Chapter 7. Where the Hackers Are
Hackers are people and, like most people, hackers paradoxically embrace their individuality while immersing themselves in their collective identity as rebels, free thinkers, mischief makers, and technology wizards. Despite appearances to the contrary, people do not become hackers because of how they look, what they wear, or how they speak. People become hackers by virtue of how they think and what they do.
In the world of hacking, there are “good” hackers (called white hat hackers) and there are “bad” hackers (called black hat hackers). In between are the so-called gray hat hackers, who cross the border between good and bad depending on what’s convenient for them at the time (like most people in the world).
Even the definition of hacker remains controversial. Some people lump both good and bad hackers together, but others define hacker as someone who’s simply curious, and use the term cracker for someone who’s deliberately malicious.
Whatever you call them, hackers are people, and like any group of people (Americans, police officers, teachers, accountants, Christians), some will be good and some will be bad. But unlike most other groups, hackers often rely exclusively on technology, in the form of computers and the Internet, to communicate with each other.
Finding a hacker on the Internet is fairly easy if you know where to look, just as you can find a drug dealer or a policeman if you know where to look in a city (depending on the city, the policeman might be the drug dealer).
Hacker Websites
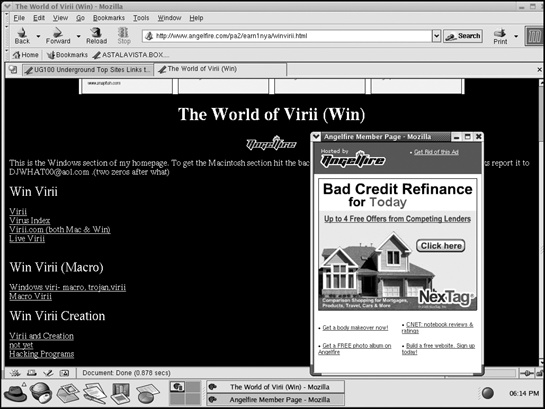
There are two kinds of hacker websites: those run by hackers and those run by reformed hackers who have decided that it’s more profitable to become security professionals. Initially, many hackers created websites using free web hosting services such as Tripod (www.tripod.lycos.com), Geocities (http://geocities.yahoo.com), and AngelFire (http://angelfire.lycos.com). Such websites are often short-lived, as hackers grow tired of updating them. Besides, few people are interested in visiting personal websites that bombard visitors with advertisements, as shown in Figure 7-1.
On rare occasions, an ambitious hacker may actually spend the time and money to create a website with a descriptive domain address. Like their free web hosting counterparts, these hacker websites rarely last long because anything considered too controversial (such as live computer viruses and software patches designed to circumvent Microsoft Windows’ product activation feature) can quickly get the website operator in trouble with the authorities, who will shut it down. It’s said that when hackers started distributing a program that disabled Windows XP from running its product activation feature, for example, Microsoft quickly shut down any websites that offered it.
Hacker websites for fun and profit
Although individual hackers rarely set up websites anymore, groups of hackers often do so to provide a platform for their views and a place where they can release their hacker tools or make a profit selling hacker merchandise such as T-shirts or CDs. Some of the more stable hacker group websites are listed in this section.
This site provides both current and archived news about computer security, including a list of allegedly fraudulent people and organizations in the computer security business (www.attrition.org).
AusPhreak
AusPhreak offers a meeting site for Australian and international hackers to gather and share ideas (www.ausphreak.com).
Chaos Computer Club
One of the oldest hacker groups and one of the largest in Europe, Chaos Computer Club is perhaps best known for its loose affiliation with a West German hacker, Karl Koch, who was accused of breaking into American government computer networks and selling military secrets to the Soviet KGB intelligence agency (www.ccc.de).
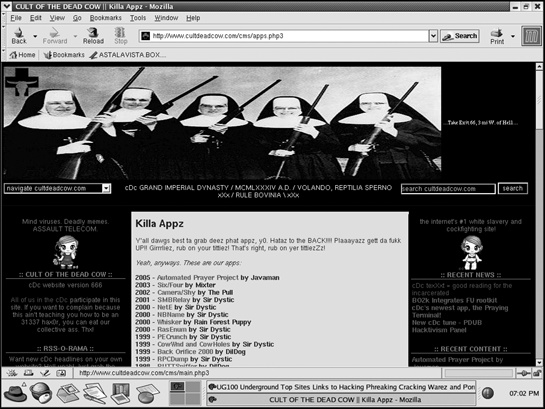
Cult of the Dead Cow
The Cult of the Dead Cow (see Figure 7-2) is known for releasing a variety of hacker tools with great fanfare. Some of their more notable hacker tools include the remote-access Trojan horse dubbed Back Orifice, a steganography tool for hiding information in images called Camera/Shy, and an anonymous peer-to-peer tunneling protocol called Six/Four (www.cultdeadcow.com).
