|
3 |
U.S. Compliance Laws and Information Security Policy Requirements |
IN RECENT YEARS globalization has been driven by technology and the growth of the Internet. More than 2.3 billion people worldwide have access to the Internet, according to a Brookings Institution report published in February 2013.1 Equally impressive, in 2013, 77 percent of individuals in developed countries had access to the Internet, according to the SUNY Levin Institute.2
Additionally, the expansion of Internet access continues to grow rapidly in developing countries. The Internet’s explosive reach has created global economic opportunity never seen before. You can see this in products you buy every day. Technology has helped create a global supply chain that delivers, to consumers worldwide, an array of low-cost goods that would have been unimaginable just a few years ago.
But all this has come at a price. Privacy has become an issue. People may feel, not unreasonably, that every action they take is being captured. Cellphones leave computer records of who called whom. Social media provide channels for cyberbullying in schools. Hackers have been able to steal massive amounts of credit card information through the Internet. And countries have used the Internet to launch attacks on other countries.
In February 2014, President Obama declared, “Cyberterrorism is [the] country’s biggest threat.”3 In general, cyberterrorism, or cyberwarfare, refers to an attempt to cause fear or major disruptions in a society through hacking computers. The idea is to attack government computers, major companies, or key areas of the economy. Such attacks can come from terrorist groups or individuals, as well as nation-states (sovereign countries). But given the resources involved, it shouldn’t be surprising that cyberterrorism is often sponsored by nation-states.
No government can sit on the sidelines with so much at stake. In the United States, the federal and state governments establish laws that define how to control, handle, share, and process the sensitive information that this new economy relies on. Much of that information is about you. It’s personal data about your finances, health, buying habits, and more. To these laws are added regulations, typically written by civil servants to implement the authority of the law. Regulators are the individuals or entities who help enforce these rules. Industry groups also try to self-regulate, which means they create standards their members must follow. Failure to follow regulations or industry standards can result in fines or limits placed on a company’s ability to operate. Gross violations of regulations can be seen as violation of criminal law. These violations can result in the arrest of officers of the company and possible jail time.
This chapter discusses major government laws and their compliance requirements. When the term regulations appears in this chapter, it means those that relate to U.S. laws. You will read how these requirements will influence security policies. You will read about major drivers for the regulations and the importance of protecting personal privacy. You will see how to create compliant polices, standards, procedures, and guidelines. The chapter also examines industry standards that drive security policies. Any one of these laws or standards could take up the pages of an entire book. But the focus here is on high-level principles that drive security policies and controls.
Chapter 3 Topics
This chapter covers the following topics and concepts:
• What U.S. compliance laws are and why they are important
• Who is protected by these laws
• How security policies are influenced by the laws
• What approaches are used to make security policies, standards, procedures, and guidelines comply with regulations
• What industry leading practices are
• Why industry standards are important
When you complete this chapter, you will be able to:
• Compare and contrast different U.S. compliance laws
• Describe regulations and their importance in organizations
• Describe government drivers to implement regulations and their importance in maintaining compliance with laws
• Define cyberterrorism and the nation-state threat
• Explain approaches to align policies with regulations
• Explain leading practices and how they fit into the industry
U.S. Compliance Laws
Tremendous economic benefits flow from private markets. These benefits often rely on the use of technology. There is no single way of looking at government’s role in regulating or intervening in these markets. However, government is concerned with consumer protection, promoting a stable economy, and maintaining a reliable source of tax revenue. The government must balance these needs against the threat of cyberterrorism. All of these drivers are linked. If people feel safe using the Internet to buy goods and services, a stable economy emerges. People also have to trust the government to keep them safe. When you have a stable sector of the economy, government has a reliable source of tax revenue. It is good to understand what drives government regulations. In the end, government regulations are mandates. Security policies must achieve their goals while balancing business needs. You will see that organizations put stronger security in areas where the perceived threats to resources or employees are greater.
When you implement security policies, remember that there are pressures and tradeoffs. For example, you may have to place restrictive controls on data to comply with a regulation that limits how your business operates. If your company is part of the country’s critical infrastructure, there may be certain security policies it must comply with. As you balance competing interests, you must talk to business leaders to understand their priorities and issues. Security policies reflect how the business wishes to balance competing interests.
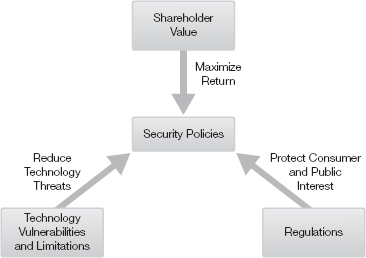
Shareholders of a company are investors who expect to make money. Maximizing profit and maintaining a healthy stock price is a business concern. The government focuses more on fairness, health, and safety issues. One of the challenges organizations face is the cost of keeping pace with ever-changing technology. This includes the need to update policies at the same time the organization updates technology. Failure to do so could create weaknesses in the system. These weaknesses could make business processes out of compliance with industry and government regulations. The role of well-defined security policies is to be clear and concise on how these goals and vulnerabilities will be addressed. Figure 3-1 illustrates these competing interests—shareholder value, technology vulnerabilities and limitations, and regulations.
