Chapter 2: The Evolution of Security and Security Operations
In order to understand the true importance and impact of the Microsoft Security Operations Analyst and their role within an organization, we need to take a quick step back and understand the true evolution of both security and security operations.
In this chapter, we hope to outline some important topics to give a passionate learner the ability to understand the past a bit. You must understand this because it quickly becomes an important part of your role! The topics we will cover will include the following:
- A quick introduction to the terminology
- Understanding the traditional approach to security
- Introducing the modern approach to security
- Getting to know traditional SOC issues
- Exploring modern ways to resolve traditional SOC issues
Let's dive into each topic throughout this chapter to hopefully give you a better understanding of the evolution of security and security operations.
A quick introduction to the terminology
During this chapter, we will be using the terms feeds and alerts very frequently. We want to ensure that you have a full understanding of the differences and the use cases. What is a feed? What is an alert? Let's get right into this!
Feed
A feed is a constant stream of activity that has been configured for ingestion or analysis. This activity is used for statistical purposes, and sometimes this is referred to as an audit trail or log/logging:
- Example: A record of each time a door opens and closes. This would be an audit of how many times and each time the door was opened or shut.
Alert
An alert is a notification generated in response to an event or a sequence of events that is characteristic of suspicious behavior. The alert is intended to bring the event(s) to the attention of an operator or a Security Operations Center (SOC) analyst:
- Example: Whenever that same door is slammed opened or slammed shut, an alert will be generated. You will then be able to review the audit log/feed of how many times it was opened and closed before it was slammed opened or slammed shut.
Now that we have covered these topics and terminologies, let's dive into a little background on what the traditional approach to security has been, along with the downfalls that allow you to fully understand the importance of modern security operations in your enterprise today!
Understanding the traditional approach to security
Security. It has always been important to enterprises worldwide because without it, the risk factors of compromise, data exfiltration, and overall breach, which may or may not be publicly disclosed, having a massive financial and trust impact on an enterprise increases greatly. Most of us realize the shift that is occurring in the world of security. Historically, if you look back at security, it has been focused on network boundaries, getting feeds and logging from all network appliances and all devices, and very much a four-wall approach to any resource access – meaning, an employee must be within a known network boundary, such as a Virtual Private Network (VPN) connection, if they are not within the office, or of course, within an office subnet or known network segment. While network segmentation and security boundaries do indeed possess their importance in security, it has been an increasingly losing battle, one that comes with many gaps and downfalls. Such downfalls are as follows:
- SOC analysts are completely overwhelmed by alert influx and fatigue.
- SOC analysts are struggling to keep traditional values relevant in a modern "remote work" world.
- SOC analysts are spending too much time investigating, versus proactively protecting or allowing modern technologies to do the anomalous behavior analysis.
Traditionally, SOC analysts spend their day analyzing feed and signal data, collaborating with other teammates to make a disposition on the next steps for alerts that come into their Security Incident and Event Management (SIEM)/security tools. However, with this ever-growing threat landscape, there must be a mechanism in place that decreases the requirement for human interaction and coordination and increases the ability to have tools in an enterprise that include automatic investigation, triaging, comparison, and even remediation of active threats in an enterprise. The issue here is that traditionally, the tools and operations available did not support these new preferred requirements. These are indeed requirements in the world we live in today – there is a ridiculously small chance that keeping such processes in place will allow your enterprise to maintain a healthy and secure environment.
So, what has changed? Is it just merely tooling? Or is there more to this story? Let's dive into the next section, review the modern approach to security, and move onward to what has changed in the approach and evolution to security operations.
Introducing the modern approach to security
Many of you will have noticed some noticeably substantial changes in the approach to security. In modern enterprises, teams can shift their focus from the traditional approach, as discussed previously, and move toward an approach that fits the requirements and landscape of their enterprises. We have all heard of security teams ingesting and analyzing network-level logging details, keeping as much authentication, access, and authorization internal as possible and approaching service publishing with a block-first mentality.
