Chapter 10
Managing Passwords
IN THIS CHAPTER
![]() Updating password policies based on current best practices
Updating password policies based on current best practices
![]() Configuring self-service password reset
Configuring self-service password reset
![]() Discovering the MyApps portal
Discovering the MyApps portal
As the IT admin for a small business, you wield great power. In your capable hands lies the future of a modern workplace and a productive workforce as the result of the technology you make available for your end users. But as Uncle Ben in Spiderman so wisely said: “With great power comes great responsibility.”
That wisdom is particularly apt for IT admins in today’s security landscape. Cyberattacks, data leakage, and security breaches are the realities we must deal with daily. According to a study released by Microsoft and YouGov in April 2018, one in four SMBs are targeted by hackers. The average loss for these breaches is almost $80,000. Want to know what’s worse? In the study, 33 percent of the companies admitted that they spent more money solving the problems caused by the attack than it would have cost to prevent it.
Although these sobering statistics can be enough to make IT admins retreat into their obscure server room, there is good news! Microsoft 365 Business has built-in security functionalities to help IT admins perform the tasks necessary to secure their IT environment and minimize risks. Note that I used the word minimize. No matter what anyone might say, no security solution can guarantee that your company will never be attacked. Therefore, as an IT admin, you should operate under the assumption that your IT environment is currently under attack. Only with that mindset will you be able to responsibly take measures to protect your users and your company data.
In this chapter, I cover the tasks you need to complete to secure the most common attack vector: stolen passwords. Be prepared to rethink your approach to password policies because what you are doing today may be out of date. I also walk you through the steps to enable end users to reset their own passwords, thus relieving you of this repetitive but time-consuming task.
Knowing What You’re Up Against
You’ve heard of software as a service (SaaS), platform as a service (PaaS), infrastructure as a service (IaaS), and a whole bunch of cloud-based services using the as-a-service model. This model is great news for SMBs because it has leveled the playing field and allowed small businesses to compete with large enterprises.
The bad news is that bad actors are also using this model. Did you know that anyone with access to bitcoins can also buy ransomware as a service (RaaS)? Do a search online — you don’t even have to be in on the dark web — and you’ll find entrepreneurial hackers offering their services to the public for as low as $39 for a lifetime license. Some of them even offer technical support!
Imagine what the call must be like to these guys from some shady person who’s trying to hack a small business. “Hey man, I’m trying to hack this company and I’m running into issues trying to get someone to click a phishing email. Any ideas?”
As you can see, the barrier for entry into the hacking business has become very low. As an IT admin, you must be on high alert for cyberattacks. Fortunately, with the advancements in cloud technologies, you don’t need 20 years of infrastructure experience and tons of money to build a perimeter of protection around your organization. With a few tasks based on current best practices, you can start securing your organization and minimizing the risk of a breach.
Today’s common attacks
Unless you’ve been living under a rock the last couple of years, you most likely have been affected directly or indirectly with a cyberattack. Whether you had the credentials from your favorite online store stolen, or had your Facebook data exposed in the Cambridge Analytica scandal, or received an email from a “prince” in Nigeria wanting to transfer a million dollars into your account, most of us have been attacked.
You are not alone. Here are the top three attacks Microsoft is seeing in their ecosystem.
-
Password spray: In August 2018 alone, more than 200,000 accounts were compromised by this type of attack. In a password spray, attackers use a common password such as 123456 or password against many accounts, hoping to find a few users who didn’t get the memo about using stronger passwords.
And even a user who did get the memo and is diligent about updating passwords every 90 days will most likely recycle old passwords and simply add an exclamation point at the end. Hackers count on this behavior when they do a password spray. After they get a hit on just one account, they will have the ability to access the company’s address book, which can then be used for a phishing campaign.
-
Phishing: Attackers using this tactic usually try to lure users into giving up personal information after following a link in an email. In 2018, Office 365 blocked about 5 billion phish emails and analyzed approximately 300,000 phish campaigns. Microsoft’s logs show that 20 percent of users will click phish email within five minutes of receipt.