New Order
New Order offers hacker software, security exploits, and lists of interesting projects such as GhostProxy, which is designed to let you browse the Internet anonymously; MD5 Reverse Lookup Database, for helping you crack MD5 encrypted files (also known as hashes) used to protect passwords; and Slut-Box, a server specifically set up to allow people to practice breaking into a computer without getting arrested (http://neworder.box.sk).
Nomad Mobile Research Centre
Provides plenty of hacker tools and research papers geared towards finding exploits in popular programs (www.nmrc.org).
The Shmoo Group
Website of security professionals who donate their time to creating useful tools for hacking or for catching hackers (www.shmoo.com).
Underground News
Hacker tools and news are posted on Underground News along with the latest rumors circulating around the computer industry (www.undergroundnews.com).
Computer security “hacking” websites
The main reason most hackers no longer set up their own websites is because there’s no money in it. Between the cost of running a website, the time needed to design and maintain it, and the possible legal liabilities of offering programs that encourage piracy, most hackers choose the more lucrative route of calling themselves “security professionals” instead. Rather than risk going to jail for hacking, such reformed hackers/security professionals sell their hacking skills to the highest bidder.
One prominent hacker group, dubbed L0pht Heavy Industries, transformed itself from a hacker group to a computer security firm called @Stake, which in turn was bought out by Symantec. Given the choice between serving prison time or getting paid to hack legally, it’s easy to see why hackers would opt to become security professionals.
AntiOnline
This source for hacker news, virus source code, and Trojan horse programs also offers various forums where security professionals can chat and exchange information (www.antionline.com).
DShield
Gathers information from firewalls to track the different types of hacker attacks occurring around the world (www.dshield.org).
Hideaway.net provides news, information, and links to different types of security software and anonymous web browsing sites (www.hideaway.net).
Home of the Nmap security scanner, this site also lists the top security tools to protect your computer and network from attack (www.insecure.org).
PacketStorm
Provides both historical and current information and tools about hackers and the latest exploits (http://packetstormsecurity.org).
Security News Portal
A massive directory of links to various computer security resources, news, companies, and security threats is available at Security News Portal (www.securitynewsportal.com).
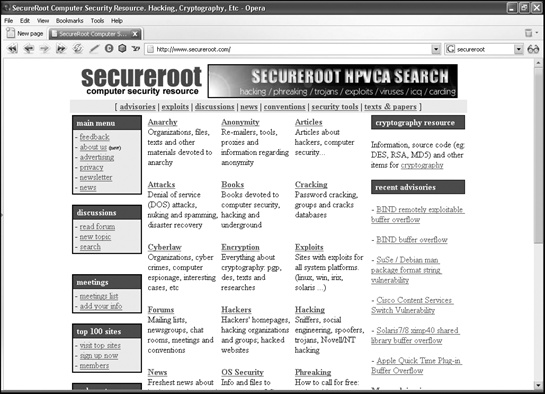
SecureRoot
This site organizes links to various hacker and computer security resources in categories for easy browsing (www.secureroot.com), as shown in Figure 7-3.
SecurityFocus
Home of the BugTraq mailing list of the latest exploits in different software, SecurityFocus also provides a library of security programs along with a security-related job bank (www.securityfocus.com).
Another huge directory of different computer security companies, hacker groups, and security software tools is available at Startplaza.nu (www.startplaza.nu).
Sys-Security Research
This site provides white papers examining computer security issues with a special emphasis on VoIP (www.sys-security.com).
Talisker’s Security Portal
British security website that provides real-time security alerts and updates for government and military organizations (and anyone else who visits their website, too)—www.securitywizardry.com.
WindowsSearch
This site packages coverage of computer security (focusing exclusively on Windows) as well as an online Trojan horse scanner, an email vulnerability scanner, and a network security scanner (www.windowsecurity.com).
