CHAPTER 2
Auditing Subsystem Architecture
The Windows auditing subsystem was introduced in the earliest Microsoft Windows versions. It provides the ability to report auditing events for kernel- and user-mode applications and components.
In this chapter you will find information about legacy and advanced auditing settings, Windows auditing group policy settings related to auditing, auditing subsystem architecture, and security event structure.
Legacy Auditing Settings
Legacy auditing was the only available security auditing mechanism on pre-Vista Windows systems. It was not as agile as the new advanced auditing introduced in Windows Vista, but still was able to perform its function.
Legacy auditing settings can be configured using Windows group policy settings. No built-in command-line tools, such as auditpolauditpolauditusr
Group policy settings for legacy auditing categories are located under the Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesAudit Policygpedit.msc
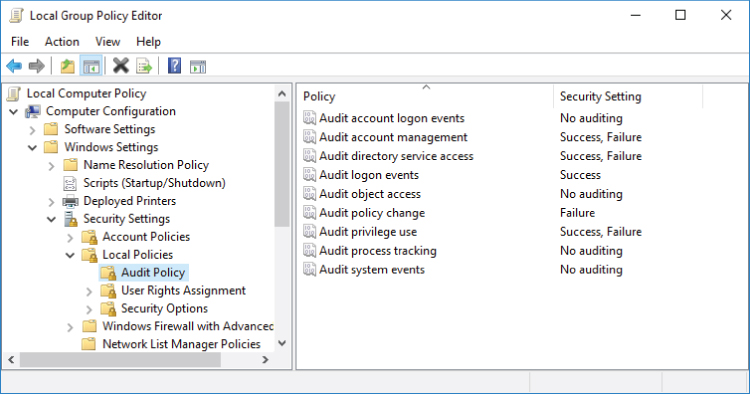
Figure 2-1: Legacy auditing group policy settings
Table 2-1 shows available legacy auditing categories and their descriptions.
Table 2-1: Legacy Auditing Categories
| CATEGORY NAME | DESCRIPTION |
| Audit account logon events | Audit NTLM-family and Kerberos protocols credential validation operations. On domain controllers this category enables Kerberos AS_REQ, TGS_REQ, and AP_REQ requests auditing. |
| Audit account management | Audit user, computer, security group, distribution group, and Authorization Manager (AzMan) application group management operations. This category also provides monitoring of password hash import operations during Active Directory account migration and Password Policy Check API calls. |
| Audit directory services access | Audit Active Directory object modifications, object access attempts, and replication operations. |
| Audit logon events | Audit account logon, logoff, and lockout events. Provides detailed auditing for IPsec modes. Audit logon events for members of special groups (see Chapter 4 for more details) and special privileges owners (Chapter 11). Audit workstation lockouts, terminal session connections, and screensaver operations. Also enables auditing on Network Policy Servers (NPS). |
| Audit object access | Audit filesystem, registry, kernel objects, handles, file shares, and filtering platform operations. Also enables auditing for Active Directory Certificate Services role operations. |
| Audit policy change | Audit authorization, authentication, filtering platform, audit and Windows firewall policy changes. |
| Audit privilege use | Audit use of sensitive and nonsensitive privileges. |
| Audit process tracking | Audit process creation, termination, and Data Protection API (DPAPI) operations. |
| Audit system events | Audit security-related changes and operations, IPsec driver events, Windows firewall service and driver events, Windows startups, and system time changes. |
Auditing settings are stored in the Local Security Authority (LSA) policy database. The LSA policy database is located in the HKLMSECURITYPolicyDefaultHKLMSECURITYPolicyPolAdtEv
Events generated in the Windows security event log by legacy auditing categories have ID numbers that are between 500 and 900. Legacy auditing events are available only in pre-Vista Windows operating systems. In more recent Windows versions, legacy events are replaced by new events with event ID numbers between 4000 and 7000.
Legacy auditing policies can be set to one of the following states:
- Success: Only
Audit Success - Failure: Only
Audit Failure - Success, Failure: Both
Audit SuccessAudit Failure - No auditing: In legacy audit policy settings, “No auditing” is not the same as “No Auditing” in advanced audit policy settings. In the legacy audit settings, No auditing means “Not Configured.” That means that you have not set a value for that audit setting. For example, if you set a setting to Success and later switch to “No auditing,” the value will still be the same as before switching to “No auditing” (that is, it will be Success).
Legacy auditing settings “tattoo” the registry, which means that they are applied directly to auditing subsystem registry keys, not to temporal group policy keys.
This book does not go any deeper into legacy auditing settings and events because modern Windows systems have advanced auditing settings available, which allows for configuring more granular auditing settings using subcategories. There is no real value in using legacy audit settings on modern Windows versions. Later in this book you will find information about relationships between legacy and advanced auditing settings on modern Windows systems and how they affect each other.
Advanced Auditing Settings
Prior to Windows Server 2008 and Windows Vista it was difficult to exclude unneeded events from auditing. This was because auditing included nine categories and, for example, if you enabled Object Access auditing it would start to collect data for registry, file system, file share, and other object operations. However, in most cases you don't need to audit all of those.
Advanced audit introduced subcategories for each of the nine legacy categories, and you can configure them to include or exclude security events. The general category names were also changed in comparison with legacy auditing.
