CHAPTER 5
Local User Accounts
All Microsoft Windows operating system versions have number of pre-defined built-in local user accounts. These accounts have different purposes depending on which operating system version is in use or which OS features, software, and roles are installed/enabled. All these accounts have different default property values that depend on many variables, which we discuss further in this chapter.
Some of these local user accounts, such as the built-in “Guest” account, are disabled by default and, in most companies, should remain disabled. Some other accounts, such as the built-in local “Administrator” account on the Microsoft Windows server family operating systems, are enabled by default and usually remain enabled in most companies.
Highly privileged local accounts, such as the built-in local Administrator account, should also be monitored for each modification and action performed by such accounts.
This chapter provides information about different built-in local user accounts on Microsoft Windows operating systems and specific monitoring scenarios for the most important operations/changes done to these accounts.
Built-in Local User Accounts
As a first step in the process of learning about possible anomalous behavior related to built-in local user accounts you should, first of all, know which built-in local user accounts exist on different Microsoft Windows operating system versions. You should know their default settings, purpose, group membership information, and so on. This section covers the information you need to know about default Windows local accounts.
Administrator
This account considered the most privileged default user account on Windows operating systems.
The built-in local Administrator user account is intended for OS administration, and should be used for administrative tasks only, such as software installation, making changes to operating system settings, changing system registry key values, and so on. This account is usually the first account attackers try to compromise, but many companies still use this account to run, among other things, system services, scheduled tasks, and daily operations.
By default, the built-in local Administrator account has no user privileges and logon rights associated directly to it, but it has privileges and logon rights inherited from membership in the local Administrators security group. The local Administrators security group has the following user privileges (applicable to all modern Microsoft Windows operating system versions):
- Adjust memory quotas for a process
- Back up files and directories
- Bypass traverse checking
- Change the system time
- Change the time zone
- Create a pagefile
- Create global objects
- Create symbolic links
- Debug programs
- Force shutdown from a remote system
- Impersonate a client after authentication
- Increase scheduling priority
- Load and unload device drivers
- Manage auditing and security logs
- Modify firmware environment values
- Obtain an impersonation token for another user in the same session (Windows Server 2016 only)
- Perform volume maintenance tasks
- Profile single process
- Profile system performance
- Remove computer from docking station
- Restore files and directories
- Shut down the system
- Take ownership of files or other objects
The local Administrators security group has the following user logon rights (applicable to all modern Microsoft Windows OS versions):
- Access this computer from the network (Network logon type)
- Allow log on locally (Interactive logon type)
- Allow log on through Remote Desktop Services (RemoteInteractive logon type)
- Log on as a batch job (Batch logon type)
The built-in local Administrator account has the following default characteristics and parameters, no matter which version of operating system, considering only modern versions, it belongs to:
- It is a member of the local Administrators security group. It cannot be removed from this group.
- It has the “Password never expires” parameter enabled, which means that its password will never expire.
- It cannot be easily locked out or deleted, and doing so may cause significant operational difficulties.
- It has default Relative Identifier (RID) in its SID: 500.
In Microsoft Windows 7, 8, 8.1, and 10 this account is disabled by default. For server operating system versions it is enabled.
If the Microsoft “Homegroup” feature is enabled and the computer is a member of any homegroup, the built-in local Administrator account will also be a member of the HomeUsers local group. The Homegroup feature is available only on Microsoft Windows client operating system versions.
The built-in local Administrator account is automatically enabled when the computer is booted using safe mode. In client operating system versions, the built-in local Administrator account is usually treated as an “emergency account” that should be used in case a user forgets the password for the normal local user account, which typically is created during the operating system installation. In server operating systems this account is also used as an “emergency account” or “break glass” account.
Guest
The Guest account is considered to be the least privileged default user account in the Windows operating system. It is designed to be used when you need to provide limited access to your computer to someone for Internet browsing or access to some default applications like Calculator or WordPad.
By default, the Guest account is not a member of any User Rights group policy settings on Windows server operating systems. But on client operating systems (Windows 7, 8, 8.1, and 10) it is a member of the following User Rights and Logon Rights group policy settings:
- Allow log on locally (Interactive logon type)
- Deny access to this computer from the network
- Deny log on locally
- Bypass traverse checking (inherited from the Everyone security principal)
Because the Guest account is included in the “Deny log on locally” policy setting on client systems, you will not be able to log on locally using the Guest account right after you enable it. To log on locally, you must first remove it from the “Deny log on locally” local policy setting.
The Guest account has the following default characteristics and parameters no matter which version of operating system it belongs to:
- It is a member of the local Guests security group.
- It has the “Password never expires” parameter enabled, which means that its password will never expire even if it is empty.
- It has the “User cannot change password” parameter enabled, which prevents anyone using the Guest account from changing or setting the Guest account's password.
- It is disabled.
- It cannot be easily deleted, and doing so may cause significant operational difficulties.
- It has the default Relative Identifier (RID) in its SID: 501.
In general, this account should not be enabled in most companies, because it has only a limited number of scenarios in which it is useful. Also, this account allows for logging on to the system without a password, which is a big security issue.
Custom User Account
During installation, all modern Microsoft Windows client operating systems ask you to create a new local account with local administrative permissions, which should be used instead of the built-in local Administrator account.
By default, a manually created custom user account has no user privileges and logon rights associated directly to it, but it has privileges and logon rights inherited from a membership in the local Administrators security group. See the “Administrator” section earlier in this chapter for more information.
A custom user account has the following default characteristics and parameters no matter which version of operating system it belongs to:
- It is a member of the local Administrators security group.
- It has the “Password never expires” parameter enabled, which means that its password will never expire.
If the Microsoft Homegroup feature is enabled and the computer is a member of any homegroup, the custom user account will also be a member of the HomeUsers local group. The Homegroup feature is available only on Microsoft Windows client operating systems.
In general, this account is used as a regular daily account on non–domain-joined machines.
HomeGroupUser$
The HomeGroupUser$ account is an optional account. It exists only if the Windows Homegroup feature is enabled. This account allows your computer to share files with other computers on your network, if they also have the Homegroup feature enabled and they are members of the same homegroup as your computer. The HomeGroupUser$ account's password acts as a shared secret for communications between computers within the same homegroup.
