Intense scan is a very detailed, comprehensive scan. Logically, this means the intense scan may take up much more time scanning than the others will probably take, though it may come in useful when you want accurate results. This scan does the following scans and detections to reach the most accurate result as possible:
- OS detection
- Version detection
- Script scanning
- Traceroute
Let's cover these first. OS detection does a detailed detection of operating system running on a host. Nmap does this scan by stack fingerprinting, which works by sending series of TCP/UDP packets and then monitoring the response from the target. This scan is one of the best-known scans of Nmap. More about OS detection is given on the following pages.
The version detection is, described by Nmap, a high speed, parallel the operation via nonblocking sockets and a probe definition grammar designed for efficient yet powerful implementation. Version detection determines the application name and version number where available; it supports both TCP and UDP protocol and multiple platforms, including Linux, MAC OS X, Windows, Solaris, and others.
If available, Nmap connects using SSL (if OpenSSL is present), which allows it to discover various services such as HTTPS, POP3 as well as providing version details. If the SunRPC service is discovered, a brute-force RPC grinder is launched to find the program name along with the version number. Nmap has a very comprehensive database, recognizing more than one thousand service signatures and covering over 180 service protocols such as ACAP, AFP, XML-RPC, or Zebra. You've probably asked yourself if it is really important to determine the exact version type and number on the target? Yes, it is—obviously this helps in determining which exploit the target is vulnerable to. Another good reason is that multiple services can share the same port number—for instance, a TCP port 258 is used by both the Checkpoint Firewall-1 GUI management interface and the Yak Windows chat client. This makes a guess based on the nmap-services inaccurate. Also, you can often find services listening to unregistered ports (a registered port is a network port defined within the Internet Protocol, in the range of 1-65535 for use with a certain protocol or application)—these unregistered ports are a mystery without version detection. The next thing is that filtered UDP ports can often look the same as open ports. But if they respond to the specific probes sent by Nmap version detection, you can be 100 percent sure that these ports are open.
The result from a completed version scan would look like this:
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
Let's move on to the script scanning, which is also involved in the Intense scan. Script scanning is normally done in combination with a Port scan because scripts may be run or not run, depending on the port states. Script scanning involves the Nmap Scripting Engine (NSE) and directly executes the most common scripts while scanning. To specify and run a custom script in zANTI2, simply run the Script Execution and select your desired script. The scripts executed during the Intense scan are included in the default set of scripts (in Nmap defined as –sC or –script=default) and these are mostly the ones that finish quickly (this excludes force authentication crackers, web spiders, and scripts performing brute-force attacks). Default scans are meant to produce valuable, actionable, and easy-to-understand information about the target. These scripts are often the most reliable ones and none of them are intrusive, meaning they belong to the safe category and they're not trying to exploit or find any vulnerability in the system.
A typical script that's executed during the Intense scan is nbstat, which attempts to retrieve the target's NetBIOS names and their MAC addresses. The script displays the name of the computer and the logged-in user along with all names the system thinks it owns. The result would look like this:
Host script results: | nbstat: NetBIOS name: WINDOWS2003, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:c6:da:f5 (VMware) | Names: | WINDOWS2003<00> Flags: <unique><active> | WINDOWS2003<20> Flags: <unique><active> | SKULLSECURITY<00> Flags: <group><active> | SKULLSECURITY<1e> Flags: <group><active> | SKULLSECURITY<1d> Flags: <unique><active> |_ x01x02__MSBROWSE__x02<01> Flags: <group><active>
The result is, as always, saved into the Nmap scans log that you can access anytime during the scan.
The last scan type involved in the Intense scanning is traceroute.
Generally speaking, traceroute is a utility that records the route through the Internet between your computer and a specified destination computer. Traceroute also calculates the amount of time each hop took.
This utility is a handy tool and is widely used, mostly for finding problems in the network. Traceroute works by sending a packet (using the Internet Control Message Protocol or ICMP), including a time limit known as the time to live (TTL) that limits the lifespan of data in the network. This enables traceroute to determine the exact amount of time required for the hop to the first router. Values are then printed along with the hops.
Have a look at the traceroute result in the Nmap log inside of zANTI2:

The distance is 1 hop with round-trip delay time (RTT) of 13.30 ms. RTT marks the length of time it takes for a signal to be sent plus the length of time it takes for an acknowledgment of the same signal to be received.
