|
2 |
Business Drivers for Information Security Policies |
TECHNOLOGY PLAYS A VITAL ROLE in business. Around the world, business has become dependent on technology—so much so that if it were taken away, many business operations would stop. Almost all businesses and governments use technology to support their operations, from the most basic to the most complex. Dependence on information technology has grown so rapidly over the past decades that it’s hard for people to envision their lives without it. Consider what it would be like to disconnect from technology for week. No cell calls. No GPS to find that new restaurant. No Internet. It’s not only the products people use or consume but the way they get these products. Without technology, delivery of products and services often would not be possible. Whether in the public or private sector, the threat of information being stolen or unauthorized access is a major concern. When you reduce these types of risks to information assets, you reduce risks to the business as well. Security policies let your organization set rules to reduce risks to information assets.
It is impossible to eliminate all business risks. In fact, you would not want to. Taking risks and making a return on those risks are essential to business. How you manage that risk is what makes businesses successful. A good policy can reduce the likelihood of risk occurring or reduce its impact. A business must find a way to balance a number of competing drivers. Some of these drivers include:
• Cost—Keep costs low.
• Customer satisfaction—Keep customer satisfaction high.
• Compliance—Meet regulatory obligations.
• Measurement—Be self-aware and avoid surprises.
Security policies define how to protect and handle information. These security policies should be brief and concise. They should define in simple terms how information should be handled and processed to meet business goals. Aligning security policies with business objectives makes policies easier to understand and more likely to be followed.
This chapter provides an overview of concepts that can reduce business risk. Although the term business is used, the concepts apply equally to both public and private organizations, and for-profit as well as nonprofit entities. When the term risk is used, it refers only to the risk to information assets. It is impossible to discuss all potential business drivers to reduce risk for every organization. This chapter focuses on key risk areas.
Chapter 2 Topics
This chapter covers the following topics and concepts:
• What a business driver is and why business drivers are important
• What it means to maintain compliance
• What business risk exposure is
• What business liability is
• What operational consistency is and why it is important
Chapter 2 Goals
When you complete this chapter, you will be able to:
• Describe basic business risks
• Explain the difference between business risk exposure and business liability
• Describe some techniques the business uses to reduce risk
• Explain the important issues related to operational consistency
• Describe the relationship between business risks and security policies
Why Are Business Drivers Important?
Computer systems continue to evolve and become more complex. This makes it hard for the business to understand the technology that supports it. Yet a security breach can have a significant impact on the bottom line. The following are two examples of why organizations need good security policies:
The national retailer Target Corporation, with more than 1,700 stores in the United States, suffered a major data breach during the 2013 holiday shopping season. This breach put at risk the financial information of an estimated 40 million customers. The costs incurred to companies involved in this fiasco reached upwards of $200 million.
The health care provider BlueCross BlueShield of Tennessee in 2009 suffered a theft of hard drives. It reported 57 hard drives stolen. The company had to notify 220,000 members that their personal information might have been compromised. BlueCross reported spending more than $7 million. Customers were offered free credit monitoring for two years.
Both these cases resulted from a security policy failure. In 2011, the Poneman Institute conducted a study of the cost and cause of data breaches for that year. Organizations reported that 39 percent of the data breaches were attributed to negligence. While the exact percentage may vary each year, the point is that having good policies isn’t enough. Businesses must be self-aware and measure whether those policies are being followed. Businesses cannot afford data breaches resulting from employees’ failure to follow good policies.
Organizations are increasingly concerned with how information risks are managed and reduced. Security policies are not considered solely a technology issue anymore. Organizations also expect security policies to reflect how they want information handled. An organization’s security policies, taken collectively, show its commitment to protect information. Good security policies keep the business healthy. Some of the basic concerns with implementing such a policy include:
• Cost—Cost of implementing and maintaining controls
• Impact—Impact on the ability of the business to serve the customer
• Regulation—The organization’s ability to defend its policies and practices before regulators, should the need arise
• Adoption—The degree to which employees understand and are willing to follow policies—“to make them their own,” in other words
Policies are effective only if they are enforced. Managers dislike surprises. Finding out later that security policies are too costly or that they negatively impact customers is not acceptable. To avoid this, management needs to take part in creating and implementing security policies. Even in the best of situations data can be stolen. By having good security policies, the organization is better positioned to defend its actions to the public and in the courts. For example, an e-mail security policy that warns employees that their messages may be monitored can help defend against a lawsuit for violation of privacy.
Maintaining Compliance
The term compliance refers to how well an individual or business adheres to a set of rules. Security policy compliance means adhering to security policies. It is difficult to know whether an organization complies with every security policy. To state that an organization is compliant, you must be able to validate that the requirements within security policies have been applied to security controls and information. Difficulties arise due to the sheer volume of digital information. Even a relatively small business with only a few hundred employees could have tens of thousands of files. These files travel between servers, desktops, laptops, backup media, universal serial bus (USB) drives, and more. The issue becomes even more complex in large organizations with thousands of employees and millions of files. Knowing exactly what data is captured where and how it is used in an ever-growing complex environment is difficult. Businesses are concerned with not only files that employees can access but also with files exposed to vendors and suppliers.
Compliance Requires Proper Security Controls
The key to security policy is being able to measure compliance against a set of controls. Security controls define how you protect the information. The security policies should define why you set the goal. This effectively bridges business requirements with security controls. The security policies also define what type of protection will be achieved. How you implement the security policy can vary. For example, implementing strong authentication depends on several factors. Do you understand what is meant by “strong authentication?” Are you aware of the technology choices available given your specific application? Within those choices, does your organization prefer to keep things standardized? Has the choice you made been properly approved? How do you measure that the right choices were made? How do you measure whether both the policy and the right processes were followed?
