Chapter 5: Identifying and Profiling Threat Actors
Identifying the potential kind of threat actor behind a cyberattack is one of the most important things you need to pay attention to when responding to a cybersecurity incident, and you can achieve this by analyzing in detail the characteristics and context of the attack.
Knowing in advance the different attackers' profiles and their intentions behind an attack is a big help because you can anticipate their moves, and it is also helpful in developing strategies to respond to and contain these attacks efficiently.
Knowledge of adversaries is very important in incident response; when you have information about them, including their profile, capabilities, techniques, and tools, you can use it as intelligence that can be actionable in multiple ways.
In this chapter, we will study the different types of threat actors, and we will learn how to profile them based on their behavior, motivations, and mode of operation. This information will be useful when we get evidence and want to consult our intelligence base to identify potential adversaries behind an attack.
In this chapter, you will cover the following topics:
- Exploring the different types of threat actors
- Researching adversaries and threat actors
- Creating threat actor and campaign profiles
Technical requirements
In case you haven't already done, you need to download and install VMware Workstation Player from this link https://www.vmware.com/products/workstation-player/workstation-player-evaluation.html.
You'll also need to download from the book's official GitHub repository https://github.com/PacktPublishing/Incident-Response-with-Threat-Intelligence the following:
- Virtual machine:
- IR-Laptop
Exploring the different types of threat actors
There are specific categories of threat actors, and their characteristics and motivations mainly define these categories. Different attackers can pose a risk to the organization at particular times. Therefore, according to the circumstances, it is imperative to know their categories and interests. Let's look at the main types of threat actors.
Hacktivists
The term hacktivism is a portmanteau of the words hacker and activism. These actors are related to movements that look to get attention using digital tools in a non-violent way for their ideological interests.
The motivations behind hacktivism are more related to social struggles, the search for justice, defiance of political and economic powers, and even in some cases with a certain sense of the search for anarchy, but rarely with malicious intentions.
What makes these groups dangerous is that they can sometimes be infiltrated or manipulated by people or groups outside the causes that undermine the movement's actual goals.
There is also the possibility that these groups are too heterogeneous with different views and objectives, causing some participants to act independently by applying their own agendas.
The roots of hacktivism date back to the 1980s–1990s when the internet emerged, with devices interconnected through a global network.
The potential risk of this type of threat is that it can occur at any time, due to a geopolitical or socio-economic event, or even simply by having a relationship or link with a targeted third party. Another important aspect is that it is difficult to associate the specific capabilities of these groups beyond their characteristics; they can only be people or groups that want to send a message or state actors with high skills and sufficient economic and technological resources.
Script kiddies
Script kiddies are a particular category within groups that can pose a threat to organizations. Unlike hacktivists, they do not have a clear motivation; sometimes, they will do it for money, for fun, to compete with their peers, or to gain recognition and notoriety within their circles.
They have basic technical skills and often learn how to use tools without fully knowing how they work; this would be the equivalent of having a weapon and not knowing how to use it, with the risks that this poses.
Usually, they prefer to work individually rather than collectively and pose a risk to organizations precisely because they can turn an organization into a target incidentally and provoke a more significant impact unexpectedly, making them a potentially dangerous threat.
In 2015, a 15-year-old script kiddie was arrested in the UK for unauthorized access to systems and theft of information from a telecommunications company called TalkTalk Telecom Group Limited. The teenager managed to access the systems through a SQL Injection (SQLI) attack. It is no secret that many websites share cheat sheets, instructions, or even tools that automate SQL injection, and some people abuse these tools for unethical or non-professional purposes.
Script kiddies are dangerous because, most of the time, they do not have a specific, defined goal and lack the technical knowledge or skills with the tools they use, so they can turn any organization into an involuntary target.
Insiders
This group of adversaries represents one of the greatest threats to organizations because it involves employees, collaborators, or business partners who regularly have access to the physical facilities of corporate systems.
The problem is that they have the privileges and permissions necessary to carry out different activities. Therefore, they often go unnoticed, so their malicious actions are not detected in time, as it is all based on trust.
Sometimes, these threat actors act on their own, and their motivations may be the theft of confidential information for their benefit to use or sell, or sabotage for a personal vendetta.
Another significant risk may occur when the company's internal staff is threatened or extorted by third parties who force them to perform malicious activities, which may include the actions described previously or the installation of malicious code that implants a backdoor or rootkit.
Insiders can be divided into three categories – malicious, accidental, or negligent – and are classified according to their motivations and behaviors, as described in the following diagram:

Figure 5.1 – The categories of insiders
In August 2020, Egor Igorevich Kriuchkov, a 27-year-old Russian citizen and a member of a criminal group, contacted an employee of Tesla, the car manufacturer, asking them to install a ransomware program on the company's devices in exchange for a significant sum of money.
Fortunately for the company, the employee decided to report the incident, and they, in turn, reported it to the authorities. After agreeing to cooperate with the Federal Bureau of Investigation (FBI), they managed to arrest Kriuchkov.
If this attempt had succeeded and information had leaked, the disruption of Tesla's operations would have resulted in the company losing millions, affecting its reputation; this demonstrates the potential risk and threat of insiders.