The Homegroup feature is available only on Microsoft Windows client operating systems.
On client operating systems (Windows 7, 8, 8.1, and 10), if a computer is a member of any homegroup, HomeGroupUser$ is included in the following User Rights local policy settings:
- Deny log on locally
- Deny log on as a batch job
The HomeGroupUser$ account has the following default characteristics and parameters no matter which version of client operating system it belongs to:
- It is a member of local HomeUsers security group.
- It has the “Password never expires” parameter enabled, which means that its password will never expire.
DefaultAccount
The DefaultAccount is a new local account that first appeared in the Windows 10 and Windows Server 2016 operating systems. This account is undocumented and managed by the operating system itself.
By default, the DefaultAccount user account has no user privileges and logon rights associated directly to it or inherited.
The DefaultAccount has the following default characteristics and parameters:
- It is a member of the local System Managed Accounts Group security group.
- It has the “Password never expires” parameter enabled, which means that its password will never expire.
- It is disabled.
If the Microsoft Homegroup feature is enabled and the computer is a member of any homegroup, the DefaultAccount will also be a member of the HomeUsers local group. The Homegroup feature is available only on Microsoft Windows client operating systems.
Built-in Local User Accounts Monitoring Scenarios
In this section you learn about monitoring operations related to user accounts, such as account creation, deletion, change, and so on.
New Local User Account Creation
New local user accounts can be created using multiple ways: manual creation by another user, created as part of installation process of the new software or feature, automatic creation by script or application, and so on. At the end, the result is always the same: a new user account.
The most important questions to answer about monitoring user creation activity are: should someone ever create local user accounts on this machine and if yes, should you be informed about it? Typically, after initial system setup, software installation, creation of system services, and so on, no new local accounts should be created. Because of that, it's recommended that you track all local account creation events and perform root cause analysis, especially on high-priority/critical systems.
Two types of user creation security events exist:
- A user was successfully created.
- An attempt was made to create a user account, but failed for some reason.
In both cases the information you probably want to know is:
- Who created the user account?
- When was the user account created?
- What is the name of newly created account?
- How was this account created?
This information is useful in investigations and is important for monitoring systems.
For unsuccessful account creation events, it is also important to know why an account creation action failed.
Successful Local User Account Creation
The sequence of security events that appears in the security event log when new user account is created using the standard Computer Management snap-in is discussed in this section. The standard user Computer Management snap-in user creation window is shown in Figure 5-1.
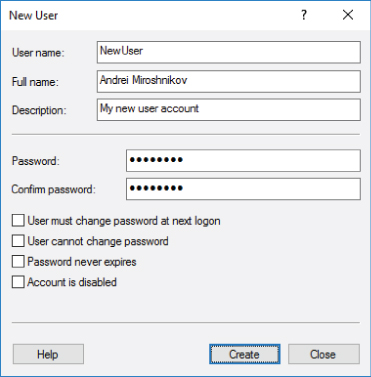
Figure 5-1: User account creation using the Computer Management snap-in
The events shown in Listing 5-1 appear in the Windows security event log when a new local user account is successfully created:
The first step in local user account creation is that CreateUserAudit Success
Object ServerSecurity Account Manager
Object TypeSAM_DOMAIN
This event shows you that the account with the name Administrator2016DC%%5392(ReadPasswordParameters)%%5396(CreateUser)%%5401(LookupIDs)SAM_DOMAIN2016DCC:WindowsSystem32lsass.exeProcess ID 0x30c
The Windows Event Viewer automatically resolves all access type constants into values. For example, the %%5392ReadPasswordParameters
The Access MaskSAM_DOMAIN
Table 5-1: SAM_DOMAIN Object Access Rights
| ACCESS MASK | CONSTANT | VALUE |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Access Mask0x21100x200 (LookupIDs)0x10 (CreateUser)0x01 (ReadPasswordParameters)
The Subject:Security ID
Listing 5-2 is the main event, which shows you that the new account was successfully created.
This event contains answers for some of our initial questions:
- Who created the user account? Answer:
Subject: Account DomainSubject: Account Name - When was the user account created? Answer: the event creation time.
The important information here is the New Account: Account Name
Note that any local user account created using the Computer Management snap-in, by default, is created in a disabled state and has the Password Not RequiredPrimary Group ID513
By default, if you use the Computer Management snap-in, local user accounts are created with a blank/empty password and then the password reset operation is performed. That is why the Password Last Set%%1794 (<never>)
The Display Name%%1793 (<value not set>)
New user accounts, by default, are created with the following account properties:
%%2080 (Account Disabled)%%2082 ('Password Not Required' - Enabled)%%2084 ('Normal Account' - Enabled)
Table 5-2 contains a complete list of user account UAC setting constants and access mask values defined in Windows operating systems.
Table 5-2: User Account UAC Flags
| CONSTANT | ACCESS MASK | VALUE |
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
You can also see these flags in a hexadecimal mask in the New UAC Value0x15Old UAC ValueNew UAC Value
This event also contains many other attributes, but they are not as important as those discussed in this section.
As shown in Listing 5-3, immediately after creation, the new user account (Member: Security ID security group, which, basically means this account is not a member of any global group. This built-in group is not displayed by the Nonewhoami /groups
The term global security group is applicable to the Microsoft Active Directory environment. Local accounts are not members of any global security groups, but local accounts still have the Global Group property, which can be shown using the net user
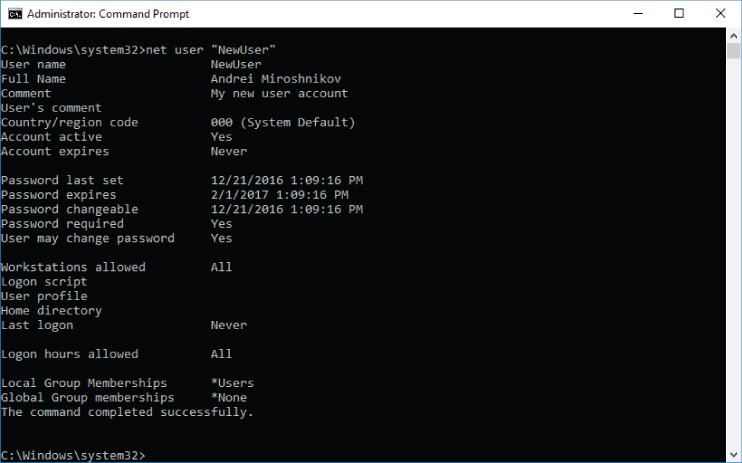
Figure 5-2: Local user account properties
Listing 5-4 shows the account being enabled, because by default all local user accounts that are created using the Computer Management snap-in are created in the disabled state.
