Enumerate: Determine What’s Out There
Introduction
Enumeration: To count off or name one by one. Enumeration is one of the most important steps a penetration tester performs. It is also extremely valuable to job seekers. In most cases, job seekers enumerate the positions that are available. In order to successfully find your first INFOSEC job, you also need to enumerate your own skills and the ways to highlight those skills to prospective employers.
Chances are you have a pretty good idea of your skills. Chances are you have no idea how to make those skills work for you. There are a number of ways to improve your odds of landing that coveted INFOSEC job. Networking, education, increasing your profile in the community; all are important, but what does that mean? Where do you network, and with whom? What type of education should you pursue? How about “increasing your profile in the community?” What in the world does that mean?
This chapter teaches you these concepts and more. By applying the principles outlined in this chapter, you’ll learn to effectively network with the right people. You’ll also be exposed to the educational choices of successful INFOSEC professionals. You’ll learn about the security community and now to improve your visibility in it. The truth about certifications is revealed, and it probably isn’t what you think. Finally, some proven ways to increase your value to potential employers are presented. Some of the principles outlined in this chapter are fun; some are hard; some are hard and fun … and guess what? Some are hard and not one bit fun, but hey, you want to be an INFOSEC professional. Everything can’t be gravy.
What Should I Do First?
Ok, if you made it through that daunting introduction, not to mention the first two chapters, chances are you are still interested in pursuing a job in the INFOSEC field. Now you may be asking, “Where in the world should I start? I have all of these wicked skillz, but no one seems to care.” Well my friend, you have come to the right place. Believe it or not, chances are you have already taken the first step in pursuing your new career … you just didn’t realize you were doing it.
Networking
Yep, it’s networking. Before you get worried, you can put those Cisco manuals down. It’s not that kind of networking. This is the kind of networking that is even MORE fun than playing with the latest IOS. It’s the kind where you get to hang out with other people who enjoy the same type of things you do. You know – discussing the latest kernel modules; talking about the latest Windows vulnerability; talking to other people about their INFOSEC jobs. Wait. Talking about INFOSEC jobs?
Local ‘Hacker’ Meetings
One of the best places to work on your networking skills is your local hacker group meetings. There are several different types of meetings. Defcon Groups (DC Groups) (www.defcon.org/html/defcon-groups/dc-groups-index.html) and 2600 Meetings (www.2600.com/meetings/) are a good start. Attendees at these meetings are usually an eclectic mix of people working in INFOSEC, people who want to work in INFOSEC, and people who create the need for people who work in INFOSEC.
Usually, there are one or two topics per meeting, and can range from beginner-level to extremely technical. Don’t be discouraged if you don’t understand something a speaker is presenting. They are presenting information so that others can learn from their experiences. Although cliché, it is true that the question you feel silly asking is probably on the minds of several others in the room.
Go beyond asking questions. Engage the speaker in a dialogue. You may have some information that is new to the speaker. For example, if the speaker is giving a presentation on exploiting PL/SQL, and he doesn’t cover a point you know, mention it. If he is aware of your point, he’ll probably work it into the presentation, and if he isn’t, he’ll want to know more. Everyone will learn from you as well as the speaker.
Once you have been to a few meetings and feel comfortable with the people and the material being presented, take it to the next level. Ask the group coordinator for a slot for you to speak at an upcoming meeting. Before you start worrying that you may have bitten off more than you can chew, relax. You’re not trying to wow the group with your technical expertise just yet. Rather, you want to get in front of them and make sure they know you, know who you are, and start to get a feel for your abilities. Furthermore, public speaking is a sought after skill, and getting experience and recognition as someone who can speak will benefit you down the road.
Another great strategy is to make time both before and after meetings to socialize. Remember, many of the attendees at these meetings are already working in the industry. The old axiom, “It’s not what you know, it’s who you know,” is often true. Remember, you aren’t necessarily looking for the job you’ll retire from. You are looking to get your foot in the door. Personal references from a respected employee go farther with prospective employers than almost any other tool in your arsenal. Taking time for one-on-one conversations with other people in the industry, while making sure to let them know of your desire to work in the industry, can result in a goldmine of potential leads. One caution – don’t be fake. It is easy for people to spot someone trying to use them to further their personal agenda. On the other hand, it is equally easy to spot a person that is genuine.
Local Users Groups
Much like local hacker group meetings, local user groups are also a great place to network with people in the INFOSEC industry. Probably the most prevalent type of user group is the Linux User Group or LUG (www.linux.org/groups/). Many INFOSEC professionals are also members of local LUGs and attend meetings regularly. Pretty much any type of technology has some form of user group community. The Snort Intrusion Detection System (www.snort.org) has a growing user group community (www.snort.org/community/usergroups.html). Wireless User Groups (WUGs) have been springing up all over the world in recent years. You probably already know what you are interested in, intrusion detection, forensics, vulnerability assessment, operating systems (Linux, BSD, and so on). Simply go to Google and search for your favorite hardware, software, technology, or special interest, followed by the words ‘user group’ and you will likely find a user community that gathers to discuss and promote that technology.
You will find that the larger the user community, the more hits you will get (shocking isn’t it?). For instance, a search for ‘linux user groups’ will likely yield significantly more results than a specific search like “HP-UX user groups,” but don’t be discouraged. Many of these user groups have mailing lists that you can subscribe and contribute to. Although e-mail or Internet contact is not always as fruitful as face-to-face contact, many strong, valuable relationships can begin with an online introduction. Hey, eharmony.com is in business for a reason. Additionally, almost all of these smaller, more specific communities have Internet Relay Chat (IRC) channels where you can begin to cultivate relationships.
Regardless of the way that you make contact (face-to-face at meetings or through some form of online community), the principles mentioned in the Local Hacker Meetings section also apply for user group meetings. Listen, learn, speak, and be genuine. Once you start to make a name for yourself in a specific community, you’ll find that your skills are recognized, and if you let it be known that you are looking for work in INFOSEC, it is quite possible that one of your contacts in these communities is aware of an opening and can put in a good word for you.
If you get nothing else out of this chapter get these four words: Google Is Your Friend! The easiest way to alienate yourself with a user community is to ask questions that are easily answerable using a search engine. That isn’t to say that you shouldn’t ask your questions. Rather, search first. If you can’t find the answer, reword your search string and search again. If that doesn’t yield valuable results, yep, you guessed it, reword your search string and search again. If you still haven’t found the answer to your question, it’s a safe bet that when you ask the question you won’t get the standard “Google it” or “RTFM (if you don’t know what RTFM is … GOOGLE IT!)” response.
