Chapter 5. Trojan Horses and Worms
member of the Ready Rangers Liberation Front
I do it for the pleasure of creating something, seeing that it works, and making something that could really survive, spread, and hold its own in the wild. A virus is something that lives. In real life you can’t make a kind of animal. You can in the computer. It’s like playing God.
Back in the ’80s, a programmer named Bob Wallace started a software company based on a unique marketing scheme. Rather than force people to pay for software before using it and risk finding out later that it doesn’t quite do what they expected, Wallace gave away his software for free. Under his rules, later dubbed shareware, anyone could freely and legally copy and share his program, a word processor called PC-Write. Users who went the extra step and registered the program for $75 not only got a printed manual and technical support, but they also got a $25 commission every time someone else also registered their copy of PC-Write. Naturally, users spread copies of their registered PC-Write program wherever they could, most commonly through BBS systems around the world.
With so many people sharing copies of PC-Write, the inevitable happened. In 1986, a malicious hacker wrote a Trojan horse and disguised it as a legitimate copy of PC-Write. When unsuspecting users tried to run the bogus copy of PC-Write, the Trojan horse would format their hard disk and erase all their files.
The World of Trojan Horses
Although this doctored-up version of PC-Write was one of the most prominent of the early IBM-PC Trojan horses, Trojan horses have been around since the first computers. One of the simplest and oldest types of Trojan horses is a password-stealing program. These are especially common on shared computers used by many different people, such as those in a school computer laboratory. Such computers typically require a user to type in a user name and password, so all a hacker had to do to steal someone’s password was create a fake program that looked like the usual login screen. The fake login screen would store the information, return an error message, and then display the real login screen. The unsuspecting user would then retype his user name and password and gain access to the computer, never realizing that he’d actually fed his personal information to a password-stealing Trojan horse during that first login attempt.
Just like the ancient Greek ruse from which it derives its name, Trojan horse programs rely on trickery. Trojan horses usually run only once, but that is enough to wipe out files, steal passwords, or cause other types of damage. After the introduction of the PC-Write Trojan horse, malicious hackers started creating similar Trojan horses masquerading as games or utility programs like those commonly found on BBSs. Most would run once and wipe out all the files stored on a hard disk, thereby removing the Trojan horse itself as well and preventing it from spreading. So while Trojan horses are dangerous, they rely on the gullibility of users in order to propagate themselves.
Because Trojan horses can only work by tricking people into running them, many disguise themselves as enticements, such as naked pictures of the latest celebrities or security updates from trusted companies such as Symantec or Trend Micro. Trojan horse writers are also quick to exploit the latest current events. When someone started spreading the following hoax about a virus named AOL4Free, another individual created a Trojan horse to exploit the rumor:
Subject: E-MAIL VIRUS!!!!! -- THIS IS NOT A JOKE!!!!!!
Anyone who receives this must send it to as many people as you can. It is essential that this problem be reconciled as soon as possible.
A few hours ago, someone opened an E-mail that had the subject heading of “AOL4FREE.COM”.
Within seconds of opening it, a window appeared and began to display all his files that were being deleted. He immediately shut down his computer, but it was too late. This virus wiped him out. It ate the Anti-Virus Software that comes with the Windows ’95 Program along with F-Prot AVS. Neither was able to detect it.
Please be careful and send this to as many people as possible, so maybe this new virus can be eliminated.
DON’T OPEN E-MAIL NOTING “AOL4FREE”
VIRUS ALERT!!!
Be aware that there are letters going around that you have won free Aol until 1998....or AOL 4 free...... PLEASE DELETE...... contains a virus that will wipe out your harddrive...... after you download and it executes.....
SUBJECT AREA OF EMAIL....... CONGRATULATIONS! You are a WINNER!
SUBJECT AREA OF EMAIL.......AOL 4 Free - Get AOL For Free
SENDERS................................Matthews27 or VPVVPPVVP
WARN YOUR FRIENDS!!!!!!!!!!!!!!!!!!!!!!
The AOL4Free virus didn’t actually exist, but soon after this hoax email got into circulation, a malicious hacker went ahead and created one. This Trojan horse claimed it would give users free access to America Online. Since people had already been told that the AOL4Free virus didn’t exist, they felt safe running the “new” AOL4Free Trojan horse. This one actually would wipe out all the files on their hard disk.
