Internet Connection Sharing
After determining which type of high-speed Internet connection is best for a SOHO LAN, the next decision is how to share the connection among all the PC hosts in a facility. There are several approaches, all of which involve routing data to and from the PC hosts attached to the SOHO LAN. Routing represents a SOHO network of PC hosts as a single IP address to the next-level ISP. They in turn also represent their network as a single IP address to the next-higher-level ISP. This process continues until the highest-level ISP connects into the top-level Internet backbone.
There are two general approaches to connection sharing: a hardware approach requiring the installation of a hardware router, and a software approach requiring that routing software be installed on a PC host that connects to both the LAN and to the high-speed Internet channel. Windows XP comes with Internet connection sharing software built in, but other connection sharing packages are available.
Windows Internet Connection Sharing (WICS)
Windows Internet Connection Sharing (WICS) connects PC hosts in a SOHO LAN to the Internet using a single connection. A WICS hosting computer needs two network connections. The first is a private LAN connection automatically created by installing a network adapter. The private LAN connection connects to other PC host computers on the SOHO LAN. The second connection, using a modem, an ISDN CSU/DSU, a DSL modem, or a cable modem, connects the home- or small-office network to the Internet. WICS must be enabled on the connection to the Internet connection. By doing this, the shared connection can be used by PC hosts on a SOHO LAN to connect to the Internet. Users outside the SOHO network do not receive IP addresses from the SOHO network that conflict with their ISP-assigned addresses. Duplicate and conflicting ISP addresses cause PC hosts not to work on the Internet.
When choosing a computer to host WICS in a SOHO LAN you should consider the following:
The WICS hosting computer should be running Windows XP.
The WICS hosting PC should be a fast PC with lots of RAM. A PC with a GHz or higher CPU and with 512 MB of RAM would be better than a 500-MHz machine with 64 MB of RAM.
This WICS hosting computer generally operates 24 hours a day and 7 days a week; otherwise, the shared connection to the Internet is not available.
The WICS hosting computer should use the highest-speed Internet connection possible, such as a DSL or cable modem.
Only one computer can act as a WICS hosting computer. If WICS is running on another computer, turn off WICS on that computer before starting it on another Windows XP host PC.
Shared printers should be installed on the WICS hosting PC because it is always running on the SOHO LAN to provide Internet access. Since it is always running, any printers attached to that machine would always be available for printing as well.
When setting WICS on a SOHO network, the Network Setup Wizard in Windows XP Professional can be used to enable Internet connection sharing. The Network Setup Wizard is the easiest way to install WICS because it automatically provides the network settings needed to share an Internet connection with all other PC hosts.
Alternatively, to enable Internet connection sharing on any network connection, click the right mouse button on My Network Places, then select Properties from the drop down menu. Click the right mouse button on the network connection that you are going to share. Select Properties from the drop down menu, and then select the Advanced tab. If the network connection is not sharable, sharing does not appear as an option. This same menu is found when under Network Tasks, the Change Settings Menu option is selected when pointing at a specific network connection and then the Advanced tab is selected. See Figure 5.11.
Figure 5.11. Network settings.
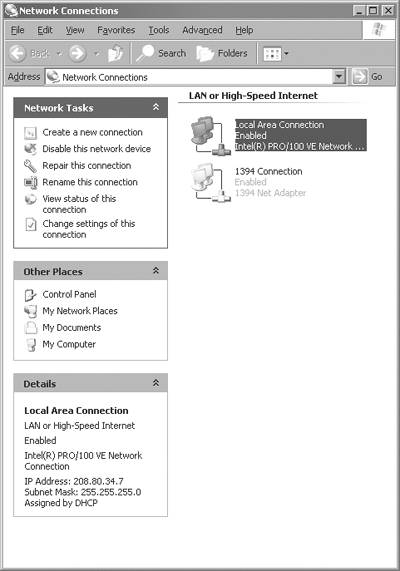
One computer connects to the Internet by using a high-speed DSL connection with WICS enabled, then the other computers on the network connect to the Internet through this high-speed connection.
When a network connection is sharable the Internet Connections sharing box appears under the Advanced Settings tab, as shown in Figure 5.12.
Figure 5.12. Internet Connection Sharing box.

Checking off “Allow other network users to connect through this computer's Internet connection” enables WICS. Clicking on the Settings button sets up the specific services that users can access through the shared Internet connection. Typical connections would include every service except perhaps remote desktop and Telnet server. Custom services can be added by clicking on the Add button.
