Chapter 2
The Attacker
You're gonna need a bigger boat.
—Jaws
The offense is routinely underestimated. When companies are hacked, they react as if they had only done this one thing or avoided this one mistake everything would have been okay. The adversary is treated as if they just got lucky. So another hole is patched, another finger put into the dike, and the exploited company continues onward, utterly surprised the next time it is hacked.
The offense is routinely overestimated. When companies are hacked, they react as if it was inevitable, that no amount of effort could have prevented it. They resign themselves to cleaning up the mess and waiting for the next time, secure in the hopeless certainty there will be a next time.
The truth is that the offense is neither lucky nor invincible, but they are successful. To break their winning streak, you must step back and understand the attacker and the nature of operations. The same is true for the opposite motivation: If people want to extend the winning streak and attack more effectively, they must understand how they are guided and restricted by the first principles of Computer Network Exploitation (CNE).
Principle of Humanity
CNE is grounded in human nature.
The attacker is a person or a group of people. The attacker may be a lone actor, a well-ordered hierarchy, or a loose conglomeration of thousands, but regardless the attacker is human. For this reason, from now on this book uses the proper noun “Attacker” as a reminder that there are people behind it all.
Attacker motivations are many and varied. Internet vandals may attack systems just for kicks or to make a political statement. Criminals look to make money. Nations gather intelligence to seek military advantage, to track down terrorist plots, or to counter drug smuggling, among other things. These are all human motivations. Indeed the true objective of any CNE operation is ultimately human in nature.
For the Attacker, thinking of operations in terms of the human objectives frees them from becoming narrowly focused on trying to create perfect technical solutions. Good enough should suffice as long as the objective is met.
For the Defender, understanding that the Attacker is human opens a wider range of options. No longer are we battling Trojans and other faceless programs. There is a real adversary to be reckoned with, and the countermeasures can be technical, political, legal, or economic. Just imagine if the next time Amazon were hacked it decided to raise prices across the board at the Chinese site Amazon.cn. Would this have an effect? Maybe. Maybe not. But until one starts thinking of the Attacker as a group of people, these types of creative solutions will never enter people's consciousness.
Although Attackers and their motivations are quite human, the means of an operation seem the opposite, completely technical. Attacker tools that elevate privileges, capture keystrokes, or look for payment information in memory, to name but a few, are all technical—so are the things these tools exploit: web browsers, databases, network protocols, operating systems, and more. Defensive tools such as firewalls, intrusion prevention systems, antivirus software, and enterprise management systems are also just as technical.
Yet all these technical tools, from the most basic to the most complex, reflect the expertise and biases of the humans that developed them. From the industrial control system created with no concept of being networked to the supercool smartphone app pushed out to market without a second thought about security, the marks of the designers are left throughout. And because of this reflection, like their creators, the technology is full of flaws.
The Attacker that can understand the paradox of the humanity infused into technology will think like its creators, will see their assumptions, and will find ways to violate those assumptions to great effect. Likewise, the Defender that sees the humanity of the Attacker can begin to counter the actual problem instead of going after the Hydra's latest head.
Life Cycle of an Operation
Before diving into the other first principles of CNE, you must first understand the typical sustained operational life cycle. The stages of an offensive operation are targeting, initial access, persistence, expansion, exfiltration, and detection, as shown in Figure 2.1.
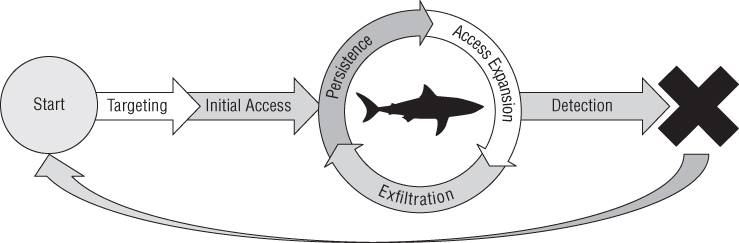
Figure 2.1 Ideal operational life cycle
Although it is often useful to think of the stages as discreet steps, one leading to another, this is inaccurate. Each stage often remains ongoing throughout the entire operation. The true life cycle of an operation is more like Figure 2.2—a tangled mess.
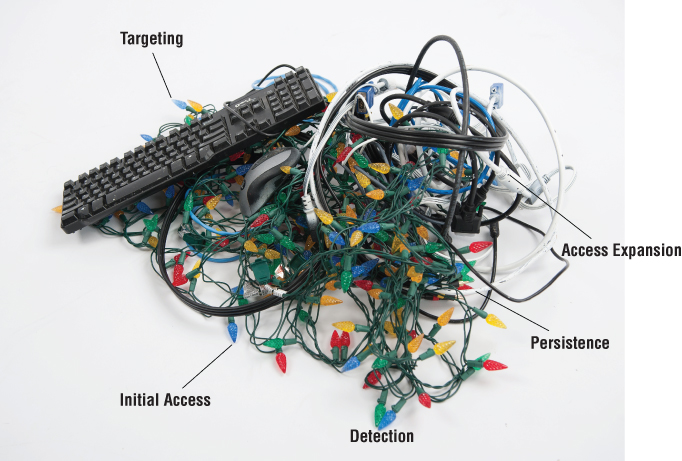
Figure 2.2 Real operational life cycle
Stage 1: Targeting
Targeting can be broken into two distinct parts: identification of the target network and identifying the attack strategies and tactics necessary to exploit that network. It is the difference between figuring out which bank to rob and then determining how to rob it.
Identifying a target network is not necessarily easy. For example, suppose you were interested in the design of an adversary's new weapons system. Where would you start? To identify the key computer networks, you might need to understand the organizational structure of the armed forces, determine the physical location of where the system is designed, or identify potential subcontractors and their organizational structures. All this information is potentially required just to figure out which network to go after.
Unfortunately, there's not much the targeted can do to disrupt this stage. Much of the initial targeting can take place without ever touching the network, and there are no available tools that can notify an organization that someone is gathering information about it elsewhere, except maybe AdWords. I can just imagine the marketing campaign in Figure 2.3.

Figure 2.3 Unlikely products
Clearly this is not going to happen. So targeting will remain invisible to the targeted. This is notably in contrast to the real world where countersurveillance is an important defensive measure.
