Chapter 4
Firewall Practical Applications
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to:
![]() Explain the requirements of single machine, small office, network, and enterprise firewalls.
Explain the requirements of single machine, small office, network, and enterprise firewalls.
![]() Evaluate the needs and constraints of an individual or company to determine what type of firewall solution is appropriate.
Evaluate the needs and constraints of an individual or company to determine what type of firewall solution is appropriate.
![]() Compare popular firewall solutions.
Compare popular firewall solutions.
![]() Recommend an appropriate firewall solution for a given situation.
Recommend an appropriate firewall solution for a given situation.
Introduction
Chapter 3, “Fundamentals of Firewalls,” discussed the conceptual basis for the firewall. It described the various approaches to packet filtering used by different sorts of firewalls. This chapter examines the practical aspects of firewall selection. Firewalls can be classified based on a number of different criteria. In Chapter 3 these were classified based on configuration and type. This chapter classifies firewalls based on the practical situation in which they will be used.
Each section of this chapter examines the practical requirements of each category. We will look at the security needs, as well as budget limitations. Then we will examine one or more actual products designed for that environment. However, in no case am I specifically endorsing any product. I chose firewalls based on how widely they are used because the most widely used firewall solutions are the ones you are most likely to encounter in your career, regardless of their technical merits.
All firewalls can be categorized in the groups discussed in Chapter 3. This means they can be packet filtering, stateful packet inspection, application gateway, or circuit gateway. It is rare today to find a commercial firewall that is only packet filtering. Most commercial firewalls support additional features such as including intrusion detection and VPN connections, and some even have built-in antivirus. It is also common for commercial firewalls to support both blacklisting and whitelisting, described in Chapter 3.
Regardless of the firewall solution you choose, these devices need to be monitored. They also require updating/patching. You cannot simply install them and forget them.
Using Single Machine Firewalls
A single machine firewall is a firewall solution running on an individual PC (or even a server). Home users often protect their computers with single machine firewalls. In many cases, security-conscious organizations set up individual firewalls on all workstations on their network in addition to the firewall solution used for the network itself. I recommend that strategy over simply having a perimeter firewall. That is not to say there does not need to be a perimeter firewall. I am simply stating that you should not rely only on the perimeter firewall. Regardless of which scenario you are working in, single machine firewalls have many things in common:
![]() These can be packet filtering, SPI, or even application gateways.
These can be packet filtering, SPI, or even application gateways.
![]() All are software based.
All are software based.
![]() Most are easy to configure and set up.
Most are easy to configure and set up.
Most single machine firewalls were designed with the home user in mind, though some are more sophisticated. For example, single machine application firewalls are often designed to run on a database or web server, and provide an additional layer of protection to that device.
For example, more than one virus has spread by scanning nearby machines on a network, looking for open ports and connecting to that port. One version of the infamous MyDoom virus used port 1034 to facilitate its spread. A network that had all individual machines with their own firewalls blocking port 1034 would be immune to this avenue of attack even if one of the machines on the network was infected. In fact, it is common for malware such as Trojan horses to use specific ports. Having a firewall block all of those ports on individual machines is a significant improvement in security. In short, having individual firewalls on all workstations means that even if one machine is breached, the breach will not necessarily affect all machines on the network. We will examine the Windows 10 firewall, a Linux firewall, and a couple of commercial firewalls (i.e., ones that don’t come with the operating system but must be purchased separately). Note that the Windows firewall interface is very similar in Windows 8/8.1, Windows 10, and Server 2016.
When you select a single machine firewall solution, keep in mind that most were designed with several assumptions. Since the home user is the primary target customer for these products, ease of use is generally a high priority. Secondly, most of these products are very low cost and in some cases free. Finally, you should keep in mind that they are not meant for highly secure situations but merely to provide essential security for a home user.
Windows 10 Firewall
Windows first started shipping a primitive firewall, called Internet Connection Firewall (ICF), with Windows 2000. It was very simple. Each version of Windows since then has expanded upon this idea. Windows 10 ships with a fully functioning firewall. This firewall can block inbound and outbound packets. To access the Windows 10 firewall, click the Start button and type Firewall. The basics of the Windows 10 Firewall can be seen in Figure 4-1.
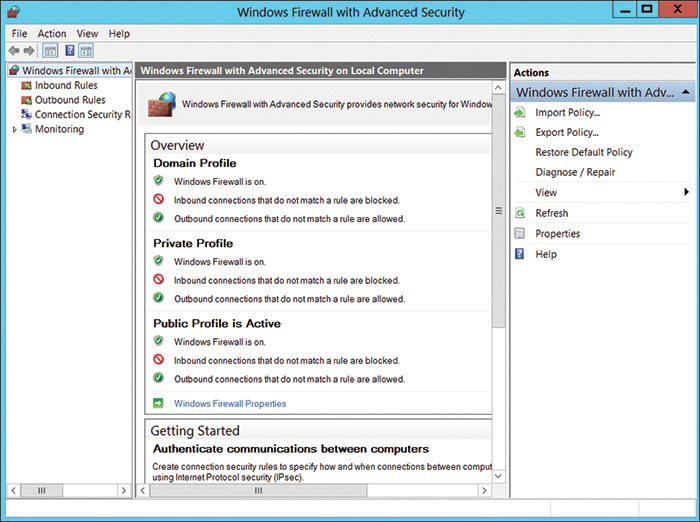
FIGURE 4-1 Windows 10 Firewall
Note that this looks the same as the firewall settings in Windows Server 2012 and 2016, but different from those in Windows 7.