Advanced audit settings can be configured using group policy settings for operating system versions starting from Windows 7 or Windows Server 2008 R2. Auditing settings can also be configured using the built-in auditpolauditpolauditpol
Group policy settings for advanced audit categories were first introduced for Windows 7 and Windows Server 2008 R2 systems. They are located under the Computer ConfigurationWindows SettingsSecurity SettingsAdvanced Audit Policy ConfigurationAudit Policies

Figure 2-2: Advanced audit group policy settings
You will find detailed explanations of each advanced audit subcategory and recommendations for workstations, servers, and domain controllers in Chapter 3.
Advanced audit subcategories can be set to one of the following states:
- Success: Only
Audit Success - Failure: Only
Audit Failure - Success, Failure: Both
Audit SuccessAudit Failure - No Auditing: Auditing for the subcategory is disabled. No events will be generated.
- Not Configured: No changes are made to the advanced audit policy. The host will use previously applied settings.
Each advanced audit category and subcategory has its own global unique identifier (GUID). These GUIDs are consistent among all Microsoft Windows versions. All GUIDs have the following format:
- Category:
XXXXXXXX-797A-11D9-BED3-505054503030XXXXXXXX - Subcategory:
XXXXXXXX-69AE-11D9-BED3-505054503030XXXXXXXX
To view all GUIDs for categories and subcategories use the following command in the Administrator ➪ Command Prompt window: auditpol /list /subcategory:* /vauditpol /list

Figure 2-3: Listing auditing categories and subcategories GUIDs using the auditpol command-line tool
The Windows group policy editor (gpedit.mscComputer ConfigurationWindows SettingsSecurity SettingsAdvanced Audit Policy ConfigurationAudit Policies
The following sections cover different methods for configuring advanced audit settings on a machine.
Set Advanced Audit Settings via Local Group Policy
If advanced audit settings are changed in the local group policy, the following file is modified:
%WINDIR%system32grouppolicymachinemicrosoftwindows ntauditaudit.csv
If no advanced audit settings were applied to the system before, the audit.csv file will be created. The grouppolicy
Figure 2-4 shows an example of the audit.csv

Figure 2-4: Audit.csv file content example
The Machine Name
The Inclusion Settings
The Exclusion
The Setting ValueInclusion Setting
- 0: No Auditing
- 1: Success
- 2: Failure
- 3: Success and Failure
After the audit.csvHKLMSECURITYPolicyDefaultHKLMSECURITYPolicyPolAdtEv
Set Advanced Audit Settings via Domain Group Policy
Advanced audit settings modification using domain group policy is similar to the process for local group policy that was explained in the previous section. After domain policy is applied, group policy settings are copied locally to the %WINDIR%GroupPolicyDataStore�sysvolDOMAIN_NAMEPoliciesgroup_policy_foldermachinemicrosoftwindows ntauditaudit.csvaudit.csv
C:WindowsSystem32GroupPolicyDataStore�sysvolhqcorp.localPolicies{6AC1786C-016F-11D2-945F-00C04fB984F9}MachineMicrosoftWindows NTAuditaudit.csv
The audit.csv
After the audit.csv
Set Advanced Audit Settings in the Local Security Authority (LSA) Policy Database
The only way to modify advanced audit settings in the LSA Policy Database using built-in Windows tools is to use auditpol
To modify auditing settings for a subcategory, you need to execute the following command:
auditpol /set /subcategory:SUBCATEGORY_GUID_OR_NAME {options}
This command should be executed in an elevated command-line processor, not PowerShell. You already know how to find a GUID for a subcategory. The {options}
/success:/failure:
These two parameters may have one of the following two values assigned:
enable:disable:
For example, if you need to enable Success auditing and disable Failure auditing (assuming it was enabled) for the Logoff subcategory, you may use one of the following commands:
auditpol /set /subcategory:{0CCE9216-69AE-11D9-BED3-505054503030} /success:enable /failure:disableauditpol /set /subcategory:"Logoff" /success:enable /failure:disable
It is also possible to change settings for multiple subcategories by listing them one after another, separated by a comma: /subcategory:{0CCE9216-69AE-11D9-BED3-505054503030},{0CCE9240-69AE-11D9-BED3-505054503030}
Read Current LSA Policy Database Advanced Audit Policy Settings
The only way to get current advanced audit settings directly from a local LSA Policy Database using built-in Windows tools is to use the auditpol
You can use the following command to get current settings:
auditpol /get /category:*
Advanced Audit Policies Enforcement and Legacy Policies Rollback
The new “Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings” group policy setting was introduced for the Windows Vista and Windows Server 2008 operating systems, which enforce the use of new advanced audit subcategories instead of legacy categories.
This group policy setting is located under the ComputerConfigurationWindows SettingsSecurity SettingsLocal PoliciesSecurity OptionsHKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsascenoapplylegacyauditpolicy
Possible values:
- 0: Disabled
- 1: Enabled
Table 2-2 contains a dependency scheme between legacy and advanced audit categories for operating systems starting from Windows Vista and Windows Server 2008.
Table 2-2: Dependency between Legacy Audit and Advanced Audit Categories
| LEGACY CATEGORY | ADVANCED CATEGORY |
| Audit account logon events | Account Logon |
| Audit account management | Account Management |
| Audit directory services access | DS Access |
| Audit logon events | Logon/Logoff |
| Audit object access | Object Access |
| Audit policy change | Policy Change |
| Audit privilege use | Privilege Use |
| Audit process tracking | Detailed Tracking |
| Audit system events | System |
For example, if the “Audit policy change” category is enabled for Success in legacy audit settings and some additional requirements (discussed in the following section) are met to permit the use of legacy settings, then all subcategories under the Policy Change advanced category will be enabled for Success auditing.
