In this chapter, we will discuss how you might protect our secrets using provider services. We will explore the various ways AWS will enable us to encrypt secrets. Based on this exploration, we will select an approach that has a balance between encryption and convenience, and explore that approach in Azure and Google Cloud.
The provider allows us to encrypt your secrets in multiple ways. We will explore the various ways AWS will enable us to encrypt secrets. Based on this exploration, we will select an approach that has a balance between encryption and convenience, and explore that approach in Azure and Google Cloud.
The Importance of Secrets Management
Serverless functions may need to interface with external services, which may require a username and password, an API key, or a secret key to verify the account and validate the session. For example, your application may need to process credit card transactions, and the payment processor API might require an API key unique to your account to accept API requests. If someone obtains access to this API key, that individual might start processing unauthorized credit card transactions. These illegal transactions could result in financial loss, customer complaints, or other actions degrading the business brand. Therefore, we must take extra measures to protect secrets, like an API key, to reduce risk.
Protecting Secrets
We want to avoid accidentally disclosing secrets to help prevent scenarios like those previously discussed. We should take as many measures as possible, and as practical, to protect our secrets. We should have a business process for protecting secrets and a secure software process in our application.
The business process might be the responsibility of the Information Technology, Information Security, or Cybersecurity departments or the application team if the organization is small. Whoever is responsible, having a process in place, is essential and need not be elaborate. It might be as simple as using a password manager to store all secrets and limiting who has access to it. Some organizations might store a physical sheet of paper containing the passwords in a safe, and the knowledge of the safe’s code is limited. Both situations, in essence, have the same process in different mediums, digital vs. physical. Whatever process our business adopts, we need to use it consistently and periodically reassess it.
The secure software process is likely a shared responsibility between the software development team and the team responsible for the business process. It is a shared responsibility because the software developers need to develop software that securely uses the secrets, and the business process team might be involved in establishing the process and auditing it. We will discuss the general principles for how you might develop your secure software process for protecting secrets and how you might implement them for each provider.
General Principles
Reference an environment variable.
Reference a provider service that contains the value.
Use an encrypted value in the Serverless configuration file.
An Example of Referencing an Environment Variable Containing an API Key
An Example of Defining an Environment Variable in the Serverless Configuration
You might notice defining the API key in the Serverless configuration has the actual API key value. The configuration might be captured in a repository1 and no longer kept secret. We have moved the API key from the function source code to the Serverless configuration, which diminishes the security patch or software update. We should have the Serverless configuration file reference the “apiKey” value rather than storing it.
An Example of Referencing an Environment Variable in the Serverless Configuration
The CI/CD pipeline should have limited access and have security measures (e.g., up-to-date software, host-based firewalls) in place to reduce the risk of accidentally disclosing the environment variables.
We can reference a provider service that contains the API key, which centralizes where the value is stored. We will see examples in the AWS, Azure, and Google Cloud sections. We want to use IAM permissions to limit who and what functions have access to the value.
We can use encryption in combination with the previous three approaches we have discussed. Using encryption further reduces the risk of disclosing the secret API key by the CI/CD server, the function, or the developer. In the event the environment variables are disclosed, only the encrypted version of the API key is made known. The recipient will need to decrypt the encrypted data to obtain the API key. Remember, using a stronger encryption method will better protect the secrets.2,3
The decryption algorithm should leverage well-known algorithms rather than building a custom decryption algorithm which may introduce unknown vulnerabilities. We should consider using an encryption-decryption capability included in the provider’s libraries.
We will now explore how to protect secrets using provider capabilities.
Amazon Web Services (AWS)
In AWS, we can leverage the Systems Manager (SSM) Parameter Store,4 Secrets Manager,5 Key Management Service,6 or a combination to manage our secrets. SSM Parameter Store enables us to store the values in plaintext (i.e., unencrypted) and ciphertext (i.e., encrypted) when at rest. We can reference them in our Serverless configuration or Lambda function code. Secrets Manager enables us to store values in ciphertext at rest and can reference them in our Serverless configuration or Lambda function code. KMS allows us to encrypt and decrypt data using customer master keys (CMKs), which are unique encryption keys we generate within AWS. SSM Parameter Store and Secrets Manager use KMS to encrypt and decrypt the ciphertext. These are the three services we’ll consider to manage our secrets.
