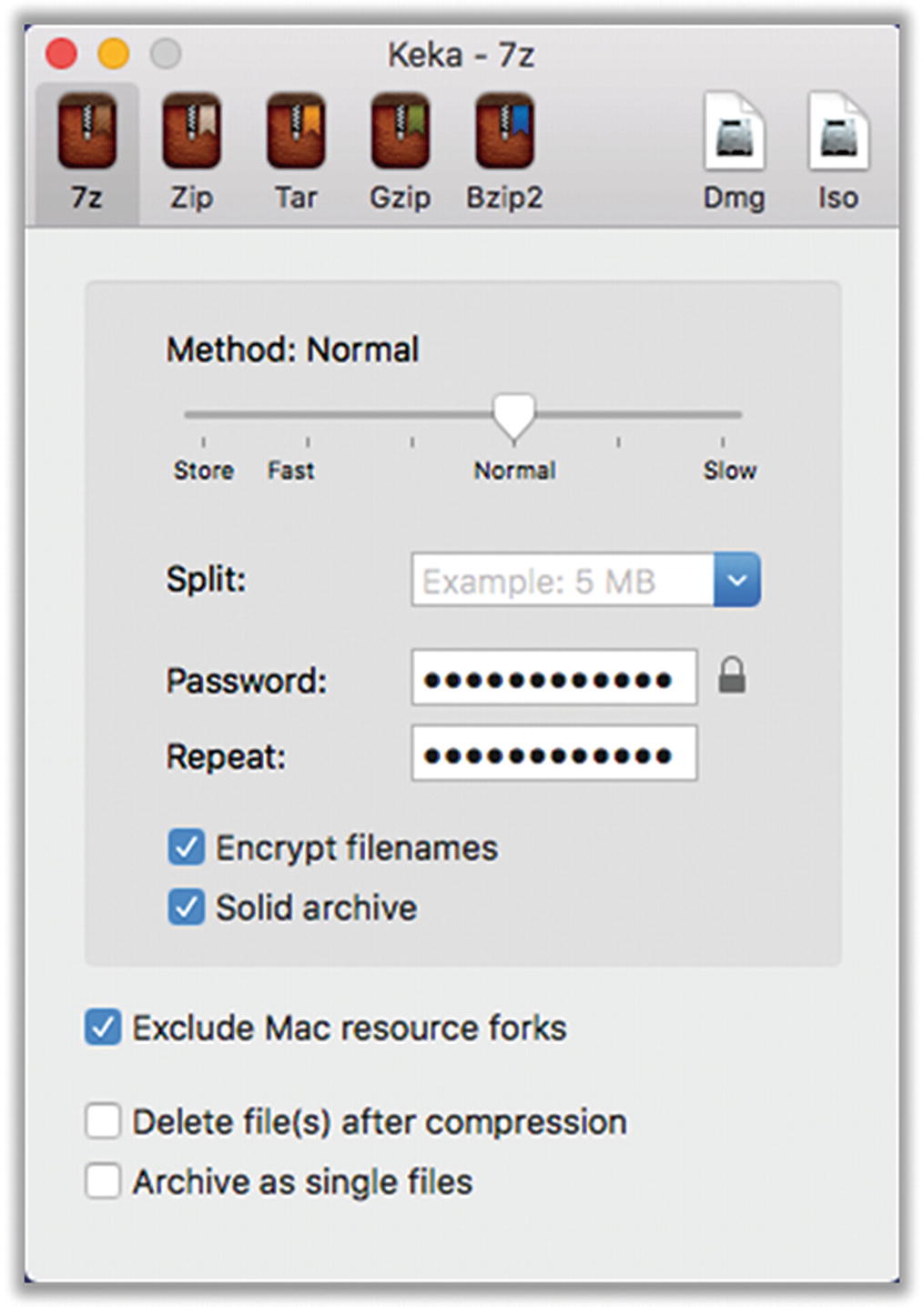 Figure 8-7
Figure 8-7Keka password-protected archive settings
- 3.Put all of your files into a single folder, say “private files.” Drag that folder on top of the Keka window and it will change (like Figure 8-8). Just let go and your encrypted 7z file will be created (by default, it will be in the same location as the original folder).
 Figure 8-8
Figure 8-8Keka creating an encrypted archive
- 4.
Send this file to your recipient. If they have trouble opening it, have them download 7-Zip (Windows) or Keka (Mac).
Tip 8-4. Send Files Securely Using the Web
- 1.This service currently supports sending single files only. If you have multiple files or folders, you should first zip them all up into a single file. When you do the following, you’ll end up with a file ending in .zip that you can send. This is not encrypted! But the sending process will protect it.
On Windows, right-click the main folder and select “Send to…” and then “Compressed (zipped) folder.”
On Mac, right-click the main folder and select “Compress (folder name).”