Table 2-1 provides a conceptual example of a high-level security policy and control statement. A policy must describe a clear set of actions needed to be compliant. Vague or open-ended statements create confusion. They may lead people to make incorrect choices. However, policies that are too detailed cannot be applied broadly. So some situations can arise to which no policy applies. Again, this can be confusing and lead people to wrong choices. A well-written policy should follow a few basic guidelines. It is critical that a policy strike the right balance. It must be clear and concise. It must lead to specific outcomes and embody principles that can be applied broadly. Writing good policy is an art as much as a science.
To know whether an organization is complying with security policies, you must measure the level of compliance. The level of compliance can change depending on what exactly is measured. Consider the example in Table 2-1. You could perform a simple measurement of compliance by verifying that firewall rules exist. However, simple measurements can be less accurate or misleading. For example, assume four firewalls allow the traders access to the Internet. You check each firewall and find that three contain the proper firewall rule described in Table 2-1. At first glance, a simple measurement indicates the business is 75 percent compliant with this policy. On further inspection, you discover that the fourth firewall does not follow the required rule. This firewall represents 70 percent of the traders’ Internet traffic. This new fact could mean the business is only 30 percent compliant.
TABLE 2-1 An example of security policy and control components.
| POLICY OR CONTROL | ANSWERS | ISSUE |
| Security policy | Why | Securities and Exchange Commission (SEC) under rule 17A-4 requires stock traders’ conversations with clients to be recorded and retained. In this case the purpose is to ensure a detailed record of transactions with the client. Establishing a record allows regulators to audit for compliance with disclosure rules. |
| Security policy | What | To ensure compliance, all traders should communicate with clients only through company telephones or the company’s e-mail system. |
| Security control | How | Using the firewall, stop all traffic for traders to the Internet except for Web browsing and company e-mail. |
| Security control | Measurement | All attempts by traders to use the Internet should be logged. Each trader’s log should be reviewed by a manager at least monthly to ensure compliance. |
TABLE 2-2 Control measurement benefits.
| CONTROL MEASUREMENT CONSIDERATION | BENEFIT TO THE BUSINESS |
| Determine which security controls to measure. | Defines the scope of the compliance being measured |
| Verify these controls are working. | Defines the effectiveness of the controls being measured |
| Express compliance in terms of adherence to policy, not controls. | Defines what business goals are to be achieved |
| Express compliance in terms of potential impact to the business. | Defines the impact to the business if the goals are not achieved |
| Ensure there is a way to measure compliance. | Defines how the policy will be enforced |
A more accurate measurement gives the business more confidence to understand its risks. This clarity of thought on risk often leads to a consensus on a solution. Even when no solution is available, this strong understanding of risk can help an organization prepare if an incident occurs. It is not possible to measure compliance to each individual policy. With thousand or millions of transaction daily, not every employee action can be logged. So taking measurements and reviewing logs often focus on high-risk activities, those activities that would lead to significant impact if the policy was not followed.
Table 2-2 illustrates what can be achieved with good policy compliance measurements.
Security Controls Must Include Information Security Policies
Security controls are the means of enforcing security policies that reflect the organization’s business requirements. These controls ensure the confidentiality, integrity, and availability of the information. These controls can be used to protect physical resources, including worker safety. They are also the means to measure security compliance. You should build security controls based on the security policies. If you know the security controls work, you know you are complying with security policies.
Security policies do not contain security controls. However, a security control may have to change if the related security policy changes. By treating them separately, you can change the control to meet the security policy. This is an advantage as technology evolves. For example, suppose you have six separate IDs and passwords to access six different systems. Let’s assume technology is introduced to allow all six systems to recognize one ID and password. Much of the security policy on password controls may not change: You still know to keep your password a secret and how to select a complex password. When security policies are well established and understood by employees, they are more easily enforced. When policies change too frequently, they become confusing.
A number of classifications can be applied to security controls. The three most common are:
• Physical control—As the name implies, this refers to some physical device that prevents or deters access. A locked door, a camera, an electric fence, and a security guard are all examples of physical controls.
• Administrative control—Also known as a “procedural control,” relies on a human to take some action. A few examples of a procedural control could be providing security awareness training or having a manager check an employee’s work.
• Technical control—Refers to software that creates a logical control. Passwords and antiviral software are examples of technical controls. Dedicated hardware, such as a firewall, would be considered a technical control because it contains the necessary software to create the logical control.
Security controls also follow three unique design types—preventive, detective, and corrective, as shown in Figure 2-1.

FIGURE 2-1
Three unique security control design types.
A preventive control stops incidents or breaches immediately. As the name implies, it’s designed to prevent an incident from occurring. A firewall ideally would stop a hacker from getting inside the organization’s network. This kind of control is an automated control.
An automated control has logic in software to decide what action to take. With an automated control, no human decisions are needed to prevent an incident from occurring. The human decisions occurred when designing the security control.
Detective Security Control
A detective control does not prevent incidents or breaches immediately. Just as a burglar alarm might call the police, a security control alerts an organization that an incident might have occurred. When you review a credit card statement, your review is a detective control. You review the statement for unauthorized charges. The process of reviewing the statement did not prevent the unauthorized charge from occurring. The review, however, triggers corrective action if needed.
