Chapter 5: Understanding and Implementing Microsoft Defender for Cloud (Microsoft Defender for Cloud Standard Tier)
One of the more cloud-focused tools within the Microsoft 365 Defender suite is Microsoft Defender for Cloud. In this chapter, we will be covering numerous topics around Microsoft Defender for Cloud, including ASC, so that you can get a better understanding of how to properly leverage this tool in your role as the Microsoft security operations analyst for your enterprise.
In this chapter, we will cover the following topics:
- Introduction to Microsoft Defender for Cloud and ASC
- Implementing ASC
- Implementing Microsoft Defender for Cloud
- How do ASC and Microsoft Defender for Cloud fit into the security of an enterprise?
By the end of this chapter, you will be able to fully understand all of the steps you need to take to not only be successful in deployment and implementation but also properly plan and utilize Microsoft Defender for Cloud in your role as a Microsoft security operations analyst. Let's go!
Technical requirements
During this chapter, we will be using shortened terms and acronyms we want to ensure you can understand throughout. The following list outlines a few of these terms for your reading and understanding:
- ASC: This is an acronym for Microsoft Defender for Cloud. Considering Microsoft Defender for Cloud is integrated into ASC, both in this book and within online publishings, you will see ASC used frequently.
- ATP: This is an acronym for advanced threat protection. Within ASC, many ATP elements will be available for enablement (as you will soon read), so instead of typing it out fully, we will simplify this by presenting it as ATP.
- KQL: This is an acronym for Kusto Query Language. When we cover monitoring and hunting, KQL will be an acronym you see frequently.
- LA/LAW: This will be our acronym for Log Analytics/Log Analytics workspace. LA is an under-the-hood part of ASC, as you will shortly find out.
- CSPM: This is an acronym for cloud security posture management. We will dive into what this is specifically later in this chapter.
- CWP: This is an acronym for cloud workload protection. We will dive into what this is specifically later in this chapter.
Okay! Now that we have covered the shortened terms and acronyms we expect you to encounter within this chapter, let's dive into what Microsoft Defender for Cloud is! Ready? Let's roll!
Introduction to Microsoft Defender for Cloud and ASC
Think about, for a moment, how vast the Microsoft Azure platform can be in your enterprise. Think about all the different resource types, locations, security controls, configurations, baselines, attack vectors, access requirements, authentication methods, and authorization methods. Then, add in the fact that the best practices around securing everything that exists within Azure (and, technically, Google Cloud Platform (GCP) and Amazon Web Services (AWS) as well) is ever-changing. How can an organization stay up to date with all of this, on top of what exists on-premises? Microsoft Defender for Cloud and ASC are here to help you with this!
Note
We will no longer be adding in formerly ASC Standard tier going forward—we will merely refer to this solution by its current name of Microsoft Defender for Cloud.
So, what is Microsoft Defender for Cloud? We believe, before diving into what Microsoft Defender for Cloud is, you must first know what ASC is. Microsoft Defender for Cloud is integrated into ASC, so let's first dive into ASC a bit so that you have a better understanding of the differences, integration, and enterprise use cases for the solution.
What is ASC?
ASC is Microsoft's CSPM offering. This offering in and of itself is free for you to consume in your enterprise. ASC enables you to truly strengthen the security of your Azure environment by identifying where you can potentially perform tasks that will harden your security posture on resources you may or may not even know exist! Each item that has been identified on various resources is a recommendation that is continually evolving as security evolves. This is a living recommendations list that looks at your data, compute, services, and applications in the cloud. Events that are collected from native or installed agents (potentially on-premises or in another cloud) and those that come from assets that live in Azure are correlated on the backend of the tool and are customized and tailored to provide recommendations on how you can improve your security posture on every resource in your environment. These recommendations are designed to secure your workloads and detect threats accordingly. See the following screenshot for an overview of the Security Center portal:

Figure 5.1 – ASC
In summary, ASC provides a solution for the three most prevalent and difficult-to-manage security challenges, which we explore in more detail here:
- Quickly changing and growing cloud workloads: Compared to how on-premises resources are created and managed, the cloud brings great simplicity and quickness to resource and workload deployment. While this is great, this wonderful thing is also a challenge for most security teams. How do you, as part of the security operations team, ensure that the team responsible for resource deployment is using the proper and approved (thus secure) templates and patterns? How do you also quickly identify non-compliance or insecure resources in an expeditious manner? This is a challenge.
- Threat actors are adding increasingly sophisticated attacks to their arsenal: Whether your workload in the cloud is internal or internet-facing and is basic or complex, there is a foundational and ever-present truth—attacks are getting increasingly sophisticated; attackers are learning the tools and discovery methods that exist in security tools; attackers are using this knowledge to adapt and obfuscate very quickly—many times, quicker than security teams can defend against. This is also a challenge.
- Staffing properly skilled resources is hard: Staffing has been a problem for decades in the security space. However, with the introduction of the cloud landscape into your enterprise, you will quickly find out that the number of security alerts and different tools and solutions that are noticing these alerts is far outweighing and outnumbering the number of staffed resources and security administrators. Even worse is the fact that even if you can find the financial means to hire more resources, it becomes even more difficult to find security administrators that possess the proper skillset and experience to defend against attacks properly. Staying up to date with the latest set of attacks being carried out by threat actors is a constant losing battle. This is, once again, a challenge.
With all these challenges present, ASC can help you and your organization prepare against these challenges by providing you with tools to do the following:
- Improve and harden your security posture: ASC, by default, will assess and review your resources in your environment and will allow you as a security administrator to fully understand deep insights into your resources and determine whether they are secure, based on best practices per resource type. This is all done automatically, as we will get into in later sections of this chapter when we discuss the deployment of ASC.
- Protect against threats: ASC, while assessing your workloads, will also raise awareness through recommendations on additional ways to protect against threats and resolve security alerts that correlate to your workload resources.
- Expedite your enterprise processes to get secure more quickly: ASC was born in the cloud, and with that comes simplified processes and expediting implementing recommendations that make your environment more secure! Also, since ASC is natively integrated with Azure cloud resources, deployment of ASC is an absolute breeze (as we will soon cover, later in this chapter). This includes various policy elements (Azure Policy) and auto-provisioning options available for your enterprise right away!
