CHAPTER 6
Local Security Groups
Security groups are a primary mechanism for assigning permissions or roles to security principals in Microsoft Windows operating systems. Each modern Windows operating system has a set of default built-in local security groups. Each such group has its own set of access permissions defined for operating system objects, and has specific user privileges, logon rights, and so on, because each group has its own purpose. Built-in local security groups cannot be deleted and each has a hardcoded relative identifier (RID), which is the last part of a unique security identifier (SID), assigned to it.
Windows allows you to easily create, delete, and add members to a security group and perform other operations with security groups. Because security groups are used to assign permissions to specific accounts or groups, which are members of these groups, it's important to have good monitoring mechanisms for all actions performed with local security groups, especially with high privileged groups, like the local Administrators group.
Non–domain-joined machines have only two types of security groups that can be used within a machine:
- Local security groups
- Global security groups
All non–built-in local security groups are stored in the Security Account Manager database at the following registry path: HKLMSAMSAMDomainsAccountAliasesHKLMSAMSAMDomainsBuiltinAliasesNewGroup

Figure 6-1: Local security groups in Security Account Manager database
As you can see, security group properties are stored in the registry key as a hexadecimal value, which is the group's relative identifier (RID). In Figure 6-1, 000003E9, which is the RID of a newly created group named NewGroupC000003E9C
The MembersNewGroup
The Names
In this chapter you learn about different scenarios related to local security groups, such as security group creation, deletion, and modification. You see which events appear in the Windows security event log for most common scenarios related to security groups.
Built-in Local Security Groups
Each modern Microsoft Windows version has a specific set of built-in local security groups, but these groups vary depending on operating system type (server or client) and version. Table 6-1 contains information about built-in security groups present in each modern Microsoft Windows operating system version.
Table 6-1: Built-in Local Security Groups by Microsoft Windows OS Version
| GROUP NAME | 2008R2 | 2012/2012R2 | 2016 | WIN 7 | WIN 8/8.1 | WIN 10 |
| Access Control Assistance Operators | + | + | + | + | ||
| Administrators | + | + | + | + | + | + |
| Backup Operators | + | + | + | + | + | + |
| Certificate Service DCOM Access | + | + | + | |||
| Cryptographic Operators | + | + | + | + | + | + |
| Distributed COM Users | + | + | + | + | + | + |
| Event Log Readers | + | + | + | + | + | + |
| Guests | + | + | + | + | + | + |
| Hyper-V Administrators | + | + | ||||
| IIS_IUSRS | + | + | + | + | + | + |
| Network Configuration Operators | + | + | + | + | + | + |
| Performance Log Users | + | + | + | + | + | + |
| Performance Monitor Users | + | + | + | + | + | + |
| Power Users | + | + | + | + | + | + |
| Print Operators | + | + | + | |||
| RDS Endpoint Servers | + | + | ||||
| RDS Management Servers | + | + | ||||
| RDS Remote Access Servers | + | + | ||||
| Remote Desktop Users | + | + | + | + | + | + |
| Remote Management Users | + | + | + | + | ||
| Replicator | + | + | + | + | + | + |
| Storage Replica Administrators | + | |||||
| System Managed Accounts Group | + | + | ||||
| Users | + | + | + | + | + | |
| WinRMRemoteWMIUsers__ | + | + | + |
As shown in Table 6-1 some operating system versions have specific built-in local security groups. For example, only Windows Server 2016 has a “Storage Replica Administrators” local security group.
One way to view the list of local security groups that exist on the system is to use the built-in “Computer Management” snap-in (compmgmt.msc

Figure 6-2: The Computer Management snap-in showing local security groups
The following sections describe each of local security groups listed in Table 6.1 and discuss which of these groups are critical to monitor and why.
Access Control Assistance Operators
Members of this group can remotely query authorization attributes and permissions for resources on the local computer. There is not much information available about access permissions this group has. It has no members in it by default. It is recommended to monitor any account added or removed from this group, because it is, usually, remains empty.
Administrators
The built-in local Administrators security group is considered the most privileged built-in security group. Members of this group can perform any action on the local machine. It has one default member: the built-in Administrator account. It might also have other members created during installation, which is typical for client operating systems, or it might have members previously added to this group if the system was upgraded. This group should be considered as critical and any changes to it must be monitored. This group cannot be deleted, but can be renamed.
