Maintaining Compliance
The term compliance refers to how well an individual or business adheres to a set of rules. Security policy compliance means adhering to security policies. It is difficult to know whether an organization complies with every security policy. To state that an organization is compliant, you must be able to validate that the requirements within security policies have been applied to security controls and information. Difficulties arise due to the sheer volume of digital information. Even a relatively small business with only a few hundred employees could have tens of thousands of files. These files travel between servers, desktops, laptops, backup media, universal serial bus (USB) drives, and more. The issue becomes even more complex in large organizations with thousands of employees and millions of files. Knowing exactly what data is captured where and how it is used in an ever-growing complex environment is difficult. Businesses are concerned not only with files that employees can access, but also with files exposed to vendors and suppliers. A common issue with security in many organizations is that there may be adequate policies, but there is no effective mechanism to ensure compliance with those policies. Even the best policies are almost useless without some compliance assurance.
Compliance Requires Proper Security Controls
The key to security policy is being able to measure compliance against a set of controls. Security controls define how you protect the information. The security policies should define why you set the goal. This effectively bridges business requirements with security controls. The security policies also define what type of protection will be achieved. How you implement the security policy can vary. For example, implementing strong authentication depends on several factors. Do you understand what is meant by “strong authentication”? Are you aware of the technology choices available given your specific application? Within those choices, does your organization prefer to keep things standardized? Has the choice you made been properly approved? How do you measure that the right choices were made? How do you measure whether both the policy and the right processes were followed?
TABLE 2-1 provides a conceptual example of a high-level security policy and control statement. A policy must describe a clear set of actions needed to be compliant. Vague or open-ended statements create confusion. They may lead people to make incorrect choices. However, policies that are too detailed cannot be applied broadly. So, some situations can arise to which no policy applies. Again, this can be confusing and lead people to wrong choices. A well-written policy should follow a few basic guidelines. It is critical that a policy strike the right balance. It must be clear and concise. It must lead to specific outcomes and embody principles that can be applied broadly. Writing good policy is an art as much as a science.
| POLICY OR CONTROL | ANSWERS | ISSUE |
|---|---|---|
| Security policy | Why | The Securities and Exchange Commission (SEC), under rule 17A-4, requires stock traders’ conversations with clients to be recorded and retained. In this case, the purpose is to ensure a detailed record of transactions with the client. Establishing a record allows regulators to audit for compliance with disclosure rules. |
| Security policy | What | To ensure compliance, all traders should communicate with clients only through company telephones or the company’s email system. |
| Security control | How | Using the firewall, stop all traffic for traders to the Internet except for web browsing and company email. For all security policies, the how is a critical component. |
| Security control | Measurement | All attempts by traders to use the Internet should be logged. Each trader’s log should be reviewed by a manager at least monthly to ensure compliance. Effective metrics are the clearest way to assure compliance with policies. |
 TIP
TIP
Make your security policies relevant to business needs. They stand a better chance of being followed.
To know whether an organization is complying with security policies, you must measure the level of compliance. The level of compliance can change depending on what exactly is measured. Consider the example in Table 2-1. You could perform a simple measurement of compliance by verifying that firewall rules exist; however, simple measurements can be less accurate or misleading. For example, assume four firewalls allow the traders access to the Internet. You check each firewall and find that three contain the proper firewall rule described in Table 2-1. At first glance, a simple measurement indicates the business is 75 percent compliant with this policy. On further inspection, you discover that the fourth firewall does not follow the required rule. This firewall represents 70 percent of the traders’ Internet traffic. This new fact could mean the business is only 30 percent compliant.
A more accurate measurement gives the business more confidence to understand its risks. This clarity of thought on risk often leads to a consensus on a solution. Even when no solution is available, this strong understanding of risk can help an organization prepare if an incident occurs. It is not possible to measure compliance to each individual policy. With thousand or millions of transactions daily, not every employee action can be logged. So, taking measurements and reviewing logs often focus on high-risk activities—those activities that would lead to significant impact if the policy was not followed.
 NOTE
NOTE
Employees must be aware of and formally educated on all company policies. Awareness is the first step in ensuring policies are followed.