Listing 5-5 shows a password reset event, which informs you about a password set operation performed on a newly created account. The password, which you typed during account creation, is set at this step.
The 4738 event shown in Listing 5-6 informs you that the Password Not RequiredDisabledPassword Last SetUser Account Control
This event also shows that the Display NameSAM Account Name
The 4738 event will be covered in more detail later in this book.
The event in Listing 5-7 informs you that the previously opened handle with ID 0x184580fcf70CreateUserSAM_DOMAIN 2016DC
The event in Listing 5-8 exists only on Windows Server 2016 and Windows 10 operating systems. Multiple 4798 events are shown in the security event log during new local user account creation.
Event 4798 informs you that the AdministratorSubjectNewUserUserC:WindowsSystem32mmc.exeusermgmt.msc
This event is informational only in the case of new user creation.
Listing 5-9 shows that at this time some access types (AccessesSAM_USERDOMAINSAccountUsers�00003EA
The SAM_USER
DOMAINSAccountUsers�00003EA
000003EA
You can use the following PowerShell code to get the SID of a specific local user account:
$objUser = New-Object System.Security.Principal.NTAccount("ACCOUNT_NAME")$strSID = $objUser.Translate([System.Security.Principal.SecurityIdentifier])$strSID.Value
Figure 5-4 shows an example of an output of this script for the “newuser” local account.
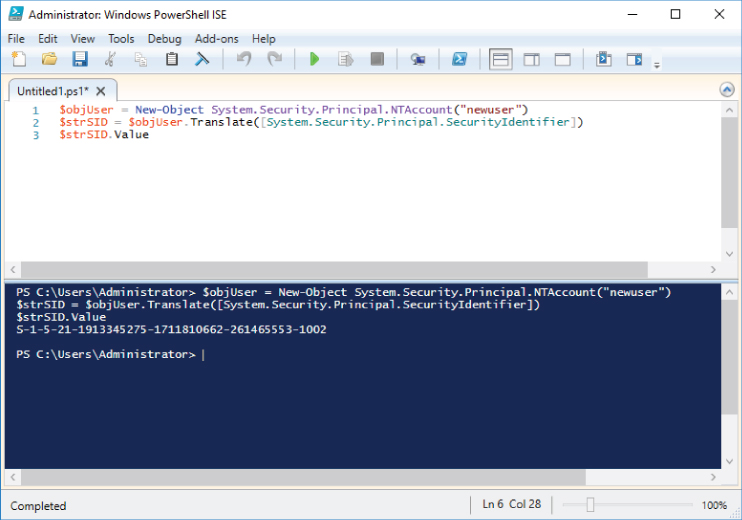
Figure 5-4: Local user account SID extraction using PowerShell
The AccessesSAM_USERSAM_USER
Table 5-3: SAM_USER Object Access Right Constants
| CONSTANT | ACCESS MASK | TEXT |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
The Access Mask
The Access Mask0x601B4SAM_USER0x04 (WritePreferences)0x10 (ReadAccount)0x20 (WriteAccount)0x80 (SetPassword (without knowledge of old password))0x100 (ListGroups)0x20000 (READ_CONTROL)0x40000 (WRITE_DAC)
Returning to the event in Listing 5-9, basically speaking, it shows you that some access types were successfully requested for our newly created user account SAM
The event in Listing 5-10 shows us that the user account's Display NameAndrei MiroshnikovDisplay Name
Then, as Listing 5-11 shows, the handle with ID 0x184580fc100
Next, a handle request event is issued for the Security Account ManagerSAM_USERDOMAINSAccountUsers�00003EA
The event in Listing 5-12 is absolutely the same as the previous 4738 event in Listing 5-10. One of the problems related to the “4738: A user account was changed” event is that for some actions it triggers but doesn't show the real change that causes it. For example, when the user account description (DescriptionDescription
So, this event shows us that something was changed in the user account NewUser
Listing 5-13 shows that the handle, which was opened for the previous account change operation, was closed.
The event in Listing 5-14 shows that some access permissions (AccessesSAM_ALIASDOMAINSBuiltinAliases�0000221
The SAM_ALIAS
DOMAINSBuiltinAliases�0000221regedit.exe0x221545
This event shows you that the handle for the local Users security group was requested, which allows the following: operations: AddMemberRemoveMemberListMembersReadInformation
The Access MaskSAM_ALIAS
Table 5-5: SAM_ALIAS Object Access Permissions
| ACCESS MASK | CONSTANT | PERMISSION |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
The Access Mask0xFSAM_ALIAS0x01 (AddMember)0x02 (RemoveMember)0x04 (ListMembers)0x08 (ReadInformation)
Listing 5-15 shows the next event which, as expected, tells you that the account with SID S-1-5-21-3815211123-123488468-2019406087-1002S-1-5-32-545AdministratorMember: Account Name
Listing 5-16 shows that the handle, which was opened for the previous group membership change operation, was closed.
Now you know the sequence of events that shows in the Security event log each time a new local user account is created using the Computer Management snap-in. And now you know the answers for the following questions (see Listing 5-2: Event ID 4720: A user account was created.):
- Who created the user account? The answer is in the event
Subject - When was the user account created? Event 4720 provides the event creation time.
- The name of newly created account? The account name is shown in the event
New Account - How was this account created? There is no easy way to detect how exactly the account was created, using which tools, scripts, applications, or other methods. A general recommendation here is to inspect all events prior to the account creation event and try to find any information about methods being used to create the account. For example, you may search for the “4688: A new process has been created” event to find the name of the application that was run right before the account was created.
Sometimes you may find some useful events in the “Application” event log that were generated at the same time the user account was created.