A detective control is considered a manual control. A manual control relies on a human to decide what action to take. Still, manual controls can have automated components. For example, a system administrator could automatically receive a cell phone text when the number of invalid logon attempts reaches some threshold on a server. The administrator still needs to take some manual action.
Corrective Security Control
A corrective control does not prevent incidents or breaches immediately. A corrective security control limits the impact to the business by correcting the vulnerability. How quickly the business can restore its operations determines the effectiveness of the control.
For example, backing up files to enable data restoration after a system crash is a corrective security control. A corrective control is either automated or manual. For instance, you may automatically mirror (create exact copies of) files and then restore them in the event of hard drive failure. This is an automated control. If a human is required to decide when to restore the backup, that is a manual control.
Mitigating Security Controls
To appreciate and understand how data is protected, you must look beyond a single control. It is important to look at how preventive, detective, and corrective controls work together. For example, assume someone entered the wrong Social Security number by accidentally reversing two of the digits. There may not be a control in place to catch this mistake as it’s entered. However, later in the process, a corrective control may catch and correct it. When considering how well protected the system is, look at the process end to end. While there may be a lack of control on the front end, there may be something that stops it on the back end. That back-end control would mitigate any negative impact and so would be considered a mitigating control. Mitigating controls can be preventive, detective, or corrective.
Relationship Between Security Controls and Information Security Policy
Security policies and security controls have a mutual relationship. Security policies rely on security controls to enforce their rules. A security control is based on security policy goals. Without security controls, you could not enforce security policies. Without security policies, you could not systematically put controls in place that protect business information adequately. You rely on both to prevent a breach or restore operations after a breach. Figure 2-2 illustrates these key relationships.
It’s possible to have too many security controls and policies too complicated to follow. A security control is not effective when it cannot distinguish between good and bad behavior. Security policies are not effective when they’re too confusing to follow. If the policy is not clear, you cannot build reliable security controls. This is less of an issue if the resulting control built from the policy has been automated. In other words, if the computer prevents something or alerts you when something is wrong, then complexity is not such a problem. But when you expect a human to take an action, the complexity and volume matter. If a policy is too long, it is simply hard to understand. It also becomes a challenge to train employees.
A simple example of this human nature is origami. Most people have made paper airplanes. Usually that can be done with a simple four- to six-step process that anyone can easily learn. Now try to teach the same person to make a swan using a 30- to 40-step process. Then apply that knowledge across thousands of employees. Your likelihood of success goes way up if you teach the people to make paper airplane rather than the swan. Keep policies as simple as possible.
The most important relationship between controls and policy is the business requirement. A common error is to overlook the business context. Knowing the context helps you keep competing priorities in balance. Equally important, when an incident occurs, you can better understand the impact if you know the business context.
How can information security policies help? Well-defined security policies balance business requirements and limit behavior. The policy reflects how the business wants to manage its risks. The importance placed on such issues as customer privacy and protecting company secrets directly influences employee behavior.
Security policies must drive a culture that mitigates risk exposure. Policies, and the way they are enforced, reflect the business perception of risk. They are more than just simple business requirements that translate into security controls. Policies can reduce business risks by setting the tone at the top and promoting a risk-aware culture.
Educate Employees and Drive Security Awareness
Security is ultimately a function of people, processes, and technology working well together. A well-educated employee goes a long way toward reducing risk. Policies cannot define every risk. Unlike automated security controls, which look only for specific risks, an aware employee can better detect unusual activity. This ability to detect and deal with the unexpected makes employees extremely valuable in reducing business risk.
A good security awareness program makes employees aware of the behaviors expected of them. All security awareness programs have two enforcement components, the carrot and the stick. The carrot aims to educate the employee about the importance of security policies. You can use rewards to motivate compliance. The stick reminds the employees of the consequences of not following policy. Motivation is a powerful tool in any environment. Positive reinforcement often yields better results than negative consequences. Unfortunately, you need both components to implement a successful security policy program.
You can implement a security awareness program in many ways. Here are some generally accepted principles:
• Repetition—Most employees do not deal with risk daily, so they need to be reminded.
• Onboarding—New employees should be told of their responsibilities immediately.
• Support—Leaders should provide visible support.
• Relevance—Rules that show awareness of the business context are more likely to be followed.
• Metrics—Test your employees’ knowledge of policies.
Security awareness is about good communication. It’s not about memorizing policy word for word. You need to focus on key concepts and teach employees when to ask for help. An employee should know what to do when encountering something suspicious or unexpected. Be sure to point out resources such as intranet sites within the organization. Most important, a security awareness program should teach an employee where to go for help. New employees especially need to know they are not alone in dealing with unexpected issues.
Leaders need to provide visible support for the program. Training takes time away from employees’ regular work. Leaders need to walk the talk. They themselves need to take the training and reinforce the message with their teams. How leaders reward when policies are consistently followed or react when they are not sends a strong message. The daily message sent by leaders determines the risk culture of an organization.
A security awareness program gains credibility when the business sees a reduction of risk. Each employee plays a role in the business process. Multiple benefits come with a security awareness program that emphasizes the business risk, including:
• Value—Policies relevant to business are more likely to be followed by the business.
• Culture—Well-understood and enforced security policies promote a broad risk culture.
• Resiliency—Policies provide a basis for dealing with the unexpected.
Competence is difficult to measure. At a minimum, most programs track names of those who attended classes. However, simply taking roll is not a good way to measure competency. Many awareness programs have short quizzes to test key areas of knowledge. The challenge is that an employee may need to apply the knowledge long after the class ends. Often the best measure is noting real-world problems that occurred by not following policy. That way you can go back and continuously improve the training.
