Chapter 8
Introduction to Ad Hoc and Sensor Networks
In previous chapters we have considered issues required to provide the protocols and software support needed to use the resources available in a pervasive computing environment. In the following several chapters we introduce a different aspect of pervasive computing.
One of the envisioned uses of mobile computing, as well as a potential advantage of such a paradigm, is the ability of the device and its user to interact with the surrounding environment. As mobile users travel, their devices should interact in a seamless way with computing devices embedded in the surrounding area. This part of this book discusses the protocols needed to provide a scalable and cost-effective realization of this vision of ubiquitous computing, which relies on the dissemination of wireless sensor nodes, also called smart sensors, sensor nodes, or simply sensors, that have the ability to monitor physical, chemical, or biologic properties. Instead of addressing only those tasks required to connect networks of these sensor nodes with preexisting networks, we instead focus on the requirements for supporting wireless networks of sensors to accomplish their intended purposes of sensing, monitoring, and disseminating information.
8.1 Overview
Wireless networks of smart sensors have become feasible for many applications because of technological advances in semiconductors, energy-efficient wireless communications, and reduced power budgets for computational devices, as well as the development of novel sensing materials (Akyildiz et al., 2002). Figure 8.1 shows a generic wireless sensor node partitioned into some basic components. Besides the CPU and memory, the sensor node has, of course, a number of analog sensors. These sensor outputs must be converted to digital data that can be processed by the CPU. This transformation is performed by the analog-to-digital converter (ADC). Batteries or passive power sources could provide the wireless sensor node with power as indicated by the power supply component. Although other wireless communication mechanisms are possible, most wireless sensor nodes use radio frequency (RF) transmissions, so the final component shown in the sensor node is the RF transceiver. The entire sensor node is encapsulated in the appropriate packaging for the environment in which the sensor node will operate.
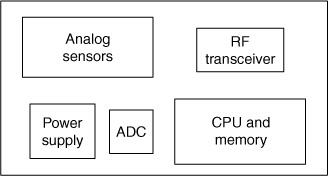
Figure 8.1 Generic wireless sensor node.
In the near future, it is reasonable to expect that technology has advanced to the point where cost-effective implementations of these sensor nodes allow for extensive deployments of large-scale wireless sensor networks. The availability of such networks will change the methods of solving many existing problems dramatically and also will offer an opportunity for novel solutions that have yet to be imagined. Wireless sensor networks hold the promise of allowing us to improve our understanding of the environment, both the natural environment of animal habitats and artificial environments such as a building or an automobile engine. A better understanding of these environments will allow us to use sensor networks more efficiently and control them more precisely.
Now that such networks can soon be realized, it is imperative that protocols be developed to enable these networks to achieve their intended purposes along with the flexibility to support future protocols that will be created once sensor networks become deployed widely. In this part of this book we describe many of these protocols, differentiating them from existing protocols for wireless and wired networks. We also provide an overview of some applications being considered for wireless sensor networks.
8.1.1 Outline of chapter
This chapter presents an introduction to ad hoc networking, wireless sensor networking in particular. This chapter also serves to introduce applications that motivate the protocols that will be presented in subsequent chapters. In the following subsections we briefly summarize the contents of this chapter.
Overview of ad hoc networking.
Ad hoc networking refers to a network with no fixed infrastructure (Perkins, 2000). When the nodes are assumed to be capable of moving, either on their own or carried by their users, these networks are referred to as mobile ad hoc networks (MANETs). Otherwise, these networks are simply ad hoc networks with fixed nodes but without a preexisting infrastructure. The nodes that form the network rely on wireless communication to collaborate with each other. The advantage of ad hoc networking is that the absence of a fixed infrastructure reduces the cost, complexity, and time required to deploy the network. On the other hand, the lack of a fixed infrastructure introduces challenges to using and maintaining ad hoc networks.
Example applications.
Many applications have been proposed for wireless sensor networks (Akyildiz et al., 2002). Although we do not describe each application in detail, a brief overview of a number of these intended applications will be discussed in Section 8.4. This discussion serves to distinguish the properties and requirements of sensor networks, as well as to motivate the underlying protocols that have been proposed to satisfy these requirements. To motivate this topic, we outline two sample applications of wireless sensor networks to demonstrate the scope of their applicability.