Beginning with Windows Server 2008 and all versions after that, Windows Firewalls are stateful packet inspection firewalls. With the Windows 10 Firewall, you can set different rules for outbound and inbound traffic. For example, your standard workstation will probably allow outbound HTTP traffic on port 80, but you might not want to allow inbound traffic (unless you are running a web server on that workstation).
You can also set up rules for a port, a program, a custom rule, or one of the many predefined rules that Microsoft has for you to select from. You can also choose not only to allow or block the connection, but to allow it only if it is secured by IPSec. That provides you with three options for any connection.
Rules allow or block a given application or port. You can also have different rules for inbound and outbound traffic. The rules allow you to decide whether a particular type of communication is blocked or allowed. You can have different settings for inbound and outbound traffic. You can set rules for individual ports (all 65,554 available network ports) and for applications. The rules in the Windows firewall give you a lot of flexibility.
More importantly, you can apply rules differently depending on where the traffic comes from. You can set up rules for three areas or profiles:
![]() Domain: For those computers authenticated on your domain.
Domain: For those computers authenticated on your domain.
![]() Public: For computers from outside your network. You would treat outside traffic more carefully than traffic coming from another machine in your domain.
Public: For computers from outside your network. You would treat outside traffic more carefully than traffic coming from another machine in your domain.
![]() Private: Private refers to traffic from your own computer, thus the term private.
Private: Private refers to traffic from your own computer, thus the term private.
Administrators should always follow these rules with all packet filtering firewalls:
![]() If you do not explicitly need a port, then block it. For example, if you are not running a web server on that machine, then block all inbound port 80 traffic. With home machines you can usually block all ports. With individual workstations on a network, you may need to keep some ports open in order to allow for various network utilities to access the machine.
If you do not explicitly need a port, then block it. For example, if you are not running a web server on that machine, then block all inbound port 80 traffic. With home machines you can usually block all ports. With individual workstations on a network, you may need to keep some ports open in order to allow for various network utilities to access the machine.
![]() Unless you have a compelling reason not to, always block ICMP traffic because many utilities such as ping, tracert, and many port scanners use ICMP packets. If you block ICMP traffic, you will prevent many port scanners from scanning your system for vulnerabilities.
Unless you have a compelling reason not to, always block ICMP traffic because many utilities such as ping, tracert, and many port scanners use ICMP packets. If you block ICMP traffic, you will prevent many port scanners from scanning your system for vulnerabilities.
![]() Occasionally, I would suggest continuing to write out acronyms such as ICMP just to make sure this is reinforced.
Occasionally, I would suggest continuing to write out acronyms such as ICMP just to make sure this is reinforced.
The Windows Firewall also has a logging feature, but it is disabled by default. Turn this feature on (when you configure the firewall you will see a place to turn on logging). Check this log periodically. You can find more details on the Windows 10 Firewall at https://docs.microsoft.com/en-us/windows/access-protection/windows-firewall/windows-firewall-with-advanced-security.
FYI: Log Files
If you are using the Windows Firewall on a workstation within a network that already has a perimeter firewall and the Windows Firewall on all workstations, you may not want to turn on the logging because reviewing the log for your perimeter firewall and all the workstations’ firewall logs is impractical. The sheer cumbersome nature of reviewing all of those logs makes it likely that they will never be reviewed.
Typically, you will review logs on your perimeter firewall and on all server firewalls, but not on workstation firewalls. Of course, if your security needs dictate that you log all system firewalls and you have the resources to routinely review those logs, it is certainly a good idea to do so.
User Account Control
User Account Control (UAC) is not a firewall technology but is strongly related to security. Windows Vista first introduced it, and it has been expanded in Windows 7 and it still exists with Windows 10. UAC is a security feature that prompts the user for an administrative user’s credentials if the task requires administrative permissions. UAC was first introduced in Windows Vista, but with Windows Server 2008 and Windows Server 2012, and beyond, it has become much more fine tunable. This feature allows you to decide how you want the user account controls to respond. It is not just an on or off proposition; degrees of filtering are available.
Linux Firewalls
Linux has firewall capabilities built into the operating system. This has been a part of the Linux operating system for many years, with occasional improvements in the technology.
Iptables
The first widely used Linux firewall was called ipchains. It was essentially a chain of rules for filtering traffic, thus the name. It was first introduced in version 2.2 of the Linux kernel and superseded the previous ipfwadm (which was not widely used). The more modern iptables replaced ipchains and is the primary firewall for Linux. The iptables service was first introduced in Linux kernel 2.4.
