"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world."
– Eric Hughes, "A Cypherpunk's Manifesto", 1993
(https://www.activism.net/cypherpunk/manifesto.html)
Ask any individual how important privacy is and you will get the same answer every time: privacy is very important but in a digital age, where we don't have control over our personal information, how do we take it back? In April 2018, this importance was further highlighted in a very public Facebook–Cambridge Analytica data scandal.
An app was created in 2014 called This Is Your Digital Life and about 270,000 people were paid to participate. The glitch was that it not only collected personal data from the people who agreed to participate but also the personal information of all the people in those users' Facebook social networks. This led to the accumulation of around 87 million Facebook users' data (https://www.theguardian.com/technology/2018/apr/04/facebookcambridge-analytica-user-data-latest-more-than-thought). Cambridge Analytica obtained the data and used it to profile individuals, in order to target them with personalized political advertisements. This was done to influence public opinion, as explained by Alexander Nix, the Cambridge Analytica CEO:
"Today in the United States we have somewhere close to four or five thousand data points on every individual... so we model the personality of every adult across the United States, some 230 million people." (https://news.sky.com/story/behind-the-scenes-at-donald-trumps-uk-digital-war-room-10626155).
The Cambridge Analytica saga is but one example in a history of infamous data breaches that includes Equifax, Ashley Madison, and Sony, but blockchains and tokens can change all of this. Personal data can be stored on a blockchain that is only accessible by you. You then have the ability to choose who can access this data and for how long. With tokens, you can now also choose how much people can access your data for.
If everything is being tokenized, why not tokenize ourselves? We could tokenize the time we have available or tokenize our personal data. We can then encrypt it and give it or sell it to those who want it or those who need it. These quantum packets of tokens could even be placed on a quantum blockchain, which may not be as far off as many imagine. One particular paper titled Quantum Blockchain Using Entanglement in Time even discusses these concepts (https://techcrunch.com/2018/04/24/meet-the-quantum-blockchainworks-like-a-time-machine/).
The point here is that the self-sovereignty of data will become a reality, which will naturally create a market of tradable tokenized personal data, and then a bidding war between the global brands. As we trade our personal data, perhaps it won't be as private as we think. Perhaps it will be pseudo-private just like how bitcoin is pseudo-anonymous. We will have ultimate control, but will flaunt it around so much that our data will be everywhere and when a quantum computer with AI has the ability to crack conventional cryptography, it will be the Y2K bug all over again. There will be a huge rush to upgrade all the systems to use new forms of quantum cryptography.
Tip
Y2K or the Year 2000 bug: Because many programs represented four-digit years with only the final two digits, there was a concern that the year 2000 would be indistinguishable from 1900 and that computer programs running critical services, such as nuclear power plants, and air traffic control systems, could become compromised. When January 1, 2000, did arrive, the bugs that arose were generally regarded as being relatively minor.
Hughes' manifesto explains more on privacy:
"Privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy."
Although "A Cypherpunk's Manifesto" was written over 25 years ago, it is still as relevant as ever, particularly in regards to building anonymous systems, defending privacy with cryptography, and freedom of speech being fundamental to an open society. However, there is a movement by various governments around the world to shake things up.
India announced a ban on its largest denominated bills, the 500 and 1000 rupees, the equivalent of $8 USD and $14 USD, in November 2016 (https://www.nytimes.com/2016/11/09/business/india-bans-largest-currency-bills-for-now-n-bid-to-cut-corruption.html). Australia announced that it will be illegal to purchase anything over $7,500 USD ($10,000 AUD) with cash from July 2019 (https://gizmodo.com/australia-bans-cash-for-all-purchases-over-7-500-start-1825946888?IR=T). In France, the maximum payment in cash is €1000. Many other governments around the world are following in the same direction. The reason these governments are attempting to reduce the reliance on a cash economy is to reduce money laundering and tax evasion. Large transactions will have to be done electronically so they can be tracked.