Government agencies that regulate information handling exist at the federal and state levels. These agencies sometimes have competing interests. As a result, laws often overlap requirements but are written from different perspectives. A federal banking regulation, for example, might define data privacy differently than a state law does. Competing regulatory agencies may have different missions and use different enforcement tools. Compliance can be difficult and costly with conflicting language and different interpretations. For example, a large U.S.-based bank needs to comply with hundreds of regulations.
Staying compliant means incurring the cost to keep up with changes in many laws, continually documenting evidence of compliance, and dealing with onsite visits of regulators. Staying compliant with regulations can be a distraction for businesses and the technology teams that support them. Yet they are very important. In large companies, compliance teams act as a go-between for the technical staff and regulators. These compliance teams know the regulations and requirements. They obtain information from the technical teams. The compliance teams meet with regulators. These are usually specially trained individuals who know company policy, the company’s technological capability, and the law. This allows the technical staff to stay focused primarily on delivering technological solutions.
What Are U.S. Compliance Laws?
What are the major concerns of U.S. regulations? How do you manage competing interests in security policies? As much as these regulations might differ, there are also common concepts. In recent years there has been increased partnership between the U.S. government and private companies. This partnership comes in many forms, such as the sharing of good security policies and the sharing of resources to investigate hacking incidents. Most notably, the government now shares intelligence information about threats and the type of attacks that might occur. In February 2013 the White House issued an executive order for key agencies to share cyberthreat information with private companies.4 This sharing of cyberthreat information helps companies better defend themselves.
The best approach to regulatory compliance is common sense. Rather than building rules into security policies for each regulation, you should build in the key control concepts found in many regulations. By mapping these key control concepts to specific security policies, you can quickly demonstrate compliance across a broad set of regulations. If you can master these concepts, you can learn how to recognize these principles in regulations. This gives you the basic tools needed to keep your security policies compliant.
In this chapter, it’s not possible to discuss all key concepts for information security in every U.S. regulation. Instead, you will learn about several major regulations. These regulations deal with consumer rights and personal privacy. These laws protect consumers from potential scams and ensure the privacy of personal information. Consumer rights in e-commerce broadly deal with creating rules on how to handle a consumer’s transaction and other information. Personal privacy in e-commerce broadly deals with how to handle personal information and what it is used for. Table 3-1 identifies key concepts found in many regulations that influence what will appear in your security policies.
Federal Information Security Management Act (FISMA)
The Federal Information Security Management Act (FISMA) is a good example of government self-regulation. The federal government is unique in that it can identify the standards it wants to follow and passes laws requiring the standards to be followed. FISMA was put into law in 2002.
FISMA requires government agencies to adopt a common set of information security standards. Some parts of the government go beyond these standards, such as the military. For many government agencies, FISMA creates mandatory requirements to ensure the integrity, confidentiality, and availability of data. If your organization processes data for the government, you may be required to follow these same standards. FISMA also requires that agencies send annual reviews to the Office of Management and Budget (OMB). For example, an audit of the Veterans Affairs (VA) Department in 2012 found 15,000 security policy violations. As a result the VA was found to be noncompliant with FISMA.
The National Institute of Standards and Technology (NIST) is responsible for developing FISMA-mandated information security standards and procedures. Each agency is then responsible for adopting them as part of their agency’s information security policies. NIST standards, processes, and guidelines are available at http://csrc.nist.gov/publications/PubsSPs.html.
TABLE 3-1 Key concepts contained in U.S. compliance laws affecting information security policies.
| CONCEPT | OBJECTIVE |
| Full disclosure | The concept that individuals should know what information about them is being collected. A company must give written notice on how it plans to use your information. |
| Limited use of personal data | The key idea is that the company can use the information collected only for the immediate service provided, or transaction made, such as a purchase. For example, assume a bank just approved your credit card purchase of ski equipment. In most states the bank could not then share that information with someone who will try to sell you a ski vacation. |
| Opt-in/opt-out | The practice of asking permission on how personal information can be used beyond its original purpose. For example, a real estate company might ask permission of someone who sold their home if their information can be shared with a moving company. |
| Data privacy | A company must tell an individual how personal information will be protected and limits placed on how the data will be shared. |
| Informed consent | The concept that someone is of legal age, has the needed facts, and is without undue pressure to make an informed judgment. |
| Public interest | The concept that an organization has an obligation to the general public beyond its self-interest. It’s a vague term, but it’s not unusual for regulators to look at the impact an organization has on the industry or the economy in general. |
NIST publications outline a complete set of security standards and processes. To be compliant, your policies must include key security control requirements. Some of these key requirements include:
• Inventory—The NIST standards require an inventory of hardware, software, and information. The inventory identifies the type of information handled, how data passes to the systems, and special attention to national security systems.
• Categorize by risk level—The NIST standards require the inventory to be classified. The idea is that this classification will highlight higher-risk areas that need more protection.
• Security controls—The NIST standards outline which controls should be applied and when. They outline how these controls are documented and approved. It is a risk-based approach giving some flexibility to the agency to tailor controls to meet its operational needs.
• Risk assessment—The NIST standards require risk assessments to be performed. Risk assessments are an essential part of a risk-based security approach. The risk assessment results drive the type of security controls to be applied.
• System security plan—The NIST standards require a formal security plan for major systems and for the system or application owner. The security plan serves as a road map. It is updated to keep current with threats and is an important part of a certification and accreditation process.
