9
Depth Analysis On DoS & DDoS Attacks
Gaurav Nayak1, Anjana Mishra1*, Uditman Samal1 and Brojo Kishore Mishra2
1Department of Computer Science and Information Technology C.V. Raman Global University, Bhubaneswar, Odisha, India
2GIET University, Gunupur, Odisha, India
Abstract
Denial of Service (DoS) attacks are some of the most expensive and threatening cyberattacks that exist on the internet. Their main aim is to restrict the users/ victims’ access to a specific resource. This chapter comprises all ideas, classification, and solutions to a DoS attack. DoS compromises the availability goal of the CIA triad [16]. Here, DoS attacks are classified into the network and attacker behavior like TCP SYN, which is network-based, whereas a UDP attack is bandwidth-based. Distributed Denial of Service (DDoS) is the revamped and advanced version of DoS which uses multiple sources/zombies/agents to carry out the attack. Zombies/ Agents are the compromised computers that attackers use to attack another computer. Viruses, worms, and Botnet are the main reasons for DDoS attacks. Due to DoS attacks, there is a threat to major new technologies such as VANET, IoT, etc., which are not yet fully developed. To avoid DoS attacks users must install regular security patches, antivirus, and anti-trojan software and also run firewalls. Post-Attack Forensics is the type of countermeasure in which a pattern of the traffic of a previous DDoS attack is collected to identify and block the same kind of attack.
Keywords: DoS, CIA triad, TCP SYN, UDP, zombies, VANET, IoT, post-attack forensics
9.1 Introduction
The Internet is the most valuable asset in the 21st century. Every business in the world tries to get benefit through it. The Internet has become the powerhouse of websites, business, and communication channels, with slight disruption of any sector causing huge inconvenience to users, owners, and service providers. The unavailability of Internet services leads to immense financial losses [2]. The disruption can be either natural like due to power failure or due to planned cyberattacks. Cyberattacks are attacks carried out with the help of computers, network devices, or both. Mostly these attacks are carried out to extract money and disrupt others’ business [19].
Denial of Service (DoS) attacks are some of the most expensive and threatening cyberattacks that exist on the Internet now. DoS is a type of attack in which the main aim is to restrict the users/victims’ access to a specific resource [3]. It focuses on blocking and disrupting permitted access to a resource by restricting the system’s operation and function. DDoS is the modified and advanced version of DoS. Distributed Denial of Services (DDoS) is the same as a DoS attack but uses multiple sources/zombies/ agents to carry out the attack. Zombies/Agents are compromised computers that attackers use to attack another computer. Attackers take advantage of security vulnerabilities, backdoors, viruses, worms, and more to compromise the computer system to create zombies. Zombies function as a node that follows the attacker’s commands and sends a huge volume of data and queries to websites, or sends numerous spam emails to a single email address, preventing the victim from accessing the resource or causing service providers to suffer. DoS and DDoS compromise the availability goal of the CIA triad.

Figure 9.1 DDoS using zombie network [13].
Due to DoS and DDoS attacks on major commercial websites such as Amazon, eBay, CNN, Yahoo, and other websites have faced major financial losses and inconsistent connectivity. These attacks sometimes cause a threat to public security, as in 2003 when the Houston port system in Texas was taken down [2].
9.1.1 Objective and Motivation
The objective of this paper is to gain new insight into one of the most threatening cyberattacks, i.e., Denial of Service (DoS). Each year many companies, personnel, and governments face huge losses in the financial sector and many of them lose their reputation and brand value. The study is carried out to discover the behavior and phenomenon of DoS attacks, and to accrue knowledge about their nature and how frequently these attacks affect the resource and power of individuals/companies/government. This chapter focuses on how to deal with Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks with the help of different countermeasures and defense mechanisms. The purpose of this study is to analyze the growth in the severity of DoS and DDoS attacks, which can help us to build advanced defense measures by tracking their activity through analyzing attackers’ previous approaches. Due to the huge widening of Internet users, the attacker always gets a feasible way to attack any users, so to enable people to wake up to the risk that is presented, this paper gives some insight and knowledge.