With the slow squeeze on cash, the transition into a digital society is inching closer. Blockchains and cryptocurrencies, such as bitcoin, actually increase transparency. To insure privacy is maintained, it has to be fought for. "A Cypherpunk's Manifesto" highlights a dedicated motivation to ensuring privacy is not lost. Translating the manifesto “Cypherpunk’s Manifesto”, privacy coins, such as Monero (XMR), Zcash (ZEC), Dash (DASH), Verge (XVG), and many others, continue to fight for the right to privacy and therefore can only continue to grow in the coming years.
Before we jump into more detail about these coins, let's compare privacy with anonymity because they are two different concepts. Privacy is the ability to keep something to yourself. Privacy also is not free, as it takes effort to create and the greater the privacy, the greater the cost. For example, if you don't want people on the street looking into your house, you need to take appropriate steps, such as having curtains or a high fence.
In contrast, anonymity is when you want people to see what you do, just not that it's you doing it. The most famous example is Edward Snowden, a former CIA employee who leaked classified information from the NSA. He wanted the NSA's information to be public, but his identity to remain anonymous. A cheeky example:
This is relevant because some coins enhance privacy and some enhance anonymity, and some do both. In the future, these coins will grow and tokens will also encapsulate these features.
There is a difference between a privacy coin and a coin with privacy features. Monero, for example, is a coin whose main goal is to achieve privacy. Coins with privacy features implement privacy as a feature, such as Dash with coin mixing and Verge with the Invisible Internet Protocol (I2P).
These coins also have what is called "scope of anonymity." Verge, for example, anonymizes only the sender's IP address, while Monero obscures the sender's details and receiver's details, as well as the amount.
Coins with privacy features often provide the user with the option to send transactions in private mode or transparent mode. Privacy coins, such as Monero, force all transactions to be sent privately.
Monero is a cryptographically private coin by default, meaning there is no option for the user to send transparent transactions like with the other coins. Monero achieves privacy utilizing several techniques, such as ring confidential transactions (RingCT) and stealth addresses.
RingCT are designed to improve privacy and security by joining a user's transaction with other older network transactions, such that an observer cannot tell which transaction in the ring is the "real" one. The added advantage is that these other transactions do not need to occur simultaneously with the one that a user wishes to create.
Ring signatures and stealth addresses are used to hide both the sender's and the receiver's address in a transaction. This obfuscation of the addresses makes blockchain analysis virtually impossible. For example, you cannot explore the Monero blockchain or trace any transactions.
Zcash offers privacy using a technology called Zero Knowledge Succinct Non-Interactive Arguments of Knowledge, or zk-SNARKs. Just being able to remember the acronym is good enough to impress your friends!
zk-SNARKs is a mathematical proof proving that the transactional information sent is accurate, without having to reveal what that information is. It also serves to allow for both the verification and the privacy of data at the same time, and is used to encrypt addresses, as well as transaction amounts. However, it is not private by default, mainly due to the inefficiency of the algorithm.
Zcash is a coin where privacy is an option, which unfortunately has meant that currently, according to Zcash's blockchain, only about 3% of funds are shielded or held in addresses starting with "z" (https://explorer.zcha.in/statistics/value). The rest are held in transparent addresses starting with "t."