This all is being found in one scan. Besides these detections, the Intense scan also scans TCP and UDP ports.
UDP uses a simple transmission model and has no handshaking dialogues, thus is often marked as unreliable with no guarantee of delivery, ordering, and such. Then there's TCP, commonly referred to as TCP/IP, thanks to its complementation to Internet Protocol (IP). Many internet applications and services rely on this protocol, such as the World Wide Web (WWW), e-mail, or file transfer.
If a service does not require a reliable but fast data stream, UDP is used—thanks to its connectionless transmission model.
We distinguish four types of Intense scan:
- Intense scan
- Intense scan plus UDP
- Intense scan, all TCP ports
- Intense scan, no ping
The Intense scan plus UDP does exactly the same thing as the Intense scan does (OS detection, version detection, script scanning, and traceroute), in addition to scanning TCP and UDP ports. While most popular services on the Internet run over the TCP protocol, UDP services are widely deployed. The most common are DNS, SNMP, and DHCP. UDP scanning is generally slower—open and filtered ports rarely send any response, leaving Nmap to time out and then conduct retransmissions in case the probe or response were lost.
UDP scan works by sending a UDP packet to every target port. Occasionally, a service will respond with a UDP packet, proving that this port is open. If no response is received, this port is marked as open|filtered. In this case, the version detection is used to differentiate the ports that are actually opened.
Intense Scan, all TCP ports does again, the same thing as the Intense scan and also scans all TCP ports—leaves no TCP port unchecked. Normally, Nmap scans a list of 1000 most common protocols, but in this case, Nmap scans every port from 1 to 65535.
Followed by Intense scan, no ping, this scan does exactly the same as the Intense scan without checking to see whether targets are up first. This type of scan can be useful in situations when a target seems to ignore the usual host discovery probes or if it's blocking ping request and you already know that the target is up.
Before proceeding to next scan types, let's explain the OS detection, that is an essential part of the Intense scan.
OS detection is one of the best-known features in Nmap. This scan is used by TCP/IP stack fingerprinting—your phone sends a series of TCP and UDP packets to the victim and carefully examines the response given from it. Nmap then compares the results with more than 2000 known OS fingerprints. Then, this finds out any matches and prints them into your log.
If you take a look at the log in the previous screenshot, you can clearly see the results are pretty accurate—I am indeed running Windows 7 Professional.
Now, you may be asking yourself whether these OS scans are really that important and useful?
OS detection is mainly used for finding out vulnerabilities, more precisely, reducing false positives of exploits on the targets. For instance, if a certain OS version contains an unpatched vulnerability, you can run an OS scan to find out which targets are vulnerable.
On the other side, as a system admin, OS detection provides a really easy way to search for vulnerable targets in your network and patch these before hackers exploit them. OS scans can also prevent hacker attacks caused by unprotected networks. If an employee in a big company installs a wireless access point on the network, this might just start a new threat for the company. Nmap even has a special category for WAPs, so as a system administrator, you can safely detect unauthorized devices like these before bad guys do.
Several things are being determined using this detection. Let's have a look at them.
These are parts of the OS detection that are collecting information based on the fingerprints. There are eight of them:
- Device type
- Running
- OS CPE
- OS details
- Uptime guess
- Network distance
- TCP sequence prediction
- IP ID sequence generation
All of these items are safely stored in the scan log, where you can view the results.
It is now more than obvious that OS detection plays a big role in the game, helping you detect outdated software that might be vulnerable to attacks. Let's take a closer look at the individual parts listed above and explain what they mean for us.
Take a look at a result of the OS detection scan done on my laptop.
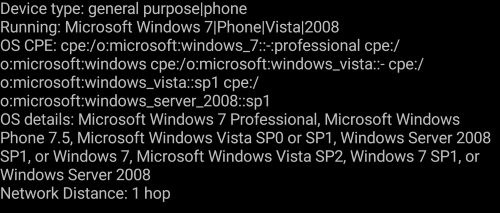
For the best and most accurate scan results, Nmap has to find one open and one closed port. If not found, Nmap can still provide and show some results but they might not be reliable and accurate.
Let's have a look at these one by one.
