CHAPTER 6 Threats and Vulnerabilities
Overview
After the initial chapters that provided an overview of the risk landscape, in Chapter 4, we took an initial look at the components of the information security landscape – assets, threats, vulnerabilities, and controls. We then began a deeper look at these components. In Chapter 5, we looked at assets, including asset types, their classifications, and characterizations.
In this chapter, we will take a close look at threats. At the end of this chapter, you should have a clear understanding of the different aspects of threats including:
- Threat models, integrating the components of a threat
- The forces that could act upon an asset (agents)
- The methods by which these agents could affect an asset (actions)
- Vulnerabilities and their relevance to threats
Introduction
We have defined threats as the capabilities, intentions, and attack methods of adversaries to exploit or cause harm to assets. This is consistent with the NIST 800-30 definition of a threat as “any circumstance or event with the potential to adversely impact organizational operations and assets, individuals, other organizations or the nation through an information system via unauthorized access, destruction, disclosure or modification of information, and/or denial of service.”1 Once the organization has identified and characterized its assets, the next step in the analysis of its information security requirements is an analysis of the threats faced by the organization. We saw in the last chapter how many of our daily actions revolve around the availability of assets, and how we take those assets for granted. What happens if access to these assets suddenly goes away?
As an information security analyst, you will routinely be asked to estimate the importance of emerging threats. Is the fact that Microsoft just found out that Internet Explorer is vulnerable to cross-site scripting attacks a serious-enough threat that all computers in the organization must be forced to upgrade within the next 24 hours? This is analogous to the estimation that Florida residents like us have to make every time we read about a hurricane developing in the Atlantic – is the threat this time serious enough that we should finally buy a generator in case the power fails for an extended period?
Threat models
Threats arise from motivated people (agents) taking specific actions to exploit assets. The interactions between relevant agents, actions, and assets constitute the threat model facing an organization. This is represented in Figure 6.1. In the rest of this chapter, we use part of the VERIS2 incident classification model, the piece dealing with threat, as the basis for discussion. While some of the specific agents and actions discussed in this chapter are based on VERIS, the idea of threats being the actions of agents on assets is quite generic. We have already discussed assets. In this chapter, we focus on the remaining components of a threat – agents and actions.
Sidebar – Microsoft STRIDE threat model3
VERIS is one of many threat models that can help classify a threat. Another model is the Microsoft STRIDE model, named after the six classes it uses to categorize a particular threat.
Spoofing an identity. An example of identity spoofing is illegally accessing and then using another user's authentication information, such as username and password.
Tampering with data. Data tampering involves the malicious modification of data. Examples include unauthorized changes made to persistent data such as that held in a database or alteration of data as it flows between two computers over an open network such as the Internet.
Repudiation. Repudiation threats are associated with users who deny performing an action without other parties having any way to prove otherwise – for example, a user performs an illegal operation in a system that lacks the ability to trace the prohibited operations. Non-repudiation refers to the ability of a system to counter repudiation threats. For example, a user who purchases an item might have to sign for the item upon receipt. The vendor can then use the signed receipt as evidence that the user did receive the package.
Information disclosure. Information disclosure threats involve the exposure of information to individuals who are not supposed to have access to it – for example, the ability of users to read a file that they were not granted access to, or the ability of an intruder to read data in transit between two computers.
Denial of service. A Denial of Service (DoS) attack forces the system under attack to reject service to valid users – for example, by making a Web server temporarily unavailable or unusable. You must protect against certain types of DoS threats simply to improve system availability and reliability.
Elevation of privilege. In this type of threat, an unprivileged user gains privileged access and thereby has sufficient access to compromise or destroy the entire system. Elevation of privilege threat includes those situations in which an attacker has effectively penetrated all system defenses and become part of the trusted system itself, a dangerous situation indeed.
The VERIS model is more general, allowing any threat including threats not yet discovered, to be modeled within the framework. It is also aligned with the academic literature on the topic as well as with standard risk models we consider later in the book. Hence our use of the VERIS threat model.
Threat agent
A threat agent is the individual, organization, or group that originates a particular threat action. Threat agents can be classified into three different types, each with different motivations, to initiate a threat:
- External agents
- Internal agents
- Partners
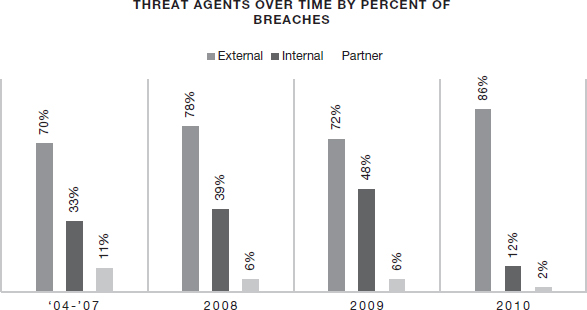
Figure 6.2 shows how the relative frequencies of the different threat agents classified by the VERIS system have evolved since 2004.4 It is clear that the number of internal attacks has reduced considerably since 2009 while external threat agents have increased during the same period.
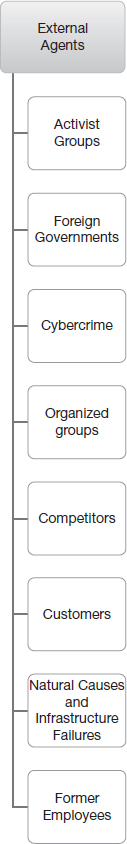
External agents
As the name suggests, external agents are agents outside the organization, with no link to the organization itself. According to the VERIS 2012 Data Breach Report,5 98% of the attacks in 2012 originated from an external agent. We look at the important external agents below. A quick list is given in Figures 6.3.
Activist groups
The Anonymous group has become popular in the last few years as a “hacktivist” organization, groups that mix political activism with hacking activities. A loosely formed group composed of hackers and other Internet enthusiasts, Anonymous members portray themselves as individuals who oppose all types of perceived oppression, Internet censorship, and surveillance by government agencies around the world. A brief listing of their latest exploits is included here.
Recent Anonymous exploits
August 2012: A group associated with Anonymous brought down several government sites in Uganda. This was done in protest to pending bills considered oppressive to members of the gay and lesbian communities in that country. They left the following message: “Anonymous will continue to target Ugandan government sites and communications until the government of Uganda treats all people including LGBT people equally.”
September 2012: Anonymous claimed responsibility for taking down the GoDaddy Domain Name Servers, which affected many businesses, from small community websites to larger companies such as JHill's Staffing Services, a recruitment & career consulting firm.
October 2012: Anonymous threatens to go after targets in Sweden in retaliation to the raiding of the ISP web host PRQ, which hosted The Pirate Bay and the Wikileaks site.
Foreign governments
According to a report issued by the Office of the National Counterintelligence Executive in October 2011,6 “sensitive US economic information and technology are targeted by intelligence services, private sector companies, academic and research institutions, and citizens of dozens of countries.” One well-publicized incident involved the suspected theft of the designs of military aircraft (Figures 6.4a and 6.4b).
According to the report, China is at the top of the list, with Chinese hackers attacking US private sector firms repeatedly. Russia's intelligence service also actively conducts cyber espionage against US targets to collect economic and technology information.
Mandiant report on APTs from China's PLA
On February 18, 2013, security analyst firm Mandiant released a report identifying a unit of the Chinese People's Liberation Army (PLA) it calls APT1, to be the source of some of the most damaging cyber-attacks on US government and corporate networks. Mandiant's investigations suggest that APT1 has operated since at least 2006 and has targeted a wide array of targets.
At the time of the report, Mandiant had analyzed APT1's intrusions against nearly 150 victims. Mandiant was able to confirm that APT1 was located in Shanghai and could recognize various elements of its tools, tactics, and procedures. The report revealed three identities within APT1 in order to convince readers that APT1 was populated by people, and was not a bot-network. Mandiant believes that these identities are soldiers, simply following orders given to them by superiors.
The existence of the organization for over 7 years suggests to Mandiant that APT1 is a government-sponsored entity, sustained by direct government support. Further investigations suggest that PLA Unit 61398 could be APT1, given the similarities between APT1 and unit 61398 and their locations. Mandiant reports that APT1 is likely to be housed in a 130,663 square foot 12-story high facility built in 2007.
Mandiant has identified 141 companies in 20 major industries that have been compromised by APT1. APT1 steals large volumes of valuable intellectual property from the companies it compromises, tracking the companies' network over several years. The average duration of an attack was 356 days, with the longest observed attack lasting 1,764 days, or 4 years and 10 months. APT1's focus seems to be to steal intellectual property, including technology blueprints, manufacturing processes, and business plans. In one case, Mandiant has observed APT1 stealing 6.5 terabytes of compressed data from a single organization over a 10-month time period. APT1's targets are companies in industries identified by China as strategic to their growth.
APT1 requires that its personnel be trained in computer security and be proficient in English. It recruits heavily from the Science and Engineering departments of universities such as Harbin Institute of Technology and Zhejiang University School of Computer Science and Technology.
But that's not all. Even US allies and partners use their access to US institutions to access information using a multitude of threat actions. Loss estimates from economic espionage range so widely as to be meaningless – $2-400 billion or more a year.
Industrial espionage
In December 2010, David Yen Lee was sentenced to 15 months in jail and ordered to pay more than $30,000 in restitution to Valspar, a maker of paints and industrial coatings. After returning from a trip to China, Lee, former technical director of new product development for Valspar's architectural group, quit the company. When Valspar workers examined the company laptop computer and BlackBerry device he turned in when he resigned they noticed traces of activities that suggested Lee was trying to cover his tracks on laptop usage. Closer examination unveiled Valspar trade secrets downloaded to the laptop.
Government involvement is widespread and not limited to attacks against the United States. The US government is involved in cyberwarfare as well. The New York Times7 claims that President Obama secretly ordered increased cyber-attacks against the computer infrastructure of Iranian nuclear facilities weeks after he assumed office. The same article alleges that US and Israel were involved in the deployment of Stuxnet, which temporarily took out 20% of the centrifuges operating in Iranian facilities.