Cybercriminals
Cybercrime could not survive without the ecosystem that supports it. This ecosystem has allowed the interconnection of various actors and components that depend on and correlate with each other, with related interests, which guarantees their survival.
Cybercriminals use technology and financial resources to break into organizations' information systems or against ordinary users illegally to get profits. They organize into groups that sometimes focus only on technology-related activities and are sometimes part of organized crime groups that decide to expand their cyber-field of action to increase their profits.
A characteristic of these groups is that they often recruit members with high technical skills and pay them considerable amounts of money to keep them motivated. The money they get from their illegal activities is what also allows them to maintain technological infrastructures.
The types of cybercrime activities relate to, among other things, identity theft, email and internet fraud, cyber extortion, banking fraud, theft of financial data, and the robbery and sale of corporate information and industrial secrets. Cybercrime threat actors use different techniques and tools where the main element is social engineering, such as phishing and malware.
They even extend their cheating techniques to a third party – for example, there is an attack called SIM swapping. This consists of tricking the operators of a mobile company into reactivating a cell line on attacker's own devices, thus having access to the information of their victims and their Two-Factor Authentication (2FA) mechanisms that use SMS messages.
The main motivation of cybercriminals is obviously financial, and their main targets are users with little knowledge of the risks to which they are exposed when using technology, as well as any company or organization that they can take money from. With a very robust and mature ecosystem, it is a growing threat.
Ransomware gangs
Without a doubt, ransomware has become one of the biggest threats today to individuals and businesses worldwide. Moreover, this extortion-based activity is one of the most lucrative for cybercriminal groups, which make millions of dollars with every successful operation.
Behind these groups, there are people with skills and knowledge in different areas who plan their campaigns in detail and carefully choose their potential targets, as described in the findings of the security company Kaspersky, shown in the following diagram:
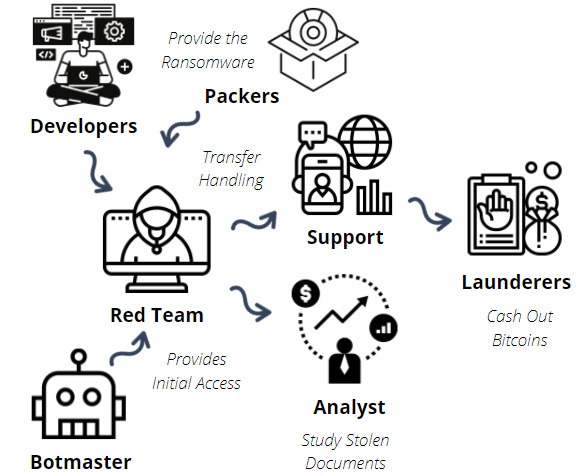
Figure 5.2 – The ransomware group's structure (source – Securelist)
Their victims are companies, such as hospitals, schools, governments, financial institutions, and energy companies. In addition, they now must deal with the theft of information, which cybercriminals use as an additional form of extortion or to make greater profits by selling it to the highest bidder.
Return on investment and million-dollar profits have caused these groups to consolidate and new groups to appear. The business is extensive and works through different operational models, such as ransomware as a service or affiliate programs, where ecosystems facilitate the distribution of profits among groups that play different roles.
According to estimates from different studies, more than half of companies pay the requested ransom to retrieve their information or resume their business operations.
In December 2020, at the Remote Chaos Communication Congress (RC3), a research team presented an exciting study. In their investigation, they analyzed cybercriminal campaigns, following the footprints they left in cryptocurrency transactions.
One of the most important findings was that, over 2 years, 19,750 victims transferred about $16 million to a small number of traders, concentrating almost 90% on only two of the most active ransomware families at the time, Locky and Cerber.
According to DarkTracer, there was leaked information from more than 2,000 companies on the dark web in April 2021. However, just 30 ransomware cybercriminal groups controlled those operations, as shown in the following screenshot:
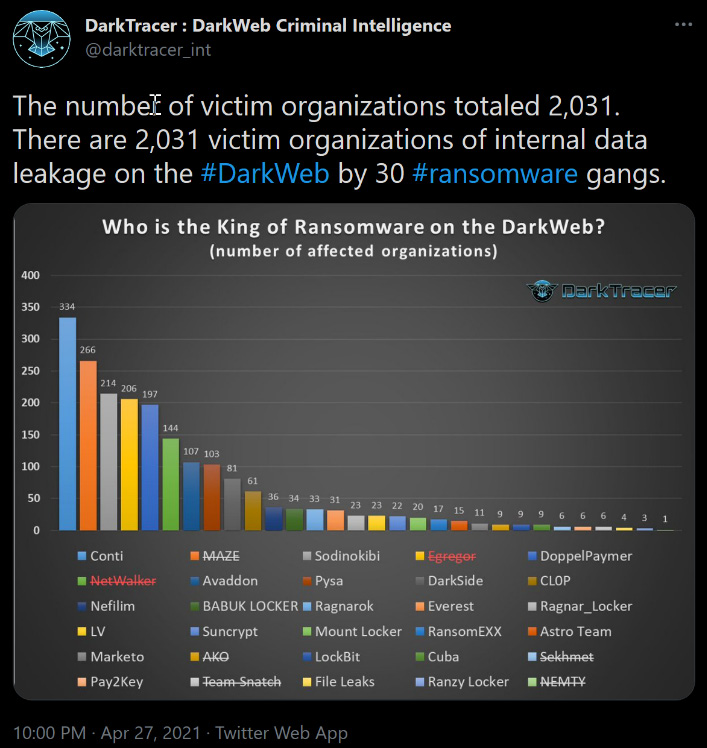
Figure 5.3 – The affected organizations and ransomware gangs
This growth in ransomware-related threats and the evolution in attackers' techniques and procedures make responding to these incidents successfully a challenge. The early identification of attacks and the ability to contain a threat are essential to reduce the impact on an organization.