This blunder happened to TalkTalk, the United Kingdom’s leading business-to-business telecom provider, and landed them in a high-profile data breach. The breach started when a user clicked a malicious link in an email that started encrypting the data on the machine. The user then forwarded the email to the manager, writing something like “Something weird happened to my machine when I clicked this link. What happens when you do it?” Of course, the manager clicked the link. The company ended up paying a record fine for security failings leading to the theft of personal data for almost 157,000 customers.
-
Breach replay: Microsoft processed 2 billion credentials in 2018 and were able to match 650,000 accounts with leaked credentials. A breach replay happens when a user uses the same username and password on many sites.
Admit it, most of us have done it. In fact, even smart people in Washington, DC do it, as we learned from the Ashley Madison scandal, in which 15,000 government officials accessed the extramarital dating site by using email addresses registered to the White House, top federal agencies, and military branches.
If any company is well positioned to address security challenges in today’s computing environment, it is Microsoft. Every month, Microsoft scans 400 billion emails for malware and phishing attacks from Office 365 and Outlook, and processes 450 billion authentications every month from their 200-plus cloud consumer and commercial services globally. In addition, Microsoft has scanned 18 billion-plus Bing web pages and collected data from a billion Windows devices. These insights provide Microsoft with visibility into the current threat landscape like no other company. And that bodes well for an IT admin for a small business with no budget or expertise to maintain a security infrastructure.
Applying the latest password guidance
If you’re looking for the latest guidance for password best practices, you should check out the following two resources:
- National Institute of Standards and Technology (NIST) Digital Identity Guidelines at
https://pages.nist.gov/800-63-3/sp800-63b.html - Microsoft Password Guidance White Paper at
https://www.microsoft.com/en-us/research/publication/password-guidance/
As an IT admin, you can complete two action items today to make your environment secure with your Microsoft 365 Business license: enabling multi-factor authentication and eliminating mandatory password resets.
I cover multi-factor authentication in a separate chapter (Chapter 11) because the topic requires a thorough discussion to ensure a good experience for your end users if you roll it out.
I had initially thought eliminating mandatory password resets was counter to driving a more secure environment. The argument presented in the guidance from Microsoft, however, does make sense. Their experiment showed that users who are asked to update passwords often do not create a new, independent password. Rather, they update an old one. Full disclosure: I have done that myself but will no longer do so, now that I have read these new guidelines.
Want a remember or tip icon for the preceding paragraph?
To eliminate mandatory password resets, do the following:
-
Log in with your global admin credentials for Microsoft 365 Business at
http://admin.microsoft.com.You will need your Microsoft 365 Global Admin credentials.
-
From the left menu, click Settings and then select Security & Privacy.
The Security & Privacy page appears, as shown in Figure 10-1.
-
In the Password Policy section, click Edit.
A form appears on the right.
- In the Password Policy form, toggle On the switch next to Set Users Passwords to Never Expire.
-
Click the Save button and then click the Close button.
Your changes are saved and you return to the Security & Privacy page.
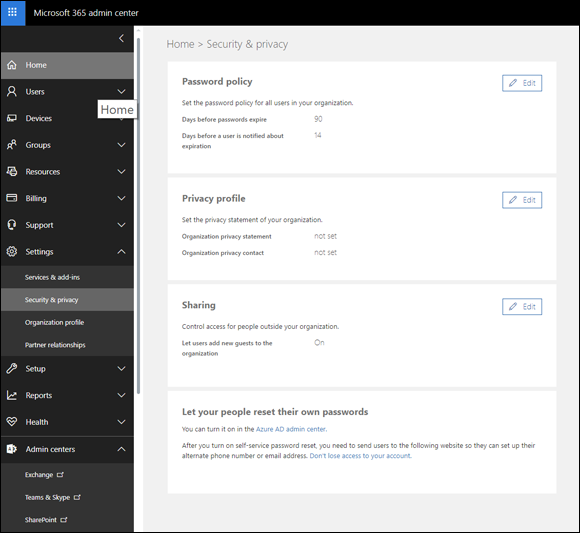
FIGURE 10-1: The Security & Privacy page in Microsoft 365 Admin Center.