Wiretapped
Wiretapped specializes in cryptography and network monitoring with plenty of links to packet capturing, network mapping, and network intrusion detection software (www.wiretapped.net).
Hacker search engines
To find more hacker and security-related websites, you could use an ordinary search engine, such as Google, but you’ll wind up sifting through lots of irrelevant links. For a more targeted alternative, use the specialized hacker search engine, AstalaVista (www.astalavista.com). AstalaVista can help you track down everything from the latest source code for the newest worm or virus to the current version of a port scanner designed to probe another computer’s defenses.
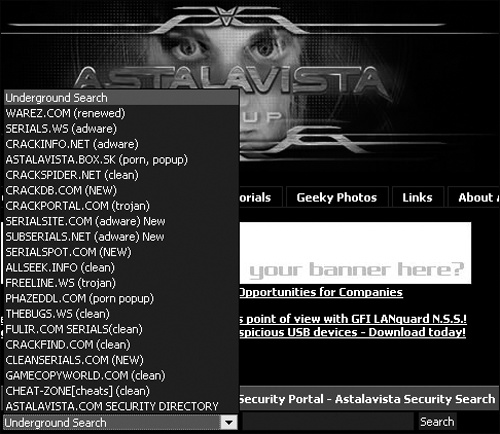
If AstalaVista can’t find a hacker website for you, it also provides a list of additional hacker search engines you can use instead, as shown in Figure 7-4, or you can try http://astalavista.box.sk.
Hacker Magazines
Kids may read Teen People magazine, and adults may read Time or Newsweek (or the Weekly World News). Hackers like to read their own magazines, too. Although none of these titles is prominently displayed in the checkout aisles of supermarkets, they can be found in some larger bookstores as well as on the Internet. Hacker magazines tend to have irregular publishing schedules, so don’t be surprised if the latest issue is several months old (or if the magazine has stopped publishing altogether).
2600
Published quarterly, 2600 is one of the oldest and most respected hacker magazines. Its website doesn’t offer any articles from the magazine, but it does provide the latest hacker news along with lists of hacker conventions (www.2600.com).
Blacklisted! 411
Another hacker magazine published sporadically is Blacklisted! 411 (shown in Figure 7-5). Its website offers articles from back issues along with the latest hacker news (www.blacklisted411.net).
Hacker News Magazine
This interesting French hacker magazine provides hacker tools, news, and articles for browsing (assuming you know how to read French, of course)—www.hackermag.com.
The Hackademy Premium
This French magazine, geared to white hat hackers, provides articles and news in French, Spanish, and English. The staff also offers training classes at their hacking school in Paris (http://premium.thehackademy.net).
Phrack
One of the oldest hacker magazines, in operation since 1985, Phrack reported on networking, telephony, phone phreaking, and other computer hacking topics until recently ceasing publication. Maybe by the time you read this another group will have stepped up to keep the magazine going (www.phrack.com).
Private Line
Private Line is an unusual magazine that specializes in all aspects of phone phreaking, including cell phones and VoIP along with ordinary landline telephone systems (www.privateline.com).
Hacker Usenet Newsgroups
Hackers often communicate through the anonymity of Usenet newsgroups, sharing information and answering questions between insults, posts of virus source code, ads for get-rich-quick schemes, and links to the latest temporary hacker website that everyone should visit before it gets shut down for one reason or another.
General hacking newsgroups
To start learning about hacking in general, try one of the general-purpose hacking newsgroups listed below. Unlike other types of newsgroups that focus on stamp collecting or photography, hacker newsgroups tend to stray from their topics. For example, the alt.binaries.hacking.beginner newsgroup, which says it is about helping new hackers find and use hacking programs, is often filled with discussions about virus programming and encryption, or vicious insult wars. Other hacking newsgroups include alt.hacker, alt.hacking, alt.binaries.hacking.beginner, alt.binaries.hacking.websites, alt.2600.hackers, and comp.hackers.
Computer virus newsgroups
Computer virus writers often publish their latest creations in newsgroups (or post URLs where you can download them). If you want to find the latest live virus (or virus source code), visit one of the following newsgroups: alt.comp.virus, alt.comp.virus.source, alt.comp.virus.source.code, or comp.virus.
Encryption newsgroups
Because hackers often skirt the legal boundaries of their countries’ laws, they wisely hide their identities or messages using encryption, the same technology that government agencies use to protect national secrets. To learn the latest about using and writing encryption to protect your sensitive data (topics you’ll read more about in Chapter 22), visit one of the following newsgroups: alt.cypherpunks, alt.security, alt.sources.crypto, misc.security, sci.crypt, or sci.crypt.research.