Scenario: Using AWS Systems Manager (SSM) Parameter Store
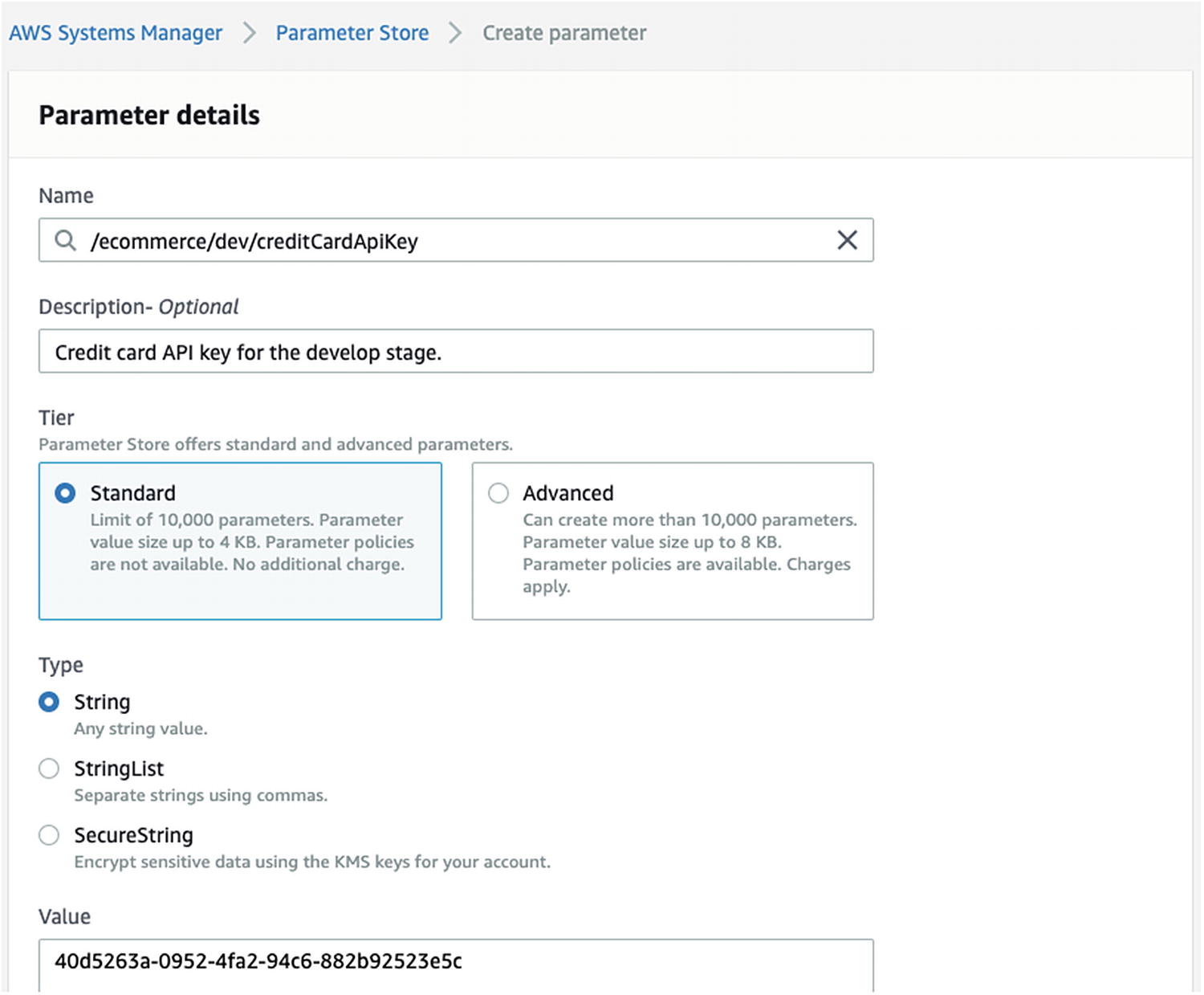
An Example of Creating an AWS SSM String (Plaintext) Parameter

An Example of Creating an AWS SSM SecureString (Ciphertext) Parameter, Part 1

An Example of Creating an AWS SSM SecureString (Ciphertext) Parameter, Part 2
The String parameter is stored as plaintext, whether at rest, in motion, or in use. The SecureString parameter is stored as ciphertext when at rest or in motion and is converted to plaintext when in use by the correct KMS key.
An Example of Referencing an AWS SSM String Parameter in the Serverless Configuration
An Example of Referencing an AWS SSM SecureString Parameter in the Serverless Configuration
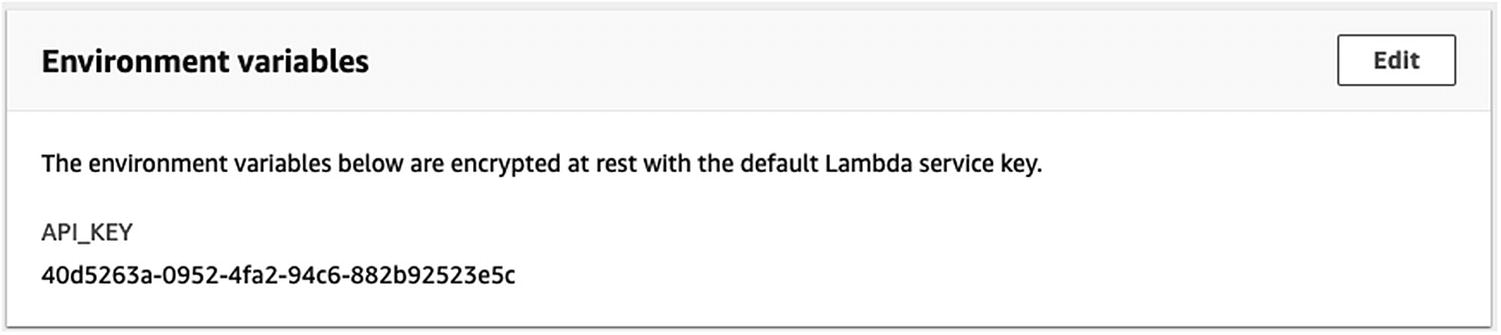
An Example of AWS Lambda Environment Variables Containing Plaintext Secrets
Updating the Serverless Configuration to Use the SSM Parameter Name
An Example of Obtaining an SSM SecureString Parameter in a Lambda Function
We no longer have to maintain the Serverless configuration file and deploy it whenever the SSM parameter is updated. The Lambda function will dynamically obtain the latest SSM parameter value every time it executes. We should consider using the SSM SecureString parameter because the data is encrypted using an AWS-managed KMS key.
Scenario: Using AWS Key Management System (KMS)
We will explore how to use Key Management System (KMS) keys to encrypt our secrets.