DARPA's PLAN X
In 1958, the Defense Advanced Research Projects Agency (DARPA) was established to prevent strategic surprise from negatively impacting US national security and create strategic surprise for US adversaries by maintaining the technological superiority of the US military. Recently, DARPA released information on the start of “Plan X.” According to the agency, it seeks innovative research in four key areas, in support of Plan X. This is something many of you may like to follow as these guidelines can impact hiring plans for many military establishments and defense contractors:
Understanding the cyber battlespace: This area focuses on developing automated analysis techniques to assist human operators in planning cyber operations. Specifically, analyzing large-scale logical network topology characteristics of nodes (i.e., edge count, dynamic vs. static links, usage) and edges (i.e., latency, bandwidth, and periodicity).
Automatically constructing verifiable and quantifiable cyber operations: This area focuses on developing high-level mission plans and automatically synthesizing a mission script that is executed through a human-on-the-loop interface, similar to the autopilot function in modern aircraft. This process will leverage formal methods to quantify the potential battle damage from each synthesized mission plan.
Developing operating systems and platforms designed to operate in dynamic, contested, and hostile network environments: This area focuses on building hardened “battle units” that can perform cyberwarfare functions such as battle damage monitoring, communication relay, weapon deployment, and adaptive defense.
Visualizing and interacting with large-scale cyber battlespaces: This area focuses on developing intuitive views and overall user experience. Coordinated views of the cyber battlespace will provide cyberwarfare functions of planning, operation, situational awareness, and war gaming.
Cybercrime
In the late 1990s, when the commercial Internet was in its infancy, hackers were primarily “script kiddies:” usually a teenager who found an exploit script somewhere and decided to deface a web page just to show that the hacker was capable of modifying a website. Many of these scripts recklessly destroyed data on affected machines simply as proofs of concept.
Somewhere down the line, the script kiddies got smart. Why destroy machines when you can make money out of the user of that machine? Why replace a web page when you can sit at home and monitor all activity until you see something you like? Enter what we now call cybercrime. Cybercrime is an incredibly lucrative business, offering a higher profit with a lower probability of being identified and prosecuted than traditional crime such as bank robberies.
One popular cybercrime threat agents are the hackers involved with the Nigerian Scam, also known as the “419 Nigerian Scam” referring to an article in the Nigerian Criminal Code dealing with fraud. What follows is a sample email.
LAGOS, NIGERIA.
ATTENTION: THE PRESIDENT/CEO
DEAR SIR,
CONFIDENTIAL BUSINESS PROPOSAL
HAVING CONSULTED WITH MY COLLEAGUES AND BASED ON THE INFORMATION GATHERED FROM THE NIGERIAN CHAMBERS OF COMMERCE AND INDUSTRY, I HAVE THE PRIVILEGE TO REQUEST FOR YOUR ASSISTANCE TO TRANSFER THE SUM OF $47,500,000.00 (FORTY SEVEN MILLION, FIVE HUNDRED THOUSAND UNITED STATES DOLLARS) INTO YOUR ACCOUNTS. THE ABOVE SUM RESULTED FROM AN OVER-INVOICED CONTRACT, EXECUTED COMMISSIONED AND PAID FOR ABOUT FIVE YEARS (5) AGO BY A FOREIGN CONTRACTOR. THIS ACTION WAS HOWEVER INTENTIONAL AND SINCE THEN THE FUND HAS BEEN IN A SUSPENSE ACCOUNT AT THE CENTRAL BANK OF NIGERIA APEX BANK.
WE ARE NOW READY TO TRANSFER THE FUND OVERSEAS AND THAT IS WHERE YOU COME IN. IT IS IMPORTANT TO INFORM YOU THAT AS CIVIL SERVANTS, WE ARE FORBIDDEN TO OPERATE A FOREIGN ACCOUNT; THAT IS WHY WE REQUIRE YOUR ASSISTANCE. THE TOTAL SUM WILL BE SHARED AS FOLLOWS: 70% FOR US, 25% FOR YOU AND 5% FOR LOCAL AND INTERNATIONAL EXPENSES INCIDENT TO THE TRANSFER.
THE TRANSFER IS RISK FREE ON BOTH SIDES. I AM AN ACCOUNTANT WITH THE NIGERIAN NATIONAL PETROLEUM CORPORATION (NNPC). IF YOU FIND THIS PROPOSAL ACCEPTABLE, WE SHALL REQUIRE THE FOLLOWING DOCUMENTS:
(A) YOUR BANKER'S NAME, TELEPHONE, ACCOUNT AND FAX NUMBERS.
(B) YOUR PRIVATE TELEPHONE AND FAX NUMBERS – FOR CONFIDENTIALITY AND EASY COMMUNICATION.
(C) YOUR LETTER-HEADED PAPER STAMPED AND SIGNED.
ALTERNATIVELY WE WILL FURNISH YOU WITH THE TEXT OF WHAT TO TYPE INTO YOUR LETTER-HEADED PAPER, ALONG WITH A BREAKDOWN EXPLAINING, COMPREHENSIVELY WHAT WE REQUIRE OF YOU. THE BUSINESS WILL TAKE US THIRTY (30) WORKING DAYS TO ACCOMPLISH.
PLEASE REPLY URGENTLY.
BEST REGARDS
Thousands of emails would be sent out at a time. Inevitably, the fraudsters would receive a couple of responses.
In Nigeria, cyber cafes dedicate a number of their systems specifically to individuals intending to engage in fraudulent activities. They are known as “Yahoo Boys,” after the fact that these users create phony yahoo accounts to use for their schemes.
Government efforts to prevent financial cybercrime continue. In Nigeria, notices are pasted on walls of cafe owners, warning users of possible arrests for scammers who send fraudulent emails. But, generally speaking, users are learning to pay attention to the adage: “if it sounds too good to be true, it probably is.”
Defining cybercrime in the Philippines
A new cybercrime law in the Philippines that could see people jailed for 12 years is generating outrage among citizens and rights groups. The stated aim of the wide-ranging law is to tackle a multiplicity of online crimes, including pornography, hacking, identity theft, and spamming. It is the politician's response to police complaints stating they did not have the legal tools needed to follow up on complaints.
The problem is that this new law also includes a provision that puts the country's criminal libel law into force. Users posting comments online that would later be considered libelous by the courts would face a maximum prison sentence of 12 years and a sanction of $24,000. This in comparison with printed media libel fines of half of that amount and a prison term of 4 years.
And that's not all. The Cybercrime Act would allow law enforcement agencies in the Philippines to collect data and monitor all cyber communications without a warrant.
Organized groups
Some threats require the cooperation of multiple agents acting together. The organization of certain cybercrime groups is remarkable. For instance, websites exist that coordinate the sale and purchase of restricted information such as credit cards, social security numbers, bank account info, and more. These sites usually employ a large number of individuals, each with their own job duties.
- Admins: Run the escrow service and control membership
- Global Moderators: Supervise content and arbitrate any disputes
- Moderators: Monitor individual topic areas
- Reviewers: Evaluate quality of vendor products
- Vendors: Have permission to sell goods and services to forum members
- Members (fraudsters): Purchase the goods
In order to become a vendor you have to provide a set of credit card numbers to a reviewer. This person goes out and makes purchases using those numbers. If the cards are mostly valid, you are accepted as a vendor (Figure 6.5). Below is an example of a vendor being rated:
Review Results: Zo0mer's dumps. Within 24hrs, I received a total of 50 dumps. … 41 accepted, 9 declined – however he will replace declines if notified within 48hrs I also done a store test on 4 cards … 3 was accepted £500, £1.2K and £1.8K, US card decline Product: 9/10 Service 9.5/10
One example of such site was CarderPlanet. CarderPlanet was a criminal organization founded in 2001. It operated and maintained the website www.carderplanet.com for its criminal activities. By August 2004, the site had attracted more than 7,000 members. Although most of the postings on the forum were in Russian, and most of the CarderPlanet members were from Eastern Europe and Russia, the forum had a significant English-speaking component.8
The organization was set up in a manner similar to the mafia with the highest ranking members, or “the family,” having titles such as the Godfather and “capo di capi” (or boss of all bosses). It was shutdown in 2004 after the arrest of some of its senior members. According to the US Secret Service, “the network created by the founders of CarderPlanet … remains one of the most sophisticated organizations of online financial criminals in the world. This network has been repeatedly linked to nearly every significant intrusion of financial information reported to the international law enforcement community.”9
Competitors
Competitors are always interested in gaining advantage over the competition. This is true not only in private industry but also in politics. In 2003, internal memos from Democrat minority leaders were distributed to GOP-friendly media. “At first, the Republican majority denied any G.O.P. complicity after the memos were leaked and published. The documents detailed how Democratic senators had strategized and consulted outside interest groups dedicated to opposing some of President Bush's more conservative judicial nominees. But after the police moved in last week, Senator Orrin Hatch, the Utah Republican who is the Judiciary Committee's chairman, reversed himself and announced that he had been ‘shocked’ to find out that it was a member of his own staff who had hacked into the minority's computer files.”10
Customers
Customers can easily be agents as well, internal or external, depending on where you draw the boundaries of your service. With the Student Information System, for instance, IT has the student users as well as the administrators of the different modules of the SIS application: Financial Aid, Accounts Payable, Financial Aid, etc. These are normally known as “Functional Users.” As customers, these users at times also require functionality and privileges that, while could make their job easier, could also put the University at risk. Someone from Financial Aid, for instance, with access to student Social Security Numbers, could feel tempted to sell a list of those in the hacker market.
Natural causes and infrastructure failures
In the United States we have wild fires and earthquakes in the west. Tornadoes in the Midwest. Hurricanes and flash floods on the East Coast and along the Gulf States. Practically no area of the country is 100% safe. And you still have the human intervention: leaky pipes, accidental building fires, etc. All of these are external, natural disasters that could affect a business' IT infrastructure. When the IT infrastructure fails the financial damage can be considerable. That's what happened with Sears in 2013. “… the five-hour failure, in the rush just after the holidays, cost Sears $1.58 million in profit, according to the lawsuit. (Sears did $12.3 billion in sales during the fourth quarter but lost $489 million.) The server farm ran on generators for eight days, burning through $189,000 in diesel fuel.”11
Former employees
Disgruntled employees are a particularly dangerous type of agent, since they oftentimes have insight on the internal workings of the company, and they are capable of using internally known vulnerabilities to gain access and damage the business.