The first application is the use of a wireless sensor network for habitat monitoring. Although biologists can monitor habitats by visiting the sites and making observations, there are a number of drawbacks to this approach. First, careful examination of a large area requires many people and continuous observation. Second, the act of observing the habitat may modify the behavior of the animals studied. For example, animals may refuse to nest in preferred areas because of human activity. Sensors, however, can measure data such as temperature and humidity at nesting sites accessible to humans only through direct contact with the nesting site. In some cases, monitored areas may not be feasible to reach, or reaching them could scare the animals away. An example implementation of this application domain is tracking of the nesting habits of seabirds, which requires monitoring a large geographic region without a human presence (Mainwaring et al., 2002).
The second application we consider, which is completely different from the first, is the use of what are essentially sophisticated wireless sensor nodes for the exploration of Mars. Each remotely operated spacecraft takes soil samples, analyzes those samples using the sensors within the spacecraft, and relays sensor readings to Earth using wireless communication. The Mars Exploration Rovers (Hong et al., 2002) and spacecraft from Europe and Japan being sent to Mars are examples of the use of wireless sensor technology for this application. The sensors used in space exploration are much different from the types of sensors assumed for most applications that we will discuss because they are carried on small solar-powered robotic vehicles that perform a great deal of complex processing of data before data transmission. Even so, this example serves to show the wide range of potential applications for which sensors are already being used. Up-to-date information on the Mars Exploration Rovers can be found at http://marsrovers.nasa.gov/home/.
Hardware limitations.
For many applications, wireless sensor networks are expected to comprise nodes with limited computational capabilities, limited memory and storage, and little power (Estrin et al., 1999; Pottie and Kaiser, 2000). This introduces many challenges to achieving the potential of wireless sensor networks. We describe these challenges in greater detail as motivation for the difficulties involved in making scalable wireless sensor networks a reality.
Wireless sensor network tasks.
In order to allow a wireless sensor network to support a particular application, many of the following tasks need to be supported. Many of these tasks are discussed in this book, although some have been omitted to focus on the most basic or essential tasks. The following complete list is useful, however, to gain a better understanding of the many avenues for further exploration:
![]() Neighbor discovery
Neighbor discovery
![]() Self-organization or self-configuration
Self-organization or self-configuration
![]() Sensing
Sensing
![]() Signal processing or sensor data processing
Signal processing or sensor data processing
![]() Data aggregation, storage, and caching
Data aggregation, storage, and caching
![]() Target detection, target tracking, and target monitoring
Target detection, target tracking, and target monitoring
![]() Topology control for energy savings
Topology control for energy savings
![]() Localization
Localization
![]() Time synchronization
Time synchronization
![]() Routing
Routing
![]() Medium access control
Medium access control
Protocol requirements and proposed approaches.
In subsequent chapters we first describe, in more detail, the implications various sensor network application requirements and sensor node limitations have on the design of protocols for wireless sensor networks. Then we present proposed protocols that satisfy the various requirements of wireless sensor network applications. These protocols are heavily dependent on the characteristics of the sensor networks and the intended applications. As will become clear in these discussions, the proposed protocols differ in significant ways from protocols in traditional networks for similar problems, such as routing or medium access control.
8.2 Properties of an Ad Hoc Network
Ad hoc wireless networks differ from those of wired networks in several ways. This produces some unique challenges to protocol design. Knowledge of these various factors will help to motivate understanding of the protocols that have been developed for ad hoc networks. In this section, we briefly introduce and explain each of these properties.
8.2.1 No preexisting infrastructure
By definition, ad hoc networks do not have any infrastructure. The nodes in the network rely on wireless communication for information dissemination and gathering. This obviates the expense of providing many resources and allows the use of ad hoc networks in remote environments, as well as making them attractive for additional applications because of the reduced cost of setting up and using such networks. Wireless sensor nodes generally need to communicate with base stations (Pottie and Kaiser, 2000), which may be fixed nodes. However, sensor nodes themselves do not tend to rely on any underlying infrastructure for performing their duties locally. In Fig. 8.2, a sample wireless sensor network is shown with a single base station. Although the sensor nodes are placed randomly in this figure, regularly placed sensor nodes are important for certain applications. In addition, a wireless sensor network could have multiple base stations, but a single base station simplifies the figure. As shown in the figure, the base station provides a gateway between the wireless sensor network and other networks such as the Internet. Such a gateway may not exist in every case; e.g., privacy or security may limit the connectivity of the wireless sensor network with the Internet.
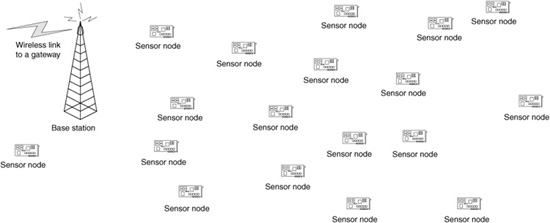
Figure 8.2 Sample wireless sensor network.
