Chapter 5
Intrusion-Detection Systems
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
![]() Explain how intrusion-detection systems work.
Explain how intrusion-detection systems work.
![]() Implement strategies for preventing intrusion.
Implement strategies for preventing intrusion.
![]() Identify and describe several popular intrusion-detection systems.
Identify and describe several popular intrusion-detection systems.
![]() Define the term honeypot.
Define the term honeypot.
![]() Identify and describe at least one honeypot implementation.
Identify and describe at least one honeypot implementation.
Introduction
Chapter 4, “Firewall Practical Applications,” discussed several firewall solutions that have built-in intrusion-detection systems (IDS). An IDS is designed to detect signs that someone is attempting to breach a system and to alert the system administrator that suspicious activity is taking place. This chapter analyzes how an IDS works and how to implement some specific IDS solutions.
IDSs have become much more widely used in the last few years. An IDS inspects all inbound and outbound port activity on a machine/firewall/system and looks for patterns that might indicate an attempted break-in. For example, if the IDS finds that a series of packets were sent to each port in sequence from the same source IP address, this probably indicates that a system is being scanned by network-scanning software such as Cerberus (scanners are discussed at length in Chapter 12, “Assessing System Security”). Since this is often a prelude to an attempt to breach a system’s security, it can be very important to know that someone is performing preparatory steps to infiltrate a system. The IDS may also detect an abnormally large flow of packets from the same IP address, all in a brief period of time. This may indicate a DoS attack. In either case, these are situations the network administrator should be aware of and should take steps to prevent.
Understanding IDS Concepts
A full discussion of intrusion-detection systems, the subject of entire books, is beyond the scope of this section. However, this section provides an overview of IDSs to explain how these systems work. There are six basic approaches to intrusion-detection and prevention. Some of these methods are implemented in various software packages, and others are simply strategies that an organization can employ to decrease the likelihood of a successful intrusion. The following paragraphs describe and examine each.
Let’s begin our discussion of intrusion-detection systems with a look at the concepts. How do IDSs work? Well, to explore this, we must first review how networks function. Historically, when IDSs were first developed, hubs were used very frequently. Today, switches are used rather than hubs. With a hub, after a packet has travelled from its source network to the destination network (being routed by its destination IP address), it finally arrives at the network segment on which the target is located. After it gets to that final segment, the MAC address is used to find the target. All the computers on that segment can see the packet, but because the destination MAC address does not match the MAC address of their network card, they ignore the packet.
At some point, enterprising individuals realized that if they simply chose not to ignore packets not destined for their network card, they could see all the traffic on the network segment. In other words, one could look at all the packets on that network segment. Thus the packet sniffer was born. After that it was just a matter of time before the idea came about of analyzing those packets for indications of an attack, thereby giving rise to intrusion-detection systems.
Preemptive Blocking
Preemptive blocking, sometimes called banishment vigilance, seeks to prevent intrusions before they occur. This is done by noting any danger signs of impending threats and then blocking the user or IP address from which these signs originate. Examples of this technique include attempting to detect the early footprinting stages of an impending intrusion, then blocking the IP or user that is the source of the footprinting activity. If you find that a particular IP address is the source of frequent port scans and other scans of your system, then you would block that IP address at the firewall.
This sort of intrusion detection and avoidance can be quite complicated, and there is the potential of blocking a legitimate user by mistake. The complexity arises from distinguishing legitimate traffic from that indicative of an impending attack. This can lead to the problem of false positives, in which the system mistakenly identifies legitimate traffic as some form of attack. Usually, a software system will simply alert the administrator that suspicious activity has taken place. A human administrator will then make the decision whether or not to block the traffic. If the software automatically blocks any addresses it deems suspicious, you run the risk of blocking out legitimate users. It should also be noted that nothing prevents the offending user from moving to a different machine to continue his or her attack. This sort of approach should only be one part of an overall intrusion-detection strategy and not the entire strategy.
