Working with File Permissions
As you have seen in examples throughout the book, UNIX treats all directories as files; they have their own size (independent of their contents), their own permissions strings, and more. As a result, unless it's an important difference, from here on I talk about files with the intention of referring to files and directories both. Logic will confirm whether commands can apply to both, or to files only, or to directories only. (For example, you can't edit a directory and you can't store files inside other files.)
Task 5.1: Understanding File Permissions Settings
In the past hour you learned a bit about how to interpret the information that ls offers on file permissions when ls is used with the -l flag. Consider the following example: |
% ls -l
total 403
drwx------ 2 taylor 512 Sep 30 10:38 Archives/
drwx------ 3 taylor 512 Oct 1 08:23 InfoWorld/
-rw------- 1 taylor 106020 Oct 10 13:47 LISTS
drwx------ 2 taylor 1024 Sep 30 10:50 Mail/
drwx------ 2 taylor 512 Oct 6 09:36 News/
drwx------ 2 taylor 512 Sep 30 10:51 OWL/
-rw------- 1 taylor 4643 Oct 10 14:01 RUMORS.18Sept
drwx------ 2 taylor 512 Oct 10 19:09 bin/
-rw------- 1 taylor 3843 Oct 10 16:22 iecc.list
-rw-rw-r-- 1 taylor 280232 Oct 10 16:22 mailing.lists
-rw-rw---- 1 taylor 1031 Oct 7 15:44 newlists
drwx------ 2 taylor 512 Oct 10 19:09 src/
The first item of information on each line is what is key here. You learned in the preceding hour that the first item is called the permissions string or, more succinctly, permissions. It also is sometimes referred to as the mode or permissions mode of the file, a mnemonic that can be valuable for remembering how to change permissions.
The permissions can be broken into four parts: type, owner, group, and world permissions. The first character indicates the file type: d is a directory and - is a regular file. There are various other types of files in UNIX, each indicated by the first letter of its permissions string, as summarized in Table 5.1. You can safely ignore, however, any file that isn't either a regular file or a directory.
| Letter | Indicated File Type |
|---|---|
| d | Directory |
| b | Block-type special file |
| c | Character-type special file |
| l | Symbolic link |
| p | Pipe |
| s | Socket |
| - | Regular file |
The next nine letters in the permissions string are broken into three groups of three each—representing the owner, group, and everyone else—as shown in Figure 5.1.
Figure 5.1. Interpreting file permissions.

To understand what the permissions actually mean to the computer system, remember that UNIX treats everything as a file. If you install an application, it's just like everything else, with one exception: The system knows that an application is executable. A letter to your Mum is a regular file, but if you were to tell UNIX that it was executable, the system would merrily try to run it as a program (and fail).
There are three primary types of permission for files: read, write, and execute. Read permission enables users to examine the contents of the file with various programs, but they cannot alter, modify, or delete any information. They can copy the file to a directory where they have write permission and then edit the new version.
Write permission is the next step up. Users with write access to a file can add information to the file. If you have write permission and read permission for a file, you can edit the file—the read permission enables you to view the contents, and the write permission enables you to alter them. With write permission only, you'd be able to add information to the file, but you wouldn't be able to view the contents of the file at any time. Admittedly, write-only permission is unusual in UNIX, but you might see it for log files, which are files that track activity on the system. Imagine if each time anyone logged in to your UNIX system the computer recorded the fact, noting who logged in, where they logged in from, and the current time and date. Armed with that information, you could ascertain who last logged in, who uses dial-up phone lines, and who uses the computer the most. (In fact, there's a UNIX command that does just that. It's called last.)
So far you've learned that you can have files with read-only permission, read-write permission, and write-only permission. The third type of access permission is execute, noted by ls with an x in the third slot of the permissions string. You can set any file to be executable; shell scripts, perl, and other interpreted languages are text files that are executed.
% ls -l bin
total 57
-rwx------ 1 taylor 1507 Aug 17 13:27 bounce.msg
-rwxrwx--- 1 taylor 32916 Oct 10 19:09 calc
-rwx------ 1 taylor 18567 Sep 14 22:14 fixit
-rw------- 1 taylor 334 Oct 1 09:53 punt
-rwx------ 1 taylor 3424 Sep 10 22:27 rumor.mill.sh
 Try listing the files in the directory /etc on your system, and see whether you can identify which are executable files or programs, which are directories, which are symbolic links (denoted with an l as the first character of the permissions string; they're files that point to other files, or directories that point to other directories), and which are regular files.