In May 2013, a criminal complaint was unsealed on Thursday in federal court in the Eastern District of New York charging Michael Meneses – who was arrested earlier that day in Smithtown, Long Island – with hacking into the computer network of a company that manufactures high-voltage power supplies, causing the company over $90,000 in damage. “He employed various high-tech methods to hack into the victim company's network and steal his former colleagues' security credentials, including writing a program that captured user log-in names and passwords. He then used the security credentials of at least one former colleague to remotely access the network via a virtual private network (VPN) from his home and from a hotel located near his new employer, corrupting the network.”12
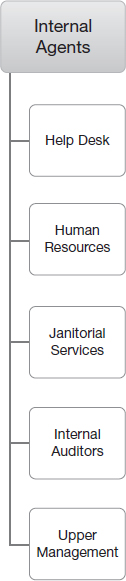
Internal agents
Internal agents are people linked to the organization, often as employees. They include your expected agents, the sys admins, the Help Desk assistants, the software developers. But other unexpected individuals such as janitorial staff can also be threat agents (Figure 6.5).
Help Desk
Help Desk employees may be assigned certain privileges that, either through error or misuse, could affect the operations of a company. It is not uncommon to allow Help Desk employees the ability to change passwords for users, after checking their identities. This privilege opens the door for potential bribery and blackmail of the employee, especially when the activity goes unchecked.
Human resources
The hiring and termination of personnel in an organization, normally handled by the HR department, kicks off a number of activities potentially including the assignment and removal of privileges in IT systems. These actions are usually known as onboarding and offboarding. If these are performed automatically, the consequences could be disastrous.
In 2005 a small community bank in the State of Florida had to retrieve all of its employees' emails from backup tapes after an entry error in the HR system laid off all of its employees and all their email accounts were deprovisioned.
Janitorial services
Server rooms and datacenters are normally off limits to anyone without a need to be there. However, not all servers go in server rooms. It is not uncommon in an University environment to have servers in common offices, without physical protection or redundancy.
Back in 2003 a helpful janitor at the University of South Florida, after noticing that a particular office was a bit dirty, decided to vacuum the room. He unplugged the UPS to plug in the vacuum cleaner and neglected to plug it back in when he was done. The UPS ran out of power and the College was left without email until the next day, when the local administrator came back into the office.
Internal auditors
Auditors come in a variety of different flavors. Some are willing to work with administrators and understand different priorities, resource allocation, and how IT processes fit in the overall mission of the organization. Others are simply interested in pointing out the perceived failures of the IT department. Some are fully prepared to discuss database schemas and network routing, as well as cash collection and financial aid. Some in the industry consider auditor to be the consummate generalist, the proverbial Jack of all trades, but not necessarily the master of any.
The primary concern of auditors is compliance. IT systems must be compliant with local, state, and federal laws. They also must ensure that all official policies and procedures adopted by the organization are followed. With that in mind, it is necessary to emphasize that compliance is different from security. And it is this difference that at times may turn an auditor into a threat agent.
For instance, assume your organization has a policy stating, “all employee ID numbers will be encrypted when stored electronically.” IDs are stored on a database server, which, for the sake of argument, is only turned on when data is needed. The server is inside an access-controlled facility, and you are the only person with access to the box. From your perspective, the risk of a leak or data loss is extremely small. However, as we will see in future chapters, regulatory compliance, federal and state laws established with the intent to protect users' privacy, are often single minded in their purpose and do not consider the overall system security as a whole, instead focusing simply on the piece it needs to protect. Therefore, any auditor, internal or external, will insist that the data still must be encrypted or the policy amended if the organization is assuming the risk. Even if your organization will have to spend thousands of dollars in order to encrypt the data.
Auditors may also affect IT operations. In the State of Florida, if your server room is not up to code because power is stringed through the use of extension cords, Fire Marshalls are authorized to disconnect the power immediately, even if critical processes are brought down because of the disconnection.
Upper management
Managers can be considered a threat agent in multiple ways. But perhaps the most threatening would be top management's lack of support for IT in general and lack of understanding of security concerns.
IT systems are ubiquitous to organizations nowadays, and yet people do not realize the dependency that creates. In a university, faculty paychecks, registration, transcripts, and financial aid, all depend on the fact that IT systems are available and operating properly.
Most of IT operates in a world where “no news is good news.” While that is nice from the operational point of view, it creates a disconnect with users. It is difficult to justify the expenses associated with purchasing a new server if, from the end user's perspective, services are still being offered with no impact on performance. In the long run, IT's success could potentially create its own downfall if management is not reminded constantly of the business dependency on services IT provides.
New University: Florida Polytechnic
In 2012, Florida State Officials approved the creation of a new accredited State University, Florida Polytechnic, or FPU. FPU was previously part of the University of South Florida System. This decision by the state government of this new entity created challenges for IT, providing an example by which top management decisions create trickle-down problems that could potentially have adverse effects on the overall security of an organization:
Every software license had to be reviewed since computers and servers were now owned by a new University and not the University of South Florida. Failure to do so could result in severe legal issues.
IT personnel had to be reallocated to provide support and move content from the FPU servers to other servers owned by USF, leaving certain areas thinly supported.
While some employees were transferred to the system, many were laid off. This created the perfect potential scenario for a disgruntled employee to become a threat agent by committing fraud.
Partners
Partners include any third party sharing a business relationship with the organization. This includes suppliers, vendors, hosting providers, outsourced IT support, etc. Some level of trust and privilege is usually implied between business partners (Figure 6.6).
Consulting services and contractors
This category also includes installation services and maintenance services. These are services paid for by an organization in order to perform a specific job or to augment local staff.
Consulting organizations do their best to comply with any special requirements of their clients. However, clients with special needs may get blindsided if an overlooked detail is extremely important to the client. Consider the recent case of the security leak at the National Security Agency (NSA) involving Edward Snowden. Mr. Snowden was an employee of Booz-Allen Hamilton, a contractor that did a lot of technology work for the NSA and other sensitive federal agencies.
From June 5 to June 21, 2013, the Guardian newspaper revealed extremely confidential orders permitting the NSA to gather information about US citizens. Lawmakers and the public were surprised by the revelations. Reactions ranged from calling Mr. Snowden a hero for bringing the activity to light, to calling him a traitor for revealing security procedures that have kept America safe. At the time of this writing, his eventual fate is unknown. The US Govt. is working to have him brought to the US for trial (Figure 6.7).
However, from an information security perspective, the incident brought several things to attention. Given the nature of the institution, it is impossible to assert how Mr. Snowden got his data out of the NSA, until it is revealed in a court trial, federal testimony, or other similar outlet. However, it has been speculated that Mr. Snowden used a USB thumb-drive to save his data. Sensitive organizations typically disable these ports on computers to prevent such leakage. So, many experts are surprised at this possibility at the NSA. It is also remarkable how an employee of a partner had access to such sensitive documents.
In the early 2000s, Sun Microsystems was responsible for the installation of several high-performance systems at the University of South Florida. In order to facilitate their work, maintenance engineers from Sun would set up all boxes, including ones set up in other organizations, with the same administrator login and passwords. And to add to the lapse in security, that password was based on a dictionary word.
Cloud services
Cloud services are a very large class of services. NIST13 lists five essential characteristics of cloud computing: on-demand self-service, broad network access, resource pooling, rapid elasticity or expansion, and measured service. It also lists three “service models” (software, platform, and infrastructure), and four “deployment models” (private, community, public, and hybrid) that together categorize ways to deliver cloud services.
These services were all considered “outsourcing” at one point in time. But since the word outsourcing is linked with people losing their jobs, the industry reinvented itself and was rebranded as services “in the Cloud.”
Normally when a company moves some of its services to the cloud there is an assumption of improved redundancy, reliability, with multiple servers hosting failover applications in multiple geographic locations. While that is the case in most situations, it is not always the case. Businesses should never make that assumption. When services are moved, here are a few things to check:
- Does the datacenter have the required security certifications?
- Where are the Center's geographic locations?
- What controls are positioned to protect the data?
It is also crucial to have an exit strategy from the get-go. Establish the methods by which, in an emergency, the data could be moved to another location. A failure in any of these points could move the outsourced service provider from a partner to a threat agent.
Examples of issues with Cloud providers
Dropbox
In July 2011, the cloud data storage company made sweeping changes to its terms and license agreements as a result of an earlier issue involving a software bug in its authentication system. “By submitting your stuff to the Services, you grant us and those we work with to provide the Services worldwide, non-exclusive, royalty-free, sublicenseable rights to use, copy, distribute, prepare derivative works (such as translations or format conversions) of, perform, or publicly display that stuff to the extent reasonably necessary for the Service.” Dropbox quickly reversed its position once the customers started refusing the agreement and pulling their data back.
Salesforce is known for its Customer Relation Management (CRM) software, as well as its cloud offerings: the Sales Cloud, for sales managements, and the Service Cloud, a call center-type service. However, Salesforce does not have its own datacenters. It uses another company, Equinox, and its DR structure to maintain its services.
In July 2012, a brief, one-minute power outage in one of Equinox's Data Center locations in California caused a cascade of problems that eventually took out the entire Salesforce network for nearly 6 hours.
Outsourcing your server room infrastructure is a popular thing to do. It gets the physical worries out of the way and allows organizations to worry about the important part of their business. This is particularly true for news blog sites and certain social media venues.
In October 2012, Hurricane Sandy slammed the East Coast near Atlantic City. Readers woke up the next day disappointed that some of their favorite news sites were brought down, including The Huffington Post and Gawker. These sites used the ISP Datagram as their primary platform. Datagram's datacenter was flooded, and fuel lines feeding the generators failed, bringing the entire datacenter down (Figure 6.8).
Vendors and suppliers
When vendors or suppliers are not able to provide needed resources, or do not exercise proper quality control on devices, or do not properly evaluate the business relationships they maintain, the effect to a business may be considerable.
In May 2013, Nokia won an injunction against HTC in the Netherlands, related to the sale of HTC One android phone; HTC was apparently using a microphone in the HTC One which is developed by STMicroelectronics, and Nokia apparently has exclusive rights for the use of this microphone in its devices.