Anomaly Detection
Anomaly detection involves actual software that works to detect intrusion attempts and notify the administrator. This is what many people think of when they talk about intrusion-detection systems. The general process is simple: The system looks for any anomalous behavior. Any activity that does not match the pattern of normal user access is noted and logged. The software compares observed activity against expected normal usage profiles. Profiles are usually developed for specific users, groups of users, or applications. Any activity that does not match the definition of normal behavior is considered an anomaly and is logged. Sometimes we refer to this as “trace back” detection or process. We are able to establish from where this packet was delivered. The specific ways in which an anomaly is detected include:
![]() Threshold monitoring
Threshold monitoring
![]() Resource profiling
Resource profiling
![]() User/group work profiling
User/group work profiling
![]() Executable profiling
Executable profiling
Threshold Monitoring
Threshold monitoring presets acceptable behavior levels and observes whether these levels are exceeded. This could include something as simple as a finite number of failed login attempts or something as complex as monitoring the time a user is connected and the amount of data that user downloads. Thresholds provide a definition of acceptable behavior. Unfortunately, characterizing intrusive behavior solely by the threshold limits can be somewhat challenging. It is often quite difficult to establish proper threshold values or the proper time frames at which to check those threshold values. This can result in a high rate of false positives in which the system misidentifies normal usage as a probable attack.
Resource Profiling
Resource profiling measures system-wide use of resources and develops a historic usage profile. Looking at how a user normally utilizes system resources enables the system to identify usage levels that are outside normal parameters. Such abnormal readings can be indicative of illicit activity underway. However, it may be difficult to interpret the meaning of changes in overall system usage. An increase in usage might simply indicate something benign like increased workflow rather than an attempt to breach security.
User/Group Work Profiling
In user/group work profiling, the IDS maintains individual work profiles about users and groups. These users and groups are expected to adhere to these profiles. As the user changes his activities, his expected work profile is updated to reflect those changes. Some systems attempt to monitor the interaction of short-term versus long-term profiles. The short-term profiles capture recent changing work patterns, whereas the long-term profiles provide a view of usage over an extended period of time. However, it can be difficult to profile an irregular or dynamic user base. Profiles that are defined too broadly enable any activity to pass review, whereas profiles that are defined too narrowly may inhibit user work.
Executable Profiling
Executable profiling seeks to measure and monitor how programs use system resources with particular attention to those whose activity cannot always be traced to a specific originating user. For example, system services usually cannot be traced to a specific user launching them. Viruses, Trojan horses, worms, trapdoors, and other such software attacks are addressed by profiling how system objects such as files and printers are normally used not only by users, but also by other system subjects on the part of users. In most conventional systems, for example, any program, including a virus, inherits all of the privileges of the user executing the software. The software is not limited by the principle of least privilege to only those privileges needed to properly execute. This openness in the architecture permits viruses to surreptitiously change and infect totally unrelated parts of the system.
Executable profiling enables the IDS to identify activity that might indicate an attack. Once a potential danger is identified, the method of notifying the administrator, such as by network message or e-mail, is specific to the individual IDS.
IDS Components and Processes
Regardless of what IDS you select, they all have certain components in common. It is important to have a general understanding of these components. The following terms will familiarize you with basic components and functions in all IDSs:
![]() An activity is an element of a data source that is of interest to the operator.
An activity is an element of a data source that is of interest to the operator.
![]() The administrator is the person responsible for organizational security.
The administrator is the person responsible for organizational security.
![]() A sensor is the IDS component that collects data and passes it to the analyzer for analysis.
A sensor is the IDS component that collects data and passes it to the analyzer for analysis.
![]() The analyzer is the component or process that analyzes the data collected by the sensor.
The analyzer is the component or process that analyzes the data collected by the sensor.
![]() An alert is a message from the analyzer indicating that an event of interest has occurred.
An alert is a message from the analyzer indicating that an event of interest has occurred.
![]() The manager is the part of the IDS used to manage, for example a console.
The manager is the part of the IDS used to manage, for example a console.
![]() Notification is the process or method by which the IDS manager makes the operator aware of an alert.
Notification is the process or method by which the IDS manager makes the operator aware of an alert.
![]() The operator is the person primarily responsible for the IDS. This is often the administrator.
The operator is the person primarily responsible for the IDS. This is often the administrator.
![]() An event is an occurrence that indicates a suspicious activity may have occurred.
An event is an occurrence that indicates a suspicious activity may have occurred.
![]() The data source is the raw information that the IDS uses to detect suspicious activity.
The data source is the raw information that the IDS uses to detect suspicious activity.