In addition to addressing the most challenging and prevalent issues that are present in your enterprise for you and your team, ASC also provides the following features that can easily be implemented to quickly assist your team:
- Making managing your enterprise cloud security policies and compliance easy: ASC works alongside Azure Policy (which is another great security tool that can be described as the Group Policy of the cloud, at a super high level). Each policy that comes with any recommendations of ASC is built on top of Azure Policy controls; these policy controls are key in forming your enterprise security policy posture, along with compliance tracking. As resources in your cloud workloads are spun up and down, these compliance numbers adapt to that and keep you focused on what you need to remediate to maintain compliance and a firm security posture. This is huge for security teams, allowing you to have a tool in place that will constantly be tracking any shadow information technology (IT) activities that happen in your cloud workloads without the direct involvement of anyone on the security team. Let the tool work for you!
Note
We do recommend you begin looking into Azure Policy—there are numerous resources out there for your reading. You will find out that in the cloud, Azure Policy is huge for security administrators and operation teams!
Security policy management in ASC
ASC is continually assessing your workloads and subscriptions for any added resources that have been deployed, reviewing existing resources, and assessing whether they are configured according to various security best practices. See the following screenshot for an example of security policy management:

Figure 5.2 – Policy management
What is great is that if any resources are not configured with best practices, they will be flagged and shown as an object that will have recommendations on how to become more aligned with security best practices. Within Azure, there is a specific security benchmark that resources are compared against; this benchmark is called the Azure Security Benchmark (ASB). This is a benchmark designed and authored by Microsoft and is specifically designed for Azure architecture. This was derived from the Center for Internet Security (CIS) and the National Institute of Standards and Technology (NIST) and compiled into a single, easy-to-follow benchmark that resources are assessed against.
Secure Score from assessments in ASC
ASC can monitor the security status of your Azure network. Whether you have an infrastructure-as-a-service (IaaS) or a platform-as-a-service (PaaS) cloud environment, networking will be a requirement! See the following screenshot for an overview of ASC Secure Score:

Figure 5.3 – Secure Score recommendations
ASC will analyze any network component in your workload architecture and call out any flaws that lead to security vulnerabilities or implementations that go against best security practices.
Network maps from ASC
One of the core features within ASC is the native ability to provide recommendations that are customized and specific to your workload resources. This is normally a task that is taken up by someone on the security operations team, but the wonderful thing about ASC is that it does this administrative task for you. See the following screenshot for an example of a network map:
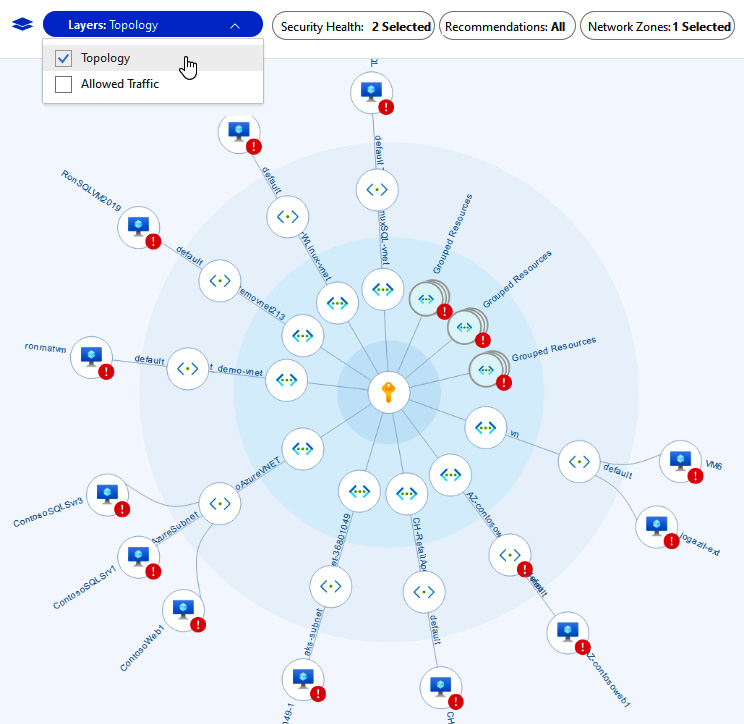
Figure 5.4 – Network map
What is even better is that these recommendations and actions can tie into other parts of the Microsoft 365 Defender stack of tools such as Microsoft Sentinel and Microsoft Defender for Endpoint (MDE). These recommendations help you reduce improper configurations in your workloads and reduce the attack surface across all your resources. Some examples would be Azure Virtual Machines (Azure VMs), any PaaS resource, storage accounts, and Structured Query Language (SQL) resources. Instead of manually doing this review and putting together a list of recommended security tasks for your enterprise, let ASC do this for you!
Bonus Note
There are many one-click-fix options with these recommendations that allow you to remediate these configurations through the single click of a button! Check them out!
Recommendations you can apply through ASC
Now let's learn about integration with MDE in your enterprise (when paired with Microsoft Defender for Cloud). One thing you will learn about throughout this book is the incredible integration capabilities of the Microsoft 365 Defender stack—this includes integration capabilities of ASC and MDE. See the following screenshot for an example of an alert:

Figure 5.5 – Example alert
You can onboard devices to either service from either portal/tool. You can also view and close out alerts that are generated from either service to the other. This is a great integration capability that proves to be super helpful for security operations teams and analysts alike to ensure you have a single pane of glass to manage and view alerts from both solutions!
Integration settings within ASC
See the following screenshot for an example of integration settings:

Figure 5.6 – Environment settings
So, back to the original question—what is Microsoft Defender for Cloudr?
What is Microsoft Defender for Cloud?