An Example of Creating a Customer Managed Key
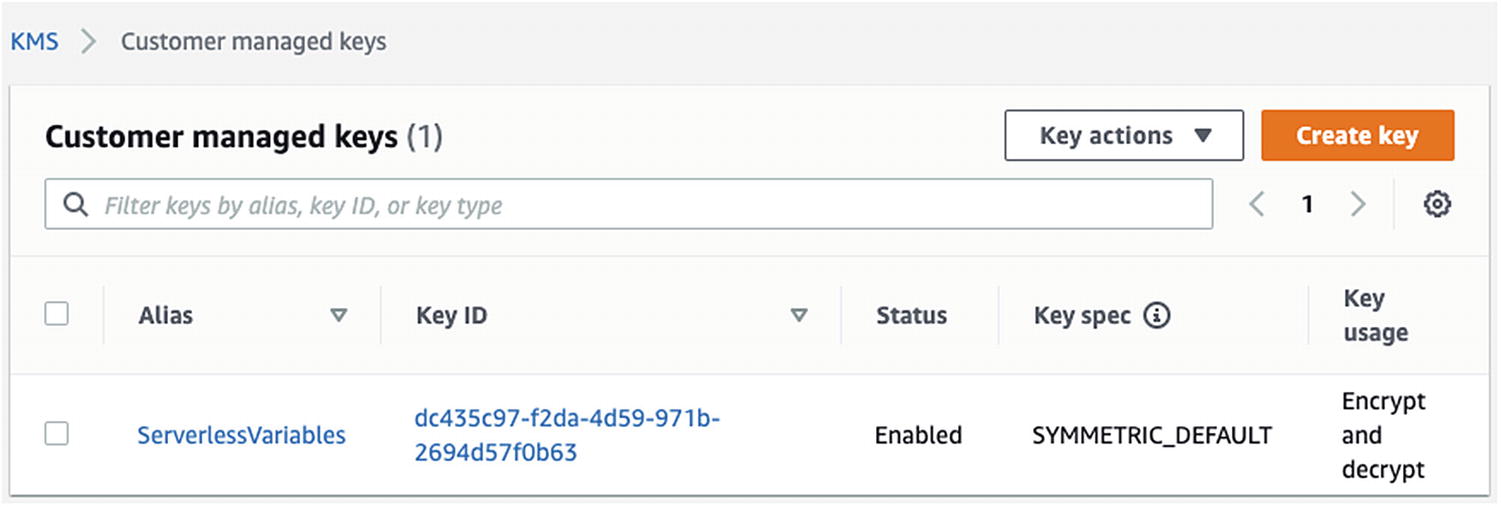
An Example of a Customer Managed Key ID
An Example of Encrypting an API Key Using the AWS CLI
An Example Output of the Encryption
Specifying the Ciphertext in the Serverless Configuration File
Decrypting the Ciphertext Environment Variable
We can integrate this KMS encryption and decryption approach with SSM by creating a parameter containing the ciphertext or integrate with Secrets Manager by creating a secret containing the ciphertext.
We might consider this approach as the most secure, yet it is arguably the most cumbersome and expensive. We first need to pay to create a CMK. We need to encrypt the API key. We need to store the encrypted API key in the Serverless configuration file and deploy it. The Lambda function needs to decrypt the API key. Whenever the CMK or API key is changed, the previous steps need to account for the change also.
Scenario: Using AWS Secrets Manager
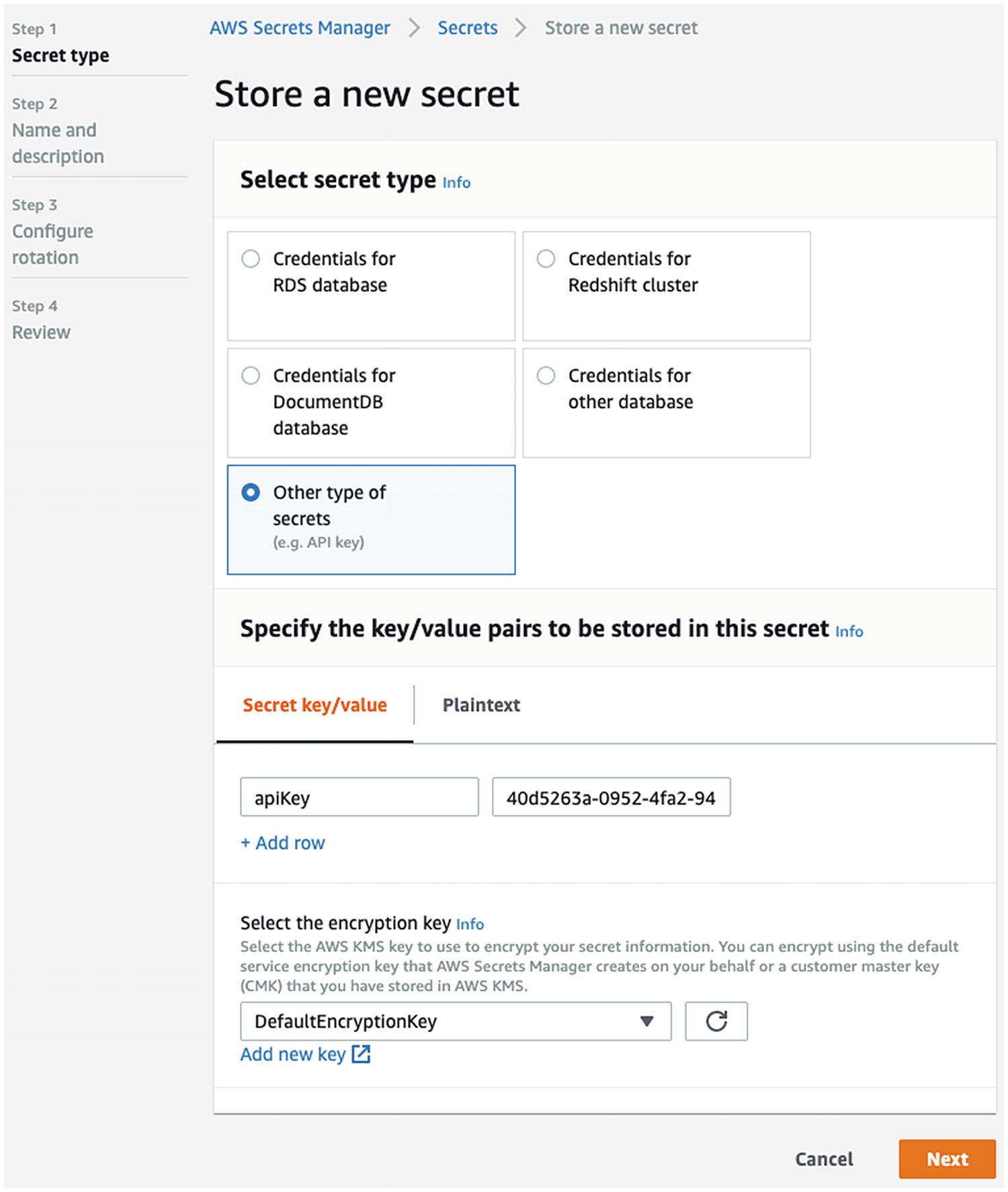
An Example of Creating an AWS Secrets Manager Secret, Part 1
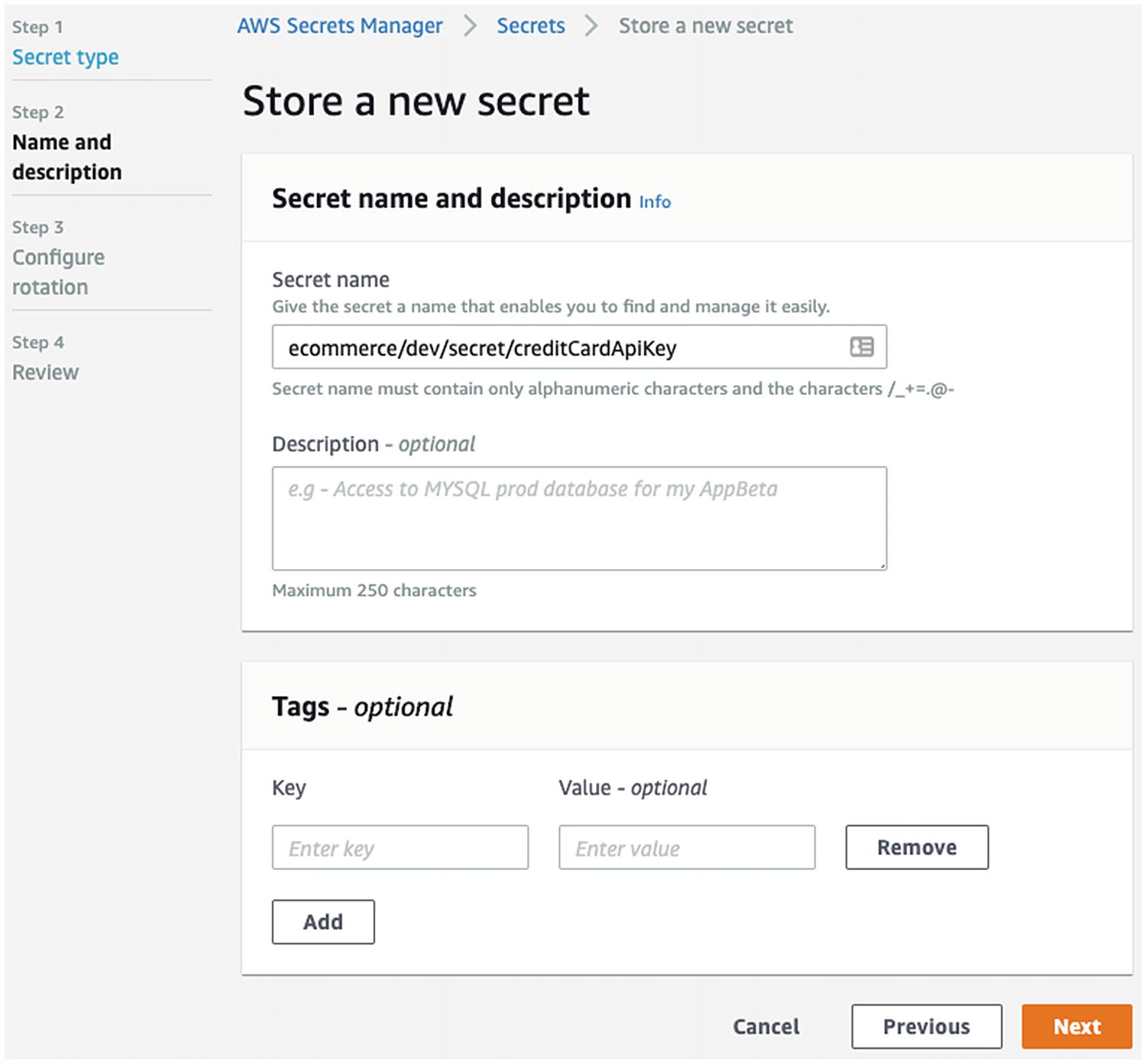
An Example of Creating an AWS Secrets Manager Secret, Part 2
The secret is stored in ciphertext when at rest and in motion and is converted to plaintext when in use by the correct KMS key.
Updating the Serverless Configuration to Use the Secrets Manager Secret Identifier
An Example of Obtaining a Secrets Manager Secret in a Lambda Function
The Lambda function will dynamically obtain the latest secret value every time it executes.
From all the scenarios, this approach has an appropriate balance between security and convenience. We still use an encryption key, but the Secrets Manager performs the encryption for us. We do not store the KMS encrypted value in the Serverless configuration. Instead, we reference the Secrets Manager secret ID. Whenever we update the secret in Secrets Manager, we do not have to update the Serverless configuration nor redeploy it. This approach has the security benefits of using KMS encryption and the convenience of referencing an SSM parameter.
Azure
In the previous section, the AWS Secrets Manager had an appropriate balance between encryption and convenience. Therefore, we will focus on using the Azure Key Vault7 feature that provides a similar capability.