On most Linux systems, iptables is installed as /usr/sbin/iptables. However, if it was not included in your particular Linux installation, you can add it later as shown in Figure 4-2.
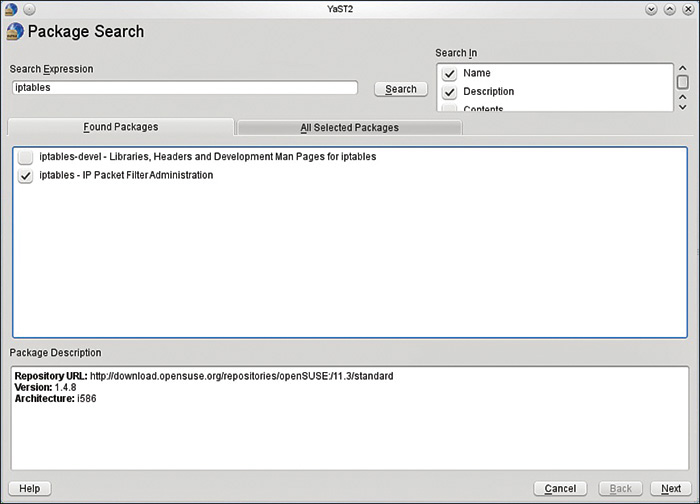
FIGURE 4-2 Finding iptables
An iptables firewall is made up of three different kinds of objects: tables, chains, and rules. Basically, the tables contain chains of rules. Put another way, iptables is an expansion on the concept of ipchains. Each chain has a series of rules that define how to filter packets. There are actually three tables and each has some standard rule chains in it. You can, of course, add your own custom rules. The three tables and their standard chains are as follow:
![]() Packet filtering: This table is the essential part of the firewall. It is a packet filtering firewall and it contains three standard chains: INPUT, OUTPUT, and Forward. The INPUT chain processes incoming packets, and the OUTPUT chain processes traffic sent out from the machine. If the firewall system is also acting as a router, only the FORWARD chain applies to routed packets.
Packet filtering: This table is the essential part of the firewall. It is a packet filtering firewall and it contains three standard chains: INPUT, OUTPUT, and Forward. The INPUT chain processes incoming packets, and the OUTPUT chain processes traffic sent out from the machine. If the firewall system is also acting as a router, only the FORWARD chain applies to routed packets.
![]() Network address translation: This table is used for performing network address translation on outbound traffic that initiates a new connection. This is used only if your machine is serving as a gateway or proxy server.
Network address translation: This table is used for performing network address translation on outbound traffic that initiates a new connection. This is used only if your machine is serving as a gateway or proxy server.
![]() Packet alteration: This table is used only for specialized packet alteration. It is often called the mangle table because it alters, or mangles, packets. It contains two standard chains. This table might not even be needed for many standard firewalls.
Packet alteration: This table is used only for specialized packet alteration. It is often called the mangle table because it alters, or mangles, packets. It contains two standard chains. This table might not even be needed for many standard firewalls.
Iptables Configuration
Iptables requires some configuration. You can do it through the GUI (KDE, GNOME, etc.) but the shell commands are common to most distributions. Let’s take a look at some common, basic configuration issues.
To cause iptables to function as a basic packet filtering firewall, you need these commands:
![]()
iptables -F
![]()
iptables -N block
![]()
iptables -A block -m state --state ESTABLISHED,RELATED -j ACCEPT
Obviously, that is the most basic and essential iptables configuration. However, here are some others.
To list the current iptables rules you use:
iptables -L
To allow communication on a specific port, in this example using SSH port 22, you use:
iptables -A INPUT -p tcp --dport ssh -j ACCEPT
Or perhaps you need to allow all incoming web/HTTP traffic:
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
Logging dropped packets is also a good idea. The following command does that:
iptables -I INPUT 5 -m limit --limit 5/min -j LOG --log-prefix "iptables denied: " --log-level 7
As you can see, there are flags that can be passed to the iptables command. The following is a list of the most common flags and what they do.
![]()
A: Append this rule to a rule chain.
![]()
-L: List the current filter rules.
![]()
-p: The connection protocol used.
![]()
--dport: The destination port(s) required for this rule. A single port may be given, or a range may be given as start:end.
![]()
--limit: The maximum matching rate, given as a number followed by "/second", "/minute", "/hour", or "/day" depending on how often you want the rule to match. If this option is not used and -m limit is used, the default is "3/hour".
![]()
--ctstate: Define the list of states for the rule to match on.
![]()
--log-prefix: When logging, put this text before the log message. Use double quotes around the text to use.
![]()
--log-level: Log using the specified syslog level.
![]()
-i: Only match if the packet is coming in on the specified interface.
![]()
-v: Verbose output.
![]()
-s --source: address[/mask] source specification.
![]()
-d --destination: address[/mask] destination specification.
![]()
-o --out-interface: output name[+] network interface name ([+] for wildcard).
This is not a complete list, just some of the common flags used. But it should be enough for you to get iptables basically configured and functioning.