Try listing the files in the directory /etc on your system, and see whether you can identify which are executable files or programs, which are directories, which are symbolic links (denoted with an l as the first character of the permissions string; they're files that point to other files, or directories that point to other directories), and which are regular files.Execute permission is slightly different from either read or write permission. Any file with execute permission can be treated like a program. You enter the name of the file on the command line, and if the directory is in your PATH, the file is executed.
% pwd /users/taylor % env PATH /users/taylor/bin:/bin:/usr/bin:/usr/ucb:/usr/local:/usr/local/bin: % ls -l bin/say.hi -rwxrwx--- 1 taylor 9 Oct 11 13:32 bin/say.hi % say.hi hi
You can now see the importance of your search PATH. Without a search PATH, the system wouldn't be able to find any commands, and you'd be left with a barely functional system. You can also see the purpose of checking the executable permission status. I'm going to jump ahead a bit to show you one use of the chmod function so that you can see what happens if I remove the execute permission from the say.hi program:
% chmod -x bin/say.hi % ls -l bin/say.hi -rw-rw---- 1 taylor 9 Oct 11 13:32 bin/say.hi % say.hi /users/taylor/bin/say.hi: Permission denied.
This time UNIX searched through my search path, found a file that matched the name of the program I requested, and then ascertained that it wasn't executable. The resultant error message: Permission denied.
Now try entering say.hi on your computer system. You'll get a different error message, Command not found, which tells you that UNIX searched all the directories in your search path but couldn't find a match anywhere.
Check your PATH and find a directory that you can add files in. You'll probably have a bin directory in your home directory on the list, as I have /users/taylor/bin in my search path. That's a good place to add a file using the touch command:
% env PATH /users/taylor/bin:/bin:/usr/bin:/usr/ucb:/usr/local:/usr/local/bin: % touch bin/my.new.cmd % ls -l bin -rw-rw---- 1 taylor 0 Oct 11 15:07 my.new.cmd
If you're using the C Shell as your command interpreter, it probably won't find the new command you just created. This is because, to speed things up, it keeps an internal table of where different commands are found in your search path. You need to force the program to rebuild its table, and you can do that with the simple command rehash. If, when you enter the filename, you don't get permission denied but instead see Command not found, enter rehash and try again. |
Finally, use chmod to add execute permission to the file, and try executing it one more time:
% chmod +x bin/my.new.cmd % ls -l bin/my.new.cmd -rwxrw---- 1 taylor 0 Oct 11 15:07 bin/my.new.cmd % my.new.cmd %
Voila! You've created your first UNIX command, an achievement even though it doesn't do much. You can now see how the search path and the UNIX philosophy of having applications be identical to regular files, except for the permission, can be invaluable as you learn how to customize your environment. (Note: You can also specify octal permissions using chmod, but these are a bit more complicated. It's more intuitive to use the +- conventions.)
Execute permission enables the user to run the file as if it were a program. Execute permission is independent of other permissions granted—or denied—so it's perfectly feasible to have a program with read and execute permission, but no write permission. (After all, you wouldn't want others altering the program itself.) You also can have programs with execute permission only. This means that users can run the application, but they can't examine it to see how it works or copy it. (Copying requires the ability to read the file.) |
Though actual programs with execute-only permission work fine, a special class of programs called shell scripts fail. Shell scripts act like a UNIX command-line macro facility, which enables you to easily save a series of commands in a file and then run them as a single program. To work, however, the shell must be able to read the file and execute it too, so shell scripts always require both read and execute permission. |
There are clearly quite a few permutations on the three different permissions: read, write, and execute. In practice, there are a few that occur most commonly, as listed in Table 5.2.
These permissions have different meanings when applied to directories, but --- always indicates that no one can access the file in question.