Threat actors behind ransomware attacks must be considered high-risk for any organization, and it is essential to know their capabilities, modes of operation, and the tactics and techniques they use before the ransomware is deployed.
Advanced Persistent Threats (APT) groups
It is more common within targeted attack groups to find threat actors who have enough resources and skills to direct those attacks toward very high-profile targets, such as diplomats, politicians, governments, financial institutions, and security and energy companies.
Regularly, their attacks are more elaborate and tend to be harder to detect, usually being successful. Thus, the challenge in addressing such threats is to develop the capacity for early identification and detection capabilities to improve the effectiveness of an incident response of this type.
One feature that defines an attack as advanced is that it has components that require careful planning and execution. To achieve this, threat actors go through a phase of gathering detailed information about their targets to identify potential attack surfaces and weaknesses; otherwise, these attacks might not be as successful.
Sometimes, these groups develop sophisticated malicious code that exploits zero-day vulnerabilities, which is challenging to detect. Furthermore, these groups also use open source programs created by third parties, which reduces the time and the cost of an operation.
Persistence is undoubtedly an essential component in this category of attacks. A cyberattack can hardly succeed in the short term because each company's environment and infrastructure are complex and different, so attackers must know and adapt their attack strategy.
Even if they have managed to gather sufficient information from their targets' infrastructure, they may encounter elements that require adapting their strategies and selecting which tools to use.
No company should be considered exempt from becoming a target of these threat actors, as we have seen APT attacks on organizations of any size, from family businesses to large corporate companies, including governments.
Cyber-mercenaries
Cyber-mercenaries are individuals or groups of malicious actors who offer their services to perform specific actions. These threat actors act under contract from a third party that pays them to achieve a goal, and they rarely have any direct motivation related to their victim.
Some of these threat actors offer their services openly in darknet markets, while others handle lower profiles, and their customers must contact them through very closed channels.
The way these groups operate is known as hit and run – that is, persistence is less important because instead of maintaining the compromise of their victims for a long time, once they achieve what they are looking for, they end the operation.
In 2011, my colleagues on Kaspersky's Global Research and Analysis Team (GreAT) opened an investigation into a malicious actor called Icefog, also known as Dagger Panda according to CrowdStrike.
Icefog/Dagger Panda is a small group of attackers whose objective was to compromise supply chains related to government institutions, the defense sector, telecommunications, and high technologies in South Korea and Japan.
As in any other field, a mercenary is a high potential risk mainly because they have different capacities, a clear monetary interest, and no direct link to their targets, so they have little to lose.
As you can see, threat actors have different interests and can pose different levels of risk to an organization. This is why it is essential to know them with a mindset of developing better defense capabilities and responding to an incident; the more you know the adversaries, the greater the chance you have of understanding how to follow the investigation of a case.
Researching adversaries and threat actors
It would be challenging to know who the actor is behind an attack in the first security incident. However, the more you know about different adversaries, the more information you will have to assess the incident and decide how best to act when considering the characteristics of a security breach.
Fortunately, there is a lot of threat intelligence information about different malicious campaigns and the threat actors behind them. Some security companies have documented details behind high-profile cyberattacks and the groups related to these attacks. You can consult this information on sites such as MITRE ATT&CK (https://attack.mitre.org/groups/), Kaspersky (https://apt.securelist.com/), and Mandiant (https://www.mandiant.com/resources/apt-groups), among others.
However, sometimes, it is handy to create your own intelligence documentation with specific threat actors' profiles. The key elements to consider when profiling threat actors and their capabilities are as follows:
- The name of the threat actor
- A suspicious origin
- The category or type
- Victimology and target countries
- Campaigns related to this actor
- Associated Tactics, Techniques, and Procedures (TTPs)
- The malware used
Integrating this information will help us to create intelligence, correlate actors with campaigns and malware or the tools used by them, join the dots, and have access to a fuller context when responding to an incident.
STIX and TAXII standards
STIX and TAXII are two open source standards developed to create and share cyberthreat intelligence information. In this chapter, we will focus specifically on Structured Threat Information eXpression (STIX). Alternatively, Trusted Automated eXchange of Intelligence Information (TAXII) defines the standard and protocols needed to carry out the transport and exchange of intelligence information. According to its official website, STIX is a standardized language created by MITRE and the OASIS committee for cyberthreat intelligence to describe threat information.