During targeting, some targets are sought out, but the target identification process may also work in reverse. Targeting can be opportunistic. The Attacker identifies a weakness or a working attack strategy and then searches for vulnerable networks. The access is established first and the objective afterward. This is especially useful for strategic access operations where the specific objective may not be known.
Imagine a criminal that knows how to unlock and hot-wire a Trans Am. She won't wait for a particular person to buy one. Instead, she would go to a mall parking lot and seek out victims. Depending on a host of factors, the thief may just open the cars and search for money, or perhaps if conditions permit, she would steal one and sell it. The exact goal of the operation is unknown at the onset, but there is a known vulnerability, a capability, and hope.
Sometime in 2009, a few Romanians compromised the sandwich chain Subway. Over the next 2 years, they managed to steal somewhere between $3 million and $10 million, an amount that would allow them to eat fresh for quite some time. How did they do it? As reported by Wired1:
The hackers allegedly scanned the internet to identify vulnerable POS systems with certain remote desktop software applications installed on them, and then used the applications to log into the targeted POS system, either by guessing the passwords or using password-cracking software.
Our presumably hungry foes used opportunistic targeting. They had a known vulnerability and sought out a vulnerable system. It could have just as easily been Jimmy John's, PF Chang's, or Dairy Queen, all of which were also compromised in the last 2 years.
Of course, the victims may not care whether they were specifically targeted or were just a target of opportunity. The losses are the same. But they should care. If someone has his car stolen, it makes a big difference whether it was intentionally sought out or just left in the wrong place. The answer speaks to the likelihood of having the next car stolen. It also indicates whether he should focus more on the car's inherent security features or on where he parks.
Some companies do not believe they will be targeted because they are uninteresting or have little of value. There is something intuitive to this line of thinking. I used exactly this thought process for deciding never to bother locking the doors of my first car, a machine that was literally held together by coat hangers, duct tape, and staples. I reasoned that if someone were going to steal a car, they would steal a better car than mine.
But while decidedly true for my lemon, the “better car” theory of security breaks down when attacks can be automated and there is a potential positional use for every point of access. Yes, Olivia, you are a target whether or not you think you have anything worthwhile.
Targeting does not end after a network is identified. The Attacker must determine the plan and layout the tactics necessary to successfully execute and sustain the operation. This may be easy if the network were opportunistically found, but it's not as straightforward otherwise.
Targeting at this stage includes gathering technical information, like the public network presence or the software the organization uses. This is used to attack the organization from the outside in.
Targeting also includes nontechnical information such as the names, e-mail addresses, and tastes of employees. Phishing e-mails, the targeted e-mail attacks that entice a user to go to a website or perform some other action, require knowing where to cast and what to use as bait.
For example, according to Slate magazine2, the Associated Press had its Twitter account compromised with this short e-mail:
From: [An AP staffer]
Subject: News
Hello,
Please read the following article, it's very important:
http://www.washinqtonpost.com/blogs/worldviews/wp/2013/04/23
This simple and direct lure required knowing the name and e-mail address of the sending AP staffer, as well as the e-mail address(es) of the recipients, information almost certainly gathered without ever touching an Associated Press computer.
Targeting yields a series of contingencies for gaining initial access to the network. But even when one of these plans is successful, and a network is breached, targeting does not stop. In 2010, when the NASDAQ stock market exchange was compromised:
The agents figured the hackers first broke into Nasdaq's computers at least three months before they were detected, but that was just a guess.
—Businessweek3
Goodwill Industries was compromised for at least a full year and a half before anyone noticed. During this time, the Attacker most certainly continued targeting and retargeting, watching for how the network was changing, looking for another way in or out, or for another place to hide, just in case.
Targeting may be the first stage but it is also continual.
Stage 2: Initial Access
Initial access consists of penetrating any defensive security and gaining the ability to run commands or other software on one of the target's computers or network devices. This can be accomplished through exploiting vulnerabilities, leveraging network misconfigurations, social engineering, or many other means, some of which are discussed in the “Access” section later in this chapter.
Gaining initial access is the most glorified and media-hyped stage of an operation, but it is also the shortest and often the easiest.
As shown in Figure 2.4, according to the National Institute of Science and Technology (NIST) National Vulnerability Database4, the number of new reported vulnerabilities has remained around 5,000 per year for the past 5 years.
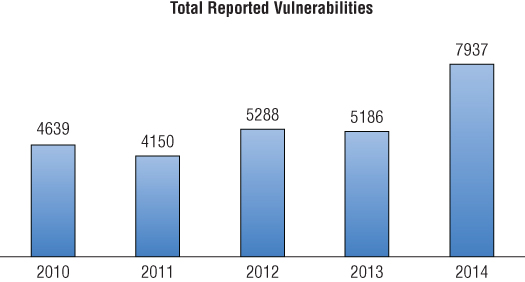
Figure 2.4 Total vulnerabilities
The vulnerabilities are scored based on a number of factors including whether they require local or remote access, the ease of exploitation, whether the Attacker must be authenticated, the impact to the integrity of the system, and so forth. The most dangerous vulnerabilities, the type often used to gain initial access, are rated “high severity,” defined as 7 or above on a 10-point scale. These vulnerabilities are showing no signs of slowing down either as shown in Figure 2.5.
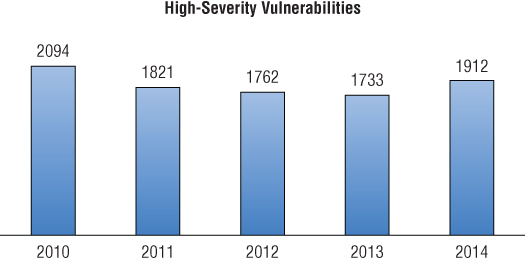
Figure 2.5 High-severity vulnerabilities
There is no shortage of vulnerabilities to gain access, and the evidence indicates the supply will continue. Yet there are different levels of initial access depending on who and what is compromised. In the physical world, a thief technically “has access” to a bank when they are standing in the lobby. This is very different than being alone inside the vault with keys to the safety deposit boxes after hours.