Interpretation of the following few examples should help:
-rw------- 1 taylor 3843 Oct 10 16:22 iecc.list -rw-rw-r-- 1 taylor 280232 Oct 10 16:22 mailing.lists -rw-rw---- 1 taylor 1031 Oct 7 15:44 newlists -rwxr-x--- 1 taylor 64 Oct 9 09:31 the.script
The first file, iecc.list, has read and write permission for the owner (taylor) and is off-limits to all other users. The file mailing.lists offers similar access to the file owner (taylor) and to the group, but offers read-only access to everyone else on the system. The third file, newlists, provides read and write access to both the file owner and group, but no access to anyone not in the group.
The fourth file on the list, the.script, is a program that can be run by both the owner and group members, read (or copied) by both the owner and the group, and written (altered) by the owner. In practice, this probably would be a shell script, as described earlier, and these permissions would enable the owner (taylor) to use an editor to modify the commands therein. Other members of the group could read and use the shell script but would be denied access to change it.
Task 5.2: Directory Permissions Settings
Directories are similar to files in how you interpret the permissions strings. The differences occur because of the unique purpose of directories, namely to store other files or directories. I always think of directories as bins or boxes. You can examine the box itself, or you can look at what's inside. |
In many ways, UNIX treats directories simply as files in the file system, where the content of the file is a list of the files and directories stored within, rather than a letter, program, or shopping list.
The difference, of course, is that when you operate with directories, you're operating both with the directory itself and, implicitly, with its contents. By analogy, when you fiddle with a box full of toys, you're not altering just the state of the box itself, but also potentially the toys within.
Three permissions are possible for a directory, just as for a file: read, write, and execute. The easiest is write permission. If a directory has write permission enabled, you can add new items and remove items from the directory. It's like owning the box; you can do what you'd like with the toys inside.
The interaction between read and execute permission with a directory is confusing. There are two types of operations you perform on a directory: listing the contents of the directory (usually with ls) and examining specific known files within the directory.
 Start by listing a directory, using the -d flag :
Start by listing a directory, using the -d flag :% ls -ld testme dr-x------ 2 taylor 512 Oct 11 17:03 testme/ % ls -l testme total 0 -rw-rw---- 1 taylor 0 Oct 11 17:03 file % ls -l testme/file -rw-rw---- 1 taylor 0 Oct 11 17:03 testme/file
For a directory with both read and execute permission, you can see that it's easy to list the directory, find out the files therein, and list specific files within the directory.
Read permission on a directory enables you to read the “table of contents” of the directory but, by itself, does not allow you to examine any of the files therein. By itself, read permission is rather bizarre:
% ls -ld testme dr-------- 2 taylor 512 Oct 11 17:03 testme/ % ls -l testme testme/file not found total 0 % ls -l testme/file testme/file not found
Notice that the system indicated the name of the file contained in the testme directory. When I tried to list the file explicitly, however, the system couldn't find the file.
Compare this with the situation when you have execute permission—which enables you to examine the files within the directory—but you don't have read permission, and you are prevented from viewing the table of contents of the directory itself:
% ls -ld testme d--x------ 2 taylor 512 Oct 11 17:03 testme/ % ls -l testme testme unreadable % ls -l testme/file -rw-rw---- 1 taylor 0 Oct 11 17:03 testme/file
With execute-only permission, you can set up directories so that people who know the names of files contained in the directories can access those files, but people without that knowledge cannot list the directory to learn the filenames.
I've actually never seen anyone have a directory in UNIX with execute-only permission, and certainly you would never expect to see one set to read-only. It would be nice if UNIX would warn you if you set a directory to have one permission and not the other. However, UNIX won't do that. So, remember for directories always to be sure that you have both read and execute permission set. Table 5.3 summarizes the most common directory permissions.
| Permission | Meaning |
|---|---|
| --- | No access allowed to directory |
| r-x | Read-only access, no modification allowed |
| rwx | All access allowed |
One interesting permutation of directory permissions is for a directory that's write-only. Unfortunately, the write-only permission doesn't do what you'd hope, that is, enable people to add files to the directory without being able to see what the directory already contains. Instead, it's functionally identical to having it set for no access permission at all.