Unsuccessful Local User Account Creation: Access Denied
The unsuccessful local user account creation events sequence, where the Subject
This is a failed handle request event. It is almost the same as the 4656 handle request event that you saw for the successful local user account creation operation in the Listing 5-1, but in this case it has an Audit Failure
This event shows you that account amiroshSubjectReadPasswordParametersCreateUserLookupIDsSAM_DOMAIN 2016DC
Here are the answers for the most important questions you might have about a failed local account creation event, where the reason for the failure is “access denied” (see Listing 5-17: Event ID 4656: A handle to an object was requested):
- Who tried to create new user account?
The answer is in the
Subject - When did this happen?
4656 is the
Audit Failure - How did it happen?
In an
Audit FailureProcess Information - Where can I find more details about the account that is supposed to be created?
There is no event in the security event log that provides this information You might try to find this information in the application-specific logs.
Unsuccessful Local User Account Creation: Other
If the Subject
Because the SubjectSAM_DOMAINCOMPUTER_NAMECreateUser
However, after the handle is received by SubjectAudit Success
But this event still must be considered a new local user account creation attempt by an account with sufficient permissions, which failed for some other reason.
Monitoring Scenarios: Local User Account Creation
Useful events to monitor for successful and unsuccessful local user account creation are shown in Table 5-6.
Table 5-6: Events to Monitor for Local User Account Creation
| SUCCESSFUL LOCAL ACCOUNT CREATION | ||
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4720: A user account was created | User Account Management | |
| UNSUCCESSFUL LOCAL ACCOUNT CREATION | ||
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4656: A handle to an object was requested | SAM | |
| 4656: A handle to an object was requested | SAM | |
Any successful local user account creation events should be monitored on high-value and critical hosts. Usually, after initial system setup, no local user accounts are created. Each local account creation event must be investigated and the root cause of this operation must be found.
Some scenarios in which a new local user account needs to be created include:
- By malware, as persistence method for the malware to remain in the system
- By software, server role, or feature installation
- Manually, as a dedicated account for system service or scheduled tasks
You should monitor for any “4720: A user account was created” Audit Success
On high-value and critical hosts, monitor for any unsuccessful local user account creation event that fails due to insufficient access permissions. Each such attempt is important because someone or something tried to create a local user account without having required permissions.
In this case you should monitor for “4656. A handle to an object was requested” Audit FailureAccess Mask"0x211"Object TypeSAM_DOMAIN
- The XPath filter for this is shown in the following code:
*[System[band(Keywords,4503599627370496) and (EventID=4656)]] and*[EventData[Data[@Name='ObjectType'] and (Data='SAM_DOMAIN')]] and*[EventData[Data[@Name='AccessMask'] ='0x211']]
It is recommended that you have a list of accounts (domain and local) that are allowed to create local user accounts. If you have such a list, you should compare every “4720: A user account was created” event Subject
For example, you know that only Domain Admins should be used to create local user accounts on domain-joined machines. You should compare the Security ID field with the SIDs of all Domain Admins accounts in order to verify that. In this case you should set an event importance level to “High” if any other account was used to create a local user account.
For non–domain-joined machines, for example, only the built-in local Administrator account should be used to create new local user accounts by default. In this case you could check the Account NameAdministratorSecurity ID
Monitor these events:
- Monitor for “4720: A user account was created”
Audit Success - Monitor for “4656: A handle to an object was requested”
Audit FailureAccess Mask"0x211"Object TypeSAM_DOMAIN - Monitor for “4656: A handle to an object was requested”
Audit SuccessAccess Mask"0x211"Object TypeSAM_DOMAIN
All local user accounts created using built-in Windows operating system tools (such as the Computer Management snap-in, the net user
- Primary Group ID: 513
- New Uac Value: 0x15, which means:
- Account Disabled
- ‘Password Not Required’ - Enabled
- ‘Normal Account’ - Enabled
Check that all “4720: A user account was created” events have these properties set to their default values using the following snippets. This method might help you to detect local user account creation actions that were performed using nondefault system tools/applications.
The XPath filter for Primary Group ID != 513
*[System[band(Keywords,9007199254740992) and (EventID=4720)]] and*[EventData[Data[@Name='PrimaryGroupID'] !='513']]
The XPath filter for NewUacValue != 0x15
*[System[band(Keywords,9007199254740992) and (EventID=4720)]] and*[EventData[Data[@Name='NewUacValue'] !='0x15']]
You can verify that all newly created local user accounts follow a specific naming convention. Check the New Account: Account Name
Local User Account Deletion
Local user accounts are usually deleted manually or as one of the steps during an application or feature removal/uninstall operation. These events are not routine or common for hosts, which is why I recommend monitoring for any such event, especially on high-value and critical hosts. This section presents information about detection methods for both successful and unsuccessful local user account deletion attempts.
When there is a successful local account deletion operation it is good to know the answers to the following questions:
- Who deleted the user account?
- When was the user account deleted?
- Which account was deleted?
- How was this account deleted?
For unsuccessful account deletion attempts you also should know why the deletion attempt was unsuccessful.
Successful Local User Account Deletion
To better understand the local user account deletion process, look at the events that appear in the Windows security event log when a local account is deleted using the standard Computer Management snap-in.
The event shown in Listing 5-19 exists only on Windows Server 2016 and Windows 10.
It is mostly for informational purposes and informs you that account AdministratorSubjectNewUserUserC:WindowsSystem32mmc.exe
Listing 5-20 shows an important access request event for the DOMAINSBuiltinAliases�0000221SAM_ALIASUsersRemoveMember
This user account should be removed from all groups when it's deleted. This handle request action for one of the groups the deleted user belongs to is a first step in the user deletion process. In this example the deleted user is a member of only one local security group: Users
The event shown in Listing 5-21 informs you that the account with SID S-1-5-21-1913345275-1711810662-261465553-1002BuiltinUsers
The handle 0x184580fd910
As you saw in the “Successful Local User Creation” section earlier in this chapter, during account creation, the account is added to the NoneNone
Listing 5-24 is a handle request for DELETESAM_USERDOMAINSAccountUsers�00003EANewUser
Listing 5-25 is the main security event, which informs you about successful user account deletion. In this event you can see who (SubjectTarget Account
Event 4726 is the most important event for account deletion, which shows you the fact that account was successfully deleted.
Because a user account object in the SAM database was deleted, there is also a separate 4660 event (Listing 5-26) that informs you about changes in the SAM database.