TABLE 2-2 illustrates what can be achieved with good policy compliance measurements.
| CONTROL MEASUREMENT CONSIDERATION | BENEFIT TO THE BUSINESS |
|---|---|
| Determine which security controls to measure. | Defines the scope of the compliance being measured |
| Determine appropriate metrics. | Defines precisely what metrics will be recorded and why. Measurement is only effective if the appropriate metrics are measured. |
| Verify these controls are working. | Defines the effectiveness of the controls being measured |
| Express compliance in terms of adherence to policy, not controls. | Defines what business goals are to be achieved |
| Express compliance in terms of potential impact to the business. | Defines the impact to the business if the goals are not achieved |
| Ensure there is a way to measure compliance. | Defines how the policy will be enforced |
Security Controls Enforce Information Security Policies
Security controls are the means of enforcing security policies that reflect the organization’s business requirements. These controls ensure the confidentiality, integrity, and availability of the information. They can be used to protect physical resources, including worker safety. They are also the means to measure security compliance. You should build security controls based on the security policies. If you know the security controls work, you know you are complying with security policies.
Security policies do not contain security controls; however, a security control may have to change if the related security policy changes. By treating them separately, you can change the control to meet the security policy. This is an advantage as technology evolves. For example, suppose you have six separate IDs and passwords to access six different systems. Let’s assume technology is introduced to allow all six systems to recognize one ID and password. Much of the security policy on password controls may not change: You still know to keep your password a secret and how to select a complex password. When security policies are well established and understood by employees, they are more easily enforced. When policies change too frequently, they become confusing.
 TIP
TIP
Reducing the frequency of security policy changes makes policies easier to enforce. It’s also easier to train employees.
A number of classifications can be applied to security controls. The three most common are:
- Physical control—As the name implies, this refers to some physical device that prevents or deters access. A locked door, a camera, an electric fence, and a security guard are all examples of physical controls.
- Administrative control—Also known as a procedural control, this relies on a human to take some action. Some examples of a procedural control could be providing security awareness training or having a manager check an employee’s work.
- Technical control—This refers to software that creates a logical control. Passwords and antivirus software are examples of technical controls. Dedicated hardware, such as a firewall, would be considered a technical control because it contains the necessary software to create the logical control.
Security controls also follow three unique design types—preventive, detective, and corrective—as shown in FIGURE 2-1.
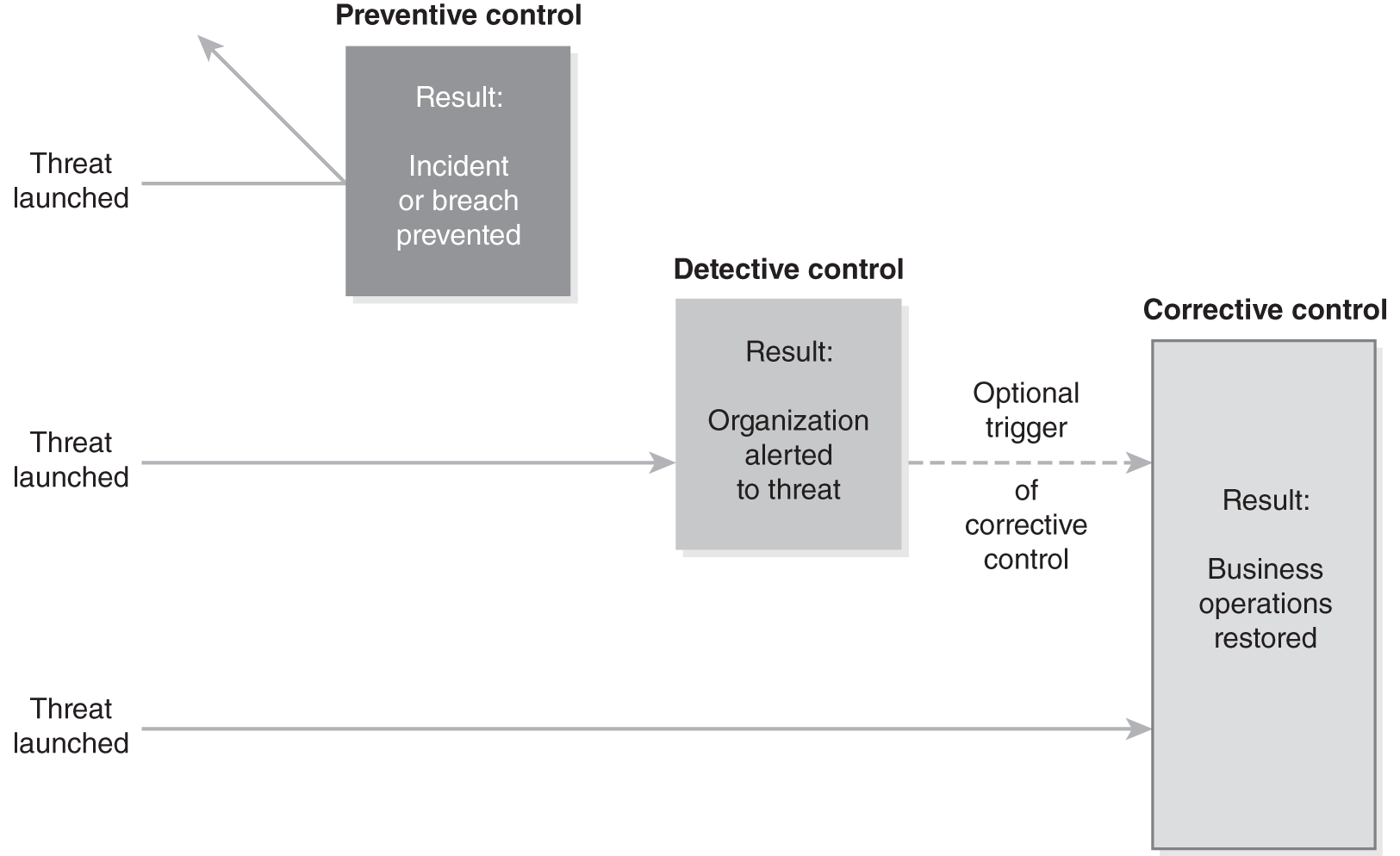
FIGURE 2-1 Three unique security control design types.
Preventive Security Controls
A preventive control stops incidents or breaches immediately. As the name implies, it’s designed to prevent an incident from occurring. A firewall ideally would stop a hacker from getting inside the organization’s network. This kind of control is an automated control.
An automated control has logic in software to decide what action to take. With an automated control, no human decisions are needed to prevent an incident from occurring. The human decisions occurred when designing the security control.
Detective Security Control