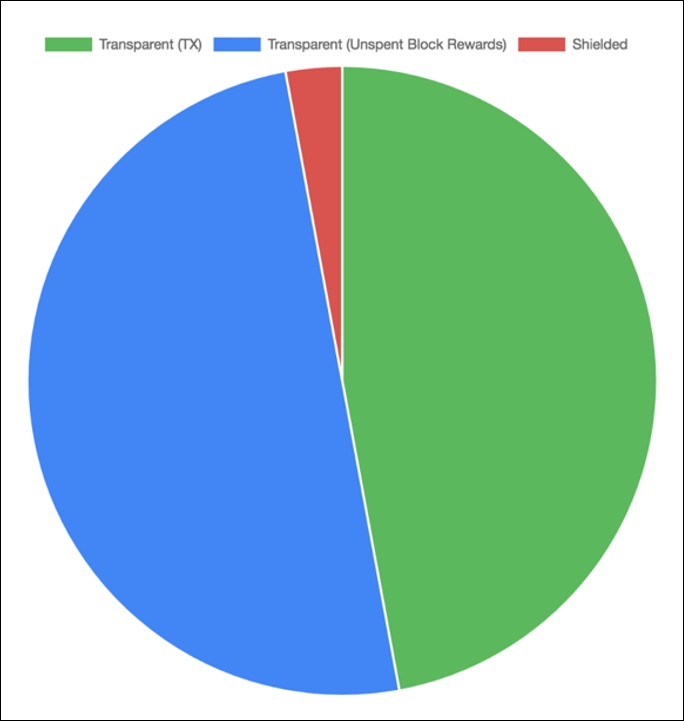
Figure 4: The percentage of private (shielded) Zcash transactions is very low because it is an opt-in and not a mandatory feature
Dash, a portmanteau of Digital Cash and formerly known as Darkcoin, provides some anonymity features but they are opt-in (https://news.ycombinator.com/item?id=14672691). It contains a "PrivateSend" feature, where during the process, your coins are mixed with other coins being sent on the network by special "master nodes." Because of this mixing, Dash is often labeled as not being cryptographically private, but it achieves privacy through mixing.
Dash is also not anonymous in the traditional sense because the transactions can be viewed in a blockchain explorer. It's just very hard to figure out who sent what. Therefore, like Zcash, Dash is a coin with privacy features.
Verge is not natively private but offers privacy by way of Tor and I2P routing, to obfuscate traffic and conceal a user's IP address when transacting. Tor stands for The Onion Router and is a network that disguises your identity by moving your traffic across different Tor servers, and encrypting that traffic so it isn't traced back to you. This is known as onion routing because your data passes through many layers.
I2P is another network of roughly 55,000 computers around the world (https://en.wikipedia.org/wiki/I2P). It is often called the garlic routing protocol. Each message is a garlic clove, with the entire encrypted bundle representing the bulb. Each encrypted message has its own specific delivery instruction, with all the cloves finding their own way to the end destination.
Therefore, with Verge, all information, including the destination of the transactions and the amounts being transacted, is transparent on the blockchain, and easily viewable by an observer. Moreover, the privacy, traceability, and ability to link transactions and addresses on the Verge blockchain are exceptionally worse than bitcoin because the Verge blockchain contains fewer transactions overall.
Privacy coins will be critical to the future of the technology moving forward. The realization of the ability to track a token back to an owner, identify them and then link them to other coins or tokens will be the impetus to create privacy tokens to protect those who value privacy and anonymity.
Formally, hashgraph is known as the consensus algorithm "technology," Swirlds as the consensus platform that implements the hashgraph consensus algorithm, and Hedera as the public ledger that is built on top of the Swirlds consensus platform, that implements the hashgraph consensus algorithm. It is a layered approach because a ledger is a lot more than just a consensus mechanism.
A more simplified version is to think of Hedera hashgraph as being similar to Microsoft Excel, where the first word is the company or brand and the second word is the technology, which in this case is the consensus technology.
The concept of Hedera stemmed from the idea of the code not forking or having to be pruned in the technical sense. Hedera is a vine and grows, spreads, and interlinks, as opposed to a fruit tree, for instance, which you have to prune regularly. This reflects the fact that information on a hashgraph can grow and spread without having to be pruned. Therefore, Hedera organically suited the concept of the algorithm.
Tip
Unless you are in the field of horticulture, you may not have come across the word Hedera. Hedera is actually the genus or type of 12 to 15 species of evergreen climbing or ground-creeping woody plants in the family Araliaceae. In biology, part of the taxonomy goes family -> genus -> species, so here it goes Araliaceae -> Hedera -> 12 to 15 species of ivy plants.
In any distributed network, the consensus algorithm is a big deal. Without a secure consensus algorithm to essentially prevent double spending, everything else fails. Within consensus, there is also a distinction between preventing consensus and corrupting consensus.