There is no detailed information about the object that was deleted, but it is possible to find a “4656: A handle to an object was requested” event with the same handle ID (0x184580fc5d0
Listing 5-27 shows that the handle 0x184580fc5d0NewUser
Here are the answers to the questions posed at the beginning of this section about a successful account deletion operation (see Listing 5-25: Event ID 4726: A user account was deleted):
- Who deleted the user account?
The answer is in the
Subject - When was the user account deleted?
Event “4726: A user account was deleted” provides the event creation time.
- Which account was deleted?
The answer is in the
Target Account - How was this account deleted?
There is no easy way to detect how exactly the account was deleted, using which tools, scripts, applications, or other methods. A general recommendation here is to inspect all events prior to the account deletion event and try to find any information about methods being used to delete the account. For example, you may search for the “4688: A new process has been created” event to find the name of application that was run right before the account was deleted.
Sometimes you may find some useful events in the “Application” event log at the same time when the user account was deleted.
Unsuccessful Local User Account Deletion - Access Denied
This section provides information about an event that is triggered when the NewUseramirosh
An unsuccessful local user account deletion operation using the standard Computer Management snap-in leaves only the two events shown in Listings 5-28 and 5-29 in the Windows security event log.
The event in Listing 5-28 is triggered no matter which method is used to delete the account. It informs you that amirosh
Listing 5-29 shows an unsuccessful attempt to open a handle to the DOMAINSAccountUsers�00003ECSAM_USERDELETEObjectSubject
The answers to initial questions about this account deletion operation are (see Listing 5-29: Event ID 4656: A handle to an object was requested):
- Who tried to delete the user account?
The answer is in the
Subject - When was the attempt made?
Event “4656: A handle to an object was requested” provides the event creation time.
- The name of the target account?
The answer is in the
Object - How was this account deleted?
There is no information about this in event 4656. You should use the methods described in the “Successful Local User Account Deletion” section earlier in this chapter to find this information.
Unsuccessful Local User Account Deletion - Other
Sometimes, a user account has all required permissions to delete another local user account, but fails for some other reasons.
One example of such a scenario is when an account with sufficient permissions tries to delete a built-in system account, such as the built-in local Administrator
In this case the events in Listings 5-30 and 5-31 will be displayed in the Windows security event log.
The AdministratorSubjectDELETEDOMAINSAccountUsers�00001F4SAM_USER
Right after the “4656: A handle to an object was requested” event you will see “4658: The handle to an object was closed” in which the just-opened handle to the DOMAINSAccountUsers�00001F4SAM_USER
Account deletion failure occurs at the application level and is not recorded in the Windows security event log. Unfortunately, built-in Windows applications, such as the net user
There is no information in the security event log explaining why a target account was not deleted, and you will not find a “4726: A user account was deleted” event in the security event log if the target account was not successfully deleted when error occurs on the application level.
Monitoring Scenarios: Local User Account Deletion
Useful events to monitor for successful and unsuccessful local user account deletion are shown in Table 5-7.
Table 5-7: Events to Monitor for Local User Account Deletion
| SUCCESSFUL LOCAL ACCOUNT DELETION | ||
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4726: A user account was deleted | User Account Management | |
| UNSUCCESSFUL LOCAL ACCOUNT DELETION | ||
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4656: A handle to an object was requested | SAM | |
| 4656: A handle to an object was requested | SAM | |
All successful local user account deletion operations should be monitored, especially on high-value and critical hosts. The main reason why these operations are important is that there are not many local user account delete operations performed during a machine's lifecycle. Such operations might be an indicator of someone trying to:
- Remove all signs of compromise after the machine is compromised
- Delete some important accounts to facilitate performing denial of service attacks
- Hide or correct configuration errors or mistakes
This is not an exhaustive list. There can be other reasons for account deletion operations that are dependent on a variety of circumstances.
You should monitor for “4726: A user account was deleted” Audit Success
All unsuccessful local user account “access denied” deletion attempts must be monitored on all categories of hosts. All attempts to delete a local user account without having required permissions might be an indicator of malware activity or other suspicious activity. There is also a chance that someone forgets to run an application using administrative privileges, that is, with a nonelevated token, and the operation fails. This should be considered a false positive alert.
You should monitor for “4656: A handle to an object was requested” Audit FailureAccesses%%1537 (DELETE)Object TypeSAM_USER
Monitor for this using the following XPath filter:
*[System[band(Keywords,4503599627370496) and (EventID=4656)]] and*[EventData[Data[@Name='ObjectType'] and (Data='SAM_USER')]] and*[EventData[Data[@Name='AccessList']='%%1537 ']]
It is recommended that you have a list of accounts (domain and local) that are allowed to delete local user accounts. If you have such a list, you should compare every “4726: A user account was deleted” event's Subject
Refer to the examples for this monitoring recommendation in the “Monitoring Scenarios: Local User Account Creation” section earlier in this chapter.
It is recommended that you have a list of critical local user accounts that should never be deleted—for example, service accounts or accounts for scheduled tasks. Monitor all “4726: A user account was deleted” events where the Target Account
Local User Account Password Modification
You are able to detect two main operations with local user account passwords using the Windows security event log:
- Password reset: This operation is usually performed by another account. For a password reset operation you don't need to know the current account's password. If you have appropriate permissions, you can reset another account's password using built-in tools, such as the Computer Management snap-in.
- Password change: This operation allows you to change the password for the account. It requires entering the account's current password. The most common way to invoke the password change dialog is to press Alt+Ctrl+Del and click the “Change a password” menu item.
Successful Local User Account Password Reset
Listings 5-32 through 5-35 are the events that show in the Windows security event log when an account's password is reset.
The event in Listing 5-32 shows you that someone (SubjectDOMAINSAccountUsers�00003ECSetPassword (without knowledge of old password)
You will find the event in Listing 5-33 with the Password Last Set:
Listing 5-34 is the most important event, which informs you that the SubjectTarget Account
After the password was reset, there is no need to keep the handle to SAM account “DOMAINSAccountUsers�00003EC
Unsuccessful Local User Account Password Reset - Access Denied
When an account tries to reset the password for another user account without having the required permissions to perform that action, it will get an “Access Denied” response at the handle request phase. The event related to the “Access Denied” response is shown in Listing 5-36.
