Recently, a trend has occurred in which a malicious Trojan horse is hidden in popular open source programs. The authors of the programs do not do this. Instead, it is done by attackers modifying the source at distribution points such as ftp download sites. The best way to ensure you don't install software that has been modified after the authors created the ZIP or TAR file is to check either the MD5 message digest or the GPG signature of the files you download. The latter is significantly better than the former because the attacker could have easily changed the MD5 value as well.
In this appendix, we walk through the process of verifying the code you download.
Checking the MD5 digest value is easy if you're on a UNIX system. Most of the modern systems now have a command md5sum. Md5sum computes the MD5 digest value for the file name entered at the command line. Thus, you check the digest of the recent OpenSSL distribution with the following command:
bash-2.05$ md5sum openssl-0.9.7-beta4.tar.gz 43cf89b428fbdd7873b5aae2680cd324 openssl-0.9.7-beta4.tar.gz
The output of MD5sum is the 128-byte MD5 digest in hexadecimal of the file, or files, you entered on the command line. You must check that value with the value that would be contained in openssl-0.9.7-beta4.tar.gz.md5. The two values should be identical. If you're lazy and are familiar with the UNIX command line, you can also do:
md5sum TARBALL | awk '{print $1;}' | cmp - TARBALL.md5
If you don't get any output from the above command, then the digests match.
An MD5 digest isn't foolproof. As mentioned before, an attacker could also change the value stored in the digest file so it always matches. A far better way to ensure the integrity of files you download is to check the digital signature of the file downloaded.
Checking the signature requires that you have either PGP (www.pgp.com) or GPG (www.gnupg.org) installed on one of your systems. You'll also need the public key of the creator of the signature.
Here's how you would go about checking the integrity on our openssl file.
bash-2.05$ gpg openssl-0.9.7-beta4.tar.gz.asc gpg: Signature made Tue Nov 19 05:15:12 2002 EST using RSA key ID E06D2CB1 gpg: Can't check signature: public key not found bash-2.05$
We ran GPG on the signature file, but we don't have the public key for the signer. So, we have to find the key at a keyserver using the key ID 0xE06D2CB1. The easiest way to do that is to go to www.keyserver.net and enter the key ID into the window, as shown in Figure C.1, making sure to enter “0x” before the key ID. In this case, we're entering “0xE06D2CB1”.
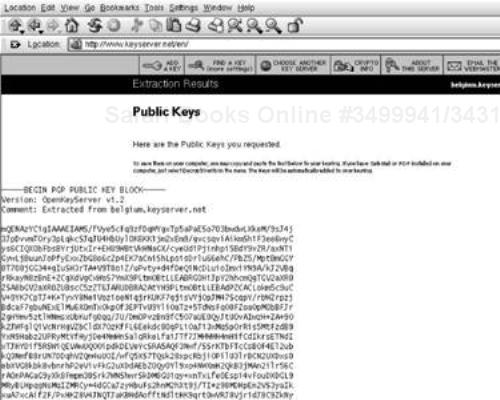
If a key exists in the server with the ID you entered, you'll see it displayed as the result of your query. The answer to our query is shown in Figure C.2.
In this case, you'll see that Richard Levitte is the owner of the public key associated with the key ID 0xE06D2CB1. Now, you need to make sure that Richard Levitte is authorized to sign the file you downloaded. To answer this question, we simply look at the list of developer team members for OpenSSL on their home page, and we see that Richard Levitte is a member of the development team. Ideally, the team should also put their OpenPGP fingerprints on this page to verify that the Richard Levitte associated with the public key we found is in fact the Richard Levitte associated with the OpenSSL project.
Once we're happy that we have the correct key, we can view an ASCII representation of it and cut and paste the key into a file we can import into our OpenPGP application. The ASCII representation of Richard Levitte's key is shown in Figure C.3.
Now, assuming that we saved a copy of the ASCII representation in the file levitte.asc, we import the key into our public key ring with the command:
bash-2.05$ gpg --import levitte.asc gpg: key E06D2CB1: public key imported gpg: Total number processed: 1 gpg: imported: 1 (RSA: 1)
Now that we've loaded the proper key into our public key ring, we can verify the integrity, or authenticity, of the file we downloaded.
bash-2.05$ gpg openssl-0.9.7-beta4.tar.gz.asc gpg: Signature made Tue Nov 19 05:15:12 2002 EST using RSA key ID E06D2CB1 gpg: Good signature from "Richard Levitte <[email protected]>" gpg: aka "Richard Levitte <[email protected]>" gpg: checking the trustdb gpg: no ultimately trusted keys found gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Fingerprint: 35 3E 6C 9E 8C 97 85 24 BD 9F D1 9E 8F 75 23 6B
You'll see that the signature of the file verified correctly. But there's a warning message. The warning is just telling us that Richard Levitte's public key certificate isn't signed by anyone we trust.