8.2.2 Limited access to a base station
Ad hoc wireless sensor networks perform most of their functions without a base station. A more powerful computer thus may function as a base station to act as a gateway to the Internet or other networks (Pottie and Kaiser, 2000). This base station would inject queries into the sensor network and accumulate and archive information generated by the sensors; however, the ad hoc network would need to perform many tasks locally rather than relying heavily on the base station. There are several reasons why this is desirable. Fundamentally, the cost of communicating with the base station could be a significant power drain on the nodes in the network. Multihop communication from the sensors consumes power at each sensor along the path toward the base station. Sending large amounts of data will exhaust the energy of nodes even more rapidly. Another reason is that the sheer volume of information that can be generated by the sensor nodes could easily overwhelm the base station, especially for a large-scale sensor network.
Better scalability can be achieved by reducing the volume of information sent to the base station. The requests from the application can be distributed to the sensor nodes, and each sensor node can determine which sensor readings match the application requirements and return only the relevant data. A third reason is that much of the information that a sensor needs, such as number of neighbors or local routing decisions, can be determined locally more efficiently without interaction with the base station. Therefore, although a base station is available in most cases, nodes that make up the ad hoc network are responsible for acting on their own without using a base station for arbitrary routine tasks.
8.2.3 Power-limited devices
Sensor nodes or other computational devices that make up the ad hoc network exist in an environment that is assumed to be devoid of resources such as power. In fact, because of the absence of any underlying infrastructure, power outlets generally are not available.
For this reason, devices that form the ad hoc network use either battery power or passive power sources, such as solar energy (Doherty et al., 2001) or vibration energy (Shenck and Paradiso, 2001). For example, power could be generated by harvesting the energy produced in a shoe from toe taps or vibration of an automobile engine (Roundy, Wright, and Rabaey, 2003). Although passive sources of energy are attractive options because of their ability to provide power on a continual basis, the quantity of power gathered by solar collectors and other types of passive power collectors tends to be relatively modest (Doherty et al., 2001). In the future it may be possible to power small sensor nodes using these extremely limited power sources. Currently, however, a sensor node could operate at only a very low level of functionality if it depended on strictly passive power sources.
For this reason, it seems likely that for many applications the nodes in an ad hoc network must use battery power or a similar active power source to function at an acceptable level. Because there is no convenient and efficient method for recharging these batteries, the lifetime of an ad hoc network is limited to the lifetime of the batteries powering the nodes in the network. Hence aggressive power management and power conservation are required to extend the lifetime of the ad hoc network (Bhardwaj, Garnett, and Chandrakasan, 2001). This leads to substantially different protocols for using these networks because power usage of the protocol becomes one of the fundamental constraints in the protocol design.
8.2.4 No centralized mechanisms
Since ad hoc networks do not have any underlying infrastructure and wireless communication is employed, centralized algorithms are not feasible. The cost of transmitting data from all the nodes in the network to a central location becomes prohibitively expensive in terms of power usage. In addition, there are the typical problems with scalability and fault tolerance because centralized algorithms suffer from being a single point for processing all the information. Therefore, centralized processing of large volumes of data or data from a large number of nodes is impractical in most cases. It is often more practical to perform some localized processing within the network, reducing the amount of data that must be delivered to the base station (Estrin et al., 1999). This approach saves on computation at the destination, as well as saving network energy that otherwise would be used for communicating large amounts of data rather than a small amount of data that must be transmitted. Although not practical for all applications, especially if the processing required to achieve data reduction exceeds the capabilities of the nodes, distributed processing is not only more scalable but also more energy efficient when it is feasible. An example of processing that cannot always be performed efficiently at the sensor nodes is complex signal or image processing (Zhao, Shin, and Reich, 2002), particularly when data from many sensors are required to perform the processing.
8.3 Unique Features of Sensor Networks
By necessity, protocol design depends on the expected uses of the underlying technology. In this section we discuss some of the unique properties of sensor networks that influence the protocol design for these devices.
8.3.1 Direct interaction with the physical world
Sensor nodes are designed to interact with the physical world and to perform computational tasks based on the information gathered from the surrounding environment (Estrin et al., 2001). In fact, these nodes are often referred to as smart sensor nodes because they combine both sensing functions with digital logic, which allows for some intelligent processing of the readings obtained from the on-chip sensor(s).