Beyond these basic components, IDSs can be classified either based on how they respond to detected anomalies or based on how they are deployed. An active IDS, now called an IPS (intrusion prevention system), will stop any traffic deemed to be malicious. A passive IDS simply logs the activity and perhaps alerts an administrator. The problem with IPS/active IDS is the possibility of false positives. It is possible to have activity that appears to be an attack, but really is not.
You can also define IDS/IPS based on whether a single machine is monitored or an entire network segment is monitored. If it is a single machine, then it is called a HIDS (host-based intrusion-detection system) or HIPS (host-based intrusion prevention system). If it is a network segment then it is called a NIDS (network-based intrusion-detection system) or NIPS (network-based intrusion prevention system).
Understanding and Implementing IDSs
Many vendors supply IDSs, and each of these systems has its own strengths and weaknesses. Deciding which system is best for a particular environment depends on many factors, including the network environment, security level required, budget constraints, and the skill level of the person who will be working directly with the IDS. This section discusses the most common IDSs.
Snort
Snort is perhaps the most well-known open source IDS available. It is a software implementation installed on a server to monitor incoming traffic. It typically works with a host-based firewall in a system in which both the firewall software and Snort run on the same machine. Snort is available for Unix, Linux, Free BSD, and Windows. The software is free to download, and documentation is available at the website: www.snort.org.
FYI: What Is Open Source?
Open source is a way of licensing software. It means that the software is freely distributable and contains the source code. This means that users can make copies, give them to friends, and even get a copy of the source code. Users can even modify the source code and then release their own version (though that release must also be open source).
The idea behind open source is to encourage users to examine the source code for a product and, if possible, to improve it. The belief is that through review and improvements by so many people, a product will reach a higher level of quality faster than commercial ones. There are a number of products available via open source licenses besides Snort, including products such as Open Office (www.openoffice.org), Linux (a), and Gimp (www.gimp.org).
More details about open source software are available at https://opensource.org.
Snort works in one of three modes: sniffer, packet logger, and network intrusion-detection.
Sniffer
In packet sniffer mode, the console (shell or command prompt) displays a continuous stream of the contents of all packets coming across that machine. This can be a very useful tool for a network administrator. Finding out what traffic is traversing a network can be the best way to determine where potential problems lie. It is also a good way to check whether transmissions are encrypted.
Packet Logger
Packet logger mode is similar to sniffer mode. The difference is that the packet contents are written to a text file log rather than displayed in the console. This can be more useful for administrators who are scanning a large number of packets for specific items. Once the data is in a text file, users can scan for specific information using a word processor’s search capability.
Network Intrusion-Detection
In network intrusion-detection mode, Snort uses a heuristic approach to detecting anomalous traffic. This means it is rules-based and it learns from experience. A set of rules initially governs a process. Over time Snort combines what it finds with the settings to optimize performance. It then logs that traffic and can alert the network administrator. This mode requires the most configuration because the user can determine the rules she wishes to implement for the scanning of packets.
Snort works primarily from the command line (Shell in Unix/Linux, command prompt in Windows). Configuring Snort is mostly a matter of knowing the correct commands to enter and understanding their output. Anyone with even moderate experience with either Linux shell commands or DOS commands can quickly master the Snort configuration commands. Perhaps Snort’s greatest advantage is its price: It is a free download. For any organization to not be using some IDS is inexcusable when a free product is available. Snort is a good tool when used in conjunction with host-based firewalls or as an IDS on each server to provide additional security.
Cisco Intrusion-Detection and Prevention
The Cisco brand is widely recognized and well respected in the networking profession. Along with their firewalls and routers, Cisco has several models of intrusion detection, each with a different focus/purpose. In the past, Cisco had two specific, widely used IDS products, the Cisco IDS 4200 Series Sensors and Cisco Catalyst 6500 Series Intrusion-Detection System (IDSM-2) Services Module. Information about all Cisco IDS solutions is available at https://www.cisco.com/c/en/us/support/security/intrusion-prevention-system/tsd-products-support-series-home.html. However, now the product being sold is the Cisco Next-Generation IPS solution: https://www.cisco.com/c/en/us/products/security/ngips/index.html.