Symantec Norton Firewall
The makers of Norton AntiVirus also sell a personal, single-machine firewall. It is part of the Norton Security suite.
The Norton firewall also includes some additional features such as pop-up ad blocking and privacy protection. It accomplishes the latter task by preventing information about you from being transmitted via the browser without your knowledge. This firewall gives you a relatively easy-to-use interface, similar to Windows Explorer, that also enables you to set browser security. It also has a feature that enables you to connect to Norton’s website and have that site scan your system for vulnerabilities. This feature is shown in Figure 4-3.
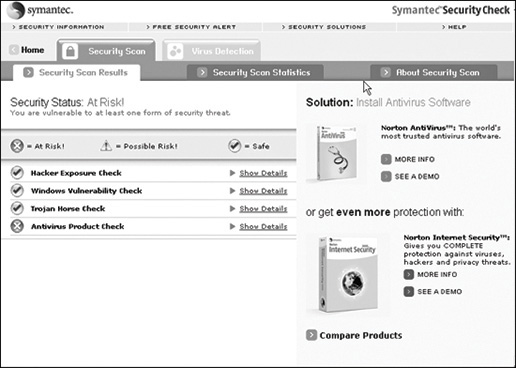
FIGURE 4-3 Norton vulnerability scan
It should be noted that all of these tasks can be done without Norton. You can set your browser security settings, and you can scan your machine for vulnerabilities (even using free tools downloaded from the Internet, some of which will be discussed in Chapter 12, “Assessing System Security”). However, with Norton you can accomplish all of this via a simpler interface. This is particularly appealing to novice users. It should also be stressed that, unlike less advanced firewalls, Norton’s firewall can block outgoing traffic as well.
As of the 2016 version of the Norton Firewall, it adds some additional features that are more like an intrusion detection system. It will notify you of any port scans, suspicious traffic, or unusual connection attempts. It does also support rules, like any firewall. You can learn more about the Norton firewall at ftp://ftp.symantec.com/public/english_us_canada/products/norton_internet_security/2015/manuals/NIShelp.pdf.
The advantages and disadvantages of Norton Firewall are summarized in the following.
Advantages
![]() Norton Firewall can be purchased as a bundle with Norton AntiVirus software.
Norton Firewall can be purchased as a bundle with Norton AntiVirus software.
![]() Norton Firewall is easy to use and set up.
Norton Firewall is easy to use and set up.
![]() Norton Firewall has several extra features, such as the ability to scan your system for vulnerabilities.
Norton Firewall has several extra features, such as the ability to scan your system for vulnerabilities.
![]() Norton Firewall has other IDS-like features that are quite useful.
Norton Firewall has other IDS-like features that are quite useful.
Disadvantages
![]() Norton Firewall costs about $40 per copy.
Norton Firewall costs about $40 per copy.
![]() Many of Norton Firewall’s features can be done with separate, free tools.
Many of Norton Firewall’s features can be done with separate, free tools.
McAfee Personal Firewall
McAfee and Norton are among the most widely used antivirus software vendors. McAfee Personal Firewall, which is now part of the McAfee Total Protection Suite, comes in many versions, from a personal version to an enterprise version. The personal version is quite easy to use. Figure 4-4 shows the initial screen for the McAfee firewall, and Figure 4-5 shows filtering with McAfee.
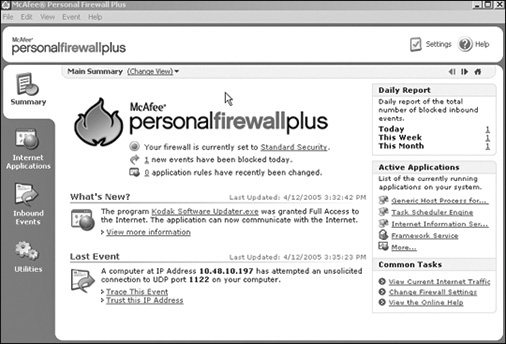
FIGURE 4-4 The initial McAfee firewall screen
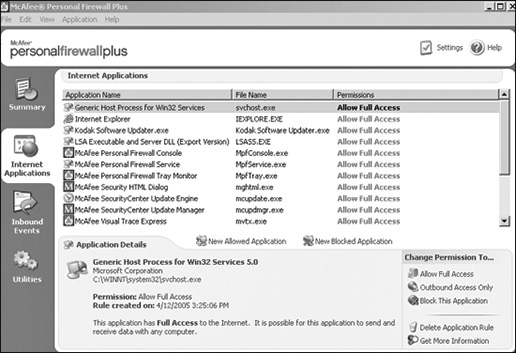
FIGURE 4-5 Filtering with McAfee
McAfee does offer a few interesting features that are not found in most personal firewall solutions:
![]() Tracking: McAfee Personal Firewall has a utility that will show you on a map the path from which an attack is coming. It does this in much the same way as the
Tracking: McAfee Personal Firewall has a utility that will show you on a map the path from which an attack is coming. It does this in much the same way as the traceroute command, but instead performing traceroute commands on the incoming packets and then displaying those routes on a map.
