The Microsoft-DS file-sharing port with number 445 is one of the biggest targets for hackers. This port is type SMB (Server Message Block), meaning it operates as an application-layer network protocol and is mainly used for providing shared access to files, printers, and whatnot. This is one of the reasons this port is a favorite place for hackers—it allows the transfer of malicious content to remote machines:
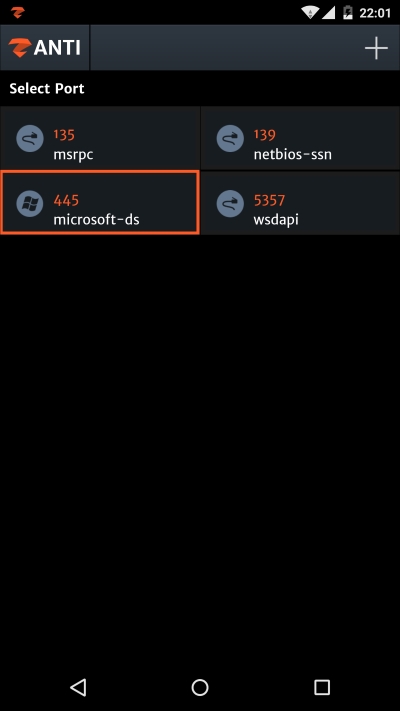
Port 445 has been present in Windows systems since Windows 2000 and for most of the time stays open, which exposes the target to worms such as W32.Deloder or Iraqi worm, and of course, makes it vulnerable to the power of zANTI2.
After selecting the port you will be prompted (again) for a Username with a Password. These credentials are the same as the ones used to log in to your Windows station:

If these credentials are unknown to you, use the password-complexity audit once again to attempt to crack the password. Instead of applying the attack against the SSH protocol, choose the SMB protocol since this is an SMB port.
Tap GO to establish a connection:
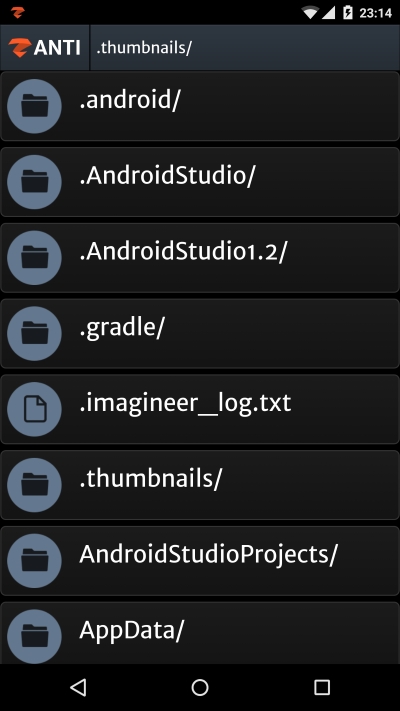
Since this port is used for file sharing and access, it is possible to display some parts of system and see the folders and files on it without the target even realizing.
This is very useful for viewing folders and files of a remote target through a local area network. Although it lets us investigate the target in an intrusive way, it still won't let us take full control over it. Let's look at Microsoft's Remote Desktop, the port number 3389.