There are a number of products in this group, notably the Firepower 4100 series, the Firepower 8000 series, and the Firepower 9000 series. All the products include malware protection as well as sandboxing. These Cisco products also integrate cyber threat intelligence features. The Firepower 4100 is shown in Figure 5-1.
The 4100 series is meant for smaller networks. The 9000 series is designed for large-scale networks. You can see the Firepower 9000 series in Figure 5-2.

FIGURE 5-2 The Cisco Firepower 9000
One of the chief benefits of using Cisco security products is their widespread use across the industry and the availability of good training. The fact that so many organizations use Cisco indicates a high level of successful field testing, which generally indicates a reliable product. Cisco also sponsors a range of certifications on its products, making it easier to determine whether someone is qualified on a particular Cisco product.
Understanding and Implementing Honeypots
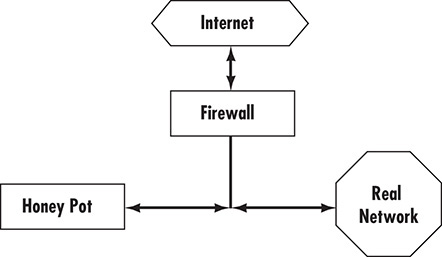
A honeypot is a single machine set up to simulate a valuable server or even an entire subnetwork. The idea is to make the honeypot so attractive that if a hacker breaches the network’s security, she or he will be attracted to the honeypot rather than to the real system. Software can closely monitor everything that happens on that system, enabling tracking and perhaps identification of the intruder.
The underlying premise of the honeypot is that any traffic to the honeypot machine is considered suspicious. Because the honeypot is not a real machine, no legitimate users should have a reason to connect to it. Therefore, anyone attempting to connect to that machine can be considered a possible intruder. The honeypot system can entice him to stay connected long enough to trace where he is connecting from. Figure 5-3 illustrates the honeypot concept.
Specter
Specter is a software honeypot solution. Complete product information is available at www.specter.com. The Specter honeypot is comprised of a dedicated PC with the Specter software running on it. The Specter software can emulate the major Internet protocols/services such as HTTP, FTP, POP3, SMTP, and others, thus appearing to be a fully functioning server. The software was designed to run on Windows 2000 or XP but will execute on later versions of Windows, but it can simulate AIX, Solaris, Unix, Linux, Mac, and Mac OS X. Figure 5-4 shows the primary configuration window for Specter.
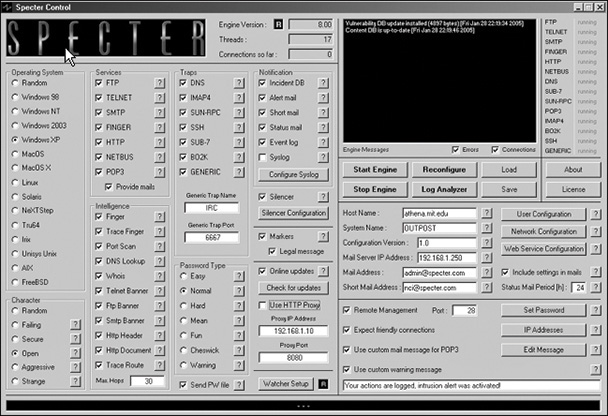
FIGURE 5-4 The Specter configuration window
Specter works by appearing to run a number of services common to network servers. In fact, in addition to simulating multiple operating systems, it can also simulate the following services:
![]() SMTP
SMTP
![]() FTP
FTP
![]() TELNET
TELNET
![]() FINGER
FINGER
![]() POP3
POP3
![]() IMAP4
IMAP4
![]() HTTP
HTTP
![]() SSH
SSH
![]() DNS
DNS
![]() SUN-RPC
SUN-RPC
![]() NETBUS
NETBUS
![]() SUB-7
SUB-7
![]() BO2K
BO2K
![]() GENERIC TRAP
GENERIC TRAP
Even though Specter appears to be running these servers, it is actually just monitoring all incoming traffic. Because it is not a real server for your network, no legitimate user should be connecting to it. Specter logs all traffic to the server for analysis. Users can set it up in one of five modes:
![]() Open: In this mode the system behaves like a badly configured server in terms of security. The downside of this mode is that you are most likely to attract and catch the least skillful hackers.
Open: In this mode the system behaves like a badly configured server in terms of security. The downside of this mode is that you are most likely to attract and catch the least skillful hackers.