Likewise, initial access can vary from that of a restricted user on an unimportant computer to full access rights on a key piece of critical infrastructure. In the beginning, the Attacker will not be picky. Any access is better than none. This partially explains why, for example, there have been 70+ reported vulnerabilities in WordPress since 2010. The Attacker is unlikely to care about the information the popular website management and blogging software holds. It's probably already public. Compromising WordPress provides initial access to the web server, a toehold on the target's network. (The complete explanation is that it also gives the Attacker a way to serve up malware to others.)
Preventing this initial access is the focus of much of the security industry. Whether it's a good network design that limits the attack surface area, or an intrusion detection system that looks for known patterns of malicious network traffic, the industry has spent much of the past 2 decades trying to keep the Attacker out.
The results of this effort, unfortunately, speak for themselves. Attackers have found a way around almost every technology that seeks to prevent initial access, and once they do, they maintain that access for the long haul.
Stage 3: Persistence
Persistence is the art of turning initial access into reoccurring access. It is the foundation that makes sustaining an operation possible.
Persistence is the first defensive action of the Attacker, the consolidation and securing of future access. Vulnerabilities are unreliable. First, they are of unknown duration: some may last years, others a few weeks. Second, they do not always work. Depending on the type of vulnerability and the skill of the Attacker, success rates can vary from 1 in 10 to every time. Staking future access on a vulnerability is a poor plan.
Attackers must install their own form of persistence, commonly called a backdoor. The goal is to maintain access through normal usage, including system restarts, and to establish a reliable command and control channel.
Persistence can take many forms: an addition to the web browser, a new Run key entry, a modification to the computer's boot process, and more. The Microsoft tool Autoruns lists over 15 different methods of persisting on Windows. And those are just the approved ones.
Some methods require a user to login to become active. Others only require the computer to turn on. Regardless of form, persistence seeks to eliminate the need to ever have to repenetrate security again.
Personal security products have had varying degrees of success preventing the establishment of persistence on desktop computers. Most, for example, will catch and then prompt a user to confirm installing a driver—a privileged program that interacts with the underlying operating system.
This has caused Attackers to engage in an arms race; to redouble their efforts and find new ways to persist that are not monitored by these products; to attack the prevention methods directly; or to persist on routers, servers, or other computers that do not run personal security products. Regardless of who is winning at the moment, the persistence stage will remain a key battleground area between offense and defense.
Stage 4: Expansion
Expansion involves increasing access to a target network. This is done to establish a more robust level of persistence or to locate and access wanted data. The Stuxnet attack went after centrifuge controllers, but the initial access probably started on an unrelated computer and expanded.
Even in less advanced cases, expansion is a necessity. Companies commonly employ tiered network architectures like the sample shown in Figure 2.6.
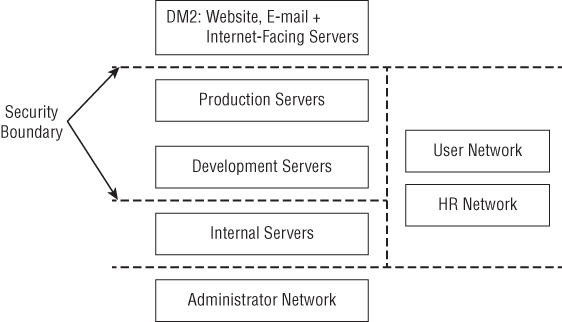
Figure 2.6 Sample corporate network
The Attacker must expand to persist. Initial access usually starts in the DMZ or on the user network. These segments are by far the most vulnerable to the outside world. However, they are also the most monitored. Beyond that, the Attacker will not want to have their access through a single point of failure. Maintaining access as the target network updates, upgrades, and expands itself is no small task.
In addition, the initial access point will rarely contain the communications, credit card databases, design drawings, or payroll data that the Attacker wants. The Attacker must expand to be successful. This information is located elsewhere, spread among different users, production servers, and internal file servers.
Expansion is time intensive. It requires surveying, collecting, and analyzing information to identify the next step of the operation. It can take months and sometimes years for an Attacker to go from her initial point of access to the virtual crown jewels.
It is also the stage of greatest Attacker susceptibility because it may require subverting internal security. For example, the Attacker may gain access to the Administrator network to bridge connectivity between parts of the company or to secure privileged credentials. Or, she may have an internal server push data to the DMZ for retrieval. These actions are not “normal” to the network.
Despite these potential anomalies, expansion is one area lacking in defensive technologies. Although products look at a specific computer's actions, to date, few, if any, can correlate anomalous actions across a network and present something actionable. Expansion is necessary, and therefore detecting it is an area for defensive improvement.
Stage 5: Exfiltration
Exfiltration is the retrieval of wanted data from the target network. There is no use in gaining access to a network if you cannot get data back out of it. Exfiltration is the ultimate measure of success for strategic and directed collection operations. Even non-kinetic CNA may have exfiltration requirements because an Attacker is going to want some sense of the amount of damage done to the network.
Initial access and expansion deal with establishing a command and control channel to the right portions of the target network. It is a different problem to retrieve large amounts of data. The Attacker must contend with the trade-off between the amount of data, the speed of retrieval, and operational security. The more data retrieved or the faster it is transmitted, the more noticeable it is.
From the Defender's perspective, exfiltration is a hard problem. When you exclude volume of data, it is difficult to differentiate legitimate outbound traffic from carefully crafted malicious traffic. There are simply countless ways to embed data going out of a network. Do your users e-mail outside contacts, use chat, post to facebook, or browse the web? If so, there is a way to exfiltrate data.
Without exfiltration there is no point to the operation, excluding the most contrived non-kinetic CNA scenarios. This stage, like others before, is performed continuously. It is and will remain a key battleground area between offense and defense.
Stage 6: Detection
Detection occurs when an operation is exposed to the target. Detection is like death: the exact timing is unknown; it may come suddenly or after a long decline.
Consider that the most sophisticated attacks known to date are just that, known.
Attacks include
- Stuxnet—Targeting Iran's nuclear program
- Flamer—Targeting various Mideast countries
- Operation Aurora—Targeting Google, Adobe, Juniper, and others
- Red October—Targeting diplomatic and government agencies, particularly in Eastern Europe
Each of these operations is suspected to be backed by nation states with enormous resources. And yet, all of them were detected. It may have taken years, but they succumbed. When that detection occurred, years' worth of offensive technological development and thousands of hours invested into the operations evaporated. Hopefully for the Attacker, there were contingency plans in place to absorb this loss. Hopefully for those and other potential targets, there weren't.