Enabling Self-Service Password Reset (SSPR)
According to the Gartner Group, 20 to 50 percent of calls to the IT help desk are for password resets. Forrester Research estimates that the labor cost for a single password reset is about $70. If you have a small IT team or are the only IT team for your organization, you might want to let your end users reset their own passwords. Self-service password reset (SSPR) is available in Azure Active Directory, which is included in your Microsoft 365 Business license.
Why get bogged down with password reset tasks when you can empower your users to do it themselves? Instead, you can do many other tasks to proactively manage your IT environment — unless, of course, the reset request comes from your CEO.
Rolling out SSPR in your organization
Change is difficult for some people, so before you roll out SSPR in your organization, be sure to let people know about your plans. If you want to minimize the risk of people getting mad at you for implementing yet another newfangled thing, first do a pilot rollout of SSPR to a few receptive folks.
To enable SSPR, follow these steps:
-
Log in to Microsoft 365 Admin Center at
http://admin.microsoft.com.You need your Microsoft 365 Global Admin credentials.
-
On the left menu, click Settings, and then select Security & Privacy.
The Security & Privacy page is displayed.
-
At the bottom of the Security & Privacy page, in the Let Your Users Reset Their Own Passwords card, click the link to Azure AD Admin Center.
A new browser window opens and the Azure Active Directory Admin Center page is displayed. Alternatively, you can reach the same page by going to
https://aad.portal.azure.com. -
On the left side of Azure Active Directory Admin Center, shown in Figure 10-2, click Users.
The Users — All Users blade is displayed.
-
In the Users — All Users blade, click Password Reset, as shown in Figure 10-3.
The Password Reset — Properties blade is displayed.
-
In the Properties page, click All to enable SSPR for all users in your organization, and then click the Save button (see Figure 10-4).
The system processes your changes. After your changes are saved, the Save button appears dimmed.

FIGURE 10-2: Azure Active Directory Admin Center.
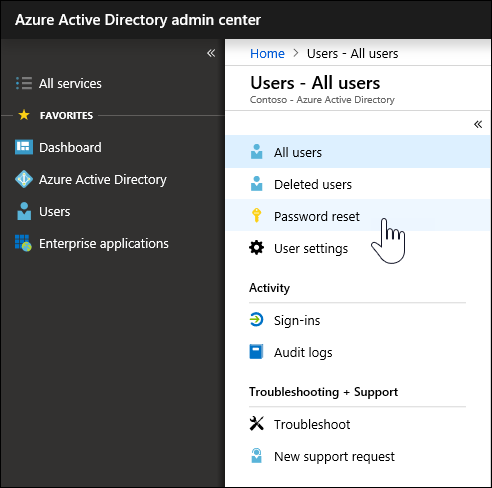
FIGURE 10-3: Password Reset option in the Users — All Users blade.
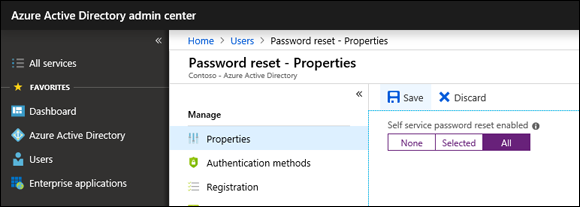
FIGURE 10-4: Enabling SSPR for all users.
After SSPR is enabled, users will be prompted to provide additional contact information the next time they log in to Office 365 so that the system can verify their identity should they reset their password on their own.
By default, users will be asked to provide two methods of verification if they reset their password. Two is the recommended setting, but you can change it to one from the Authentication Methods blade, as shown in Figure 10-5.
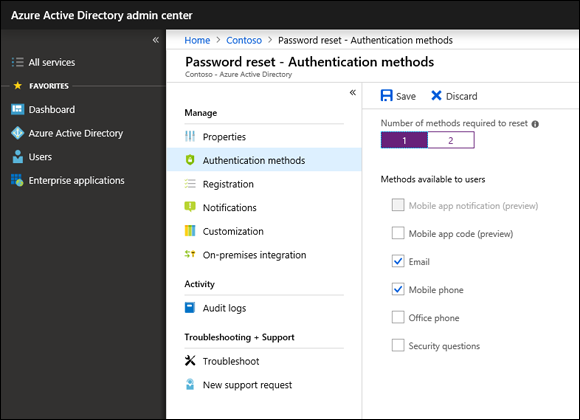
FIGURE 10-5: Change the verification method to 1 instead of 2.