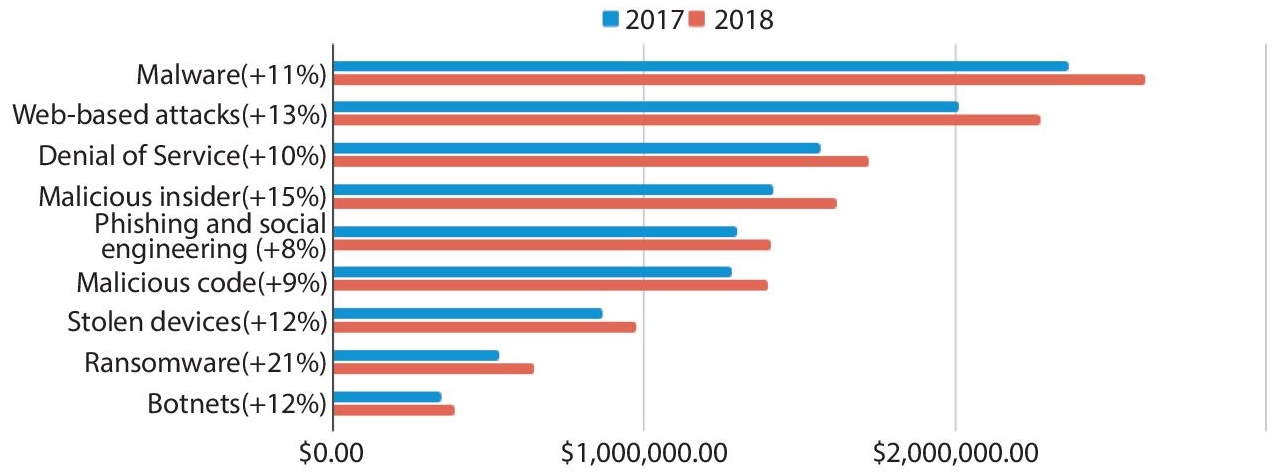
Figure 9.2 Average annual cost of cyberattack by its type (2018 costs about US$13.0 million) [4].
The study carried out by Accenture and the Ponemon Institute in 2018 found that Denial of Service is the third most expensive IT security crime for victim organizations [4].
According to more than 2,600 security and IT professionals at 355 organizations around the world [4], DoS attacks have increased victim cost by nearly 10% in 2018 as compared to 2017.
DDoS attacks also continue to grow. Here are some statistics that can affect the potential market forecasts for 2020 and beyond [6]:
- According to Cisco Visual Networking Index (VNI) - 2017 data, DDoS assaults are projected to grow twice of 14.5 million by 2022 globally.
- The impact of dominant DDoS attacks is widespread; about 25% of all web traffic is used when they are active.
- According to Kaspersky’s SecureList, China and the United States were the most common targets for DDoS attacks in Q2 2019, up 84& from Q1.
- According to the A10 Network Study, the agency monitored over 20.3 million DDoS resources in Q2 2019.
The scale of DDoS assault has grown dramatically in recent years, according to Arbor Network’s 12th annual report in Waterman, and these attacks are steadily rising year by year. In Figure 9.3, in the last 10 years, the growth of attack by volume size increases tremendously with major growth seen in 2016 [5].

Figure 9.3 Size of DDoS attack in Gb/s [5].
9.1.2 Symptoms and Manifestations
Symptoms of Denial-of-Service attacks, according to the U.S. Computer Emergency Response Team, include [8]:
- Network output that is unusually slow.
- A particular web page is unavailable.
- Unable to open any website.
- The amount of spam messages obtained has skyrocketed— (the following form of DoS is known as an email bomb).
9.2 Literature Survey
In paper [2], among the three goals of computer security, availability describes the accessibility of desired resources on time. DoS attacks are attacks which disrupt the availability goal of internet security. The CERT Coordination Center describes three specific types of attacks: 1) the disruption or modification of configuration information, 2) the use of finite, restricted, or nonrenewable resources, and 3) the physical disruption or modification of connected devices. They have looked into different DoS attack mechanisms and summarized a more realistic taxonomy of attack and also provided some comprehensive taxonomy on defense practices. After reviewing a huge number of research proposals, the existing taxonomy on attacks has added some new attack classification and could be added more shortly.
In [28], the authors discuss a sequence of Denial of Service attacks against a victim’s computer and suggest a DoS attack mitigation algorithm. The requesting client passes through three layers of this algorithm for effective verification. The TCP 3-way handshake can be exploited by flooding a huge number of TCP SYN requests, which results in system crashes and unresponsive servers. Packet monitoring using TTL Approach and Anomaly Detection using Entropy are two approaches that are not ideal methods for preventing but can be used. Based on retrieval time, the suggested algorithm outperforms current algorithms in detecting legitimate users and stopping attackers from accessing the server.
In [14], both proven and possible attack pathways are used to explain the attack taxonomy. Along with this definition, this research goes through key characteristics of each attack type, which helps to characterize the complexities of countering these attacks. The end-to-end approach is used in Internet architecture: connecting end hosts use dynamic features and functions to attain expected service promises. It was found that to gain unparalleled strength and survivability, attackers collaborate to share attack code and knowledge about compromised computers, as well as to assemble their agents into organized networks.
In [21], to detect and identify anomalous network traffic behavior, an advanced intrusion detection system (IDS) is needed. The method is assisted in this article using the most recent dataset that contains the most common forms of DDoS attacks, such as (HTTP flood, SIDDoS). To detect DoS attacks, Decision trees are utilized in conjunction with well-known classification approaches such as Naive Bayes, Support Vector Machine (SVM), and Multilayer Perceptron (MLP). Machine learning techniques are important for providing insight into the severity of an attack and, as a result, allowing businesses to take appropriate steps to minimize specific attacks which would permit the scope of attacks on a network link or an entity to be measured, allowing the network to be protected by appropriate firewall laws.