Backup Operators
Members of this group can back up and restore files and folders on the system, shut down the system, log on as a batch job, and log on locally. Because of backup and restore privileges this group should be considered critical. These privileges allow users to take a copy of any file in the system, including the Security Account Manager database, and then perform any action with these files offline. This group cannot be deleted, but can be renamed. It is empty by default. You can find more information about user privileges in Chapter 11.
Certificate Service DCOM Access
This group only applies to servers with the Certification Authority role installed. All security principals that need to enroll certificates from the Certification Authority must be a member of this security group on Certification Authority servers. Membership in this security group doesn't give accounts any critical privileges. This group should be considered as a low-privileged group. This group cannot be deleted, but can be renamed. It is empty by default.
Cryptographic Operators
The Federal Information Processing Standards Publication 140-2 (FIPS 140-2) defines a “Crypto Officer” role, which is represented by the Cryptographic Operators group in Windows.
When the “System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing” security policy setting is configured in local or group policy objects, only members of the Cryptographic Operators group or the local Administrators group can configure Cryptography Next Generation (CNG) settings. Specifically, Cryptographic Operators can edit the cryptographic settings in the IPsec policy of Windows Firewall with Advanced Security (WFAS).
This security group is very rarely in use and doesn't have any critical permissions associated with it. This group should be considered a low-privileged group. This group cannot be deleted, but can be renamed. It is empty by default.
Distributed COM Users
The Distributed COM Users group by default has the “Local Access” and “Remote Access” access permissions security limits set for all COM objects on the system. It also has the “Local Launch,” “Remote Launch,” “Local Activation,” and “Remote Activation” launch and activation permission security limits set for all COM objects on the system. These permissions can be set using the “Component Services” management console (comexp.msc
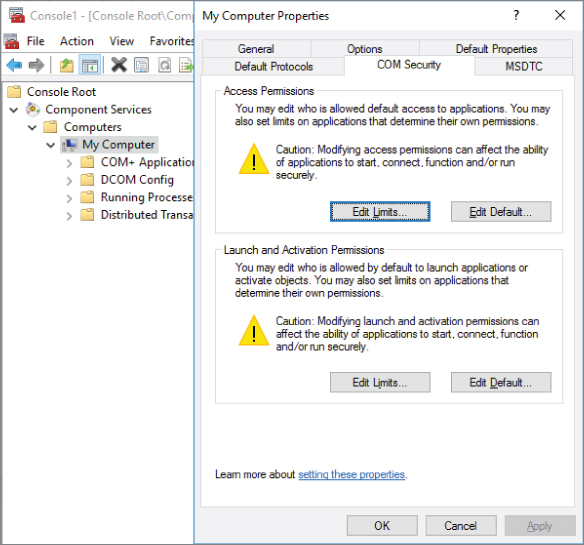
Figure 6-3: Component services security settings
It is important to understand that by default Distributed COM Users group is included only in “Security Limits” and doesn't have any DCOM permissions by default. “Security Limits” defines the permissions limit for any COM object in the system. Basically, if COM application permissions will somehow get beyond the “Security Limits,” only permissions defined in the “Security Limits” will work. The Distributed COM Users group, theoretically, can have unlimited local and remote access for any COM application, if these permissions are set for that application manually. The criticality level of this group depends on individual settings for each COM application in the system. Members of this group, by default, cannot log on the system locally. This group has no members by default. I recommend considering this security group to be of medium importance and monitoring any change to it.
Event Log Readers
Members of this group can read any event log on the local system, but cannot log on into the system locally. This group has only read access to event logs. Membership in this group often includes other computers that monitor or query local log events, but this group is empty by default. It is recommended that this group is considered to be of medium criticality.
Guests
The Guests group is designed to provide guest access to the system if it's required. This group has similar permissions as the built-in Users group, but is more restricted. The only default member of this group is the Guest account. Members of this group, because of default local security policy settings, cannot log on to the system locally. If guest access is not needed, it is recommended to remove the Guest account from this group and performing monitoring of this group for any change, because no changes to this group should occur.