Here is the thing: this approach simply does not fit the mold of how end users and enterprises are required to function anymore. Increasingly, there are online services, such as Office 365, Teams, or Dynamics, that enterprises use that require a shift of security mindset and operations around how enterprise end users can access such online services. Additionally, online services are not the only items that require a shift. Often, there is an increasing number of end users that are working remotely; this can be by design or by situation – either way, remote work has increased tremendously over the past few years, and security needs to provide services to remote workers in a secure manner just like they would if they were in the office.
So, how does a security team shift and meet these newer and more modern requirements? Zero trust! Security teams must understand zero trust. There are so many vendors out in the security world that have a zero-trust model defined for enterprises to follow. For us, however, we will be following and referring to the Microsoft Zero Trust framework.
In today's world, cloud application usage, such as Office 365 and other online services, mixed with the increasing amount of mobile and remote workforces, has forced the security perimeter to be redefined. End users and employees are more commonly bringing in their own devices to the office and many are even working remotely. Corporate data is being accessed from locations that are outside the standard corporate network; this same data is also being shared and collaborated on with external partners and businesses. Enterprise applications and data are moving from a traditional on-premises location to hybrid and many times cloud-only. The traditional approach of security using physical locations and network devices to define the perimeter now shifts to essentially every single access location and point where corporate data and applications/services are accessed.
Nowadays, whenever an end user or employee goes to access such resources, the traditional on-premises perimeter is bypassed, and security models that are dependent on network firewalls and VPNs are null and void. Any enterprise that relies on those traditional security models will lack the visibility, solutioning, and ability to deliver timely, end-to-end SOC coverage.