Taunting the victim
Instead of destroying files, some Trojan horses simply annoy or taunt the user with pranks, such as displaying a fake dialog box that says “Now formatting hard disk” when nothing is actually happening, or playing beeping sounds through the computer’s speaker randomly.
An Arabic Trojan horse named Yusufali sneaks into a computer and monitors the title bar of the currently active window, such as a web browser. If it finds words such as XXX, sex, or teen, indicating that the user may be visiting a pornographic website, the Trojan horse displays passages from the Koran, as shown in Figure 5-1.
While Trojan horses like Yusufali don’t harm any files, they can prevent you from using your computer, to the point where you may need to reboot to get rid of their annoying distractions.
Attacking the victim’s pocketbook
In addition to destroying files, Trojan horses can also cost you money.
In 1989, someone wrote the AIDS Trojan horse, which claimed to offer information about AIDS and HIV. When users ran the program, the Trojan horse would encrypt their hard disk and display a message demanding money in exchange for a password that could be used to decrypt the hard disk and recover their files. If users didn’t send any money, the Trojan horse’s author asserted, their hard disk would remain encrypted, their data essentially held hostage until the ransom was paid.
In 2005, this type of Trojan horse reappeared when someone spread the PGPcoder Trojan, which would also encrypt files and attempt to extort users for cash in return for a password to unscramble their files. The following year in 2006, another extortion Trojan appeared called Cryzip, starting what security experts say could be the start of a new category of malware tentatively dubbed ransomware.
As more people became aware of the dangers of viruses, more computer users started using antivirus programs that could detect both viruses and Trojan horses, so malicious hackers began to search for easier targets. They found their opportunity in the vulnerable world of smart phones, which allow people to play games, retrieve email, and play music. For example, one malicious hacker started circulating a Trojan horse called Mosquito, which posed as a game that would work on any smart phone running the Symbian operating system. Once someone copied the Mosquito Trojan horse onto his or her smart phone and ran it, the Trojan horse would start sending text messages to phone numbers in the United Kingdom, Germany, the Netherlands, and Switzerland, saddling the victim with huge phone bills.
Besides messing with personal computers and smart phones, malicious hackers have also gone after Sony PlayStation Portable users. Many PlayStation users like to modify their PlayStation units so that they can run other types of programs in addition to official Sony game cartridges, a hobby known as modding. Targeting these modders, a malicious hacker wrote the first Trojan horse for Sony PlayStations in 2005, dubbed Trojan.PSPBrick. It would supposedly remove a Sony upgrade that made the device more resistant to modding. When people installed this Trojan horse, however, it would delete key files and turn the PlayStation Portable unit into an unusable piece of hardware.
The coming of the RATs (remote-access Trojans)
Up until the late ’90s, hackers wrote more viruses than Trojan horses because viruses could spread more widely and cause greater damage than a Trojan horse ever could. All that changed in 1998 when a hacker group called The Cult of the Dead Cow released Back Orifice, a new type of Trojan horse called a remote-access Trojan (RAT), that took advantage of the Internet. Like other Trojan horses, RATs could only run by tricking users, but once they were launched they could also connect to the Internet and communicate directly with the hacker who created them.
Sneaking a RAT onto a computer
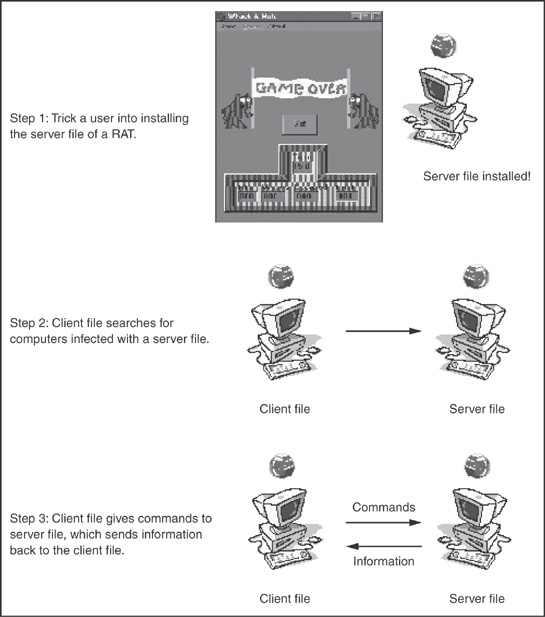
RATs consist of two separate programs: a client file and a server file. The server file infects a computer by deceiving the user into running it. The client file runs on the hacker’s computer and controls any computer infected by the RAT’s server file.