![]() Connected to HackerWatch.org: McAfee Personal Firewall is connected to HackerWatch.org, an anti-hacking website that enables you to get tips and news on the latest threats.
Connected to HackerWatch.org: McAfee Personal Firewall is connected to HackerWatch.org, an anti-hacking website that enables you to get tips and news on the latest threats.
FYI: Traceroute
traceroute is a command available from the command prompt in Windows or the shell in Unix/Linux that is used to trace where a packet is coming from.
McAfee Personal Firewall now has advanced features, such as basic intrusion detection and integration with the HackerWatch website to follow current intrusion patterns. It also will alert you of any personal information leaving your computer, thus helping to mitigate spyware from exfiltrating data.
While this source is a bit dated, there is a whitepaper on the McAfee firewall at https://www.sans.org/reading-room/whitepapers/analyst/advanced-network-protection-mcafee-generation-firewall-35250. McAfee Personal Firewall has advantages and disadvantages, listed below.
Advantages
![]() McAfee Personal Firewall blocks outbound and inbound traffic.
McAfee Personal Firewall blocks outbound and inbound traffic.
![]() McAfee Personal Firewall is easy to use and set up.
McAfee Personal Firewall is easy to use and set up.
![]() McAfee Personal Firewall links to anti-hacking news and tips.
McAfee Personal Firewall links to anti-hacking news and tips.
Disadvantages
![]() McAfee Personal Firewall costs from $30 to $50 depending on the version.
McAfee Personal Firewall costs from $30 to $50 depending on the version.
![]() Some extra features in McAfee Personal Firewall (like the link to anti-hacking news) can be obtained without this product.
Some extra features in McAfee Personal Firewall (like the link to anti-hacking news) can be obtained without this product.
In Practice
You may have noted that many of the firewall solutions come with a variety of extra features not directly related to packet filtering/blocking. You have probably also noticed that many of these features can be obtained from other sources for free. So, the question arises: Why not just use the built in Windows firewall or some other free firewall, and then get the other features on your own?
The answer is really ease of use. In addition to functionality, any technology product has to be evaluated based on usability. For example, you can do traceroute commands, scan your machine for vulnerabilities, and monitor various websites to keep current with attacks, but given that most administrators are quite busy, isn’t it more convenient to have these features all in one place?
Home users certainly do not have access to a dedicated network administrator and certainly do not have a dedicated network security professional. Many small- to medium-sized organizations are in the same boat. They may or may not have a basic general technical support person on site. In this case the person handling security is likely to have limited skills and will benefit from tools that do much of the work for him.
From a practical point of view, some of these features might be superfluous to a security-savvy network administrator or a dedicated network security professional. However, for the home or small office user, they can be absolutely critical. You will be asked to recommend security solutions on the job as well as in your private life. You must keep in mind not only the technical strengths of each product, but how easy the product will be for the person who uses it.
There are other personal firewall solutions. Most Linux distributions have one or more built-in firewalls. A Google or Yahoo search on “free firewall” will provide several options. In most cases, personal firewalls will simply be packet filtering firewalls. Most free solutions have rather limited features, whereas many commercial products will add in additional features.
Using Small Office/Home Office Firewalls
The small office/home office system (often referred to as SOHO) will frequently have needs similar to the individual PC firewall. The personnel maintaining the firewall will likely have limited network administration and security training. Both Norton and McAfee offer solutions designed to be perimeter firewalls for a small network. These products are quite similar to their individual PC firewalls, but with added features and a slightly higher cost. However, there are other solutions for the SOHO which we will examine here. Keep in mind that one critical consideration with any firewall for this environment is ease of installation and use.
SonicWALL
SonicWALL is a vendor of several firewall solutions. Their TZ series is made specifically for small networks with 10 to 25 users. It costs between $350 and $700, depending on the version and retailer. TZ200 is a router-based firewall, as shown in Figure 4-6. You can purchase their products from their vendor SonicGuard, http://www.sonicguard.com. That one is now discontinued and the current products are TZ300 or TZ400, or you can use TZSOH (Small Office Home Office).

FIGURE 4-6 The SonicWall TZ 200 01-SSC-8741 Security Appliance Firewall
Most importantly, this product uses stateful packet inspection, which is significantly more secure than basic packet filtering.
One additional feature that SonicWALL products offer is built-in encryption so that all transmissions are encrypted. Currently their products offer AES and 3DES encryption. While not strictly a firewall feature, this is an important part of network security. When packets are being sent around a network and outside the network, it is not difficult to intercept those packets with a packet sniffer and get the data if the packets are not encrypted.
Management of the SonicWALL firewall should be easy to master for those familiar with Windows 2000 and later versions of Windows because the management is based on objects, such as users, groups, and even IP address ranges. Once a group is defined, you can apply filtering/blocking properties to that group.
