Definition of a Hierarchy
An Active Directory hierarchy comprises of several elements. Depending on the design of the hierarchy, you can include all the elements or just a subset. The way that all these elements are combined determines the structure of the hierarchy. The elements of a hierarchy are
Object
OU
Domain
Tree
Forest
Object
The most basic element of the namespace hierarchy is an object. Objects are the building blocks of the Active Directory structure. Objects can include, but are not limited to, the following:
Computers
Users
Groups
Printers
Security policies
OUs
Applications
Shared folders
In addition to these standard objects, it is possible to create custom objects. An example of a custom object is the user profile for an Enterprise Resource Planning (ERP) application that your human resources department uses. This profile might contain security definitions for the users as they apply to the ERP application. It might also contain definitions for the application modules, which the users have access to when they launch the application. If Active Directory is utilized as a repository of profile information for applications, it might be necessary to extend the Active Directory schema to accommodate new object classes.
Computers
Computer objects are the objects that define the properties of a computer machine account in the domain. The properties of the computer object might define the specific application settings on a machine or the individual users who have permission to access the machine.
Users
The user object defines, by the set of properties for user accounts, how resources are accessed within both Active Directory and the Forest. Specific properties include which groups the user is a member of, what time of day the user can access the network, and what the password expiration parameters are for the user. Many other parameters can be defined for each user object.
Groups
Groups define collections of specific user and group objects within the Forest. Groups can be used for security purposes, such as defining an administrative group that contains all the administrators who have rights to administer resources in the domain or Forest. Groups can also be used for administration purposes, such as defining a sales group that contains all the users in the domain or Forest who are in the sales organization, thus making it easier to assign access rights or applications policies to the sales force. In addition, Active Directory provides the ability to have groups that are mail-enabled. For example, a set of user objects for executive assistants and executive staff could all be collected in a single group, so that email could be delivered to them all by sending to a single mail alias.
In addition to using groups for security or administration purposes, groups in Windows 2000 can also be configured as distribution groups. This is significantly different from Windows NT 4.0. In Windows NT 4.0, it was not possible to configure a group as a distribution group for email. With Active Directory Windows 2000, it is possible to configure a security group as an email distribution group. This helps to eliminate the administrative overhead of having to maintain identical groups in the network operating system (NOS) directory and in the email system directory, as was the case with Windows NT 4.0 and Exchange Server 5.5.
Printers
Printer objects define the properties of printers in the Forest. Printer properties include the types of printer drivers, printer locations, and specific printer configuration requirements, such as whether a duplexer is installed on the printer.
Security Policies
Security policies are applied to objects in the directory. Security policies can control everything from the access rights that a user has for a specific resource to whether the traffic between two specific hosts on a network should be encrypted. Security policies in Active Directory are implemented as a subset of the Group Policy Object (GPO). In that they are applied to groups of directory objects, including users and computers. In addition, security policies can be applied directly to the local host machine using security templates.
OUs
OUs are both objects in the directory and the containers in the directory in which objects reside. OUs are discussed in more detail later in this chapter.
Applications
Applications can be registered in the directory as objects. By registering applications as objects, it is possible to assign security policies to the objects and to assign specific applications to specific groups of users. Applications either can be made available to users and groups, or they can be required. The distinction between the two is that in the first instance users, users can decide if they want to install an application or not. In the second instance, users, who are members of groups to which an application has been assigned, are required to accept the installation of the application.
Shared Folders
Shared folders are objects in the directory that identify the location and properties associated with file locations in the network environment.
OU
The next level of element in the Active Directory hierarchy is the OU. The OU is the container in which all the different types of objects can be grouped. If there is an object in Active Directory, it exists within the context of an OU, or a container. It is important to note that some of the containers that are set up in Active Directory by default are not OUs, and consequently, they cannot have group policies assigned to them. These include the containers for Users and Computers.
OUs are used for logical administrative groupings or for objects that are used to delegate administration within a domain. Although delegation of administration is one of the main reasons for developing OUs, it should not be the only reason. Several reasons for creating OUs are discussed later in this chapter. One of the most critical decision points in developing an Active Directory hierarchy is deciding whether to create new OUs.
Domain
A domain is defined by a common security context and policy, and it is unified by a single namespace within the directory hierarchy. This chapter discusses why and when to utilize a domain for segmenting objects in the directory rather than an OU.
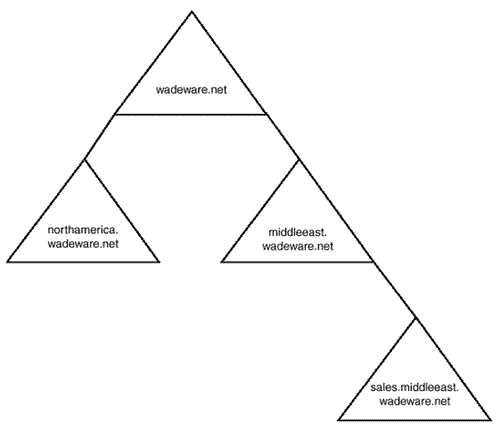
Tree
A tree is a collection of Windows 2000 domains that fall under a contiguous and unified namespace, as illustrated in Figure 20.1. All the domains in a tree share a common security context and a Global Catalog (GC). This is also the case with domains in a Forest.
Figure 20.1. A domain tree comprising all the domains that participate in a contiguous namespace.
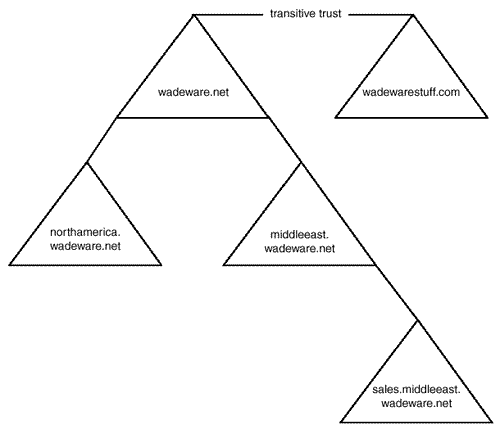
Forest
A Forest is typically composed of a single domain tree with domains unified under a contiguous namespace. If you create a single Windows 2000 domain, you also create a tree and a Forest. However, a Forest differs from a tree in that it can also contain multiple domain trees that do not participate in a contiguous namespace, as shown in Figure 20.2. In this example, the domain tree defined by wadeware.net does not share a namespace with wadewarestuff.net. However, they do share a common security context, a common directory schema, and a common configuration by participating in the same domain tree. The common security context is established by the default transitive trust, which is automatically established between the top-level domains of each tree.
Figure 20.2. A Windows 2000 domain Forest is differentiated from a single domain tree in that it can contain multiple domain trees with discontiguous namespaces.