To trick victims into running the server file, RATs might masquerade as an attached news story (such as a hoax about Osama bin Laden’s capture by US military forces), as a file claiming to contain graphic images of celebrities having sex, or as just a simple game, as shown in Figure 5-2.
One problem with RAT server files is that they tend to be fairly large, as big as 1MB. An astute user might wonder why a file containing a purported news story would be so large. To avoid tipping off a potential victim due to the bulky size of a RAT’s server file, RAT hackers use two deception strategies: backdoor Trojan horses and binder programs.
Unlike a full-size RAT, a backdoor Trojan horse is usually a small file whose size allows it to masquerade as something else, such as a simple game or a news story. When the victim runs the backdoor Trojan horse, the program does nothing more than open a network port—a “backdoor”—into the infected computer. Now the hacker can send a much larger file, such as a full-featured RAT, through this open port. Once this is installed on the computer, the backdoor Trojan horse has no further use and can be ignored or deleted.
An alternative way to sneak a full-featured RAT onto a computer is to use a binder program, which combines two programs in a single file. When someone runs a “bound” file, both programs run at the same time. Hackers use binder programs to bind RATs to a legitimate program, which can turn any file into a vehicle for installing a Trojan horse. Since most programs, such as game demos or trial versions of utility programs, are already hefty in size, the added bulk of a bound RAT isn’t likely to be noticed. When a victim runs a bound file, the RAT secretly installs itself along with the legitimate program.
How RATs work
RATs work by sending information through Internet ports. When computers exchange information over the Internet, they divide their physical Internet connection into virtual ports, with each port handling a specific type of information; for example, email messages are received on one port and web pages are viewed through another. Port numbers identify the type of information received on each port so that the operating system knows where to direct it. For example, by convention, any data arriving at a computer’s port 25 should be email, and any data arriving at a computer’s port 80 should be a web page.
The first thing a RAT’s server program does after infecting a computer is to open one or more ports on its network connection in order to broadcast its presence to the RAT client program. Since a computer can theoretically use thousands of different numbered ports simultaneously, and the gory details are hidden from the casual user by the operating system, most users will never notice if a RAT opens one of the many available ports or if an open port is being used by a RAT rather than a legitimate application.
After opening a port on an infected computer’s network connection, the RAT server waits to hear from the RAT client, which runs on the malicious hacker’s computer. How does the RAT client locate instances of the RAT server? Hackers simply scan the open ports on every networked computer they can find, searching for the specific port that the RAT server opens after it installs itself. Different RATs use different ports, and a RAT hacker can thereby tell when its RAT is at work on a machine. For example, a RAT named Backage uses port 411, while another RAT named Ripper Pro uses port 2023, although hackers can configure RATs to connect to any port number.
RAT client files can only control computers infected by the corresponding server file, so a hacker would need to use the Ripper Pro’s client file to control computer infected by the Ripper Pro server file, for example. Once a hacker finds an open port used by his particular RAT, he can use the RAT client program to connect to the server and, through it, control the infected computer as if he were physically sitting at the keyboard. Anything typed on the infected computer (passwords, credit card numbers, Social Security numbers, etc.) can be seen by the hacker running the RAT client. This interaction is shown in Figure 5-3.
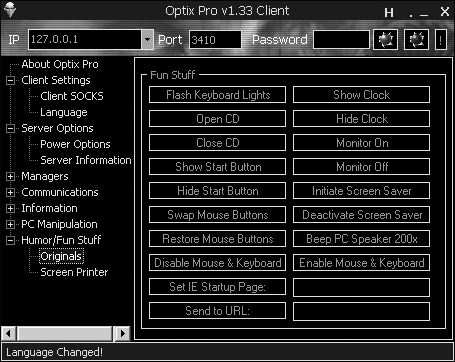
Some RATs can even capture screen images and keystrokes from an infected computer and send them (encoded as plain text) back to the hacker. Figure 5-4 shows the user interface of the Optix Pro RAT client, which provides push-button access to its many features for controlling an infected computer.