Threat action
The agent is the first part of the threat, but until an agent performs some actions to hurt an asset, no threat is created. The action is the activity performed by the agent in order to affect the confidentiality, integrity, or availability of the asset. Creating an exhaustive list of actions is futile since new threat actions are limited only by the ingenuity of the agents. However, most common threat actions may be classified into the following categories:
- Malware
- Hacking
- Social engineering
- Physical
- Error
- Environment
Malware
Malware is short for “malicious software.” It is software specifically designed to damage, disrupt, steal, or in general inflict some other “bad” or illegitimate action on computers. Viruses, worms, Trojans, and bots are all examples of malware.
The number of malware in the wild has increased tremendously, going from 1,300 in 1990 to 50,000 in 2000, then to more than 200 million in 2010.
Viruses
Viruses propagate with the use of a “host” file that requires human interaction for it to activate. The infected file itself may reside on a computer's hard drive, but the machine would not be infected until the file is executed. A virus propagates when someone transfers that infected file to a new machine and the file is executed on the new host.
The first piece of code considered to be a virus was created in 1971 by an employee of the so-called BBN, now Raytheon BBN. BBN built packet switching networks for ARPANET, the precursor for the Internet. The software called Creeper was designed as a proof of concept for a self-replicating software. It would jump to from one server to another, installing itself, then removing the previous copy and displaying the message “I am Creeper, catch me if you can” on the screen of the new host.
The Melissa Virus outbreak was the one of the first viruses to impair corporate networks. Melissa was different from other viruses because of the speed with which it spread. It disguised itself as an email with the subject “An Important Message From <someone you know>.” The email carried a Microsoft Word document with a macro virus, a virus that would execute automatically when the file was opened.
Machines infected with the Melissa Virus would present a couple of symptoms:
- Unexplained shutdown with the error message shown on Figure 6.9
- Word documents opened while the machine was infected would display quotes from episodes of the TV show “The Simpsons”
- Random files would be selected to be emailed out as the carriers of the virus to 50 users present in the computer's address book.
Besides the end user–centered problems, Melissa caused severe problems to the email infrastructure of corporations due to the load infected machines imposed on email servers. The author of Melissa virus was caught and sentenced to 20 months in prison and $5,000 in fines.
Worms
While infection and propagation of viruses depends on human intervention, worms use operating system or application vulnerabilities to infect and network access to exploit the same vulnerability on other machines.
The first Internet worm was the Morris Worm, released in 1988. Although like the Creeper virus this worm was intended to be a proof of concept, due to a coding error the software had a fixed chance to spawn multiple copies of itself on the infected machine, causing the host's load to increase and sometimes eventually crash.
The SQL Slammer worm, released in January 2003, is to date one of the fastest spreading worms in history, taking advantage of a buffer overflow vulnerability in Microsoft SQL Server 2000 to replicate. Results of SQL Slammer infections around the world were particularly visible:
- Many ATM Machines from Bank of America were unavailable when the Slammer virus hit.
- Continental Airlines had cancelled and delayed flights because ticketing counters were infected.
- The City of Seattle 911 system was inoperable.
The biggest culprit was not the infection itself, but the alarming rate at which the worm tried to propagate. A single infected machine had the ability to flood the network within minutes, effectively creating a Denial of Service Attack by using up all the network bandwidth available. Estimates are that 90% of all vulnerable servers on the Internet were infected within 10 minutes of the worm's release.
Bots
One of the latest botnets discovered by the security industry is known as ZeroAccess. As of September 2012, it is estimated that the ZeroAccess malware has been installed about 9 million times. Bots are general use software programs, empty husks, which contact a Command and Control server for their orders. The ZeroAccess bot uses a peer-to-peer like network to download plugins from the C&C servers. These plugins carry out tasks designed to generate revenue for the botnet operators. It accomplishes this task with two primary methods: Click Fraud and Bitcoin Mining.
Click fraud happens in connection with a business using Pay Per Click (PPC) advertising model. The motivation varies. Often hackers are hired to try to drain out competitors' advertising budget. The most frequent perpetrators of click fraud, though, are publishers themselves, many of whom run successful pay per click scams.14
Bitcoin is touted to be the new virtual currency to replace cash in the Internet. Much like the Federal Reserve is in charge of regulating our currency, regulation of Bitcoins is delegated to a peer-to-peer network composed of computers running a Bitcoin client, or a Bitcoin Miner. When you install a Bitcoin Miner on your computer, your machine essentially works as a Bitcoin bank, issuing the currency, validating transactions, etc. Individuals usually become part of a “mining pool” and receive payout bitcoins as part of their payment. Obviously, botnets are perfect for this activity.
Hacking
According to the VERIS Data Breach Report for 2011, 81% of the breaches in 2011 involved some type of hacking action. Some of the methods used to gain access to a computer are also used by malware code. The primary difference between a hacking breach and a malware infection is that malware infections propagate automatically, without intervention from a human. Although they both may use the same methods of penetration, a hacking breach is an attack targeted towards a specific host or organization, directed by a hacker.
Brute-force attack
Brute force is a method by which a hacker tries to gain access to an account on the target system by trying to “guess” the correct password. Usually this is an automated process that may take hours to complete.
Although the “made for TV” versions of this attack sound a bit far-fetched, with the hacker simply trying a few passwords and easily accessing to the computer, it is not too far from the truth. An analysis of the 450,000 passwords leaked with the Yahoo attack mentioned previously in this chapter brought up the following pearls of wisdom:
- 160 Yahoo accounts had the password “111111”
- “password” was used as the password 780 times
- “ninja” was used 333 times (not as “ninja” as they'd like it to be)
What follows is a sample of inadequate passwords, the 25 worst passwords of 2011 (Table 6.1) as extracted by antivirus vendor ESET:15
Default credentials attacks
Appliances designed to be connected to a network usually come from the factory with a default password. So do certain software applications and databases. Default Credential attacks refer to incidents in which a hacker gains access to the system or software protected by standard preset (and therefore widely known) usernames and passwords.
There are many websites that collect lists of default passwords. CIRT.net, for instance, maintains a database with 1937 default passwords, from 467 vendors like Microsoft and Verizon.
Microsoft's SQL Server 2000 install will complete and leave a database administrator account “sa” with no password needed.
In July 2012, a major ISP from Holland discovered that costumer accounts were vulnerable due to default credentials. Their user id were set to be their zip code + their street address, and the initial login password was “welkom01.” When they performed a security check on the accounts they discovered that 140,000 customers never bothered changing the initial default password.
A slight variation on the theme is a Wireless Access Point (WAP), like the one you probably have at home. In order to associate with your home router and gain wireless network access, all you need is the SID (the name of the network), which is usually broadcasted and discoverable by your computer, and the router password. There are two popular passwords for WAPs as delivered by your Internet Service Provider: either the MAC address of the router or another hexadecimal value. Both can easily be found written on the underside of the WAP. All a hacker would need is quick access to your network, during a get together or a party, and voila, instant access.
Jailbreaking iPhones
In 2010 universities around the world started observing a new rash of port scans targeting port 22, a port dedicated to the encrypted console daemon SSHd. When the IPs were tracked down, all belonged to jailbroken iPhones.
The term “jailbroken” refers to the fact that the iPhone IOS Operating System had been replaced by another Operating System by the iPhone user. Jailbreaking a device is easy and removes certain limitations Apple imposes to app developers. But, as it turns out, it also adds a SSH server to the iPhone, with the default “root” account and a default password of “alpine.” A quick scan of the network and users with jailbroken iPhones with default passwords were “owned” by a hacker.
Buffer overflow attacks
Let's start with an analogy. A buffer overflow is like dumping 1 gallon of water in a container that only holds one cup. The water will eventually overflow and use other spaces where it was not supposed to go. Usually the spill is wasted. But in the computer world, a precisely formed spill can yield the keys to the kingdom.
In computing, a buffer overflow happens when a program buffer or container is not dimensioned properly, and the content that was supposed to fit in the memory “spills over” other parts of the computer memory. If the contents of the spillover are crafted properly, the computer may be “tricked” into believing that the spillover is actually part of the program that needs to be run.
Hello World on the PS Vita
Among hackers, Sony's PSP is a favorite for its ease of penetration. The portable console can be altered to play custom games and programs (known as homebrews). With the unveiling of its new portable, the PS Vita, Sony hoped that the days of the hacked portable were gone. Alas, they were wrong.
A Japanese hacker going by the handle Wololo posted the first Hello World on the PS Vita. Using a buffer overflow, he has found a way into the PS Vita, and with many PSP Game exploits still around and not published for the whole homebrew and hacking community this means that in the short term homebrew is here on the PS Vita.
The Code Red worm used a buffer overflow by connecting to a vulnerable Microsoft IIS Server and sending it a large string of N's (capital letter N). At the end of this string, it would send a snippet of code to be executed by the web server. Simple and efficient!
Compiler protection against known buffer overflow problems
New compilers will warn users when they try to compile programs containing dangerous function calls prone to be exposed to BOs:
user@server ∼/user $ gcc simple.c -o simple /tmp/ccECXQAX.o: In function ‘main’: simple.c:(.text+0x17): warning: the ‘gets’ function is dangerous and should not be used.
Cross-site scripting (XSS) attacks
XSS is one of the most common web-based attacks. It occurs when a website allows a malicious user to enter information with malicious content in it. The content is usually javascript code executed on the client when other users are visiting that site. Common targets for these attacks are web-based forums. The software powering these sites often do not validate the user input, allowing users to enter html or java code. The code is then published on the forum for other users to see and execute (Figure 6.10).
According to Accunetix,16 a company that specializes in web-based vulnerability assessment tools, exploited XSS sites are commonly used to perform the following malicious activities:
- Identity theft
- Accessing sensitive or restricted information
- Gaining free access to otherwise paid-for content
- Spying on user's web browsing habits
- Altering browser functionality
- Public defamation of an individual or corporation
- Web application defacement
- Denial of Service attacks
Below is a basic example of an XSS attack. Start with the code below for an ordinary web page that gets a variable from the URL that “should” be a name, then displays a warm introduction message to the screen.