The NewUserREAD_CONTROLWRITE_DACWritePreferencesReadAccountWriteAccountSetPassword (without knowledge of old password)ListGroupsDOMAINSAccountUsers�00001F4Accesses
Unsuccessful Local User Account Password Reset - Other
One example of when a password reset failure event is generated is when a new account's password does not meet the local password group policy.
The events in Listings 5-37 through 5-39 are generated in the Windows security event log when a new account's password length is less than minimum password length defined in the local password group policy.
The event in Listing 5-38 informs you that SubjectTargetAccountAccount NameSecurity ID
Monitoring Scenarios: Password Reset
Useful events to monitor for successful and unsuccessful local user account password resets are shown in Table 5-8.
Table 5-8: Events to Monitor for Local User Account Password Resets
| SUCCESSFUL LOCAL ACCOUNT PASSWORD RESETS | ||
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4724: An attempt was made to reset an account's password | User Account Management | |
| UNSUCCESSFUL LOCAL ACCOUNT PASSWORD RESETS | ||
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4656: A handle to an object was requested | SAM | |
| 4724: An attempt was made to reset an account's password | User Account Management | |
If you know, for example, that the only local account on the host is the built-in local Administrator account and a password reset operation is not performed for this account at all or performed once a month at the same time/day for all hosts in the company, you should monitor for all password reset events for local user accounts.
All successful and unsuccessful password reset events for critical local accounts, such as built-in local Administrator or local service accounts, must be monitored. To make this task easier it is recommended that you have a list of such important local accounts. Here are some account examples that might be included in such a list:
- Built-in local Administrator account (or renamed local Administrator account)
- Fake (honeypot account) local Administrator account
- Any other accounts that have local administrative rights
- Local accounts for system services
- Local accounts for scheduled tasks
- Local accounts for Internet Informational Services (IIS) application pools
Monitor for these events:
- “4724: An attempt was made to reset an account's password”
Audit SuccessAudit FailureTarget Account - “4656: A handle to an object was requested”
Audit Failure
All unsuccessful password reset attempts due to insufficient permissions should be monitored. These attempts might indicate some suspicious activity or, also, might be a result of using an application without elevated privileges (such as not using “Run as administrator” option in Windows Explorer).
Because the password reset operation for local accounts is not a regular system or maintenance operation, it's recommended that you monitor for any successful and unsuccessful password reset attempts on all hosts, especially on critical and high business impact hosts.
Successful Local User Account Password Change
Now let's switch to password change operations. Multiple events in the Windows security event log appear when a user changes its password. Most of these events are related to the logon process right after the password change.
The most important event directly related to password change is shown in Listing 5-40.
This event informs you that the Administrator
Unsuccessful Local User Account Password Change
In all cases other than a successful local user account change, such as:
- User typed incorrect current account's password.
- User account has “User cannot change password” setting enabled and tries to change its password.
- New password does not match local password policy settings.
The message shown in Listing 5-41 is generated in the Windows security event log.
You will not find any details in the Windows security event log about why the password change operation failed.
Monitoring Scenarios: Password Change
Useful events to monitor for successful and unsuccessful local user account password changes are shown in Table 5-9.
Table 5-9: Events to Monitor for Local User Account Password Change
| SUCCESSFUL LOCAL ACCOUNT PASSWORD CHANGE | ||
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4723: An attempt was made to change an account's password | User Account Management | |
| UNSUCCESSFUL LOCAL ACCOUNT PASSWORD CHANGE | ||
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4723: An attempt was made to change an account's password | User Account Management | |
If you know that no local accounts should change their own password (all password reset operations are made using a script, application, scheduled task, or some other method), you should monitor for all successful and unsuccessful password change events.
Successful and unsuccessful password change events are important to monitor for high-privileged or critical accounts, such as local accounts with administrative rights, local service accounts, accounts for scheduled tasks, and so on.
Monitor for “4723: An attempt was made to change an account's password” Audit SuccessAudit FailureTarget AccountSubject
Local User Account Enabled/Disabled
Some local user accounts are disabled by default after operating system installation, such as the GuestAdministrator
Local User Account Was Enabled
After a local user account is enabled using the standard Computer Management snap-in or other methods, the events in Listings 5-42 through 5-45 will appear in the Windows security event log.
The event in Listing 5-42 shows you that someone (SubjectDOMAINSAccountUsers�00001F5GuestWriteAccount
Listing 5-43 is the main event, which informs you that SubjectTarget Account
Listing 5-44 shows an “A user account was changed” event, which contains the same information as the previous “A user account was enabled” event, because “Account enabled
Listing 5-45 shows that “the handle, opened for account enable operation, was closed.”
Local User Account Was Disabled
All events for a “disable account” operation are the same as for “enable account,” except that the “4722: A user account was enabled” event will be replaced by the event in Listing 5-46.
In this example the AdministratorGuest
Monitoring Scenarios: Account Enabled/Disabled
Useful events to monitor for account disable/enable status changes are listed in Table 5-10.
Table 5-10: Events to Monitor for Account Status Changes
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4722: A user account was enabled | User Account Management | |
| 4725: A user account was disabled | User Account Management | |
Monitor for “Account Enabled” events for local accounts that should never be enabled, such as:
- Guest
- Administrator (for Windows clients operating system family)
- DefaultAccount
- Any other accounts that must remain disabled
Monitor for “4722: A user account was enabled” Audit SuccessTarget Account
Monitor for “Account Disabled” events for critical local accounts that should always remain enabled, such as:
- Administrator (for Windows server operating system family)
- Service accounts
- Accounts for scheduled tasks
- Accounts for IIS application pools
- Depending on your situation, any other accounts that might also need to be always enabled
Monitor for “4725: A user account was disabled” Audit SuccessTarget Account
It's recommended that you have a list of accounts that have permissions to enable/disable other local accounts. For example, this list may contain only the local AdministratorAudit SuccessSubject
Local User Account Lockout Events
Local user lockout events appear in the Windows security event log if the number of account logon attempts using invalid password reached the “Account lockout threshold” local policy setting value.
The account lockout policy settings path is Computer ConfigurationWindows SettingsSecurity SettingsAccount PoliciesAccount Lockout Policy
Figure 5-5 shows an example of account lockout policy settings in Windows 10.