Once WICS is set up and running, make sure that all SOHO network PC hosts communicate with each other and that all PC hosts can access the Internet. Test the Internet connection using Internet Explorer or Netscape to browse the Web.
WICS is used in networks where a single computer hosting WICS controls and directs communication between SOHO PC hosts and the Internet. WICS assumes that in a SOHO LAN, only the computer hosting WICS is connected to the Internet. Other computers on the SOHO LAN can use modems to access the Internet, but their primary Internet connection is through the PC hosting WICS.
WICS may need to be configured so that outside Internet users can access specific PC hosts. When a SOHO LAN hosts a Web server and external Internet users need to connect to the Web server, access to the Web server service must be configured on the computer hosting WICS.
WICS is configured on the public connection of the SOHO LAN. When more than one network adapter is installed on a PC hosting WICS, one local area connection—the private network connection—communicates with the other PC hosts on your home- or small-office network. The other network connection—the public network connection—is the shared network connection. When there are three connections in a PC host, two connections are private network connections and the other connection is the public shared network connection. However, in the case of three network adapters the two private network adapters must be bridged. When a network bridge is created that does not include all of the SOHO LAN connections, the bridged connections can be selected as the private connections. The remaining connection is then the shared or public network connection. However, if a network bridge is created that includes all LAN connections into the PC host, the bridge is automatically selected when WICS is enabled because WICS assumes that the shared public connection is included in the bridged connections.
The WICS feature must be specially configured in existing networks with domain controllers, DNS servers, gateways, DHCP servers, or systems configured with static IP addresses. When WICS is enabled, LAN connections to a SOHO network are given a new static IP address. Consequently, TCP/IP connections established between any SOHO PC hosts and the WICS hosting computer are at that time lost and would need to be reestablished. Also, there can be no conflicts between the IP address assigned to the WICS hosting computer and the other PC hosts that have fixed addresses. Also, the proper subnet mask and IP address range must be selected to ensure that all SOHO PC hosts have access to the WICS hosting PC and the shared public Internet connection.
To complete WICS setup, you must be logged in with administrative privileges. When a PC host is connected to a network, network policy settings may also prevent WICS setup.
When a Virtual Private Network (VPN) connection is created on a WICS hosting computer, and WICS uses this connection, then all traffic is routed to the network at the other end of the VPN connection. All PC hosts in the SOHO LAN can access the corporate network and through it the Internet. When WICS is disabled on the VPN connection, other SOHO PC hosts cannot access the corporate network even if the VPN connection is active on the WICS hosting computer.
WICS, Internet Connection Firewall, Discovery and Control, and Network Bridge are not available on Windows XP 64-bit edition; they are only provided with the 32-bit Windows XP software. This is not a big deal because the Windows XP 64-bit edition only runs on 64-bit architecture Itanium CPU chips and not on the more commonly available 32-bit architecture Pentium CPU chips.
Routers
Routers connect two or more networks. A router would link a LAN to the Internet or to other LANs. Routers decide which way to send packets based on the router's current knowledge of the status of the LANs or networks to which it connects. In connecting LANs to the Internet a router is a network component or software in a PC that determines the next network point to which a packet (TCP/IP packet) is forwarded so that the packet can reach its final destination.
Routers create or copy a table of available routes through a network and maintain data on their status. Routers use this information combined according to routing algorithms with distance and cost data to calculate the best route for a packet to follow to reach its final destination. Typically, packets travel through several routers to reach their final destination.
Routers work in the Windows Networking Model Adapter and Protocol Layers. Routers must understand IP routing to function properly. An Internet gateway is a router. Some new routers are a combination of switch and router, as illustrated by the Linksys cable modem/DSL four-port switch router in Figure 5.13.
Figure 5.13. DSL/cable modem router and four-port Ethernet switch.

Routers provide increased network capacity by reducing excess network traffic. They send data from source to destination based upon network routing information contained in IP packets. This is more than just the media access control (MAC) address information that switches use. The tradeoff here is that routers are capable of handling fewer packets per unit of time than switches can handle.
Firewalls
A firewall is a security system that provides a protective boundary between the SOHO LAN and the public Internet. A firewall performs routing and packet filtering functions. Firewalls work closely with routing programs. The firewall examines each network packet and determines whether to forward it toward its destination or to discard it.
By protecting the resources of a private network from unauthorized users and sometimes limiting network users in how they can access the public Internet, firewalls provide more functionality than routers alone. An enterprise with employees accessing the public Internet installs a firewall to prevent unauthorized outsiders from accessing its private data and for controlling the specific Internet resources (e.g., no gambling or sex sites permitted) its users can access.