FYI: AES and 3DES Encryption
Chapter 6, “Encryption Fundamentals,” describes encryption in detail, including how various encryption methods work. At this point it is important to understand that both AES and 3DES are considered highly secure encryption methods and should be appropriate for almost any network security situation. However, AES is preferred by the NIST (National Institute of Standards) and is generally recommended above 3DES.
SonicWALL, as well as many other modern firewalls, offers built-in NAT. This technology is designed to replace proxy servers. It accomplishes the same goal of hiding internal network IP addresses from the external world.
SonicWall also offers more advanced firewall solutions with their next-generation security appliances. NSA 2650 is one of those appliances. These include features such as the ability to decrypt SSL/TLS and examine it. This prevents internal users (or malware) from using SSL/TLS to exfiltrate data from your network. These systems also have integrated intrusion prevention systems (IPS). We will be discussing IPS in detail in Chapter 5, “Intrusion-Detection Systems.”
The advantages and disadvantages of SonicWALL are briefly listed here.
Advantages
![]() SonicWALL firewalls provide stateful packet inspection.
SonicWALL firewalls provide stateful packet inspection.
![]() SonicWALL firewalls provide built-in encryption.
SonicWALL firewalls provide built-in encryption.
![]() SonicWALL firewalls provide management and configuration that is easy for Windows administrators.
SonicWALL firewalls provide management and configuration that is easy for Windows administrators.
![]() SonicWALL firewalls provide built-in NAT.
SonicWALL firewalls provide built-in NAT.
Disadvantages
![]() The price of SonicWALL firewalls may be prohibitive for small offices on a tight budget.
The price of SonicWALL firewalls may be prohibitive for small offices on a tight budget.
![]() SonicWALL firewalls require some skill to configure and are not intended for the complete novice.
SonicWALL firewalls require some skill to configure and are not intended for the complete novice.
D-Link DFL-2560 Office Firewall
D-Link makes a number of products for home users and for small offices. Its NetDefend firewall product is a router-based firewall that uses stateful packet inspection to filter network traffic. D-Link has products for small and large businesses, and you can see all of their products at http://us.dlink.com/home-solutions/cloud/product-family/. The NetDefend Network UTM Firewall DFL-2560 is shown in Figure 4-7.

FIGURE 4-7 The DFL-2560
This firewall is fairly easy to configure and has a web-based interface, similar to the type used by many home wireless router manufacturers. By using any computer connected directly to the router, you can enter the router’s IP address and you will be presented with a web page that enables you to configure the router. Of course, one of the first things you should do is change the password to prevent other parties from reconfiguring your router-based firewall. This firewall solution can be a bit more expensive than the others we have discussed, costing several thousand dollars. However, it is not a single machine firewall solution, but rather a solution for your gateway, protecting your entire network. Unlike many firewall solutions, the vendor does not require any additional licenses for additional users, so if your company goes from 20 to 50 users, it need not purchase additional licenses.
Here are the advantages and disadvantages of the DFL-2560.
Advantages
![]() The DFL-2560 includes built-in reliable encryption.
The DFL-2560 includes built-in reliable encryption.
![]() The DFL-2560 supports whitelisting and blacklisting.
The DFL-2560 supports whitelisting and blacklisting.
![]() The DFL-2560 has built-in intrusion detection systems.
The DFL-2560 has built-in intrusion detection systems.
![]() The DFL-2560 has built-in antivirus.
The DFL-2560 has built-in antivirus.
![]() The DFL-2560 uses stateful packet inspection.
The DFL-2560 uses stateful packet inspection.
![]() The DFL-2560 combines multiple firewall types.
The DFL-2560 combines multiple firewall types.
![]() The DFL-2560 includes built-in NAT.
The DFL-2560 includes built-in NAT.
![]() The DFL-2560 includes built-in VPN.
The DFL-2560 includes built-in VPN.
Disadvantages
![]() The DFL-2560 lacks some security features that more advanced systems might offer.
The DFL-2560 lacks some security features that more advanced systems might offer.
Using Medium-Sized Network Firewalls
Medium-sized networks can be defined as having as few as 25 users up to several hundred users all on a single LAN at a single location. Administrators of medium-sized networks face configuration and security issues beyond what an administrator in a home or small offices might encounter. To begin with, medium-sized networks are likely to have a more diverse group of users and applications running. Each of these presents different access needs and security requirements. On the other hand, medium-sized networks typically benefit from the support of dedicated network administration personnel. This means there is someone on site who has at least a basic understanding of computer security.
Check Point Firewall
Check Point is a well-known manufacturer of security equipment, and it offers a range of firewall products designed explicitly for use on medium- to large-sized networks. The 1400 and 3000 security appliance models are for branch offices, the 5000 model is for small to midsized businesses, and the 15000 series is for enterprise applications. Finally, the 23000 series is for large enterprises. You can see all of these at https://www.checkpoint.com/products-solutions/next-generation-firewalls/enterprise-firewall/.
Check Point offers a number of other security products, including intrusion-detection systems (IDS will be discussed in detail in Chapter 5). Check Point sells many package solutions that include a firewall as well as some of these additional security products, though such packages can cost anywhere from $3000 to more than $50,000.