Is Education Important?
Is a formal education important? This question gets asked all the time of INFOSEC professionals. The answer will depend on who you ask. Some of the best INFOSEC professionals out there have never seen the inside of a college classroom. These people will tell you that education isn’t important. However, ssking the same question of someone with a Masters of Science in Information Security will bring a completely different answer. So who should you believe?
No single factor – education, experience, reputation, or anything else, is going to get you the job you are looking for. Rather, a combination of all of these factors is going to be required. Let’s look at each of these.
Experience This is probably the hardest to get. That’s why you bought this book in the first place – so you can get a job in INFOSEC and get some experience. The problem with experience is the same in INFOSEC as it is in any other field. Every employer wants it, but few employers want to be the one to help you get it if you don’t already have it. Remember though, you are a hacker. You have been finding ways around things most of your life. It’s time to apply those principles to your job hunt. Remember, formal experience is not the only type of experience employers look at. Volunteer experience also looks great on a resume, and almost every type of organization in your area uses some form of information technology – schools, churches, Girl or Boy Scout groups – you name it. They are all great places to volunteer your time and talents. Contact the school board and let them know that you are pursuing a career in Information Security and that you would like to volunteer your services at a local high school. Since this puts you around kids, which tends to make some people nervous, you will have better luck if you know someone on the board or at a specific school who can recommend you (hey … that goes back to that networking thing we talked about). Churches on the other hand are usually much more receptive to any type of volunteer help they can get. Be creative; find an organization in your area that will let you practice your trade while building real world experience. Don’t be discouraged if the first few places you try don’t show much interest. Keep plugging away. You have a valuable skill, and there is someone out there who will let you use it.
Your reputation is gold. Well, you hope it’s gold anyway. If you have a good reputation in the user group community, or in the community where you live, it will carry you a long way. If a prospective employer searches for your name on Google (yes, they actually do this) and finds three or four presentations at a local hacker group, and several well-written, informative posts on INFOSEC message boards or mailing lists (more on those later), they are likely to be impressed. This both increases your chances of getting an interview and increases their opinion of you before you even set foot in the door. If, on the other hand, they search for your name and find a string of poorly written, abusive posts, several pictures your college roommate took of you passed out with your pants around your ankles, and a bunch of questions posted to message boards that could have been answered with a cursory Google search … well, odds are you aren’t going to be called in for an interview. These are all factors in your reputation.
That brings us back to education. Is formal education necessary? Maybe not. Is it a definite way to increase the likelihood that you will be able to break into the INFOSEC field? It sure is. You’ve probably heard people talking about not needing a college degree because college has nothing to teach them. Maybe. Maybe not. The fact is, a college degree does more than demonstrate what you have learned. It demonstrates to a prospective employer that you have the ability to stick to a task and see it through for an extended period of time. Most bachelor’s degrees take at least four years to complete. Many projects that you will work on in the INFOSEC field are long term. Just having the degree tells a prospective employer that he can count on you to stay the course.
Setting aside the benefit of demonstrated tenacity for a minute, look at your decision to obtain a degree a different way. Think of it from a purely selfish standpoint. Many INFOSEC jobs, in fact, many IT jobs in general, require a college degree. Without obtaining a degree you may not make it past the Human Resource (HR) resume screeners to even get an interview. HR people don’t usually have an understanding of the specific job duties they are recruiting for. They have a list of ‘requirements’ they look for. A college degree is often one of these requirements. When these people look at your resume and see no experience and no degree, well … you get the picture.
Fields of Study
Okay, so we have determined that it is in your best interest to bite the bullet and get that bachelor’s degree. Now the question kicks in: “What should I get my degree in?” Your choice here is very important. A liberal arts degree isn’t going to pull as much weight as a bachelor of science in an IT-related field. There are several good choices of potential degrees. Bachelor of science degrees in the following fields of study are the most sought after by employers looking for INFOSEC professionals:
This list is by no means comprehensive. A bachelor of science degree in other fields will probably meet the degree requirement. These are just the degrees that employers often list as acceptable in job descriptions. In addition to the bachelors of science degrees, there are several master’s degree programs that specialize in Information Security. While a master’s degree is rarely required, especially an entry level position, if you are inclined to pursue a higher degree, a Master of Science in Information Security can never hurt.
Certifications: Magic or Myth?
Some of the most common questions for INFOSEC professionals revolve around the issue of professional certifications. Some will say that certifications are the greatest asset you can have and that an alphabet soup after your name only increases your value. Others will tell you that certifications are a waste of time and only people that can’t actually ‘do’ the job waste their time getting certifications. The truth lies somewhere in between.
Getting selected certifications can be beneficial. Some companies or contracts require a Certified Information System Security Professional (CISSP) certification (www.isc2.org). Much like a degree, this is something a HR person will screen resumes looking for. If they don’t see it, they won’t consider your application. The CISSP focuses heavily on security policy issues. If you are looking to get your foot in the door with a Certification and Accreditation (C&A) position, then the CISSP could be very beneficial to you. CISSP certification is also useful when applying for analyst work such as risk assessment or compliance auditing positions. On the other hand, some people in the industry tend to think the CISSP has been devalued and is no longer a realistic indicator of the skills an individual possesses. This can be the case with any certification. When the job market becomes saturated with a particular certification, the value of that certification decreases. This was the case a few years ago with Microsoft Certified System Engineer (MCSE) certification. Individuals with MCSE certification were widely sought after and could command high starting salaries with relatively little experience. As the demand for MCSE certified people grew, a lot of MCSE ‘boot camps’ sprung up that were teaching the test and not the concepts required to understand the skills a MCSE needed. This led to a market with a lot of ‘paper MCSEs’ - people who were certified but didn’t have the knowledge required to do the actual job they were hired for.
The SANS Institute has worked to combat the ‘paper certification’ problem by introducing the Global Information Assurance Certification (GIAC) line of security certifications. In addition to two examinations, students were required to complete a practical assignment within six months of taking the GIAC training until April 15, 2005. This requirement was dropped as of that date. GIAC certifications are available in a wide range of disciplines. From the most basic GIAC Security Essentials Certification (GSEC) to more advanced INFOSEC specialties like Forensics and Security Administration. Information about the GIAC certifications can be found at www.giac.org/certifications.