Are there other undetected operations out there? Without question. But to ignore detection as a natural part of the operational life cycle is to condemn an Attacker to a perpetual series of crises. To quote Forrest Gump, “It happens.” An Attacker must develop both their technical and nontechnical strategies accordingly.
Principle of Access
There is always someone with legitimate access and a means to use it.5
The first principle of access is the Attacker's comfort. As Duggan and Parks wrote almost 15 years ago, the virtual world is “built and controlled by humans and their tools.” No matter the security in place, some person has access to whatever the Attacker is after. The Attacker's goal is therefore to find a method to subvert and assume the identity of a legitimate user or software agent with such access. This may be difficult, but it is never impossible.
If this were a movie, then gaining access to a high-value computer network would require an elaborate disguise, retina-altering contact lenses, and a set of cables to suspend the intruder above the pressure-sensitive floor. (Okay, did anyone else think about how the CIA could have saved millions of dollars on biometric locks and pressure-sensitive flooring by hooking up a $100 motion detector to a $5 air horn? I digress.) Outside the movies, impersonating a legitimate user is much less elaborate.
The approach the Attacker takes to gain initial access depends on the type of connectivity the target network offers. There are four basic types of connectivity: inbound access, outbound access, both, and neither. Each type presents a different type of challenge to overcome.
Inbound Access
A network that enables inbound access means that someone from outside the network can initiate a connection into the network as shown in Figure 2.7.

Figure 2.7 Network with inbound access
Inbound access can be open to everyone, like a public website, or restricted. When restricted, access is controlled by one or more of the following: something one knows, something one has, or the virtual location.
The “know” part is typically a password; though it may also be a VPN key, a picture selection, or a specific mouse movement, among other things. The user connects, is prompted to enter a password or perform some kind of action, and access is granted.
The “have” part is a physical item, such as a secure key fob or a cell phone. The user confirms possession of the item by sending information that only the item's possessor could have, such as a random confirmation code sent via a text message to the phone.
The “virtual location” of access control limits connections to those originating from specifically allowed network addresses. Unless the user initiates the connection from a specific point, the connection will be denied. This method of access control is meant to limit the avenues of attack.
Each of these forms of access control is subject to attack. Passwords, or any form of knowledge, can be guessed or stolen. Hardware tokens can be stolen or reverse engineered. The latter was done in March 2011, when someone hacked RSA, the provider of SecureID tokens for two-factor authentication, and then used this information to break into several U.S. defense contractors.
Cell phones can be stolen or infected with malware. A malicious program for smart phones dubbed Zeus-in-the-mobile, or ZitMo, intercepts banking codes known as mobile transaction authentication numbers (mTAN) and forwards them to the Attacker. This allows the Attacker to gain the access necessary to initiate banking transactions without physical access to the victim's phone.
Finally, controlling by virtual location just moves the line of defense one hop out. Defense becomes as effective as that next network. When Attackers learn the allowed points of origin, they will gain access by compromising those networks first.
The previous attack methods work by impersonating legitimate access. There are also methods of gaining illegitimate access. The Attacker may circumvent all access control by exploiting an exposed software service. This is done by taking advantage of a logic or programming flaw in a software program that is accessible by outsiders. The famed Morris Worm, which allegedly took down some 10 percent of the Internet in 1988, spread by this method.
Illegitimate access can also be gained by escalating privileges. This means the Attacker leverages regular user-level access, such as that provided by Facebook, Netflix, or thousands of other companies, to gain more access or gather more information than the company intended to grant. The social media texting and photo-sharing application Snapchat fell victim to this kind of attack when someone managed to leverage a regular user account to gather the account information of millions of other users.
In short, allowing any kind of inbound access increases the target's susceptibility. In addition, attacks can be waged on the Attacker's time frame. Most inbound access is open 24 hours per day, 7 days a week. The Attacker can hammer away at finding inbound flaws around the clock.
Yet there are no easy answers. Denying all access may deny a company's employees the flexibility of working from home. It may stop a headquarters IT person from fixing issues in a satellite office. It may prevent communication with vendors or customers. In some cases, like the aforementioned Snapchat, having users that can access inbound services is what makes their business a business.
Denying all inbound access is not realistic. The Attacker knows this and will look for ways to impersonate legitimate access or grant themselves illegitimate access.
Outbound Access
A network that allows outbound access means that someone from inside the network can initiate a connection to somewhere outside the network as shown in Figure 2.8. If someone can browse the web, then the network allows outbound access. Most networks do.

Figure 2.8 Network with outbound access
How does the Attacker go after a network when there is nothing accessible from the outside to attack? Simple. They get the user to do something that connects out to them. This often begins with an e-mail.
E-mail Attacks
E-mail is a common approach to attacking a network with outbound connectivity. There are three basic approaches to an e-mail attack: attachments, attacking the e-mail program, and malicious links.
The first generation of malicious e-mail attachments was to attach an executable program to an e-mail and ask the user to execute it—simple, direct, and for a long time, effective. The attached program might pretend to do something useful such as play a video or extract compressed files, or it may appear to do nothing at all, but in the background, it would install something to grant access to the Attacker. This blatant approach still works now and again, but automatic filtering and user awareness has cut down on its effectiveness.
The second generation of e-mail attachments were not programs, but documents that contained the ability to run code. Most notably, the Microsoft Office product line offered a “macro” feature by which people could script certain behavior within a document, such as inserting the current date or restricting a field to numbers only. The macros had few restrictions. They could, for example, access the e-mail program Microsoft Outlook and send a copy of the document to the first 50 e-mail addresses in the address book. This is what the Melissa Virus did in 1999 to infect hundreds of thousands of computers. Microsoft has since instituted macro security to prevent this kind of blatant behavior.
The third generation of e-mail attachments were programs again, but they didn't seem to be programs. Files with esoteric extensions such as .chm or .hta would slip through the filters and be run by users. The so-called iLOVEYOU virus spread as LOVE-LETTER-FOR-YOU.txt.vbs, and Microsoft Windows by default would helpfully hide the .vbs part of the file and make it look like a harmless text file. E-mail filters have since been updated to catch most of these; though occasionally something slips through.