<?php $name = $_GET[‘name’]; echo “My name is $name<br>”; echo “<a href=“http://xssattackexamples.com/”>Click to Download</ a>”; ?>
A malicious hacker could craft the following URL to
index.php?name=guest<script>alert(‘owned’)</script>
This is a non-persistent XSS vulnerability, and it is by far the most common type of attack. It happens when the data provided by a web client is used by server-side scripts to generate a page of results for that user, without validating the request.17
SQL injection attack
SQL injection is an attack technique used to exploit how web pages communicate with back-end databases. An attacker can issue commands (in the form of specially crafted SQL statements) to a database using input fields on a website.18 As you can see, SQL injection is remarkably similar to an XSS. The primary difference being that an XSS attack is executed at the web front end, whereas the SQL attack is executed at the server. The problem in both cases is that user input was never validated properly.
As an example, let's assume a website that allows you to enter your last name in a text box, hit submit, and then displays your first name and your phone number. The query the web server sends to the back-end database may look something like this:
SELECT fname, phone FROM contacts WHERE lname = ‘doe’
But what if we entered the following in the text box:
doe’ OR ‘1=1’;
Since the ‘1 = 1’ condition is always true, the database would return all of its contents. But it gets worse.
doe’ exec master.dbo.xp_cmdshell ‘iisreset/Stop’
If the database server allows shell escapes (commands could be executed outside the database environment, on the actual operating system itself), the above input would stop the IIS web server on the machine.
In October 2012, the hacktivist group Anonymous used SQL Injection attacks against vulnerable web front ends to disclose information stored in database servers of 50 universities around the world, including Princeton, John Hopkins, and Rutgers.19
Misuse
Misuse involves the unauthorized use of assets. In most cases, misuse is a result of the absence of a common security principle known as “need-to-know.” With the need-to-know principle, an individual only has access to an asset if he or she needs access to that asset in order to perform his job. And that principle applies independently of the position the person has in the organization.
Abuse of privileges
Abuse of privileges occurs when an employee uses his or her position and/or access to assets in an improper manner, causing damage to the asset and/or the organization.
As an IT person, the first thing that comes to mind is a systems administrator misusing their privileges. Take IT contractor Steven Barnes, for example. Steve worked for Blue Falcon Networks, now known as Akimbo Systems. In 2008, Steven was ordered, by a court in California, to pay $54,000 restitution to Akimbo and spend 1 year and 1 day in jail. The reason? Steven used his access to log in to Akimbo's Exchange email server and remove restrictions set up on that server keeping spammers from using it as a spam proxy. The result was the equivalent of a Denial of Service attacks, with Akimbo's email system going down as soon as spammers found the opening. According to Steven, he opened the flood gates as retaliation after coworkers from Blue Falcon Networks, now known as Akimbo Systems, came to his home and took away his personal computers by force in 2003.20
Fraud and embezzlement
The Counterfeit Access Device and Computer Fraud and Abuse Act (18 U.S.C.A. § 1030), passed by Congress in 1984, was the first attempt by the Federal government to deal with the issue of fraud in the IT arena. The act also criminalizes the use of computers to inflict damage to computer systems, including their hardware and software and was primarily tailored towards hackers. Since then, the CFAA has been used to prosecute employees who use their position and access to assets to defraud and embezzle money from organizations and their customers.
Fraud and embezzlement cases using IT resources are abundant, especially when individuals find themselves in financial hardship. This has led companies to require a credit check for those employees with access to assets that could potentially lead to fraud.
In August 2012, a Knoxville woman began to serve 5 years on probation after admitting she committed computer fraud while working as a retail operations manager for SunTrust Bank.21 Her job was to ensure branches in her region followed internal security practices, according to prosecutors. She had access to the financial records of SunTrust's customers through her work computer, according to the US attorney. Below are some more examples of computer fraud:
- Sending hoax emails intended to scare people (scareware or ransomware)
- Illegally using someone else's computer or “posing” as someone else on the Internet
- Using any type of malware or emails to gather information from an organization or a company with the intent of using it for financial gains
- Using the computer to solicit minors into sexual alliances
- Violating copyright laws by downloading and sharing copyrighted material without the owner's permission
- Using a computer to change information, such as grades, work reports, etc.
Use of unapproved software
Employees may become threat agents when they go against company policy and install software application on their computers. Software installed in desktops or smartphones may provide hackers a way into restricted company assets.
Allowing users to install software on their desktops is a particularly problematic issue for universities. By default, universities are supposed to be open, unrestricted, places where curiosity and research come together to foster innovation. On the other hand, that same openness could end up exposing research data and other information assets to threat agents with dire consequences to the department as well as to the individual.
In the late 1990s, a perfect example of the issues associated with these installations was Bonzi Buddy. The Bonzi purple gorilla was cute and adorable, a favorite of many university users on campus. It roamed around their desktops and kept users entertained. Unfortunately, it also gathered information about the user's surfing habits, store preferences (spyware), and displayed related advertisement on the screen (adware). Finally, it used up so much power from the CPU that all other applications would slow down to a crawl (Figure 6.11).
Because of their openness, most universities do not have a policy prohibiting users to install software on their computer, but many other organizations do. In August 2012, the US District Court for the Western District of Oklahoma held that an employee who downloaded shareware from the Internet in violation of company policy may be liable under the CFAA for using the downloaded software to obtain confidential company documents. In Musket Corp. v. Star Fuel of Oklahoma LLC, the court held that anyone who is authorized to use a computer for certain purposes but goes past those limitations is considered to have “exceeded authorized access” under the CFAA.
Threat shifting is the response of hackers to controls, in which they change some characteristic of their intent/targeting in order to avoid and/or overcome those safeguards/countermeasures.22
Social engineering
Social attacks involve conversations, a dialog with users convincing them to do something they would not ordinarily do. Even savvy computer users may be susceptible to social engineering attacks given the correct circumstances.
Pretexting
Pretexting is a technique in which the attacker uses a fictitious scenario to manipulate someone into performing an action or divulging information. Pretexting is also known outside the technical area as “con game” or “scam.”
One type of pretexting is phishing, in which the attacker uses an email to try to get the recipient to divulge information. Phishing emails can be made terribly convincing, visually appealing, and the senders can pose as a figure of authority or someone the user knows. Phishing is normally coupled with spamming, where the attacker sends thousands and thousands of emails in the hopes that a small percentage of the recipients will be convinced and open a file infected with malware or reply with an account number or password.
Successful spear phishing at the Financial Times
On May 29, 2013, the Financial Times reported a successful spear phishing attack that caught knowledgeable reporters at the venerable newspaper by surprise. The emails were highly customized and targeted to the organization. Hackers calling themselves the Syrian Electronic Army (SEA), perhaps after the ongoing events in Syria at that time, were able to get access to the email account of many veteran reporters. For more details, read the details reported by the newspaper at the link in the reference below.
One interesting feature of the report is that it indicates that many organizations are now very comfortable acknowledging being the victims of attacks and laying out how other organizations, including their competitors, can save themselves the ignominy of being victims of similar attacks. This is a major development from some years prior when organizations would rarely acknowledge such attacks so publicly.
Reference
- Betts, A. “A sobering day,” Financial Times labs, http://labs.ft.com/2013/05/a-sobering-day/ (accessed 07/16/2013)
With the move phone communication is making towards Voice Over IP (VOIP), a new method of delivery for the pretexting attack is appearing. Spam over Internet Protocol or SPIT is bulk dialed prerecorded calls using a breached VOIP network. They usually instruct the person answering the call to “stay on the line” or answer to questions that will be recorded and passed on to hackers. Contrary to email delivery, where available controls stop most of the spam received by a user, there are no means to control the calls a person's phone will receive. While some carriers have “black lists” available for customers (for a small fee), the situation would be unmanageable when the source of the calls change periodically.
Physical
A physical action involves the tangible or palpable aspect of an asset. Unfortunately, many organizations do not consider the physical threat action enough of an issue to warrant the expense of protecting against it.
Unauthorized access
This is a common threat. Many organizations require to have certain areas protected by card access mechanisms. However, in an effort to be cordial and polite, employees in these organizations will hold the door open if they see someone else running to use the opportunity to enter the building without searching for their access badge. Employees will often not challenge other individuals if they handle themselves with certainty and conviction, with that air of “I am supposed to be walking around here without my badge.”
In an age where terrorism went from a relatively unknown threat agent to a serious concern, control of unauthorized access to areas and systems relating to the country's infrastructure, such as airports, power plants, and even electrical substations serving a limited region have become a critical issue. While fences and other access controls were initially primarily designed to keep people from gaining access and getting hurt by electrocuting themselves, now the concern is that unauthorized access will lead to serious shortage in critical infrastructure services. Organizations are reviewing their guidelines and standards for protection of assets, such as the Institute of Electrical and Electronics Engineers (IEEE) and their Standard for Physical Security of Electrical Power Stations,23 focusing on these new and previously ignored threat agents.
Barnes and Nobles
In October 2012, customers of the giant bookstore Barnes and Nobles had their debit card numbers and PINs stolen when entry pads from 63 stores were apparently tampered (another physical threat action) to record information from all customers that used them for payment. Tampered PIN pads were discovered in multiple locations throughout the United States, and all indication point to individuals with unauthorized access to these data entry points.
Theft
Walk around campus, go to your university library or another study area. You will notice how easy it would be to take someone's laptop when they step out quickly to go to the restroom. That's plenty of time to close the lid, unplug the power and take off with the new device.
AvMed theft
In 2009, two laptops containing 1.2 million records from AvMed customers were stolen from AvMed Health Plans' Gainesville office in Florida. It took 3 months for AvMed to comprehend the extent of the breach and notify affected customers. The records stored in the laptops contained AvMed members' names, home addresses, phone numbers, Social Security Numbers, as well as other highly sensitive medical history data such as diagnosis information, medical procedure, and prescription information. A class action lawsuit was filed in 2010 on behalf of customers.
Error
The error category of threat agents includes everything done incorrectly and unintentionally. It includes omissions, accidents, trips, hardware and software malfunctions, etc. Errors do not include things left undone or done incorrectly but intentionally.
Data entry error
Data entry errors come in two varieties: omission or commission. With errors of omission, a value is not entered in the appropriate manner. Errors of commission refer to the integrity of the data entry.