Obtaining professional certifications can be in your best interest. For instance, if you are interested in pursuing a vulnerability assessment position, the National Security Agency (NSA) INFOSEC Assessment Methodology (IAM) and INFOSEC Evaluation Methodology (IEM) certifications can be very beneficial. For more information on the IAM and IEM, check out www.securityhorizon.com and www.iatrp.com/main.cfm. The IAM is a framework for doing assessments that are policy driven, and the IEM is a hands-on technical evaluation of an organization’s security posture. Most operating system vendors also offer some form of operating system-specific security certification. There are wireless security certifications available, as well as network security certifications from vendors and third-party organizations.
A few targeted certifications can help beef up your resume and show a prospective employer that you have some background knowledge and skill in the specific area they are looking for. If, on the other hand, you pursue every certification out there, you run the risk of employers concluding that you are possibly a good test taker, but without experience to back your certifications up, they may just pass.
Getting Your Name Out There
You have the skills, and you’ve put time and effort into getting your bachelor’s degree and a couple of relevant certifications, but you’re still having trouble getting your foot in the door. One of the best ways to get that initial interview is to get your name out in the INFOSEC community so that you are recognized. There are several ways to make this happen. Here, we discuss a range of methods – from things you can do in your own house for little or no money, to more expensive and time-consuming strategies.
Mailing Lists
Much like the LUGs mentioned earlier in this chapter, there are mailing lists available for pretty much any product or technology you might be interested in. There are some very good lists specifically for INFOSEC professionals, as well. The Bugtraq mailing list (www.securityfocus.com) and the Full Disclosure mailing list (https://lists.grok.org.uk/mailman/listinfo/full-disclosure) are specifically designed to discuss security vulnerabilities associated with information systems. Archives for both of these lists can be found online (http://securityfocus.com/archive/1 and http://lists.grok.org.uk/pipermail/full-disclosure/). Before subscribing to any mailing list, it is a good idea to read through the archives for the last few months. This will accomplish a couple of things. First, you will get a feel for the ‘tone’ of the list. Some lists are very high volume, like Full Disclosure. You will get at least 10 or 15 e-mails per day from the Full Disclosure mailing list. If a new vulnerability is a hot topic of discussion, that number will triple or even quadruple. Similarly, the Bugtraq mailing list traffic increases significantly with new, hot topics of discussion.
Because not everyone wants to get a continuous stream of e-mail from mailing lists, most of them offer a digest option. This is a single e-mail that is sent out daily containing all of the posts to the list in the past 24 hours. This can be a great option for high-volume mailing lists.
The Bugtraq mailing list is hosted by Security Focus (www.securityfocus.com). Along with Bugtraq, Security Focus offers several other mailing lists geared to more specific INFOSEC interests (as shown in Figure 3.1).
Don’t try to throw your arms around the entire field by joining every list that is offered. You will spend all your time reading and sifting e-mail to find the relevant information you need. A popular technology has been the use of RDF Site Summary or Rich Site Summary (RSS) feeds for keeping current on your chosen lists. You can then skim them much easier, rather than spending all your time handling the noise on the list, and you can use that time to respond to a topic that interests you. Another advantage of using RSS to handle multiple lists is that some lists choose to update frequently and can easily overwhelm your capacity to stay current. Other outlets may pick up the information later that day or week, but with RSS you can be up-to-date with the information and not overloaded by the sheer number of posts.
Forums
Forums, love them or hate them, are a prominent fixture in the Internet community. In many ways, they are the evolution of the bulletin board, some of the first communications channels used between hackers and professionals. If you are already a member of a forum that might garner some positive attention, like the Defcon Forums (http://forum.defcon.org), or a more specialized forum, like NetStumbler (www.netstumbler.org/), then your reputation is already in place. It sounds silly, but a well-established presence on boards such as these can do wonders, especially if the HR people have used those forums for reference in the past.
There are also forums out there for professional organizations or certifications, like the CISSP® (https://forum.isc2.org/index.php?) or GIAC (www.giac.org/certified/boards/). Membership to these boards is usually restricted to certified members, but there are related forums that offer open membership. Those are great avenues to try to find like-minded colleagues who might have more specialized skills.
Since there are as many lists for skills, almost, as the skills themselves, I will not list them all here. One way to narrow down the search, however, would be to include a prominent tool, vendor, or aspect of the skills to focus the exposure. An example of one way to gain recognition in wireless networking and security is to check out the previously-mentioned NetStumbler forums, as well as Kismet, www.kismetwireless.net/forum.php, a very popular tool for performing wireless network detection and monitoring.
Don’t Just Read … Contribute
Now, perhaps you are thinking “Hey. Why should I even bother filling my inbox up with all this mailing list traffic? You already told me that archives are online.” While it is true that the archives are online, you can only read those. In order to really get your name out there, you need to contribute. You can contribute by asking insightful questions or by providing new information, depending on the type of list. For instance, if you have discovered a new vulnerability in a product, the Bugtraq and Full Disclosure mailing lists are good places to report them. Be careful with this type of disclosure though. Irresponsible disclosure can be counterproductive, and more detrimental than no contribution at all. Before posting a vulnerability to one of these lists, you should contact the vendor and provide them with information about the vulnerability. After an agreed upon time for the vendor to develop and release a patch, a joint announcement between the vendor and you to these lists is an outstanding way to get your name out to the community.
There will be cases where vendors decline to fix a vulnerability, or an inordinate amount of time passes after vendor notification. In these cases, you are forced to make a decision. Should you disclose the vulnerability, or not? There is no hard and fast rule. Some people will tell you that the benefits of alerting the community to a vulnerability so that they can try to find ways to mitigate the effects outweigh the potential for an attacker to use the information for untoward means. Other people feel the exact opposite. You will have to make this decision on a case-by-case basis, but always keep in mind that an irresponsible disclosure could backfire and hurt your reputation in the community.
Of course, not everyone in INFOSEC discovers new vulnerabilities, and you don’t necessarily have to go that route to get your name out there. If, as an example, you have developed strong Solaris skills, you can begin to get your name out by answering questions on the Focus on Sun mailing list. If you have done research on firewalls that you feel would benefit the community at large, then posting that information to the Firewalls mailing list would be an outstanding way to begin getting your name out to the community.