Because sensor nodes interact directly with their environment, these nodes include a mechanism for converting analog information derived from sensor measurements into digital values that are processed by an on-chip processor. Inputs to these nodes are the measurements the sensors make. Outputs are the data each sensor node transmits based on its readings. The ability of sensors to measure physical, chemical, biologic, and other types of properties of the environment provides novel opportunities for computing systems, as well as imposing unique requirements on the implementation of protocols.
For example, sensor nodes respond to their measurements in a variety of ways depending on the application requirements. At one extreme is the case where a sensor node responds only under extraordinary conditions, such as when a thermal sensor detects an extremely high temperature consistent with a fire. At the other extreme is the situation in which a photo sensor reports the ambient light on a regular basis. Because the region around each sensor is the source of the data, traffic patterns for communication involving sensor nodes are likely to differ from traffic patterns in typical computer networks.
8.3.2 Usually special-purpose devices
Sensor nodes are expected to be low-cost computing devices with a small form factor. Many different types of sensors have been developed, including thermal sensors, magnetic sensors, vibration sensors, chemical sensors, biologic sensors, light sensors, and acoustic sensors. The cost and complexity of providing many sensors on the same node may be too high. In addition, sensor nodes have limited memory and processing power. For all these reasons, it is expected that these nodes will be customized for a specific application rather than functioning as a general-purpose computational device. This allows sensor nodes to be optimized for a specific sensing task, thereby lowering the cost and increasing the range of applications that can employ sensors. Because it is assumed that sensors will be deployed widely, it may be cost-effective to design special implementations for many different categories of sensor applications. The memory in a sensor node makes it possible to install different programs, so a single sensor could be used for multiple applications. Although it is possible to update the software in a node even after it has been deployed (Qi, Xu, and Wang, 2003), the overhead of transmitting new code and installing it may limit the viability of this option. In addition, it is likely that a sensor network will be deployed with a specific mission in mind. Thus it makes little sense to change the functionality of these sensor nodes unless it is possible to reposition them.
For all these reasons, it seems likely that sensor networks will be used as special-purpose systems, where a single task is assigned to the sensors, and this task does not change significantly during the lifetime of the sensor network.
Of course, sensor nodes may be designed to process relatively generic requests, such as responding to events like an elevated temperature reading, where the temperature range of interest and the frequency of reporting events could be disseminated by a base station after deployment (Shen, Srisathapornphat, and Jaikaeo, 2001). However, it seems likely the processing of the requests will be predefined in the sensor node software.
8.3.3 Very limited resources
Wireless sensor nodes obviously have limited communication bandwidth because of the need to share the wireless medium among many sensor nodes. However, these nodes have other severe limitations because of the anticipated low cost of sensor nodes, along with the constraints mentioned previously. The limited available power is a special challenge for sensor nodes.
Power is one of the primary resources that are limited, which implies that communication costs need to be managed carefully. For example, sending a single kilobit packet a distance of 100 m requires as much power as 3 million computations on a 100 MIPs/W processor (Pottie and Kaiser, 2000). For this reason, it is desirable to perform as much local preprocessing of data as reasonably possible.
On the other hand, because of the need to maintain a low cost for these nodes, the memory and computation resources available locally on the sensor are very modest. As an example, consider the Mica 2 motes, a third generation of sensor nodes (the first being Rene motes), designed by the Smart Dust research group (Hill and Culler, 2002). A Mica 2 mote has a 4-MHz Atmel processor with 128 kB of SDRAM and 512 kB of programmable memory, which must contain the operating system and application code (Hill and Culler, 2002). Even though Moore’s law and related observations on general technology trend suggest that it will become cost-effective in the future to place more storage and computing capabilities on a smart sensor, the capabilities of sensor nodes will remain orders of magnitude less than the resources available to desktop computers. In fact, these nodes have substantially fewer resources than typical personal digital assistants (PDAs). Although preprocessing of sensor readings reduces the communication overhead, sophisticated processing of these readings is not feasible with existing hardware designs (Zhao, Shin, and Reich, 2002). These limited resources also restrict the complexity of the communication protocols that the sensors can support.
8.3.4 Operate without a human interface
Sensor nodes have a small form factor. One reason is to reduce the cost. Another reason for limiting the form factor is to increase the opportunities where the sensors can be placed. By making the sensors small and unobtrusive, more applications become viable. A third reason is that security may necessitate that these nodes be hidden or at least hard to find. Making the sensors small decreases the chances of detecting them.
