We have reached the last chapter of this book, which undoubtedly is going to be the most interesting chapter. Man-in-the-middle (MITM) attacks are one of the biggest threats to any public network, they let anyone steal your personal data without your knowledge or freely control the traffic on the local area network. It's pretty simple.
In this chapter, you will learn the following:
- What is MITM, how it works, and how you can easily trigger this attack and intrude into anyone's computer on the local area network (LAN) using zANTI2.
- Things that you can do by taking advantage of this attack, including redirecting websites, injecting custom scripts on the websites, replacing images, and much more.
- More about protection against these types of attacks because after all, you could be the next victim! Also we'll have a look at the Hyper Text Transfer Protocol Secure (HTTPS) protocol, which is here to prevent these types of attacks but also shows how to bypass this security by performing an SSL Strip on a target.
So, as you probably read in previous chapters, you know that the MITM attack stands for Man in the middle. Although this might sound a bit out of key, it accurately expresses the substantiality of the whole thing. Let's see how this attack works.
Some of you might've heard about the Alice and Bob example, which explains what the MITM attack is based on. For those who are not familiar with this, let's say that there are two people—Alice and Bob. Alice tries to communicate with Bob by sending him a message. What they don't know is that there's an attacker trying to intercept and eavesdrop the whole conversation by performing the MITM attack on a network where these two people communicate on.
First, Alice asks Bob for his public key. Obviously, this doesn't happen in a normal conversation, but the public key is necessary in this case to establish a key-protected conversation between Alice and Bob. Public keys are typically used to encrypt plaintext (for example, text messages and documents) or to verify a digital signature. There is also a private key, which is used to decrypt the encrypted text or create a digital signature. In other words, the private key is used for the opposite operation as the public key is used for.
This key contains the algorithm for further encryption of any messages sent between Alice and Bob, so nobody except these two knows what messages they are sending. However, don't forget that there's an attacker on the network. The attacker is able to intercept this public key by launching an MITM attack and is now capable of not only viewing sent messages, but also modifying them by decrypting them using the key and encrypting them afterward.
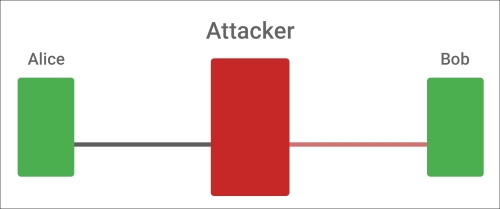
The preceding picture clearly shows how such an attack works. The attacker literally stands between two (or more) targets, intercepting network packets sent from Alice, modifying them and then sending the messages to Bob, who has no idea that the messages are being changed. Let's continue with our example:
Alice starts the conversation. She sends the following message:
Hey Bob, it's Alice—give me your key!
His conversation is already being intercepted by an attacker, which first arrives to him and then gets sent to Bob. He then responds:
Hi Alice, here's my key [Bob's key].
Since the attack cannot really intercept an encrypted conversation, he needs to know the key algorithm used for encrypting/decrypting messages. He does this by sending his own key instead of Bob's key to Alice, so he can easily decrypt and see the content of any further message sent between these two guys. The attacker slightly modifies the message as follows:
Hi Alice, here's my key [Attacker's key].
Alice encrypts the message thinking that it's the Bob's key and only he can read messages encrypted with this key. She sends a message:
How was your day? [encrypted with the attacker's key]
Alice thinks that she encrypted the message with Bob's key, so only he can decrypt and read it. However, in fact, the key was modified by the attacker, so he can decrypt and read it as well. The attacker will decrypt the message and re-encrypt it with Bob's key, so he doesn't spot anything.
How was your day? [encrypted with Bob's key]
The conversation goes on. Nobody spots a thing this way.
Attacks like this are generally possible against any message sent using public key technology. Public-key cryptography is based on algorithms that require two separate keys—private and public.
A large, random number is generated for keys that are suitable for use for the encryption. You can see on the picture, in an asymmetric key encryption scheme, anyone can encrypt messages using the public key, but only the holder of the private key can decrypt them. Therefore, security of the entire communication depends on the secrecy of the private key.