Remember, your goal in posting to these lists is to get your name out in the community to either prospective employers, or to other professionals. Name recognition can go a long way toward getting an interview. You can, however, shoot yourself in the foot by participating in flame wars and being condescending on these lists, particularly when you are a new poster. Additionally, it is in your best interest to craft your e-mail using proper grammar and spelling. Almost every job in INFOSEC requires some level of written communication. Using proper spelling and grammar demonstrates to prospective employers that you have this necessary skill.
Security Conferences
Another great resource available to you as you pursue your first INFOSEC job is security conferences. Unfortunately, there are many conferences out there, and many of them are very expensive. You obviously can’t attend them all, so you have to make decisions about how to get the most bang for your buck.
Attend Conferences
Attending conferences can be a fantastic way to learn some of the newest information in the INFOSEC field. Some of the brightest people in INFOSEC speak at annual conferences like the Black Hat Briefings (www.blackhat.com). The presentations at most of these conferences range from introductory level INFOSEC concepts to advanced, previously unreleased information. Additionally, many conferences include a track for managers responsible for INFOSEC matters within their organization. The technical talks are obviously beneficial to you as you round out your arsenal of security knowledge, but the management-level presentations can also be very helpful. By understanding the issues that managers have to deal with, you can better prepare yourself for an interview with them.
There are so many conferences geared toward the INFOSEC professional that you will have to choose the conferences you decide to attend wisely. Before deciding which conferences to spend your money on, you should understand that different conferences attract different types of attendees. If you are looking for a conference that is mainly attended by other hackers, Defcon (www.defcon.org), held annually in Las Vegas, Nev., has the largest attendance, usually around 5,000 total attendees. If your goal is to meet other hackers and people that have a recognizable name or handle in the hacker underground, you will find a lot of them at Defcon. You may, however, find that it is difficult to get any one-on-one time with these people because of the sheer number of other attendees vying for their attention.
Fortunately, in addition to the big conferences, there are several smaller conferences that take place throughout the year. Interz0ne (http://interz0ne.com/) in Atlanta, Ga., ShmooCon (www.shmoocon.org/) in Washington DC, Toorcon (www.toorcon.org/) in San Diego, Calif., and Layer One (www.layerone.info), in Los Angeles, Calif., all provide smaller, more regional conferences in the United States. Also, Canada offers CanSecWest (www.cansecwest.com/) in Vancouver BC. These conferences are all INFOSEC specific and can provide you with an opportunity to attend a conference without having to travel as far, if at all. Additionally, because these conferences generally have smaller attendance bases, you will probably have more of an opportunity for one-on-one time with the speakers, staff, and other attendees.
Most of these conferences provide PDFs or Powerpoint slides of past presentations on their websites. In addition to providing a wealth of knowledge, these past presentations will give you a jumping off point for conversations with speakers when you meet them at a future conference. Most speakers at professional conferences are more than happy to spend some time talking with attendees about their presentations (current and past). Asking insightful questions will allow you to begin to get your name out to individuals with established reputations in the INFOSEC field. As with presentations at smaller user group meetings, it is imperative that you are sincere. If a conference speaker believes that you are trying to use him to further your own reputation, or that you are being disingenuous, they are very likely not going to spend much time with you and are likely to remember you in a negative way.
Speak at Conferences
One of the greatest ways you can increase your chances of landing your first INFOSEC job is by not just attending security conferences, but speaking at them. As we mentioned earlier, many of these conferences are attended not only by people currently working in the field, but also by the managers that hire them. By presenting at these conferences, you are providing a prospective employer with hard evidence that you are a leader in your area of expertise. Your interview process will be significantly easier because employers will be able to gauge your knowledge level before they even meet you.
In addition to routine background checks, most employers also run rudimentary search engine queries on people they plan to interview. A simple query of your name and the word presentation (which you will obviously mention on your resume) will provide a prospective employer with valuable information about your ability and standing in the community as shown in the example in Figure 3.2.
A simple Google search for the name Chris Hurley followed by the word “presentation” yielded over 30,000 results. Obviously all of these results aren’t actual links to presentations; however, the searcher could quickly verify that the information listed on a resume was in fact legitimate. By pulling up and viewing some of the presentations, he could determine the level of technical ability of an individual in a specific area. After this initial research, the interview process will likely be much easier for you because if the company representative decided to call you in after reviewing your conference presentations, chances are very good that they were impressed with your skill level. At this point, it is probably your job to lose, rather than something you have to fight tooth and nail for.
Regardless of the method or methods you choose to get your name out there, you need to use your real name, not your handle, if you have one. Companies hire Chris Hurley. They don’t hire Roamer. If a company doesn’t know that you are the name behind the handle, you are going to have a difficult time turning your name recognition into a paying position.
Training / Teaching
Training and teaching are similar to the authoring and presenting methods; you can often combine them and create a training session. A common INFOSEC training outlets is the SysAdmin, Audit, Network, Security (SANS) Institute, www.sans.org/. Although it take an accomplished individual to offer SANS classes, you can do the same on a smaller scale. Check out your local community college or high school for opportunities to provide free training classes on INFOSEC topics. Libraries and other public institutions are often budget restricted and welcome someone offering to give lessons to the community. This is an excellent way to give back to the community (also discussed in Chapter 10). For example, to get your foot in the door, you could teach a basic Windows security course. Chances are, if you have bypassed security on them, you have a pretty good idea about how to reinforce them. Also, this is a good way to complete continuing education hours required by some certifications, such as the CISSP.
On the receiving side of training, the ability to list many INFOSEC-related skills on your resume is critical when developing your resume. Check out free tools and resources to up your familiarity with INFOSEC processes. Projects like Nessus, www.nessus.org/, MetaSploit, www.metasploit.org/, and the Open Source Security Testing Methodology Manual (OSSTMM) can provide you with the experience and skills necessary to build up your resume and skill sets. If you are planning to pursue a career in penetration testing or any type of assessments, get very familiar with these tools, as they are common throughout INFOSEC. Just a word of caution, don’t download these tools and just fire them off at random addresses; test your home machines only. Certifications can be included here, as well, although they usually have a financial cost to them. Some companies offer free or discounted certifications through sites like Brainbench, www.brainbench.com/. Take advantage of those as much as possible. Any opportunities to gain vendor certifications should also be utilized, as long as you do not rely on them solely for gaining work opportunities.