STIX version 2.1 defines 18 objects known as STIX Domain Objects (SDOs) and 2 STIX Relationship Objects (SROs), described here: https://oasis-open.github.io/cti-documentation/stix/intro. An example of how they integrate is shown in the following diagram:

Figure 5.4 – A STIX threat description example
The basic structure of an object represented in JSON is shown in the following screenshot:
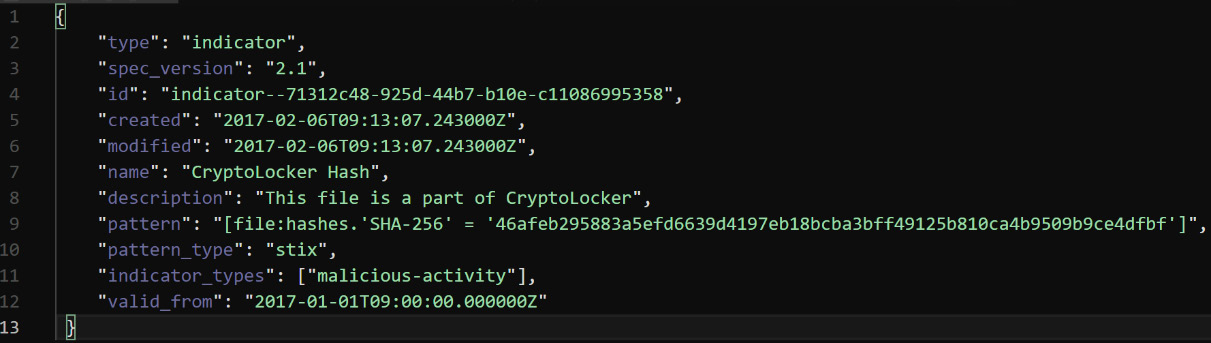
Figure 5.5 – An example of the JSON representation of a STIX object
You can interconnect different objects through "relationships" to establish a context that describes threats, considering their abilities, motivations, and capacities.
Working with STIX objects
You can work with STIX JSON files using several tools, including Microsoft Visual Studio Code, Sublime, and Atom, in a very simple way. In the following screenshot, you can see the structure of a STIX bundle object:
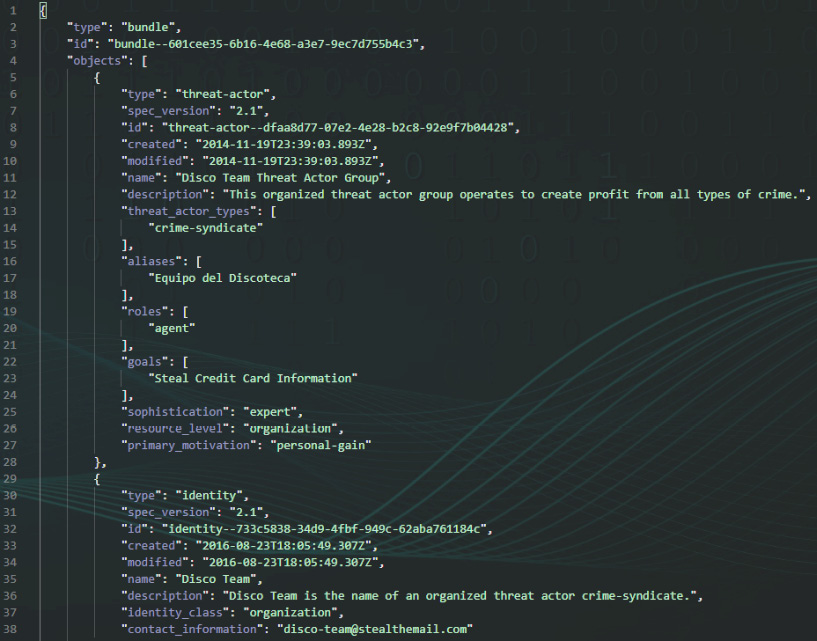
Figure 5.6 – The structure of a STIX object in JSON format
For the visualization of STIX JSON files, you can use the STIX Visualizer tool, https://oasis-open.github.io/cti-stix-visualization/; you just need to upload a file or copy and paste the code directly, and you will see the graphic representation of this code, as shown in the following screenshot:
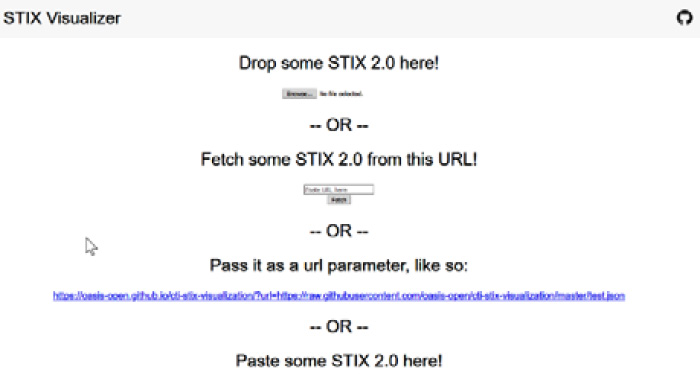
Figure 5.7 – The STIX Visualizer tool
Once you provide the information, a graph will show the relationship between the different objects; thus, you will get a clearer idea about the threat, as shown in the following diagram:
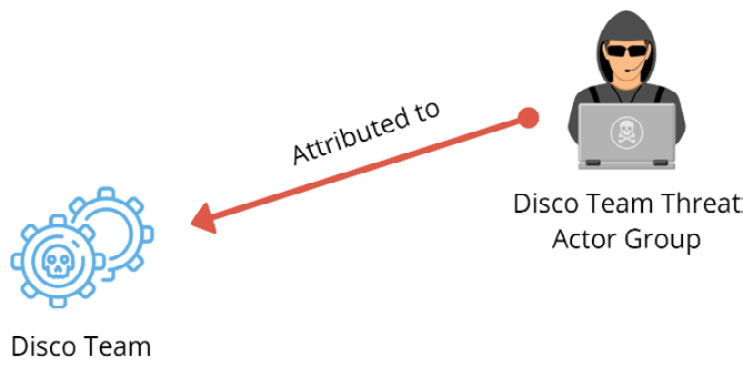
Figure 5.8 – The visualization of STIX objects and relations
In the next section, you will learn how to create profiles of threat actors and malicious campaigns.