At the beginning of this hour, I used ls to list various files and directories in my home directory:
% ls -l total 403 drwx------ 2 taylor 512 Sep 30 10:38 Archives/ drwx------ 3 taylor 512 Oct 1 08:23 InfoWorld/ -rw------- 1 taylor 106020 Oct 10 13:47 LISTS drwx------ 2 taylor 1024 Sep 30 10:50 Mail/ drwx------ 2 taylor 512 Oct 6 09:36 News/ drwx------ 2 taylor 512 Sep 30 10:51 OWL/ -rw------- 1 taylor 4643 Oct 10 14:01 RUMORS.18Sept drwx------ 2 taylor 512 Oct 10 19:09 bin/ -rw------- 1 taylor 3843 Oct 10 16:22 iecc.list -rw-rw-r-- 1 taylor 280232 Oct 10 16:22 mailing.lists -rw-rw---- 1 taylor 1031 Oct 7 15:44 newlists drwx------ 2 taylor 512 Oct 10 19:09 src/Now you can see that all my directories are set so that I have list, examine, and modify (read, execute, and write, respectively) capability for myself, and no access is allowed for anyone else.
The very top-level directory is more interesting, with various directory owners and permissions.
% ls -l / -rw-r--r-- 1 root 61440 Nov 29 1991 boot drwxr-xr-x 4 root 23552 Sep 27 11:31 dev -r--r--r-- 1 root 686753 Aug 27 21:58 dynix drwxr-xr-x 6 root 3072 Oct 11 16:30 etc drwxr-xr-x 2 root 8192 Apr 12 1991 lost+found lrwxr-xr-x 1 root 7 Jul 28 1988 sys -> usr/sys drwxrwxrwx 65 root 12800 Oct 11 17:33 tmp drwxr-xr-x 753 root 14848 Oct 5 10:07 usera drwxr-xr-x 317 root 13312 Oct 5 10:17 userb drwxr-xr-x 626 root 13312 Oct 8 13:02 userc drwxr-xr-x 534 root 10752 Sep 30 13:06 users drwxr-xr-x 34 root 1024 Oct 1 09:10 usr drwxr-xr-x 5 root 1024 Oct 1 09:20 varClearly, this machine has a lot of users. Notice that the link count for usera, userb, userc, and users are each in the hundreds. The dev directory has read and execute permission for everyone and write permission for the owner (root). Indeed, all the directories at this level are identical except for tmp, which has read, write, and execute permission for all users on the system.
Did you notice the listing for the sys directory buried in that output?
lrwxr-xr-x 1 root 7 Jul 28 1988 sys -> usr/sys
From the information in Table 5.1, you know that the first letter of the permissions string being an l means that the directory is a symbolic link. The filename shows just the specifics of the link, indicating that sys points to the directory usr/sys. In fact, if you count the number of letters in the name usr/sys, you'll find that it exactly matches the size of the sys link entry too.
Try using ls -l / yourself. You should be able to understand the permissions of any file or directory that you encounter.
Permissions of files and directories will prove easier as you work with UNIX more. |
Task 5.3: Modifying File and Directory Permissions with chmod
Now that you can list directory permissions and understand what they mean, how about learning a UNIX command that lets you change them to meet your needs? You've already had a sneak preview of the command: chmod. The mnemonic is “change mode,” and it derives from early UNIX folk talking about permission modes of files. You can remember it by thinking of it as a shortened form of change permission modes. |
To sound like a UNIX expert, pronounce chmod as “ch-mod,” “ch” like the beginning of child, and “mod” to rhyme with cod. |
The chmod command enables you to specify permissions in two different ways: symbolically or numerically. Symbolic notation is most commonly used to modify existing permissions, whereas numeric format always replaces any existing permission with the new value specified. In this task, you learn about symbolic notation, and the next task focuses on the powerful numeric format.
Symbolic notation for chmod is a bit like having a menu of different choices, enabling you to pick the combination that best fits your requirements. Figure 5.2 shows the menus.
Figure 5.2. The menu of symbolic chmod values.

The command chmod is like a smorgasbord where you can choose any combination of items from either the first or last boxes, and stick your choice from the center box between them.
For example, if you wanted to add write permission to the file test for everyone in your group, you would, working backward from that description, choose g for group, + for add, and w for write. The finished UNIX command would be chmod g+w test.
When you have an account assigned to you, you have a unique user name, but you are also included in one or more groups. Group permissions let other people working on the same project share information without opening up the information to the rest of the world. |
If you decided to take away read and execute permission for everyone not in your group, you could use chmod o-rx test to accomplish the task.