Understanding Opportunities and Gaining Experience
Everyone needs experience. Earlier in this chapter we looked at ways to gain unconventional experience. While unconventional experience is great, traditional, conventional, actual experience is virtually impossible to replace on a resume. A couple of years experience can be the difference between getting an interview and being passed over. It can mean the difference between being offered a job or having it offered to an equally qualified, but more experienced candidate.
There are ways to get real, traditional experience – the experience that many potential employers value very highly. Experience that can often give you the edge you need. Experience that, depending on your background and mentality, may challenge your ideas of whether or not it is worth gaining.
Gaining Your First Experience
What would you say if you were told that you could gain three years of traditional INFOSEC experience without having to go to an actual job interview? Without having to have any prior experience? Chances are, you would either think you were being conned, or you would ask where to sign up. Well, sign up is probably the best way to describe it. Think “military.”
The Military
Yep, you read that right; the military. The military is an outstanding place to gain traditional INFOSEC experience. Now, before you slam this book shut and throw it across the room like it was trying to bite you, read on for a page or so.
Unlike many other employers, the military looks at your aptitude for doing a specific job rather than your experience and education level. For someone trying to break into a particular field, the military offers the opportunity for you to gain both training in that field, and then experience.
Many people reading this have spent some amount of time in the ‘hacker underground’ or ‘the scene’ as it is sometimes called. As you know, this is a culture that is very free and tries not to be bound by many of the restraints and restrictions that society has placed on people. In fact, in many cases, it is that disdain for restraints and restrictions that initially drew you to the hacker community. At this point, you are going to have to make some choices about what is important to you. If you are serious about making a jump into the INFOSEC field, you are probably going to have to give up some of these ideas. You need to be willing to wear appropriate attire to work instead of shorts and t-shirts. You are going to have to follow the direction of your manager or supervisor. The military may take these things to an extreme that makes you uncomfortable (uniforms and orders instead of buttondown shirts and tasking), but the concepts are basically the same.
All four branches of the United States Military offer multiple careers that will provide experience in INFOSEC or INFOSEC-related fields. All allow you to choose and be guaranteed a specific job, if you are able to demonstrate an aptitude for that specialty. Once you have completed your initial training, you can gain experience performing the duties associated with that job. Additionally, many prospective employers appreciate the discipline and ideals that the military stands for, and this will give you an additional leg up. The military also offers tuition assistance to active duty servicemen and women that pays up to 75 percent of college course fees. And, in lieu of enlistment bonuses, tens of thousands of dollars for education can be chosen for use after enlistment ends. This provides you with traditional experience and the ability to obtain formal education – both of which prospective employers desire.
The military is not for everyone. You should be realistic about this fact. You are going to need to assess your ability to adhere to the restrictions placed on you by the military. If you believe you can’t do this, then you should not consider gaining experience in the military. As favorable as an honorable discharge from the military can be, a dishonorable discharge, or a general discharge under less than honorable conditions, will almost certainly sink your chances with most employers.
The Government
Another place you can sometimes obtain an entry-level INFOSEC position is with the government. To some of you, working for the government equates to sleeping with the enemy. However, government positions offer several advantages and opportunities. USAJOBS (www.usajobs.opm.gov/), run by the United States Government Office of Personnel Management is the official job listing for positions with the federal government. It allows you to search current listings for available positions.
When looking for entry-level positions, narrow your search to only positions listed between the pay grades of GS-1 and GS-7. Figure 3.3 shows an example of government entry-level listings.
Most government positions that have an experience requirement allow you to substitute education for experience. In addition, many government positions only require general experience as opposed to specialized experience. You can almost always apply the volunteer and non-traditional experience mentioned earlier in this chapter to a general experience requirement.
Government positions offer several potential advantages over commercial positions. The government has placed a premium on all security fields, including INFOSEC, since September 11, 2001. This means that many agencies budgets include line items for Information Security. Big budgets mean good equipment. It is always fun to have the latest and greatest equipment available to you, and government positions often afford you that opportunity. Also, while corporate America is controlled by the bottom line, and layoffs, even for INFOSEC professionals are common, government positions generally offer a strong level of job security. At a minimum, you maintain an awareness of the government INFOSEC positions available for entry-level candidates so that you can keep all options open to you. The one difficulty you may face when trying to get a government INFOSEC position is that many require some form of security clearance.
Security Clearances
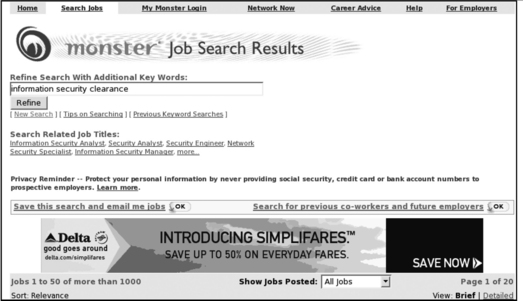
One of the most frustrating aspects of searching for INFOSEC jobs can be that so many of the positions require some form of government security clearance. A search of Monster.com listings for ‘information security clearance’ returns over 1000 listings (see Figure 3.4).
It is obvious from these results that persons with security clearances are in high demand. Unfortunately, getting a security clearance is not as easy as requesting one. Most of the time, companies are reluctant to invest in the background investigations required for a clearance and would prefer, and in some cases require, that an applicant have an active clearance. This puts entry-level job seekers at a decided disadvantage. There are a couple of ways to get this clearance.
The first, and most common, way to get a clearance is by joining the military (you were hoping we weren’t going back to that weren’t you?). In addition to the benefits mentioned earlier, the military is not reluctant to invest in putting you through the clearance process. If your job requires a clearance, the military pays for it. It is as simple as that. Many people join the military for this benefit more than any other.
A less common way to get an initial clearance is through a sponsorship program with a company that has contracts requiring clearances. This method can be expensive. Using a corporate sponsorship works this way. First, you pay for the background investigation (around $2500) instead of the company. Since $2500 doesn’t sound like that much money to a company, you may be asking yourself what the big deal is. Put simply, the real expense to a company isn’t the background investigation. It is the time that you have to spend on overhead (not billing to the contract since you don’t have the required clearance to perform the work). A “Top Secret” clearance can take between six months and two years to complete. Two years on overhead is very costly to a company, even for an entry-level position. The company doesn’t offer you a position, but rather, agrees to hire you after your clearance has been granted. During this time you will have to continue working at a different job. Most companies are reluctant to do this type of sponsorship for a couple of reasons. First, clearance-required contracts specify a certain number of cleared positions. These billets are usually filled by people actually working on the contract. Second, the company has no real guarantee that you will take the position with them after you have been granted a clearance.