![]() Secure: This mode has the system behaving like a secure server.
Secure: This mode has the system behaving like a secure server.
![]() Failing: This mode is interesting in that it causes the system to behave like a server with various hardware and software problems. This might attract some hackers because such a system is likely to be vulnerable.
Failing: This mode is interesting in that it causes the system to behave like a server with various hardware and software problems. This might attract some hackers because such a system is likely to be vulnerable.
![]() Strange: In this mode the system behaves in unpredictable ways. This sort of behavior is likely to attract the attention of a more talented hacker and perhaps cause her to stay online longer trying to figure out what is going on. The longer the hacker stays connected, the better the chance of tracing her.
Strange: In this mode the system behaves in unpredictable ways. This sort of behavior is likely to attract the attention of a more talented hacker and perhaps cause her to stay online longer trying to figure out what is going on. The longer the hacker stays connected, the better the chance of tracing her.
![]() Aggressive: This mode causes the system to actively try and trace back the intruder and derive his identity. This mode is most useful for catching the intruder.
Aggressive: This mode causes the system to actively try and trace back the intruder and derive his identity. This mode is most useful for catching the intruder.
In all modes, Specter logs the activity, including all information it can derive from the incoming packets. It also attempts to leave traces on the attacker’s machine, which can provide clear evidence should civil or criminal action later be required.
Users can also configure a fake password file in all modes. These are particularly useful because most hackers attempt to access a password file to crack the passwords. If they are successful they can then log on as a legitimate user. The holy grail of hacking is getting the administrator’s password. There are multiple ways to configure this fake password file:
![]() Easy: In this mode the passwords are easy to crack, leading a would-be intruder to believe that she has actually found legitimate passwords and usernames. Often a hacker with a legitimate logon will be less careful covering her tracks. If you know that logon is fake and the system is set up to monitor it, you can track it back to the hacker.
Easy: In this mode the passwords are easy to crack, leading a would-be intruder to believe that she has actually found legitimate passwords and usernames. Often a hacker with a legitimate logon will be less careful covering her tracks. If you know that logon is fake and the system is set up to monitor it, you can track it back to the hacker.
![]() Normal: This mode has slightly more difficult passwords than the easy mode.
Normal: This mode has slightly more difficult passwords than the easy mode.
![]() Hard: This mode has even harder passwords to crack. There is even a tougher version of this mode called mean, in which the passwords are very difficult to break so that the hacker can be traced while he is taking time to crack the passwords.
Hard: This mode has even harder passwords to crack. There is even a tougher version of this mode called mean, in which the passwords are very difficult to break so that the hacker can be traced while he is taking time to crack the passwords.
![]() Fun: This mode uses famous names as usernames. In my opinion this one, and the related one named Cheswick, have dubious security value.
Fun: This mode uses famous names as usernames. In my opinion this one, and the related one named Cheswick, have dubious security value.
![]() Warning: In this mode the hacker gets a warning telling him he has been detected if he is able to crack the password file. The theory behind this mode is that most hackers are simply trying to see if they can crack a system and do not have a specific objective. Letting this sort of hacker know he has been detected is often enough to scare him off.
Warning: In this mode the hacker gets a warning telling him he has been detected if he is able to crack the password file. The theory behind this mode is that most hackers are simply trying to see if they can crack a system and do not have a specific objective. Letting this sort of hacker know he has been detected is often enough to scare him off.
The cost of this software system is about $900, and it requires a PC to install it on. The purpose of honeypots like Specter is not preventing intrusion. Instead, they minimize the damage once someone is in. They serve to direct the hacker’s attention away from critical systems. They also can be very helpful in tracking down hackers.
Symantec Decoy Server
Because Symantec is such a prominent vendor for both antivirus software and firewall solutions, it should come as no surprise that it also has a honeypot solution. The first Symantec honeypot product was Decoy Server. It simulated being a real server by simulating many server functions, such as incoming and outgoing e-mail traffic. You can learn full details about this product from Symantec; however, their product line and web page changes frequently. The best way to find out about their honeypots is to just go to Symantec’s main site and perform a search.
As the Decoy Server works as a honeypot, it also works as an IDS monitoring the network for signs of intrusion. If an attack is detected, all traffic related to that attack is recorded for use later in whatever investigative, criminal, or civil procedures that may arise.