The final and current generation of e-mail attachments takes advantage of the programs that open them. These attachments are Microsoft Word documents (.doc), Excel spreadsheets (.xls), Adobe PDFs (.pdf), compressed files (.zip), or other third-party application-specific documents. When these poisoned documents are opened, they exploit vulnerabilities within the applications themselves to execute Attacker-supplied code. Go check the spam folder on a Yahoo, Hotmail, and Gmail account to find a recent example.
The next e-mail-based attack approach is to send a specially crafted e-mail that corrupts the e-mail program into executing Attacker-supplied code. This is the ideal attack because it requires nothing more from the user than previewing or viewing the e-mail. The extra step of opening an attachment is not necessary. These types of attacks were quite common in the early days of Microsoft Outlook and Outlook Express. Though they have waned, they still crop up now again against Outlook, Lotus Notes, or other popular corporate e-mail clients.
The last e-mail-based attack approach is to send a link to a website. Most users have heard the admonition against opening attachments, but what is so harmful about a link? People browse the web and go to random websites all the time. This is exactly the point. Because of conditioning, a link seems much less dangerous.
However, these links bring the user to websites that are specifically designed to leverage vulnerabilities in web browsers or their plug-ins. Internet Explorer, Firefox, Safari, Chrome, and other less popular browsers have all had numerous vulnerabilities in which just visiting a website is enough to give the website operator control of the client computer. And even if these web browsers were perfect, which history shows otherwise, there are myriad plug-ins that have an even worse track record. Active X, Flash, and Java are often used to make websites seem more interactive, and they have been a historical death knell to browser security. Links are just as unsafe as attachments.
Again, there are no easy answers. Opening e-mails from only those people you know isn't practical for most businesses, and even if it were, it isn't much protection. E-mail is easily spoofed. Beyond that, the sender may be compromised. Virus after virus has made use of people's e-mail address books to spread themselves in a more convincing manner.
E-mail attacks are executed with the goal of gaining a foothold on the network. After that foothold is gained, the Attacker can circumvent outbound restrictions as explained in “Circumventing Outbound Restrictions” later in the section.
Website Hijack Attacks
Using e-mail is not the only way to gain a foothold on the network that only allows outbound access. Another approach is to commandeer legitimate sites that the Attacker knows or hopes a target user will visit. These have been dubbed “watering hole” attacks because the Attacker waits for the target to come to them. This has the same result as an e-mail link–based attack except it does not require the e-mail to direct the user.
There are a few ways of commandeering a site. The first, and most obvious, is for the Attacker to take over and replace the content of a popular website with malicious code. Generally, the Attacker inserts a small amount of code into the existing website so that nothing appears amiss to the user.
The second approach is to use a cross-site-scripting attack (XSS). In the more dangerous form of this kind of attack, the Attacker uploads code that the website then displays to other users—any site that allows users to post information or comments, such as Monster.com, is potentially vulnerable. You may think you are just viewing the profile of John Smith, when in reality, John's online resume contains malicious code that attacks your browser directly or redirects you to another site that does. As the target, you are visiting a legitimate site, and yet you may still be compromised. Ebay, LinkedIn, Facebook Chat, Twitter, the NYTimes, and countless other household-name websites have had cross-site-scripting vulnerabilities.
A third approach avoids commandeering the website itself, but instead hijacks the domain name. The domain name system, or DNS, allows users to find and connect to computers by name instead of by the more esoteric IP address. Every website, for example www.example.com, registers its name with a domain name registrar, which responds to queries about where the computer with that name is located. Browse to www.example.com, and behind the scenes, your computer will query a DNS server, get a response of 93.184.216.119 (as of this writing), and then connect to that address.
The registrars are vulnerable to being hacked or tricked into changing this information. When this happens, and you browse to www.example.com, your browser will be redirected to somewhere else entirely. In 2013, a group hijacked the security company Rapid7's website in this manner by sending a spoofed fax to Rapid7's registrar, Register.com. This particular case was immediately obvious as the group defaced the site with a political message, but other examples have been more subtle and served up malicious software.
Finally, commandeering a website may not even be necessary. Ad networks serve up advertisements that can be placed by anyone, including the Attacker, across a wide range of websites. Most advertising companies attempt to sanitize malicious code from the ads before displaying them, but they are not always successful.
There are also many shady malware serving websites and a plethora of “free” software that is tainted and posted for download. Many of these websites are intertwined with pornography, illegal software, or pirated movies, all things that human nature seems to seek out. Name any company over 1,000 employees, and odds are there will be at least one employee there that has used a company computer to browse these parts of the Internet while at work, opening the company up to an intrusion.
Website hijacking attacks have one goal in common: to provide a method of attacking a network that allows only outbound connections. There are many different ways to accomplish this task, but all are a type of positional access operation designed to lead one step closer to the target.
Other Attacks
There are still more ways to go after a network that allows only outbound access. Someone could spread malicious thumb drives in the parking lot. In 2011, the Department of Homeland Security performed this exact test against several federal agencies and contractors. Roughly 60 percent of CDs and thumb drives picked up were inserted into a computer; 90 percent if they contained an official logo; and it only takes one instance to breach security.5
Or give thumb drives out as part of a gift basket as the Russians did for diplomats at a G20 meeting. You know what they say “Beware of Russians bearing removable media.”
The Attacker may look for employees with company laptops. If people connect the laptop to both their home network and the corporate network, the corporate network is only as secure as their home network.
The Attacker may also look for wireless access points they can reach. Does the company share an office building with someone else? Then someone else can likely sit unwatched and attempt to penetrate the wireless network for hours on end.
Speaking of wireless, smartphones have provided an entirely new vector. If a person is allowed to bring their phone into work and connect it to the company wireless network, there's another attack vector to gain access from the inside.
Certainly there are even more technical methods.
On the nontechnical side, there is just plain calling people and asking them to do something that compromises their security. This is called social engineering, and as Kevin Mitnick famously detailed through his escapades compromising the security of PacBell and other organizations, it is quite effective.
There are also physical access attacks such as breaking in and installing hardware or software, getting a job at the target, or by paying off an insider. These require a geographically colocated Attacker, a hurdle to be sure, but they are possible.