A risk-aware culture may be the critical success factor that affects the business the most. This means a culture that shares common set of values, beliefs, and knowledge about the importance of managing risks. When you develop a risk-aware culture, people want do the right thing all the time. It is second nature to follow the rules and support one another. This translates into an increased likelihood of policies being followed. When this behavior is modeled every day by everyone, it becomes the norm and defines the risk culture.
Prevent Loss of Intellectual Property
Legal-definitions.com, an online law dictionary, defines intellectual property (IP) as “any product of human intellect that is unique and un-obvious with some value in the marketplace. Intellectual property laws cover ideas, inventions, literary creations, unique names, business models, industrial processes, computer program code, and more.”1 In business, IP is a term applied broadly to any company information that is thought to bring an advantage. For instance, you need to protect secrets in order to protect your advantage over competitors. IP comes in many forms, and can be electronic or physical. Security policies should state how to protect that information regardless of format.
Protecting IP through security policies starts with human resources (HR) policies. These HR policies establish a code of conduct. They should give employees clear direction as to what the organization owns with respect to IP. The issue of IP ownership can be confusing when a new employee brings to the workplace IP acquired or created while he or she was at another firm. Employment agreements may even attempt to enforce the confidentiality of IP after an employee leaves the organization or for work performed during the employee’s spare time. These HR policies and employment agreements may or may not be enforceable, depending on current law and location. Nonetheless, when building security policies, you should take a close look at HR policy. You want to be sure there are no conflicts between HR policy and security policy.
Labeling Data and Data Classification
Once an organization clearly defines its IP, the security policies should define how to label or classify the information. There is a difference between labeling and classifying data. In both cases, a label identifies the level of protection needed. A label is typically a mark or comment placed inside the document itself; for instance, putting a “confidential” label in the footer of a document. When you classify a file in a process known as data classification, a label may or may not be applied. When data classification is applied, the sensitive file is placed in a secured location.
IP can be difficult to label or classify and even harder to inventory. IP material comes in many forms. Consider a simple document labeled as sensitive IP. Portions of the document may be cut and pasted to create new material. How much of that new material should be considered IP? Although this can be difficult, the generally accepted approach is to label what you can. Restrict access based on the label. Treat any new document containing any portion of the original IP with the same restrictions you placed on the original material.
One of the most important deliverables of security policies is the labeling and data classification approach. The approach selected will drive the cost of handling data. An employee needs to know how to handle both kinds of information—labeled and classified. Security policies instruct an employee on the proper handling depending on the business requirements. The combination of the following is a widely accepted practice to help prevent loss of IP:
• Label and classify IP data.
• Restrict access.
• Filter e-mail and other communication tools for IP data.
• Educate employees on handling IP material.
Digital assets are any digital content an organization owns or has acquired the right to use. PC Magazine defines digital assets as “Any digital material owned by an enterprise or individual including text, graphics, audio, video and animations. A digital asset is owned by an organization if it was created on the computer by its employees or if it was custom developed for and purchased by the organization. Images scanned into the computer are also a digital asset if the original work was owned by the company.”2 The term “digital assets” is often inaccurately applied to all computer-related resources. This chapter will use the strict definition.
You can protect digital assets with a good inventory. Only at the moment you identify a specific digital asset and apply a label or data classification do you know where the data is. The challenge is keeping track of the information as it is moved, changed, created, and deleted. A good inventory of digital assets allows you to design security controls where the data resides. Security policies define what an asset is. They also define what label or classification should be applied. You can see these key relationships needed to protect information in Figure 2-3.
The ability to protect information starts with well-defined security policies. The definition of digital assets is so broad it is difficult to create a complete inventory. Many organizations rely on tools that scan servers, desktops, and laptops. They try to inventory sensitive information based on patterns such as Social Security numbers (SSNs). When they see a pattern match, they can determine the level of security control to apply.
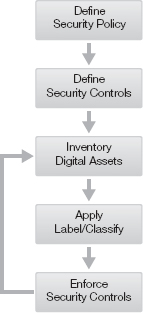
FIGURE 2-3
Key components in protecting digital assets.
To protect digital assets, you need to know where your data is. You need good tools to inventory information and networks. You will need to refresh this inventory often. Finally, you need to be able to label or classify data quickly. The sooner data is labeled or classified the sooner it is protected. The ability to inventory digital assets is a major policy implementation issue.
Once data is inventoried, it’s fairly straightforward to apply a label or classify the data. But you need to be sure the security policies clearly define the handling for each label and data class. It’s almost impossible to classify every data file. Think of the thousands of files on a single personal computer or laptop: data in the form of documents, essays, screen shots, pictures, tax returns, and much more. Much of this is considered unstructured data. The data was not predefined or as well organized as you would find in a production environment such as a bank, which will have defined processes for transactions such as taking deposits. Production systems organize data in a well-defined manner. Their processes are unambiguous and repeatable.
Applying data classification to unstructured data is a major challenge. Often data classifications are applied to where data is stored. In other words, you may not know all the files within a user’s laptop, but you know it’s a user’s laptop. Based on that knowledge, any data placed on a laptop may have a certain data classification. This is good technique when assessing data classification at a file level is not possible.
technical TIP
Whenever possible, you should put inventory tools that automatically classify data into log mode. In log mode, the security control records only what it would have done but does not take the action. Then, by reviewing the logs with management, you can assess the impact of classifying data in that way. It is not unusual for automated tools to over-classify, locking the business out of key systems. For example, let’s assume you highly restrict access to customer addresses. Potentially, the logs would show that the customer care desk could not access the data to verify customers’ identity when they call in for help. You can avoid upset users by rehearsing log use before applying preventive controls. In this example, no actual customers or business functions would be affected. The security control could then be adjusted to include access for the customer care desk. Log mode is a good way to gain business support for implementing more restrictive security controls.