Switch from Advanced Audit Settings to Legacy Settings
Two main requirements must be satisfied to switch from advanced audit back to legacy audit:
- Disable the “Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings” group policy setting.
- Delete the
Audit.csv%WINDIR%system32grouppolicymachinemicrosoftwindows ntaudit
If you need to set a subcategory to the “disabled state”, you can use one of the following options:
- Use the advanced audit “No Auditing” group policy setting value.
- Use the
auditpol /set /subcategory:SUBCATEGORY_GUID_OR_NAME /failure:disable /success:disable - Use the
auditpol /clear
Switch from Legacy Audit Settings to Advanced Settings
To switch from legacy audit back to advanced audit, perform the following steps:
- Enable the “Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings” group policy setting.
- The
Audit.csv%WINDIR%system32grouppolicymachinemicrosoftwindows ntaudit
Windows Auditing Group Policy Settings
Multiple additional group policy settings are related to the Windows auditing subsystem. In this section you will find detailed information about them.
Manage Auditing and Security Log
The “Manage auditing and security log” group policy setting controls the SeSecurityPrivilegeSeSecurityPrivilege
SeSecurityPrivilege
This group policy setting is located at the following path: Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesUser Rights Assignment
See Chapter 11 for more information about user rights and privileges.
Generate Security Audits
The “Generate security audits” group policy setting controls the SeAuditPrivilege
SeAuditPrivilegeReportEvent()AdvApi32.dll
This group policy setting is located at the following path: Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesUser Rights Assignment
Security Auditing Policy Security Descriptor
Security auditing policy has its own security descriptor that controls access to it. To view it, use the auditpol /get /sdD:
D:(A;;DCSWRPDTRC;;;BA)(A;;DCSWRPDTRC;;;SY)
A:DCSWRPDTRC:DC:SW:RP:DT:RC:
BA:SY:
By default, the preceding security descriptor is set for the local security auditing policy on all Windows versions starting with Windows Vista.
You can set the security descriptor for the local auditing policy using the auditpol /set /sd:DESCRIPTOR_SDDL_STRING
To view or set the security descriptor for the local auditing policy using the auditpolSeSecurityPrivilege
There is no group policy setting you can use to set the local auditing policy security descriptor. It is stored in the following registry key: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsaAuditAuditPolicyAuditPolicySD
Group Policy: “Audit: Shut Down System Immediately If Unable to Log Security Audits”
If this group policy setting is enabled, it causes the system to stop if a security audit event cannot be logged for any reason. It is a requirement for Trusted Computer System Evaluation Criteria (TCSEC)-C2 and Common Criteria certification to prevent auditable events from occurring if the audit system is unable to log them.
This policy modifies the following registry key: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsacrashonauditfail
0:1:
It is also possible to modify the crashonauditfailauditpol
- Disable:
auditpol /set /option:CrashOnAuditFail /value:disable - Enable:
auditpol /set /option:CrashOnAuditFail /value:enable
If the crashonauditfail
The 4906 event shows the new value for the crashonauditfail
If, for example, crashonauditfail1
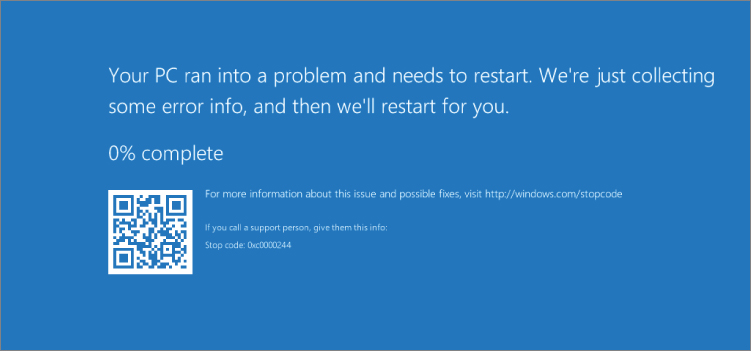
Figure 2-5: Windows Server 2016 CrashOnAuditFail blue screen
Stop code 0xc0000244 has the following meaning: {Audit Failed} An attempt to generate a security audit failed.
The group policy setting path is Computer ConfigurationPoliciesWindows SettingsSecurity SettingsLocal PoliciesSecurity Options
Group Policy: Protected Event Logging
Protected Event Logging is a new feature that allows Windows components and applications to encrypt their event logs using the Cryptographic Message Syntax (CMS) standard and asymmetric cryptography. For now the only application that supports protected event logging in Windows is PowerShell v5 and higher. Using this feature, PowerShell can write encrypted events in the PowerShell event log.