So, what is required? What must change? Enterprises need a new security model and approach that adapts to the changes and complexity of the new requirements and new business interactions. This model must embrace and understand the mobile workforce, the remote workforce, and the accessibility of cloud applications that go far beyond the traditional perimeter. This is the absolute core of zero trust.
The following diagram shows that shift, the signals, the processing, then the authorization that exists in this new model:
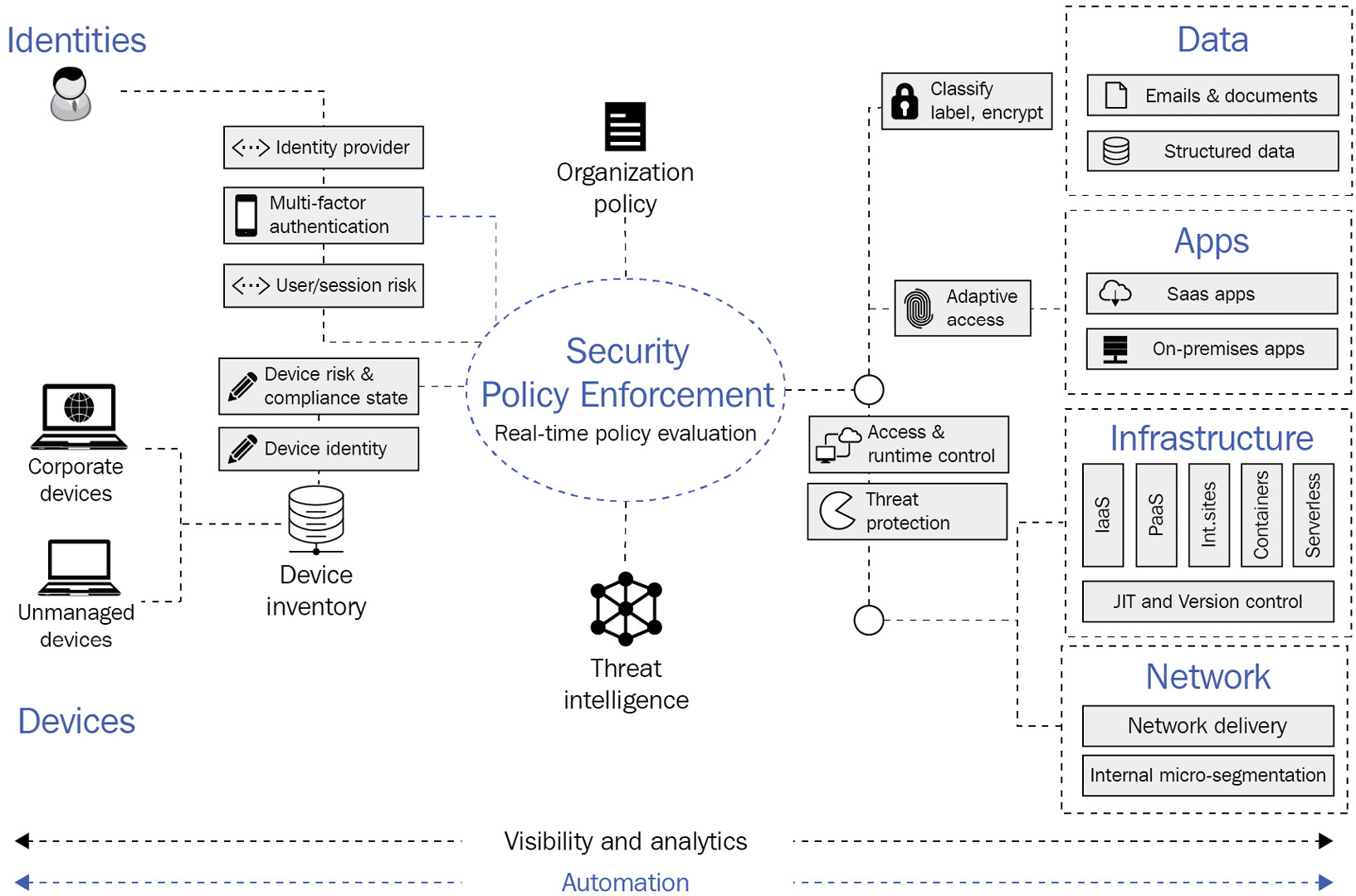
Figure 2.1 – Zero-trust model
So, what is at the core of the zero-trust model? Every single access request by any user (employee, partner, or vendor) must be authenticated, then it must be authorized by an enterprise policy, and then inspected for any anomalies before granting access. There are various feeds that will be a part of the inspection process that we will cover in later chapters. Again, every single access request, by any user, will be inspected no matter where that request is coming from; that's the core of zero trust.
In summary, here are the general guiding principles of zero trust:
- Verify explicitly. Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies. This must be done for all requests. Ensure your enterprise policies and discussions fully take this into account.
- Use least privileged access. Limit user access with Just-In-Time and Just-Enough Access (JIT/JEA), risk-based adaptive policies, and data protection to protect both data and productivity.
- Assume breach. Minimize the blast radius for breaches and prevent lateral movement by segmenting access by network, user, device, and application awareness. Verify all sessions are encrypted end to end. Use analytics to get visibility, drive threat detection, and improve defenses.
With this model in place, security teams can begin supporting modern access and security needs effectively and efficiently. But with such a shift also comes a shift in how the SOC operates with this new model. Let's dive into the traditional issues prevalent within a SOC and the modern ways to resolve the issues accordingly.