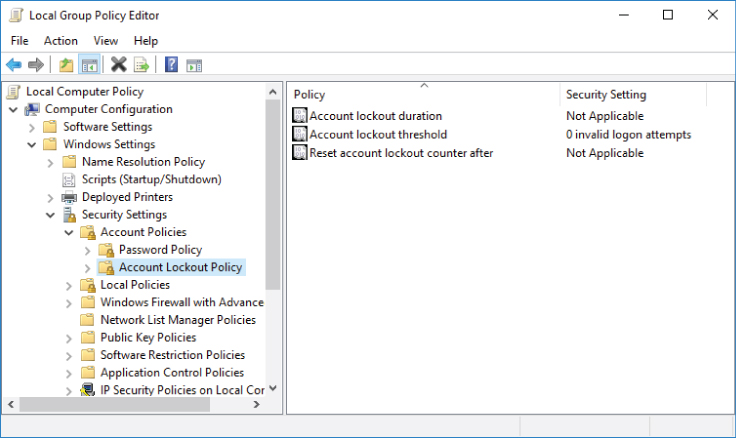
Figure 5-5: Account lockout group policy settings
By default, all non–domain-joined machines have the following account lockout policy settings:
- Account lockout duration: Not Applicable
- Account lockout threshold: 0
- Reset account lockout counter after: Not Applicable
Account lockout is usually not enabled on non–domain-joined machines and local accounts will never be locked out on such hosts.
Additionally, no matter which local account lockout policy settings are applied to the operating system, the built-in local Administrator
Local account lockout policy settings can be changed locally or applied from domain group policy, if the computer is joined to the domain.
Local User Account Lockout
No matter which logon type is used (Interactive, RemoteInteractive, Network, Service, Batch job, and so on) the events shown in Listings 5-47, 5-48, and 5-49 will be recorded in the Windows security event log.
The Logon TypeFailure ReasonUnknown user name or bad password
Event 4625 (shown in Listing 5-47) is the only source of the following information for account lockout operation:
- Logon type
- Name of the process that invoked authentication request
- IP address of remote workstation (for “remote” logon types, such as Network or RemoteInteractive logon types)
- Source port of the authentication connection request
- Logon Process name
- Authentication Package name
You can get more information about account logon events in Chapter 4.
The Subject
For “remote” logon types such as Network or RemoteInteractive, the Caller Computer Name
The event in Listing 5-49 informs you that the credential validation for Logon Account0xC000006A
All logon types for local accounts will use NTLM-family protocol, because the Kerberos authentication protocol is available only in Active Directory environments for domain accounts.
Source WorkstationSource WorkstationCaller Computer Name
Local User Account Unlock
Following are two typical scenarios for user account unlock operations:
- Manual unlock
- Automatic unlock after the number of minutes, defined in the “Account lockout duration” local policy setting, passed
A manual local user account unlock operation will trigger the events shown in Listings 5-50 through 5-53 in the Windows security event log.
The event in Listing 5-50 shows you that someone (SubjectDOMAINSAccountUsers�00003ECNewUserWriteAccount
Listing 5-51 shows that SubjectTarget Account
The “A user account was changed” event shown in Listing 5-52 is generated because the account has changed (become unlocked), but, unfortunately, there is no information about this change in the event itself.
No events are generated in Windows security event log for automatic local user account unlocks.
Monitoring Scenarios: Account Enabled/Disabled
Useful events to monitor for account lockout/unlock operations are shown in Table 5-11.
Table 5-11: Events to Monitor for Account Lockout and Unlock Operations
| SECURITY EVENT | EVENT SUBCATEGORY | EVENT TYPE |
| 4767: A user account was unlocked | User Account Management | |
| 4740: A user account was locked out | User Account Management | |
It's recommended that you monitor for all “4740: A user account was locked out” events for local user accounts, especially on high business impact and critical hosts. The main reason why these events are important is that local accounts are not often in use in comparison with domain user accounts, so any local account lockout event can be a sign of a password brute force or password guess attack.
If you do not expect anyone to manually unlock local user accounts, you should also track all “4767: A user account was unlocked” events.
Local User Account Change Events
Almost every change to a local user account will generate events in the Windows security event log, but it is not always possible to find what exactly was changed.
A local account change event contains detailed information about the following local user account properties:
- User Account Flags:
- User must change password at next logon
- User cannot change password
- Password never expires
- Account is disabled
- Account is locked out
- Account Name
- Full Name (Display Name)
- Profile tab:
- User Profile Path
- User Profile Logon Script
- User Profile Home Directory
- User Profile Home Drive
A change to the DescriptionGeneralDescription
Changes in the Member Of
For Windows server operating systems, changes in the following local user account tabs will invoke local account change event, but this event will not have any details about the change:
- Environment
- Sessions
- Remote Control
- Remote Desktop Services Profile
- Dial-in
For all changes to the fields in these tabs, the above User Parameters%%1792value changed, but not displayed>)
Local User Account Change Event
The events shown in Listings 5-54, 5-55, and 5-56 will appear in the Windows security event log after the account's “Password never expires” property has been enabled:
Listing 5-54 shows you that someone (SubjectDOMAINSAccountUsers�00003ECNewUserWriteAccount
Listing 5-55 shows who (SubjectTarget Account
The biggest problem with the “4738: A user account was changed” event is that the only fields that guarantee that their values have been changed are New UAC ValueUser Account Control
In the current example, the User Parameters%%1792<value changed, but not displayed>User Parameters
The only way to verify which field value was changed (except for the New UAC ValueUser Account Control
Table 5-12: Event Field Default Values
| EVENT FIELD | CONSTANT | VALUE |
| Home Directory | %%1793 | <value not set> |
| Home Drive | %%1793 | <value not set> |
| Script Path | %%1793 | <value not set> |
| Profile Path | %%1793 | <value not set> |
| User Parameters | %%1793 | |
| Display Name | <value not set> | Same as |
After the default value is changed, the only way to track which property was changed (again, except for the New UAC ValueUser Account Control
Basically speaking, the only event fields that show that something was really changed—and it's easy to verify—are New UAC ValueUser Account Control
The Old UAC ValueNew UAC ValueOld UAC ValueUser Account Control