Remember when we talked about ASC being a CSPM tool? Well, Microsoft Defender for Cloud is integrated into ASC, but it serves a different purpose for your enterprise! Microsoft Defender for Cloud is Microsoft's CWP offering. Microsoft Defender for Cloud integrates into ASC and provides advanced, ever-changing, cloud-driven protection of your Azure and hybrid cloud workloads. In addition to the built-in policies that come with ASC, with Microsoft Defender for Cloud you can enable other custom security policies and compliances (such as NIST, Payment Card Industry (PCI), PCI Data Security Standard (PCI DSS), and Azure CIS. In theory, as with ASC, you can enable and extend the capabilities of Microsoft Defender for Cloud into your on-premises environment as well as into multi-cloud environments (AWS and GCP as an example).
Note
Microsoft Defender for Cloud is a paid offering that you can enable on resources. There is a different cost of CWP capability coverage (also referred to as ATP) per resource type you want to deploy this on. We will dive into which types of resources support Microsoft Defender for Cloud here in a moment.
Considering Microsoft Defender for Cloud is a part of ASC, to administer it within your enterprise, you will be navigating through ASC, as shown in the following screenshot:
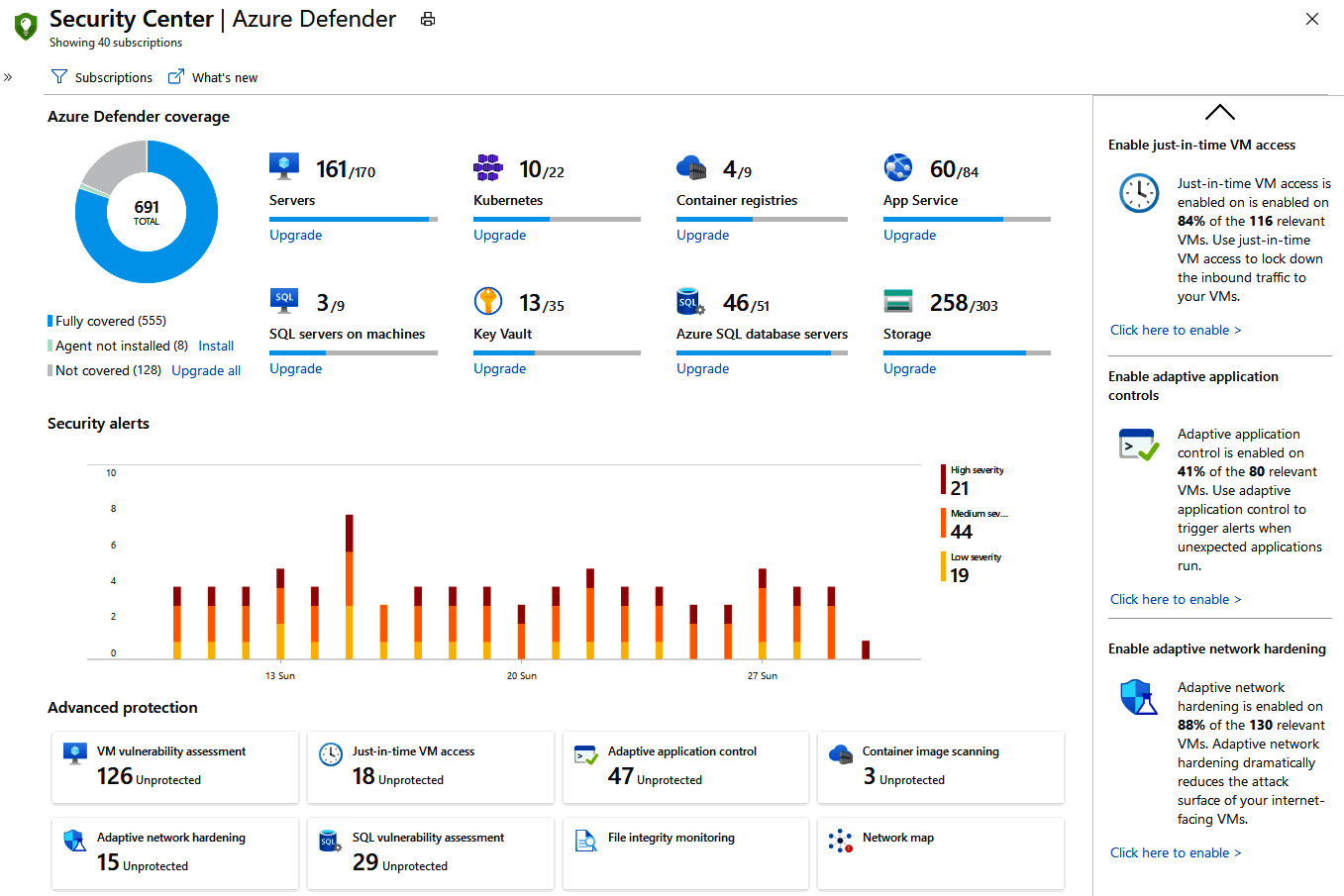
Figure 5.7 – Home dashboard
First, let's start with which types of resources support Microsoft Defender for Cloud, thus allowing you to enable this capability upon such resources within your workloads.
The following resource types support Microsoft Defender for Cloud (as of August 2021 from Microsoft Docs):
- Microsoft Defender for Cloud for Servers
- Microsoft Defender for Cloud for App Service
- Microsoft Defender for Cloud for Storage
- Microsoft Defender for Cloud for SQL
- Microsoft Defender for Cloud for Kubernetes
- Microsoft Defender for Cloud for container registries
- Microsoft Defender for Cloud for Key Vault
- Microsoft Defender for Cloudr for Resource Manager
- Microsoft Defender for Cloud for Domain Name System (DNS)
- Microsoft Defender for Cloud for open-source relational databases
Important Note
ASC will still provide proactive assessment and recommendations for all of the preceding services for free, but if you want protection elements to defend against threat actors, you will need to enable Microsoft Defender for Cloud, which is paid per resource type for such protection.
In short: ASC (CSPM) = free; Microsoft Defender for Cloud (CWP) = paid
We want to take some time, as it is something that will come up a lot when applying Microsoft Defender for Cloud in your enterprise, to cover what Microsoft Defender for Cloud brings to the table for each supported resource type. Let's go!