Because sensor nodes are small, they have few, if any, peripherals. There are no input devices, such as a keyboard, mouse, or pen. In fact, the only item remotely constituting an input device may be an on/off switch. The only outputs that provide directly human-readable output are at most a few indicator lights and perhaps a speaker. Although these can be used in creative ways to simplify monitoring and diagnostics of the application, the data that can be obtained are minimal.
In general, users must interact with the sensor nodes through software. This means transmitting packets from the user to the sensor to initiate new actions on the part of the sensor and receiving packets from the sensor to determine sensor readings or to obtain diagnostic information from the sensors.
The lack of a human interface creates problems when deploying the sensors because there is no method for keying in application-specific information for each sensor as it is set up. Instead, self-organization among sensor nodes is required (Sohrabi et al., 2000). In fact, self-organization is desirable for all cases because of the need for scalability because manual deployment and configuration of a large sensor network consisting of thousands of nodes could prove to be prohibitively expensive. Redeployment of additional nodes to replace faulty or expired sensors also would become costly if manual reconfiguration is required.
8.3.5 Specialized routing patterns
Routing in the Internet is designed around the principle that any two hosts can communicate with each other. Sending an e-mail from one user to another is an example of such communication. In a wireless sensor network, on the other hand, routing has a much more predictable pattern. Other than messages exchanged among neighboring sensors, most of the traffic in the network is between a base station and a sensor node. In a hierarchically organized network, communication occurs primarily between nodes at adjacent levels of the hierarchy.
In addition, the communication generated by a wireless sensor network toward a base station consists of either periodic replies from all the sensors to a base station or event-driven replies from each sensor observing an event that matches the base station’s query. In Fig. 8.3a we see an event, represented by an explosion, with the surrounding sensors that detect the explosion forwarding these sensor readings to the base station. On the other hand, Fig. 8.3b depicts a periodic response from all the sensors to the base station. In both cases, the transmission of messages on a hop-by-hop basis from the sensors to the base station is depicted.
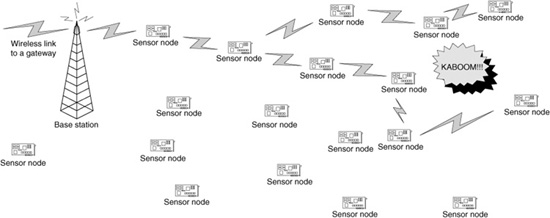
Figure 8.3 (a) Example of an event-driven sensor response.
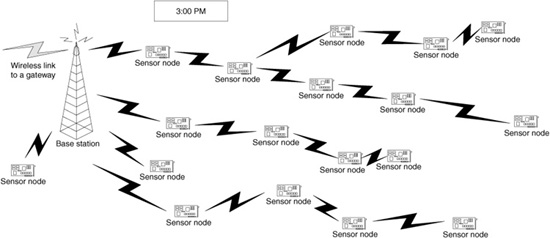
Figure 8.3 (b) Example of a periodic sensor response.
8.4 Proposed Applications
Wireless sensor networks have attracted a great deal of interest for many possible applications. In this section, we categorize many applications that have been proposed.
8.4.1 Military applications
Potential military applications are attractive for a number of reasons. First, the potential to save and protect soldiers in the battlefield is a noble goal. Second, sensor nodes can become an important component of existing systems for battlefield communications and monitoring. Third, the budget available for such networks is likely to be higher than for industrial and commercial applications. Finally, applications deployed in military scenarios often have similarities with applications in other domains, thereby leveraging the investment in research and development of wireless sensor networks for military objectives.
Several military applications have been identified. One is the tracking of enemy troop movements. This could be done in a scenario in which the location of enemy troops is known, and monitoring where they relocate is of value. Another scenario of interest is deploying a wireless sensor network in areas where no known enemy troops are located, but instead the sensor network detects the movement of troops into the area. Both tasks are similar to a scouting operation but without the potential for loss of human life (assuming that the sensor network performs correctly).
Another military application is the use of sensors to detect the use of biologic or chemical weapons. If the sensors detect the use of these weapons, the sensors could relay this information to commanders, allowing sufficient time for soldiers in the field to take defensive measures. Effective deployment of sensors for this purpose would discourage the use of these weapons because the element of surprise would be removed.
A third example of military applications that benefits from wireless sensor networks is improved battlefield communications. An instance would be an application where a soldier with a PDA has extended senses by interacting with a surrounding wireless sensor network (Ye et al., 2002). In essence, the soldier becomes “an army of one” with access to sensing resources that allow the soldier to extend his or her senses. Not only can a wireless sensor network provide updated and more precise information to central authorities, but the network also can serve to connect soldiers by functioning as multihop routers.