Hyper-V Administrators
This group is designed for Hyper-V administrators. All members of this group have unrestricted access to all Hyper-V features on the local machine. Members of this group, by default, cannot log on in to the system locally. The importance level of this group depends on the importance of Hyper-V virtual machines, installed on the system. I recommend considering this group to be of low criticality, because this group exists only on Windows client operating systems, which don't typically have any critical virtual machines installed.
IIS_IUSRS
The IIS_IUSRS group is designed to be used by the Internet Information Services (IIS) component. IIS_IUSRS is the group for IIS Worker Process Accounts, which means the identity that the IIS application pool itself runs under. By default, if the Internet Information Services component is not installed, this group has no user privileges associated to it and has no members. After you install the IIS, this group gets the following privileges:
- Log on as a batch job
- Impersonate a client after authentication
If the IIS component is not installed on the system this group has a low importance level. After the IIS component is installed, the IIS_IUSRS group gains the “Impersonate a client after authentication” privilege, which may be used to impersonate more privileged user accounts logged in to the machine using RPC, COM, or named pipes. The probability of such attacks is quite low, but still, I recommend treating this group as of high importance, because of “Impersonate a client after authentication” privileges, and monitoring any change to this group.
Network Configuration Operators
Network Configuration Operators group members can perform the following actions:
- Modify the Transmission Control Protocol/Internet Protocol (TCP/IP) properties for a local area network (LAN) connection, which includes the IP address, the subnet mask, the default gateway, and the name servers
- Rename the LAN connections or remote access connections that are available to all the users
- Enable or disable a LAN connection
- Modify the properties of all of remote access connections of the user
- Delete all the remote access connections of the user
- Rename all the remote access connections of the user
- Issue
ipconfig/releaseipconfig/renew - Enter the PIN Unblock Key (PUK) for Mobile Broadband devices that support a SIM card
Because members of this group have the ability to change TCP/IP settings, this group should be considered as of high importance. By default this group is empty. I recommend that you monitor any change to this security group, because it is uncommon for this group to be in use.
Performance Log Users
This group is designed to provide access to measure system performance using performance counters, trace providers, and so on. The main difference between Performance Log Users and Performance Monitor Users is that Performance Log Users has Write access (can modify the logging schedule, for example), whereas Performance Monitor Users has only Read access. This group has the “Log on as a batch job” user privilege by default. I recommend considering this security group to be of low importance, because setting performance counters may affect overall system performance, but it is hard to use this functionality to compromise the system.
Performance Monitor Users
Members of this group can view real-time performance data in Windows Performance Monitor (Perfmon.msc
Power Users
This group initially was designed to provide users limited administrative access to the system, such as installing software that does not modify operating system files or installing system services, running legacy applications, and so on. Starting from Windows Vista, Power Users permissions were reduced, mostly to provide access to some system configuration tasks, such as changing the system time zone. Usually, there is no need to use the Power Users group, but, because this group still has the ability to change some system settings, I would recommend considering this group to be of medium importance and monitoring any change to it.
Print Operators
This group is essentially designed for Active Directory Domain Controllers and on local servers it does not have any logon rights or user privileges assigned to it. Members of this group can modify, create, share, and delete printers connected to domain controllers in the domain. On standalone servers this group should remain empty. There is no need to use it, because it does not have any permissions and user rights associated to it on member servers.
Remote Desktop Users
Members of this group have “Allow log on through Remote Desktop Services” user privileges and are able to remotely log on to the local machine using a Remote Desktop connection. I recommend treating this group as a high importance group, because it provides remote access to the machine, and monitoring any change to this group.
Remote Management Users
This group is designed mainly to provide remote management access to the local machine using the WS-Management protocol (for example, remote connections using Server Management console use this protocol). This group also allows connection to the host using Windows Remote Management (WinRM) protocol, which is used, for example, by remote PowerShell connections. By default this group has no user rights assigned to it. Because this group provides remote access to the local machine, it should be considered as a high importance group and any change to this group should be monitored.
Replicator
The Replicator group is designed to support Active Directory replication operations. This group should remain empty on member servers. It has no object permissions, logon rights, or user privileges associated to it on member servers. I recommend considering this group to be of low criticality on member servers.