Microsoft Defender for Cloud for Servers
Microsoft Defender for Cloud for Servers is a feature that will add deep threat-detection capabilities and advanced defense mechanisms for your enterprise Windows and Linux workloads. Whenever you onboard servers to Microsoft Defender for Cloud, ASC will present alerts that Microsoft Defender for Cloud finds and give you suggestions on how to rectify known security issues. Remember, Microsoft Defender for Cloud and ASC work together as they are integrated with one another.
Here are some added benefits of Microsoft Defender for Cloud for Servers:
- Whenever you enable Microsoft Defender for Cloud for Servers, MDE will also be enabled, which adds excellent value and deep endpoint detection and response (EDR) capabilities to your servers.
- One of the deep ATP features that comes with Microsoft Defender for Cloud for Servers is Qualys vulnerability scanning. Vulnerability assessment scanning on your servers is done through Qualys, and all the outputs of that scanning are shown within the portal! The best part is that you do not even need a Qualys license, as it is included with Microsoft Defender for Cloud for Servers.
- Ever wondered how to secure your access from a Microsoft Remote Desktop Protocol (RDP) perspective? Ever been asked to turn off RDP functionality completely because threat actors use it maliciously? Good news! With Microsoft Defender for Cloud for Servers, you will get a feature called Just-in-Time (JIT) VM Access, which will allow you to enable RDP through a governed process to certain users, for a set amount of time! This reduces that attack vector in your enterprise right away!
- Typically, whenever a threat actor is making moves within your enterprise, they are changing files and registry settings without your knowledge. With Microsoft Defender for Cloud for Servers, you will have a feature available to you called File Integrity Monitoring (FIM). This feature examines files and registries of the operating system, application software, and other changes that might resemble or be indicative of an attack. This feature is for both Windows and Linux workloads!
- Being able to control which applications run on your servers has historically been a tough task to feat; however, with Microsoft Defender for Cloud for Servers, you will have a feature called adaptive application controls (AAC) that will allow you to set a list of known applications that can run on the server. If any application attempts to run, you will get a notification and an alert in ASC accordingly!
- With Microsoft Defender for Cloud for Servers, you will also have a feature available to you that will automatically adapt and manage network complexities based on the behavior of applications and workloads. This feature is called adaptive network hardening (ANH), and Microsoft Defender for Cloud for Servers will automatically modify network security groups (NSGs) to only allow traffic that is normal for your application workloads!
- Many times, threat actors inject malicious workloads into memory. With Microsoft Defender for Cloud for Servers, you will have a feature called fileless attack detection that will monitor and protect your servers from such adversary activity!
Microsoft Defender for Cloud for App Service
Microsoft Defender for Cloud for App Service is a feature available for enrollment that is designed to deeply protect your App Service deployment in your enterprise. Any application that you have running on Azure App Service will be fully protected by Microsoft Defender for Cloud if you enable it to do so. Learning from already existing processes that Azure possesses around general and deep threat-learning activities, that information is then fed to Microsoft Defender for Cloud for App Service to ensure protection and monitoring are in place to defend against these ever-changing attacks on App Service-based applications.
Here are some added benefits of Microsoft Defender for Cloud for App Service:
- ASC will continually assess your App Service plan and identify security risks, then show these to you as recommendations against your resources within the App Service plan.
- In addition to general assessment, Microsoft Defender for Cloud for App Service will also detect threats to your App Service resources by monitoring numerous fabric-level items, such as the following:
a. The VM instance that your App Service resource is running on under the hood
b. Requests to and from your App Service applications
c. Underlying sandboxes and VMs that your app services might be using
d. All internal logs of your app service
- Think about the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) framework for a moment—think about all the parts of the framework. Microsoft Defender for Cloud for App Service will detect and protect against a good majority of them!
DNS dangling is something that is often overlooked from a process perspective; so, whenever you decommission a site but keep the DNS entry present in your registrar, that can easily be used by a threat actor in a malicious way. Microsoft Defender for Cloud for App Service will alert you whenever you decommission a site and the DNS entry is still present and registered! The following screenshot shows an example of a DNS dangling alert in ASC from Microsoft Defender for Cloud for App Service:

Figure 5.8 – Additional alert details
Microsoft Defender for Cloud for Storage
Microsoft Defender for Cloud for Storage is a feature that will add an extra layer of security to your storage accounts within Azure. We see far too often that an exposed storage account has been compromised or scanned with data being exfiltrated by threat actors. Microsoft Defender for Cloud for Storage is here to solve that for your enterprise.
Here is an overview of Microsoft Defender for Cloud for Storage:

Figure 5.9 – How it all works together
Here are some added benefits of Microsoft Defender for Cloud for Storage:
- If there are any access attempts made to your storage account that match a suspicious access pattern, you will get an alert.
- If Microsoft Defender for Cloud for Storage sees any data exfiltration that appears suspicious, you will get an alert.
- If Microsoft Defender for Cloud for Storage sees any malicious data being uploaded to your storage accounts, you will get an alert.
- Constant guidance on how to better secure your storage accounts will be shown in ASC's recommendations.
- All file hashes that are stored, uploaded, or touched within your storage account are analyzed against Microsoft Threat Intelligence Center.
Microsoft Defender for Cloud for SQL
Microsoft Defender for Cloud for SQL is a feature that brings a deep and cloud-backed level of threat protection to your SQL workloads in Azure. This can be either Azure SQL, SQL on an IaaS VM, Azure SQL managed instances, a dedicated SQL pool in Azure Synapse, Azure Arc-enabled SQL servers, and—when configured and supported—even your SQL servers running on Windows on-premises! You might wonder which threat protection features this brings to your enterprise. Let's dive into those a little bit!
Here are some added benefits of Microsoft Defender for Cloud for SQL:
- Whenever you enable Microsoft Defender for Cloud for SQL, you will instantly gain the ability to have vulnerability assessments run on every supported SQL database or instance. This is huge for your enterprise, to assist in detecting and protecting against known vulnerabilities that exist within your SQL enterprise that could lead to data exfiltration or database compromise.
- In addition to the vulnerability assessments being done for best practices from a security standpoint, Microsoft Defender for Cloud for SQL will also bring you ATP elements that will continually monitor your SQL servers for various threats such as brute-force attacks, SQL injection, and privilege abuse. All of these will show in your dashboard as alerts that are then followed up with recommendations for remediation, investigation, and protection!