 Turn to your computer and, using touch and ls, try changing permissions and see what happens. I'll do the same:
Turn to your computer and, using touch and ls, try changing permissions and see what happens. I'll do the same:% touch test % ls -l test -rw-rw---- 1 taylor 0 Oct 11 18:29 test
The first modification I want to make is that people in my group should be able to read the file. Because I don't really want them altering it, I'll rescind write permission for group members:
% chmod g-w test % ls -l test -rw-r----- 1 taylor 0 Oct 11 18:29 test
But then my boss reminds me that everyone in the group should have all access permissions. Okay, I'll do so.
% chmod g+wx test % ls -l test -rw-rwx--- 1 taylor 0 Oct 11 18:29 test
I also could have done that with chmod g=rwx, of course.
Wait a second. This test file is just for my own use, and nobody in my group should be looking at it anyway. I'll change it back.
% chmod g-rwx test % ls -l test -rw------- 1 taylor 0 Oct 11 18:29 test
Great. Now the file is set so that I can read and write it, but nobody else can touch it, read it, modify it, or anything else.
If I relented a bit, I could easily add, with one last chmod command, read-only permission for everyone:
% chmod a+r test % ls -l test -rw-r--r-- 1 taylor 0 Oct 11 18:29 test
Permissions in UNIX are based on a concentric access model from Multics. (In Hour 1, “What Is This UNIX Stuff?” you learned that the name UNIX is also a pun on Multics.) Figure 5.3 illustrates this concept. |
Figure 5.3. The concentric circles of access.

As a result, it's incredibly rare to see a file where the owner doesn't have the most access to a file. It'd be like buying a car and letting everyone but yourself drive it—rather silly. Similarly, members of the group are given better or equal permission to everyone else on the machine. You would never see r--r--rwx as a permissions string.
Experiment a bit more with the various combinations possible with the chmod symbolic notation. How would you change permission on a directory to enable all users to use ls to examine it but to deny them the ability to add or remove files? How about adding write access for the owner but removing it for everyone else?
Task 5.4: Setting New File Permissions with chmod
The second form of input that chmod accepts is absolute numeric values for permissions. Before you can learn how to use this notation, you have to learn a bit about different numbering systems first. |
The numbering system you're familiar with, the one you use to balance your checkbook and check the receipt from the market, is decimal, or base 10. This means that each digit—from right to left—has the value of the digit raised by a power of 10, based on the digit's location in the number. Figure 5.4 shows what the number 5,783 is in decimal.
Figure 5.4. Interpreting decimal numbers.

You can see that in a base-10 numbering system, the value of a number is the sum of the value of each digit multiplied by the numeric base raised to the nth power. The n is the number of spaces the digit is away from the rightmost digit. That is, in the number 5,783, you know that the 7 is worth more than just 7, because it's two spaces away from the rightmost digit (the 3). Therefore, its value is the numeric base (10) raised to the nth power, where n is 2 (it's two spaces away). Ten to the second power equals 100 (102 = 100), and when you multiply that by 7, sure enough, you find that the 7 is worth 700 in this number.
What does all this have to do with the chmod command? At its most fundamental, UNIX permissions are a series of on/off switches. Does the group have write permission? One equals yes, zero equals no. Each digit in a decimal system can have 10 different values. A binary system is one in which each digit can have only two values: on or off, 1 or 0, yes or no. Therefore, you can easily and uniquely describe any permissions string as a series of zeros and ones, as a binary number. Figure 5.5 demonstrates.
Figure 5.5. Permissions as binary numbers.
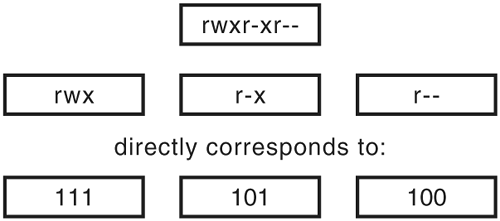
The convention is that if a letter is present, the binary digit is a 1—that permission is permitted—and if no letter is present, the digit is a zero. Thus, r-xr----- can be described as 101100000, and r--r--r-- can be described in binary as 100100100.