Creating threat actor and campaign profiles
Usually, Threat Intelligence Platforms (TIPs) have a section with the profiles of different threat actors, their characteristics, the campaigns attributed to them, and their main TTPs.
If you do not have access to a TIP, you can still consult the information about threat actor profiles and their malicious campaigns from public sources such as MITRE ATT&CK (https://attack.mitre.org/groups/), AT&T OTX (https://otx.alienvault.com/browse/global/adversaries), or this compilation created by industry colleagues: https://apt.threattracking.com.
However, these information sources cover only threat actors with a specific visibility level due to the nature of their attacks or the relevance of their targets. So, there will be many others that do not appear there, but they threaten organizations nonetheless.
Sometimes, organizations should create their own internal threat actor profiles and campaigns from their incident response teams or other organizations. In practice, this is within the remit of the threat intelligence area, but it is beneficial to familiarize yourself with this process.
In the following section, you will learn how to create threat actors' profiles from intelligence collected from a fictitious company's incident response team.
Creating threat actors' profiles using Visual Studio Code
If you have used Microsoft Visual Studio Code (VS Code) (https://code.visualstudio.com/) previously for software development, you might not have imagined that it can be a practical tool to create threat actor profiles.
The security company Red Canary did an extraordinary job developing an open source extension for VSCode called VSCode ATT&CK. This extension allows you to research and directly add MITRE ATT&CK TTPs from VSCode.
Let's learn how to create threat actor profiles using this extension:
- On the IR-Laptop virtual machine, open VS Code, clicking on the control panel icon, as shown in the following screenshot:
Figure 5.9 – Opening VS Code
- Once VS Code is open, click on the extensions icon.
- In the Search Extensions in Marketplace text box, type ATT&CK.
- On the VSCode ATT&CK extension, press the Install button, as shown in the following screenshot:
Figure 5.10 – Installing the VSCode ATT&CK extension
Now, we need to add another extension to export our reports in different formats.
- As we did in the previous step, in the search textbox, type Yzane Markdown PDF, and then click on the Install button, as shown in the following screenshot:
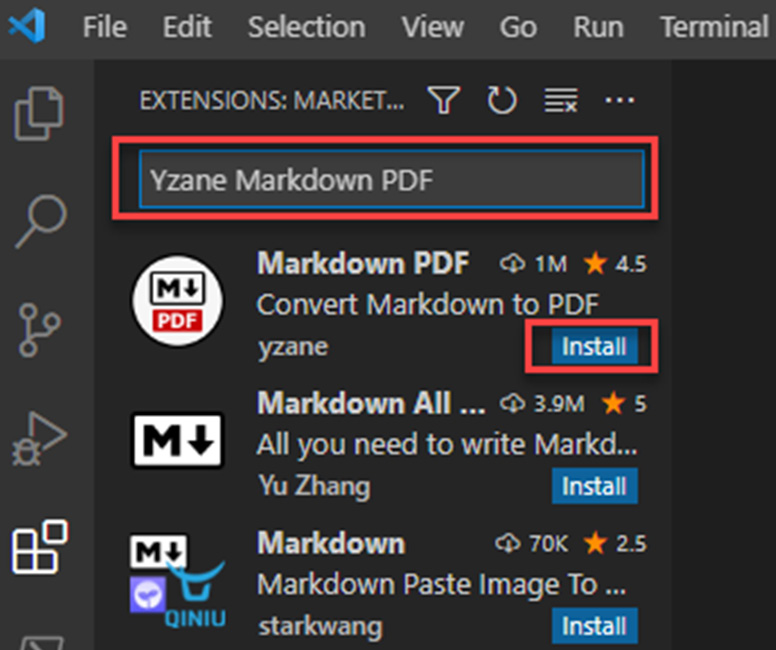
Figure 5.11 – Installing the Yzane Markdown PDF extension
You are ready to start creating threat profile reports using VS Code. We will use the Markdown format (.md) as the default format, since the VSCode ATT&ACK extension recognizes this format, to map the MITRE ATT&CK TTPs (we will learn more about MITRE ATT&CK in the following chapters).
To create the threat actor's profile, we are going to use a fictitious security incident:
- In VS Code, open the File menu and select New File.