• Certification and accreditation—This process occurs after the system is documented, controls tested, and risk assessment completed. It is required before going live with a major system. Once a system is certified and accredited, responsibility shifts to the owner to operate the system. This process is also referred to as the “security certification” process.
• Continuous monitoring—All certified and accredited systems must be continuously monitored. Monitoring includes looking at new threats, changes to the system, and how well the controls are working. Sometimes a system has so many changes that it must be re-certified.
Health Insurance Portability and Accountability Act (HIPAA)
The Health Insurance Portability and Accountability Act (HIPAA) became law in 1996. The law protects a person’s privacy. If you handle someone’s health records, you must adhere to HIPAA. This includes doctor’s offices, hospitals, clinics, and insurance companies. The law recognizes that digital data exchange of health records, such as between insurance companies and doctor’s offices, is a necessity. But in 2013 new restrictions were placed on access to health records by subcontractors and vendors. The law wants to make sure that patient privacy is maintained.
The HIPAA law defines someone’s health record as protected health information (PHI). The term PHI refers to both digital and physical paper copies of health records. Electronic PHI (EPHI) refers to just the electronic form of PHI records. HIPAA establishes privacy rules that outline how EPHI can be collected, processed, and disclosed. There are significant penalties for violating these rules. In 2013 these fines were increased to a maximum of $1.5 million per violation. This regulation applies to any covered entity that manages health records, including:
FYI
The U.S. Department of Health and Human Services has several publications on HIPAA privacy and security standards at http://www.cms.hhs.gov/HIPAAGenInfo/04_PrivacyandSecurityStandards.asp.
• Health care providers—Doctors, hospitals, clinics, and others
• Health plans—Those that pay the cost for the medical care such as insurance companies
• Health care clearinghouses—Those that process and facilitate billing
• “Business associates”—Vendors and subcontractors of any covered entity
For your security policies to be HIPAA-compliant, they must include the following key control requirements:
• Administrative safeguards—Refers to the formal security policies and procedures that map to HIPAA security standards. It also refers to the governance of the security policies and their implementation.
• Physical safeguards—Refers to the physical security of computer systems and the physical health records.
• Technical safeguards—Refers to the controls that use technology to protect information assets.
• Risk assessment—Refers to a standard requirement of a risk-based management approach to information security.
Gramm-Leach-Bliley Act (GLBA)
The Gramm-Leach-Bliley Act (GLBA) became law in 1999. The law is not focused on technology. Rather, it was meant to repeal existing laws so that banks, investment companies, and other financial services companies could merge. Prior to GLBA, banks, for example, were restricted on the types of products they could offer. However, under what is known as Section 501(b), the law outlines information security requirements for the privacy of customer information.
The law is enforced through regulators who are members of the Federal Financial Institutions Examination Council (FFIEC). The FFIEC publishes booklets of what type of computer security policies and controls must be in place for an institution or company to be compliant with GLBA. These booklets define availability, integrity, confidentiality, accountability, and assurance as key objectives.
FYI
The FFIEC booklets are used by many government agencies. They are available to the public. Aligning security policies to these booklets will help keep a company compliant with government regulations. See http://ithandbook.ffiec.gov/it-booklets/information-security/information-security-strategy/architecture-considerations/policies-and-procedures.aspx.
FYI
GLBA applies to any financial institution defined as “any institution the business of which is engaging in financial activities as described in section 4(k) of the Bank Holding Company Act (12 U.S.C. § 1843(k)).” This is broadly defined to mean any organization that lends, exchanges, transfers, invests, or safeguards money or securities. Generally any company that deals in credit or loans would be covered. This includes businesses offering payment plans, such as car dealerships commonly offer.
The FFIEC booklets are publicly available through the council’s Web site. The following Web site introduces the 501(b) rules: http://ithandbook.ffiec.gov/it-booklets.aspx.
To be GLBA-compliant, your security policies must include the following key components:
• Governance—Requires a strong governance structure in place. This includes designating someone in an organization as accountable for information security. This is often the chief information security officer (CISO) or chief information officer (CIO). Most boards receive formal GLBA reporting through the audit committee. The head of information security usually writes this report each quarter.
• Information security risk assessment—Requires a well-defined information security risk assessment to identify threats, potential attacks, and impacts to the organization.
• Information security strategy—Requires a formal security plan to reach compliance.
• Security controls implementation—Requires a process to properly design and install security controls that meet the security plan objectives.
• Security monitoring—Requires continuous monitoring of security controls. This is to ensure that the design meets the objectives. This is event-based monitoring and includes incident response.
• Security monitoring and updating—Requires monitoring of trends, incidents, and business strategies, and appropriate updates to the security plan.
Sarbanes-Oxley (SOX) Act
The Sarbanes-Oxley (SOX) Act became law in 2002. The law was enacted in reaction to a series of accusations of corporate fraud. Some companies were accused of “cooking the accounting books” or making illegal loans to their top executives. Companies such as Enron and WorldCom became symbols of corporate greed and corruption. Enron filed for bankruptcy in 2001 amid accusations of cooking the books to inflate its stock price. WorldCom filed for bankruptcy in 2002 amid accusations of illegal loans to its chief executive officer (CEO), as well as billions in accounting fraud to inflate the stock price. These two highly visible corporate fraud cases shook shareholder and public confidence. SOX was enacted to restore confidence in the markets.