Storage Replica Administrators
The Storage Replica Administrators group is dedicated for Storage Replica feature administrators. Members of this group have full access to all Storage Replica features. By default this group is empty. If the Storage Replica feature is not in use, it has no object permissions, logon rights, or user privileges associated to it. I recommend considering this group as of low criticality on member servers.
System Managed Accounts Group
This built-in security group is not well documented yet. It contains accounts managed by the operating system. This group provides full access for local machine account (Local System) to all members of this group. By default, this group has only one member in it, the DefaultAccount account. (See Chapter 5 for more information about the DefaultAccount account.) I recommend considering this group as of low criticality.
Users
Any new local user account becomes a member of this security group by default right after it is created. The main purpose of this security group is to provide users with all the non-administrative functions needed to use the computer. Membership in this group does not provide any type of administrative access to the machine, but allows members to, for example, run applications which don't require elevation of privileges, use local and network printers, and lock the computer.
Windows server operating system versions have the following logon right and user privileges assigned to the Users security group:
- Allow Log on locally
- Access this computer from the network
- Bypass traverse checking
- Increase a process working set
Windows client versions additionally have the following user privileges assigned to the Users security group:
- Remove computer from docking station
- Shut down the system
- Change the Time Zone
Basically speaking, the Users security group has more privileges on Windows client system versions than on server versions.
This group should be considered as of medium criticality; changes in this group might indicate local user account deletion or creation operation. Any change to this group should be monitored, especially on critical servers and workstations.
WinRMRemoteWMIUsers__
The WinRMRemoteWMIUsers__ group initially was designed to allow its members to run Windows PowerShell commands remotely. Starting from Windows 2016 and Windows 10 this group was completely replaced by the “Remote Management Users” security group. By default this group has no members and permissions assigned to it. Because this group provides remote access to the local machine, it should be considered as of high importance and any change to this group should be monitored.
Built-in Local Security Groups Monitoring Scenarios
Different actions can be performed with security groups: groups can be created, deleted, modified, and so on. All these scenarios generate different events in the Windows security event log. It's important to know which events are generated in the security event log for all typical operations and which useful information is available for monitoring in these events.
In this section of the chapter you will find information about security events generated during typical operations with local security groups.
Local Security Group Creation
You can use several methods to create a local security group, including the Computer Management console (compmgmt.mscnet group
During creation of new local security group using the Computer Management console you can specify the following group parameters:
- Group name
- Description
- Group members
That is all that is available to change for local security groups.
For each local security group creation event it's important to know the following information:
- Who created the group?
- When the group was created?
- How this group was created? Which tools were used?
- What is the name of new group?
In this section you will find information about how to find answers to all of these questions.
Successful Local Security Group Creation
The events shown in Listings 6-1 through 6-7 will appear in the Windows security event log when a new local security group is successfully created.
This event represents a handle request invoked by the Subject
To create a new local security group a request to create a new local group (CreateLocalGroupSecurity Account Manager SAM_DOMAIN
The Object Server:Security Account Manager
Object Type:SAM_DOMAIN
The access types (Accesses field) requested for the Security Account Manager SAM_DOMAIN
%%5398:CreateLocalGroup%%5401:LookupIDs
(See Table 5.1 for the full list of SAM_DOMAIN
The CreateLocalGroup
The Access MaskSAM_DOMAIN
This event also shows a Process Informationlsass.exelsass.exelsass.exelsass.exe
There is no information about how a new local security group was created or which tools were used. You can try to track 4688 process creation events, which occur prior to new local group creation events, to find which applications were run before a new local security group was created.
The event in Listing 6-2 informs you about new local security group creation.
There are two types of local groups that you might see in Windows security events:
- Security-enabled: Standard security groups
- Security-disabled: Active Directory distribution groups
In this event you also can find who created a new group (SubjectGroup NameSAM Account Name
The SID History
This 4731 event contains all important information about successful local group creation:
- Who created a new group:
Subject - The name of newly created group:
Group Name - When new group was created: Event generation time
Listing 6-3 shows a local security group change event. The biggest problem with this event is that it shows changes to only a limited set of attributes: SAM Account NameSID HistorySAM Account Name
In this event you see that a change was made to the NewGroup
Listing 6-4 shows that the handle, which was opened to the SAM_DOMAIN
The Handle IDHandle ID
Listing 6-5 is another handle request, but this time it is for the SAM_ALIASSecurity Account ManagerSAM_ALIAS
The Object NameSecurity Account Manager000003EA000003EA1002
You also can see that the WriteAccountAccessesAccess MaskSAM_ALIAS
This event means that the SubjectWriteAccount1002.