In [26], engineering scalable security technologies designed for the IoT environment are needed to execute safe IoT growth. The growth in IoT has also triggered the frequency of DoS attacks as the low-end IoT devices do not have robust encryption mechanisms, making them vulnerable to attacks. Software-Defined Networking (SDN) is a hopeful model which would help detect and reduce Denial of Service (DoS) and Distributed Denial of Service (DDoS) risks in the 5G networks. A stateful Software-Defined Networking (SDN) protection is an approach that can be used to identify and minimize DoS and DDoS attacks using the principle of entropy as the detection mechanism.
9.3 Timeline of DoS and DDoS Attacks
In 1974, 13-year-old David Dennis performed the first DoS attack. Dennis wrote a program that forced a few computers in a nearby college research lab to shut down using the “external” or “ext” command [7]. Two decades later, Panix, one of the oldest ISPs in the world, was the target of a DoS attack, according to theory. On September 6, 1996, Panix was hit by a SYN flooding attack, which knocked out the company’s networks for weeks while device manufacturers, particularly Cisco, worked out an appropriate defense. Khan C. Smith demonstrated a DoS attack on the Las Vegas Strip in 1997 at a DEF CON conference by shutting down Internet connections for more than an hour. Following the publication of that code, countless Internet attacks against EarthLink, E-Trade, Sprint, and other companies occurred over the next few years [8].
DDoS is a more sophisticated and complex version of DoS attacks. In late 1999, comments in the code indicated that a major attack was planned for December 31 but fortunately never happened [9]. In 2000, the first recorded DDoS attacks that hit several popular internet sites, like eBay, CNN, E-Trade, and Yahoo, were carried out by a 15-year-old boy, Michael Calce, using a cover named “Mafiaboy”. Calce hacked into several university computer networks. He used their servers to launch a distributed denial-of-service (DDoS) assault. In 2016, a huge DDoS attack targeted Dyn, a big domain name system (DNS) vendor, knocking out prominent internet sites and services like GitHub, Amazon, CNN, Airbnb, Spotify, PayPal, Netflix, Visa, The New York Times, and Reddit [10].
On March 1, 2018, GitHub was struck by a 1.35 Tb/s attack. On March 5, 2018, an unidentified consumer of Arbor Networks, a US-based service provider, was hit by the biggest single DDoS attack to that point, with a high of around 1.7 Tb/s. In February 2020, Amazon Web Services (AWS) was hit by an attack with a record high intensity of 2.3 Tb/s. In June 2019, during the anti-extradition riots in Hong Kong, the chatting application Telegram changed into an allotted denial of service (DDoS) attack geared toward stopping protesters from the usage of it to coordinate their movements [8].
9.4 Evolution of Denial of Service (DoS) & Distributed Denial of Service (DDoS)
Virus, Worms, Malware, Spyware, and BotNets are the type of malicious code designed to exploit vulnerabilities and resources. According to [1], a Trojan horse is a script that appears to do one thing while doing something else behind the scenes. Apart from worms and viruses, Trojans do not spread by attacking other resources or replicating themselves; instead, they generate security holes that enable unauthorized users to gain access to a device [11]. In the same way, as a virus is a self-replicating program that binds itself to executable programs, so is a worm. Robert T. Morris revealed the first big Internet worm, the ‘88 RTM Internet Worm,’ in 1988 [1].
Attackers can use that script to carry out Distributed Denial of Service attacks until they have an army of infected computers. Code Red, Code Red II, and Sasser are worms that can infiltrate hundreds and thousands of computers and transform them into attack targets [1]. The targeted web addresses receive multiple requests at a time from several infected computers leading to a denial of service. These Trojan programs infect computers and carry out DoS attacks called Trojan-DDoS [12]. Mytob and its various variants, as well as Bayfraud, Fanbot, and Bagle have all appeared recently. Malicious scripts have been a significant cause of discussion in big enterprises because they often cause downtime.
Even if the biggest botnet found using calculation and identification techniques only had 20,000 servers there have been reports of 100,000-host zombie networks. Extortion, identity theft, and credit card fraud are all popular uses for armies. Leaks of hacker “Bot-Wars” expose their strategic sophistication when they fight for possession of these valuable items by creating scripts that eliminate their competitors before they have the biggest army.
Due to the use of IRC networks and protocols, it is now harder to recognize Distributed Denial-of-Service networks, as these enable a valid network service to monitor a community of Distributed Denial-of-Service zombies through outbound connections to a standard service. Since these communication channels get a lot of traffic, an intrusion could go unnoticed. The attacker is also helped by the IRC server, which keeps track of which agents are available online. The intruder can access the IRC server, which gets this information through IRC network software alerts [1].