The end user’s experience in SSPR
When end users log in to Office 365 after SSPR is enabled, they enter their username and password as usual. After they successfully enter their credentials, the More Information Required window will appear to prompt the user to provide additional information. Figure 10-6 shows the user interface for a non-admin end user. Note that an admin user may have a slightly different user interface.

FIGURE 10-6: End user login experience after SSPR is enabled.
After clicking Next, the end user will be guided through the process of providing additional information. After the process is finished, the end user can now reset his or her password at any time.
For example, let’s say that a user forgot her password. Here are the steps the user should follow to reset the password:
-
Navigate to
https://portal.office.com, enter the username, and then click Next.The Enter password window is displayed.
-
Click Forgot My Password, as shown in Figure 10-7.
The Get Back Into Your Account page appears.
-
Enter the characters in the box above the phrase Enter the Characters in the Picture or the Words in the Audio, and then click Next.
You see the first verification step.
-
Choose the contact method for verification.
To follow along with the example, choose Email.
-
Click the Email button.
The system sends an email to the email address provided during the end user SSPR setup.
-
Enter the code from the email in the box, and then click Next.
The next verification step is displayed.
-
Enter the code received from the secondary verification method (a text message, for example) and then click Next.
The Choose a Password page is displayed.
-
Enter the new password twice and then click Finish.
The Your Password Has Been Reset page appears.
-
Sign in to Office 365 with your new password by clicking the Click Here link and following the prompts.
The sign in page is displayed, prompting the user to enter his or her username. The rest of the login process proceeds as usual.

FIGURE 10-7: Selecting Forgot my password to reset the password.
Changing passwords from the MyApps portal
Sometimes users need to change their password even though they know the current password. You can complete this task in the MyApps portal.
The MyApps portal is a web-based portal for users who are licensed for Azure Active Directory through their Office 365 or Microsoft 365 Business subscription. In this portal, users can reset passwords, view the apps to which they have access, view their account details, set up multi-factor authentication, and more. It’s best to bookmark the portal and visit it often because new features may show up as the service evolves.
To change an existing password, follow these steps:
-
Navigate to
https://myapps.microsoft.comand log in in with your Microsoft 365 Business credentials.The MyApps page is displayed.
-
Click your profile photo (at the top right of the page) and then select Profile, as shown in Figure 10-8.
The Profile page appears.
-
On the right, under Manage Account, click Change Password.
The Change Password page is displayed.
-
Enter the old password, enter the new password twice, and then click Submit.
You return to your profile page.

FIGURE 10-8: Accessing the profile page from the MyApps portal.
Living in a Password-Less World
One of the exciting things coming up in Azure Active Directory is the notion of a world where a password is not required. The idea is that all you need to access your Microsoft 365 Business services is your phone and your fingerprint. Your phone would have the Microsoft Authenticator app, which is the gateway to your cloud services. Instead of entering a password after entering the username, users would see a message in the Microsoft Authenticator app, asking them to tap a number and then swipe a fingerprint to complete the authentication.
This feature is currently in Preview and is slated for global availability sometime in 2019. This solution holds great promise because it would render password breaches useless. Imagine a world where there is no password spray, no phishing, and no breach replay!

 Although both documents are written in different styles (the NIST document is more official looking and wordy), they are aligned on best practices. I recommend using the white paper from Microsoft as a reference if you want to skip the formal talk.
Although both documents are written in different styles (the NIST document is more official looking and wordy), they are aligned on best practices. I recommend using the white paper from Microsoft as a reference if you want to skip the formal talk. One of the highly recommended tasks for securing the IT environment is to enable multi-factor authentication (MFA). I cover that subject in the next chapter. For now, note that the end user is also required to set up MFA from the MyApps portal.
One of the highly recommended tasks for securing the IT environment is to enable multi-factor authentication (MFA). I cover that subject in the next chapter. For now, note that the end user is also required to set up MFA from the MyApps portal.