To enable this feature, you need to provide a certificate with a public key that will be used for encryption. Then you can use the Unprotect-CmsMessage
The “Protected Event Logging” group policy setting is supported only by Windows 10 and Windows Server 2016. It is located at the following group policy path: Computer ConfigurationPoliciesAdministrative TemplatesWindows ComponentsEvent Logging
Group Policy: “Audit: Audit the Use of Backup and Restore Privilege”
The “Audit: Audit the use of Backup and Restore privilege” group policy setting allows you to enable full privilege use auditing, which includes the SeBackupPrivilegeSeRestorePrivilege
The associated registry value is HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsafullprivilegeauditing
40:41:
The group policy setting path is Computer ConfigurationPoliciesWindows SettingsSecurity SettingsLocal PoliciesSecurity Options
Group Policy: “Audit: Audit the Access of Global System Objects”
The “Audit: Audit the access of global system objects” group policy setting works in conjunction with the “Audit object access” auditing subcategory setting. It enables default SACL on global system objects.
Global system objects are temporary kernel objects that have had names assigned to them by the application or system component that created them. These objects are most commonly used to synchronize multiple applications or multiple parts of a complex application. Because they have names, these objects are global in scope and, therefore, visible to all processes on the device. These objects all have a security descriptor; but typically, they do not have a SACL assigned. If you enable this policy setting and it takes effect at startup time, the kernel assigns a SACL to these objects when they are created. This policy setting does not affect container objects.
Usually, detailed access monitoring of access requests to global system objects, such as mutexes and semaphores, is not required and also generates a high volume of events.
This group policy setting is located at the following path: Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesSecurity Options
The associated registry value is HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsaauditbaseobjects
0:1:
Audit the Access of Global System Container Objects
The “Audit: Audit the access of global system objects” policy setting discussed earlier does not enable auditing for global system container objects. Container objects might contain other global system objects. You can modify the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsa, auditbasedirectories
0:1:
Windows Event Log Service: Security Event Log Settings
The Windows Event Log service has its own settings for the security event log. These settings are stored in the local registry under the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesEventLogSecurity
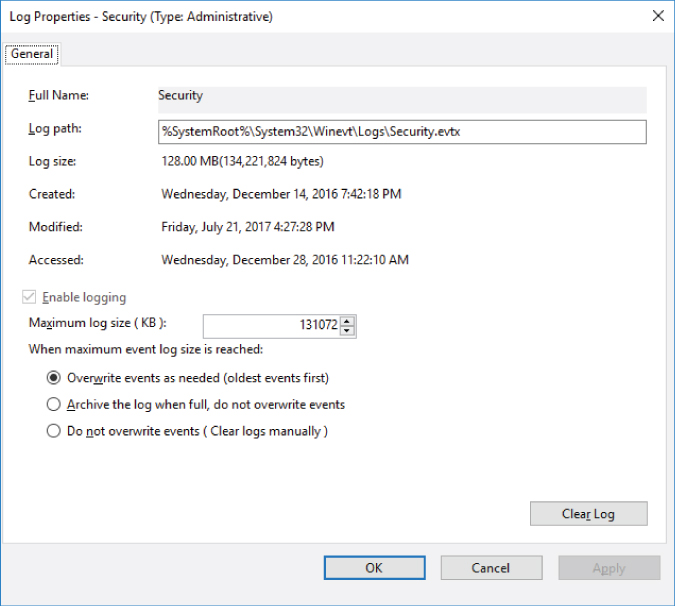
Figure 2-6: Event Viewer security event log settings
The group policy settings are located under the following group policy path: Computer Configuration PoliciesAdministrative TemplatesWindows ComponentsEvent Log ServiceSecurity
The following sections discuss the most common security event log settings.
Changing the Maximum Security Event Log File Size
You can use two group policy settings to change the maximum security event log file size:
Computer ConfigurationPoliciesAdministrative TemplatesWindows ComponentsEvent Log ServiceSecuritySpecify the maximum log file size (KB)Computer ConfigurationPoliciesWindows SettingsSecurity SettingsEvent LogMaximum security log size
These group policy settings allow you to configure the maximum size of the security event log file. The size is specified in kilobytes and should be between 1,028 kilobytes (1.07 megabyte) and 2,147,483,647 kilobytes (2 terabytes). The group policy interface for the “Specify the maximum log file size (KB)” setting does not allow you to set a value smaller than 20,480 kilobytes for this setting. The group policy interface for the “Maximum security log size” setting allows you to specify the range for the log size from 64 KB to 4,194,240 KB. If you set the size to any value between 64 KB and 1,028 KB, it will be recorded in the registry as 1,028 KB.
If both the “Specify the maximum log file size (KB)” and “Maximum security log size” settings are set in the same group policy, the “Specify the maximum log file size (KB)” setting has higher priority.
The default security event log size for Windows Server 2016, Windows Server 2012 R2, Windows Server 2012, and Windows Server 2008 R2 is 128 MB (131,072 KB).
The default security event log size for Windows Server 10, Windows 8.1, Windows 8, and Windows 7 is 20 MB (20,480 KB).
These defaults are usually not enough to store security events for a long period of time. Your security monitoring policies determine how long the events should be stored on the machine after they are generated. It also depends on whether you are using a centralized event collection and storage solution.
The associated registry value for these policy settings is HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesEventLogSecurityMaxSize
The associated event log properties setting is Log size
Group Policy: Control Event Log Behavior When the Log File Reaches Its Maximum Size
This group policy setting allows you to configure overwrite policy for events in the security event log. By default new events overwrite the oldest events in the log, but you can change this behavior and control it by enabling this policy setting.