9.5 DDoS Attacks: A Taxonomic Classification
To conceive a DDoS attack taxonomy, we must first classify the attacks in terms of their actions and properties [14]. The trait of the attack is defined by analyzing the methods that are used to carry out and plan the attack. In Figure 9.4, the DDoS attack is classified into various types according to the behavior of attacks, such as the impact of attacks, types of automation, the rate dynamics of attacks, and many more.
9.5.1 Classification Based on Degree of Automation
The attacker must first identify a compromised agent computer and inject it with malicious code to plan for the attack. We distinguish among Manual, Semi-Automatic, and Automatic DDoS attacks based on the degree of automation [15].

Figure 9.4 Classification of DDoS attacks by degree [15].
- Manual: The intruder manually scans remote devices for bugs, gains access to them, downloads the attack code, and then orders the attack to begin.
- Semi-Automatic: The DDoS network in semi-automated attacks is made up of handler (master) and agent (slave, daemon, zombie) computers. Recruit, hack, and infect are all automatic processes. During the usage process, the attacker determines the attack type, onset, length, and target to zombies, which then deliver packets to the target through the handler.
- Automatic: In an automation DDoS attack, the attack code pre-programs the attack’s start time, attack form, length, and victim. Since the attacker is only interested in issuing a single instruction at the outset of the procurement process, the deployment methods of this attack class expose the attacker to the bare minimum. Additionally, if agents interact through IRC networks, these channels may be used to make changes to the current code.
9.5.2 Classification Based on Exploited Vulnerability
Distributed Denial of Service attacks use a variety of tactics to prevent the target from providing service to its customers. On the basis of Exploited vulnerabilities, we distinguish among brute-force attacks and protocol attacks [14].
- Protocol Attack: Protocol attacks take advantage of a particular function or implementation flaw in a protocol built on the victim to absorb a large portion of its resources. Examples include the CGI request attack, the TCP SYN attack, and the authentication server attack.
- Brute-force Attacks: These attacks are carried out by launching a large number of apparently legal transfers. The target network’s resources are exhausted since an originating network can typically have more traffic bandwidth than the target system can handle.
9.5.3 Classification Based on Rate Dynamics of Attacks
The Rate Dynamics of Attack are classified into two different rate attacks, namely Constant rate and Variable rate attack [15].
- Constant Rate: A constant rate function is used in the majority of documented attacks. Agent machines produce attack packets at a constant rate after the onset order is sent, typically as many as their resources allow. The victim’s services are easily disrupted by the unexpected packet surge.
- Variable Rate: Variable rate attacks change an agent machine’s attack rate to slow or stop detection and reaction.
9.5.4 Classification Based on Impact
Based on the impact of a DDoS attack on the target, we can distinguish among degrading and disruptive strikes [14].
- Disruptive Attack: Disruptive attacks aim to stop the target from providing service to its customers.
- Degrading Attack: The aim of degrading attacks is to drain a specific percentage of a target’s resources continuously. Because these threats don’t cause complete service interruption, they can go unrecognized for an extended period.
9.6 Transmission Control Protocol
Transmission Control Protocol (TCP) is a standard for establishing connections using IP suites. The communications devices should create a link before transmitting data and close the connection after transmitting the data, according to communication-orientation. HTTP, HTTPs, SMTP, FTP and Telnet use TCP.
9.6.1 TCP Three-Way Handshake
When a device needs to make a TCP/IP link (the most popular internet connection), it sends TCP/SYN and TCP/ACK packets of data to another computer, typically a server.
Steps performed during TCP 3-way handshake [17]:
- A randomized sequence number is sent by the client to the server in an SYN (synchronize) packet.
- The sender transmits an SYN-ACK packet with a randomized sequence number and an ACK that acknowledges the client’s sequence number.
- In response to the server sequence number, the client shares the ACK number with the server.

Figure 9.5 TCP 3-way handshake [17].
- Both sides use the same sequence numbers. Data will now be sent and received independently from both parties.
9.7 User Datagram Protocol
UDP is a TCP/IP data transfer protocol. Since UDP is a “stateless” protocol, it does not accept whether or not a packet has been sent. As a consequence, the UDP protocol is widely used in video streaming [18].
9.7.1 UDP Header
The UDP header is a plain 64-bits static header. Since each UDP port field is 2 bytes long, the port number range is 0 to 65535, with 0 being reserved. Various user queries or procedures are identified by port numbers.

Figure 9.6 UDP header [29].
- Source Port: Used to recognize several sources and is 16 bits long.
- Destination Port: Utilized to recognize the destined packet port and is 16 bits long.
- Length: It includes the UDP header and the data; is of 2-Bytes Field.
- Checksum: The field is 16-bits.