Military applications also impose special requirements on the wireless sensor network. First, as mentioned previously, the sensor network protocols should support autodeployment and self-organization. A common illustration of this point is the idea of deploying a sensor network by dropping a large number of sensors from an airplane. Second, each sensor node must be difficult to detect. If an adversary is able to determine the location of sensor nodes easily and compromise these nodes, the objectives of this network will be undermined. Finally, security is required to ensure that a compromised node is unable to inject invalid information into the network or steal information from the network that it would not be entitled to obtain. This is particularly challenging for sensor nodes. Since they have limited computation and communication costs, large keys and sophisticated security protocols may not be practical. It is also possible, however, that the security protocol may need to be sufficient only to prevent the cracking of keys for a short duration of time, corresponding to some small multiple of the expected lifetime of the network after deployment (Perrig et al., 2002; Ye et al., 2004).
8.4.2 Medical applications
Sensor nodes also are being envisioned as medical devices that could be implanted within or reside on the body and perform tasks currently done with additional cost or inconvenience (Schwiebert et al., 2001). A few examples include glucose monitors for diabetic patients (DirecNet, 2003), artificial retinal and cortical implants for the visually impaired (Schwiebert et al., 2001), heart monitors (Conway et al., 2000), and a vital statistics repository (Arnon et al., 2003). A glucose monitor could provide continual readings of insulin levels, reporting problems to the patient or giving readings at regularly scheduled times. A log could be kept that would report these fluctuations in readings at subsequent doctor’s office visits. In cases of extreme readings of glucose levels, emergency personnel could be notified directly. Similar to a glucose monitor, a heart monitor could be used to keep track of the functioning of the heart. This could replace the need for hospital stays to determine the causes of irregular heartbeats and also provide chronic heart monitoring for persons with coronary diseases or other heart-related problems. The vital statistics repository could take the form of a medical smart card that holds medical information on the user, similar to the tags that some people wear in case of medical emergencies but with the added advantages of having sensors that provide up-to-date medical information.
There is also great interest in developing sensors that could be implanted in the eye or on the visual cortex, the part of the brain that provides visual processing (Schwiebert et al., 2001). These sensors would be used to electronically transmit information to visually impaired persons. Because of the large quantity of information to be transmitted, as well as the need to avoid infection, wireless communication with these sensors is a better alternative to wired connections.
Persons with severe allergies to penicillin or other medications frequently carry medical tags that indicate the need for emergency medical personnel to avoid administering these drugs. By implanting a sensor that holds this information, the risk of the person forgetting to carry this notification or of accidents arising when the information is lost or unseen until it is too late is avoided. Vital statistics also could be stored on such a device, including blood pressure and other measurements, thereby keeping a running record of a person’s vital signs.
Sensors used for medical applications also have unique requirements. First, these sensors must be safe and biocompatible so that they continue to function inside the body and do not cause damage to the surrounding tissues. Owing to the risks of surgery, power must be provided to these sensors so that surgical replacement of sensors is not required on a regular basis simply because the node runs out of power. For similar reasons, the sensor node should be designed for long-term operation, which implies that a high level of fault tolerance and redundancy, along with graceful failure modes, must be incorporated into the design. The sensors also need to function correctly even in the presence of RF noise and interference from other wireless devices. Finally, patient confidentiality must be maintained so that unauthorized personnel cannot extract sensor readings from the sensors.
8.4.3 Industrial applications
The potential of wireless sensor networks has been recognized for industrial applications as well (http://www.zigbee.org/). Low-cost sensor nodes could be attached to equipment to monitor performance or attached to parts as they move through the shop floor. By tracking parts through the manufacturing plant, inefficiencies in plant process flow could be recognized more quickly, rush orders could be expedited more easily, and customer queries could be answered faster and with more accuracy. A similar application is the requirement that all suppliers for the Department of Defense place radio frequency ID (RFID) tags on all items (except bulk items such as gasoline and gravel). Similar interest has been expressed by Wal-Mart to require all its suppliers to place RFID tags on all merchandise. This would allow fast and accurate scanning of items at checkout, as well as inventory tracking. However, privacy concerns have been raised about RFID technology, especially the ability to track purchasers (McGinity, 2004). Quality assurance could be enhanced by tracking parts to ensure that necessary steps in the assembly process are not skipped, including quality assurance checks at various stages in the manufacturing process. A third example is the use of wireless sensors for inventory tracking. This potentially reduces both the time and cost of maintaining accurate inventory counts. It also simplifies the difficulty of finding misplaced items and can be used for employee and customer theft reduction.