In order to obtain a U.S. Government security clearance, you will be required to fill out an SF 86 form. This form provides the investigating agency with the information it needs to begin a background investigation commensurate with the clearance that is being requested for you. Even if a clearance isn’t required, you may be subjected to a public-trust background check (SF 85) or National Agency Check (NAC). These are less intrusive background checks that focus on past criminal activity.
So How Do I Get There?
Okay. All of that information was great, but how do you translate it into a job? Well, let’s start with where you are, and look at where you want to be. First, what defines a hacker? This was covered in Chapter 1, but it should be described here, as well. A hacker is someone who can take something, such as code, hardware, or radio waves, and do something new and different with it. Contrary to what television and other media may have you believe, being a hacker is not a bad thing. The INFOSEC profession was founded on hacker and hacking principles. Many argue that the best person to create a secure infrastructure is someone who possesses skills in bypassing the security services in that architecture. This being said, you will face many in the INFOSEC field who, mistakenly, view all hackers as criminals. Be prepared to defend the term if you choose to use it.
Taking this to the professional level, a hacker needs to be able to view the ethical challenges in all INFOSEC activities and be able to meet those challenges in a positive manner. It is an act of supreme faith for an administrator or business owner to allow someone from the outside to come in and perform an evaluation or even just operate in his or her “trusted” environment. In order to gain that trust, you need to be able to project a presence of technical competency along with the demeanor of someone who would be a good steward of that information. Data security depends on trust. Without trust you cannot allow multiple people access to the same resources.
One advantage a hacker has when moving into the INFOSEC field is the ability to “think outside the box.” Although this is a much-overused phrase by management, it does have validity. Many workers have a hard time moving their thinking patterns out of the standard processes and cannot see problems from various perspectives. This is a critical skill for any type of troubleshooting or root-cause analysis. Meeting challenges from a hacker’s perspective allows you to understand all of the levels of the problem or situation, and then figure out someway to make it work. It may not be the cleanest or smoothest solution, but if it gets the job done, it can be refined later. Use your innate curiosity and talent to figure out different ways to solve a problem and provide solutions.
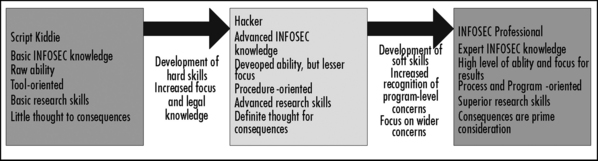
Figure 3.5 shows a high-level overview of the skill progression from a script kiddie (you know who you are) to an INFOSEC professional.
Welcome to the Jungle
The work environment that you will be entering will vary depending on the type of job, as well as the culture of your employer. Some companies still use the “laid-back” approach of the late ‘90s dot-com businesses, whereas some positions and employers are as bureaucratic as they come. For the INFOSEC field, however, there are some constants for which you should be prepared, no matter where you find work.
Obviously security for security personnel is paramount. If you cannot protect your own resources, how can you be expected to do so for other clients, internally or externally? Fewer people will have root access to the data than you may be used to; think about the recent rise in the number of phishing scams and identity theft cases. Improperly stored data is not something that just happens to your clients or co-workers; it can happen to you. Apply the same work ethic you use in your job, to your job.
If you have issues about people watching over your shoulder while you work, or expect you to explain your actions, then you should try to resolve those before advancing far into INFOSEC. With the ability and access you are granted, a much larger responsibility for handling those resources is also granted. If you take the track of functional security testing, some circumstances may require keystroke logging that will be reviewed by an independent third-party to ensure that you followed the Rules of Engagement (ROE). The work of an INFOSEC professional is always under review and scrutiny, and not because of some perceived threat from you. The nature of the job requires diligent protection against all threats, including internal. Also, when you walk into a position where you have specialized skills, many times other workers and clients will want to learn from you. Expect that anytime you are doing things that you consider fun; others will want to gain information about what you are doing.
Once you get your new position, it is entirely likely that you will be working with people whose skills do not match yours in depth or level. It is paramount, however, that you work well with these people and use the skills they do possess to your advantage. So what if your team member doesn’t understand SQL or how you can use it to bypass poorly written security controls in a web environment? That is your job, and theirs may be to show you the policies are written to reinforce those controls. Use their knowledge of the topics you are weakest in to supplement your own and get the job finished. You will gain a reputation as being a hard-tech person who works well with soft-skills people and may have more opportunities given to you. Be upfront with people you work with about your skills and weaknesses. Working in INFOSEC is a continual process, just like INFOSEC itself, and continuous change is the norm. If you do not keep your skills current and try to increase them in scope, you will be left behind.
Summary
There are many ways to can increase your odds of landing that coveted first INFOSEC job. Some of these ways are fun and exciting. Some are time consuming and difficult. In both cases, it is possible to take the skills that you have and complement them through different traditional and non-traditional means to increase your chances of getting your foot in the door.
One of the best ways to do this is to become part of an extensive network of people in the industry. You can network at local hacker and user group meetings, or at professional conferences. Regardless of where you start building these relationships, once you have a strong network of INFOSEC professionals that recognize your worth and abilities, their recommendations will vastly increase your odds of getting an interview with organizations that respect their opinions.
Formal college education is another way to increase your worth to prospective employers. An information technology-related degree, such as Computer Science, and/or an engineering degree, such as Electrical Engineering, demonstrate to employers that you have the ability to both grasp the concepts required to perform your job and the dedication to complete a long term project. A degree says much more about you than what you know. It speaks to your character. In addition to formal education, certifications relevant to the type of position you are seeking show employers that you have either grasped the required concepts of the job or that you are proficient in the skills required to perform the job, depending on the certification.
Getting your name out there and recognized in the INFOSEC community is invaluable. You can do this in a number of ways. Speaking in front of local hacker groups is a good start. Subscribing and contributing to mailing lists where your skills are strongest puts your name in front of industry professionals. The respect of these professionals that you gain through thoughtful, well-written contributions help your name be both recognized and respected. Attending security conferences and meeting industry leaders is a great way to begin increasing your visibility in the INFOSEC community. Taking the next step and actually speaking at these conferences helps get your name in front of both industry professionals and HR managers that you may interview with. Regardless of how you do it, increasing your name recognition will benefit you in countless ways as you pursue your first INFOSEC job.