9.8 Types of DDoS Attacks
DoS (Denial of Service) assault is categorized in several ways depending on the network and the attacker’s actions. Because of their ease, Distributed Denial of Service (DDoS) attacks are becoming increasingly common with hacktivists, script kiddies, and hackers. In Figure 9.7, the types of DDoS attacks are divided by their attack characteristics. Here, the main five DDoS attack types are explained briefly.

Figure 9.7 DDoS attacks types [5].
9.8.1 TCP SYN Flooding Attack
TCP SYN flooding, also known as the TCP half-open attack, occurs when a user sends an SYN packet from the host to the server in order to create an approved TCP Connection. SYN and a valid source address may be used to establish a connection. The server responds with an ACK to the client’s SYN packet, then waits for the client’s response before allocating memory to that client. This wastes memory and time on the server. The victim server will buffer connection requests until the client responds after establishing a half-open connection. There is a timeout policy in place, and the connection will be terminated when the timer expires. The attacker sends SYN packet connection requests incessantly, outpacing the server’s ability to expire pending connection requests. Due to the following activity, 3-way handshake will be affected by DoS Attack [20].

Figure 9.8 TCP SYN flood [3].
9.8.2 UDP Flooding Attack
In UDP flooding, the attacker uses IP packets having UDP packets to target and exploit the host’s random ports as one type of huge volume DoS attack. During this type of attack, the hosts search for applications associated with specific datagrams. If none are found, the host returns to the sender with an “Unreachable Destination” envelope. As a result of the flood bombardment, the network will be overwhelmed and therefore unable to respond to legitimate traffic [21].
9.8.3 Smurf Attack
The Smurf attack utilizes the Internet protocol to bombard a DoS assault. It has several benefits over the Internet Control Message Protocol (ICMP) and the IP. The ICMP protocol is used by network components and administrators to communicate between nodes [20]. Massive groups of ICMP packets are transmitted to a network connection across an IP relay address, the majority of which use the target’s fake source IP. Devices on the web can respond by replying to the source IP address. If the number of devices receiving and reacting to this kind of packet on the network is large, traffic will overpower the attacker’s machine [21].

Figure 9.9 UDP flood [21].
9.8.4 Ping of Death Attack
It is a form of DoS attack where the attacker sends an IP packet of more than 65,536 bytes, which is permissible by the IP protocol. TCP/IP protocol fragments incoming packets into subpackets, which is one of its functions. When the attackers discovered the packet split into small packets totaling more than 65,536 bytes, they took advantage of this capability. When an extra-large packet is sent, several operating systems are unsure what to do. The operating systems eventually froze, rebooted, and/or crashed as a result [20].

Figure 9.10 Smurf attack [20].

Figure 9.11 Ping of death [20].
9.8.5 HTTP Flooding Attack
An HTTP flooding is a DDoS attack that is designed to overload a single server with HTTP-GET requests. There would be denial of service for individual queries by genuine users when the target has been flooded with inquiries and is unable to respond to normal traffic [21].
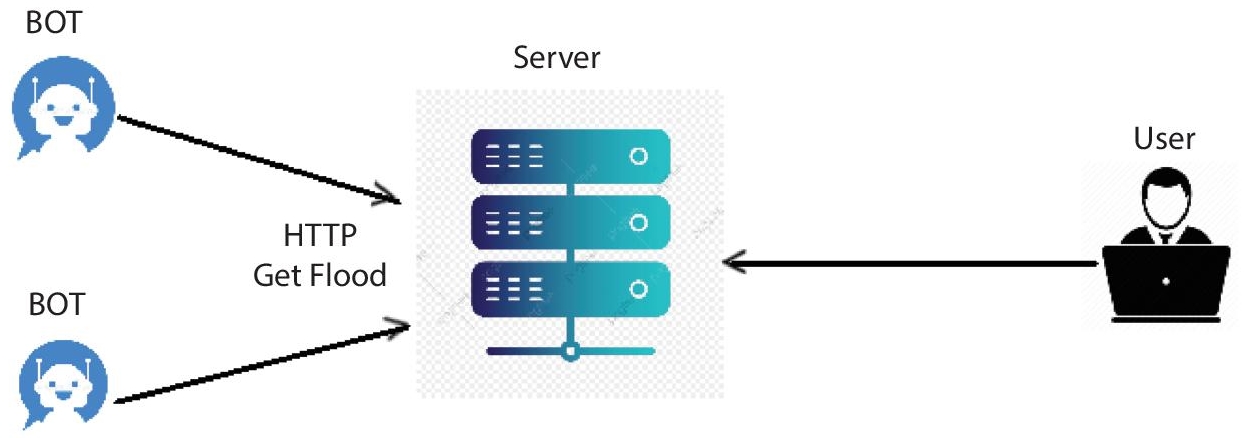
Figure 9.12 HTTP flood attack [21].