Firewalls represent a network as a single IP address to the Internet. Sometimes a firewall is a specially designated computer separate from the rest of the network or it may be software installed in each PC host. Windows XP provides such firewall software but this is not as effective as firewall software products offered by other software developers.
A firewall may use a separate router and only perform the packet filtering functions. The firewall may physically separate the Internet from a LAN so no packets can directly access the LAN without going through the firewall first.
Firewall packet filtering includes screening packets to ensure they come from previously identified domain names and IP addresses. Firewalls can also scan packet headers and contents for key words and phrases. These can be used to discard unauthorized packets.
Firewalls allow laptop users LAN access through secure logon procedures and authentication certificates.
Firewall features include logging and reporting, automatic alarms at given thresholds of attack, and a Windows user interface for managing and configuring the firewall.
Because Internet traffic and attacks change so often, it is hard to make a firewall totally impervious to external attacks. Firewalls require constant maintenance to keep filtering effective. Sometimes firewalls filter too well and block LAN access from sites that are authorized to connect to a LAN.
While firewalls can prevent unauthorized LAN access from the Internet, they typically cannot effectively filter viruses from packets passing through the firewall. LAN users must use virus scanning programs, must not blindly open files with Visual Basic Script (VBS) macros, and must delete mail from unknown users to keep their chance of getting a virus infection low.
Firewalls must be designed specially to protect against Trojan horse software that gathers passwords and user account information. HAPPY99 was one such program that captured password information and sent them to an Internet account in China. At one time Microsoft in its update and registration process was capturing Ethernet NIC MAC addresses and storing them.
When surfing authorized Web sites, cookies are exchanged between the surfing PC and the Web site. These cookies and other information are used to track Internet usage. Firewalls do not effectively protect against this information gathering activity on the Internet.
Brain Teaser: Firewall ProductsCheck out the firewall products listed at ipw.internet.com/protection/firewalls/firewalls/. Did you find both hardware and software firewalls? Use a search engine and see what other firewall products you can find. Can you find firewall products at the www.pricewatch.com shopping site? Check Networking Products and then Other to find them. |
Windows Internet Connection Firewall (WICF)
Windows XP's Internet Connection Firewall (WICF) is firewall software that sets restrictions on what information is communicated from a PC host to and from the Internet.
When a SOHO LAN uses WICS to monitor Internet access for multiple PC hosts, WICF is enabled on the PC host supporting the WICS Internet connection. WICS and WICF can be used separately.
WICF also protects individual PC hosts connected to the Internet. When a single PC host is connected to the Internet with a cable modem, a DSL modem, or a dialup modem, WICF protects the Internet connection. WICF should be enabled on the Internet connection for all computers that are connected directly to the Internet.
Note that WICF interferes with the operation of file sharing and other VPN functions; consequently, WICF should not be run on VPN connections.
WICF monitors all communications that cross its path and inspects the source and destination address of each message that it handles. To prevent unsolicited traffic from the public Internet connection from entering the private network connection, WICF uses a table listing all communications that have originated from the WICF computer. In a PC host, WICF tracks traffic originated from the PC host. If WICF is used with WICS, WICF tracks all traffic originated from the WICF/WICS computer and all traffic originated from private network PC hosts. Inbound traffic from the Internet is compared against the entries in the table and only allowed to reach PC hosts in a SOHO LAN when an entry matches the table showing a communication exchange initiated from within the PC host or the private SOHO LAN.
Communications originating from Internet sources outside the WICF computer are dropped by the WICF. Special entries may be placed in the table to permit specifically expected traffic to enter the private SOHO LAN. WICF silently discards unsolicited communications, stopping port scanning and other simple network hacking. Instead of notifications WICF creates a security log of activity tracked by the firewall. This log can be viewed to determine if hacking has been attempted.
WICF setup panels are shown in Figure 5.14.
Figure 5.14. WICF setup panels.
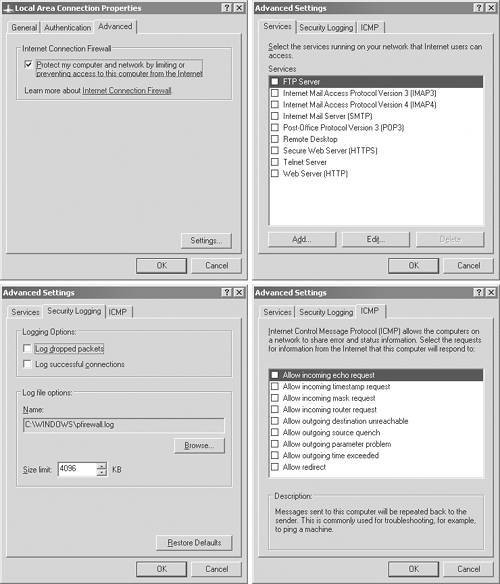
WICF can be configured to permit unsolicited traffic from the Internet to be forwarded by the WICF to the private network. An HTTP Web server would require unsolicited Internet traffic to function. By enabling the HTTP service on the WICF, unsolicited HTTP traffic is forwarded by the WICF to the HTTP server. Operational information, known as a service definition, is required by WICF to allow the unsolicited Internet traffic to be forwarded to a Web server on a private SOHO LAN.