Some alert types are listed here:
- Suspicious database activity
- Anomalous database access and query patterns
- Potential SQL injection attacks
Microsoft Defender for Cloud for Kubernetes
Microsoft Defender for Cloud for Kubernetes is a feature that comes with Microsoft Defender for Cloud, should you choose to enable it. Microsoft Defender for Cloud for Kubernetes provides you protection for your Kubernetes clusters, but guess what? It can provide protection wherever they are running, not just within Azure! This includes the following:
- Azure Kubernetes Service (AKS), which—as you know—is Microsoft's managed service within Azure for managing, deploying, and even developing containerized applications.
- On-premises and multi-cloud environments that use Kubernetes. This will be achievable by implementing Azure Arc and using the extension for Kubernetes! Super-cool stuff!
Microsoft Defender for Cloud for Kubernetes will assist you in identifying additional ways to harden your Kubernetes environment, as well as providing real-time protection. When this is combined with Microsoft Defender for Cloud for Servers, information on your Linux AKS nodes will also be available! Pretty cool to see these features combine forces to provide you clarity, protection, and best practices to ensure your containerized applications are backed with the ultimate protection and security!
Microsoft Defender for Cloud for container registries
Microsoft Defender for Cloud for container registries is a feature that works alongside Azure Container Registry (ACR), which is a quite common solution used by organizations to manage container images in a centralized manner! If you use ACR in your cloud workloads, you can take advantage of Microsoft Defender for Cloud for container registries. This is a feature that will scan your images whenever they are pushed to your registry, giving you instant visibility into your images and information on any vulnerabilities found. What is great is that this is powered by Qualys, which—as discussed before—is an industry leader in the vulnerability scanning world! Whenever issues are identified by Qualys or ASC, you will get a notification within your ASC dashboard that will provide detailed information about that issue, such as the severity classification, the potential MITRE mapping, and guidance on how to fix the security issue within your images.
When are these images scanned? Great question—the scanning happens here:
- On push
- Recently pulled
- On import
The following screenshot gives you a better visual understanding of how ASC and ACR work together behind the scenes for this protection:
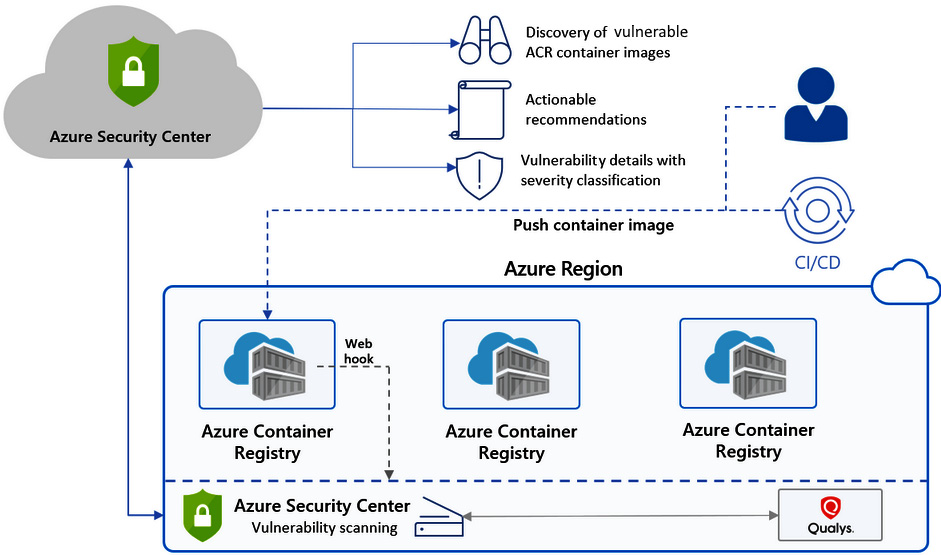
Figure 5.10 – Defender for containers
The preceding screenshot provides an example of Defender for Containers.
Microsoft Defender for Cloud for Key Vault
Microsoft Defender for Cloud for Key Vault is a feature that will provide ATP for any Azure Key Vault instance you have in your environment. When enabled, Microsoft Defender for Cloud for Key Vault will detect any potentially harmful attempts to access or even exploit Key Vault accounts. This is all powered by a vast machine learning (ML) engine within Microsoft Defender for Cloud. Whenever Microsoft Defender for Cloud suspects any anomalous activities, you will see alerts (such as the one shown in Figure 5.11), and if you enable it to do so, Microsoft Defender for Cloud can send emails to whoever needs to be notified about the key vault with this behavior! Considering Azure Key Vault is a critical solution to manage your keys, secrets, and passwords in the cloud, this feature will be well used and appreciated within your security team!
Here is an example of an Azure Key Vault alert in Microsoft Defender for Cloud:

Figure 5.11 – Example Azure Key Vault alert
Microsoft Defender for Cloud for Resource Manager
All your Azure deployments go through an engine called Azure Resource Manager (ARM), no matter whether you are doing this manually through the Azure portal or programmatically through the command-line interface (CLI), PowerShell, or even Terraform. ARM is a foundational element within Azure that your deployments rely on. Microsoft Defender for Cloud for Resource Manager is a feature that will automatically monitor all resource management operations that go through ARM. Microsoft Defender for Cloud will run advanced analytics and inspection on this for you, detect any suspicious activity, and follow that up with an alert in ASC.
Here is a screenshot showing how all deployments go through ARM and where Microsoft Defender for Cloud sits within this process:
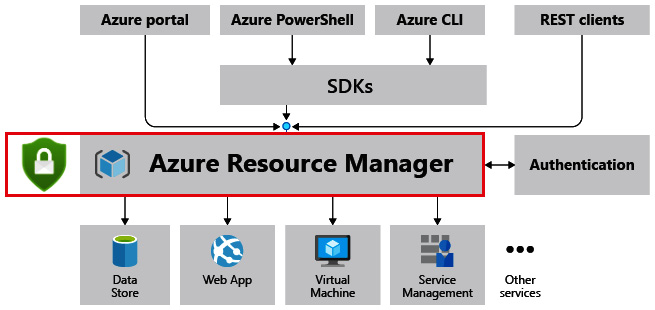
Figure 5.12 – Defender for ARM
What does it detect? Great question! Here are a few of the most important things:
- Suspicious resource management operations
- Lateral movement
- Use of exploitation toolkits
This feature will be beneficial to your organization to automate the security analysis of every deployment and every ARM operation in your Azure environment. Go check it out!