SOX goes well beyond information security policies. It also describes how a company should report earnings, valuations, corporate responsibilities, and executive compensation. The act is intended to improve the financial accuracy and public disclosure to investors. In fact, some argue the act goes too far and is too costly. This chapter focuses on those portions that affect security policies known as SOX 404.
The basic idea behind SOX 404 is to require security policies and controls that provide confidence in the accuracy of financial statements. In other words, security policies must ensure the integrity of the financial data. Independent testing of these controls is required. Additionally, top executives are required to sign off quarterly that these controls meet SOX 404 requirements or explain why they did not.
One of the challenges of SOX is cost. It is very expensive and nearly impossible to test all a company’s controls. This test of all possible controls drew many complaints from companies. So in 2007, the government changed the rules for SOX. The change allowed companies to limit testing to only the most important controls—those in areas of high risk. This lowered costs for many companies. It also made it easier for a company to prove it was compliant. All security controls are important. Well-written security policies highlight key controls to indicate which are most important.
The act created the Public Company Accounting Oversight Board (PCAOB). The PCAOB sets accounting and auditing standards. The Securities and Exchange Commission (SEC) is responsible for enforcing SOX. The challenge for information security is that SOX 404 sets broad IT objectives. It does not define how to comply. Rather than developing new information security and control standards, the PCAOB and SEC have endorsed using industry best practice frameworks. The following are endorsed frameworks that companies commonly use to meet SOX 404 requirements. These frameworks are widely used by external auditors as well to certify SOX compliance:
• Committee of Sponsoring Organizations (COSO)—As it relates to security policies, this organization creates rules for implementing internal controls and governance structures.
• Control Objectives for Information and related Technology (COBIT)—Created by ISACA, formerly known as the Information Systems Audit and Control Association. This framework is an internationally recognized best practice.
FYI
ISACA has a number of publications publicly available through its Web site. You can find an executive summary of COBIT 5.0 at http://www.isaca.org/COBIT/Pages/default.aspx?cid=1003566&Appeal=PR.
COBIT in many ways is “one-stop shopping” for SOX security policies and controls. The controls within COBIT are a rich range of activities: strategic planning, governance, life cycle, implementation, production support, and monitoring. The framework fits in and supports the COSO framework. The COBIT framework allows COSO to focus on the business side while COBIT focuses on the IT side. By leveraging both, you are able to bridge control requirements, technology issues, business risk, and shareholder concerns. The reason the framework is so popular among regulators, auditors, and IT risk professionals is that if you implement the COBIT framework, you are most likely SOX 404-compliant.
Family Educational Rights and Privacy Act (FERPA)
The Family Educational Rights and Privacy Act (FERPA) was put into law in 1974. This law applies to educational institutions such as college and universities. Any educational institution must protect the privacy of its student records and must provide students access to their own records. This gives students a way to correct errors and control disclosure of their records.
The Family Policy Compliance Office of the U.S. Department of Education enforces the act. The law broadly defines education records as any information related to the educational process that can uniquely identify the student. This has been widely interpreted as any student information from financial means to class lists to grades. The student records can be in any form from handwritten notes to digital files. There are exclusions such as law enforcement or campus security records. For the purpose of this discussion, the important point is that this broad set of student records (in any form) must be protected.
To be FERPA-compliant, security policies must contain the following key elements:
• Awareness—The school must post its FERPA security policies and provide awareness of them.
• Permission—Generally, schools must have recorded permission to share the student’s education records.
• Directory information—The school can make directory information (such as name, address, telephone number and date of birth) about the student publicly available but must provide the student with a chance to opt out of such public disclosure.
• Exclusions—The school can share information without permission for legitimate education evaluation reasons as well as for health and safety reasons.
Security policies must ensure records are kept when student permissions are not obtained under the exclusions. In addition, policies must ensure that opt-in and opt-out records are properly maintained for historical purposes to record student permissions.
FYI
The U.S. Department of Education provides a general and detailed FERPA publications Web site at http://www2.ed.gov/policy/gen/guid/fpco/ferpa/index.html.
In January 2013, two important changes were made to the law. First, it became easier to share records with child welfare agencies. For example, this would allow child welfare agencies to confirm that children under foster care are actively attending school. Second, the change eliminates some requirements to notify parents when school records are being released—to a court, for example.
Children’s Internet Protection Act (CIPA)
The Children’s Internet Protection Act (CIPA) was put into law in 2000. The law tells schools and libraries that receive federal funding that they must block pornographic and explicit sexual material on their computers. The law attempts to limit children’s exposure to such material.
The Federal Communications Commission (FCC) establishes the rules that schools and libraries must follow. The CIPA regulation was challenged in a lawsuit. The Supreme Court heard the lawsuit. The basis of the challenge is that restricting access to information is unconstitutional. Additionally, there were questions about whether the technology would end up blocking sites not originally intended by the law. The result of the court challenge was mixed. The court held that the CIPA law was constitutional. However, the courts do require schools and libraries to unblock sites when requested by an adult. The FCC has several publications on CIPA available at http://www.fcc.gov/cgb/consumerfacts/cipa.html.
Here are key CIPA components that your security policies must include:
• Awareness—The school or library must post its CIPA security policies and provide awareness of them.
• Internet filters—Best efforts must be made to keep Internet filters current so that only the targeted material intended by CIPA is blocked.
• Unblocking—There must be a process to allow the filter to be unblocked or disabled for adults who request access to blocked sites.