Every network is susceptible to a one-third attack if it can be split with a firewall. What this means is that if you can break a distributed network into one-third and two-thirds, then what the attacker really needs is just to control one-third of the network to disrupt it and prevent consensus from occurring. This is a very specific attack that every consensus algorithm, that is available right now at least, is susceptible to. Any network susceptible to a 51% attack is also susceptible to a one-third firewall attack.
To take this a step further, hashgraph requires that two-thirds of the network is honest. If more than one-third of the network is being dishonest, then it can prevent consensus for a period of time but it cannot corrupt consensus, meaning that nobody can lie. It may stall the network, but because it will be hard to maintain this, consensus will eventually be achieved.
The idea is that you can prevent consensus with a one-third attack but you cannot corrupt consensus. The only way to corrupt consensus or to tell a lie is to have a greater than two-third control of the network. So, if you wanted to adjust the balance of everyone's wallet and remove the cryptocurrency you just spent and place it back in your wallet, you would have to have greater than 66% control of the network to rewrite history. You could theoretically keep the rest of the network from coming to consensus with just 33% + 1 control of the network. Therefore, two different thresholds have two different effects.
In blockchain, people talk about a 51% attack, so comparing the theoretical threshold for corrupting consensus, it is 51% in blockchain versus 66% in hashgraph. There is also another argument for controlling the blockchain network with a 25% attack, with research done that claims that when using a particular mining attack called selfish mining, only 25% control of the network is required (https://arxiv.org/pdf/1311.0243.pdf). In summary, there are different attacks and there are different thresholds for these attacks.
There were a few licensing models that Hedera could have pursued:
- Purely proprietary and closed source
- Purely open source with an open-source license
- Some type of hybrid
If Hedera could have gone with open source it would have, but the argument was that when you accompany open source with financial incentives, it doesn't accomplish all the goals that open source was designed to accomplish. If anything, it prevents a lot of innovation because people get to the point that it is good enough to make money and they stop innovating. Therefore, it made more sense to have an organization that was about the innovation and go for a more controlled hybrid-source approach.
Going with a patented proprietary license model, but with an "open review" model, meant that the source code would be published, so it could be reviewed and potential vulnerabilities could be identified with a reward mechanism or bounty. The other value of this model centers around governance, which allows Hedera to prevent forking, to provide stability in the network, making it more favorable for mass adoption.
Any nodes, however, will be able to get the source code and compile it to ensure that they are running a valid and authentic version of the code. The intent is to embody the spirit of open source and be as transparent as possible.
We know what a 100% proprietary company looks like, such as Facebook, Google, and Amazon, which are very successful, but there are some trust issues to say the least. We've also seen what happens with open source, which usually results in a consolidation of power and forking, which creates instability and thousands of cryptocurrencies. Hedera argues that somewhere in between is the right answer: to create a stable mass market adoptable technology. The patent is there as a defense mechanism to create and ensure the stability of the network.
In some blockchain networks, there is the concept of super nodes or master nodes that have the voting power to form consensus, and regular nodes vote for these super nodes almost like in a democratic government voting system. This is commonly termed "delegated proof of stake."
In Hedera, the public network will start with 39 nodes. The key is that the owners of those 39 nodes happen to also sit on the council and they make governance decisions. The nodes themselves have no additional power over the consensus process compared to any other node. There is a concept called "proxy staking", where any node can create its own incentives to drive end users to your node.
As the network grows, there will be sharding and some of the sharding governance functions will be performed by the 39 council members transparently, but it will not affect consensus. In essence, every node has equal power at the consensus layer, relative to its stake, of course.
To help visualize the technology, anything that can be done with current blockchain technologies can be done with Hedera hashgraph. Examples include ICOs, micropayments, and even CryptoKitties. This is because the architecture contains a cryptocurrency component, a file storage component and a smart contract component. The compatibility with Ethereum smart contracts was a decision made because of the huge adoption of Ethereum.