The associated registry value is HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesEventLogSecurityRetention
0:0xffffffff:
The path to this group policy setting is Computer ConfigurationPoliciesWindows SettingsSecurity SettingsEvent Log
If this policy is disabled, new security events overwrite the oldest events. This is the default setting for all recent Windows versions.
If this policy is enabled, then depending on the “Back up log automatically when full” group policy setting (AutoBackupLogFilesAutoBackupLogFiles
AutoBackupLogFiles = 1:The associated event log properties setting is “Archive the log when full, do not overwrite events”.
AutoBackupLogFiles = 0:The associated event log properties setting is “Do not overwrite events (Clear logs manually)”.
Group Policy: Back Up Log Automatically When Full
This group policy setting allows the Windows event log service to back up a security event log file after the current file reaches its maximum size. For this policy setting to take effect, the “Control event log behavior when the log file reaches its maximum size” group policy setting should be enabled.
Archived security event log files are stored at the same location as the original file and named using the following convention:
Archive-FILENAME-YYYY-MM-DD-hh-mm-ss-msec
FILENAMEmsec
The YYYY-MM-DD-hh-mm-ss-msecArchive-Security-2017-07-22-10-20-21-127.evtx
Each time the event log is archived, it is cleared and the event shown in Listing 2-2 is recorded in the log right after it was archived.
The 1105 event shows the name of the log that was archived (LogFile
The associated registry value is HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesEventLogSecurity, AutoBackupLogFiles
0:1:
The associated event log properties setting is the Log path
The path to this group policy setting is Computer ConfigurationPoliciesWindows SettingsSecurity SettingsEvent Log
Group Policy: Control the Location of the Log File
This group policy setting allows you to specify the path and filename for a security log file. If this setting is disabled or not configured, the file is stored in the default location: %SystemRoot%System32WinevtLogsSecurity.evtx
It is recommended that you use the standard .evtx
Only local filesystem paths are allowed; any UNC (\File:\
The associated registry value is HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesEventLogSecurityFile
The associated event log properties setting is “Archive the log when full, do not overwrite events” (refer to Figure 2-6).
The path to this group policy setting is Computer ConfigurationPoliciesWindows SettingsSecurity SettingsEvent Log
Security Event Log Security Descriptor
Security event log security descriptor can be configured using the “Configure log access” group policy setting. But starting from Windows 10 and Windows Server 2016 the new “Configure log access (legacy)” policy setting was introduced. The path to this group policy setting is Computer ConfigurationPoliciesWindows SettingsSecurity SettingsEvent Log
Table 2-3 shows differences between operating system versions for security event access control settings.
Table 2-3: Security Event Log Access Control Policies
| OPERATING SYSTEM | “CONFIGURE LOG ACCESS” REGISTRY VALUE | “CONFIGURE LOG ACCESS (LEGACY)” REGISTRY VALUE |
| Pre-Windows 10 and pre-Windows Server 2016 | |
Group policy setting does not exist |
| Windows 10 and Windows Server 2016 | |
|
For Windows 10 and Windows Server 2016 it is recommended to set both policies for maximum application compatibility.
The “Configure log access” and “Configure log access (legacy)” group policy settings allow you to modify access rights for the security event log. The value for these group policy settings should be in Security Descriptor Definition Language (SDDL) format. SDDL format is described in Chapter 10.
To view current security event log security descriptor on the machine, use the wevtutil gl securitychannelAccesswevtutil gl security
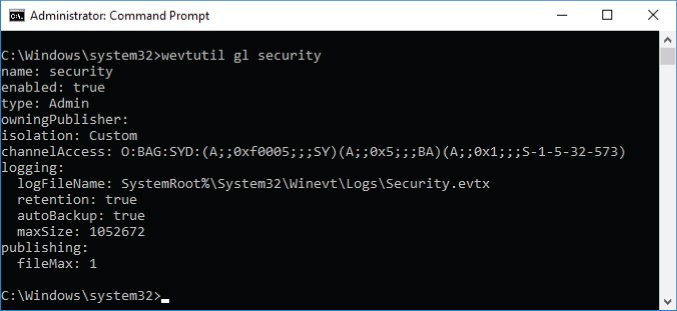
Figure 2-7: View current security event log access rights using the wevtutil tool
Let's decode the SDDL string shown in Figure 2-7: O:BAG:SYD:(A;;0xf0005;;;SY)(A;;0x5;;;BA)(A;;0x1;;;S-1-5-32-573)
O:BA:G:SY:D::(A;;0xf0005;;;SY)A:0xf0005:SY:
(A;;0x5;;;BA)A:0x5:BA:
(A;;0x1;;;S-1-5-32-573)A:0x1:S-1-5-32-573:
Table 2-4 contains information about event log access permissions that may help you to understand SDDL ACEs.
Table 2-4: Event Log Access Rights
| HEXADECIMAL VALUE | ACCESS RIGHT |
| 0x1 | Read |
| 0x2 | Write |
| 0x4 | Clear |
| 0xf0000 | Full Access |
The default value for security event log security descriptor depends on the operating system version. For all Windows versions starting from Windows Vista and Windows Server 2008 the default security descriptor is always the same as shown in Figure 2-7:
- Local System: Full access
- Built-in Administrators: Read, Clear
- Event Log Readers: Read
Any Write (0x2SeAuditPrivilege
Guest and Anonymous Access to the Security Event Log
The registry key value HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesEventLogSecurityRestrictGuestAccessComputer ConfigurationPoliciesWindows SettingsSecurity SettingsEvent LogRestrictGuestAccessRestrictGuestAccess
Windows Auditing Architecture
The Windows auditing subsystem is distributed between Windows kernel-mode and user-mode components. Both modes have components that report auditing events, which is why the auditing subsystem is present in both modes—this prevents switching between modes.