You've already learned that the nine-character permissions string is really just a three-character permissions string duplicated thrice for the three different types of user (the owner, group, and everyone else). That means that you can focus on learning how to translate a single tri-character permissions substring into binary and extrapolate for more than one permission. Table 5.4 lists all possible permissions and their binary equivalents.
| Permissions String | Binary Equivalent |
|---|---|
| --- | 000 |
| --x | 001 |
| -w- | 010 |
| -wx | 011 |
| r-- | 100 |
| r-x | 101 |
| rw- | 110 |
| rwx | 111 |
Knowing how to interpret decimal numbers using the rather complex formula presented earlier, you should not be surprised that the decimal equivalent of any binary number can be obtained by the same technique. Figure 5.6 shows how, with the binary equivalent of the r-x permission.
If r-x is equal to 5, it stands to reason that each of the possible three-character permissions has a single-digit equivalent, and Table 5.5 expands Table 5.4 to include the single-digit equivalents.
Figure 5.6. Expressing r-x as a single digit.

| Permissions String | Binary Equivalent | Decimal Equivalent |
| --- | 000 | 0 |
| --x | 001 | 1 |
| -w- | 010 | 2 |
| -wx | 011 | 3 |
| r-- | 100 | 4 |
| r-x | 101 | 5 |
| rw- | 110 | 6 |
| rwx | 111 | 7 |
The value of having a single digit to describe any of the seven different permission states should be obvious. Using only three digits, you now can fully express any possible combination of permissions for any file or directory in UNIX—one digit for the owner permission, one for group, and a one for everyone else. Figure 5.7 shows how to take a full permissions string and translate it into its three-digit numeric equivalent.
Figure 5.7. Translating a full permissions string into its numeric equivalent.

From this illustration, you can see how the permissions string rw-r----- (read and write permission for the owner, read permission for the group, and no access allowed for everyone else) is exactly equivalent to the numeric string 640.
 Try to create numeric strings on your own, using Table 5.4 to help. Turn to your computer and use ls to display some listings. Break each permissions string into three groups of three letters, and figure out the numeric equivalents. Here are some examples from the ls -C -F listing of my home directory:
Try to create numeric strings on your own, using Table 5.4 to help. Turn to your computer and use ls to display some listings. Break each permissions string into three groups of three letters, and figure out the numeric equivalents. Here are some examples from the ls -C -F listing of my home directory:drwx------ 2 taylor 512 Sep 30 10:38 Archives/
For Archives/, the equivalent numeric permission is 700.
-rw------- 1 taylor 106020 Oct 10 13:47 LISTS
For LISTS, the equivalent numeric permission is 600.
-rw-rw-r-- 1 taylor 280232 Oct 10 16:22 mailing.lists
For mailing.lists, the equivalent numeric permission is 664.
-rw-rw---- 1 taylor 1031 Oct 7 15:44 newlists
For newlists, the equivalent numeric permission is 660.
There's one last step required before you can try using the numeric permissions strings with chmod. You need to be able to work backward to determine a permission that you'd like to set, and figure out the numeric equivalent for that permission. |
Task 5.5: Calculating Numeric Permissions Strings
For example, if you wanted to have a directory set so that you have all access, people in your group can look at the contents but not modify anything, and everyone else is shut out, how would you do it? |
All permissions for yourself means you want read+write+execute for owner (or numeric permission 7); read and listing permission for others in the group means read+execute for group (numeric permission 5); and no permission for everyone else, numeric permission 0. Put the three together and you have the answer, 750.
That's the trick of working with chmod in numeric mode. You specify the absolute permissions you want as a three-digit number, and the system sets the permissions on the file or directory appropriately.
The absolute concept is important with this form of chmod. You cannot use the chmod numeric form to add or remove permissions from a file or directory. It is usable only for reassigning the permissions string of a file or directory.
The good news is that, as you learned earlier in this hour, there is a relatively small number of commonly used file permissions, summarized in Table 5.6.
| Permission | Numeric | Used With |
|---|---|---|
| --------- | 000 | All types |
| r-------- | 400 | Files |
| r--r--r-- | 444 | Files |
| rw------- | 600 | Files |
| rw-r--r-- | 644 | Files |
| rw-rw-r-- | 664 | Files |
| rw-rw-rw- | 666 | Files |
| rwx------ | 700 | Programs and directories |
| rwxr-x--- | 750 | Programs and directories |
| rwxr-xr-x | 755 | Programs and directories |
 Turn to your computer and try using the numeric mode of chmod, along with ls, to display the actual permissions to learn for yourself how this works.