Microsoft Defender for Cloud for DNS
Many organizations take advantage of Azure DNS, which is a hosting service for DNS domains that provide name resolution. Whenever organizations host domains in Azure, you can manage your DNS records and zones, leveraging the same credentials as you would use to manage other Azure resources. If your organization uses Azure DNS, then Microsoft Defender for Cloud for DNS will be a great security feature for you! Microsoft Defender for Cloud for DNS will continually monitor all DNS requests and queries to your Azure resources and provide additional security analytics to allow you to have visibility into any suspicious activity.
Microsoft Defender for Cloud for DNS will protect your resources that are tied to Azure DNS against issues such as the following:
- Malware communicating with a command-and-control (C&C) server
- DNS attacks
- Data exfiltration from your Azure resources that use DNS tunneling
- Any known or suspected communication with malicious domains that are associated with phishing and crypto mining
Microsoft Defender for Cloud for open-source relational databases
Microsoft Defender for Cloud for open-source relational databases is much like Microsoft Defender for Cloud for SQL—however, it is intended for open source databases specifically. Microsoft Defender for Cloud for open-source relational databases supports the following database types:
- Azure databases for PostgreSQL
- Azure databases for MySQL
- Azure databases for MariaDB
Here are some added benefits of Microsoft Defender for Cloud for open-source relational databases:
- Whenever you enable Microsoft Defender for Cloud for your open source databases, you will instantly gain the ability to have vulnerability assessments run on every supported open source database or instance. This is huge for your enterprise, to assist in detecting and protecting against known vulnerabilities that exist within your open source database enterprise that could lead to data exfiltration or database compromise.
Some threat intelligence (TI) alert types are listed here:
Now that we have covered each of these rich features within both ASC and Microsoft Defender for Cloud, let's move on to discuss how to implement both solutions in your environment. This information will be crucial for the SC-200 exam but, more importantly, will enable you to possess the required knowledge to be the best Microsoft security operations analyst in your environment, today!
Implementing ASC
One of the more important parts of your role as a Microsoft security operations analyst, outside of simply knowing what the tools are that make up the overall solution, is to understand the effort and requirements to implement these solutions. We want to take some time and walk through with you how to implement ASC in your enterprise. You will be glad to know that implementing ASC is a simple task—however, we highly recommend that you effectively communicate all the previously shared information to the appropriate parties within your enterprise to ensure you have full alignment on the value this adds to your organization. Often, technology makes implementation so simple that we forget to communicate and follow internal processes. We want you to be successful, so go bridge that communication gap before continuing!
First, to implement ASC, you must have the proper permissions within Azure to do so. This can be applied to your own account, an administrative account, or even a service account you leverage for Azure administration.
Prerequisites
You will need one of the following permissions to implement ASC on a subscription:
- Subscription owner
- Subscription contributor
- Security administrator
All three of these are built-in Azure roles that can be applied to an account. Once you have verified you have these permissions available to you, we can proceed with the remaining steps.
Implementation steps
Now, let's look at the steps to implement ASC. Here they are:
- Sign in to the Azure portal using the proper account that has the permissions assigned, as discussed in the preceding Prerequisites section (https://portal.azure.com).
- Once you are signed in, you will be greeted with the portal menu, as illustrated in the following screenshot. Select Security Center, or simply search for it on the top search menu:

Figure 5.13 – General portal navigation to Defender for Cloud
- Upon clicking Security Center, you will be greeted with an ASC overview page that looks like this:
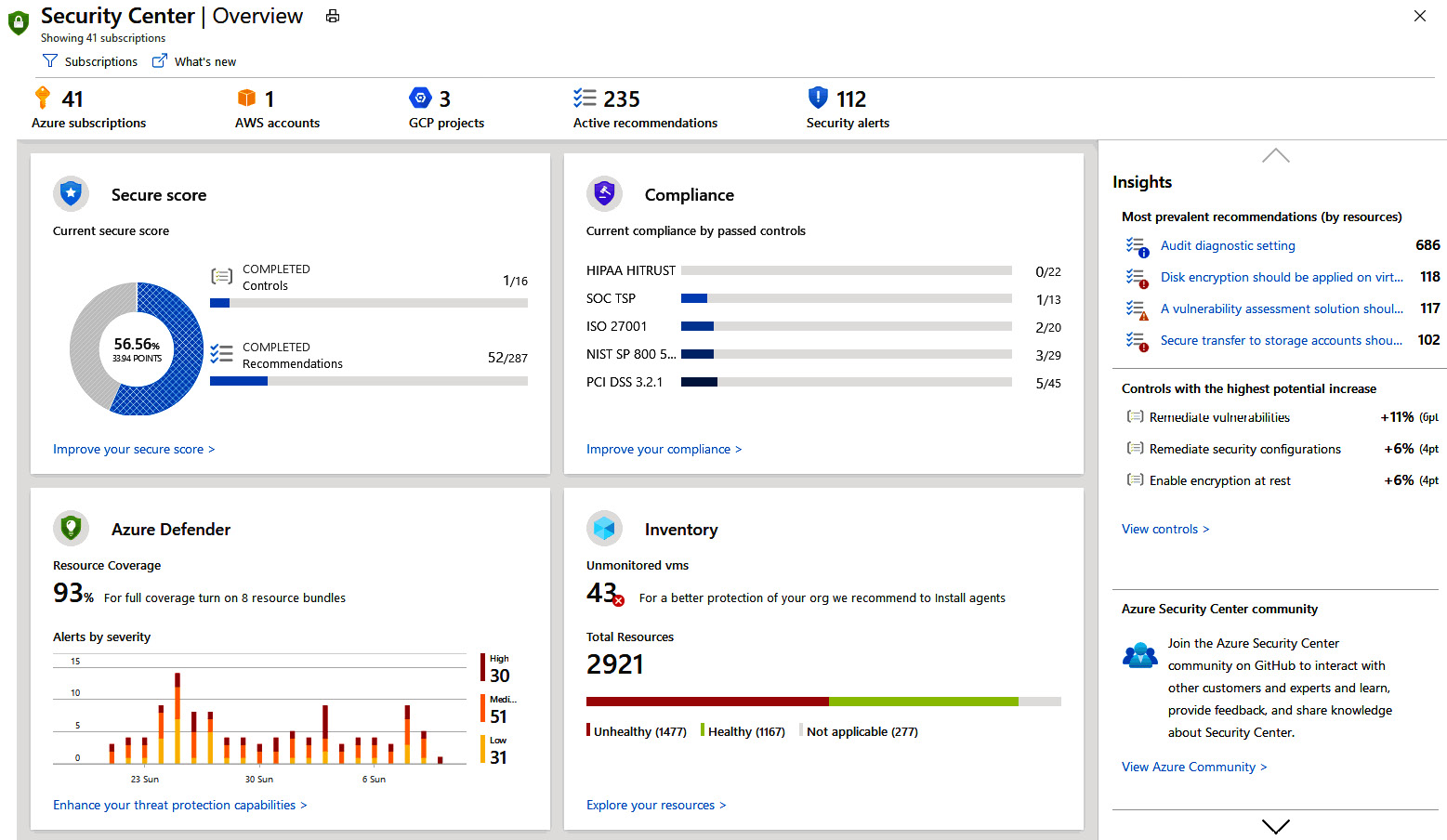
Figure 5.14 – Dashboard overview
Microsoft has made ASC enablement simple by enabling it on all your subscriptions by default. Any subscription that is created by any user in your tenant will automatically be included in all the rich features ASC provides. All you must do is open Security Center once, and within minutes, you will begin seeing the following:
- Recommendations for ways to improve the security posture of resources within your subscriptions
- An immediate inventory of all resources within your subscriptions that are now being automatically assessed by Security Center, and their security posture
That is it! Simply launch and let the data load!
Technical Note
One neat technical item to know is that enabling ASC is technically done by Azure Policy.
Here is a screenshot of the Azure Policy initiative that controls ASC enablement:

Figure 5.15 – Azure Policy
To take advantage of the additional threat protection features, we will move into showing you how to implement Microsoft Defender for Cloud on supported resource types within your subscriptions, next!
Implementing Microsoft Defender for Cloud
Having ASC enabled in your environment is a great start to strengthen your security posture; however, to protect your environment, you will lean on Microsoft Defender for Cloud. We want to walk through with you how to enable Microsoft Defender for Cloud in your enterprise.
Reminder
Microsoft Defender for Cloud is a solution that comes with various costs, so please review these before enabling.
Enabling Microsoft Defender for Cloud can be either a carte blanche task or a very granular task, down to the resource types you want protection on. Just as when you enabled ASC, some prerequisites exist before enablement is an option.
Prerequisites
Permissions are needed within Azure for you to enable Microsoft Defender for Cloud for your enterprise. Here is an outline of the available permission options that must be assigned to your user account, administrative account, or service account:
- Subscription owner
- Subscription contributor
- Security administrator
Outside of the required permissions, we want to state the importance of gaining alignment once again with proper teams. Microsoft Defender for Cloud will come with a charge that varies based on resource types. We do not want you to be shocked by a monthly bill!
So, what's next? Now that you have the proper permissions and alignment internally, we can move on to enabling Microsoft Defender for Cloud for your single subscription and then cover the steps for multiple subscriptions.
Implementation steps (single subscription)
Now, let's take a look at the implementation steps, as follows:
- Navigate to Security Center from the main menu.
- Select Pricing and Settings from the left-hand side of the overview page.
- Select the subscription you want to enable Microsoft Defender for Cloud on.
- Select Microsoft Defender for Cloud on.
- Select Save.
Here is a screenshot of Pricing and Settings | Microsoft Defender for Cloud on:
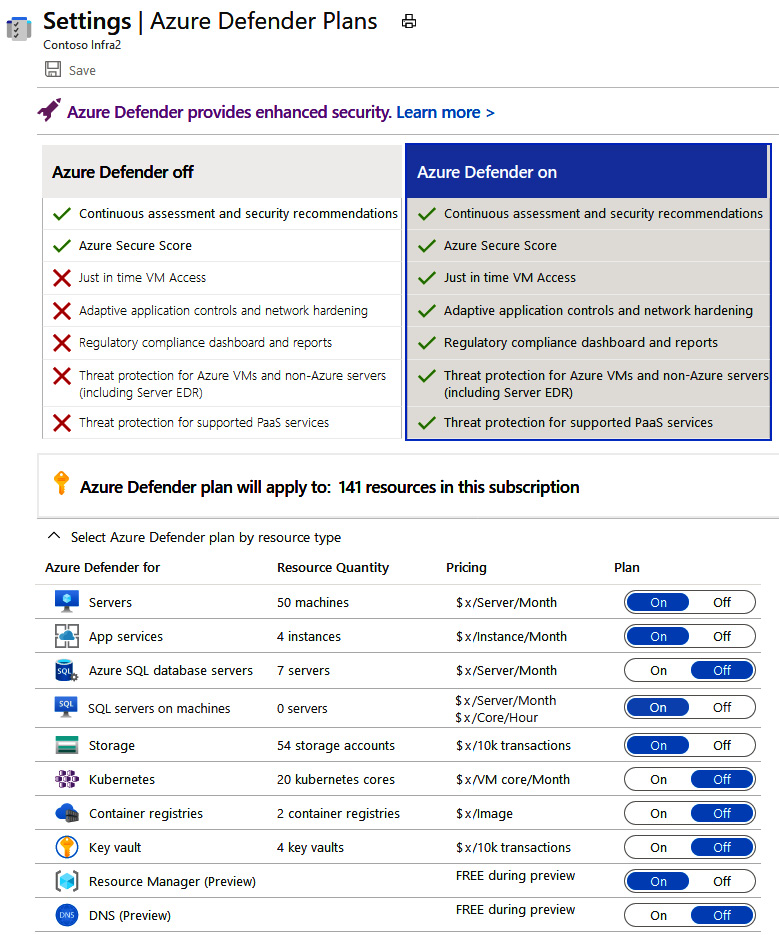
Figure 5.16 – Defender plans
Take note of the slider options you have! You can independently select per preferred resource type which plan each supported resource will have—either the free version of ASC or the paid plan option of Microsoft Defender for Cloud. Discuss these options with your team once again to ensure everyone is aligned on which resource types within your subscription you want to enable Microsoft Defender for Cloud on. You will see the pricing per resource type here as well for your rough cost calculations. Another thing to keep in mind is that what you are seeing from a resource count standpoint is what is currently deployed in your subscription. When you enable Microsoft Defender for Cloud for a specific resource type and you have automatic provisioning turned on (which we will cover a bit later), every new resource that is that same type will also be included in the Microsoft Defender for Cloud plan.