Cracking newsgroups
Most games and applications are copy-protected to prevent software piracy. Likewise, many shareware programs provide limited functionality until the user pays for a code or key to unlock additional features.
Some hackers try to circumvent, or crack, copy-protected and “locked” shareware programs. Cracking methods include sharing serial numbers, unlocking codes, and using programs designed to unlock or duplicate copy-protected games. To read about these programs and techniques, visit any of the following newsgroups: alt.2600.crack, alt.2600.crackz, alt.binaries.cracked, or alt.cracks.
Finding Hackers on IRC
You can chat with a hacker in real time in one of the many hacker chat rooms that pop up on nearly every Internet Relay Channel (IRC) network. After you install an IRC client program on your computer, such as mIRC (www.mirc.co.uk), you’ll need to pick an IRC network to join. Some of the more popular networks are EFnet, DALnet, Undernet, and 2600 net (run by the hacker magazine 2600).
Once you’re connected to an IRC network server, you can create a new chat room or join an existing one. To find a hacker chat room, look for rooms with names like #2600, #phreak, #carding, #cracks, #anarchy, or any other phrase that sounds hackerish.
Using IRC is a special skill in itself, and many hackers may get upset if you intrude on their chat rooms, so use care when exploring the different networks and chat rooms. With enough patience, you can eventually meet and make friends in the various chat rooms and become a regular and experienced IRC user too. For more help in using IRC, pick up Alex Charalabidis’ The Book of IRC, published by No Starch Press (www.nostarch.com/irc.htm).
Hacker Conventions
Hacker conventions are great places to meet people you’ve only interacted with in chat rooms or newsgroups and to listen to speakers from around the world discuss the latest trends in computer security. Since many hacker groups announce their latest hacking tools and techniques at hacker conventions, both the hacker side as well as the law enforcement side of the computer underground, including FBI and Secret Service agents, can be found lurking about at these conferences.
Anyone can attend a hacker convention, including hackers, law enforcement agents, and those who are just curious to see what life looks like in the computer hacking world.
DefCon
DefCon is an annual convention held in Las Vegas, usually attended by hackers, media, and government officials from all over the world. One popular contest is “Spot the Fed,” where attendees attempt to locate FBI agents keeping an eye on the conference (www.defcon.org).
HOPE (Hackers on Planet Earth)
Run by the hacker magazine 2600, this conference focuses on all aspects of hacking, including phone phreaking, virus writing, social engineering, and information warfare (www.2600.com).
Chaos Communication Congress
The largest European hacker conference, Chaos Communication Congress, is run by the German-based Chaos Computer Club (www.ccc.de/congress).
PH-Neutral
German hacker conference for Europeans and anyone else with enough money to fly to Berlin (http://ph-neutral.darklab.org).
RuxCon
Australian security conference dedicated to hacking in the land down under (www.ruxcon.org.au).
ShmooCon
This is an annual east coast hacker conference with plenty of speakers and opportunities to discuss computer security (www.shmoocon.org).
SummerCon
One of the oldest hacker conventions, SummerCon tends to be held in different cities each year so that hackers from different parts of the world can attend (www.summercon.org).
ToorCon
One of the newer computer security conferences, ToorCon, is run by hackers who want to combine their love for hacking with the sunshine of San Diego (www.toorcon.org).
Don’t Panic: Hackers Are People, Too
The more hackers you meet, whether through newsgroups, websites, or in person at hacker conventions, the more likely your perception of hackers will change. Some hackers fit the hacker stereotype, but others deviate dramatically from any preconceived notions.
Of course, as with any group of people, there will always be some whom you would do well to avoid. Some of these malicious hackers may try to snare your credit card number, use your identity online, or just harass you by routing a 1-900 sex hotline to your home phone.
Other hackers may look down on you as a newbie, a derogatory term for a newcomer. Ignore these obnoxious people, since even they were newbies at one time too. Just keep learning on your own and from others who are willing to help you, and soon you too will be considered as knowledgeable as the rest of them. When that happens, you’ll have to decide how you want the world to see you—as someone who’s intelligent and inquisitive, or as someone malicious and destructive. Whatever impression you want people to have about hackers, it’s up to you.