- Save the new file in the C:UsersInvestigatorWorkspaceLabsChapter-5 directory as TA-INT0012_OctopusBlack.md, as shown in the following screenshot:
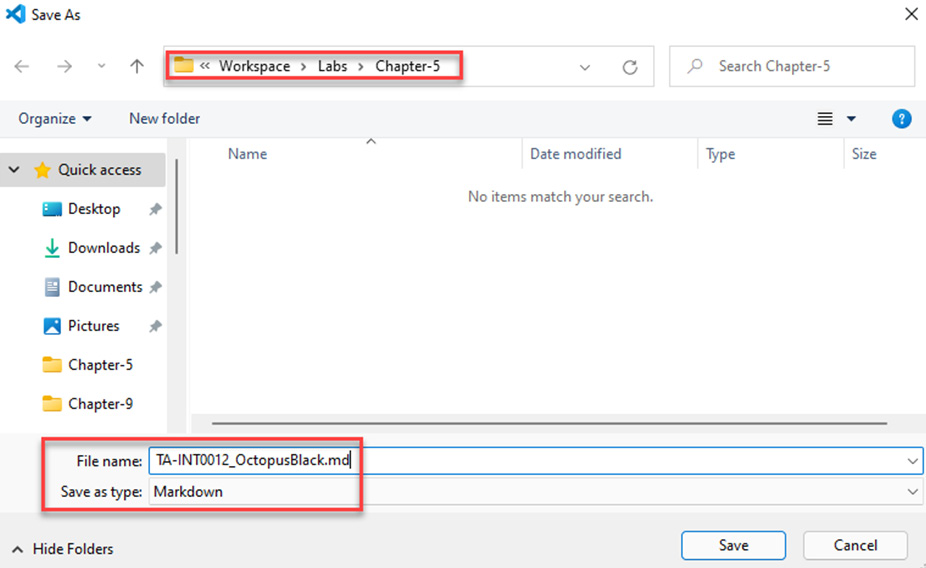
Figure 5.12 – Creating the threat actor's profile file
At the bottom of VS Code, you will see how the VSCode ATT&ACK extension recognizes the Markdown format, and the first time the Yzane Markdown PDF extension is used, it will create a Chromium plugin, as shown in the following screenshot:
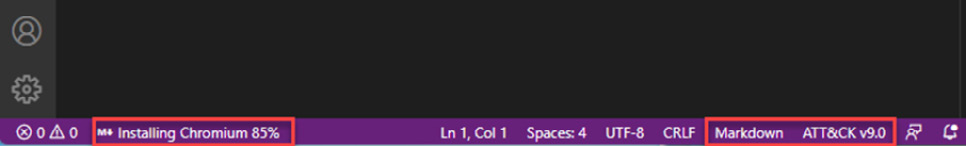
Figure 5.13 – The Markdown PDF Chromium plugin installation and loading VSCode ATT&CK
Important Note
In case you are not familiar with the Markdown language format, you can learn more here: https://www.markdowntutorial.com/.
- To enable and test dynamic previews, do the following:
- Write the following text in the VS Code editor: # This is a title
- Press Ctrl + K, release the keys, and then press V.
You will see the Editor and the Preview panels alongside each other, as shown in the following screenshot:
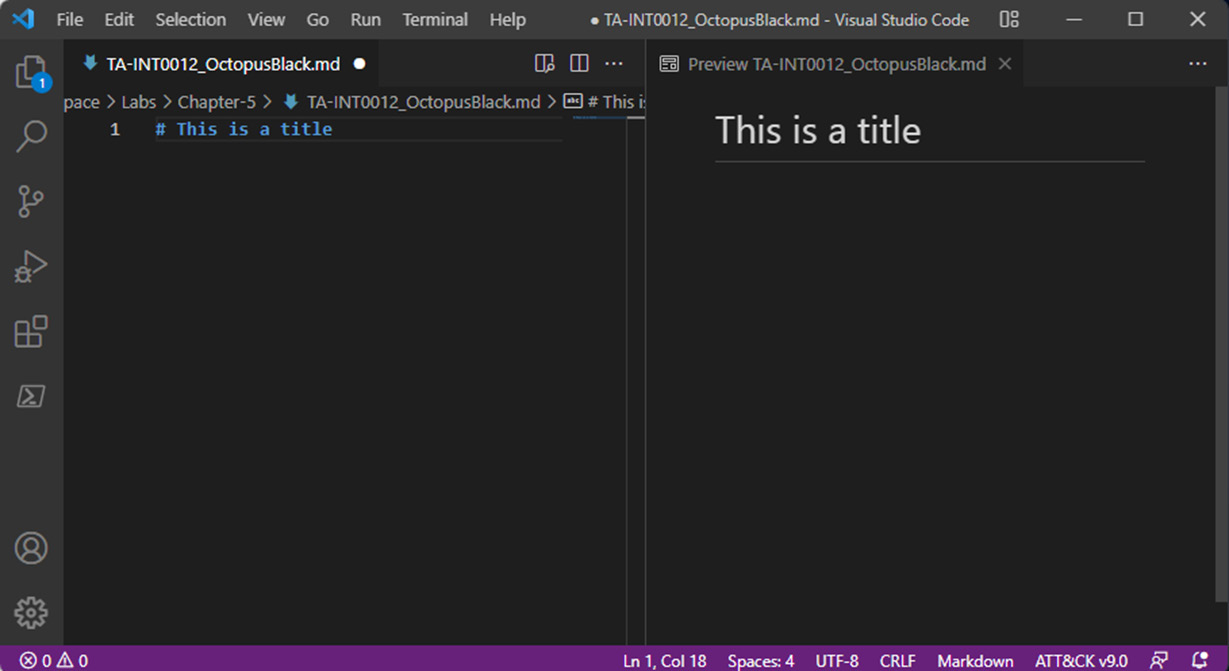
Figure 5.14 – Activating the Preview panel
- Write the following text in the VS Code editor:
# OctopusBlack
## Threat Actor profile
#### **#ID: TA_Int-I0012**
OctopusBlack is a financially motivated Threat Group that operates mainly in *Latin America*.