Okay—that was easy enough! But what if you wanted to enable Microsoft Defender for Cloud on multiple subscriptions? Let's cover that quickly.
Implementation steps (multiple subscriptions)
Many enterprises have multiple subscriptions within an Azure tenant—it would become quite a tedious task if you had to go into each subscription simply to enable Microsoft Defender for Cloud plans. Good news—you do not have to! Here, we outline the effortless steps to enable Microsoft Defender for Cloud at a higher level on all subscriptions, as follows:
- Navigate to Security Center from the main menu.
- Within Security Center, find Getting started within the Security Center sidebar.
- Once you are in Getting started, you will see a list of all your subscriptions and eligible resources for onboarding, as illustrated in the following screenshot:

Figure 5.17 – Enabling Defender for Cloud on resources
- You can now select multiple subscriptions and workspaces on which to enable your Microsoft Defender for Cloud plan!
- Once you select the proper subscriptions and workspaces, all you need to do is select Upgrade, as illustrated in the following screenshot:

Figure 5.18 – Upgrade process
Once this happens, the necessary changes will happen automatically on your selected resources, and charges will begin.
Pretty easy, right? So, what other considerations should be taken into account when you plan to enable ASC and Microsoft Defender for Cloud in your enterprise? You must consider a plan for provisioning the agents and extensions required on resources to have ASC collect data for analysis. Normally, enterprises prefer to do this in an automatic manner through ASC automatic provisioning. Next, we outline a few key points and steps you should consider before enabling automatic provisioning.
Configuring automatic provisioning for agents and extensions from ASC
Here is a quick set of steps for the prerequisites:
Note
All the previous prerequisites exist for this step as well.
- Navigate to Security Center and find Pricing and Settings.
- Identify and select the appropriate subscription or subscriptions.
- Find the Auto provisioning page, where you will see assorted options (we recommend turning all of them on where applicable). All you need to do—in theory—is turn the Log Analytics agent for Azure VMs extension on. If you would like other automatic provisioning to be completed for other required extensions based on features, then feel free to turn those settings on as well.
Here is a screenshot of the Auto provisioning settings:

Figure 5.19 – Additional settings
- Whenever you toggle an extension on, you will see a deployment configuration pane slide into view. Use this to choose which workspace you would like the data from the agent to pipe into.
- Next, from the Windows security events configuration page, select the amount of raw data to store from one of the following options:
- None: This disables security event storage, and is the default setting.
- Minimal: This collects only a small amount of datasets and events for times and configurations where you might want to minimize the event volume.
- Common: This is a set of events that from research satisfies most customers when it comes to needing a full audit trail.
- All Events: Self-explanatory—this is all events.
- Once you have decided which level of data you want to store, click Apply.
- Now, you can click Save. Please note that this change can take up to 25 minutes to apply as the workspace is provisioned and configured in the backend.
If you previously either intentionally or accidentally configured agents for monitoring on VMs, you will be asked to reconfigure them to be connected to your new workspace. In that case, simply click Yes:

Figure 5.20 – Quick question during onboarding
Okay! You did it! You have successfully learned what ASC brings to the table from a feature standpoint, as well as learning what Microsoft Defender for Cloud brings to the table in terms of protection of your various supported workloads. Not only have you learned this, but you have also learned how to deploy both tools in your enterprise! Now, let's move on to paint a picture of how ASC and Microsoft Defender for Cloud fit into the security mold of your enterprise!
How do ASC and Microsoft Defender for Cloud fit into the security of an enterprise?
As a Microsoft security operations analyst, you will be required to have tools deployed and operational in your enterprise that serve the greater security operations center (SOC) need. ASC with Microsoft Defender for Cloud enabled provides you the ultimate security posture management and workload protection where supported resource types allow. Think about this for a second—you have this amazing solution that is doing continual assessments and pointing out vulnerabilities as well as sending you alerts on threats present or detected, along with remediation activities. This is invaluable data to have at your fingertips. This data is then able to be simply maintained in ASC, or it can be piped into a security information and event management (SIEM) tool such as Microsoft Sentinel. You can see where we are going with this—ASC and Microsoft Defender for Cloud will be connected to your Microsoft Sentinel instance for you and your team to have a view into such feeds and alerts. Later, we will get into how to set up Microsoft Sentinel and connect data sources such as Microsoft Defender for Cloud and ASC.
Summary
In summary, Microsoft Defender for Cloud is simply awesome! In this chapter, we were able to cover very important aspects of Microsoft Defender for Cloud to ensure you are not only ready to pass the SC-200 exam on these topics but can also immediately apply this in your role as the Microsoft security operations analyst in your enterprise, from understanding what Microsoft Defender for Cloud is and how it integrates into ASC to knowing the prerequisites for deployment and implementation, and, finally, fully understanding how this truly fits into the security mold of your enterprise. This chapter is here for you to re-read and review as needed to prepare yourself to implement and utilize this tool in your enterprise today!
Next, we will be diving into chapters that are designed to ensure you can familiarize yourself with dashboards and alerts. Let's go!