• Education—Children must be provided education on Internet safety and on cyberbullying and how to respond.
FYI
In 2012 the CIPA was changed to include requirements to educate young people about Internet safety. The changed law said, “Beginning July 1, 2012, schools’ Internet safety policies must provide for educating minors about appropriate online behavior, including interacting with other individuals on social networking Web sites and in chatrooms and cyberbullying awareness and response.”
Why Did U.S. Compliance Laws Come About?
These laws recognize the power of information. The more personal the data, the more powerful the information. Many changes in law relate to privacy. These changes range from how personal information is collected to how it is used, and what type of written notice must be given. The power comes from the impact that personal information has in our lives. It affects what type job we can get, the car we can buy, and the home we can afford. It also determines the quality of medical care we receive. The misuse and abuse of this information is equally powerful and can make our lives miserable. Identity theft is a major problem. It can take years of effort to restore a credit rating. You’ve surely heard stories of millions of credit cards stolen each year. While slow to react, the government does respond to emerging national threats and public pressure.
Many of these laws have come about to protect our personal privacy and to limit how companies can use the information they collect. On the other hand, the sharing of information across government agencies has increased. When millions of citizens’ personal data is lost or stolen, many questions are raised. It’s hard to know exactly how many breaches occur each year. It is estimated that in the United States alone, there have been more than 4,000 data breaches since 2005. This has resulted in more than 600 million records containing personal information being stolen. A host of personal information is associated with these records, including Social Security numbers, bank account information, health records, and more. Even if these numbers are wrong (and many believe they are too low), they reflect the real danger facing society. The cost to business is high, and so is the cost to individuals. As a result, a number of regulations in recent years have come about to require organizations to do what they can to prevent such breaches. These regulations hold an organization accountable when breaches occur.
Whom Do the Laws Protect?
Is an individual’s privacy the government’s sole concern? No, it is not. These laws have four major beneficiaries:
• Individuals—A number of laws focus on protecting an individual’s private information.
• Shareholders—A number of laws are designed to provide confidence in the markets. When investors feel that a company’s financials and risks are properly managed, the investors feel they can make informed judgments. This promotes a healthy economy.
• The public interest—This term reflects the idea that an organization has an obligation to the general public beyond their self-interest. Although this is a vague term, regulators often look at the impact a company has on the industry group or the economy in general.
• National security—The idea is that cyberterrorism threatens not only the company being targeted but also the country’s critical infrastructure.
To be clear: The world is not perfect, and the goals of regulations are not always achieved. In fact, sometimes regulations get in the way of doing the right thing when outdated regulation gets in the way of good security policies. Regardless of the value you place on regulations, you shouldn’t treat them as abstract concepts. Regulations do affect security policies. They limit how business can collect, store, and process information. Security policies are looked to as a way to ensure compliance with government mandates.
It’s an accepted concept that when everyone has to follow the same rules, the playing field is level. Without regulation, companies feel the pressure to take shortcuts to maintain competitive advantage. Regulations remove some of this pressure because everyone must comply. In other words, doing the “right thing” becomes not a matter of cost or advantage, but part of the business culture and the law.
Which Laws Require Proper Security Controls to Be Included in Policies?
You cannot design effective security controls without good security policies. It’s important to create and enforce policies that demonstration compliance with regulations. This is true of organizations of all types, including business and government. But there is no cookie-cutter approach—each entity will have its own way of implementing and enforcing policies.
Regardless of the information being protected, a security control needs to be designed and implemented to enforce the control. If a law requires any type of information protection, the law requires proper security controls. This includes physical security controls to protect information in physical form such as paper reports.
Which Laws Require Proper Security Controls for Handling Privacy Data?
This is a trick question. As a general rule, you should consider that all laws in some way require controls over the handling of data. They may vary, though, in their requirements and specific obligations. Well-written policies, rather than focusing on one law, will tend to satisfy regulatory requirements by fostering sound security practices across the enterprise. Additionally, always remember you have both a legal and an ethical responsibility to your customers. And you have an obligation to shareholders to protect the company. This includes protecting customers’ personal information, even when a law doesn’t explicitly call for privacy controls. As a practical matter, a breach of customer information could leave the company facing a long and costly lawsuit. Consequently, it’s simply good business to protect customers’ personal information. Security policies should reflect this thinking—for example, a need-to-know policy, which would limit access to data to just those employees who require the information to perform their jobs. This is a simple security principle that shows customers you are protecting their interest.
A good rule of thumb is whenever your organization handles personal information, you should be sure your security policies and controls protect privacy. If you are not currently obligated to do so, there’s a good chance at some point you will be, whether at a state or federal level. Over time, it’s far less expensive and easier to implement core privacy principles, such as those in Table 3-1, and then to implement specific controls to keep pace with each changing law. One can also argue it’s simply the right thing to do.
The only conflict comes when an organization wants to use the information beyond the scope of these core principles. At that point, management should determine if using the information violates current law. Another key consideration is whether the use of the data violates the trust agreement with the customer. This includes both the privacy notice given to the customer and the organization’s core values. If the law allows, and customer trust is deemed not at risk, then a determination can be made to either change the core principles or make an exception. This pushback from business to use information beyond the core principles is healthy. It results in a candid conversation with the business about current regulations and the values the organization wants to embrace. The approach results in better understanding of the law, greater awareness of core organizational values, and a stronger foundation of controls.