Listing 6-6 shows local security group change event without any information about what exactly was changed. This change was initiated using the handle requested in the previous 4656 event.
Listing 6-7 shows that the handle, which was opened to the SAM_ALIAS DOMAINSAccountAliases�00003EA
Unsuccessful Local Security Group Creation - Access Denied
When an account doesn't have required permissions to create a local security group, the event in Listing 6-8 is recorded in the Windows security event log.
This event is an Audit FailureSubjectCreateLocalGroupLookupIDsSAM_DOMAIN Security Account Manager
No other events will be recorded for an Access DeniedSubject
Monitoring Scenarios: Local Security Group Creation
A useful event to monitor for successful local security group creation is:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4731: A security-enabled local group was created | Security Group Management | |
A useful event to monitor for unsuccessful local security group creation is:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4656: A handle to an object was requested | SAM | |
In general, all successful and, especially, unsuccessful local security group creation events should be monitored. Highest priority should be given to monitor any security group creation operation on high-importance/critical hosts, such as critical servers, administrative workstations, and so on.
Creation of a new local security group is not a common action performed after initial system setup. After a new system is provisioned and all required roles, components, features, and software are installed, it's not typical for additional local security groups to be created.
Monitor these events:
- Monitor for any “4731: A security-enabled local group was created” event.
- Monitor for “4656: A handle to an object was requested”
Audit FailureAccess Mask0x240Object TypeSAM_DOMAINHere is the XPath filter for this monitoring:
*[System[band(Keywords,4503599627370496) and (EventID=4656)]] and*[EventData[Data[@Name='ObjectType'] and (Data='SAM_DOMAIN')]] and*[EventData[Data[@Name='AccessMask'] ='0x244']]
Local Security Group Deletion
A local security group deletion operation is not something you will usually see in Windows security event logs. This operation cannot be performed against built-in local security groups, such as the built-in local Administrators group, and it's not common to see any local security groups deleted, especially after initial system setup.
In this section you will see examples of events that are generated after successful and unsuccessful local security group deletion operations.
Successful Local Security Group Deletion
The events in Listings 6-9 through 6-12 appear in the Windows security event log when a local security group is successfully deleted.
This is the initial handle request for this security group operation.
A handle with DELETESAM_ALIAS Security Account ManagerDOMAINSAccountAliases�00003EAObject Name
Event 4734 (Listing 6-10) indicates a successful local security group deletion operation.
This event has answers for the following questions:
- Who deleted the security group:
Subject - Which local security group was deleted:
Group
A local security group is an object in the Security Account Manager database. Because an object for specific local security group was deleted, you will see the event in Listing 6-11, which informs you about this.
The only way to get information about which object was deleted is to find the corresponding “4656: A handle to an object was requested” event with DELETEHandle ID0x26fddeb73e0
Listing 6-12 shows that the handle that was opened to the SAM_ALIAS DOMAINSAccountAliases�00003EA
Unsuccessful Local Security Group Deletion - Access Denied
When a user doesn't have DELETE
The AndreiDELETEDOMAINSAccountAliases�00003EC SAM_ALIAS
The Audit Failure
Unsuccessful Local Security Group Deletion - Other
When a local security group is not deleted for another reason—for example, if someone tried to delete a built-in local security group such as the local Guests group—the event shown in Listing 6-14 is generated in the Windows security event log.
The “4656: A handle to an object was requested” Audit Success
From the system's perspective, access to the specific local security group was successfully granted, but then it was denied at the application level, which the system does not monitor. You should verify whether a “4734: A security-enabled local group was deleted” event occurs after a handle request event. If yes, the security group was successfully deleted; if no, it was not deleted, but someone tried to do it.