The Azure Key Vault service provides secrets management, key management, certificate management, and hardware security modules. With secrets management, we specify the plaintext value, and the service encrypts the value when at rest and decrypts it when in use. Key management allows us to create encryption keys that we can use to encrypt and decrypt data. Certificate management will enable us to manage the certificates we use for network security. Hardware security modules will allow us to protect secrets using encryption hardware. We will focus on secrets management in this section.
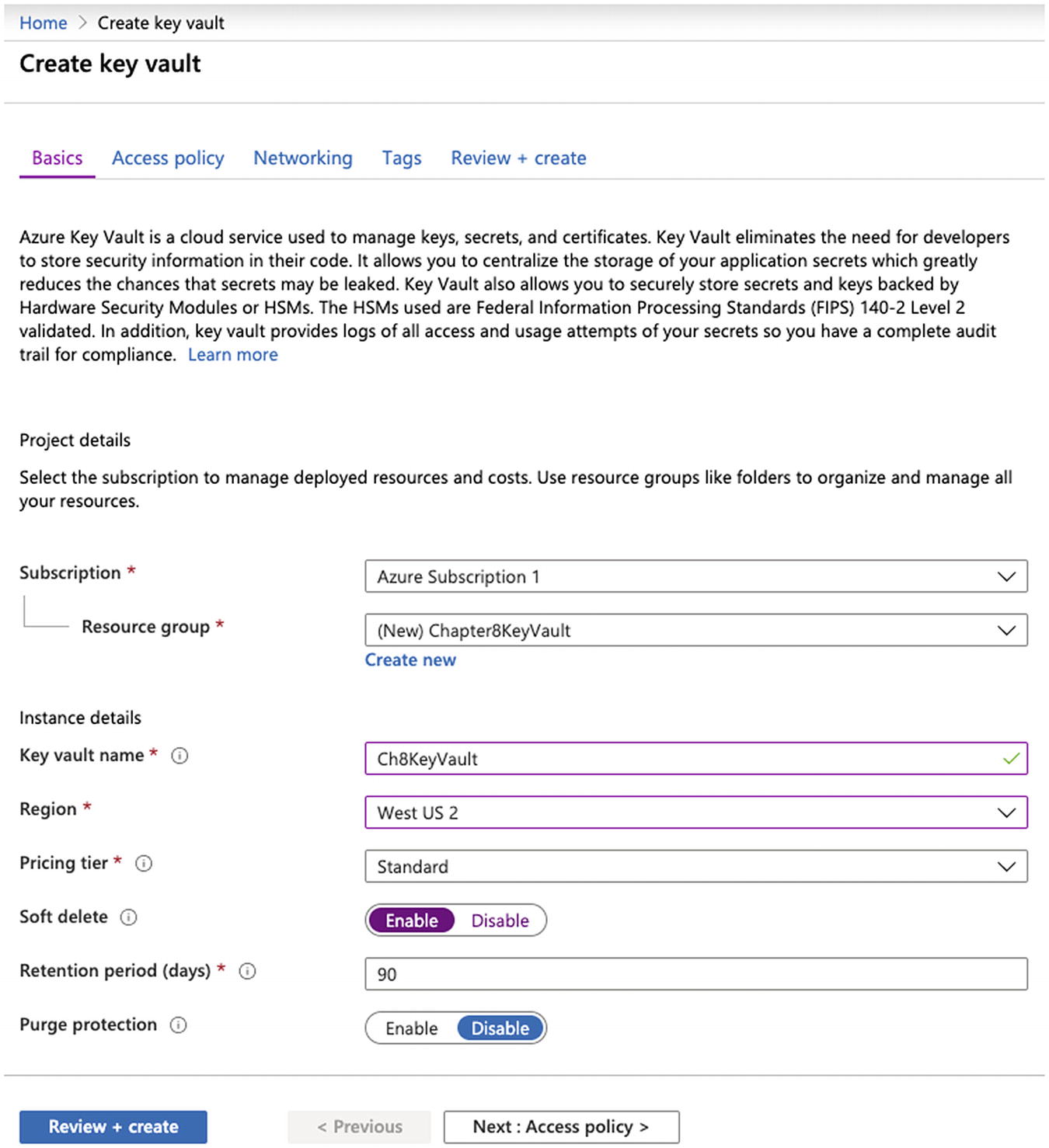
An Example of Creating a New Azure Key Vault