Decoy Server is designed to be part of a suite of enterprise security solutions that work together, including enterprise versions of Symantec’s antivirus software, firewall software, and antispyware. The product is usually purchased as part of a volume licensing agreement for a complete security package.
Intrusion Deflection
Intrusion deflection is becoming increasingly popular among security-conscious administrators. The essence of it is quite simple. An attempt is made to attract the intruder to a subsystem set up for the purpose of observing him. This is done by tricking the intruder into believing that he has succeeded in accessing system resources when, in fact, he has been directed to a specially designed environment. Being able to observe the intruder while he practices his art will yield valuable clues and can lead to his arrest.
This is often done by using what is commonly referred to as a honeypot. Essentially, you set up a fake system, possibly a server that appears to be an entire subnet. The administrator makes that system look attractive to hackers, perhaps making it appear to have sensitive data, such as personnel files, or valuable data, such as account numbers or research. The actual data stored in this system is fake. The real purpose of the system is to carefully monitor the activities of any person who accesses the system. Because no legitimate user ever accesses this system, it is a given that anyone accessing it is an intruder.
This sort of system can be difficult to set up and maintain. It also presupposes that someone is able to successfully compromise security. Intrusion deflection systems are typically only employed at sites requiring very high security. They should only be a part of the overall IDS strategy—not the entire strategy.
Intrusion Deterrence
Intrusion deterrence involves simply trying to make the system seem like a less palatable target. In short, an attempt is made to make any potential reward from a successful intrusion attempt appear more difficult than it is worth. This approach includes tactics such as attempting to reduce the apparent value of the current system’s worth through camouflage. This essentially means working to hide the most valuable aspects of the system. The other tactic in this methodology involves raising the perceived risk of a potential intruder being caught. This can be done in a variety of ways, including conspicuously displaying warnings and warning of active monitoring. The perception of the security of a system can be drastically improved, even when the actual system security has not been improved.
Because this approach costs almost nothing to implement and is relatively easy to set up, it is a good option for any system when used in conjunction with other strategies.
To implement this strategy, warn the user at every step in the process of connecting that her activities are being closely monitored, whether they are or are not. In addition, avoid advertising that the system or machine contains sensitive data by giving it an innocuous name. For example, a database server that contains research material might be named “print_server 1” rather than “research_server” to make it less attractive. When using this type of naming approach, maintaining a master list and developing a naming scheme is important. For example, all real print servers might end with X and all false print server names end in Y so that staff know that “print_server1x” is a real print server and “print_server1y” is actually a sensitive server being hidden from intruders. Some way must exist for keeping track of the real purpose of the servers.
The purpose of the multiple warnings is to scare off less skilled hackers. Although such people might not have a great deal of technical prowess, their attempts to invade a system are a nuisance and can cause problems. Many of these attackers are new to hacking and appropriate warnings can scare off a significant percentage of them.
Summary
A variety of IDSs are available. Some are designed to run on the perimeter with the perimeter firewall, often in a host-based configuration. Others are designed to be sensors throughout your network or are a router-type appliance. Honeypots entice hackers to explore phantom servers with the goal of keeping them long enough to identify them.
A complete IDS solution should have a perimeter IDS working in conjunction with a perimeter firewall. The most complete IDS solution includes multiple sensors for each subnet. Ideally, an administrator places some IDS on each major server and implements a honeypot solution.
Clearly, such a level of expenditure and complexity is not possible in all circumstances. This level certainly provides the greatest security, but many organizations do not require, nor can they afford, this level of security. At a minimum, an organization should have an IDS running with the perimeter firewall. Because free IDS solutions are available, there is no reason not to have one.