Between e-mail, website hijacks, and other attacks, the Attacker has many different possible ways to gain initial access to a network that only allows outbound connections.
Circumventing Outbound Restrictions
All the preceding methods can gain the Attacker access to a single computer on the network, but it still doesn't solve the problem of how to communicate with that computer. The network may allow outbound access, but that access may be restricted.
The first way to restrict access is through software running on the host computer, such as parental control software. This type of software monitors all outbound connections and either allows them, blocks them, or prompts the user asking what to do. Personal security products, such as Kaspersky Internet Security or McAffee Internet Security, use this method. “XYZ process is trying to connect to www.example.com. Do you wish to allow?”
The Attacker might rely on the user to click “Allow.” Or they may attack the host-based software directly and attempt to prevent that message from ever appearing. All host-based software has a way to override it if a person has full system access. It must. At a minimum, the program must have a way to be uninstalled.
Early versions of personal security products did a poor job of preventing local users from overriding their settings. Access lists were unencrypted and could be modified to add malicious software. User prompts could be closed directly by the malicious program by spoofing mouse clicks. But companies learned their lesson and now host-based security programs such as McAfee, Kaspersky, and Symantec guard against this weakness and do all sorts of things to prevent users, even privileged users, from easily disabling their software. Ultimately, this just leads to an ongoing war of attrition in which, at any given moment, one side is winning.
The second way to restrict access is through software or hardware on the network, such as a firewall or proxy server. A firewall allows or denies network traffic based on a set of criteria such as the type of traffic or the destination. A proxy serves as an intermediary between a computer and the desired network destination.
Altering or overriding network restrictions is not as straightforward as attacking host-based software. The Attacker must gain access to the network device itself. Given the diversity of network layout and types of devices, doing this “blind,” that is, with preprogrammed software, is difficult.
Therefore, to circumvent these network devices, the Attacker generally needs to establish a command and control channel into the network to make intelligent decisions. Establishing this channel, however, requires circumventing the network device first. Chicken, meet egg.
Rather than confront the problem, the Attacker avoids it by establishing outbound connections via allowed network protocols, that is, e-mail, Facebook message, instant message, and so on. This reduces the problem from attacking network devices to just determining what type of network traffic is allowed out. And this is a much easier problem.
Outbound network restrictions are notoriously porous because strict policies tend to get in the way of business. Try blocking all outbound web traffic, and what happens to the HR employee trying to research state law or search resume sites? The same thing that happens to the marketing employee researching the competition. Their work stops. This bias toward actually getting work done weakens outbound restrictions considerably.
Of course, it may seem that if the Attacker is trying to connect out of the network, they already have access. This is one-half true. The Attacker may gain initial access from a Trojan e-mail attachment or any of the methods previously mentioned, but until communication is established, the Attacker does not yet have repeatable access. In a network that allows outbound access only, the Attacker's challenge is to leverage this initial software execution to circumvent host-based and network-based restrictions and establish command and control.
Bidirectional Access
Bidirectional access, as shown in Figure 2.9, is the norm for most networks. Some types of connections are allowed in and others allowed out. Each direction may have its own set of access controls, restrictions, and monitoring.
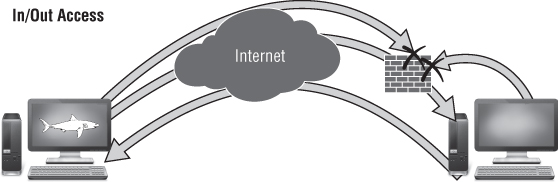
Figure 2.9 Network with bidirectional access
A more complicated network will also be segmented where specific parts of it are allowed to connect in or out in certain ways. Inbound access may be allowed to the company website but nowhere else. Users in the IT group may be allowed to use the file transfer protocol (FTP) to download data, but users on the regular user segment of the network are blocked.
The Attacker approaches a bidirectional network following the path of least resistance. Perhaps they gain initial execution via a website hijacking attack, but then they use that to open an inbound path. The Attacker mixes and matches approaches for the greatest effect.
No Outside Access
A network with no outside connectivity is commonly called an isolated network or an “air-gapped” network. (The term air-gapped was invented before wireless networks.) This network is physically separated from the Internet as shown in Figure 2.10. Access is controlled first and foremost by physical presence: the gates, guards, and locks of the buildings in which it is housed.
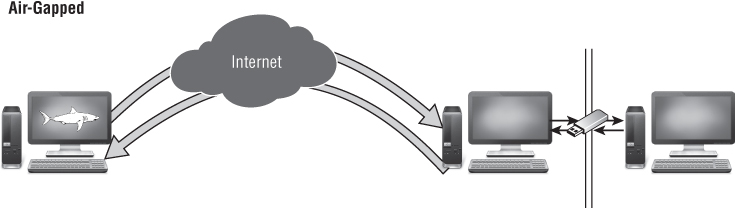
Figure 2.10 Air-gapped network
An air-gapped network takes the security versus convenience trade-off to the extreme. It is the most secure network configuration possible to protect against outsider threats and the most inconvenient for sharing information or administering.
Most secure, though, does not mean invulnerable. It just raises the bar. To gain access, the Attacker must breach physical security or trick, cajole, bribe, or blackmail users into doing it for them. A few theoretical examples of this have been covered: thumb drives in the parking lot, compromising phones or laptops that are moved into and out of the network. But there are also real-world examples.
Kevin Mitnick exploited physical security and gained access to telecommunication systems by dressing as a telephone repairman and using the right jargon and other social engineering tactics. The networks may not have been air-gapped, but they could have been. It would not have mattered. He gained access without breaking a single lock or disabling a single alarm.
In 2010, an air gap did not prevent the Stuxnet worm from compromising the stand-alone network at Iranian nuclear facilities. The method of Stuxnet's introduction is unknown and likely to stay that way, but it is possible the person was an “unwitting” insider threat, someone who moved data to the network but did not realize it contained a threat.
And, of course, there are perfectly “witting” insider threats. In 2013, an air gap (presumably) did not prevent Edward Snowden from taking an untold number of classified documents from the National Security Agency and handing them to the press. Again, the network may or may not have been isolated, but it doesn't matter; the attack would have worked just the same.