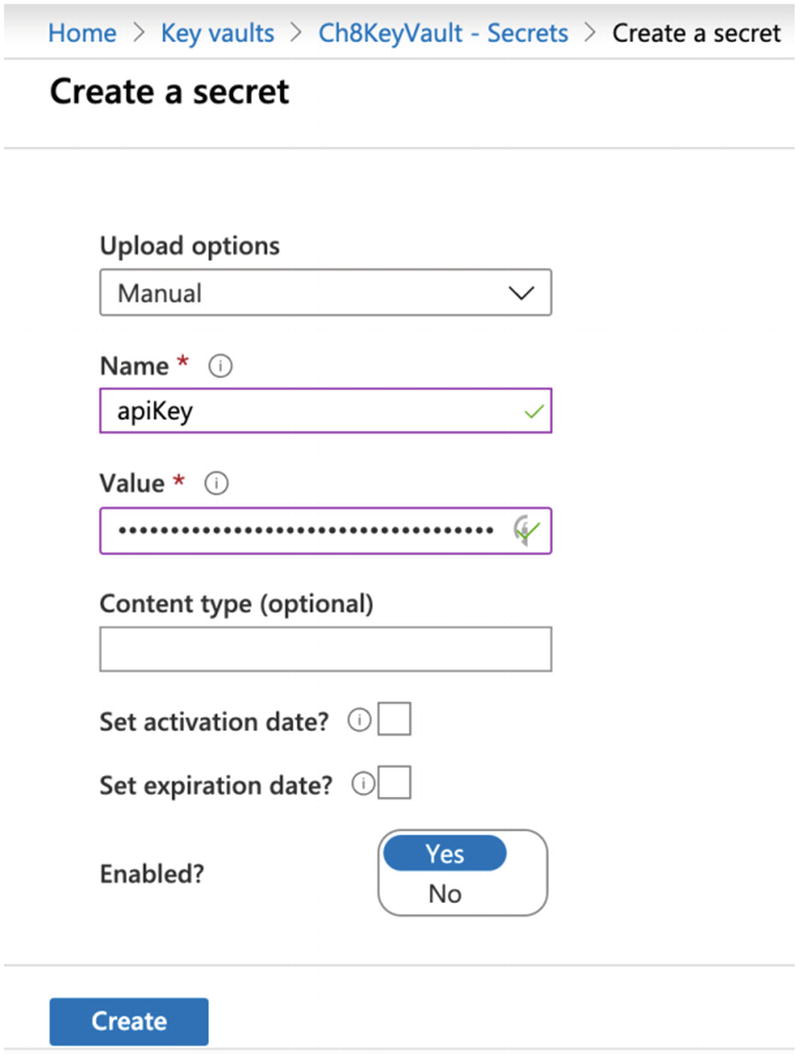
An Example of Creating a New Secret in Azure Key Vault
An Example of Defining the Secret Name in the Serverless Configuration
An Example of Accessing the Key Vault Secret in the Azure Function
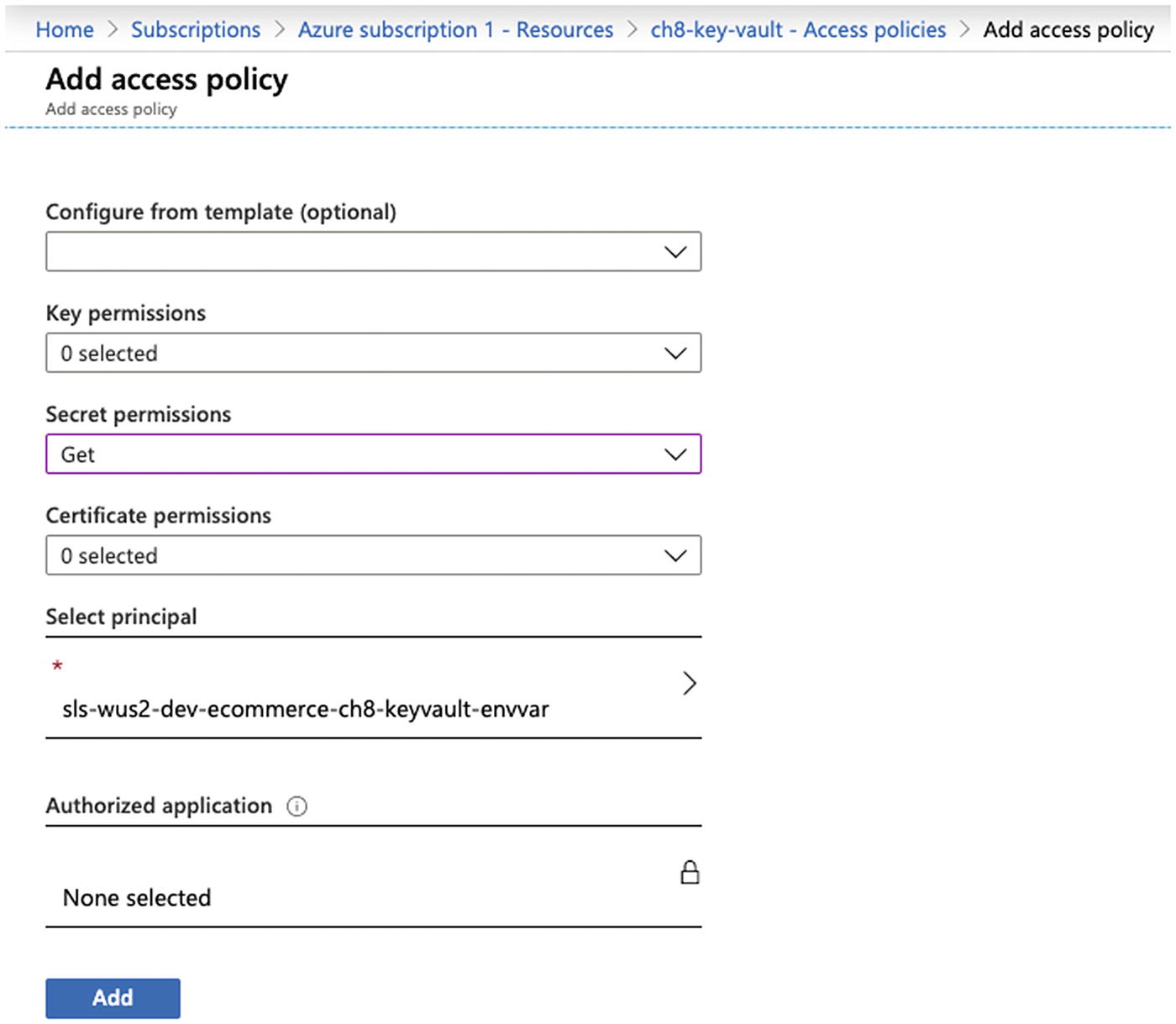
An Example of Creating an Access Policy in Azure Key Vault
The Azure Function will dynamically obtain the latest secret value every time it executes.
Google Cloud
Again, the AWS Secrets Manager had an appropriate balance between encryption and convenience. Therefore, we will focus on using the Google Cloud secrets management8 feature that provides a similar capability.