It is human nature to crave privacy when it comes to our personal matters. People want their highly personal information to be secure—whether it is their medical or financial records. What many do not realize is that this information can be stored in digital files in computers anywhere in the world. Your personal information might be found with an offshore vendor in China. Regardless of where your personal data travels, securing and protecting this information is both a trust and legal obligation. This chapter focuses on United States privacy obligations. However, all developed countries throughout the world have some form of privacy laws.
The concept of protecting privacy starts with data that identifies people as unique individuals. In 2007, the Office of Management and Budget (OMB) defined personally identifiable information (PII) as:
Information which can be used to distinguish or trace an individual’s identity, such as their name, social security number, biometric records, etc. alone, or when combined with other personal or identifying information which is linked or linkable to a specific individual, such as date and place of birth, mother’s maiden name, etc.3
Security policies need to define PII data by business type and location. A bank, for example, follows different federal regulations than a local check-cashing service or medical clinic. The state in which you operate could have different requirements than a neighboring state. Widely accepted practices help businesses navigate the maze of privacy regulations. For example, most states consider the combination of a person’s name and SSN as PII. With identity theft, a major concern for both businesses and consumers, you should be careful of any combination of information that could be used to open or access an account. Depending on the business, these types of data have a good chance of falling within the PII definition.
Because organizations must follow many different privacy regulations, some organizations have established a chief privacy officer (CPO) position. This is the most senior leader responsible for managing an organization’s risks. The CPO is responsible for keeping up with privacy laws. The CPO also needs to understand how the laws impact business. Due to the nature of the work, many CPOs are lawyers. Although they are generally not technology people, they work closely with technology teams to create strong security policies.
You should consider the following guidelines when developing policy to secure PII data:
• Examine—Understand local state and federal requirements.
• Collaborate—Work closely with CPO.
• Align—Coordinate privacy policies with data classification policies.
• Educate—Conduct awareness training on handling of PII data.
• Retain—Ensure proper controls around data retention and destruction.
• Limit—Collect only the data from an individual you need to provide the service or product.
• Disclose—Fully disclose to the individual what data is being collected and how it will be used.
• Encrypt—Consider using encryption when storing or transmitting PII data.
Full Disclosure and Data Encryption
Privacy regulations involve two important principles. Full disclosure gives the consumer an understanding of what and how the data is collected and used. Data encryption provides a standard for handling consumer information.
The first principle—full disclosure—is the idea that an individual should know what information is being collected. They should also be told how that information is being used. Many people use the Internet as a quick-and-easy way to buy products and services. It seems just as quickly our e-mail inbox fills with offers from other companies. Did the online service collect and sell your information? Did the company fully disclose how that data was to be used? These are the issues that a privacy policy needs to address.
The second principle—data encryption—recognizes that even with the best efforts, data can fall into the wrong hands. This happens when data is stolen, lost, or accidentally accessed. Encrypted data can only be read when the user has the correct decryption key. For example, Roy has an encrypted hard drive containing his business ledgers. Moss finds Roy’s laptop but Roy’s financial information is still secure because the hard drive cannot be read without an encryption key. This provides an additional layer of security.
Encryption is a preventive security control. But encrypting data and managing encryption keys can be complicated and expensive. Although expensive, it’s often a lot less expensive than having to notify millions of customers that their personal information has been lost or stolen. Beyond loss of trust, companies may face legal penalties.
Encryption is considered an effective practice. Encrypting data when transmitting over the Internet is commonplace today. Encrypting data at rest on a server’s hard drive or mass storage array is far more complicated if multiple technologies are involved. Sometimes, encrypting data at rest is not technically possible.
technical TIP
Payment Card Industry Data Security Standard (PCI DSS) mandates the use of encryption for transmitting and storing credit card information. Companies and vendors have created materials to support these PCI requirements. Even if your organization does not process credit cards, this material could provide helpful guidance on encryption for protecting PII data. The Cisco PCI Solution for Healthcare Design and Implementation Guide, for example, outlines a conceptual model for protecting data including encryption components. The Guide is located at http://cisco.com/en/US/docs/solutions/Verticals/PCI_Healthcare/PCI_Healthcare_DIG.html.
Lower Risk Exposure
Well-defined and enforced security policies lead to well-defined controls. These controls in turn protect the information. So how do you achieve lower risk exposure? The concept of exposure relies on a calculation that estimates the losses to the business in the event the risk is realized. First you need a scale that allows you to measure risk against predicted business losses. Over time, you invest in people, processes, and technology to lower that risk to an acceptable level. That acceptable level is sometimes called your “risk appetite.”
What a risk appetite tells you is how much loss an organization is willing to accept in the normal course of business. These calculations are made in many different businesses and industries. Credit card companies estimate losses from fraud and invest in countermeasures. As the fraud rises, so does the spending to stop it and lower the risk exposure. You calculate the loss if these events occur and invest in programs to lower the risk exposure. For example, most banks today have changed their security policies to require much more rigorous screening of calls to the customer service desk. It’s not unusual for a customer to be asked more detailed questions than just their name, account number, and SSN. A customer could be asked current balances, last transactions, and other details in an attempt to reduce risks of fraud.