Table 5-13 contains information that will help you in New UAC ValueOld UAC Value
Table 5-13: UAC Property Hexadecimal Values
| HEX VALUE | UNSET | SET |
| 0x01 0x02 | Account Enabled ‘Home Directory Required’ - Disabled | Account Disabled ‘Home Directory Required’ - Enabled |
| 0x04 | ‘Password Not Required’ - Disabled | ‘Password Not Required’ - Enabled |
| 0x08 | ‘Temp Duplicate Account’ - Disabled | ‘Temp Duplicate Account’ - Enabled |
| 0x10 | ‘Normal Account’ - Disabled | ‘Normal Account’ - Enabled |
| 0x20 | ‘MNS Logon Account’ - Disabled | ‘MNS Logon Account’ - Enabled |
| 0x40 | ‘Interdomain Trust Account’ - Disabled | ‘Interdomain Trust Account’ - Enabled |
| 0x80 | ‘Workstation Trust Account’ - Disabled | ‘Workstation Trust Account’ - Enabled |
| 0x100 | ‘Server Trust Account’ - Disabled | ‘Server Trust Account’ - Enabled |
| 0x200 | ‘Don't Expire Password’ - Disabled | ‘Don't Expire Password’ - Enabled |
| 0x400 | Account Unlocked | Account Locked |
| 0x800 | ‘Encrypted Text Password Allowed’ - Disabled | ‘Encrypted Text Password Allowed’ - Enabled |
| 0x1000 | ‘Smartcard Required’ - Disabled | ‘Smartcard Required’ - Enabled |
| 0x2000 | ‘Trusted For Delegation’ - Disabled | ‘Trusted For Delegation’ - Enabled |
| 0x4000 | ‘Not Delegated’ - Disabled | ‘Not Delegated’ - Enabled |
| 0x8000 | ‘Use DES Key Only’ - Disabled | ‘Use DES Key Only’ - Enabled |
| 0x10000 | ‘Don't Require Preauth’ - Disabled | ‘Don't Require Preauth’ - Enabled |
| 0x20000 | ‘Password Expired’ - Disabled | ‘Password Expired’ - Enabled |
| 0x40000 | ‘Trusted To Authenticate For Delegation’ - Disabled | ‘Trusted To Authenticate For Delegation’ - Enabled |
| 0x80000 | ‘Exclude Authorization Information’ - Disabled | ‘Exclude Authorization Information’ - Enabled |
| 0x100000 | ‘Undefined UserAccountControl Bit 20’ - Disabled | ‘Undefined UserAccountControl Bit 20’ - Enabled |
| 0x200000 | ‘Protect Kerberos Service Tickets with AES Keys’ - Disabled | ‘Protect Kerberos Service Tickets with AES Keys’ - Enabled |
Basically speaking, the UAC attribute is a bitmask and UAC fields in the “4738: A user account was changed” event just show you its previous and current hexadecimal values.
In the current example, the Old UAC ValueNew UAC ValueUser Account Control
The following “4738: A user account was changed” event fields are not applicable to local user accounts and always should have default values set:
User Principal Name: -User Workstations: %%1793 (<value not set>)Account Expires: %%1794 (<never>)AllowedToDelegateTo: -SID History: -Logon Hours: %%1797 (All)
For some changes, for example changes in a user's account Profile tab, two identical “4738: A user account was changed” events will be generated.
For changes in the Environment, Sessions, Remote Control, Remote Desktop Services Profile, or Dial-in user account tabs, an additional “empty” “4738: A user account was changed” event will be generated as shown in Figure 5-6. This is applicable only to Windows servers operating systems.

Figure 5-6: Empty 4738 event
Local User Account Name Change Event
A dedicated event is generated in the Windows security event log for local account name change operations.
After a local account name has been changed, the events in this section will appear in Windows security event log.
The event in Listing 5-57 shows who (SubjectTarget Account
The 4738 event (Listing 5-58) also shows the new account name value for account NewUser
Monitoring Scenarios: Account Changes
Table 5-14 shows useful events to monitor for account change operations.
Table 5-14: Events to Monitor for Account Change Operations
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4738: A user account was changed | User Account Management | |
| 4782: The name of an account was changed | User Account Management | |
It's not typical to change local account names, except for renaming the built-in local Administrator
Any change to high-privileged and important local accounts should be monitored. Examples of such accounts are:
- Built-in local Administrator account (or renamed local Administrator account)
- Fake (honeypot account) local Administrator account
- Any other accounts that have local administrative rights
- Guest account
- Local accounts for system services
- Local accounts for scheduled tasks
- Local accounts for Internet Informational Services (IIS) application pools
Monitor for “4738: A user account was changed” Audit SuccessTarget Account
On critical and high-value hosts, monitor for any “4738: A user account was changed” event.
It's recommended that you have a list of accounts that have permissions to change other local accounts. For example, only members of the local Administrators security group can make such changes.
Monitor for “4738: A user account was changed” Audit SuccessSubject
Monitor for all events showing that the “Password never expires” setting was enabled, but it should not have been, or when that setting was disabled, but must be enabled.
Monitor for “4738: A user account was changed” Audit SuccessNew UAC Value
Monitor for all events showing that the “User cannot change password” setting was enabled, but should not have been, or when that setting was disabled, but must be enabled.
Monitor for “4738: A user account was changed” Audit SuccessNew UAC Value
The following XPath filter will filter all “4738: A user account was changed” events where the New UAC Value
*[System[(EventID=4738)]] and *[EventData[Data[@Name='NewUacValue']!='0x10']] and *[EventData[Data[@Name='NewUacValue'] !='-']]
Blank Password Existence Validation
An internal API function, SamQueryInformationUserUserLogonUIInformation
If the following requirements are met, a 4797 event is generated in the security event log:
- The
SamQueryInformationUserUserLogonUIInformation- You are querying a user who is not you.
- You are neither a local administrator nor running with
SeTcbPrivilege
Listing 4.50 is an example of a 4797 event.
The SubjectSamQueryInformationUser
The Caller Workstation
The Target Account Name
The Target Account Domain
If you want to know what's causing this, you need to figure out what is calling SamQueryInformationUserSamQueryInformationUser