- 2.Go to https://send.firefox.com/ . Simply drop your file onto the web page to upload the file securely (Figure 8-9).
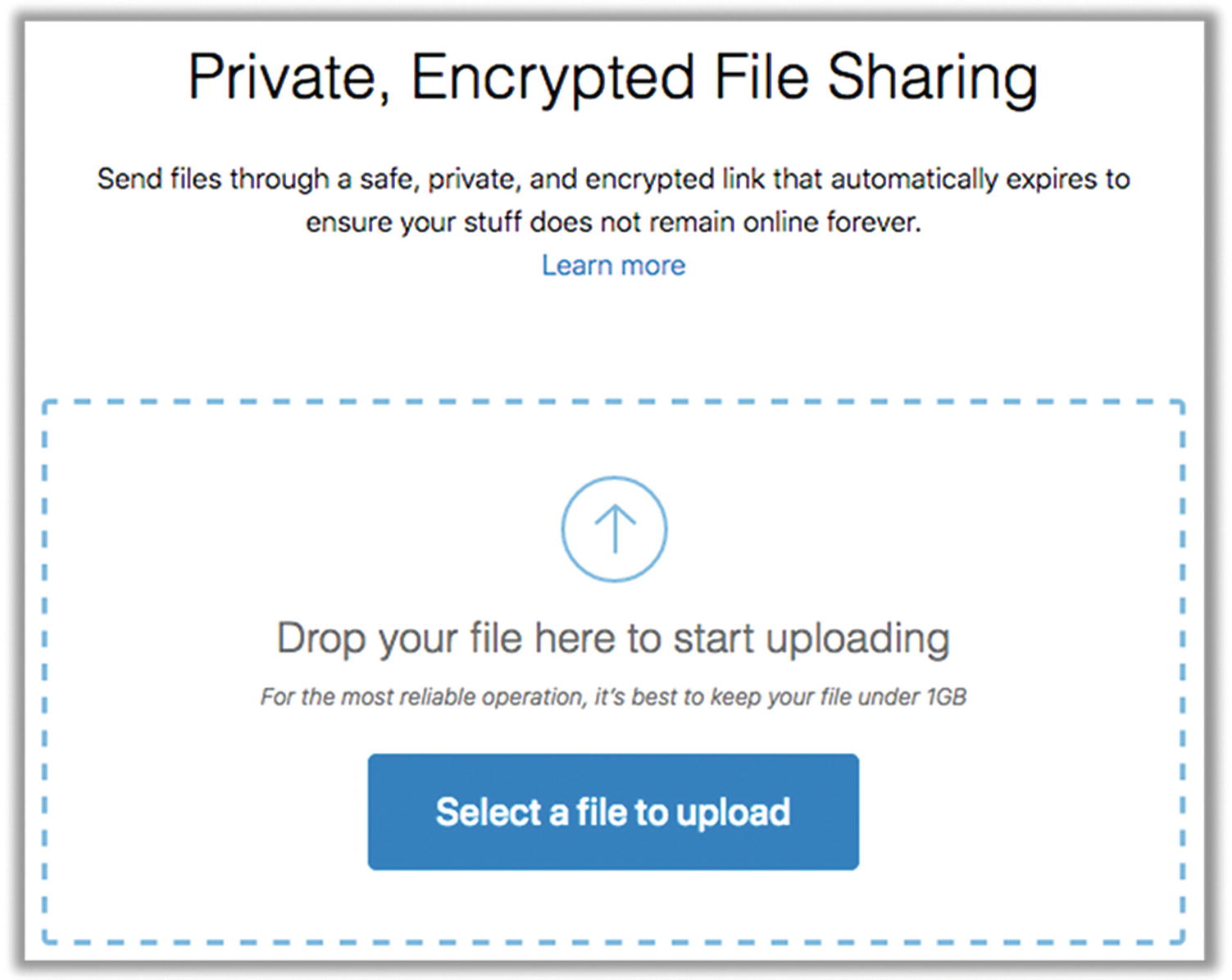 Figure 8-9
Figure 8-9Sharing a file with send.firefox.com
- 3.This will result in a unique web link that you can send to your intended recipient for secure downloading (Figure 8-10). Simply click the “Copy to clipboard” link and then paste this link in an e-mail or text message. Note that by default, this link will expire in 24 hours. It will also be good for only the specified number of downloads. After successfully being downloaded or after 24 hours (whichever happens first), the file will be deleted. You can also delete the file manually using the button on this page. I strongly recommend setting a password. Anyone with the link will be able to download the file—adding a password will add another security step.