To make these wireless sensor networks useful in commercial settings, the cost of individual sensors must be very low. The protocols in use also must be highly scalable. Both requirements are due to the large numbers of sensors required for such applications. Because of the varied conditions under which these sensors must operate, they also must tolerate interference.
8.4.4 Environmental applications
Because of the scope of the problems, wireless sensor networks also are being proposed and tested for environmental concerns. For example, tracking the nesting habits of seabirds requires monitoring a large geographic region without a human presence (Mainwaring et al., 2002). A large wireless sensor network could perform this task more thoroughly and accurately than is currently possible using only human observers. Another option is attaching the sensors directly to large mammals. This allows the monitoring of their behavior and over a large area. The sensors can exchange information when two animals are near each other, so that the researchers can obtain readings from more animals over time. Two sensor applications that have taken this approach are the SWIM project for monitoring whales (Small and Haas, 2003) and the ZebraNet project for monitoring Zebras (Juang et al., 2002). Another example is monitoring river currents (Steere et al., 2000). The flow of currents in a river depends in part on the quantities and temperatures of water flowing from and into different tributaries. Positioning sensor nodes throughout a river can give the detail of resolution required to answer certain questions about the river currents and the flow and mixture of waters from different sources. Water quality monitoring in general may be useful for determining when streams and beaches are contaminated with bacteria or other harmful pollutants. This could be used not only for human safety but also to track polluters of the waterways.
As a final example, consider the need to detect fires in the national forests or other large forests. A wireless sensor network in a large-scale distribution could be used for giving early warnings of fire outbreaks. This leads to improved response times, preventing the death and destruction of people, animals, and plants. One special requirement of environmental sensors is the need for rugged operation in hostile surroundings. Because of the remote locations where these sensors may be placed, as well as the large number of sensors that may be required, they need to operate on a long-term basis, which implies that there will be only intermittent connectivity. Individual sensor nodes may need to sleep for extended periods of time to maximize the lifetime of the network (Chen et al., 2001). This suggests that the protocols must be designed to work even when many of the sensor nodes are not responsive.
8.4.5 Other application domains
This list of example applications for wireless sensor networks is far from complete. In subsequent chapters we will see additional applications as we present various protocols for ad hoc and sensor networks. As you read these chapters, other potential applications may occur to you as well.
8.5 References
Akyildiz, I. F., W. Su, Y. Sankarasubramaniam, and E. Cayirci, “Wireless Sensor Networks: A Survey,” Computer Networks 38(4):393, 2002.
Arnon, S., D. Bhastekar, D. Kedar, and A. Tauber, “A Comparative Study of Wireless Communication Network Configurations for Medical Applications,” IEEE Wireless Communications 10(1):56, 2003.
Bhardwaj, M., T. Garnett, and A. Chandrakasan, “Upper Bounds on the Lifetime of Sensor Networks,” in IEEE International Conference on Communications, Vol. 3. Helsinki, Finland, IEEE Press, 2001, p. 785.
Chen, B., K. Jamieson, H. Balakrishnan, and R. Morris, “Span: An Energy Efficient Coordination Algorithm for Topology Maintenance in Ad Hoc Wireless Networks,” in International Conference on Mobile Computing and Networking, Rome, Italy, ACM, 2001, p. 221.
Conway, J., C. Coelho, D. da Silva, A. Fernandes, L. Andrade, and H. Carvalho, “Wearable Computer as a Multiparametric Monitor for Physiological Signals,” in Proceedings of the IEEE International Symposium on Bio-Informatics and Biomedical Engineering, Arlington, VA, IEEE Press, 2000, p. 236.
DirecNet (The Diabetes Research in Children Network) Study Group, “The Accuracy of the CGMS™ in Children with Type 1 Diabetes: Results of the Diabetes Research in Children Network (DirecNet) Accuracy Study,” Diabetes Technology and Therapeutics 5(5):781, 2003.
Doherty, L., B. A. Warneke, B. E. Boser, and K. S. J. Pister, “Energy and Performance Considerations for Smart Dust,” International Journal of Parallel Distributed Systems and Networks 4(3):121, 2001.
Estrin, D., L. Girod, G. Pottie, and M. Srivastava, “Instrumenting the World with Sensor Networks,” in International Conference on Acoustics, Speech, and Signal Processing. 2001, p. 2033.