Test Your Skills
MULTIPLE CHOICE QUESTIONS
1. IDS is an acronym for:
A. Intrusion-detection system
B. Intrusion-deterrence system
C. Intrusion-deterrence service
D. Intrusion-detection service
2. A series of ICMP packets sent to your ports in sequence might indicate what?
A. A DoS attack
B. A ping flood
C. A packet sniffer
D. A port scan
3. What is another term for preemptive blocking?
A. Intrusion deflection
B. Banishment vigilance
C. User deflection
D. Intruder blocking
4. Attempting to attract intruders to a system set up to monitor them is called what?
A. Intrusion deterrence
B. Intrusion deflection
C. Intrusion banishment
D. Intrusion routing
5. A system that is set up for attracting and monitoring intruders is called what?
A. Fly paper
B. Trap door
C. Honeypot
D. Hacker cage
6. Attempting to make your system appear less appealing is referred to as what?
A. Intrusion deterrence
B. Intrusion deflection
C. System camouflage
D. System deterrence
7. Which of the following is not a profiling strategy used in anomaly detection?
A. Threshold monitoring
B. Resource profiling
C. Executable profiling
D. System monitoring
8. Setting up parameters for acceptable use, such as the number of login attempts, and watching to see if those levels are exceeded is referred to as what?
A. Threshold monitoring
B. Resource profiling
C. System monitoring
D. Executable profiling
9. Which of the following is a problem with the approach described in Question 8?
A. It is difficult to configure.
B. It misses many attacks.
C. It yields many false positives.
D. It is resource intensive.
10. A profiling technique that monitors how applications use resources is called what?
A. System monitoring
B. Resource profiling
C. Application monitoring
D. Executable profiling
11. Snort is which type of IDS?
A. Router-based
B. OS-based
C. Host-based
D. Client-based
12. Which of the following is not one of Snort’s modes?
A. Sniffer
B. Packet logger
C. Network intrusion-detection
D. Packet filtering
13. Which type of IDS is the Cisco Sensor?
A. Anomaly detection
B. Intrusion deflection
C. Intrusion deterrence
D. Anomaly deterrence
14. Why might you run Specter in strange mode?
A. It may confuse hackers and deter them from your systems.
B. It will be difficult to determine the system is a honeypot.
C. It might fascinate hackers and keep them online long enough to catch them.
D. It will deter novice hackers.
EXERCISES
EXERCISE 5.1: Using Snort
Note: This is a longer exercise appropriate for groups. Refer to the chapter text for an explanation of the Snort product and features.
1. Go to the Snort.org website (www.snort.org).
2. Download Snort.
3. Using the vendor documentation or other resources, configure Snort as a packet sniffer. Use that resource to observe traffic on your network.
4. Compile statistics about your network’s normal traffic. These statistics include mean packets per minute, top five destination IP addresses, top ten source IP addresses, etc.
EXERCISE 5.2: Using Snort as an IDS
1. Using the Snort installation from Exercise 5.1, configure Snort to do network intrusion detection.
2. Set up rules for alerts by Snort.
EXERCISE 5.3: Open Source Honeypots
Note: This exercise requires you to use an open source honeypot. One such free solution can be found at www.projecthoneypot.org, but feel free to use any solution you like. In fact, if possible, it is best to test out multiple solutions in order to compare results.
1. Install the honeypot on a lab machine.
2. Configure it according to the vendor documentation.
3. Have one student pose as a hacker attacking the honeypot.
4. The other student(s) should use the honeypot to detect that intrusion.
EXERCISE 5.4: Recommend an IDS
1. Assume you are working for a small organization that has a moderate security budget.
2. Select a particular IDS solution you would recommend for that organization.
3. Write your recommendations, including your reasons, in a memo format as if submitting them to a CIO or other decision maker.
PROJECTS
PROJECT 5.1: IDS Strategy
Using websites and vendor documentation, create a document that outlines a complete IDS plan for a network. Plan your entire IDS strategy assuming a budget of $2,000.
PROJECT 5.2: Firewall-Based IDS
Using web resources, books, or other resources as well as your own opinions, determine whether you think a firewall-based IDS or a separate IDS is a better solution. Write a memo (as if you were submitting it to a CIO or other decision maker) explaining your position, including your reasons for coming to this conclusion.
PROJECT 5.3: How to Improve Honeypots
By now you should have a good understanding of how honeypots work, and you should have actually used at least one honeypot. But like all security technology, honeypots are evolving. Describe, in detail, at least two improvements you would like to see in honeypot technology. This could include features not currently available, improved detection, or more aggressive responses. The following sites describe current honeypot technology and might be of use to you.
![]() https://www.sans.edu/cyber-research/security-laboratory/article/honeypots-guide
https://www.sans.edu/cyber-research/security-laboratory/article/honeypots-guide