Proxy Servers
Proxy servers act as an intermediary between a PC client and the Internet. Proxy servers perform some security, administrative control, and data caching functions. A proxy server receives a request for an Internet Web page from a client PC. The proxy server filters the request similar to a firewall. If the Web page request is OK to service, the proxy server searches for the Web page in a local cache of previously downloaded Web pages. When the proxy server finds the page, it returns it to the client PC without needing to retrieve the Web page from the Internet. If the requested Web page is not in the cache, the proxy server acts as a surrogate for the client PC and requests the Web page from the server on the Internet. When the requested Web page is returned, the proxy server matches it to the original request and forwards it on to the client PC. It then stores that page in its local cache.
Proxy servers are transparent to client PCs. Internet requests and responses appear to be services of the Internet Web page server. The proxy server is not totally invisible to PC clients because its IP address has to be specified as a configuration option for the PC networking software. Further, Web browsers and other programs need to know the specific proxy server ports they use to access the Internet. See Figure 5.15.
Figure 5.15. Proxy server settings.
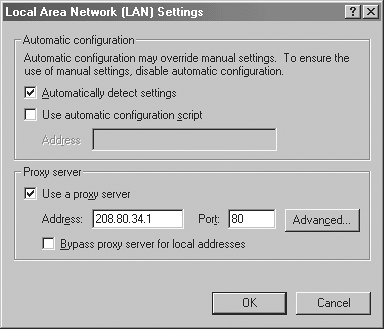
A proxy server's cache serves all LAN PC clients. If an Internet site's Web pages are frequently requested, these are likely to be stored in the proxy server's cache and retrieved from there rather than the Internet Web site. This can greatly improve Internet response time. Proxy servers can log Internet request and response activity.
Proxy servers can be associated with a gateway server separating a LAN from the Internet and with a firewall server protecting a LAN from Internet intrusion. The functions of proxy server and firewall can be in separate server programs or combined in a single package. Firewall and proxy server programs can run in different computers. For example, proxy server software may run in the same machine with firewall software or it may run in a separate server and forward requests through a firewall server.
Network Address Translation
Network Address Translation (NAT) is mapping of an Internet Protocol address (IP address) used in one network to a different IP address in another network. NAT designates one network as the inside network and the other network as the outside network. An internal LAN can use NAT to map its local inside network addresses to one or more global outside IP addresses.
Packets are sent from an IP address inside a LAN to the Internet using the global Internet IP address. Packets returned to the global Internet IP address are then translated back into the local LAN IP addresses.
The mapping process helps ensure security since each outgoing or incoming request goes through the mapping process. The mapping provides the ability to qualify or authenticate requests by matching them to previous requests. NAT reduces the number of global Internet IP addresses needed by representing a LAN to the Internet using a single Internet IP address.
NAT is part of a router and is often part of a firewall. LAN administrators create NAT tables that map global-to-local and local-to-global IP addresses. NAT can be static, using few addresses, or it can be dynamic, translating from and to a pool of IP addresses. NAT can support mapping the following:
A local IP address to one global IP address
A local IP address to any global IP addresses in a rotating pool of global IP addresses
A local IP address plus a specific TCP port to a single or pooled global IP address
A global IP address to a pool of local IP addresses
NAT reduces the need for publicly known IP addresses by mapping publicly known to privately known IP addresses. Classless interdomain routing (CIDR) aggregates publicly known IP addresses into blocks—as opposed to the previous hierarchical class IP address structure—so that fewer IP addresses are wasted. The goal is to extend the use of the existing IP version 4 (IP V4) IP addresses for several more years before the new IP version 6 (IP V6) addressing is widely supported on the Internet. IP V4 addresses are 32-bit addresses while IP V6 addresses are 128-bit addresses.
The function of all these devices is to permit a SOHO LAN to connect to the Internet over a high-speed link and represent all the PC hosts on the LAN as a single IP address to the ISP, which provides the high-speed link.