For an air-gapped network, the Attacker must find a way to be, to corrupt, or to compromise an insider. When achieved, this reduces the problem of physical access to one of insider threat security, a much easier problem.
Access Summary
Someone has legitimate access to each thing the Attacker wants. The Attacker's challenge is therefore to either circumvent any access controls, or impersonate or corrupt someone that is allowed through. Exactly how this is approached will change depending on the nature of the network. Regardless, the first principle of access means that though this task can be made extremely difficult, it is always possible. All security systems have a weakness, the legitimate users, and these people are exploitable.
Principle of Economy
Ambitions will always exceed available resources.
All ambitions are tempered by the constraints of reality. Whether it is finding targets, exfiltrating more data, or improving one's position on a network, there is always more that could be done and not enough resources to do it. Understanding these constraints is paramount in building an offensive framework.
The types of resource constraints are constant across different operations; though which resource is in shortest supply will vary greatly from day to day and from operation to operation.
Time
Time is required to conduct all stages of an operation. And it is critical for most every objective. Finding out about a drug shipment 2 months too late is not particularly useful if the goal was to intercept it.
There is only so much time the Attacker can spend on any specific target or on any one aspect of an operation. Time limits the development of offensive capabilities and the accumulation of expertise. It eats away at existing capabilities and makes technical knowledge stale. Time affects the development and use of all other resources and is therefore the most important constraint.
Targeting Capabilities
Targeting is often the most difficult and expensive part of an operation. It may require all source intelligence that collectively identifies information about a country's political, economic, or military structure. Though much is available on the Internet, much is not. In some cases, it may require the intelligence resources of a nation-state to gather.
But gathering this kind of information is not the only skill required. When gathered, targeting may require linguists, analysts, technical expertise, and subject matter experts in the target's field. For example, if Attackers want to steal from a Saudi Arabian bank, they likely need fluency in Arabic and detailed knowledge of how financial transactions work, even if they already have full access to the bank's network.
Assembling, maintaining, and training an effective team with all these varied skillsets is nontrivial and places a limitation on the Attacker's overall operational abilities.
Exploitation Expertise
Exploitation is the ability to find and exploit vulnerabilities in software programs, hardware devices, or network configurations. This expertise is required during initial access, persistence, and expansion. Without exploitation expertise, the Attacker cannot perform even the most basic operation.
Exploitation expertise requires detailed low-level knowledge of programming languages, operating systems, and hardware. It requires understanding compilers, memory managers, program data structures, and more. The practiced exploitation engineer needs the ability, patience, and mind-set to reverse engineer programs and devices to extract the most minute details and then manipulate them to his advantage.
Few of the technical skills necessary to find and develop vulnerabilities into real-world exploits are taught in the typical college curriculum. A security course may teach what a buffer overflow is and how to avoid creating one, but there is questionable academic value in teaching the intricacies of how it can be exploited to compromise a computer. Academic programs that do are the exception. Therefore, the exploitation skillset must be learned outside of standard programs, making it hard to find and expensive to cultivate.
Of course, there is no shortage of publicly available exploits that the Attacker can download and use. Money can also help mitigate the problem as exploits are routinely sold on gray and black markets for anywhere from thousands to hundreds of thousands of dollars. Yet regardless of whether the exploitation expertise is in-house, copied, donated, or purchased, it is a valuable resource necessary for all operations.
Networking Expertise
Networking expertise is the in-depth understanding of the myriad technologies used to build, operate, manage, and monitor a computer network. It is required throughout an operation, but most important during initial access, expansion, and exfiltration.
Now, generally Attackers do not have the benefit of network diagrams and configurations to guide them through. From the moment of initial access, Attackers are in the middle of a fog. While initially ignorant to their surroundings, they have to find a way to safely establish communication, to persist, to expand, to traverse, and to search a network, all while remaining hidden. (One of the objects of their search will certainly be for networking diagrams to make all this easier.)
These tasks require a thorough understanding of networks. Target networks can range from a few devices connected together via a single switch to thousands of computers and hundreds of switches that span continents. The technology involved can span decades, from old decrepit mainframes to the shiniest new application servers. In spite of this variety, Attackers must quickly gain their bearings and act.
Networking expertise creates the ability to envision plausible layouts, configurations, policies, and potential traps from little information. It is essential to exploiting a network efficiently.
Software Development Expertise
Software development expertise is the ability to develop, debug, maintain, expand, and test quality custom-built software. It is required to create robust attack, data collection, and analysis tools that are essential to all elements of the operational life cycle.
In most respects, software for CNE is no different than any other software project. However, additional constraints are placed on the CNE software engineer that are unusual to typical commercial software.
Foremost, CNE software must be fault tolerant to the extreme. Telling the “user,” that is, the target, to reboot and try again is not an option. The software used during initial access, for example, cannot report any form of success or failure unless the core of the program itself is successful. This is another chicken-and-egg problem that can be addressed only by writing software that rarely fails.
CNE software must also be highly efficient and consume few computing resources or bandwidth. There is no displaying an hour glass or spinning wheel to indicate the computer may be slow for a moment while a task completes. The slightest hiccup in performance could push a user to investigate.
CNE software often explicitly breaks or circumvents operating system and program norms. This makes it extremely sensitive to minute variations in the target environment, an environment the Attacker has no control over and little foreknowledge of. This raises the bar substantially for testing because even something as little as the current level of memory usage can affect some tools.
Finally, and perhaps the biggest difference, CNE software must work even though other programs are specifically designed to counter it. Though commercial software developers may deal with incompatibilities, none are worried about software that is specifically designed to seek out and destroy it. Okay, that is an overstatement. Defensive security vendors deal with the same problem, as do the engineers that create software licensing systems. These software development efforts are directly attacked by the CNE and pirating communities, respectively. Regardless, withstanding direct attacks is a different kind of mind-set that requires cultivation.
Altogether, a specialized and often-constrained form of software development expertise is required to create the tools used in all aspects of an operation. Without it, operational capabilities will stagnate and through time become completely ineffective.
Operational Expertise
Operational expertise is essential to creatively sustaining operations in the face of adversity. If operations were simple and experience without value, then Attackers would have long ago completely automated the process. (The easier parts have in fact already been automated.)