Monitoring Scenarios: Local Security Group Deletion
A useful event to monitor for successful local security group deletion is:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4734: A security-enabled local group was deleted | Security Group Management | |
Useful events to monitor for unsuccessful local security group deletion are:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
|
4656: A handle to an object was requested 4656: A handle to an object was requested |
SAM SAM |
|
Any successful and unsuccessful access denied local security group deletion events should be monitored on all hosts. As is true for local security group creation actions, a local security deletion operation is not a common action performed during a system's lifetime. Even at initial system setup, local security group deletion is not usually performed. It's more likely that a group creation operation will be performed.
Monitor these events:
- Monitor for any “4734: A security-enabled local group was deleted” event.
- Monitor for “4656: A handle to an object was requested”
Audit FailureAccess Mask0x10000Object TypeSAM_ALIASThe XPath filter for this monitoring is:
*[System[band(Keywords,4503599627370496) and (EventID=4656)]] and*[EventData[Data[@Name='ObjectType'] and (Data='SAM_ALIAS')]] and*[EventData[Data[@Name='AccessMask'] ='0x10000']]
Local Security Group Change
Not many parameters can be changed for local security groups using built-in Windows tools. The available changes are:
- Group name change
- Group description change
- Group members removed/added
In this section you will find information about how to monitor the first two changes from the preceding list.
Successful Local Security Group Change
Any change to the local security group, except changes in group membership, will generate the events shown in Listings 6-16 through 6-18
To make changes to the local security group object, an account must have WriteAccountSAM_ALIAS
The local security group change event shown in Listing 6-16 provides the following important information:
- Which group was changed:
Group - Who made a change:
Subject
Unfortunately, changes to a security group's description field are not shown in the 4735 event. The only included changed attributes are:
SAM Account Name:SID History:
Changes in the Description
Group membership delete/add operations do not generate a 4735 event.
If the group's name was changed, both the GroupChanged Attributes
Group:Security ID: S-1-5-21-3212943211-794299840-588279583-1004Group Name: NewGroupNameGroup Domain: 2016SRVChanged Attributes:SAM Account Name: NewGroupNameSID History: -
If the security group name was changed, then in addition to a 4735 event, the 4781 event shown in Listing 6-17 is generated.
The event in Listing 6-18 has an Old Account Name
Unsuccessful Local Security Group Change - Access Denied
By default, only local administrators and the Local System account can change a local group's name. If any nonadministrative account tries to change the settings for any local security group, it will get an access denied message and the event shown in Listing 6-19 will be generated in the Windows security event log.
In an “Access Denied” scenario you will see an Audit FailureWriteAccount
Monitoring Scenarios: Local Security Group Change
Useful events to monitor for successful local security group change are:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
|
4735: A security-enabled local group was changed 4781: The name of an account was changed |
Security Group Management User Account Management |
|
A useful event to monitor for unsuccessful local security group change is:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4656: A handle to an object was requested | SAM | |
Security group name modification is a very uncommon operation. Usually it's not critical to monitor security group name changes, but in some scenarios it might be needed. For example, you should track any changes on critical hosts and any changes to specific high-importance local security groups, such as the built-in local Administrators group. In general, security group changes (except operations with group membership) are not important to monitor.
Local Security Group Membership Operations
It is important to monitor changes to local security group membership.
The most privileged built-in local security groups are:
- Administrators
- Backup Operators
- Network Configuration Operators
- Remote Desktop Users
- Remote Management Users
- WinRMRemoteWMIUsers__
You should also verify all manually created local groups and determine which of them should be considered critical or high privileged. All changes related to critical/high-privileged groups should be monitored.
There are different ways to add/remove users from specific groups, including the Computer Management console (compmgmt.msc
In this section you will find information about auditing group member addition and removal operations.
Successful New Local Group Member Add Operation
When a new member is added to a local security group, the messages shown in Listings 6-20 through 6-23 occur in the Windows security event log.
As shown in Listing 6-20 the following access rights are requested by default when a new member is added to the security group using the Computer Management console:
%%5424 (AddMember)%%5425 (RemoveMember)%%5426 (ListMembers)%%5427 (ReadInformation)
Whether an account is added or removed from the security group, all four access types will be requested by the Computer Management console. The only access permission that must be requested to add a new member is AddMember. It is up to an application which permissions to request for a specific operation.