Two main flows in the auditing subsystem involve multiple components to support main auditing functionality:
- Policy flow: Operations with auditing policy, such as getting current auditing policy settings or changing the settings.
- Event flow: Event reporting and recording.
The following sections discuss the event and policy flow components.
Windows Auditing Policy Flow
Figure 2-8 shows the policy flow components and interactions between them. The numbers in the figure match the step numbers in the discussions that follow.

Figure 2-8: Auditing subsystem policy flow
An auditing policy management application, such as auditpol.exegpedit.mscadvapi32.dll
LsaSetInformationPolicy (PolicyAuditEventsInformation):LsaQueryInformationPolicy (PolicyAuditEventsInformation):AuditSetPolicy:AuditQueryPolicy:
Some differences in the process take place prior to Step 1 related to processing of legacy and advanced audit policies involving the audit.csv
LsaSetInformationPolicy and LsaQueryInformationPolicy Functions Route
This route is shown as a dotted line and filled circles in Figure 2-8.
Step 1. The LsaSetInformationPolicyLsaQueryInformationPolicyLSASS.exe
Step 2. Changes or information queries are performed against the LSA policy database through the RPC legacy policy interface. The LSA policy database is located in the HKLMSECURITYPolicyDefaultHKLMSECURITYPolicyPolAdtEv
Step 3. Policy changes are then sent to the RPC GAP interface which, as part of Step 4, informs the Format & Policy component about the change.
Step 5. The Format & Policy component acts as an intermediate agent between LSASS (user mode) and another Format & Policy component in the NTOSKRNL process. Communications between them are performed via Asynchronous Local Inter-Process Communication (ALPC) tunnels, which are discussed in Chapter 4. At this step, the LSASS process informs the NTOSKRNL process about policy changes.
NTOSKRNL.exeSeAccessCheckSeAuditSeAudit
Step 6. Changes are replicated to the kernel mode cached copy of the auditing settings (PolAdtEv key) from the LSA Policy Database.
AuditSetPolicy and AuditQueryPolicy Functions Route
This route is shown as a solid line and white circles in Figure 2-8.
Step 1. The AuditSetPolicyAuditQueryPolicyLSASS.exe
Steps 2–3. A change request or information query is sent to the LSA Policy Database through RPC legacy policy interface.
Steps 4–6. These steps are the same as steps 4–6 for the LsaSetInformationPolicyLsaQueryInformationPolicy
Windows Auditing Event Flow
Figure 2-9 shows the event flow components and interactions between them.
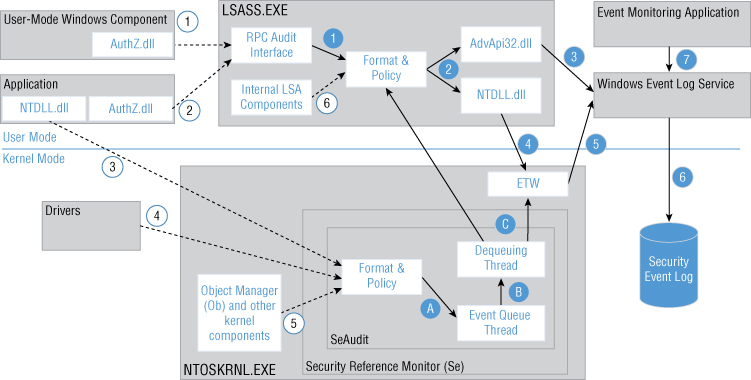
Figure 2-9: Auditing subsystem event flow
Multiple components report security events in both kernel and user modes. In Figure 2-9 these reporting methods and components are numbered using white circles and dotted lines:
- User-Mode Windows Components: Multiple Windows components use private APIs from the
AuthZ.dllLSASS.exe - Applications (User Mode): Windows applications may use multiple public
AuthZ.dllAuthzReportSecurityEventAuthzReportSecurityEventFromParamsLSASS.exe - Applications (reporting event for Kernel Mode): User-mode applications can also trigger security events by calling
NTDLL.dllNT*AuditAlarmNtOpenObjectAuditAlarmNtPrivilegeObjectAuditAlarmSeAudit - Drivers: Drivers report events in the kernel mode using kernel routines such as
SeReportSecurityEventSeReportSecurityEventWithSubCategorySeAudit - Object Manager and other kernel components: Kernel components use private kernel-mode audit APIs to report a security event.
- Internal LSA components: Internal LSA components may also report a security event using internal LSA audit APIs.
There are two main event flows: events reported to LSASS.exeNTOSKRNL.exe
LSASS.EXE Security Event Flow
User-mode Windows components and regular applications report security events using AuthZ.dllAutZ.dll
Step 1. The RPC audit interface redirects requests to the Format & Policy module, which was discussed earlier.