The advantages and disadvantages of 5000 series models are as follows.
Advantages
![]() The 5000 series includes intrusion prevention systems.
The 5000 series includes intrusion prevention systems.
![]() The 5000 series has protections against zero-day threats.
The 5000 series has protections against zero-day threats.
![]() The 5000 series supports VPN connections.
The 5000 series supports VPN connections.
Disadvantages
![]() The 5000 series requires at least moderate skill to administer and configure.
The 5000 series requires at least moderate skill to administer and configure.
![]() The cost of the 5000 series can be prohibitive to some organizations.
The cost of the 5000 series can be prohibitive to some organizations.
Cisco Next-Generation Firewalls
Cisco is a very well-known manufacturer of networking equipment, especially routers, so it should come as no surprise that it also makes firewalls. Cisco offers a wide range of Cisco Adaptive Security Appliances (ASA). Cisco is also adding the Firepower series to the ASA lineup.
There are a number of ASA models for a variety of purposes. They include firewall capabilities, but many models include other security features. For example, the ASA 5500 series also includes VPNs, intrusion prevention systems (IPS), and even content filtering. The ASA 5505 is shown in Figure 4-8.

FIGURE 4-8 The Cisco ASA 5505
One of the strengths of Cisco products is the extensive training available for their systems. Cisco sponsors a number of certifications for their products. Their highest certification, the Cisco Certified Internetwork Expert (CCIE), is one of the most widely respected and most rigorous certifications in networking. This certification process enables you to easily identify qualified people to work with your Cisco equipment. It also enables you to identify appropriate training plans for your existing staff.
The advantages and disadvantages of the 5500 series are listed below.
Advantages
![]() The 5500 series includes an advanced firewall.
The 5500 series includes an advanced firewall.
![]() The 5500 series includes VPN.
The 5500 series includes VPN.
![]() The 5500 series includes IDS/IPS.
The 5500 series includes IDS/IPS.
![]() The 5500 series includes unified communications security.
The 5500 series includes unified communications security.
Disadvantages
![]() The 5500 series may be cost prohibitive for some organizations.
The 5500 series may be cost prohibitive for some organizations.
![]() The 5500 series requires at least moderate skill to configure and administer.
The 5500 series requires at least moderate skill to configure and administer.
Using Enterprise Firewalls
An enterprise network is a large network that is often made up of several local networks connected over a wide-area network, or WAN. Large corporations and government agencies frequently use this type of environment. The enterprise environment presents a number of challenges not found in smaller networks. First, each small local network that is connected to the enterprise must be secured. You should also recognize that most enterprise networks include many different types of users, applications, and even operating systems. You may have Unix, Linux, Windows, and Macintosh running a combination of hard wired and wireless network connections. In addition, your end users will probably be quite diverse, including everything from clerical workers to skilled IT professionals. This presents a very complex security challenge, but all enterprise networks are supported by multiple network administrators. Many enterprise networks are supported by a dedicated network security professional. This provides the skill set necessary to deal with such complex situations.
The Cisco and Checkpoint models already discussed in this chapter have other models for enterprise solutions. These often have similar management interfaces to their smaller network solutions, but with more features, additional throughput, and advanced capabilities.
Summary
The type of firewall that is most appropriate for a network depends, at least in part, on the size of the network. Within each size category there are a number of options for a firewall solution, each with its own advantages and disadvantages.
It is important to consider both the technical merits of a firewall solution and the ease of use. A firewall solution’s degree of user-friendliness is largely contingent upon the skill set of the support staff that will implement it. Administrators also must balance cost versus benefit. Clearly, the more expensive firewalls have some impressive features, but they may not be necessary for an organization and may negatively impact its overall IT budget.
May I suggest another element is the overall operation of firewall systems. My thoughts are to present a discussion on THE person who has responsibility to manage. It has been my experience too often that our systems of protection are relegated to a person who may not be analytically trained to discern various intricacies of firewall setup and maintenance. It is one thing to set up a firewall and quite another to manage a firewall. We are not only limited or at risk by the equipment and person but also by company policy. For your consideration.