Data entry errors are unfortunately common, but particularly dangerous in the Health area. Electronic Health Records are being put in place in hospitals and doctor offices around the country with the intent to facilitate the exchange of data between medical practices and other points of care. However, sharing data in this manner would also share any entry error on the data itself. While technology itself may be important, appropriate training and usability tests are equality critical to the proper operation of these systems.
Misconfiguration
Special care must be taken by system administrators when dealing with servers containing Personally Identifiable Information. Unfortunately, often hardware and software upgrades are done under tremendous pressure to bring systems back online, and the integrity of the system suffers because of it.
The most common incident involving misconfiguration seems to be related to these upgrades. In 2012, the University of North Carolina at Charlotte inadvertently exposed PII of more than 350,000 people due to the failure of administrators to properly migrate security settings from an old server being decommissioned to a new server. The same happened with the Northwest College in Florida just a few months later.
Environment
Threat actions in the environment category include:
- Natural disasters such as hurricanes, tornados, and flood
- Failures of environmental controls dedicated to supporting the IT asset, such as power failures, water leaks, air conditioning failures, etc.
Sidebar – Agents for natural disasters
The question may arise: so, who or what is the agent for a natural disaster? These agents are usually geographical, related to the area where the asset is located. For instance, in the Midwest of the United States, organizations may have to deal with tornadoes. Hurricanes are a concern on the Pacific and Atlantic coasts. West Coast organizations also must be wary of earthquakes.
Air conditioning failure
Level3 is a large, multinational telecommunications company based in Colorado. It provides network transport for data, voice, and content delivery for most large telecom carriers in the United States and abroad.
In 2011, the company suffered an AC failure at one of its datacenters located in France. Since real state in a datacenter is a premium, companies tend to pack as many servers as possible to minimize the support cost. As a result, keeping the air cool is a must. After a few hours, the ambient temperature in the server room reached 131°F. When the ambient temperature reaches that point, motherboard and integrated circuits start failing. Hard drives may still function after the temperature is back to normal, but problems with brittle heads or plates can lurk in the background for months before they show up in any diagnostic.
The culprit was clear. Air conditioning systems use a supply of chilled water to work. Earlier in the day, the line supplying cooled water to the AC systems of the French datacenter ruptured. Without a redundant source of chilled water, the AC systems could not operate and were shut down.
Hurricanes
We're on the 10th and 11th floor of a corporate high rise on Poydras Ave., right near St. Charles. We have generators and tons of food and water. It is five of us total. I am not sure how the Internet connection will be affected. I have a camera and my gun. Sustained winds are 175, gusts to 215. The real danger is not the wind, it's the storm surge the wind will be pushing into the city from the Gulf through the lake. The city might never recover. Honestly, this thing could be biblical.24
The entry was posted by Michael Barnett, former Green Beret and consultant to Intercosmos Media Group, parent company of the web host company zipa.com. Barnett was hired specifically as a crisis manager for the approaching Hurricane Katrina. He was holed up with his girlfriend in the datacenter to protect the assets and hopefully ride out the storm.
Katrina proved to be a monster, with millions of dollars in damage. From his perch on the 10th floor, Barnett documented the mayhem, looting, and his struggle to keep operations going with dwindling resources. Unfortunately, this will not be the last hurricane. Every year, from June through September, organizations housed near vulnerable areas prepare for the winds and the floods generally associated with hurricanes. They are one of the most devastating threats to face datacenters and the assets they house.25
Vulnerabilities
We have defined vulnerabilities as weaknesses in information systems that give threats the opportunity to compromise assets. Both terms, vulnerabilities and threats, are often used interchangeably in the industry, especially by vendors. However, it is particularly relevant to distinguish the two. By itself, a vulnerability does not present a risk to an asset. In the same manner, a threat does not present a risk unless there is a vulnerability in the system that can be exploited by the threat.
Not every vulnerability presents a threat to a network. Not all vulnerabilities need to be patched immediately. Only a vulnerability that can be exploited is a threat to business operations and information assets. It's common for administrative teams to receive reports of vulnerabilities with requests for immediate action to eliminate them. One source of these requests is an organization's internal audit team. Another common source of fix-it-now-because-the-press/vendor-says-it's-critical messages is management, including many IS Directors. But should all vulnerabilities be considered emergencies? Are all vulnerabilities worthy of your security budget dollars?26
Side Quote: A “zero-day threat” is a threat developed by a threat agent before a solution to eliminate the vulnerability was found and made public.
Threat agents use their knowledge of vulnerabilities to produce new threats against an asset. For information assets, the modifications to existing software code that will resolve vulnerability is known as a “security patch.” The Department of Homeland Security's National Vulnerability Database (NVD)27 reported 3532 vulnerabilities in 2011, about 10 new vulnerabilities being discovered every day. This is actually an improvement compared with the figures from 2009 and 2010 (Figure 6.12).
NVD database hacked
The NVD database maintained by NIST was taken offline on March 8, 2013, when administrators observed suspicious activity and discovered malware on two of its web servers. The servers were believed to have been compromised for at least two months. A vulnerability in Adobe's ColdFusion software was held responsible for the compromise.
Source:
Operating system vulnerabilities
Operating system vulnerabilities are those problems with the operating system which could grant a hacker access to operating system functions and accounts. Because the OS is the basic building block for all applications running on a system, administrators are usually required to apply OS security patches.
Microsoft issues their patches on the second Tuesday of every month. The date is known as Patch Tuesday or Black Tuesday, as an acknowledgment to the fact that administrators should ideally apply the patch on a test server and analyze its effects prior to applying the patch on production server. If a patch is deemed to be critical, Microsoft will release a security patch between Tuesdays. This type of patch is known as an Out of Band Patch.
Among the top 10 external vulnerabilities listed by the security vendor Qualys for August 2012, the following are Microsoft internal operating system vulnerabilities. Internal vulnerabilities are those that can be exploited once the hacker has a foothold on the vulnerable computer, usually through a compromised, non-admin account. Hackers then use these vulnerabilities to gain administrative access and control over the computer.
Microsoft XML core services remote code execution vulnerability (MS12-043 and KB2719615)
Microsoft XML Core Services 3.0, 4.0, 5.0, and 6.0 accesses uninitialized memory locations, allowing remote attackers to execute arbitrary code or cause a Denial of Service via a crafted website.
A remote code execution vulnerability exists in the way that Microsoft XML Core Services handles objects in memory. The vulnerability could allow remote code execution if a user views a website that contains specially crafted content. An attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.28
Microsoft Windows unauthorized digital certificates spoofing vulnerability (KB2728973)
Unauthorized digital certificates could allow spoofing. Certificates were issued irregularly by a Microsoft Certificate Authority and used to sign parts of the “Flame” malware. Flame is a malware apparently designed to target espionage much like one of its predecessors, Stuxnet. The malware was discovered by Kaspersky Labs in May 2012 but seems to be in the wild since 2010.
Microsoft Windows shell remote code execution vulnerability (MS12-048)
A remote code execution vulnerability exists in the way Windows handles file and directory names. This vulnerability could allow remote code execution if a user opens a file or directory with a specially crafted name. If a user is logged on with administrative user rights, an attacker who successfully exploited this vulnerability could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.29
Microsoft Windows kernel-mode drivers elevation of privilege vulnerability (MS12-047)
An elevation of privilege vulnerability exists in the way that the Windows kernel-mode driver handles specific keyboard layouts. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full administrative rights.30
Microsoft Data Access Components remote code execution vulnerability (MS12-045)
A remote code execution vulnerability exists in the way that Microsoft Data Access Components accesses an object in memory that has been improperly initialized. An attacker who successfully exploited this vulnerability could run arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.31
Sidebar – Qualys Laws of Vulnerabilities 2.0 Declarations
Half-life: The half-life of critical vulnerabilities remained at 30 days across all industries. Comparing individual industries, the Service industry has the shortest half-life of 21 days, Finance ranked second with 23 days, Retail ranked third with 24 days, and Manufacturing ranked last with a vulnerability half-life of 51 days.
Prevalence: Sixty percent of the most prevalent and critical vulnerabilities are being replaced by new vulnerabilities on an annual basis. This number has increased from the 2004 research where it was 50%. The top stragglers according to Laws 2.0 are MSFT Office, Windows 2003 SP2, Adobe Acrobat, and Sun Java Plug-in.
Persistence: The Laws 2.0 declared that the lifespan of most, if not all vulnerabilities, is unlimited, and a large percentage of vulnerabilities are never fully fixed. This law was illustrated with data samples from MS08-001, MS08-007, MS08-015, and MS08-021.
Exploitation: Eighty percent of the vulnerability exploits are now available within single-digit days after the vulnerability's public release. In 2008, Qualys Labs logged 56 vulnerabilities with zero-day exploits, including the RPC vulnerability that produced Conficker. In 2009, the first patch released by Microsoft, MS09-001, had an exploit available within 7 days. Microsoft's April Patch Tuesday included known exploits for over 47% of the published vulnerabilities. This law had the most drastic change from the Laws 1.0 in 2004, which provided comfortable 60 days as guidance.32
Web application vulnerabilities
Web applications insert yet another point of ingress to the underlying assets it exposes. The Open Web Application Security Project (OWASP) is a non-profit organization with a number of chapters and projects trying to make web-based applications more secure. As part of this effort, OWASP publishes a list of the top vulnerabilities found in web applications. We already discussed a few when we talked about threat actions.
Injection
Injection happens when the mechanism doing the interpretation of the commands sent by a client computer does not validate the commands before passing them to the application to be executed. When input is not validated properly, the web server may attempt to execute commands that should be restricted and never executed. In essence, the fact that the input is not validated gives the attacker a “pseudo shell” into the server and/or its database.
Preventing injection requires keeping data passed by outside sources (such as in a web form) separate from actual back-end commands and queries.
The preferred way to deal with this issue is to use an Application Programming Interface or API. With an API, the programmer restricts the type of input accepted from the client. For instance, a programmer may have an API that only accepts single, one-word commands such as READ, WRITE, and MODIFY. Anything other than these key words is ignored.
If this method is not available, the programmer must carefully examine the interpretation and clean any command that would allow a client to break out of the environment. For instance, if the command submitted by the client will be passed as a parameter to a SQL statement, the program should error out if any semicolon is passed by the client.