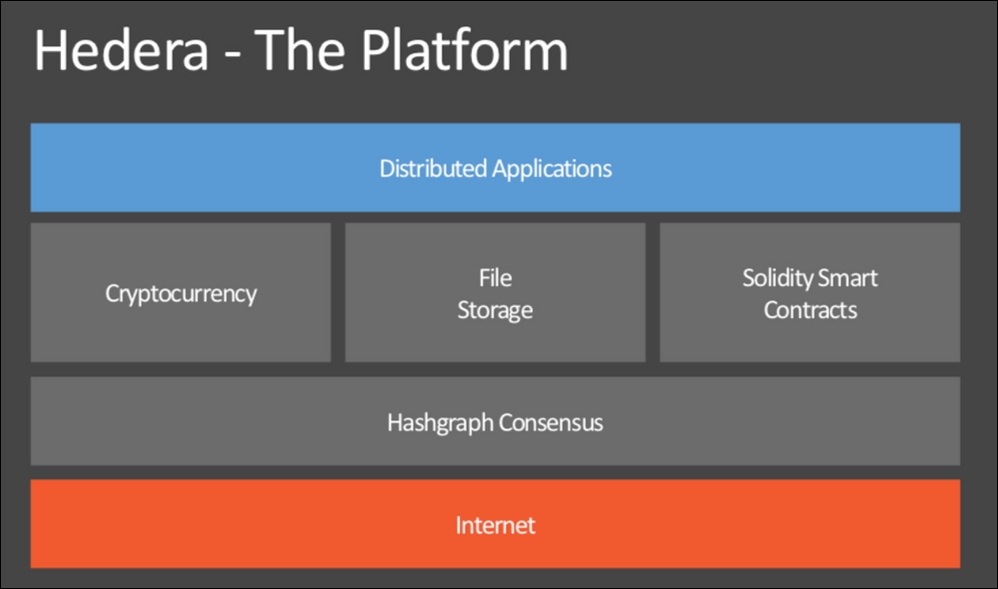
Figure 5: The Hedera platform components
One of the benefits of hashgraph is regarding persistence or the storing of data. In the blockchain world, the whole blockchain, around 200 GB at the time of writing, is required to maintain a full node. A full node is required because each transaction needs to be cryptographically verified against all previous transactions, right back to the beginning of the blockchain or the genesis block. Therefore, blockchains cannot maintain the integrity of the latest block without having a genesis block as a reference, and storing absolutely everything in between.
In hashgraph, instead of securing transactions against an ever-growing 200 GB of history, it is saying that 39 nodes (initially anyway) have confirmed that this transaction is valid and as long as we always have two-thirds of the network being honest and validating every round, we can trust the current round because it was validated against the previous round. So, because of this, hashgraph does not need the entire history to reach consensus.
A valid argument for a blockchain is around immutability, where people cannot lie about the history of transactions that took place because it is imprinted in the blockchain. In hashgraph, all of this can be optionally stored by a node. In addition to this, two-thirds of the network can provide a signature attesting that some event did happen. This is called a state proof in Hedera hashgraph.
Other neat features include multiple payments that can be processed in one transaction, great for splitting the bill or businesses building dApps, and claims that can be added to accounts (think self-sovereign identity) that are signed by an authority and the account owner.
There is also an argument against immutability, especially with GDPR and the right to be forgotten. In blockchains, you cannot forget. For instance, using the distributed file storage concept, illegal content cannot be removed from the blockchain that is potentially being stored on personal computers all around the world. Hashgraph uses the concept of controlled immutability, meaning the user can control what is stored and what is not. From a historical perspective, the network will prove consensus, store it for a period of time, and then discard it, unless it has been explicitly requested to be stored. This way, the user can pay for storage for the next seven years (accounting records for example) and afterwards it will disappear.
To understand quantum computers and their effects on blockchains, it is useful to first of all understand what they are and how they work. Let's start with the basics of how classical computers work. The term classical computer is used to describe computers as we know them in today's world.