Step 2. There are two main methods that LSASS may use to send an event to the Windows Event Log service for further processing:
- Step 3:
AdvApi32.dllReportEvent() - Step 4:
NTDLL.dll
Step 5. Event Tracing for Windows (ETW) provides a mechanism to trace and log events that are raised by user-mode applications and kernel-mode drivers. ETW is implemented in the Windows operating system and provides developers a fast, reliable, and versatile set of event tracing features. ETW functionality is implemented as a kernel-mode component of the NTOSKRNL.exe
Step 6. The Windows Event Log service writes events to the security event log.
Step 7. Event monitoring applications, such as Windows Event Viewer, may use public AdvApi32.dllOpenEventLogReadEventLog
NTOSKRNL.EXE Security Event Flow
Kernel-mode security event reporting functionality is implemented in the NTOSKRNL.EXE
Step A. An audit event generation call is sent to the event queue. The event queue is implemented as a separate thread and performs event generation. If the queue is full, the component that sent an event generation call will be blocked until the queue can process new events.
Step B. After an event is processed it goes to the separate dequeuing thread.
Step C. The dequeuing thread sends the event to ETW or LSASS for further processing. Most of the time ETW is used, which does not require switching between kernel and user modes.
Security Event Structure
Each security event has the following XML structure:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event"><System><Provider Name=" " Guid=""/><EventID></EventID><Version></Version><Level></Level><Task></Task><Opcode></Opcode><Keywords></Keywords><TimeCreated SystemTime=""/><EventRecordID></EventRecordID><Correlation/><Execution ProcessID="" ThreadID=""/><Channel> </Channel><Computer> </Computer><Security/></System><EventData><Data Name=""> </Data></EventData></Event>
The root <Event>xmlnsschemas.microsoft.com/win/2004/08/events/event
Within the <Event>
<System>:<System>schemas.microsoft.com/win/2004/08/events/event<EventData>:<Data></Data><Data></Data>- The
<Data></Data>Name<Data></Data>Security ID parameter<Data Name="SubjectUserSid">S-1-5-18</Data>
- The
The remainder of this section discusses each event's element.
The <Provider /><Provider />
- Name: Name of the provider.
- Guid: GUID of the provider.
Each event Provider has a name and unique identifier (GUID) associated to it. To list all event Providers registered with the ETW subsystem you can use the following command: logman query providers
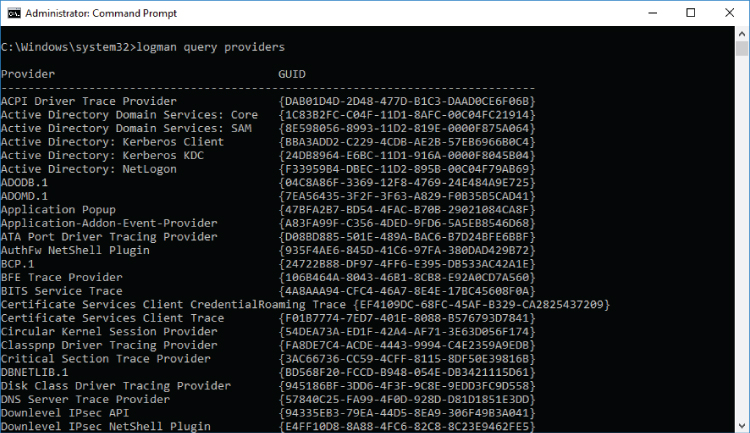
Figure 2-10: Windows Server 2016 event Providers list example
The default Windows security auditing provider is Microsoft-Windows-Security-Auditing. Its GUID is {54849625-5478-4994-A5BA-3E3B0328C30D}
The <EventID></EventID>
The <Version></Version>
Table 2-5: Security Events with Version 1 and Version 2
| EVENT ID | VERSION | NEW VERSION INTRODUCED | CHANGES SINCE PREVIOUS VERSION |
| 5140 | 1 | Windows Server 2008 R2, Windows 7 |
Added Added Added |
| 4656 | 1 | Windows Server 2012, Windows 8 |
Added Added |
| 4663 | 1 | Windows Server 2012, Windows 8 | Added |
| 5156 | 1 | Windows Server 2008 R2, Windows 7 |
Added Added |
| 5157 | 1 | Windows Server 2008 R2, Windows 7 |
Added Added |
| 4616 | 1 | Windows Server 2008 R2, Windows 7 | Added |
| 6416 | 1 | Windows Server 2016, Windows 10 [Build 1511] |
Added Added Added |
| 5632 | 1 | Windows Server 2008 R2, Windows 7 |
Added Added Added |
| 4688 | 1 | Windows Server 2012 R2, Windows 8.1 | Added |
| 2 | Windows Server 2016, Windows 10 | Added Added Added |
|
| 4624 | 1 | Windows Server 2012, Windows 8 | Added |
| 2 | Windows Server 2016, Windows 10 |
Added Added Added Added Added Added Added |
Security events that are not listed in Table 2-5 have only one version: 0.