There is no easy way to calculate risk to the business in the event of a security breach. Ideally, you should calculate risk exposure in terms of total potential losses in financial terms. Given that security breaches could also result in reputation damage, it is hard to calculate that in financial terms.
Some organizations take an easier approach. They calculate risk exposure in terms of security policy compliance. This approach takes a leap of faith that if you comply with good security policies, you are adequately controlling the risk. This approach lets you lower risk exposure to the business by measuring and improving policy compliance over time.
Regardless of approach, you cannot rely exclusively on risk score. A risk score is quantitative and as such is a numerical representation of multiple factors. It does not replace risk judgment. Nor can it replace a person making a qualitative judgment through experience and common sense. Risk scores are based on factors people think they understand at a moment in time. But the risk scores may not keep up with changes in the environment, technology, or the market. The danger is in blindly following the numbers (the quantitative judgment) when common sense and experience (the qualitative judgment) say the risk is much higher. Think of the financial crisis of 2007–2008, with trillions of dollars in losses and millions put out of work. Many risks were considered low. This is an oversimplified example, but generally quantitative scores for many banks assumed that housing prices would continue to rise forever. So it didn’t matter how much you loaned, there would always be buyers for properties and homeowners would always have equity. The qualitative side, the human judgment and common sense, was missing. As a result the United States endured the worst financial crisis since the Great Depression of the 1930s.
Minimizing Liability of the Organization
A business liability emerges when an organization cannot meet its obligation or duty. Business liability is a subset of an organization’s overall risk exposure. An obligation can be either a legal or a promised commitment.
If a business fails to follow the law, it has violated its legal obligation. This liability leaves the organization open to potential fines or limits how it conducts business. In rare cases, an organization can be found to have engaged in criminal conduct. Its officers could then face criminal charges.
A business not living up to promised commitments loses the trust of customers. When a business fails to deliver the product or service it promised, the liability is lost business. Customers post complaints on the Internet, creating the potential for lawsuits and more business loss. Customer opinions are easily and widely spread today via social media, postings on product review sites, and the like. It increasingly important that businesses live up to their commitment to customer service.
The role of security policies is to reduce these liability risks. When hackers breach a company’s security, for example, you often have both trust and regulatory issues to deal with. Each event has potential liabilities. Reviewing past events to predict future situations will help you gauge overall risk exposure and specific business liabilities. Policies must define the proper handling of each of these types of events.
Separation Between Employer and Employee
It is important that an employer act quickly when a known violation occurs. The employer may not be responsible for an employee’s action. But the employer’s failure to act will create the impression that, despite written policy, the employer condones the employee’s action. This could create legal liability for the employer. It’s not enough just to have a written policy. The policy must be enforced. Employees must be held accountable and, as needed, disciplined for noncompliance. This protects the customer and the employer.
Policies make clear to an employee what acceptable behavior is. Policies also provide a degree of separation from employees who fail to follow rules. A business can point to its policies as a statement of what should have occurred. The ability to defend the organization’s position to the public and regulators is an important byproduct of security policies.
However, just having security policies will not create this separation. The business is obligated to take steps to implement and enforce the policy. Some of these reasonable steps include:
• Policy—Have clear security policies on the handling of customer information.
• Enforce—Express strong disapproval when policy is not followed.
• Respond—Quickly respond to incidents to minimize the impact to customers.
• Analyze—Understand what happened.
• Educate—Improve employee training.
These steps will minimize losses and show a commitment to customers. When challenged by the public or regulators, this will also help separate the employer’s actions from a rogue employee.
Acceptable Use Policies
Acceptable use policies (AUPs) are formal written policies describing employee behavior when using company computer and network systems. Most AUPs outline what is acceptable and unacceptable behavior. They also need to outline the disciplinary process when an employee violates policy. Because the disciplinary process could lead to termination, the policy must be clear and concise. Many companies require the employee to sign the AUP to acknowledge receipt of the rules. Both the legal and HR departments always approve final draft policies. It is important that an AUP keep up with technology changes. It must be clear when personal devices are allowed during business hours. In particular, mobile phone use is covered in many company policies today. Often, these policies also include an overview of the use of cameras. However, today few policies cover the use of the wearable devices that are becoming available. Google Glass, for example, can take a picture with a blink of an eye.
The AUP is an important tool to create a legal separation between the employer and employee. Little tolerance exists for employees who create unnecessary liability for the organization. For example, using company computers to harass or threaten others, or view obscene materials, could result in termination.
Confidentiality Agreement and Nondisclosure Agreement
A confidentiality agreement (CA), also known as a nondisclosure agreement (NDA), is a binding legal contract between two parties. It is a promise not to disclose to any third-party information covered by the agreement. The agreement needs to clearly define the information covered. This reduces problems that may arise between the two parties or any other party asked to resolve legal disputes.
These types of employment agreements are often made at the time of hire. They outline what information should not be disclosed outside the company. These agreements could bind the employee from disclosing company information after employment terminates.
The CA or NDA is often used to explore business opportunities before buying a product or service. Let’s say a company wants to hire a consultant to redesign a major computer application. Both parties would sign a CA. The company could then disclose its problems and the consultant would have more precise information to base an estimate. The CA would bind both parties even if the company decided not to hire the consultant.
Security policies typically include guidance when a CA or NDA should be required. Most security policies require such agreements to be in place before any data can be exchanged. This includes requiring such agreements to cover employees and non-employees, such as temporary or contract workers. This is especially important for non-employees who may not go through the company’s normal security awareness training.