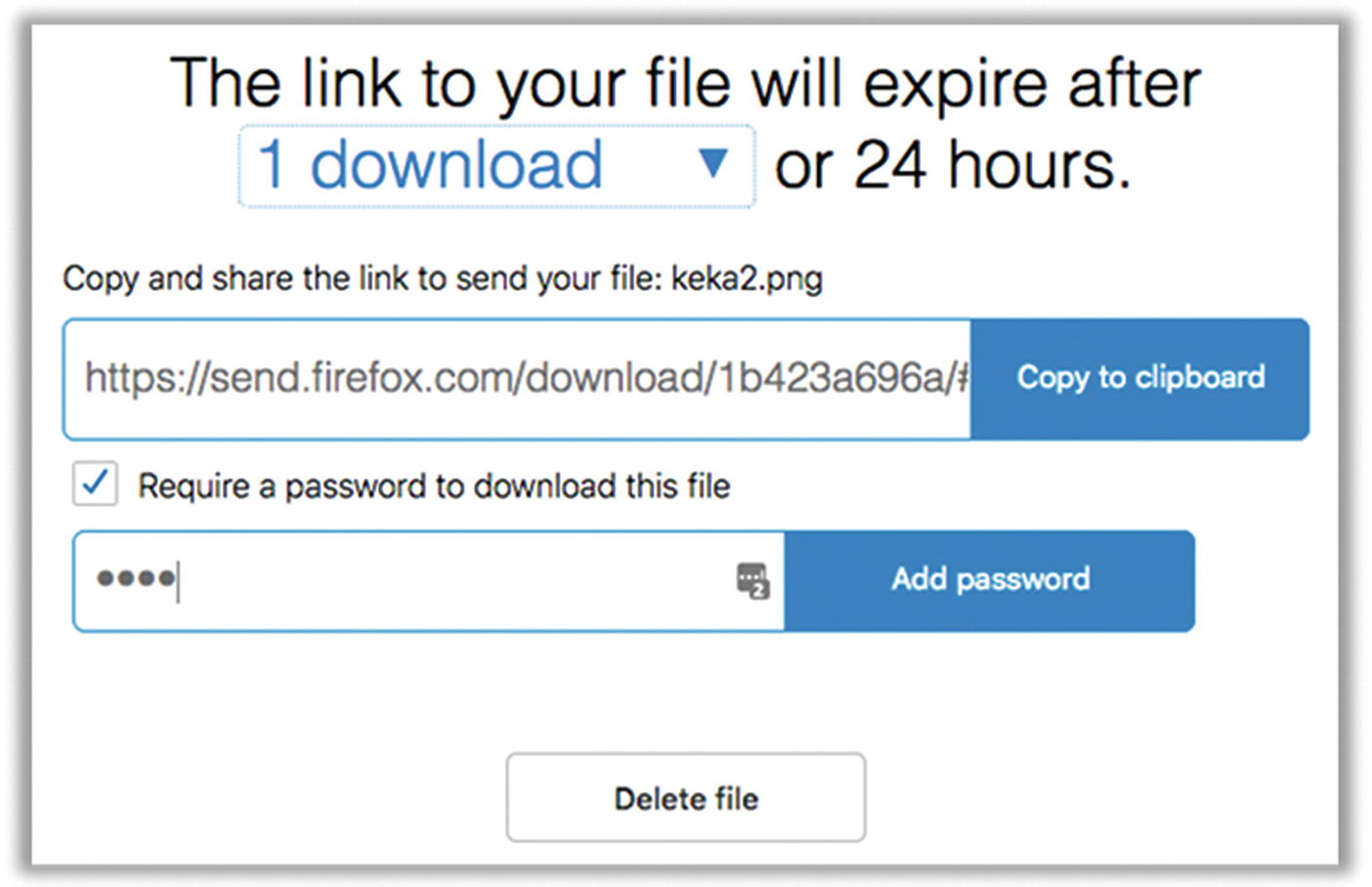 Figure 8-10
Figure 8-10Settings for sharing a file with send.firefox.com
Tip 8-5. Read Your E-mail Using the Web
While e-mail applications like Windows Mail and Apple Mail have some really handy features, sometimes it’s better to use the web-based e-mail client. Many web e-mail clients are quite good actually, including some features you can’t even get on a more traditional application you would run under Windows or Mac OS. If you’ve received a sketchy-looking e-mail, using the web client to read it can provide another layer of safety. Most popular web e-mail clients have built-in virus and link scanners. These clients also have much more limited access to your local files and operating system—they’re “sandboxed” to help contain bad things within your browser.
The one downside to strictly using a web-based e-mail client is that you don’t have a local (downloaded) copy of all your e-mails. If your e-mail provider is inaccessible for any reason, you won’t have access to any older e-mails. So I generally recommend that you use a regular mail application periodically, which will download your messages locally for offline access and backup. Examples of this would be the Mail applications that come built in to Mac OS and Windows 10.