One of the most difficult things you will face is meeting the experience requirements for many positions. Although difficult, there are ways to gain experience. Non-traditional experience such as volunteer work is usually available, if you are tenacious and dedicated. Traditional, ‘real-world,’ experience is usually more difficult to come by. Military service is one avenue open to most people for gaining this traditional experience. Pursuing work in the civilian government sector is another great way. Since many government positions require some form of security clearance, you may have to investigate ways to obtain this clearance. Once again, the military is a good place to get your first security clearance.
Assuming that you are willing to make hard decisions and work hard, you can get your foot in the door. Take advantage of these methods, and you will benefit by landing your first INFOSEC position.
Solutions Fast Track
![]() Cultivate a network of industry professionals to help you down the line in your job search. A strong personal reference from one of these professionals is often more valuable than any item on your resume.
Cultivate a network of industry professionals to help you down the line in your job search. A strong personal reference from one of these professionals is often more valuable than any item on your resume.
![]() Use local hacker or user groups to begin building your network.
Use local hacker or user groups to begin building your network.
![]() Be sincere when conversing with professionals you’d like to add to your network. People are quick to recognize someone who is trying to use them for their own gain.
Be sincere when conversing with professionals you’d like to add to your network. People are quick to recognize someone who is trying to use them for their own gain.
Is Education Important?
![]() Many positions require some sort of formal education. Even for those positions that don’t require formal education, you will increase your value by having a college degree.
Many positions require some sort of formal education. Even for those positions that don’t require formal education, you will increase your value by having a college degree.
![]() Degree fields such as Computer Science, Information Security, Computer Engineering, and Electrical Engineering are highly sought after by prospective employers of INFOSEC professionals.
Degree fields such as Computer Science, Information Security, Computer Engineering, and Electrical Engineering are highly sought after by prospective employers of INFOSEC professionals.
![]() In addition to demonstrating a grasp of the concepts required for the position you are applying for, a college degree lets an employer know you have the ability to set a long term goal and then work to achieve it. This is, in some cases, more valuable to the employer than the degree itself.
In addition to demonstrating a grasp of the concepts required for the position you are applying for, a college degree lets an employer know you have the ability to set a long term goal and then work to achieve it. This is, in some cases, more valuable to the employer than the degree itself.
![]() Most entry level positions don’t require advanced degrees; however, if you have the time and money to pursue one, a master’s degree or higher can only increase your chances of getting your foot in the door.
Most entry level positions don’t require advanced degrees; however, if you have the time and money to pursue one, a master’s degree or higher can only increase your chances of getting your foot in the door.
![]() Many online universities now offer Information Security Master of Science degrees.
Many online universities now offer Information Security Master of Science degrees.
Certifications: Magic or Myth?
![]() A reasonable number of relevant certifications can augment your college degree very successfully.
A reasonable number of relevant certifications can augment your college degree very successfully.
![]() Research the certification to determine its value to employers. Talking with your network of contacts is a good way to determine if the industry views these certifications as valuable. Do not, however, take the word of only one person. Ask a cross-section of your network what they think the value of a particular certification is before making a decision on obtaining it.
Research the certification to determine its value to employers. Talking with your network of contacts is a good way to determine if the industry views these certifications as valuable. Do not, however, take the word of only one person. Ask a cross-section of your network what they think the value of a particular certification is before making a decision on obtaining it.
![]() Pursue certifications that specifically target the type of position you are seeking. If you are seeking a vulnerability assessment position, you will likely benefit more from an IAM or IEM certification than from an MCSE. If you are looking for a policy-heavy position, the CISSP certification may help you get where you want to be.
Pursue certifications that specifically target the type of position you are seeking. If you are seeking a vulnerability assessment position, you will likely benefit more from an IAM or IEM certification than from an MCSE. If you are looking for a policy-heavy position, the CISSP certification may help you get where you want to be.
Getting Your Name Out There
![]() Contribute to security mailing lists to begin building name recognition. Most subscribers to the lists are people already working in the industry you want to break into.
Contribute to security mailing lists to begin building name recognition. Most subscribers to the lists are people already working in the industry you want to break into.
![]() Craft well-written, grammatically-correct e-mails. Most positions require some level of writing ability, and your e-mail communication to these lists should demonstrate that you possess these skills in addition to your technical skills.
Craft well-written, grammatically-correct e-mails. Most positions require some level of writing ability, and your e-mail communication to these lists should demonstrate that you possess these skills in addition to your technical skills.
![]() Do not engage in flame wars or put other posters down. Behaving like an online bully will turn many employers off very quickly. Intelligent questions, and more importantly, intelligent responses that display your technical proficiency are much more impressive than putting someone down.
Do not engage in flame wars or put other posters down. Behaving like an online bully will turn many employers off very quickly. Intelligent questions, and more importantly, intelligent responses that display your technical proficiency are much more impressive than putting someone down.
![]() Attend and, eventually, speak at security conferences. This is the single best way to develop name recognition. Most employers perform search engine queries about people they may interview. If they see that you have developed and presented technical presentations about a topic that is integral to their position, you increase your chances of getting the job, significantly. Once an employer finds your presentations online and reviews them, if you are called in for an interview, you have a very good chance of getting the job.
Attend and, eventually, speak at security conferences. This is the single best way to develop name recognition. Most employers perform search engine queries about people they may interview. If they see that you have developed and presented technical presentations about a topic that is integral to their position, you increase your chances of getting the job, significantly. Once an employer finds your presentations online and reviews them, if you are called in for an interview, you have a very good chance of getting the job.
Understanding Opportunities and Gaining Experience
![]() Recognize opportunities to gain traditional experience. Even though it may not be the most pleasant option, joining the military will provide you with traditional experience and training. You can also gain funds for your education through military service.
Recognize opportunities to gain traditional experience. Even though it may not be the most pleasant option, joining the military will provide you with traditional experience and training. You can also gain funds for your education through military service.
![]() Recognize non-traditional opportunities, such as volunteer work, to gain experience. Entry-level government positions are available to people with little or no experience, since most government positions afford you the opportunity to obtain the position with general experience as opposed to specialized experience.
Recognize non-traditional opportunities, such as volunteer work, to gain experience. Entry-level government positions are available to people with little or no experience, since most government positions afford you the opportunity to obtain the position with general experience as opposed to specialized experience.