Aligning Security Policies and Controls with Regulations
You have reviewed six major laws at a high level and their affects on security policies and controls. Depending on your organization, you may have hundreds of laws to deal with. So how do you cope? There are many factors you must consider to ensure your security policies and controls align with regulations, such as the following:
• Inventory—Make sure you have a solid inventory of hardware, software, and information. You need know to where the information is collected, stored, and processed.
• Business requirements—Your business is ultimately accountable to regulators. Ensure the business understands the data handling requirements of each regulation. Ensure that there is an acceptable use policy for the handling of different kinds of data. For example, is the customer presented with an opt-in or opt-out check box? Even these simple choices may have regulatory implications.
• Security policies—Security policies need to reflect these business requirements. It’s equally important to establish a core set of principles, such as those in Table 3-1. These core principles allow you to educate the business and address a significant number of regulations.
• Security framework—The selection of a security framework allows you to show regulators that you are using best practices. Use widely accepted standards, procedures, and guidelines.
• Security control mapping—When you build security controls, be sure to map them to the related policy or policies. Policies also map to regulations. Security control mappings are important to demonstrate coverage of regulatory requirements. They show the importance of each security control. Ideally, you also want to map security controls to the security framework. This will provide a comprehensive end-to-end overview of security.
• Monitoring and testing—Your organization must monitor and test any security control related to regulatory compliance. You should try to monitor and test all security controls. If you cannot, prioritize the controls starting with the most important ones.
• Evidence—At some point you will be required to provide regulators with evidence. Regulators want to see a well-thought-out approach to compliance. The security policies, framework, and control mapping is a good start. The mapping demonstrates a thorough understanding and intent to comply. Your monitoring and testing efforts also provide evidence that things are working as planned.
You learned earlier in the chapter that COSO and COBIT are widely accepted frameworks. Other frameworks are equally important. You should also be familiar with the publications from the International Organization for Standardization (ISO). Another important framework is the Information Technology and Infrastructure Library (ITIL). ITIL is a set of practices and predefined procedures for managing specific IT services such as change management. You will learn about ITIL later in this chapter.
Let’s look at how these frameworks help you build security policies and controls. Make sure you understand the security requirements for each regulation and your business. Also be sure to work with your compliance and legal department. It’s important that the policies reflect current regulatory requirements. Specialists in the compliance and legal department usually keep track of changing laws. Then you can start building or updating security policies, standards, controls, and procedures. The following is one approach:
1. Document the concepts and principles you will adopt.
2. Apply them to security policies and standards.
3. Develop security controls and procedures.
The typical approach involves moving from core security principles to implementing specific controls. Figure 3-2 illustrates this point using COSO, COBIT, and ITIL. In this example, COSO provides the necessary governance structure. Although COBIT defines policies and controls requirements, you can then define your procedures using ITIL predefined libraries.
The ability to map to existing standards and frameworks is powerful. This approach leverages years of experience across industries. It also provides confidence to regulators and auditors that you are properly managing risks. Even if you fail to document a risk, there’s a strong likelihood that the layered nature of the controls will mitigate the threat. It also reduces implementation time and produces high-quality policies, procedures, and security controls.
The approach is straightforward. The ability to implement quickly is not. The challenge is not in the approach but in volume. As mentioned, you might have hundreds of regulations to follow. Consider even a small company may have hundreds of applications, while Fortune 500 companies will have thousands of applications. Multiply that by the number of users, the number of files, the number of devices, and the number of Internet connections and you begin to see the difficulties. You might have an untold number of controls. Suddenly the volume can get overwhelming. That’s why it’s important not to take shortcuts with the key considerations listed above. It’s important that a policy outline the governance and oversight requirements for maintaining those controls. You also need a rigorous process for building, inventorying, and maintaining security controls.
Industry Leading Practices and Self-Regulation
You learned how news stories and public pressure drive government regulations. They also drive many industries to more self-regulation. The hope is to demonstrate to the government and the public that these industries are aware of the problem and are taking action. An industry prefers to self-regulate for two key reasons, cost and flexibility. There’s a perception that regulations increase cost because they can be restrictive and require lots of compliance evidence to be collected. Additionally, regulations can require specific solutions to a problem. Retaining the flexibility to select from an array of solutions and apply new technology is one reason given to avoid regulations. The counterargument is that, without laws, industries won’t fully address problems.
Regardless of your viewpoint on the merits of regulation, the result is that industries create standards over time that may become best practices. The term best practices is commonly understood. However, it can be confusing when trying to understand industry standards. The term is overused and difficult to quantify. What does “best” compare with? Is a simple solution best because it costs the least? Or is a solution better because it is more reliable? Another term with more precision is leading practice, which is easier to quantify. If most members of an industry adopt a method, it’s considered to be “leading.” It might be the best solution, but that’s not always the case.
Regulated companies look to leading practices as one way to shield themselves from regulators. If regulators have confidence in a leading practice by virtue of adopting it, a company should be confident it is complying with the law. You may not always be able to apply the best solution, but it’s important to be able to tell a regulator that you do conform to industry norms.