Getting to know traditional SOC issues
With the traditional approach to security being in place for years, it should not be a surprise that with such an approach, naturally there are SOC issues. There have been numerous studies conducted by Cisco, Exabeam, ESG, and Microsoft that have deeply reviewed how SOC teams work and what the gaps are that bring about issues and security threats. Think about it, with every gap, with every moment wasted on a slow triage process, the security threat increases. We will spend a little bit of time here going over the main issues and sub-issues of traditional operations within a SOC, as follows:
- Tooling, tooling, and tooling: One of the first gaps that have been assessed in studies comes down to what tools do SOC analysts have in their reach to be effective? What we have come to find out is that there are numerous teams without a proper set of tools to secure operations effectively. There might be an enterprise with a centralized logging infrastructure; in addition to the logging infrastructure, there is a monitoring infrastructure; in addition to logging and monitoring, there is another team that manages performance; in addition to logging and monitoring and performance, there is another team that manages tooling for closing out alerts; in addition to that... you see where this is going. There are too many tools, doing completely different aspects of management, managed by different teams, which simply causes problems. Even writing this out was painful; imagine having to operate within it and keep it up to date. It becomes increasingly difficult to know what is important to focus on, who needs to be involved, and what tool is triggering the alert or feed.
- Alert fatigue: With improper tooling comes another ridiculously huge issue in traditional SOCs and that is alert fatigue. Alert fatigue can have an adverse impact on your business's cybersecurity. Usually, over 50% of alerts in any organization are false positives. Most businesses deal with this problem by having a particular threshold that reduces the alert. Nevertheless, other businesses choose to ignore specific alert categories. This desensitization due to an overabundance of alerts can weaken your security system. However, with effective cybersecurity services, you can address security alert fatigue, minimizing the chances of a successful cybercrime.
- Slow triage time: Often, because of improper tooling, there is a slow triage or response time. This is because there are so many tools present, none of which integrate or talk to each other even from an API perspective, and each tool requires a different team to manage it. This quickly brings up confusing and deep communication requirements that many times do not exist within enterprises. With slow triaging and response comes the increased chance that the security threat will only spread, or at worst be missed altogether.
So, how do we resolve these traditional SOC issues? Let's discuss that in the next section!
Exploring modern ways to resolve traditional SOC issues
Keeping in mind the security shift that is required to be successful in a modern world, one of the first things enterprises must do from a security perspective to resolve traditional SOC issues is to review tooling and coverage. As we covered in the previous section, tooling has such a drastic impact on the SOC.
The overarching solution to common and traditional SOC issues is to begin integrating enterprise internal security systems into automation, coordination, and other threat intelligence backends. This type of data and integration will allow enterprises to have insight into threats that far surpass what is merely in their environments. Whenever you bring in these vast external data sources (primarily through native tooling, such as your EDR or SIEM solution), security teams in enterprises gain way more context into the actual threat that exists in their enterprise and what each alert means, but most importantly, how to act on each alert.
This solution then turns traditional SOC issues into remediated key capabilities:
- Filter out false positives: Know which alarms can truly be ignored.
- Speed up triage: Prioritize investigations based on the presence in your enterprise and the severity of the impact the threat already possesses.
- Simplify incident analysis: Determine quickly what has already been impacted, protect other vulnerable assets, and contain the damage.
The Microsoft 365 Defender stack (Microsoft Defender for Cloud, Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Defender Antivirus, Microsoft Defender for Cloud Apps, and Microsoft Sentinel) provides an all-around solution that provides proper tooling, insight, and automation to effectively manage a modern enterprise. This solution helps resolve traditional SOC issues greatly! The rest of the chapters will be dedicated to diving into each of these tools within the solution and explaining their importance in the SOC and what you need to know to deploy and manage, and then, of course, to pass the SC-200 exam!
Summary
To conclude our chapter, security and security operations have evolved vastly over the years. Change is good! There have been numerous traditional approaches to security, and with that comes traditional ways to manage the enterprise SOC – but with the ever-changing technical world and tools enterprises must operate in and adopt, there needs to be a shift; a shift from the traditional to the modern; a shift from the network to the identity; a shift from manual SOC processes with multiple tools and no integration to fewer tools, more efficiency, automation, and less alert fatigue.
We hope this chapter has laid out some additional foundations in your knowledge for your journey! Now that we have this under our belts, we can move on to our chapters on Microsoft Security Operations Analyst tools and deep dives. Let's go!