Attacks using the injection mechanism are the most popular and easy to use, such as SQL Injection or LDAP Injection.
Cross-site scripting (XSS)
XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation and escaping. XSS allows attackers to execute scripts in the victim's browser, which can hijack user sessions, deface websites, or redirect the user to malicious sites.33 While the target assets for attacks using injection are servers, the primary targets for attacks using the XSS vulnerability are the clients connecting to a server.
Cross-site request forgery (CSRF)
When you sit down to use your computer, chances are you log in to many different sites: Facebook, MSN, CNN, and others. A hacker using the CSRF vulnerability uses this fact to send “requests” to these login services on your behalf.
While the XSS attack “bounces” the payload on the server back to the client, a CSRF attack simply executes the command on the server on behalf of the client. For instance, behind the scenes, unbeknownst to you, a hacker could send an HTTP request to the server in this fashion:
http://somesite.com/change-password.php&user=jdoe?new-pwd=ilikepie The web server receives this request, confirms “jdoe” is already logged in and changes his password to “ilikepie.”
Insufficient transport layer protection
Simply put, this translates to make sure your web server has appropriate encryption enabled. Not all web servers may require data encryption. Probably the number one reason for a HTTPS connection would be a website which requires users to login. Unless the login transaction is encrypted, the entire content of the transfer is visible to a hacker with access, including the user login credentials.
It is also vital to use a valid, current industry-standard algorithm for encryption. We will look at encryption in one of the next chapters.
Finally, a certificate signed by a recognized certificate authority and renewed as needed is essential, especially for production servers. A certificate signed by the CA indicates non-repudiation (the site is what it claims) and that the encryption is trustworthy.
Example case–Gozi
When you think of information security threats, you probably think of smart but crooked people trying to attack your computer for personal gain. But did you realize that there is also a nascent industry developing professional software tools to help novices become industrial-strength for-profit attackers? On January 23, 2013, US prosecutors charged three individuals – Nikita Kuzmin of Russia, Deniss Calovskis of Latvia, and Mihai Paunescu of Romania with creating and distributing the Gozi Trojan. This software was customized for each customer to attack the specific financial institution picked by the customer. All three individuals had been arrested in different parts of the world over the previous 2 years.
The Gozi virus was created in 2005 and distributed as a pdf file. When the file was opened, the virus would secretly install itself, but do nothing malicious, thereby avoiding scrutiny from antivirus software. Eventually, it was installed on over a million computers worldwide, including over 40,000 computers in the United States.
The creators of the Gozi virus were extremely selective about picking customers. When a customer paid the team, select infected machines would be made available to the customer. The customer could then pick a financial firm to target, based on the usage behaviors or the banking preferences of the set of victims made available to him. The Gozi team would then write the customized software for the customer, which intercepted web-banking communications between the victims and their banks, allowing Gozi's customers to harvest account credentials.
To facilitate money transfers, the Gozi team had also lured individuals through envelope-stuffing schemes. These individuals would receive money from banks and mail it to the customers, providing a level of anonymity to the customers.
If convicted, each of the three members behind the Gozi team faces over 60 years in prison.
REFERENCES
http://www.justice.gov/usao/nys/pressreleases/January13/GoziVirusPR.php
http://krebsonsecurity.com/2013/01/three-men-charged-in-connection-with-gozi-trojan/
http://arstechnica.com/security/2013/01/how-the-feds-put-a-bullet-in-a-bulletproof-web-host/
http://krebsonsecurity.com/wp-content/uploads/2013/01/Calovskis-Deniss-S4-Indictment.pdf
http://krebsonsecurity.com/wp-content/uploads/2013/01/Kuzmin-Nikita-Information-1.pdf
http://krebsonsecurity.com/wp-content/uploads/2013/01/Paunescu-Mihai-Ionut-Complaint.pdf
SUMMARY
In this chapter, we saw that a threat is composed of an agent performing an action against an asset. We then looked at the important agents and actions you are likely to encounter in your careers.
CHAPTER REVIEW QUESTIONS
- What is a threat? Provide some examples.
- What is a threat model? Why are threat models useful?
- Consider your laptop as the asset. Draw your threat model for the asset.
- What are threat agents? Provide some examples.
- What are the different types of threat agents? How have they evolved in prevalence over time?
- Describe the typical Nigerian 419 scam.
- What are hacktivists?
- In your opinion, which organization in your local area would be the most likely target of a hacktivist attack? Why?
- What are some known motivations of governments to sponsor or endorse cybercrime?
- What are internal threat agents? Provide some examples. Which of these do you think is the most dangerous? Why?
- How can top management be a threat agent from the perspective of information security?
- What is a threat action? What are some common threat actions?
- What threat actions can originate from an outsourced IT services provider?
- What is a brute-force attack? What is the objective of a typical brute-force attack?
- How can former employees become threats? What can you do to minimize the threat?
- What is a zero-day threat?
- What is threat shifting? How does it affect the work of information security professionals?
- What is a cross-site scripting attack? What is the objective of a typical cross-site scripting attack?
- What are some threat actions that can originate from the environment?
- What in your opinion is the most important threat action originating from the environment in your local area?
- What are vulnerabilities?
- What is the relationship between vulnerabilities and threats?
- What does patch Tuesday refer to in the information security profession?
- What is OWASP? Why is it important to information security professionals?
- Consider the threat model you developed for the laptop in question 3 above. What in your opinion is the most important threat agent and threat action in your model?
EXAMPLE CASE QUESTIONS
- Based on the information provided in the case, what suggestions would you offer to a friend to stay safe online?
- What is “bulletproof” hosting? Why is it valuable to cybercriminals? (you may need to search online)
- What offenses is each individual in the ring charged with committing?
HANDS-ON ACTIVITY–VULNERABILITY SCANNING
In this exercise, you will install and test the Open Vulnerability Assessment Scanner (OpenVAS) on the Linux virtual machine included with this text. OpenVAS is a collection of tools that allow security administrators to manage the scanning of a large number of systems for network vulnerabilities. For more information, please see the OpenVAS website: http://www.openvas.org.
To install OpenVAS, open a terminal window and ‘su’ to the root account:
[alice@sunshine ∼]$ su- Password: thisisasecret
Next, use the YUM package manager to install the required packages:
[root@sunshine ∼]# yum -y install openvas Loaded plugins: downloadonly, fastestmir- ror, refresh-packagekit, security Loading mirror speeds from cached hostfile * atomic: www4.atomicorp.com * base: mirror.flhsi.com * extras: mirror.cogentco.com * updates: mirrors.adams.net Setting up Install Process Resolving Dependencies --> Running transaction check ---> Package openvas.noarch 0:1.0-5.el6. art will be installed --> Processing Dependency: openvas-admin- istrator for package: openvas-1.0-5.el6. art.noarch --> Processing Dependency: wmi for pack- age: openvas-1.0-5.el6.art.noarch --> Processing Dependency: openvas-scan- ner for package: openvas-1.0-5.el6.art. noarch --> Processing Dependency: wapiti for package: openvas-1.0-5.el6.art.noarch
The command will install about 40 new packages on the system. When the installation is complete (this may take some time depending on your Internet connection), run the openvas-setup command to start the OpenVAS configuration process and enter the values below.
[root@sunshine ∼]# openvas-setup Openvas Setup, Version: 0.3 Step 1: Update NVT's and SCAP data Please note this step could take some time. Once completed, NVT's and SCAP data will be updated automatically every 24 hours Updating NVTs.... Updating SCAP data... [i] This script synchronizes a SCAP data directory with the OpenVAS one. [i] SCAP dir: /var/lib/openvas/scap-data [i] Will use rsync [i] Using rsync: /usr/bin/rsync [i] Configured SCAP data rsync feed: rsync://feed.openvas.org:/scap-data OpenVAS feed server - http://openvas.org/ This service is hosted by Intevation GmbH - http://intevation.de/ All transactions are logged. Please report problems to admin@inteva- tion.de receiving incremental file list ./ COPYING 1493 100% 1.42MB/s 0:00:00 (xfer#1, to-check = 30/32) COPYING.asc 198 100% 193.36kB/s 0:00:00 (xfer#2, to-check = 29/32) debian.6.0.xml 980140 100% 652.02kB/s 0:00:01 (xfer#3, to-check = 28/32) debian.6.0.xml.asc 198 100% 0.51kB/s 0:00:00 (xfer#4, to-check = 27/32) ... Step 2: Configure GSAD The Greenbone Security Assistant is a Web Based front end for managing scans. By default it is con- figured to only allow connections from localhost. Allow connections from any IP? [Default: yes] no Step 3: Choose the GSAD admin users password. The admin user is used to configure accounts, Update NVT's manually, and manage roles. Enter administrator username: openvas-admin Enter Administrator Password: 12345qwert Verify Administrator Password: 12345qwert ad main:MESSAGE:9806:2013-01-19 14h39.33 EST: No rules file provided, the new user will have no restrictions. ad main:MESSAGE:9806:2013-01-19 14h39.33 EST: User openvas-admin has been success- fully created. Step 4: Create a user Using /var/tmp as a temporary file holder. Add a new openvassd user --------------------------------- Login: openvas-user Authentication (pass/cert) [pass] : pass Login password : secret Login password (again) : secret User rules --------------- openvassd has a rules system which allows you to restrict the hosts that openvas- user has the right to test. For instance, you may want him to be able to scan his own host only. Please see the openvas-adduser(8) man page for the rules syntax. Enter the rules for this user, and hit ctrl-D once you are done: (the user can have an empty rules set) Ctrl-D Login : openvas-user Password : *********** Rules : Is that ok? (y/n) [y] y user added. Starting openvas-administrator... Starting openvas-administrator: [ OK ] Setup complete, you can now access GSAD at: https://<IP>:9392
To complete the setup process, you will need to run one more command. Please be aware that this command can take 20 minutes or more to complete, so please be patient.
