First and foremost, we need to prevent cross-origin posting of form values unless we are absolutely sure that we have a way to control (or at least know who can do it) the POST. For a start, we can prevent cross-origin posting without permissions.
For instance, here's what we can do to prevent cross-origin posting: we first need to install cookie-session (https://github.com/expressjs/cookie-session) and CSRF (https://github.com/expressjs/csurf) and then apply them in our server.js file.
To install CSRF, simply run the command npm install –g csrf.
The settings of our server.js file now look like this:
var express = require('express'),
var bodyParser = require('body-parser'),
var app = express();
var session = require('cookie-session'),
var csrf = require('csrf'),
app.use(csrf());
app.use(bodyParser());
var port = process.env.PORT || 8080; // set our port
var mongoose = require('mongoose'),
mongoose.connect('mongodb://127.0.0.1/todos'), // connect to our database
var Todos = require('./app/models/todo'),
var router = express.Router();Now, restart your server and try to POST from external_node.html. You should most likely receive an error message to the effect that you cannot POST from a different domain. For instance, this is the error you will see from your console if you are using Google Chrome:
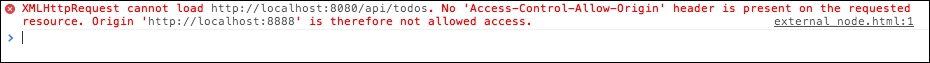
External post form now fails after we set up our server.js with basic security measures
The next technique is to escape user input first so that malicious input, such as the alert() function, cannot be executed. Here's what we can do: we first write this new JavaScript function:
function htmlEntities(str) {
return String(str).replace(/&/g, '&').replace(/</g, '<').replace(/>/g, '>').replace(/"/g, '"'),
}Now, prepend it at the start of our JavaScript code block. Then, at our todoTemplate(), we need to make the following changes:
function todoTemplate(title, body, id) {
var title = htmlEntities(title);
var body = htmlEntities(body);
var snippet = "<div id="todo_"+id+""" + "<h2>"+title+"</h2>"+"<p>"+body+"</p>";
var delete_button = "<a class='delete_item' href='#' id="+id+">delete</a></div><hr>";
snippet += delete_button;
return snippet;
}Take note of the highlighted lines of code, what we did here is to perform a conversion of HTML entities such as the JavaScript code snippet. This function is inspired by PHP's htmlentities() (http://php.net/manual/en/function.htmlentities.php).
Note
There's a useful Node.js module called secure-filters that does exactly the same thing, if not better. Visit them at https://www.npmjs.org/package/secure-filters.
Now save your file and refresh your browser again. You will notice that you no longer receive the alert() boxes and that the JavaScript code is printed out as if it's a string:
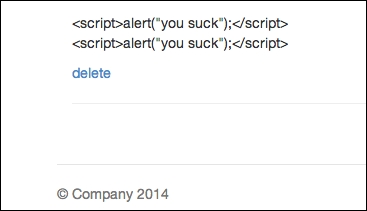
JavaScript now being printed as a string