Tip 8-6. Don’t Abandon Unused E-mail Accounts
Over the years, you may have accumulated several e-mail accounts. Sometimes your ISP will create an automatic e-mail address for you, for example. Or perhaps you had to set up an e-mail account for some special occasion and now have no need of it. If you never check it, you may never realize that it has been taken over by spammers or other ne’er-do-wells. I recommend checking in on your old accounts from time to time. Look in the Sent folder and make sure it hasn’t been hijacked. (If so, see Chapter 12 for dealing with a hacked e-mail account.)
If you don’t plan to use the account anymore, you have two options. If this account was rarely used, I would delete all e-mail in all folders, clear out any saved contacts, and then contact the e-mail provider on how to delete your account.
If you want to delete an account that you’ve used a lot and is well known to your friends and family, I would instead consider just leaving it alone. E-mail providers will sometimes recycle old e-mail addresses, meaning that someone else could end up with your address (like someone else getting your old phone number). This can lead to confusion and could even be abused. So, you might delete all the e-mails and contacts and then just check it from time to time to keep it active (from the perspective of your e-mail provider). Make sure this account has a strong, unique password, too.
If you’ve forgotten the password, you can usually find a “forgot my password” link that will send a reset e-mail to whatever your backup e-mail account was for that account. (I know... it’s a vicious cycle, right? Do you have access to that account?)
Tip 8-7. Keep an Eye on Your Account Activity Info
Many e-mail providers will alert you if they detect suspicious activity on your account. This often means accessing your account from unusual locations. (Remember, each computer has a unique IP address, and this address can be used to find your general location on the planet.) Every so often, you might take a peek at your recent activity to look for this yourself, especially if you have some reason to believe your e-mail account may have been hacked. Here are links to three of the most common e-mail account services. However, you can probably find similar “activity” information under your profile/account settings for most services.
- 1.
Sign into your Google account: https://myaccount.google.com/security#activity .
- 2.
At the left, click “Device activity & security events.”
- 1.
Go to this link: https://account.live.com/Activity .
- 2.
Sign in to view your activity.
- 1.
Go to your Yahoo profile: http://edit.yahoo.com/config/eval_profile .
- 2.
Click “Recent activity.”
Tip 8-8. Don’t Forward Something Without Verifying It First
We’ve all gotten those e-mails about dying children wanting to get e-mails from around the world or Disney giving away free passes or some celebrity dying. There are many hoaxes and “fake news” out there that sound very real. Do your part by verifying anything before sending it to all your friends and family. How do you do that? You can always just search the Web using a key phrase from your e-mail plus the word hoax . Or you can just go to snopes.com , whose whole purpose is to document these chain letter claims (as well as common urban legends). Some of them are even true. They do the homework for you.
Tip 8-9. Don’t Click Links, If Possible
Links can be faked or tweaked ever so slightly so that a human might not notice. For example, out1ook.com instead of outlook.com or tvvitter.com instead of twitter.com…did you catch the difference? It may depend on the font you’re using to view this book. It gets even worse, though. There’s a web standard called Punycode that allows the creation of web addresses using all sorts of foreign language characters that often look just like their standard English keyboard counterparts.
Whenever possible, leave the e-mail be and go straight to the source in your web browser. For example, if you get a suspicious e-mail from your bank that says “click here to verify your account,” just log into your bank directly and check your account for any notices (or call them). Note that it doesn’t really matter if the e-mail comes from someone or some company you trust—the sender can be forged, or their account could have been compromised.
The main rule here is: don’t click any links that you didn’t ask for. For example, if you just reset your password, then you would expect an e-mail shortly thereafter with a link to click.
Tip 8-10. Don’t Open E-mail Attachments, If Possible
While images are usually safe, things like Microsoft Office documents (Word, Excel and PowerPoint files), PDF files, or compressed files (like zip files) should be avoided—or any file with an extension you don’t recognize. At work, follow whatever policies your company specifies. You can’t get very far if you don’t trust e-mail from your co-workers. But at home, you should be very wary about opening any attachment that you didn’t explicitly ask for. If you’re not sure, contact the sender first (via phone or some other means) to make sure they did actually send it.
Tip 8-11. Check Files Before Sending
Tip 8-12. Deal Properly with Spam
If you get an e-mail that you’re pretty sure is junk, don’t even open it, and certainly don’t reply to it. You don’t want the sender to know your e-mail address is active and valid. Don’t try to “unsubscribe,” unless you’re sure the sender is reputable. If your e-mail application has the option to mark the message as junk or spam, do that—it will help them to filter these messages out in the future (not just for you, but for others, as well). If there is no such option, just delete the message. If the sender is a company you have an account with, then log into your account and find your e-mail preferences. You should be able to turn off (or at least reduce) their e-mails there.
Tip 8-13. Use Secure Messaging Apps
Signal is my top choice: https://www.signal.org/download/ .
Wire (use the free “personal” account): https://app.wire.com/ .