Business Liability Insurance Policies
Business liability insurance lowers the financial loss to the business in the event of an incident. Even when a business has well-defined security policies, problems can still occur. Business liability insurance will pay for losses within the limits of the policy.
Business liability insurance can be issued to both organizations and individuals. For example, a computer engineer performing consulting services could obtain professional liability insurance. Such a policy would cover any successful claims that the engineer was negligent or made errors. The same type of coverage would apply to large companies facing claims that their product or services were negligent or in error. The provisions of the coverage need to be examined closely. For instance, coverage may be dependent on the company complying with industry norms. What does that mean? Let’s say you are maintaining a company Web site. Standards in your particular industry may dictate that you must perform annual penetration testing. Failure to perform the test or to comply with your own policies could lead to your insurance claim being denied.
An important benefit of this insurance coverage is the payment of legal fees. Even when a company is found innocent, the legal costs can be substantial. These policies do have limits, conditions, and requirements that the policyholder must meet. These policies also have exclusions. They do not protect a company that has committed illegal acts. Overall these policies are another tool to further reduce the risk.
Implementing Policies to Drive Operational Consistency
Operational consistency means ensuring that an organization’s processes are repeatable and sustainable. The business goal is to have these processes executed each time with the same consistency and quality. This reliability allows the business to continuously improve quality. Processes evolve over time and the more repeatable a process can be, the more likely it is that risks can be detected and removed.
You can implement security policies the same way. This ensures that the same consistency and quality are applied to protection of information. What is meant by “a repeatable process” or “consistency”? It means when a particular risk is found again and again, the same process is used to address it each time. This consistent execution is often referred to as operational consistency.
Forcing Repeatable Business Processes Across the Entire Organization
Operational efficiency means lower costs to the business. By applying this principle across the enterprise, greater quality results can be achieved at a lower cost. For organizations with multiple divisions, developing processes once and repeating them saves time and resources. This approach also allows the organization to develop centers of excellence. These centers are typically small teams with very deep knowledge of a subject area.
An enterprise view allows senior leaders to understand how risk affects the entire organization. Someone with an enterprise view can see past the individual part to the entire structure. Such a person can see the forest and not just the trees. A single tree or group of trees might have root rot. However, the overall health of the forest may be good. This means you have a problem, but it is localized. Conversely, individual process failures may seem insignificant, but collectively they may indicate a systemic problem.
This is particularly important when it comes to security policies. Leadership needs a high level of certainty that there is operational consistency in how information is protected. Leadership is often asked by regulators to attest to security controls. For example, the chief information officer (CIO) under the Sarbanes-Oxley (SOX) Act is required to describe IT security controls goals. Many CIOs point to their company’s enforced security policies.
Policies Are Key to Repeatable Behavior
To achieve this repeatable behavior, you must measure both consistency and quality. Additionally, you will need to measure whether the implemented policy is achieving the desired results. It is not surprising to find processes that run for years while providing no real value. A typical example might be a report that was specially designed for an executive who has since left the company. The new executive continues to receive the report. He or she may even occasionally review it out of curiosity. But the executive never leverages its content for any real purpose. This report might be highly repeatable and sustainable but does not provide value.
Security policies drive operational consistency by enforcing how information is handled the same way within business processes. Policies also force close oversight and measurement of the processes. Security policies often outline oversight requirements. They explain which measurements should be captured and how often reporting is required. The following oversight phases are typically found when trying to achieve operational consistency:
• Manage—Manage process execution and note exceptions to standard procedures.
• Measure—Measure volume, consistency, and quality.
• Review—Periodically assess to ensure desired results are achieved.
• Track—Track defects, errors, and incidents.
• Improve—Improve quality continuously by making adjustments as needed.
Differences Between Mitigating and Compensating Controls
A mitigating control limits the damage caused by not having a control in place. It assumes the absence or breakdown of a primary control. It is a control after the fact. For example, suppose someone enters an invalid account number. Either a control did not exist to prevent this, or that control did not work. Either way, as long the account number is validated before further action can be taken, there is a mitigating control in place. A mitigating control, however, may not achieve the full intent of a policy.
In contrast, a compensating control achieves the desired outcome and policy intent. It doesn’t necessarily achieve it the way the policy says to do it. But the outcome is the same. Back to the example: Suppose before the account number can be entered, a master list of accounts is checked manually. Ideally the error would be caught immediately. But the manual check is still a preventive control. If the policy required an automated validation of all account numbers at time of entry, the system would be out of compliance. However, the manual check is a compensating control, and the risk is mitigated.
Understanding mitigating and compensating controls is essential in granting exceptions. What you must figure out is how much risk is left and whether that risk is acceptable.
Policies Help Prevent Operational Deviation
Operational deviation is inevitable. It’s important the intent be clear in a policy. From clearly communicated intent comes a better understanding of the desired outcome. Intent also helps employees know better what risks the company is not willing to take. It is impossible to foresee every possible circumstance. For one thing, security policies tend to cover broad topics. Second, technology is always evolving. Good policies allow the employee to apply the intent and understanding of risk to situations not explicitly outlined.
Operational deviation from policy in itself may not be a problem when there is a solid business reason. However, as the number of exceptions grows, the policy’s credibility is potentially reduced. Security policies are put in place to reduce risk. Deviating from those policies could increase the risk and prevent meeting legal obligations.
To balance these interests, most organizations have an exception process. This is also called a waiver process. Typically you submit a waiver request to a centrally managed team that reviews and approves the deviation. The waiver process examines the business rationale and tries to determine if the exception is necessary or not. When implementing a waiver process, the following should be considered:
• Independence—Be independent of the business unit seeking approval.