Some Important Industry Standards
Payment Card Industry Data Security Standard (PCI DSS)
Payment Card Industry Data Security Standard (PCI DSS) is a worldwide information security standard that describes how to protect credit card information. If you accept Visa, MasterCard, or American Express, you are required to follow PCI DSS. These card companies formed the Payment Card Industry Security Standards Council to create the standard. The PCI DSS standard was released in 2006. The current version of PCI DSS is 3.0, released in 2013. The standard applies to every organization that stores, processes, or exchanges cardholder information.
The standard requires an organization to have specific PCI DSS security policies and controls in place. The organization must also have these controls validated. If you are small merchant, you can perform a Self-Assessment Questionnaire (SAQ). Large-volume merchants must obtain their validation through a Qualified Security Assessor (QSA). Failing to validate, or failing the validation, can result in fines from the credit card companies. In extreme cases of noncompliance, you may be prevented from handling credit cards. Taking credit cards away could put you out of business.
The PCI DSS is an information security framework, so it contains a lot of technical requirements. Two in particular have been a challenge for organizations to implement: network segmentation and encryption. PCI DSS strongly encourages isolating credit card systems at a network layer. For many open network designs and shared systems, this is a challenge. If you cannot segment the systems that contain cardholder data, PCI DSS requires that all systems on that segment must comply with PCI DSS. This means if you have 20 systems on a segment and one processes credit card information, all 20 systems should comply with PCI DSS standards. This could be expensive. The second major challenge is encrypting data at rest. Encrypting data in transit is common over the Internet and public networks. Encrypting data at rest, however, can be technically challenging and at times not feasible.
There are six control objectives within the PCI DSS standard. To be compliant, you need to include these control objectives in your security policies and controls. These control objectives are:
• Build and maintain a secure network—Refers to having specific firewall, system password, and other security network layer controls.
• Protect cardholder data—Specifies how cardholder data is stored and protected. Also sets rules on the encryption of the data.
• Maintain a vulnerability management program—Specifies how to maintain secure systems and applications, including the required use of antivirus software.
• Implement strong access control measures—Refers to restricting access to cardholder data on a need-to-know basis. It requires physical controls in place and individual unique IDs when accessing cardholder data.
• Regularly monitor and test networks—Requires monitoring access to cardholder. Also requires periodic penetration testing of the network.
• Maintain an information security policy—Requires that security policies reflect the PCI DSS requirements. Requires these policies are kept current and an awareness program is implemented.
Statement on Standards for Attestation Engagements No. 16 (SSAE16)
The American Institute of Certified Public Accountants (AICPA) created the Statement on Standards for Attestation Engagements No. 16 (SSAE16). It was issued in April 2010, replacing the widely accepted auditing standard referred to as SAS 70. An SSAE16 audit examines an organization’s control environment. This usually includes an audit of the information security controls. An SSAE16 allows an independent auditor (called a service auditor) to review an organization’s control environment. The service auditor then issues an independent opinion in a cover letter. The actual audit report and opinion is provided to the organization being examined.
The popularity of an independent audit comes from the use of the opinion letters. Anyone trying to buy services from a vendor should ensure the data is protected. Organizations often request an opinion letter from a vendor to help build that confidence. Vendors often promote how well they passed an SSAE16 audit as a way of selling their services.
There is a mutual benefit in having an independent audit performed. To the customer, it provides some assurance that their vendor’s control environment has been audited. And the vendor can say there’s been independent opinion that the customer’s data is protected. A key area of examination is security policies. Having well-defined policies and evidence of their effectiveness is required as part of an SSAE16 review.
technical TIP
The opinion of the auditor depends in part on the scope of the SSAE16 review. When requesting the opinion, be sure to ask for the scope of the examination. This helps you understand the context of the opinion. For example, if you are concerned with whether a vendor can recover the system in case of an outage, be sure to ask whether backup and recovery controls were in the scope of the SSAE16 review. Simply obtaining an opinion that controls are working is not enough. You need to know which controls were tested.
Does an SSAE16 truly test if controls provide adequate safeguards to protect data? That depends in part on the type of SSAE16 audit performed. There are two types of SSAE16 audits:
• Type I—This is basically a design review of the controls. The auditor’s opinion would note if the controls are designed well. The audit also looks at documented policies and procedures. The opinion states if the policies, controls, and procedures could meet the control objective stated. This doesn’t mean the controls are working. It simply says that if the controls are executed, then they should work.
• Type II—Includes everything in Type I. In addition, the controls are actually tested to see if those controls are properly installed and working effectively.
Information Technology Infrastructure Library (ITIL)
The Information Technology Infrastructure Library (ITIL) is a series of books that describe IT practices and procedures. The collection of books originally came from a British government initiative. The first version was published in 1989 as ITIL v1.0. The current version as of this writing is ITIL 2011, which was published in 2011.
ITIL has evolved over time from over 30 booklets on different topics to a unified IT service management (ITSM) approach. ITIL focuses on the entire service life cycle. It outlines goals, activities, tasks, inputs, and outputs. It is seen as outlining the best management practices for IT.
The ITL official Web site states “ITIL provides a cohesive set of best practices, drawn from the public and private sectors internationally.”5 The concept behind ITSM is to use ITIL to optimize the IT infrastructure, lower costs, and improve quality.
FYI
ITIL is not free, and it can be expensive to buy the entire library. You can purchase just the ITIL books of specific interest. The official Web site has some free material at http://www.itil-officialsite.com/home/home.asp.