Rather, operations are complicated and require active decisions ranging from the trivial to the transformative. The most important of these decisions is what to do when things go wrong, when the software fails, when the network is not laid out as believed, and when the proverbial plan falls part. The collection software failed, and there's no indication why. Was it found and removed? Is there some incompatibility that was never tested? Should it be restarted? There is no easy template for answering these types of questions. Experience is required.
Attackers with operational expertise can adapt existing or improvise new techniques to accomplish their operational objective while remaining undetected. Like exploitation expertise, this skill is not taught in a standard IT program. It must be learned through real-world experience.
Operational Analysis Expertise
Operational analysis is leveraged to direct each step and every movement of the Attacker in every stage of the life cycle. Operational analysis may range from diagraming the network, identifying users, searching through collected data, translating documents, or aiding in the selection of tools to manage the Attacker's profile.
Depending on the operation, operational analysts may have a total lack of information or complete overload. They must not only analyze the information they have, but also determine what they are lacking. Analysts must synthesize information from disparate sources across disciplines to answer urgent questions.
For example, an operational question might be, “If and when will the target upgrade?” This simple question is crucial for sustaining an operation. Answering it may require understanding the target's finances, their access to new equipment, their update history, or even the temperament of the system administrators. This is not a simple task.
Operational analysts require years of both technical and nontechnical experience to be effective, and like the other skillsets mentioned, it is not taught.
Technical Resources
Technical resources include those things necessary to conduct operations. Examples include infrastructure, bandwidth, software, and more.
Some technical resource issues can be addressed with money. If Attackers need more bandwidth, they can buy more bandwidth. More computers (depending on the country) are just a click and a shipment away.
Others resource issues, however, may have no readily available solution. For example, a target may use proprietary technology that is hard to acquire for analysis. Do you know what a 40-year-old power plant in Turkmenistan uses to control internal processes? I don't. But whatever it is, I doubt it can be ordered on Amazon.com. This target-imposed technical constraint is not easily overcome.
Yet of all the constraints of economy, technical resources are of the least concern. Smart, capable, and creative Attackers with enough time and money will undoubtedly find a way around any technical resource constraint.
Economy Summary
Attacker ambitions will inevitably exceed available resources. This is especially true because attacking requires specialized skill sets and experience not commonly taught. Talent is the key economic concern of any Attacker, regardless of resource level or structure.
Attacker Structure
There's a saying in the design of modern architecture that “form follows function.” This tenet, first put forth in a poem by Louis H. Sullivan, means that the structure of a building, an organization, indeed “of all things physical and metaphysical, of all things human” comes from its purpose.
The technical purpose of the Attacker is to move through the operational life cycle and exfiltrate information while avoiding detection. If we assume the Attacker is flexible and efficient, we can infer a form or structure from the purpose.
Each stage of the operation requires different, though sometimes overlapping, technical and operational skillsets to execute. A human and economical approach would be to split these skillsets and corresponding functions into operating units.
Evidence for this approach is shown in the findings of Operation SMN, “a coordinated effort amongst leading private-industry security companies, led by Novetta,” 6 in its analysis of the so-called Axiom Attacker, suspected to be part of Chinese intelligence.
We also assess that different groups associated with the Axiom threat actor group likely perform various phases. This deduction is supported by the number of differences in the observed activity during these compromise stages which suggest a number of separate teams with varying responsibilities during their operation lifecycle… [D]ifferences in command and control (C2) and midpoint proxy infrastructure displayed… have led us to believe that the operational tempo, security policies, and acceptable risk levels are drastically different.6
So what might these groups be? Again, The operational life cycle consists of targeting, initial access, persistence, expansion, and exfiltration. And these require targeting, exploitation, networking, and other areas of expertise laid out in the “Economy” section of this chapter.
With this knowledge, we can postulate what a working structure for Axiom might be:
- Targeting—The driver of the overall operation. They are the high-level team that ultimately gives the orders for what to go after. They are steeped in the technical, political, or other importance of the target.
- Door kicking team—The driver of initial access. Their mission is to get in and establish communications. This team comprises or is supported by a general-purpose vulnerability discovery team and a tactical vulnerability discovery team for finding cross-target vulnerabilities and target-specific vulnerabilities, respectively.
- Rapid analysis team—The driver of persistence and immediate expansion. Their mission is to find out as much as they can as quickly as possible and establish redundant command and control. This team comprises or is supported by a tactical software development team capable of creating the customized solutions Axiom deployed.
- Networking team—The driver of long-term expansion and exfiltration. Their mission is to creep through the network and attain an ever-higher level of access while finding the optimal methods of exfiltrating data. This team comprises or is supported by networking engineers and a general-purpose software development team.
- Maintenance team—The driver of sustaining the operation. Their mission is to keep abreast of changes in target network layout or security posture while continuing to burrow ever deeper and steal ever more.
- Infrastructure team—The driver of finding, compromising, and maintaining viable website or e-mail domain attack vectors, command and control infrastructure, and often transient exfiltration points. This team may be supported by the same vulnerability specialists used in the rapid analysis team.
In total, this is six separate functional teams with up to four support teams.
Is this truly how Axiom is structured? We can only make an educated guess. Perhaps some operational functions are shared within a single team or others are further subdivided. Perhaps they have smaller multidisciplinary attack teams, more like a Special Forces unit.
In the end, the specific structure is irrelevant as it will be different between different Attackers. But understanding the general structure that Axiom requires to perform operations leads to some conclusions:
- Attackers are composed of specialists with depth of skill.
- Coordinating specialties requires some level of organizational complexity.
- The communication between units is a potential weak point. Given the Attacker is human, the different tempos, risk tolerances, tools, expertise, and leadership of the units will inevitably lead to miscommunication and potential mistakes.
Finally, the professionalism of a group like Axiom requires a strategy to build, manage, and lead. The defense will require a similar level of depth, coordination, and strategy, a bigger well-directed boat as it were, to avoid getting eaten alive.
Summary
Attackers are human, and this humanity drives the objective and nature of operations. Within those operations, there will always be a way for Attackers to gain access, whether remotely or by compromising an insider. Always. However, the ability of Attackers to find or leverage this potential access is limited by economic constraints. Together these first principles of humanity, access, and economy underlie all aspects of Attackers, their structure and their actions.
In the next chapter, we'll investigate how these same first principles impact the defense.