Turn to your computer and try using the numeric mode of chmod, along with ls, to display the actual permissions to learn for yourself how this works.% touch example % ls -l example -rw-rw---- 1 taylor 0 Oct 12 10:16 example
By default, files are created in my directory with mode 660.
To take away read and write permission for people in my group, I'd replace the 660 permission with what numeric permissions string? I'd use 600:
% chmod 600 example % ls -l example -rw------- 1 taylor 0 Oct 12 10:16 example
What if I change my mind and want to open up the file for everyone to read or write? I'd use 666:
% chmod 666 example % ls -l example -rw-rw-rw- 1 taylor 0 Oct 12 10:16 example
Finally, pretend that example is actually a directory. What numeric mode would I specify to enable everyone to use ls in the directory and enable only the owner to add or delete files? I'd use 755:
% chmod 755 example % ls -l example -rwxr-xr-x 1 taylor 0 Oct 12 10:16 example
You've looked at both the numeric mode and the symbolic mode for defining permissions. Having learned both, which do you prefer? |
Somehow I've never gotten the hang of symbolic mode, so I almost always use the numeric mode for chmod. The only exception is when I want to add or delete simple permissions. Then, I use something like chmod +r test to add read permission. Part of the problem is that I don't think of the user of the file but rather the owner, and specifying o+r causes chmod to change permission for others. It's important, therefore, that you remember that files have users so you remember u for user, and that everyone not in the group is other so you remember o. Otherwise, learn the numeric shortcut! |
File permissions and modes are one of the most complex aspects of UNIX. You can tell—it's taken two hours to explain it fully. It's very important that you spend the time really to understand how the permissions strings relate to directory permissions, how to read the output of ls, and how to change modes using both styles of the chmod command. It'll be time well spent.
Task 5.6: Establishing Default File and Directory Permissions with the umaskCommand
When I've created files, they've had read+write permission for the owner and group, but no access allowed for anyone else. When you create files on your system, you might find that the default permissions are different. |
The controlling variable behind the default permissions is called the file creation mask, or umask for short.
Inexplicably, umask doesn't always list its value as a three-digit number, but you can find its value in the same way you figured out the numeric permissions strings for chmod. For example, when I enter umask, the system indicates that my umask setting is 07. A leading zero has been dropped, so the actual value is 007, a value that British MI6 could no doubt appreciate!
But 007 doesn't mean that the default file is created with read+write+execute for everyone else and no permissions for the owner or group. It means quite the opposite, literally.
The umask command is a filter through which permissions are pushed to ascertain what remains. Figure 5.8 demonstrates how this works.
Figure 5.8. Interpreting the umask value.

Think of your mask as a series of boxes: If the value is true, the information can't exude through the box. If the value is false, it can. Your mask is therefore the direct opposite to how you want your permissions to be set. In Figure 5.8, I want to have 770 as the default permission for any new file or directory I create, so I want to specify the exact opposite of that, 007. Sure enough, with this umask value, when I create new files, the default permission allows read and write access to the owner and group, but no access to anyone else.
Things are a bit trickier than that. You've probably already asked yourself, Why, if I have 007 as my mask (which results in 770 as the default permissions), do my files have 660 as the actual default permission?
The reason is that UNIX tries to be smart about the execute permission setting. If I create a directory, UNIX knows that execute permission is important, and so it grants it. However, for some files (particularly text files), execute permission doesn't make sense, so UNIX actually masks it out internally.
Another way to look at this is that any time you create a file containing information, the original mask that the system uses to compare against your umask is not 777 (not rwxrwxrwx, to put it another way) but rather 666 (rw-rw-rw-), in recognition of the unlikelihood that you'll want to execute the new file.
The good news is that you now know an easy way to set the execute permission for a file if the system gets it wrong: chmod +x filename does the trick.
 Turn to your computer and check your umask setting, and then alternate between changing its values and creating new files with touch.