Once a RAT’s server infects your computer, anyone with the corresponding client program can access and control it. So you then have to worry not only about the hacker who originally created the Trojan horse, you also have to worry about an army of hackers who routinely probe computers on the Internet looking for infected computers with open ports and servers waiting to receive and execute instructions from RAT clients.
Worms: Self-Replicating Viruses
Most “virus outbreaks” these days are actually worms, although the media tends to use the terms “virus” and “worm” interchangeably. Technically, a virus can only spread by infecting something else, such as a program file or a Microsoft Word document, that must then be copied. When someone copies an infected program file or Word document, he or she helps the virus spread.
A worm is more dangerous than a virus because a worm is self-propagating. In its simplest form, a worm program does nothing more than copy and spread itself, but that act alone can often clog network bandwidth and slow down or crash computers, as in the case of the 1988 Morris Internet worm, which reportedly infected up to 6,000 computers. The real danger occurs when the worm delivers a malicious payload as it spreads, such as one that drops a RAT on an infected computer (so that a hacker can spy on it later) or wipes out crucial files.
Worms commonly spread through “always-on” Internet connections, such as cable or DSL modems (used by individuals), or T1 and T3 lines (used by businesses). It’s possible to spread a worm through a dial-up connection, but dial-up connections are slow, which also limits the speed that a worm can spread.
Three common ways that worms spread are through email, Internet Relay Chat (IRC) channels or instant messaging services, and Internet ports. Some worms spread themselves exclusively through one method, while others use a combination of methods to ensure they spread as quickly as possible.
Email worms
To spread by email, a worm will search for the address book of an email application such as Microsoft Outlook or Outlook Express. Once the worm finds the address book, it emails copies of itself to some or all of the stored addresses along with a deceptive subject line such as “I Love You” (used by the Love Letter worm in 2000) or “Merry Christmas” (used by the Zafi worm in 2004).
Unlike spam, which comes from an unknown source, a worm’s email comes from someone the recipient most likely knows (otherwise the email address wouldn’t have been stored in the person’s address book in the first place). People are apt to trust email from a familiar source and open the message and its attachments, not suspecting that it includes the worm.
To further entice users to run the malicious attachment, the worm may falsely describe its content as a graphics file (a celebrity having sex), as an electronic greeting card, or as a seemingly harmless text file (a technique used by the MyDoom worm). When the victim opens the attachment, the worm copies email addresses from the new victim’s address book and starts emailing itself to a new batch of people all over again.
IRC/Instant messaging worms
IRC networks are groups of chat rooms that anyone can join. To access an IRC network, a user must run an IRC program, called a client, which allows him to connect to an IRC server. After choosing an IRC network to visit, the user then chooses a specific IRC channel in which to chat.
When an IRC worm infects a computer, it starts that computer’s IRC client program, usually the popular mIRC program. Once the worm has gotten the IRC client program running on its host computer, it randomly connects to an IRC network and channel and tries to trick the chatters into accepting a file containing a copy of itself, disguising it as an MP3 file from a popular recording artist or a pornographic image of a celebrity.
The moment an unsuspecting IRC user agrees to download the file offered by the IRC worm, the worm infects that person’s computer too, and the worm can use the new victim’s IRC client to connect to yet another IRC network and start the spread of the worm once more.
Instant messaging (IM) worms work similarly to IRC worms. An IM worm loads an IM program, such as MSN Messenger, and sends out messages to everyone in a chat room offering an enticing file, which, when downloaded, infects the user’s computer and continues the cycle.
Internet worms
Both email and IRC worms use Trojan horse strategies to fool victims into infecting their computers. Internet worms can infect a computer without the user even being aware of the attack, infection, and spread. Internet worms scan vulnerable computers for specific open ports and then download themselves onto these machines, often taking advantage of flaws in the target computer’s operating system to escape undetected. Once an Internet worm has infected a computer, it then scans the Internet to find other vulnerable computers.
The Santy worm takes a slightly different approach. Instead of directly scanning targeted computers (and thereby risking revealing its presence), the Santy worm uses the Google search engine to find computers running a flawed version of a community forum program known as the PHP Bulletin Board (phpBB). It then targets those specific computers to infect. By taking this approach, the Santy worm doesn’t waste time trying to infect computers that won’t help it to spread (such as any computer running Mac OS X).