Google Cloud secrets management provides the Secret Manager,9 Berglas,10 and HashiCorp Vault11 services. With Secret Manager, we specify the plaintext value, and the service encrypts the value when at rest and decrypts when in use. With Berglas, we leverage Google Cloud KMS for encryption and decryption and store the encrypted data in Google Cloud Storage or Secret Manager. HashiCorp Vault is similar to Secret Manager and provides additional capabilities (e.g., identity-based access). We will focus on the Secret Manager in this section.

An Example of Enabling the Secret Manager API
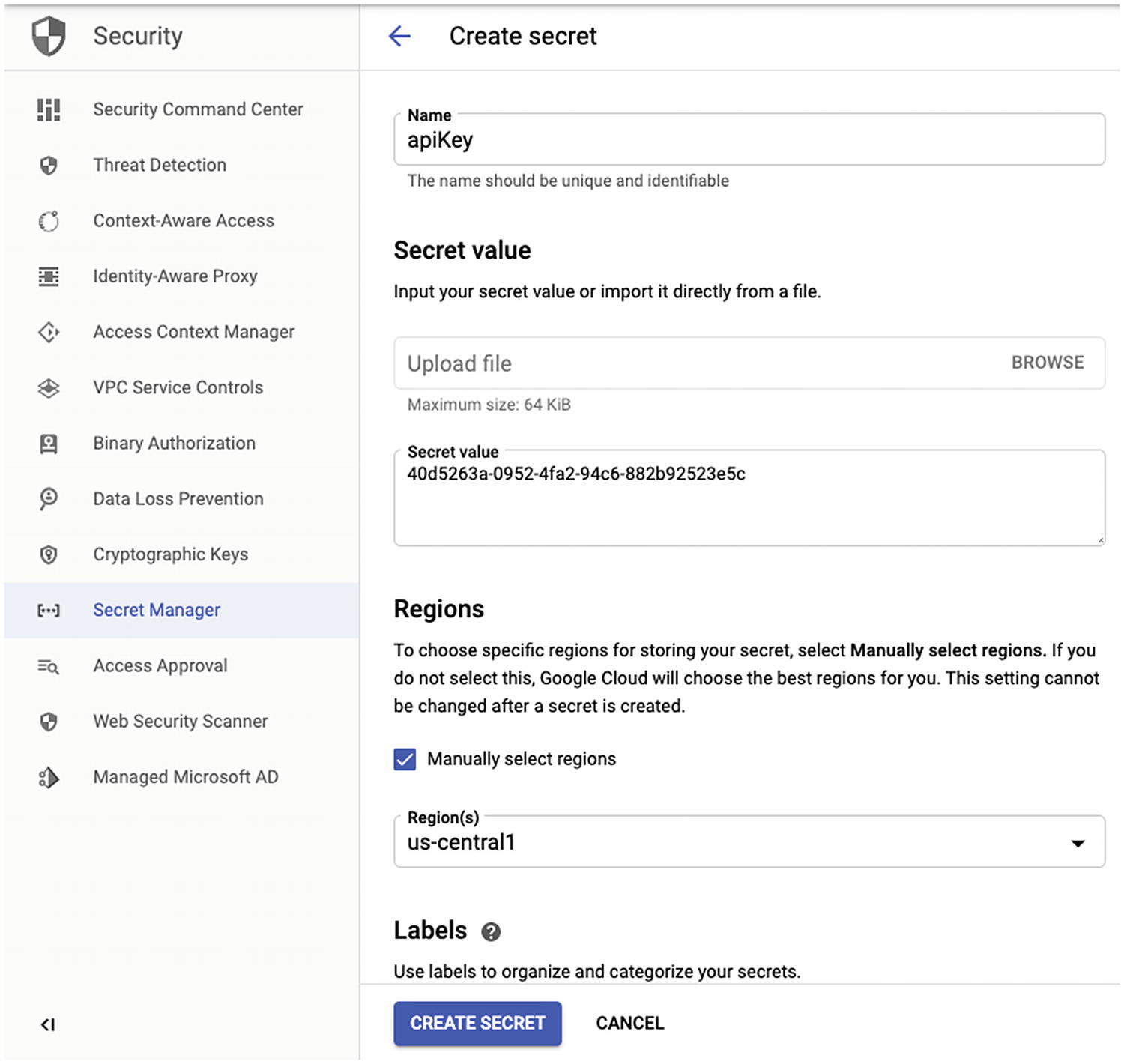
An Example of Creating a New Secret in Google Cloud Secret Manager
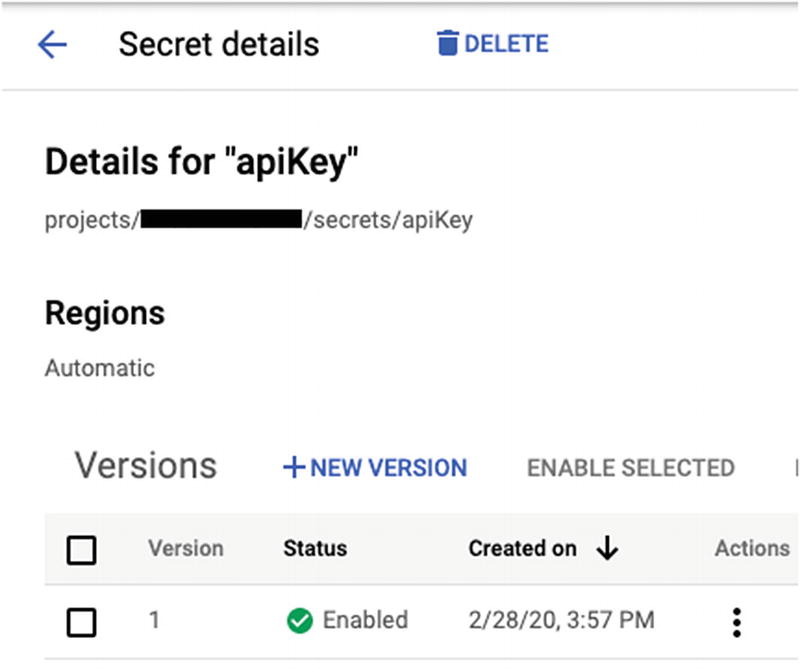
An Example of a Secret Name in Google Cloud Secret Manager
An Example of Defining the Secret Name in the Serverless Configuration
An Example of Accessing the Secret Manager Secret in the Cloud Function
After deploying the Serverless configuration, you might find the Cloud Function throws an error. The Cloud Function currently has no permissions to access the secret. We need to add an IAM policy to allow the Cloud Function’s service account to access the secret; Google Cloud automatically creates a default service account that Cloud Functions use.