9.9 Impact of DoS/DDoS on Various Areas
9.9.1 DoS/DDoS Attacks on VoIP Networks Using SIP
The mechanism for transmitting speech and visual information through Internet Protocol (IP) networks is known as Voice over IP (VoIP). As a result of its inexpensive and high level of support, VoIP systems are displacing traditional solutions around the world. With fifth-generation voice service, VoIP is anticipated to be the leading platform for (5G) networks. The Session Initiation Protocol (SIP) is implemented by most VoIP networks to conduct signaling methods. SIP is a simple text-based protocol that can be attacked in a variety of ways. The intruder normally goes after the SIP server to discourage consumers from utilizing VoIP resources or to lower the efficiency of the services provided. Flooding and malformed communications are the most common DoS attacks [22].
9.9.2 DoS/DDoS Attacks on VANET
A vehicular Ad hoc Network (VANET) is a form of network in which vehicle nodes can connect on the road in a multi-hop manner. VANET is concerned about the safety of human life when people are on the road. It aims to provide accurate data to road drivers. Because of the design of the open wireless interface used in VANET, the VANET is vulnerable to a variety of attacks. The attackers’ goal is to cause problems for legitimate users, resulting in services becoming unavailable, resulting in a denial of service. The following are the possible DoS attacks [23].
- Sybil Attack.
- Node Impersonation.
- Sending False Information.
- ID Disclosure.

Figure 9.13 DOS attack in vehicle-to-infrastructure communications [23].

Figure 9.14 DOS attack in vehicle-to-vehicle communications [23].
9.9.3 DoS/DDoS Attacks on Smart Grid System
A smart grid system is an electricity grid that incorporates several operational and energy-saving features, such as Smart distribution boards and circuit breakers, advanced metering technology, solar energies, energy-efficient resources, and enough utility-grade optical fiber [25].
The following are some characteristics of the Smart Grid network infrastructure:
- Traffic model.
- Communication model.
- Protocol stack.
- Timing requirement.
Although IEC 61850 is focused on TCP/IP and Ethernet, IEDs in a power station can become victims of DoS attacks such as movement flooding and TCP SYN attack. Jamming attacks can also become a key security concern as wireless devices are implemented in a substation [24].
9.9.4 DoS/DDoS Attacks in IoT-Based Devices
The Internet of Things (IoT), which anticipates the automated connectivity of sensors and devices while providing a variety of smart facilities, has sparked a huge market for embedded devices. However, the computing, storage, and networkability of these IoT devices are minimal, making them easy to exploit. Due to the low support of strong security mechanisms in IoT devices, they easily get exposed and attackers take advantage of the same; by interfering with malicious networks they can easily perform DoS and DDoS attacks [26].
9.10 Countermeasures to DDoS Attack
Preventing initial device compromises is the main protection against DDoS attacks. In most cases, this entails downloading fixes, antivirus applications, configuring a firewall, and keeping an eye out for intruders. The most attentive hosts, though, may become targets as a result of less equipped, less security-aware hosts. It’s hard to monitor against being the ultimate target of a DDoS attack, but it’s a lot easier to protect against being used as a zombie or master machine.
9.10.1 Prevent Being Agent/Secondary Target
The avoidance of secondary victim networks to engage in DDoS attacks is among the most successful ways to prevent DDoS attacks. To prevent secondary targets from being compromised with the DDoS zombie malware, these devices must constantly monitor their defense. They should ensure there are no zombie programs installed on their networks, and that zombie data traffic is not indirectly sent through the network.

Figure 9.15 Countermeasures to DDoS attack [27].
9.10.2 Detect and Neutralize Attacker
To stop attackers from performing DDoS attacks, victims need to detect and neutralize handlers. Examining the network protocols and collecting network traffic between attackers and agents or attackers and clients is one method for identifying network nodes that could be compromised by attacker malware. So, finding and shutting the handler down will neutralize the DDoS attack.
9.10.3 Potential Threats Detection/Prevention
Egress filtering and MIB (Management Information Base) figures may be used to recognize or deter a feasible DDoS assault. Egress filtering is the process of scanning IP packet headers and checking if it is fulfilling their criteria. The packets are routed outside of the network from which they are derived if they meet the requirements. If anything in the packets does not follow the requirements, it will not be sent. If the system administrator installs a firewall in the sub-network to block any packets without a source IP address from the sub-network, several DDoS packets with duplicate/ fake IP addresses will be discarded.
9.10.4 DDoS Attacks and How to Avoid Them
All regular and DDoS attacks will benefit from load balancing. To prevent critical links from going down in an attack, network operators may improve bandwidth on them. Another method suggested to save the system from shutting down is throttling. The server-centric Max-min Fair router throttle approach configures routers that connect to a server with a logical function that adjusts (throttles) arriving packets to server-capable speeds. This will protect servers from flood damage.