Malicious web pages
The latest technique for installing Trojan horses on unsuspecting computers involves malicious web pages. First, a Trojan horse infects a server that hosts a website. Then, every time someone visits that website, the Trojan horse infects that person’s computer.
While the thought of browsing a website that could infect your computer might be scary, the technical details prevent these types of Trojan horses from becoming more widespread. First, the Trojan horse must infect the server hosting a website. So if a hacker wanted to turn Microsoft’s website into a malicious web page, he would first have to find the servers that host Microsoft’s web pages, and then he would have to get the Trojan horse to infect that computer.
If a hacker is able to successfully infect a server, he then has to infect a user’s computer. This relies on ActiveX controls, which are miniature programs that Microsoft uses to update Windows and antivirus vendors use to run online scans of your hard disk. Since ActiveX controls only run under Windows, only Windows computers are vulnerable, and then only those Windows computers that use Internet Explorer. Since neither Firefox nor Opera allow ActiveX controls to run, Trojan horses can’t infect computers running those browsers. (ActiveX controls are more often used to install spyware on users’ computers than Trojan horses are. See Chapter 20 for more information about spyware.)
Although the threat of malicious web pages is real, the problems involved in infecting the right servers and then infecting users’ computers limit malicious web pages as a prominent way to spread Trojan horses and other malicious software.
Stopping Worms and Trojan Horses
If you connect to the Internet, chances are good that your computer will eventually be attacked by a Trojan horse or worm. To protect yourself, you need to detect and remove any Trojan horses or worms already on your computer and then prevent them from infecting your computer again.
Step one is to use an antivirus program (see Chapter 4 for a list of antivirus programs), which will look for a Trojan horse or worm’s unique fingerprint or signature and remove all traces of it from your computer. For further protection against RATs, you can also buy a dedicated anti–Trojan horse program such as:
Bo Clean | |
Ewido Security Suite | |
Tauscan | |
The Cleaner | |
TrojanHunter |
Since both RATs and worms can sneak in and out of a computer through open network ports, you also need a firewall that blocks these ports. With a firewall in place, even if a RAT or worm does infect your computer, it won’t be able to communicate and spread to the outside world through its customary ports. Unfortunately, a firewall won’t protect against any damage a worm may cause on your machine.
Many worms rely on exploiting flaws in software running on the victim’s machine, such as the operating system, so make sure you download every update issued for your operating system and applications. Of course, this won’t protect your computer from worms that know how to exploit flaws that haven’t yet been reported and patched, but it will at least limit any unnecessary exposure.
To stop the spread and infection of worms, consider using alternatives to popular software. Most RATs and worms target the Windows operating system, so nothing can make your computer more secure than switching to a non-Windows operating system such as Linux or BSD.
If you still insist on using Windows, you can foil email worms by using anything but Microsoft Outlook or Outlook Express. Instead, try Thunderbird (www.mozilla.org), Pegasus Mail (www.pmail.com), or Eudora (www.eudora.com). To stop most IRC worms, switch from mIRC to Visual IRC (www.visualirc.net), XiRCON (www.visualirc.net), or X-Chat (www.xchat.org). For further help in removing worms and Trojan horses from your computer, download a free copy of Microsoft’s Malicious Software Removal Tool (www.microsoft.com/security/malwareremove/default.mspx).
The keys to stopping Trojan horses and worms are to prevent their initial access to your computer (by using a firewall to block the ports that they use), to detect and remove any existing Trojan horses and worms (using antivirus and Trojan horse cleaning programs), and to stop using the programs most commonly exploited to spread them (Windows, Outlook, mIRC, etc.). Your computer can still become a target of Trojan horses and worms no matter what defenses you install, but at least there will be less of a chance that your computer will suffer any damage or contribute to the proliferation of these threats.
Tracking the Threats
To stay up to date on the latest security threats, visit CERT (www.cert.org/advisories), Virus List (www.viruslist.com), Security Focus (www.securityfocus.com), SANS (SysAdmin, Audit, Network, Security) Institute (www.sans.org), or Symantec (http://securityresponse.symantec.com).
Ultimately, knowledge and understanding of how Trojan horses and worms spread will be more useful in protecting your computer than all the defensive programs combined. If you don’t exercise a little common sense when dealing with suspicious threats, all the firewalls and anti–Trojan horse programs in the world won’t be enough to protect your computer.