OctopusBlack group has been active since at least **2020** and was responsible for attacks on **small and medium-sized companies**.
The malware used by this group is related to similar attacks on multiple countries from *Latin America*.
## Associated Group Descriptions
| Name | Description |
|----------|---------------------------------------------|
|Deathfish | Related to similar attacks in South America |
You should see results similar to what is shown in the following screenshot:
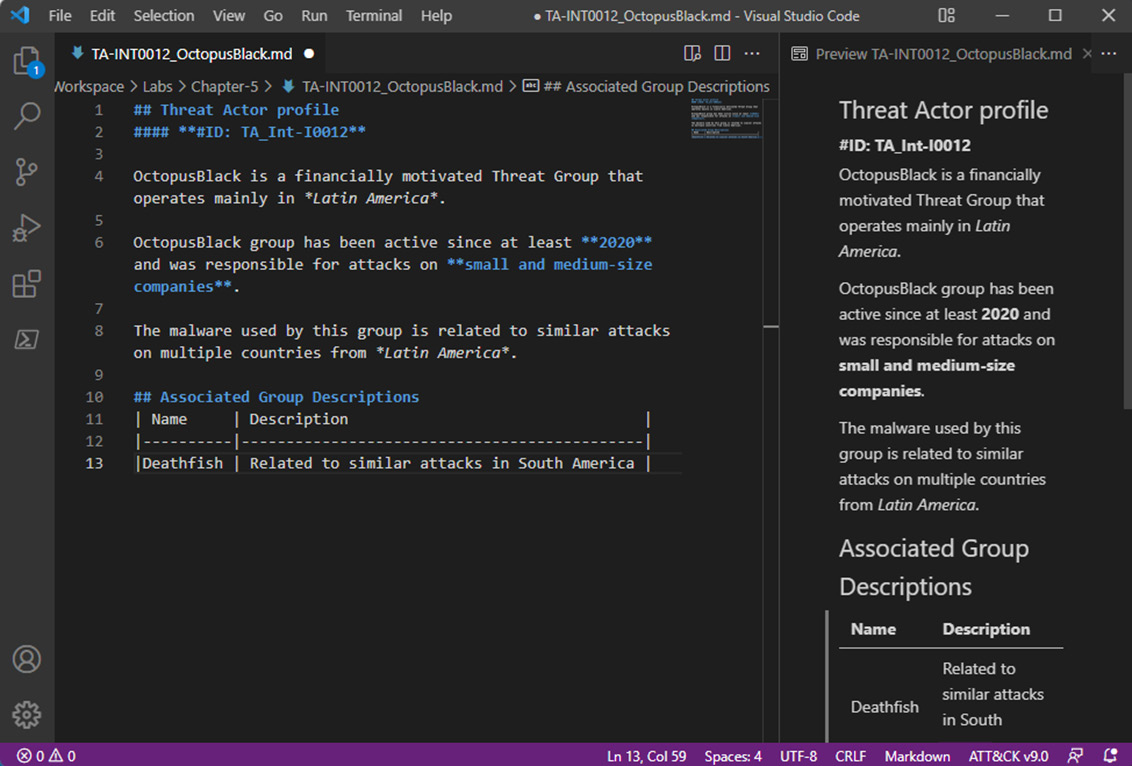
Figure 5.15 – Editing the threat actor's profile report
- Save the changes using Ctrl + S.