Everything in the digital world is represented as 0s or 1s, and transistors are used to represent these two states. A bit, which stands for binary digit is a term used to represent a single binary value. For example, one bit represents on or off. Two bits can represent on-on, on-off, off-on, and off-off.
Transistors representing these bits are getting smaller and smaller, approaching a physical technological limit. This means that each year at Christmas time, the new smart phone you receive will not be twice as fast as last year's model but only half as fast, and only a quarter as fast the year after that. To circumvent the physical limitations, a new technology or paradigm needs to be developed. This is where quantum computers come in.
In the quantum realm, physics works very differently, to the point where our understanding of traditional computers doesn't apply or even make sense. Quantum computers use the concept of quantum bits or qubits (pronounced kew bit), which like their binary counterpart can also be set to a 0 or a 1. However, a qubit can also be in any proportion of both states at once and this concept is called superposition. In other words, a qubit can be a 0 and a 1 at the same time. Weird right?
One qubit can be in a superposition of two states, two qubits can be in a superposition of four states, three qubits can be in a superposition of eight states and so on. For example, if one bit represents a door that is either open or shut, one qubit can represent a situation where the door is both open and shut at the same time, but when observed or measured, it's seen as either fully open or fully shut.
The advantage this brings can be explained by comparing this to a classical computer. In a two-bit system, four states are possible (00, 01, 10, and 11) and four operations need to be performed when evaluating these four states. With two qubits, a quantum computer can evaluate these four states all at once! Imagine what a 50-qubit system can do then!
In conjunction with superposition, another weird and unintuitive property is called entanglement. This is a close connection between two qubits that makes one qubit react to a change in state of the other qubit instantaneously, no matter how far apart they are. This means that when measuring one entangled qubit, it is possible to directly deduce the properties of the other without having to look. Another way to think about this is that tickling one qubit will make the other qubit on the other side of the Earth feel the tickle instantaneously as well.
There are a number of particles that can be used as a qubit. A single photon (a particle of light) or an electron, for example, can be used to represent 0, 1, or a superposition.
One aspect of cryptography relies upon prime numbers. Take the example where a very large integer number, let's call it M, is provided and the goal is to find two factors of M that are prime numbers. In other words, find two other prime numbers that multiply together to get M. It turns out that this is phenomenally hard to do. It is so hard in fact that this forms the basis of encryption. However, what would take billions of years to solve using a classical computer, would take potentially minutes to solve with a quantum computer. This means that the statement that "it is practically infeasible to obtain a private key from a public key" would no longer be true in the quantum world.
There are several ways to combat quantum computers affecting blockchains. Firstly, there is research to create quantum-resistant cryptograph. The aim here is to produce private keys in a much more mathematical way, other than with just prime number factorization.
The second method is to create quantum-based cryptography. This is like fighting fire with fire; it will still take billions of years for a quantum computer to crack an algorithm of its own quantum kind. Finally, there is the possibility of creating an intrinsically quantum blockchain, constructed from quantum information over a quantum network. This would be the most ambitious design.
In fact, two researchers from Victoria University of Wellington, in New Zealand, have proposed a new quantum blockchain technology that "encodes a blockchain into temporally entangled states, which can then be integrated into a quantum network for further useful operations (https://arxiv.org/pdf/1804.05979.pdf)." The researchers also show that entanglement in time, as opposed to entanglement in space, plays a pivotal role for the quantum benefit over a classical blockchain. This is a lot to grasp in a sentence, but the main point is that there are researchers contemplating these concepts already, even though we are many years away from actual realization.
The key takeaway from all of this is that while quantum is a threat to blockchain technologies, it would be a bigger threat to the entire security of the internet, and when quantum computing does arrive, a new security paradigm will take over to secure the likes of Web 10.0.
With all the attention from ICOs in the last few years, governments and law makers around the world have woken up to the fact that something has to be done to reduce scams and protect the consumer. The quickest solution is to make the glass slipper fit the existing foot. In other words, we must classify cryptocurrencies and tokens as either a currency, a property/asset, a commodity, or a security (the list goes on) and make it comply with existing rules and regulations.