In this case, the attacker takes advantage of intercepted private key security and easily reads or modifies messages from Alice or Bob based on each other's keys as follows. It's that easy:

Various defenses against MITM attacks use additional authentication techniques that include Domain Name System Security Extensions (DNSSEC), public key infrastructures (using digital certificates and public-key encryption), certificate pinning (which detects and blocks many kinds of MITM attacks and adds an extra step beyond the normal X.509 certificate validation), stronger mutual authentication, secret better-encrypted keys, and many more. One of the defenses you can come across using MITM on a network is a router firewall, which can block various types of connections, preventing you from a successful MITM attack.
ARP spoofing (or ARP poisoning) is one of the most used methods to spy on the web traffic and intercept network packages in real time. This is also the method we will use for our MITM attacks with zANTI2.
Address Resolution Protocol (ARP) is a protocol used in LAN to resolve MAC addresses of the next or final destination IP. It's a method of letting the network map out IPs rather than giving each computer a table of the mapping. This protocol is vulnerable to poisoning because there is no method of checking the authenticity of ARP replies, so they can be spoofed from other addresses on the network. An attacker sends a spoofed ARP messages onto a LAN, trying to associate his MAC / IP address, which will cause the traffic meant for that IP to be sent to him instead of the original recipient. ARP spoofing allows an attacker to intercept data frames on a network, modify the traffic or, as I'll show later, to stop the traffic completely. This kind of an attack will (in our case) be used as an opening for the MITM attack on a local network, attacking, and poisoning our victim to modify the traffic as shown in the following image:
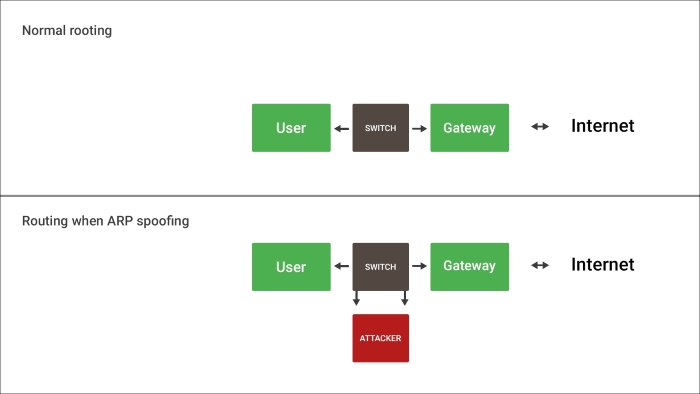
A successful ARP spoofing attack allows an attacker to alter routing on a network, which allows for an MITM attack. This is what we will use ARP spoofing for.
Although we will use the ARP method for our further attacks, there is one more available in zANTI2, in the MITM options of the app as shown in the following image:
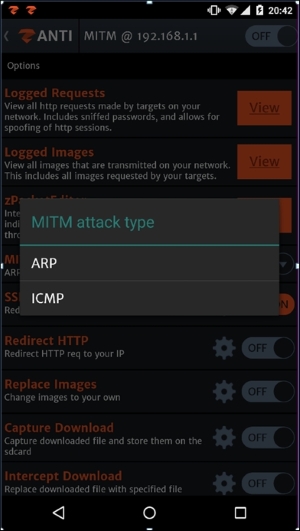
ICMP stands for Internet Control Message Protocol and is one of the most used protocols in networking technology. It is typically used by network devices, such as routers, to send error messages (that a service is not available or a host can't be reached for example).
An ICMP MITM attack is accomplished by spoofing an ICMP redirect message to any router between the victim and the server. The biggest advantage of ICMP attacks is that it does not require LAN access, but on the other hand, many routers do not accept ICMP redirect packets.
Zimperium security research, however, has disclosed a new type of MITM attack that is being widely exploited by hackers all around the world. It's a type of ICMP redirect attack and is named DoubleDirect. This attack enables an attacker to redirect a victim's traffic to the attacker's device, steal personal information, and deliver malicious payloads to the victim's device pretty easily. DoubleDirect uses ICMP redirect packets to modify routing tables of a host. This method is legitimately used by routers to notify the hosts that a better route is available for a particular destination. However, when exploited, an attacker can use the packets to alter the tables on the victim, resulting in launching an MITM attack.
This being said, zANTI2 does support full-duplex MITM using the ICMP redirect, but we'll use the ARP poisoning method for its usability, flexibility, and the presence of more victims vulnerable to this method (since many devices do not support ICMP redirects).