• Impact—Examine the risk to the entire organization.
• Benefits—Understand the business benefits.
• Mitigation—Identify security controls outside policy.
• Approvals—Residual risk should be formally accepted by management.
Residual risk is the risk that remains after security controls have been applied. When the business cannot comply with policy, the residual risk needs to be measured and compensating controls considered. A compensating control can reduce the same risk identified by policy but in a different way from what is outlined in policy. Ideally you want to implement compensating controls that reduce the same amount of risk identified in policy. If not, at least reduce some of the risk. When you cannot implement a preventive control as required by policy, consider using a detective control. These compensating controls may be outside policy but may be able to reduce some or all of the risk. Any remaining risk would then have to be properly approved. Proper approval includes vetting residual risk with those leaders who would be held accountable in the event the risk is realized. For example, if the application could not meet security policy requirements on protecting PII data, the CPO needs to approve the exception. Ultimately, if PII data is lost or stolen because of the policy exception, the CPO may have to explain to regulators why the exception was permitted.
People manage risk every day of their lives. They choose when to go bed, when to wake up, what foods to eat, what route to drive their cars, and much more. Each decision has risk and rewards attached. This is no different in the business world. Many decisions face people daily. They often operate with incomplete information. They are faced with critical deadlines that could be more easily met by sharing information outside policy guidelines. As you gain experience, these decisions become more instinctive.
For business, it is daily processes and decisions that control risk. Policies provide guidance on how to think about risk. Policies and their related controls detail how to prevent, detect, and correct errors. This landscape of controls and processes makes risk management real for every employee. Most important, it encourages behavior that positively drives the organization’s risk culture.
![]() KEY CONCEPTS AND TERMS
KEY CONCEPTS AND TERMS
Acceptable use policies (AUPs)
Automated control
Breach
Chief privacy officer (CPO)
Compensating control
Confidentiality agreement (CA)
Corrective control
Data classification
Data encryption
Detective control
Digital assets
Full disclosure
Intellectual property (IP)
Label
Manual control
Mitigating control
Nondisclosure agreement (NDA)
Operational deviation
Personally identifiable information (PII)
Preventive control
Public record
Residual risk
Risk culture
Security awareness program
Security policy compliance
1. What is policy compliance?
A. The effort to follow an organization’s policy
B. When customers read a Web site policy statement
C. Adherence to an organization’s policy
D. Failure to follow to an organization’s policy
2. What is an automated control?
A. A control that stops behavior immediately and does not rely on human decisions
B. A control that does not stop behavior immediately and relies on human decisions
C. A control that does not stop behavior immediately but automates notification of incident
D. A control that stops behavior immediately and relies on human decisions
3. Which of the following is not a business driver?
A. Ability to acquire the newest technology
B. Cost of maintaining controls
C. Ability to legally defend
D. Customer satisfaction
4. A firewall is generally considered an example of a ________ control.
5. What is an information security policy?
A. A policy that defines acceptable behavior of a customer
B. A policy that defines what hardware to purchase
C. A policy that defines how to protect information in any form
D. A policy that defines the type of uniforms guards should wear
6. Which of the following is not a type of security control?
A. Preventative
B. Correlative
C. Detective
D. Corrective
7. Tone at the top refers to:
A. A company’s leaders making sure every employee knows the priorities
B. Senior leaders implementing and enforcing policies
C. Senior managers building trust with the public and with regulators
D. All of the above
8. Privacy regulations involve two important principles: full disclosure and data encryption.
A. True
B. False
9. What are the benefits to having a security awareness program emphasize the business risk?
A. Risk becomes more relevant to employees
B. Security policies are more likely to be followed
C. Provides employees a foundation to deal with unexpected risk
D. All of the above
10. Which of the following is not a guideline to be considered when developing policy to secure PII date?
A. Align—Coordinate privacy policies with data classification policies
B. Retain—Ensure proper controls around data retention and destruction
C. Disclose—Fully disclose to the individual what data is being collected and how it will be used
D. Resiliency—Policies provide guidelines for the unexpected
11. Information used to open or access a bank account is generally considered PII data.
A. True
B. False
12. Which of the following is not a benefit of having an acceptable use policy?
A. Outlines disciplinary action for improper behavior
B. Prevents employees from misusing the Internet
C. Reduces business liability
D. Defines proper behavior while using the Internet
13. Mitigating controls always meet the full intent of the policy.
A. True
B. False
14. Which of the following do you need to measure to achieve operational consistency?
A. Consistency
B. Quality
C. Results
D. All of the above
15. Well-defined and properly implemented security policies help the business in which of the following ways?
A. Maximize profit
B. Reduce risk
C. Produce consistent and reliable products
D. All of the above
![]() ENDNOTES
ENDNOTES
1. “Intellectual Property Law Definition.” (Legal-definitions.com, n.d.). http://www.legal-definitions.com/IP/intellectual-property-law.htm (accessed March 5, 2010).
2. “Definition of: digital asset.” (Pcmag.com, 2010). http://www.pcmag.com/encyclopedia_term/0,2542,t=digital+asset&i=41283,00.asp (accessed March 5, 2010).
3. “Safeguarding Against and Responding to the Breach of Personally Identifiable Information.” (Whitehouse.gov, Office of Management and Budget memorandum, May 22, 2007). http://www.whitehouse.gov/omb/memoranda/fy2007/m07-16.pdf (accessed March 6, 2010).