A detective control does not prevent incidents or breaches immediately. Just as a burglar alarm might call the police, a security control alerts an organization that an incident might have occurred. When you review a credit card statement, your review is a detective control. You review the statement for unauthorized charges. The process of reviewing the statement did not prevent the unauthorized charge from occurring. The review, however, triggers corrective action if needed.
Perhaps the most obvious information security detective control is an intrusion detection system or intrusion prevention system (IDS/IPS). Such systems observe network activity for anomalies that appear to be related to either an attack or a violation of specific policies/rules. Then, when anomalies are detected, they are logged, and the appropriate personnel are notified. In the case of the IPS, an additional step occurs: the anomalous traffic/activity is terminated.
Some detective controls are considered manual controls. A manual control relies on a human to decide what action to take. Still, manual controls can have automated components. For example, a system administrator could automatically receive a cell phone text when the number of invalid logon attempts reaches some threshold on a server. The administrator still needs to take some manual action. However, the aforementioned IDS/IPS are automatic controls that operate without human intervention, and then inform a human operator.
 NOTE
NOTE
If human action is required, the control is considered manual. If no human action is required, the control is automated.
Corrective Security Control
A corrective control does not prevent incidents or breaches immediately. It limits the impact to the business by correcting the vulnerability. How quickly the business can restore its operations determines the effectiveness of the control.
For example, backing up files to enable data restoration after a system crash is a corrective security control. A corrective control is either automated or manual. For instance, you may automatically mirror (create exact copies of) files and then restore them in the event of hard drive failure. This is an automated control. If a human is required to decide when to restore the backup, that is a manual control. As a general rule, automated controls are preferred when feasible because when a control is automated, it is no longer subject to human error or even forgetfulness.
Mitigating Security Controls
To appreciate and understand how data is protected, you must look beyond a single control. It is important to look at how preventive, detective, and corrective controls work together. For example, assume someone entered the wrong Social Security number by accidentally reversing two of the digits. There may not be a control in place to catch this mistake as it’s entered; however, later in the process, a corrective control may catch and correct it. When considering how well protected the system is, look at the process end to end. Although there may be a lack of control on the front end, there may be something that stops it on the back end. That back-end control would mitigate any negative impact and so would be considered a mitigating control. Mitigating controls can be preventive, detective, or corrective. Just keep in mind that anything meant to mitigate an issue is a control. Controls can be technical, they can be policy, and they can be behavioral.
Beyond having all three areas of controls, it is often advantageous to have multiple controls of the same type. For example, in preventing viruses, an organization should have policy controls in addition to technical controls. To continue this example, policies regarding opening email attachments, downloading from the Internet, plugging in external devices, and the implementation of antivirus software are four separate controls, all designed to mitigate the occurrence and impact of malware.