Test Your Skills
MULTIPLE CHOICE QUESTIONS
1. Which of the following is a common problem when seeking information on firewalls?
A. It is difficult to find information on the web.
B. Unbiased information might be hard to find.
C. Documentation is often incomplete.
D. Information often emphasizes price rather than features.
2. Which of the following is not a common feature of most single PC firewalls?
A. Software-based
B. Packet filtering
C. Ease of use
D. Built-in NAT
3. What is ICF?
A. Windows XP Internet Connection Firewall
B. Windows XP Internet Control Firewall
C. Windows 2000 Internet Connection Firewall
D. Windows 2000 Internet Control Firewall
4. Should a home user with a firewall block incoming port 80, and why or why not?
A. She should not because it would prevent her from using web pages.
B. She should because port 80 is a common attack point for hackers.
C. She should not because that will prevent her from getting updates and patches.
D. She should unless she is running a web server on her machine.
5. Should a home user block incoming ICMP traffic, and why or why not?
A. It should be blocked because such traffic is often used to transmit a virus.
B. It should be blocked because such traffic is often used to do port scans and flood attacks.
C. It should not be blocked because it is necessary for network operations.
D. It should not be blocked because it is necessary for using the web.
6. Which of the following is found in Norton’s personal firewall but not in ICF?
A. NAT
B. A visual tool to trace attacks
C. Vulnerability scanning
D. Strong encryption
7. What tool does McAfee Personal Firewall offer?
A. A visual tool to trace attacks
B. NAT
C. Strong encryption
D. Vulnerability scanning
8. What type of firewall is SonicWALL TZ Series?
A. Packet screening
B. Application gateway
C. Circuit-level gateway
D. Stateful packet inspection
9. Which type of encryption is included with the T Series?
A. AES and 3DES
B. WEP and DES
C. PGP and AES
D. WEP and PGP
10. NAT is a replacement for what technology?
A. Firewall
B. Proxy server
C. Antivirus software
D. IDS
11. Which of the following is an important feature of D-Link 2560?
A. Built-in IDS
B. WEP encryption
C. Vulnerability scanning
D. Liberal licensing policy
12. Medium-sized networks have what problem?
A. Lack of skilled technical personnel
B. Diverse user group
C. Need to connect multiple LANs into a single WAN
D. Low budgets
13. What type of firewall is Check Point 5000 series firewall?
A. Application gateway
B. Packet filtering/application gateway hybrid
C. SPI/application gateway hybrid
D. Circuit-level gateway
14. What implementation is Check Point 5000 series firewall?
A. Router-based
B. Network-based
C. Switch-based
D. Host-based
15. Which of the following is a benefit of Cisco firewalls?
A. Extensive training available on the product
B. Very low cost
C. Built-in IDS on all products
D. Built-in virus scanning on all products
16. What is an advantage of an enterprise environment?
A. Multiple operating systems to deal with
B. Skilled technical personnel available
C. Lower security needs
D. IDS systems not needed
17. What is one complexity found in enterprise environments that is unlikely in small networks or SOHO environments?
A. Multiple operating systems
B. Diverse user groups
C. Users running different applications
D. Web vulnerabilities
18. Which of the following is not an advantage of the Fortigate firewall?
A. Built-in virus scanning
B. Content filtering
C. Built-in encryption
D. Low cost
EXERCISES
Note: Some of the exercises here use commercial tools. All of these exercises can also be completed using free software from the following sites:
![]() https://www.techsupportalert.com/best-free-firewall-protection.htm
https://www.techsupportalert.com/best-free-firewall-protection.htm
![]() http://download.cnet.com/ZoneAlarm-Free-Firewall/3000-10435_4-10039884.html
http://download.cnet.com/ZoneAlarm-Free-Firewall/3000-10435_4-10039884.html
EXERCISE 4.1: The McAfee Firewall
1. Download the McAfee personal firewall. You may wish to download one copy to one machine for the entire class to take turns using, or contact McAfee and request an academic discount or free copy.
2. Install and configure the McAfee firewall on your machine.
3. Examine the firewall’s configuration utilities.
4. Examine extra features such as its attack tracing utility.
5. Attempt to send packets to blocked ports on that firewall.
EXERCISE 4.2: Router-Based Firewall
Note: For cost reasons a specific router is not mentioned here. Many companies and vendors will donate old routers they no longer use to academic labs. You can go to a used computer equipment outlet and find an older router-based firewall for use in the lab.
1. Using the firewall’s documentation, set up this firewall. It should be connected to at least one machine.
2. Attempt to send packets to blocked ports on that firewall.
EXERCISE 4.3: ZoneAlarm Firewall
This product was not covered in this chapter, but you can work with it quite easily. Simply follow these steps:
1. Download the free version from https://www.zonealarm.com/software/release-history/zafree.html.
2. Install and configure this firewall.
3. Observe how it works and compare it to other firewalls you have looked at in previous exercises.
PROJECTS
PROJECT 4.1: Finding Firewall Solutions in Your Organization
Contact an organization you are associated with (an employer, your school, a local company, etc.). Explain to the organization that you are doing a school project and arrange to discuss its firewall solution with the network administrator. Determine why the organization selected its particular solution. Was cost a major factor? Was ease of use a major factor? What features were most important to them? Explain your findings and discuss whether you agree or disagree with that organization’s choice.
PROJECT 4.2: Finding a Different SOHO Solution
Using the web or other resources, find a SOHO firewall not mentioned in this chapter. Briefly compare and contrast it to the solutions that were mentioned in the chapter. Evaluate whether the firewall you found is a better choice than the ones mentioned in the chapter and discuss why or why not.
PROJECT 4.3: Selecting the Proper Firewall
Analyze the environment of your academic institution. Is it a medium-sized network or enterprise? What types of users utilize the network? Are there multiple operating systems? Is there sensitive data that requires additional security? Based on the factors you analyze, write a brief essay describing the environment and recommending a firewall solution. Explain your recommendation.