![]() Make sure to keep your nose clean. Nothing will ease your move into the INFOSEC field like an active government security clearance. If you have been arrested, you will probably not be able to obtain a clearance.
Make sure to keep your nose clean. Nothing will ease your move into the INFOSEC field like an active government security clearance. If you have been arrested, you will probably not be able to obtain a clearance.
![]() One easy way to obtain clearance is by joining the military in a job that requires a clearance. Unlike many commercial employers, the military will pay for the investigation required to get a clearance.
One easy way to obtain clearance is by joining the military in a job that requires a clearance. Unlike many commercial employers, the military will pay for the investigation required to get a clearance.
Security Clearances
![]() Many jobs, both government and contractors that provide work to the government, require a security clearance.
Many jobs, both government and contractors that provide work to the government, require a security clearance.
![]() There are many different levels of security clearance. Depending on the level of clearance required, it may be difficult to convince an employer to pay for the clearance process.
There are many different levels of security clearance. Depending on the level of clearance required, it may be difficult to convince an employer to pay for the clearance process.
![]() The military is an excellent place to obtain a security clearance.
The military is an excellent place to obtain a security clearance.
![]() Once you have a security clearance, the number of jobs that are open to you increases significantly.
Once you have a security clearance, the number of jobs that are open to you increases significantly.
Links to Sites
![]() DEFCON Groups www.defcon.org/html/defcon-groups/dc-groups-index.html
DEFCON Groups www.defcon.org/html/defcon-groups/dc-groups-index.html
![]() 2600 Groups www.2600.com/meetings/
2600 Groups www.2600.com/meetings/
![]() Linux User Groups (LUGs) www.linux.org/groups/
Linux User Groups (LUGs) www.linux.org/groups/
![]() The Snort Intrusion Detection System www.snort.org
The Snort Intrusion Detection System www.snort.org
![]() Snort User Groups www.snort.org/community/usergroups.html
Snort User Groups www.snort.org/community/usergroups.html
![]() CISSP Certification www.isc2.org
CISSP Certification www.isc2.org
![]() SANS GIAC Certifications www.giac.org/certifications
SANS GIAC Certifications www.giac.org/certifications
![]() IAM and IEM Certifications www.securityhorizon.com
IAM and IEM Certifications www.securityhorizon.com
![]() IAM and IEM Information www.iatrp.com/main.cfm
IAM and IEM Information www.iatrp.com/main.cfm
![]() The Black Hat Briefings www.blackhat.com
The Black Hat Briefings www.blackhat.com
![]() The DEFCON Conference www.defcon.org
The DEFCON Conference www.defcon.org
![]() The Interz0ne Conference http://interz0ne.com/
The Interz0ne Conference http://interz0ne.com/
![]() The ShmooCon Conference www.shmoocon.org
The ShmooCon Conference www.shmoocon.org
![]() Government Job Listings www.usajobs.opm.gov
Government Job Listings www.usajobs.opm.gov
![]() Job Search Engine Monster.com www.monster.com
Job Search Engine Monster.com www.monster.com
Mailing Lists
![]() Subscribe to different Security Focus mailing lists http://securityfocus.com/archive/1.
Subscribe to different Security Focus mailing lists http://securityfocus.com/archive/1.
![]() Subscribe to the Full Disclosure mailing list www.netsys.com/full-disclosure.
Subscribe to the Full Disclosure mailing list www.netsys.com/full-disclosure.
Frequently Asked Questions
The following Frequently Asked Questions, answered by the authors of this book, are designed to both measure your understanding of the concepts presented in this chapter and to assist you with real-life implementation of these concepts. To have your questions about this chapter answered by the author, browse to www.syngress.com/solutions and click on the “Ask the Author” form. You will also gain access to thousands of other FAQs at ITFAQnet.com.
Q: There isn’t a local 2600 or DC Group in my area. What can I do?
A: Start your own group. Becoming a DC Group organizer is easy. Instructions and information on starting a DC Group in your area can be found at www.defcon.org/html/defcon-groups/dc-groups-index.html.
Q: Sometimes it seems like the best way to get name recognition is by getting arrested. Why is that?
A: This is a misconception. A few, highly-publicized arrests have led to lucrative jobs after the attacker was released from prison. In most cases though, you just get a criminal record, and no one wants to hire you. Employers don’t trust criminals, and INFOSEC positions all require some level of trust. An employer has to be able to trust you to protect, not attack, his network.
Q: I really feel uncomfortable speaking in front of groups. Is there any other way to get my name out there in a positive way?
A: While presentations at security conferences are a great, high-profile, way to get your name out there, it isn’t the only way. Well-written, technical white papers submitted to online sites like Security Focus (www.securityfocus.com) or to print publications will go a long way toward accomplishing the same thing.
Q: Should I take an INFOSEC position that may not be exactly what I’m looking for to get my foot in the door and start building experience?
A: No one can answer that question but you. Taking a job related to your ‘dream job’ may be a great way to get your foot in the door, but it can also be demoralizing if you are unhappy with the work. In the end, you’ll need to weigh the positives against the negatives and determine the best decision for your circumstance.
Q: It seemed like you really pushed the military and government in this chapter. Why is that?
A: We didn’t really push those options, but unlike a lot of work in the commercial sector, you can obtain these types of jobs with little or no experience. Since your goal is to get that first job in this field, it is important to present all of the options available to you as you begin your quest.
Q: I have been to hacker cons for years, just as a participant; is just attending good enough to put down for a job?
A: If you have not been active in the conference, I would not recommend it. But if you have done any presenting, participated in a contest or panel, or assisted in the running of the conference, I would put that down. Companies want to see that their prospective employees have a life outside of work, and if it is on their own time, and it involves developing their skills for that job, all the better.
Q: So if I want penetration testing or vulnerability assessment for a career, and I don’t have any experience with Nessus or other scanning/testing software, I just need to download it and run it a few times?
A: That is a start. Get familiar with the way it works; if you have been able to setup an attack lab as described in further chapters, then that’s the place where you need to run it. Figure out what any problems or issues you run into are and how to get past them. See what kind of results or false positives you get back, and document them. There are lots of free resources you can access and use them to build your own skills and resume material. Like I said before, “you know more than you know.” Then you can honestly say on your resume, “experience with industry standard penetration testing and assessment software,” which is a big plus, and a requirement for many INFOSEC engineer positions.