New rules and regulations will eventually be required but, currently, we are in the tweaking and addendum phase, just like those introduced to handle drones with no-fly zones around airports. The challenge to encourage innovation, yet protect consumers, is a tough balancing act. We are already seeing smaller countries, such as Switzerland, Cyprus, Malta, and Belize, just to name a few, take the initiative and provide more crypto-friendly regulations to encourage investment and innovation, which will help to simulate and grow an economy. A small island country in the South Pacific, called Vanuatu, is even accepting bitcoin as a form of payment for its citizenship program (https://qz.com/1099475/a-small-pacific-island-will-now-let-you-buy-citizenship-with-bitcoin/).
"Thank you for your enquiry. I can confirm that Bitcoin is accepted as a form of payment for Citizenship Applications. When this story was initially picked up by various news agencies last year it was unfortunately slightly mis-reported that the Vanuatu Government were directly accepting bitcoin - whereas in fact, it is our organization – the Vanuatu Information Centre, which is a Government licensed agent for the Citizenship Program – which accepts Bitcoin payment. We then convert to fiat currency for transmission to the Vanuatu Government."
- Vanuatu Information Centre, May 2017
These smaller island nations have an opportunity to participate in this token economy, raise capital, and create projects to help provide books for schools or more desalination equipment, while existing governments clamber to figure out what is going on and how to play catch up.
Roger Ver, an early bitcoin adopter and a very vocal advocate of Bitcoin Cash, announced in September 2017 a project called Free Society (https://www.freesociety.com/). The goal is to lease a plot of land from a nation state in an effort to build a libertarian, anarcho-capitalist country. The Free Society project plans to:
"Establish a rule of law based on libertarian principles and free markets. We don't see the need to recreate traditional government structures. The rule of law/constitution can be included in the final agreement of the land sale, and will be an extension of the existing contract that will be put in place with the government that granted us the sovereignty. Enforcement will happen through private arbitration, competing court systems, and private law enforcement. It is important to establish a proper rule of law, as our project will set an example for the industry and create an important precedent with governments and the world. We want to make sure the constitution is solid but avoid the inefficiencies of existing government structures."
Don't rule out an ICO in order to raise capital to help fund this project, as the project has only raised $100 million thus far. To say this is an ambitious project would be a grand understatement, but a true tokenized economy could flourish in an environment like this. Identity tokens on the blockchain, ownership tokens, and cryptocurrencies for payments all sounds like 2001: A Space Odyssey reborn. Perhaps this is all just a pre-cursor to more futuristic concepts, such as merging blockchains and satellite technology.

Figure 6: Ver's experimental project of creating a "country" with a central government
As crazy as it may sound, and keeping in mind that it is still early days, there are startups, such as Blockstream (https://www.prnewswire.com/news-releases/announcing-blockstream-satellite-broadcasting-bitcoin-from-space-300504390.html) and Spacechain (https://www.techinasia.com/spacechain-blockstream-blockchain-to-satellite), which are researching into deploying low-cost, low-orbit, tissue-box-sized satellites into space. Spacechain wants to create an open-source satellite operating system where developers can build and run their own applications, like tracking shipping containers across the ocean or taking photos of Earth.
Spacechain aims to launch its first CubeSat into space in February 2019. This seems overly optimistic but we are in an age of amazing revolution. In fact, the late Stephen Hawking believed space exploration is crucial to human survival:
"Our population and our use of the finite resources of planet Earth are growing exponentially, along with our technical ability to change the environment for good or ill. But our genetic code still carries the selfish and aggressive instincts that were of survival advantage in the past. It will be difficult enough to avoid disaster in the next hundred years, let alone the next thousand or million. Our only chance of long-term survival is not to remain lurking on planet Earth, but to spread out into space." (https://www.huffingtonpost.ca/2011/11/18/stephen-hawking-space-exploration_n_1101975.html).