9.10.5 Deflect Attack
Honeypots are networks that are knowingly set up for low security to catch an attacker. Honeypots are used to prevent threats from reaching the networks they are defending, as well as to gather intelligence about threats by recording their actions and discovering what types of attacks and technical techniques they are using. By tracking the attacker, we get to know about the attacker and can defend against him in the future.
9.10.6 Post-Attack Forensics
If data on traffic patterns is collected throughout a DDoS attack, it could be studied afterward to check for unique features in that malicious attack. This feature information could be utilized to improve the reliability and security capacity of load balancing and throttling countermeasures by upgrading them. Packet traceback methods are recommended to aid in the identification of the perpetrators. The idea is to follow Internet traffic back to its origin. This method aids in the detection of the intruder and the network operator can discover what kind of DDoS attack it is [27].
9.11 Conclusion
In this chapter, it’s concluded that Denial of Service (DoS) and Distributed Denial of Service (DDoS) are effective attacks that cause huge resource and financial losses. There are several tools available on the Internet which make it easy for an attacker to target a zombie/agent or a DoS victim. A DoS attack disturbs the whole flow of computer traffic by transferring a huge amount of data packets and requests to the victim machine. Due to the rapid development of technologies, the number of Internet users who fear DoS attacks is rapidly growing. Data gathered by Arbor Network shows that the frequency of attacks is gradually increasing year by year. The timeline shows that these attacks are carried out mainly to disturb popular companies such as GitHub, Amazon, CNN, Airbnb, Spotify, PayPal, Netflix, Visa, The New York Times, Reddit, and many others to exploit their resources, to degrade the services to the client, etc. To be safe from these DoS and DDoS attacks every person on the Internet should take some countermeasures like preventing being an agent, trying to detect and neutralize attackers, using deflection techniques to deflect attacks, etc. Due to DoS attacks on IoT systems, a Software-Defined Networking (SDN) protection approach can be used to identify and minimize DoS and DDoS attacks using the principle of entropy as the detection mechanism [26]. Various studies suggested routing protocols to boost the stability of multi-hop networks against DoS attacks. Specifically, in the context of mobile ad hoc networks (MANETs), the logical topology changes over time using routing protocols which help to avoid such DoS attacks [30].
9.12 Future Scope
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks cannot be completely stopped due to lack of expertise and proper defense mechanisms; these attacks are not stopping soon. DOS attacks on network-based devices are a frequent phenomenon in cloud services, but they can be mitigated by introducing third-party checkpoint access [20]. Since the speed and bandwidth of 5G is much higher than the previous generation, companies will be transitioning to VoIP systems worldwide and the vulnerability in the SIP method used in VoIP gives freedom to attackers to carry out DoS attacks [22]. As different research is going on to detect DoS and DDoS attacks, a Network Function has been developed which can be used to implement as a dedicated module in the network. This will allow the identification mechanism more versatility to align with other 5G system foundations like NFV [26]. In the near future, plenty of control systems are planned to adopt wireless technology, which increases the threat of frequent DoS attacks so more cyber professionals need to do important research in this field [30].
References
- 1. Ormiston, Kathryn & Eloff, Mm. (2006). Denial-of-Service & Distributed Denial-of-Service on The Internet. 1-14.
- 2. Abliz, M., 2011. Internet denial of service attacks and defense mechanisms, [online] Available at: <https://blog.oureducation.in/wp-content/uploads/2014/06/Internet-Deniel.pdf>.
- 3. Ali, Murad M., 2006. Intrusion Detection, Denial of Service (DoS). [ebook] New York: New York Institute of Technology (NYIT), Amman’s campus. Available at: <https://www.just.edu.jo/~tawalbeh/nyit/incs745/presentations/DoS.pdf>.
- 4. Help Net Security. 2021. For enterprises, malware is the most expensive type of attack - Help Net Security. [online] Available at: <https://www.helpnetsecurity.com/2019/03/07/cyberattack-cost-2018/> .
- 5. Mahjabin, T., Xiao, Y., Sun, G. and Jiang, W., 2017. A survey of distributed denial-of-service attack, prevention, and mitigation techniques. International Journal of Distributed Sensor Networks, 13(12), p.155014771774146.
- 6. Cybercrime Magazine. 2021. The 15 Top DDoS Statistics You Should Know in 2020. [online] Available at: <https://cybersecurityventures.com/the-15-top-ddos-statistics-you-should-know-in-2020/>.
- 7. Us.norton.com. 2021. What Are Denial of Service (DoS) Attacks? DoS Attacks Explained. [online] Available at: <https://us.norton.com/internetsecurity-emerging-threats-dos-attacks-explained.html#:~:text=A%20bit%20of%20history%3A%20The,research%20lab%20to%20power%20off.>.
- 8. En.wikipedia.org. 2021. Denial-of-service attack. [online] Available at: <https://en.wikipedia.org/wiki/Denial-of-service_attack>.
- 9. Cs.columbia.edu. 2021. [online] Available at: <https://www.cs.columbia.edu/~smb/classes/f06/l22.pdf>.