[root@sunshine tmp]# /opt/book/threats/ scripts/finish_openvas_setup This pro- gram completes the OpenVAS configuration process. Stage 1: Loading and processing plugins Processing 57744 plugins. Please be patient. This will take 15 minutes or more depending on your hardware. Starting openvas-scanner: base gpgme- Message: Setting GnuPG homedir to ‘/etc/ openvas/gnupg’ base gpgme-Message: Using OpenPGP engine version ‘2.0.14’ Stage 2: Building the OpenVAS-Manger database This will take 10-15 minutes depending on your hardware. done. Stage 3: Starting services Stopping openvas-manager: Starting openvas-manager: Stopping openvas-administrator: Starting openvas-administrator: Setup complete. Please open Firefox and go to https://www.sunshine.edu:9392
Open a web browser window and go to https://www.sunshine.edu:9392. You will be presented with the certificate warning. The warning is shown because the certificate was generated during the OpenVAS installation process, so FireFox cannot verify the certificate with an external authority.
Click on the arrow next to “I Understand the Risks” and then click on the “Add Exception …” button. The screen shown in Figure 6.13 will be displayed. To accept the certificate, make sure that the “Permanently store this exception” checkbox is check and click on the “Confirm Security Exception” button.
You will be presented with a login screen for “Greenbone Security Assistant” (GSA). GSA is one of the several applications that make up the OpenVAS system. It provides a graphical interface to all of the OpenVAS scanning features. To login, use the openvas-user account and password you created above. The main screen for GSA is shown in Figure 6.14:
Select “New Task” from the “Scan Management” menu. The screen in Figure 6.15 will be shown. To create a new scan task, fill in the “Name” field – we've called this sample “myScan”, but the exact name isn't that important. Change the “Scan Config” dropdown box to “Full and very deep ultimate”; this enables all of the vulnerability scans included with OpenVAS. You can leave the other fields at their default values. Click “Create Task” to complete the configuration.
Once the task is created, you will be presented with the task screen. To begin the scan, click on the start button (see Figure 6.16). The task status will switch from “New” to “Requested.” It will take 5–10 minutes to complete the scan, but you can refresh the page in Firefox to check on the current status.
Once the scan is complete, click on the details button (see Figure 6.17).
The scan details page presents you with an overview of scans that have been run and their results. To view the report for the scan that was just completed, click on the details button to open the Report Page. In the Report Page, you can view the results of the scan or download the report in a variety of formats. To download the report, select the file format and click the download button (see Figure 6.18).
Deliverables
Save the full report as openvas_report.pdf and submit it to your instructor.
CRITICAL THINKING EXERCISE–IRAQ CYBERWAR PLANS IN 2003
In August 2009, the New York Times reported that in 2003, when the US was planning the Iraq war, US Intelligence agencies and the Pentagon developed a plan to launch a cyber-attack with the goal of freezing the bank accounts operated by Saddam Hussein. There were billions of dollars in these accounts, which were used to pay the salaries of army personnel and purchase supplies. If successful, the cyber-attack would incapacitate Saddam Hussein's ability to wage war with kinetic (conventional) weapons.
As the New York Times reported, though the officials involved in developing the plans for cyber-attacks were confident of their ability to execute the attacks, they never got approval to execute on their plans. Officials in President Bush's administration were concerned about collateral damage, i.e., impacts on accounts owned by other individuals, if any part of the cyber-attack did not go according to plan. This could create financial chaos worldwide, beginning with the Middle East, but likely to spread to Europe and even the United States.
That was 2003. Since then technology has evolved, and cyberwarfare is increasingly becoming part of the military arsenal. Even during the Iraq war in 2003, the military attack included disrupting telephone systems inside Iraq. This temporarily affected civilian telephone services in countries neighboring Iraq. However, this collateral damage was considered acceptable at that time. But the uncertain damage from a cyber-attack gone haywire was not. Since then though, the US Government has felt comfortable using cyber-attacks to advance its goals, best documented in the case of the Stuxnet virus.
REFERENCE
Markoff, J. and Shanker, T. “Halted'03 Iraq plan illustrates U.S. fear of cyberwar risk,” New York Times, August 1, 2009
Critical thinking questions
- What are some ways (however unlikely) in which the proposed cyber-attack on Saddam Hussein's accounts could have harmed you?
- What are some ways in which a cyber-attack on a military target can harm civilians?
- One traditional military constraint based on the Geneva conventions and the UN Charter is called proportionality, the idea that a punishment should befit the crime. Given the risks of cyber-attacks identified in the earlier questions, do you think cyber-attacks are more likely to cause disproportional harm to civilians than conventional weapons?
DESIGN CASE
The Help Desk at the College of Engineering at Sunshine University has special privileges. It can fix user access problems bypassing normal access control procedures.
How did this come about, you might wonder? Years ago, an Electrical Engineering professor with considerable prestige in the College was unable to submit a grant proposal because he had accidently locked his Engineering account over the weekend. The Dean of the College and the Department Chair were extremely unhappy. As a “temporary” solution, student workers at the Help Desk were given administrative privileges to the Engineering domain, so they can change passwords and unlock accounts without inconveniencing the faculty and staff. Years later, the so-called “temporary solution” has become permanent, and quick response over the weekend is expected by all users.
One Saturday morning, Adam, a new student hired as a Help Desk employee decides, against the College's policy, to install a BitTorrent client on his Help Desk computer. Later in the week, an investigation into reports of sluggish computers leads to the discovery of a botnet installation on most of the computers in the College. After days of investigation, the source of the botnet installations is discovered when a keylogger is found on the machine Adam used. He had inadvertently installed malware on the machine together with the BitTorrent installation and the keylogger malware had captured Adam's credentials.
The College Dean has asked you to have an incident report on his desk as soon as possible, including recommendations to prevent such incidents in the future.
- List the threats and vulnerabilities that allowed this situation to occur.
- Classify all the events found in 1 above, including:
- Asset affected, including asset classification and characterization34
- Threat agent (including internal, external, or partner)
- Threat action (type, etc.)
- Vulnerability used
- What recommendations would you make to the Dean going forward?
- In your opinion, what should be done with Adam, the student recently hired to the Help Desk position?
1http://csrc.nist.gov/publications/nistpubs/800-30-rev1/sp800_30_r1.pdf. While the NIST definition is more comprehensive, we believe our definition is more memorable and captures the essential elements of a threat.
2VERIS ≡ Verizon enterprise risk and incident sharing metrics framework. The VERIS model also includes a fourth element – attribute, which describes how the asset was affected. Outcome of threats are studied as part of risk analysis and are covered in the chapter on risk management
3The STRIDE Threat Model – Microsoft Corporation: Software (n.d.). Retrieved from http://msdn.microsoft.com/en-US/library/ee823878(v = CS.20).aspx
4The numbers do not add up to 100 since many incidents have more than one agent type involved
5http://www.verizonbusiness.com/resources/reports/rp_data-breach-investigations-report-2012_en_xg.pdf
6http://www.ncix.gov/publications/reports/fecie_all/Foreign_Economic_Collection_2011.pdf
7http://www.nytimes.com/2012/06/01/world/middleeast/obama-ordered-wave-of-cyberattacks-against-iran.html
8CarderPlanet also posted elaborate advertisements that now can be found copied on the F-Secure website:
- http://www.f-secure.com/weblog/archives/planet.swf
- http://www.f-secure.com/weblog/archives/carderplanet.swf
- http://www.f-secure.com/weblog/archives/555.swf
9http://www.fbi.gov/atlanta/press-releases/2010/at081110.htm
10http://www.nytimes.com/2003/12/05/opinion/partisan-hacking-in-congress.html
11http://www.chicagobusiness.com/article/20130604/BLOGS11/130609948/the-price-of-failure-data-center-power-outage-cost-sears-2-2m-in-profit#ixzz2X4M39BKI
12http://www.net-security.org/secworld.php?id = 14861
13http://csrc.nist.gov/publications/PubsSPs.html#800-145
14What is Click Fraud? – Internet Marketing Services By (n.d.). Retrieved from http://www.optimum7.com/internet-marketing/ppc/what-is-click-fraud.html
15http://blog.eset.com/2012/06/07/passwords-and-pins-the-worst-choices
16http://www.acunetix.com/websitesecurity/xss.htm
17You can see an example of non-persistent XSS on the website https://www.insecurelabs.org. The site owners specifically designed the site to be vulnerable to XSS attacks. Select one of the agenda items and paste the <script> above. If your web browser has Javascript enabled, you will see the “owned” message pop up on the screen.
18Verizon's Data Breach Investigations Report (n.d.). Retrieved from http://www.slideshare.net/cloudrunnertom/verizon-dbir
19http://pastebin.com/AQWhu8Ek
20http://valleywag.com/5076432/angry-angry-it-guy-goes-to-jail
21Former SunTrust bank employee sentenced in computer fraud (n.d.). Retrieved from http://www.knoxnews.com/news/2012/apr/04/former-suntrust-bank-employee-sentenced
22Guide for Conducting Risk Assessments – #2fishygirl on Scribd (n.d.). Retrieved from http://www.scribd.com/doc/65740364/Guide-for-Conducting-Risk-Assessments
23http://standards.ieee.org/develop/project/1402.html
24http://www.baselinemag.com/c/a/Business-Intelligence/Diary-of-Disaster-Riding-Out-Katrina-in-the-Data-Center
25Please see this article for some very good example of threat statements: Adam L. Pineberg, “I challenged hackers to investigate me and what they found is chilling,” http://pandodaily.com/2013/10/26/i-challenged-hackers-to-investigate-me-and-what-they-found-out-is-chilling/
26A Practical Approach – Adventures in Security – Home (n.d.). Retrieved from http://adventuresinsecurity.com/blog/wp-content/uploads/2006/03/A_Practical_Appr
28http://technet.microsoft.com/en-us/security/bulletin/ms12-043
29http://technet.microsoft.com/en-us/security/bulletin/ms12-048
30http://technet.microsoft.com/en-us/security/bulletin/ms12-047
31http://technet.microsoft.com/en-us/security/bulletin/ms12-045
32The Laws of Vulnerabilities 2.0 | Qualys, Inc. (n.d.). Retrieved from http://www.qualys.com/research/vulnlaws/
33Top 10 2010-Main – OWASP (n.d.). Retrieved from https://www.owasp.org/index.php/Top_10_2010-Main
34What the instructor should be looking for at some point is a worst-case scenario situation. A breach of this type could have major consequences. Once the domain admin account is compromised, the agent has access to all information stored in the domain: email, research data, PII, etc.