Simplified Implementation Process
There are many approaches to implementing IT security policies. The approach can vary based on any number of factors, such as organizational need, level of technical complexity, industry, culture, and maturity of change process. Assume, for example, you have an organization adding mobile solutions for the first time. This may be a major project for an organization with no prior experience in this area. It should have a detailed IT security plan that includes looking at business risks, cyberthreats, compliance requirements, policy changes, employee awareness, training, policy implementation, governance, and more. The addition of new mobile solutions could be expensive and time consuming.
Now consider an organization with years of experience at implementing mobile solutions. Also assume you wish to make a change to security policies. In many ways the process is the same. You still want to look at the policy change from the perspective of business risks, cyberthreats, compliance requirements, policy changes, employee awareness, training, policy implementation, and governance. However, the scale and effort in the second case would be smaller. Introducing change into a mature organization with extensive mobile experience significantly reduces the time needed to consider the risks and implications of a policy change. In fact, although the thought process may be the same, the experience and knowledge could mean some of these steps are less formal. In both cases, it’s good practice to think through the risks and needs consistently and document them well.
 NOTE
NOTE
Control environment is a term for the overall way in which the organization’s controls are governed and executed, including how effectively the controls are implemented, the risk culture of the organization, and management’s attitude.
FIGURE 13-1 shows a simple process flow for implementing IT security policies. As you can see by the figure, implementing a security policy is much more than writing and publishing a document. In fact, writing and publishing a policy document is a small part of a larger process. Creating an IT security policy is less about the document and more about the control environment the policy creates. A policy is a way of implementing a control, such as a way to prevent or detect a type of security breach. So simply publishing a policy in itself doesn’t prevent or detect a security breach. The policy implementation must be a series of steps that ensures the policy is put into practice. Put another way, a policy that is not adhered to is not useful. A proper implementation process educates, creates support for, and integrates the policy into the day-to-day operations. The policy must also minimize costs and impact on the business.
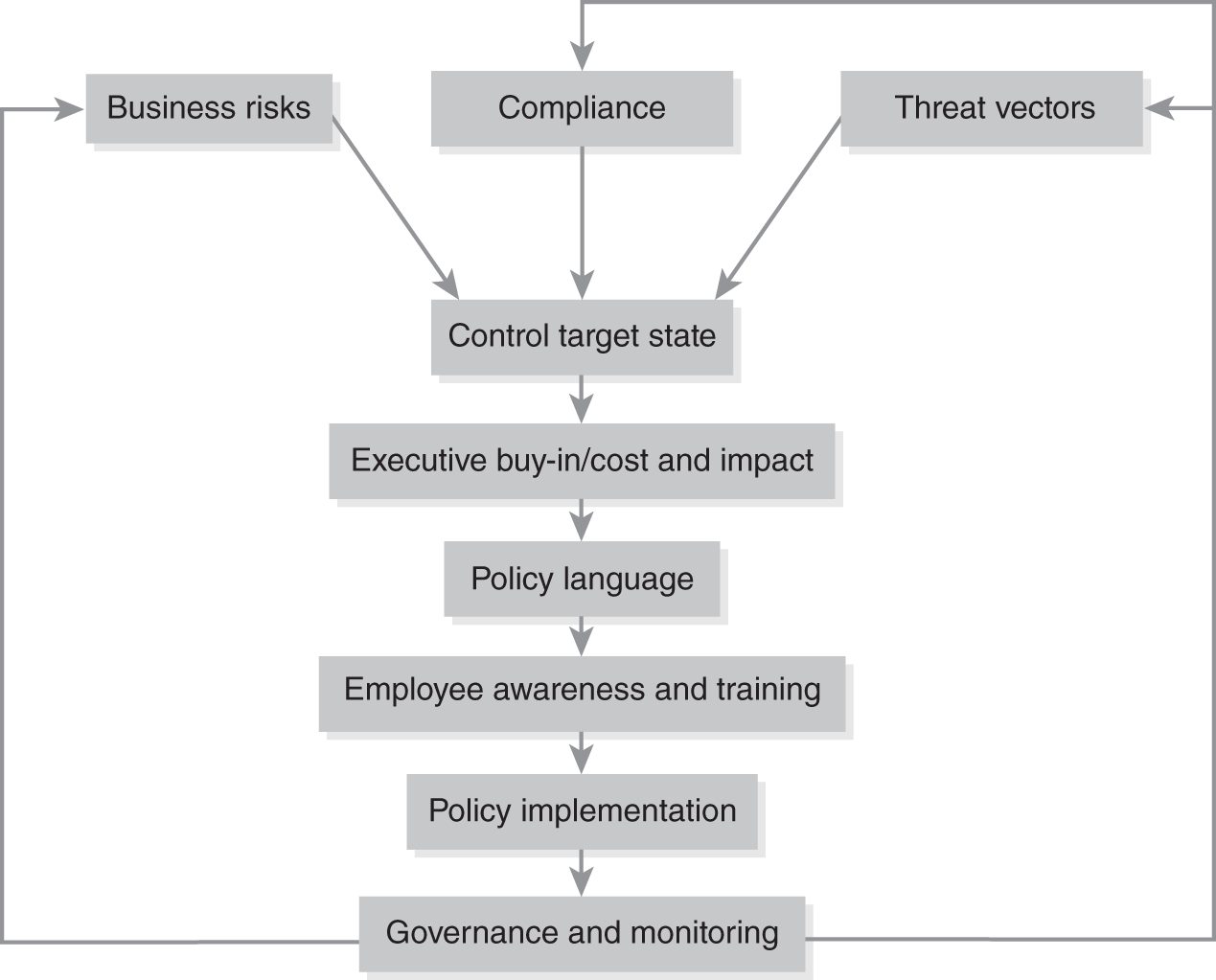
FIGURE 13-1 A process flow for implementing IT security policies.