- 10. Us.norton.com. 2021. What is a DDoS attack?[online] Available at: <https://us.norton.com/internetsecurity-emerging-threats-what-is-a-ddos-attack-30sectech-by-norton.html>.
- 11. Tools.cisco.com. 2021. What Is the Difference: Viruses, Worms, Trojans, and Bots? [online] Available at: <https://tools.cisco.com/security/center/resources/virus_differences#dos_attacks>.
- 12. www.kaspersky.com. 2021. What is a Trojan Virus? [online] Available at: <https://www.kaspersky.com/resource-center/threats/trojans>.
- 13. Gu, Q & Liu, P 2012, Denial of Service Attacks. In Handbook of Computer Networks. vol. 3, John Wiley and Sons, pp. 454-468. https://doi.org/10.1002/9781118256107.ch29
- 14. Mirkovic, Jelena, Martin, Janice & Reiher, Peter. (2003). A Taxonomy of DDoS Attacks and DDoS Defense Mechanisms.
- 15. Mirkovic, J. and Reiher, P., 2004. A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Computer Communication Review, 34(2), pp.39-53.r
- 16. Mishra, Anjana & Ghosh, Soumitra & Mishra, Brojo. (2019). Cybersecurity: A Practical Strategy Against Cyber Threats, Risks with Real World Usages. 10.1002/9781119488330. ch13.
- 17. Hsu, F., Hwang, Y., Tsai, C., Cai, W., Lee, C. and Chang, K., 2016. TRAP: A Three-Way Handshake Server for TCP Connection Establishment. Applied Sciences, 6(11), p.358.
- 18. Techterms.com. 2021. UDP (User Datagram Protocol) Definition. [online] Available at: <https://techterms.com/definition/udp>.
- 19. Mishra, Anjana & Bisoy, Sukant. (2018). Understanding the Aspect of Cryptography and Internet Security: A Practical Approach.
- 20. Gunasekhar, T., Rao, K., Saikiran, P. and Lakshmi, P., 2014. A Survey on Denial of Service Attacks. International Journal of Computer Science and Information Technologies, [online] 5 (2). Available at: <http://ijcsit.com/docs/Volume%205/vol5issue02/ijcsit20140502320.pdf>.
- 21. Arshi, M., Nasreen, M. and Madhavi, K., 2020. A Survey of DDOS Attacks Using Machine Learning Techniques. E3S Web of Conferences, 184, p.01052.
- 22. Nazih, W., Elkilani, W., Dhahri, H. and Abdelkader, T., 2020. Survey of Countering DoS/DDoS Attacks on SIP Based VoIP Networks. Electronics, 9(11), p.1827.
- 23. Hasbullah, Halabi&Soomro, Irshad& Ab Manan, Jamalul-Lail. (2010). Denial of service (DOS) attack and its possible solutions in VANET. 65.
- 24. Chourasia, A. and Chourasia, A., 2017. An analysis and review against Denial of service attack for smart grid system. International Research Journal of Engineering and Technology (IRJET), [online] 04(05). Available at: <https://www.irjet.net/archives/V4/i5/IRJET-V4I5366.pdf>.
- 25. En.wikipedia.org. 2021. Smart grid. [online] Available at: <https://en.wikipedia.org/wiki/Smart_grid>.
- 26. Galeano-Brajones, J., Carmona-Murillo, J., Valenzuela-Valdés, J. and Luna-Valero, F., 2020. Detection and Mitigation of DoS and DDoS Attacks in IoT-Based Stateful SDN: An Experimental Approach. Sensors, 20(3), p.816.
- 27. Stephen M. Specht and Ruby B. Lee, Distributed Denial of Service: Taxonomies of Attacks, Tools, and Countermeasures. Proceedings of the 17th International Conference on Parallel and Distributed Computing Systems, 2004 International Workshop on Security in Parallel and Distributed Systems, pp. 543-550.
- 28. Prakash, A. &Murali, Satish &Bhargav, T. & Natarajan, Bhalaji. (2016). Detection and Mitigation of Denial of Service Attacks Using Stratified Architecture. Procedia Computer Science. 87. 275-280. 10.1016/j. procs.2016.05.161.
- 29. Kamil, Wisam & Awang Nor, Shahrudin & Alubady, Raaid. Research Article Performance Evaluation of TCP, UDP and DCCP Traffic Over 4G Network. Research Journal of Applied Sciences, Engineering and Technology. 11. 1048-1057, 2015. 10.19026/rjaset.11.2118.
- 30. Cetinkaya, A., Ishii, H. & Hayakawa, T., 2019. An Overview on Denial-of-Service Attacks in Control Systems: Attack Models and Security Analyses. Entropy, 21(2), p. 210. Available at: http://dx.doi.org/10.3390/e21020210.
Note
- *Corresponding author: [email protected]