ITIL has five core books called volumes. The following outlines each of the five volumes:
• Service Strategy—Relates to how to define the governance and portfolio of services. This includes aligning to the business and IT finance requirements.
• Service Design—Relates to the actual design of the service and controls. Here is where you take into account all the business and technology concerns. For example, risk management, capacity management, availability, information security, and compliance are among the elements considered.
• Service Transition—Relates to the transition of services into production. For example, validation testing, release management, and change management are among the elements considered.
• Service Operation—Relates to ongoing support of the service. For example, incident and problem management, and access management, are among the elements considered.
• Continual Service Improvement—Relates to continuous improvement of the service. For example measuring, reporting, and managing service level agreements (SLAs) are among the elements considered.
![]() CHAPTER SUMMARY
CHAPTER SUMMARY
You learned in this chapter how important it is to conform to U.S. compliance laws. The chapter examined how technology and the Internet are driving globalization. With broad use of the Internet come new threats. You also learned the importance of compliance to the economy and how it serves the public interest. The chapter examined a number of major compliance regulations. From these examples, you can see an increasing government need to regulate. Sometimes regulations result from public pressure when something goes wrong. The chapter examined these pressures and motivations of both the government and the industry. The chapter also discussed how the industry tries to self-regulate to avoid government regulation to keep costs down and retain flexibility. You also read that the country faces new threats from nation-states trying to attack the country’s critical infrastructure.
The chapter also examined how security policies, controls, and procedures need to align with regulations. You read how to create this alignment. The chapter also examined how to show evidence of compliance to a regulator. You read about the challenges to comply with regulation and industry standards. You also read about the need to align security policies to both legal requirements and the company’s core values. Finally, a key lesson in this chapter is not to chase laws by building specific security policies and controls tailored to each new regulation. Rather, you should base policies on key concepts that address a broad range of regulatory concerns such as consumer protection and privacy.
Chief information officer (CIO)
Chief information security officer (CISO)
Consumer rights
Critical infrastructure
Cyberterrorism
Data privacy
Evidence
Globalization
Information security risk assessment
Information Technology and Infrastructure Library (ITIL)
Internet filters
Nation-states
Opt-in
Opt-out
Payment Card Industry Data Security Standard (PCI DSS)
Personal privacy
Risk assessment
Security control mapping
Shareholder
Statement on Standards for Attestation Engagements No. 16 (SSAE16)
![]() CHAPTER 3 ASSESSMENT
CHAPTER 3 ASSESSMENT
1. When creating laws and regulations, the government’s sole concern is the privacy of the individual.
A. True
B. False
2. Which of the following are pressures on creating security policies?
A. Shareholder value
B. Regulations
C. Technology vulnerabilities and limitations
D. B and C only
E. All of the above
3. Which of the following laws require proper security controls for handling privacy data?
A. HIPAA
B. GLBA
C. FERPA
D. B and C Only
E. All of the above
4. Which of the following are control objectives for PCI DSS?
A. Maintain an information security policy
B. Protect cardholder data
C. Alert when credit cards are illegally used
D. A and B only
E. None of the above
5. Nation-state attacks that try to disrupt the country’s critical infrastructure are sometimes referred to as ________.
6. Health care providers are those that process and facilitate billing.
A. True
B. False
7. The law that attempts to limit children’s exposure to sexually explicit material is ________.
8. The only consideration in protecting personal customer information is legal requirements.
A. True
B. False
9. You should always write new security policies each time a new regulation is issued.
A. True
B. False
10. What should you ask for to gain confidence that a vendor’s security controls are adequate?
A. An SSAE16 Type I audit
B. An SSAE16 Type II audit
C. A list of all internal audits
D. All of the above
11. Why is it important to map regulatory requirements to policies and controls?
A. To demonstrate compliance to regulators
B. To ensure regulatory requirements are covered
C. To demonstrate the importance of a security control
D. All of the above
12. Who typically writes a report to the board of directors on the current state of information security within a company?
A. Chief risk officer
B. Chief information officer
C. Chief information security officer
D. A and B
E. B and C
F. A, B, and C
![]() ENDNOTES
ENDNOTES
1. Meltzer, Joshua, “The Internet, Cross-Border Data Flows and International Trade,” Issues in Technology Innovation, No. 22, February 2013, the Brookings Institution, http://www.brookings.edu/~/media/research/files/papers/2013/02/25%20international%20data%20flows%20meltzer/internet%20data%20and%20trade%20meltzer.pdf, p. 2, accessed March 9, 2014.
2. Globalization 101, “Advances in Information Technology,” SUNY Levin Institute, http://www.globalization101.org/advances-in-information-technology/, accessed March 20, 2014.
3. Harress, Christopher, “Obama Says Cyberterrorism Is Country’s Biggest Threat, U.S. Government Assembles “Cyber Warriors,” International Business Times, February 18, 2014, http://www.ibtimes.com/obama-says-cyberterrorism-countrys-biggest-threat-us-government-assembles-cyber-warriors-1556337, accessed March 9, 2014.
4. “Executive Order—Improving Critical Infrastructure Cybersecurity,” The White House, Office of the Press Secretary, February 12, 2013, http://www.whitehouse.gov/the-press-office/2013/02/12/executive-order-improving-critical-infrastructure-cybersecurity, accessed March 10, 2014.
5. ITIL, http://www.itil-officialsite.com/home/home.asp (accessed March 22, 2010).