The <Level></Level>
Table 2-6: Event Priority Level Codes
| LEVEL NAME | VALUE | DESCRIPTION |
| Verbose | 5 | Identifies a detailed trace event |
| Informational | 0 or 4 | Identifies a nonerror event such as dynamic link library loading |
| Warning | 3 | Identifies a warning event such as long group policy processing time |
| Error | 2 | Identifies a severe error event |
| Critical | 1 | Identifies an abnormal exit or termination event |
The <Task></Task>
Table 2-7: Advanced Auditing Subcategories Task Category Numbers
| CATEGORY | SUBCATEGORY | DECIMAL | HEX |
| System | Security State Change | 12288 | 0x3000 |
| Security System Extension | 12289 | 0x3001 | |
| System Integrity | 12290 | 0x3002 | |
| IPsec Driver | 12291 | 0x3003 | |
| Other System Events | 12292 | 0x3004 | |
| Logon/Logoff | Logon | 12544 | 0x3100 |
| Logoff | 12545 | 0x3101 | |
| Account Lockout | 12546 | 0x3102 | |
| IPsec Main Mode | 12547 | 0x3103 | |
| Special Logon | 12548 | 0x3104 | |
| IPsec Extended Mode | 12549 | 0x3105 | |
| IPsec Quick Mode | 12550 | 0x3106 | |
| Other Logon/Logoff Events | 12551 | 0x3107 | |
| Network Policy Server | 12552 | 0x3108 | |
| User/Device Claims | 12553 | 0x3109 | |
| Group Membership | 12554 | 0x310A | |
| Object Access | File System | 12800 | 0x3200 |
| Registry | 12801 | 0x3201 | |
| Kernel Object | 12802 | 0x3202 | |
| SAM | 12803 | 0x3203 | |
| Other Object Access Events | 12804 | 0x3204 | |
| Certification Services | 12805 | 0x3205 | |
| Application Generated | 12806 | 0x3206 | |
| Handle Manipulation | 12807 | 0x3207 | |
| File Share | 12808 | 0x3208 | |
| Filtering Platform Packet Drop | 12809 | 0x3209 | |
| Filtering Platform Connection | 12810 | 0x320A | |
| Detailed File Share | 12811 | 0x320B | |
| Removable Storage | 12812 | 0x320C | |
| Central Policy Staging | 12813 | 0x320D | |
| Privilege Use | Sensitive Privilege Use | 13056 | 0x3300 |
| Non Sensitive Privilege Use | 13057 | 0x3301 | |
| Other Privilege Use Events | 13058 | 0x3302 | |
| Detailed Tracking | Process Creation | 13312 | 0x3400 |
| Process Termination | 13313 | 0x3401 | |
| DPAPI Activity | 13314 | 0x3402 | |
| RPC Events | 13315 | 0x3403 | |
| Plug and Play Events | 13316 | 0x3404 | |
| Token Right Adjusted Events | 13317 | 0x3405 | |
| Policy Change | Audit Policy Change | 13568 | 0x3500 |
| Authentication Policy Change | 13569 | 0x3501 | |
| Authorization Policy Change | 13570 | 0x3502 | |
| MPSSVC Rule-Level Policy Change | 13571 | 0x3503 | |
| Filtering Platform Policy Change | 13572 | 0x3504 | |
| Other Policy Change Events | 13573 | 0x3505 | |
| Account Management | User Account Management | 13824 | 0x3600 |
| Computer Account Management | 13825 | 0x3601 | |
| Security Group Management | 13826 | 0x3602 | |
| Distribution Group Management | 13827 | 0x3603 | |
| Application Group Management | 13828 | 0x3604 | |
| Other Account Management Events | 13829 | 0x3605 | |
| DS Access | Directory Service Access | 14080 | 0x3700 |
| Directory Service Changes | 14081 | 0x3701 | |
| Directory Service Replication | 14082 | 0x3702 | |
| Detailed Directory Service Replication | 14083 | 0x3703 | |
| Account Logon | Credential Validation | 14336 | 0x3800 |
| Kerberos Service Ticket Operations | 14337 | 0x3801 | |
| Other Account Logon Events | 14338 | 0x3802 | |
| Kerberos Authentication Service | 14339 | 0x3803 |
The <Opcode></Opcode><Task>
Table 2-8: Global System Opcodes
| VALUE | SYMBOL | DESCRIPTION |
|
|
An informational event |
|
|
An event that represents starting an activity |
|
|
An event that represents stopping an activity |
|
|
An event that represents data collection starting |
|
|
An event that represents data collection stopping |
|
|
An extension event |
|
|
A reply event |
|
|
An event that represents an activity resuming after being suspended |
|
|
An event that represents the activity being suspended pending another activity's completion |
|
|
An event that represents transferring an activity to another component |
|
|
An event that represents receiving an activity transfer from another component |
The <Keywords></Keywords>
- 0x8010000000000000: Audit Failure
- 0x8020000000000000: Audit Success
The <TimeCreated />SystemTime2017-07-26T20:32:31.805159100ZSystemTime
The <EventRecordID></EventRecordID>
The <Correlation /><Correlation />ActivityIDActivityIDActivityID
- 4672: Special privileges assigned to new logon.
- 4624: An account was successfully logged on.
- 4627: Group membership information.
It is the responsibility of the reporting component to mark events as part of the same transaction. This is not always done, so you may find that some events that look like part of the same transaction don't have any value in the <Correlation />
The <Execution />
ProcessID:lsass.exentoskrnl.exe- If an event is reported by the
ntoskrnl.exe - If an event is reported by the
lsass.exelsass.exe
The
ProcessID- If an event is reported by the
ThreadID:lsass.exentoskrnl.exe
The <Channel></Channel>
The <Computer></Computer>
- Domain joined machine: Computer DNS name, such as 2016dc.hqcorp.local
- Non-domain–joined machine: Computer NetBIOS name, such as Win10
The <Security />UserID<Security UserID="S-1-5-19" />