Turn to your computer and check your umask setting, and then alternate between changing its values and creating new files with touch.% umask 7 % touch test.07 % ls -l test.07 -rw-rw---- 1 taylor 0 Oct 12 14:38 test.07
To change the value of your umask, add the numeric value of the desired mask to the command line:
% umask 077This changes my umask value from 007 (------rwx) to 077 (---rwxrwx). Before you look at the following listing, what would you expect this modification to mean? Remember, you should read it as the exact opposite of how you want the default permissions.
% touch test.077 % ls -l test.077 -rw------- 1 taylor 0 Oct 12 14:38 test.077
Is that what you expected?
What would you do if you wanted to have the default permission keep files private to just the owner and make them read-only?
You can work through this problem in reverse. If you want r-x------ as the default permission (because the system takes care of whether execute permission is needed, based on file type), write down the opposite permission, which is -w-rwxrwx. Translate that to a binary number, 010 111 111, and then to a three-digit value, 277 (010=2, 111=7, 111=7). That's the answer. The value 277 is the correct umask value to ensure that files you create are read-only for yourself and off-limits to everyone else.
% umask 277 % touch test.277 % ls -l test.277 -r-------- 1 taylor 0 Oct 12 14:39 test.277
What if you wanted to have files created with the default permission being read-only for everyone, read-write for the group, but read-only for the owner? Again, work backward. The desired permission is r-xrwxr-x, so create the opposite value (-w-----w-), translate it into binary (010 000 010), and then translate that into a three-digit value: 202 (010=2, 000=0, 010=2).
As a rule of thumb, it's best to leave the execute permission enabled when building umask values so the system doesn't err when creating directories. |
The umask is something set once and left alone. If you've tried various experiments on your computer, remember to restore your umask back to a sensible value to avoid future problems (though each time you log in to the system it's reset to your default value). |
In the next hour, you learn how to use the mkdir command to create new directories, and you see how the umask value affects default directory access permissions.
Task 5.7: Identifying Owner and Group for Any File or Directory
One of the many items of information that the ls command displays when used with the -l flag is the owner of the file or directory. So far, all the files and directories in your home directory have been owned by you, with the probable exception of the “..” directory, which is owned by whomever owns the directory above your home. |
In other words, when you enter ls -l, you should see your account name as the owner for every file in the listing.
If you're collaborating with another user, however, there might well be times when you'll want to change the owner of a file or directory once you've created and modified it.The first step in accomplishing this is to identify the owner and group.
Identifying the owner is easy; ls lists that by default. But how do you identify the group of which the file or directory is a part?
 The ls command can show the group membership of any file or directory by addition of a new command flag, -g. By itself, -g doesn't alter the output of ls, but when used with the -l flag, it adds a column of information to the listing. Try it on your system. Here is an example:
The ls command can show the group membership of any file or directory by addition of a new command flag, -g. By itself, -g doesn't alter the output of ls, but when used with the -l flag, it adds a column of information to the listing. Try it on your system. Here is an example:% ls -lg /tmp -rw-r--r-- 1 root root 0 Oct 12 14:52 sh145 drwxr-xr-x 2 shakes root 512 Oct 12 07:23 shakes/ -rw------- 1 meademd com435 0 Oct 12 14:46 snd.12 -rw------- 1 dessy stuprsac 1191 Oct 12 14:57 snd.15 -rw------- 1 steen utech 1 Oct 12 10:28 snd.17 -rw-r----- 1 jsmith utech 258908 Oct 12 12:37 sol2Both owners and groups vary for each of the files and directories in this small listing. Notice that files can have different owners while having the same group. (There are two examples here: sh145 and the shakes directory, and snd.17 and sol2.)
On many System V-based systems, the output of ls -l always shows user and group. The -g flag actually turns off this display! |
Directories where there are often a wide variety of owners for directories are the directories above your own home directory and the tmp directory, as you can see in instruction 1. Examine both on your system and identify both the owner and group of all files. For files in the same group you're in (with the id command, you can find which group or groups you are in) but not owned by you, you'll need to check which of the three permission values to identify your own access privileges?
Files and directories have both owners and groups, although the group is ultimately less important than the owner, particularly where permissions and access are involved. |