An Example of Obtaining the Cloud Function Service Account
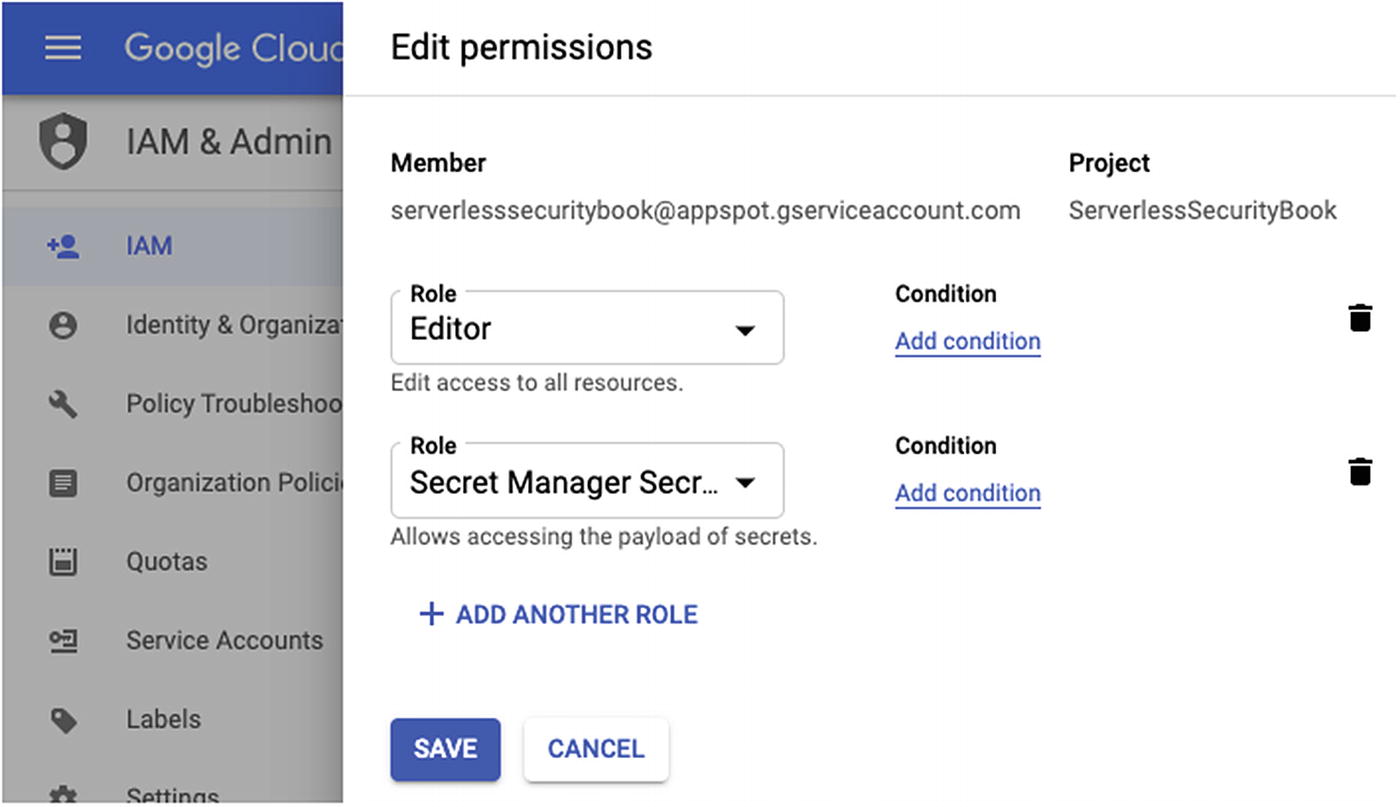
An Example of Defining IAM Permissions for Secret Manager and Service Account
The Cloud Function will dynamically obtain the latest secret value every time it executes.
Key Takeaways
We discussed how protecting secrets is essential because they might contain information that might have a business impact if accidentally disclosed. The first step to safeguarding secrets is removing that information from the function code. The next step is storing that information elsewhere and protecting it.
We found that putting the secrets in the Serverless configuration was insufficient in protecting them. We might save the Serverless configuration in a repository, but then the secret is no longer a secret. Therefore, we needed to find a different method for securely storing the secrets.
We explored three approaches in AWS to protect the secrets: SSM, KMS, and Secrets Manager. Using SSM allowed us to get the secret in multiple ways, but using the SecureString parameter and decrypting its value in the Lambda function code proved the best with this service. Using KMS allowed us to encrypt the secret, store it as an environment variable in the Serverless configuration, and decrypt it in the Lambda function code. Using Secrets Manager allowed us to securely store the secret when at rest using a CMK and decrypt it in the Lambda function. We selected the Secrets Manager approach as having the best balance between security and convenience.
We explored the Azure Key Vault secrets and Google Cloud Secret Manager because they have a comparable approach to that of the AWS Secrets Manager. We found both services allow us to securely store the secret when at rest and decrypt it in the function. We briefly discussed the other approaches Azure and Google Cloud provide.
With whatever approach we decide to use, it should provide the desired balance between security and convenience while meeting the customer and business requirements.