- To export the report to multiple formats, use the Ctrl + Shift + P shortcut, and then search for and select the Markdown PDF: Export (all: pdf, html, png, jpeg) option from the list, as shown in the following screenshot:
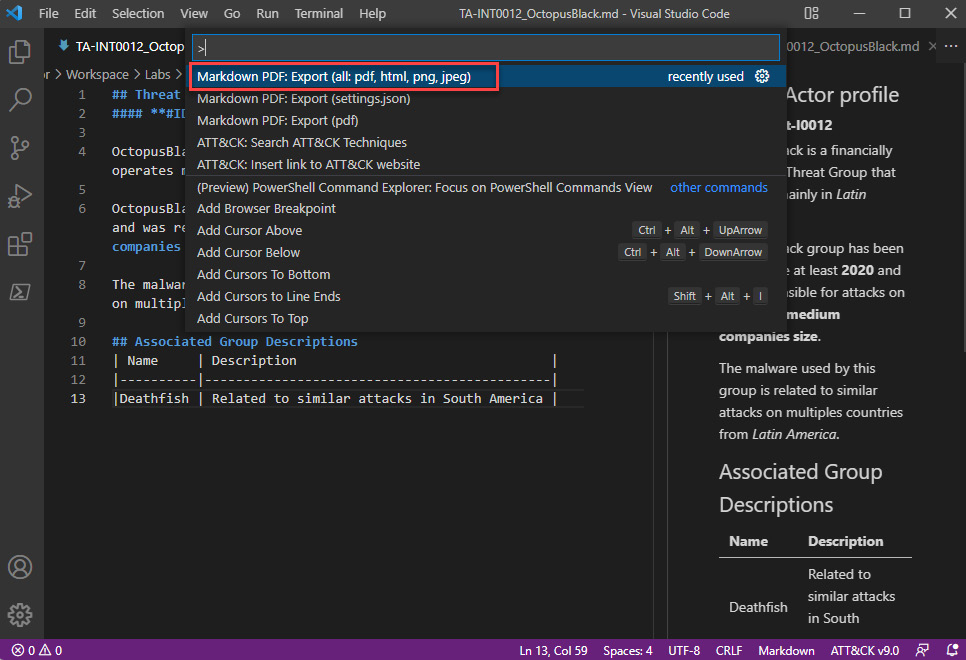
Figure 5.16 – Exporting the report to multiple formats
- On Windows Explorer, navigate to the C:UsersInvestigatorWorkspaceLabsChapter-5 directory, and you will see the report created in multiple formats, as shown in the following screenshot:
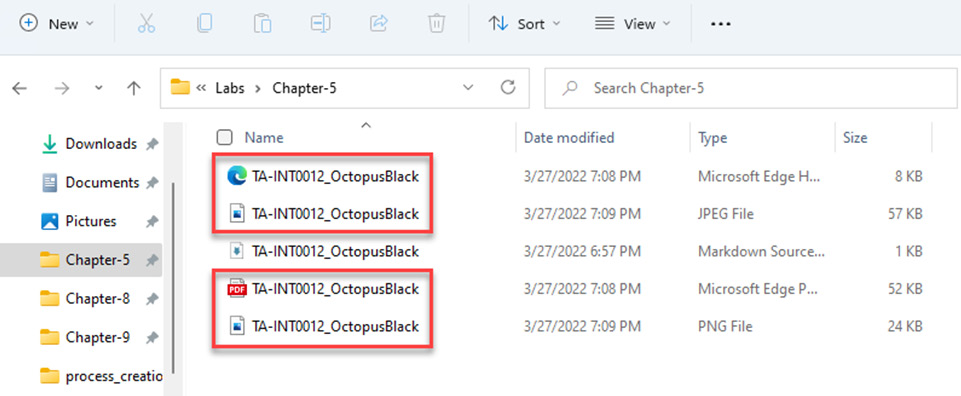
Figure 5.17 – Opening the threat actor's profile in multiple formats
- Open the report in every format to compare the different files.
The best option is to create threat actor profiles on a centralized TIP such as the Malware Information Sharing Platform (MISP) (https://www.misp-project.org/) where the information can be consulted and managed more efficiently.
But VS Code is also a great tool and an alternative way to create threat actor profiles, since the VSCode ATT&CK extension has complete integration with the MITRE ATT&CK framework.
An incident response professional must have as much information as possible about threat actors on hand at the time of a security breach, and these tools and frameworks are useful to help them act more efficiently and accurately.
Summary
In this chapter, you learned about the different categories of threat actors and the importance of knowing your adversaries and their capacities to have a better level of contextual understanding when responding to an incident.
You learned how to analyze threat profiles from different sources and the basic concepts of the STIX and TAXII standards.
You also learned how to start documenting a threat actor's profile report using VS Code, the Markup language, and the VSCode ATT&CK extension.
In the next chapter, you will learn about the different stages of an attack using the Cyber Kill Chain model, how to identify attacker TTPs using the MITRE ATT&CK framework, and how to create threat intelligence documentation for incident response.
Further reading
For more information on the topics covered in this chapter, you can refer to the following links:
- Threat Actor Basics: The 5 Main Threat Types: https://www.sentinelone.com/blog/threat-actor-basics-understanding-5-main-threat-types/
- Hacktivism: https://en.wikipedia.org/wiki/Hacktivism
- Hacktivism 101: A Brief History and Timeline of Notable Incidents: https://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/hacktivism-101-a-brief-history-of-notable-incidents
- 15-year-old script kiddie arrested in TalkTalk hacking investigation: https://siliconangle.com/2015/10/27/15-year-old-script-kiddie-arrested-in-talktalk-hacking-investigation/
- Insider Threat: https://www.imperva.com/learn/application-security/insider-threats/
- A Closer Look at the Attempted Ransomware Attack on Tesla: https://www.tripwire.com/state-of-security/featured/closer-look-attempted-ransomware-attack-tesla/
- Ransomware's cryptofootprint: https://www.kaspersky.com/blog/rc3-bitcoin-ransom-tracing/38488/
- Threat Actor Type Inference and Characterization within Cyber Threat Intelligence: https://arxiv.org/ftp/arxiv/papers/2103/2103.02301.pdf
- The Markdown Guide: https://www.markdownguide.org/
- Research ATT&CK techniques from the comfort of your VSCode editor: https://redcanary.com/blog/vscode-attack/