Estrin, D., R. Govindan, J. Heidemann, and S. Kumar, “Next Generation Challenges: Scalable Coordination in Sensor Networks,” in International Conference on Mobile Computing and Networking (MobiCOM). Seattle, Washington, ACM, 1999, p. 263.
Hill, J. L., and D. E. Culler, “Mica: A Wireless Platform for Deeply Embedded Networks,” IEEE Micro. 2(6):12, 2002.
Hong, X., M. Gerla, H. Wang, and L. Clare, “Load Balanced, Energy-Aware Communications for Mars Sensor Networks,” in Proceedings of the IEEE Aerospace Conference, Vol. 3. 2002, p. 1109.
Juang, P., H. Oki, Y. Wang, M. Martonosi, L. Peh, and D. Rubenstein, “Energy Efficient Computing for Wildlife Tracking: Design Trade-offs and Early Experiences with ZebraNet,” in Architectural Support for Programming Languages and Operating Systems (ASPLOS). San Jose, CA, ACM, 2002, p. 96.
Mainwaring, A., J. Polastre, R. Szewczyk, D. Culler, and J. Anderson, “Wireless Sensor Networks for Habitat Monitoring,” in ACM International Workshop on Wireless Sensor Networks and Applications. Atlanta, GA, ACM, 2002, p. 88.
McGinity, M., “RFID: Is This Game of Tag Fair Play?” Communications of the ACM 47(1):15, 2004.
Perkins, C. E., Ad Hoc Networking. Reading, MA, Addison-Wesley, 2000.
Perrig, A., R. Szewczyk, J. D. Tygar, V. Wen, and D. Culler, “SPINS: Security Protocols for Sensor Networks,” Wireless Networks 8(5):521, 2002.
Pottie, G. J., and W. J. Kaiser, “Wireless Integrated Network Sensors,” Communications of the ACM 43(5):51, 2000.
Qi, H., Y. Xu, and X. Wang, “Mobile-Agent-Based Collaborative Signal and Information Processing in Sensor Networks,” Proceedings of the IEEE 91(8):1172, 2003.
Roundy, S., P. K. Wright, and J. Rabaey, “A Study of Low Level Vibrations as a Power Source for Wireless Sensor Nodes,” Computer Communications 26(11):1131, 2003.
Schwiebert, L., S. K. S. Gupta, J. Weinmann, et al., “Research Challenges in Wireless Networks of Biomedical Sensors,” in International Conference on Mobile Computing and Networking (MobiCOM). Rome, Italy, ACM, 2001, p. 151.
Shen, S., C. Srisathapornphat, and C. Jaikaeo, “Sensor Information Networking Architecture and Applications,” IEEE Personal Communications 8(4):52, 2001.
Shenck, N. S., and J. A. Paradiso, “Energy Scavenging with Shoe-Mounted Piezoelectrics,” IEEE Micro. 21(3):30, 2001.
Small T., and Z. J. Haas, “The Shared Wireless Infostation Model - A New Ad Hoc Networking Paradigm (or Where there is a Whale, there is a Way),” in International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc). Annapolis, Maryland, ACM, 2003, p. 233.
Sohrabi, K., J. Gao, V. Ailawadhi, and G. Pottie, “Protocols for Self-Organization of a Wireless Sensor Network,” IEEE Personal Communications 7(5):16, 2000.
Steere, D. C., A. Baptista, D. McNamee, C. Pu, and J. Walpole, “Research Challenges in Environmental Observation and Forecasting Systems,” in International Conference on Mobile Computing and Networking (MobiCOM). 2000, p. 292.
Welsh, M., D. Myung, M. Gaynor, and S. Moulton, “Resuscitation Monitoring with a Wireless Sensor Network. American Heart Association, Resuscitation Science Symposium,” Circulation, Vol. 108, Supplement IV (abstract). Orlando, FL, American Heart Association, 2003, p. 1037. Ye, F., H. Luo, J. Cheng, S. Lu, and L. Zhang, “A Two-Tier Data Dissemination Model for Large-Scale Wireless Sensor Networks,” in International Conference on Mobile Computing and Networking (MobiCOM). Atlanta, GA, ACM, 2002, p. 148. Ye, F., H. Luo, S. Lu, and L. Zhang, “Statistical En-Route Detection and Filtering of Injected False Data in Sensor Networks,” in Proceedings of the 23rd International Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM). Hong Kong, IEEE Press, 2004.
Zhao, F., J. Shin, and J. Reich, “Information-Driven Dynamic Sensor Collaboration,” IEEE Signal Processing Magazine 19(2):61, 2002.