Listing 6-21 informs you about the addition of a new member to a local security group.
This event has the following information in it:
- Who added the new member to the local security group:
Subject - What new member was added to the group:
Member - To which group was the new member added:
Group
The Member: Account Name
For all built-in local security groups, which were listed at the beginning of this chapter, the Group DomainBuiltin
Group:Security ID: S-1-5-21-3212943211-794299840-588279583-1004Group Name: NewGroupGroup Domain: 2016SRV
Event 4658 in Listing 6-22 shows that a handle opened for a previous operation has been closed.
The event in Listing 6-23 generates each time group membership for a local security group is enumerated.
This event happens, for example, when the Computer Manager (compmgmt.msc

Figure 6-4: Group membership enumeration event and group properties window in the Computer Manager console.
If you use other methods to add a member to a local security group, which do not perform group membership enumeration, such as the following PowerShell script:
$group = [ADSI]"WinNT://2016srv/newgroup,group"$group.Add(„WinNT://2016srv/andrei,user")
then a “4799: A security-enabled local group membership was enumerated” event will not be generated.
Useful information in this event is the Process Name
Successful Local Group Member Remove Operation
A group member removal operation, performed using the Computer Management console, has exactly the same events recorded in the Windows security event log as a successful new local group member add operation, except the “4732: A member was added to a security-enabled local group” event is replaced by the event shown in Listing 6-24.
This event has the same fields as the “4732: A member was added to a security-enabled local group” event, and shows you which security principal was removed from the specific local security group.
Unsuccessful Local Group Member Remove/Add Operation - Access Denied
If a user account doesn't have sufficient permissions to add/remove members from a security group it will get an “Access Denied” message. Both add and remove operations generate the event in Listing 6-25 in the Windows security event log.
Both “add member” and “remove member” events have AddMemberRemoveMemberListMembersReadInformation
Monitoring Scenarios: Local Security Group Members Changes
Useful events to monitor for successful local security group members changes are:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
|
4733: A member was removed from a security-enabled local group 4732: A member was added to a security-enabled local group |
Security Group Management Security Group Management |
|
A useful event to monitor for unsuccessful local security group members changes is:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4656: A handle to an object was requested | SAM | |
It is critically important to perform monitoring of any successful and unsuccessful change to critical and high-privileged built-in and manually created security groups. The following built-in local security groups are considered high privileged:
- Administrators
- Backup Operators
- Network Configuration Operators
- Remote Desktop Users
- Remote Management Users
- WinRMRemoteWMIUsers__
Also, it's unusual to remove or add members to local security groups too often. Usually it happens when a machine joins the Active Directory domain or during role, feature, or application installation or removal. Any successful and unsuccessful member add and remove operations should be monitored.
Monitor these events:
- Monitor any “4733: A member was removed from a security-enabled local group” event.
- Monitor any “4732: A member was added to a security-enabled local group” event.
- Monitor for “4656: A handle to an object was requested”
Audit FailureAccess Mask0xFObject TypeSAM_ALIASThe XPath filter for this monitoring is:
*[System[band(Keywords,4503599627370496) and (EventID=4656)]] and*[EventData[Data[@Name='ObjectType'] and (Data='SAM_ALIAS')]] and*[EventData[Data[@Name='AccessMask'] ='0xF']]
Local Security Group Membership Enumeration
The last scenario for monitoring using the Windows security event log is group membership enumeration. This event triggers when someone queries a list of members for a specific local security group. For example, it will be triggered when someone opens a local security group's properties, which automatically shows you a list of the current group's members.
The event in Listing 6-26 is generated in the Windows security event log when a local security group membership is enumerated.
A 4799 event contains the following information:
- Who performed the action:
Subject - Membership of which group was enumerated:
Group - Which process requested this operation:
Process Information
By default, all members of a built-in local Users group can enumerate membership for any local security group.
Monitoring Scenarios: Local Security Group Membership Enumeration
A useful event to monitor for successful local security group membership enumeration is:
| SECURITY EVENT | SUBCATEGORY | EVENT TYPE |
| 4799: A security-enabled local group membership was enumerated | Security Group Management | |
A local security group membership enumeration event is mostly informational and could be monitored if needed.
