3
Enhanced Image Security Through Hybrid Approach: Protect Your Copyright Over Digital Images
Shaifali M. Arora and Poonam Kadian*
Maharaja Surajmal Instutute of Technology C-4, Janakpuri, New Delhi, India
Abstract
The security of the watermark against unauthorized detection is a major point of concern. If some illicit user can detect the watermark from the watermarked image then he can very easily remove that watermark by making the image copyright-free or he may also remove the originally embedded watermark and insert his watermark. In both ways, the illicit user can diminish the original owner’s copyright over the image. This leads to the requirement of methods that can provide security against the unauthorized detection of the watermark. To find the solution to this problem, a greatly secure grayscale image watermarking algorithm that uses DWT-SVD approach has been proposed. In this work, a balance between robustness and imperceptibility has also been retained. It is apparent that the proposed algorithm provides improvised robustness and imperceptibility and the method is providing security to the watermark as well.
Keywords: Watermarking, discrete wavelet transform, SVD, imperceptibility, robustness
3.1 Introduction
In the past few decades, the popularity of internet technology has increased enormously. It has led to easiness in communication and dissemination of digital documents such as image, video, text, and audio. However, the very conveniently available image processing tools make it even easier to duplicate, modify, and redistribute such multimedia data. These acts of copying, modifying and redistribution of digital data violate the intellectual property rights of the multimedia data owner. Hence, copyright protection of digital data has emerged as a potential area of research in the current scenario [1–4]. To address the issues related to copyright protection of multimedia data, a large number of data security techniques are proposed in the literature, and these are illustrated in Figure 3.1. Digital watermarking has evolved as a very effective information security technique for copyright protection or copyright authentication. Broadly, these approaches can be characterized as the Cryptography approach and Information Hiding approach [5]. In cryptographic methods, the message has been changed to a higly protected format which can be decrypted and recuperated by certified users only. But the disadvantage of this technique is that after decoding of the message, it does’t remain secure. Also, the procedure involved in cryptography is more complex than information hiding. Watermarking and Steganography techniques for information hiding are less complex and secure than cryptography techniques.
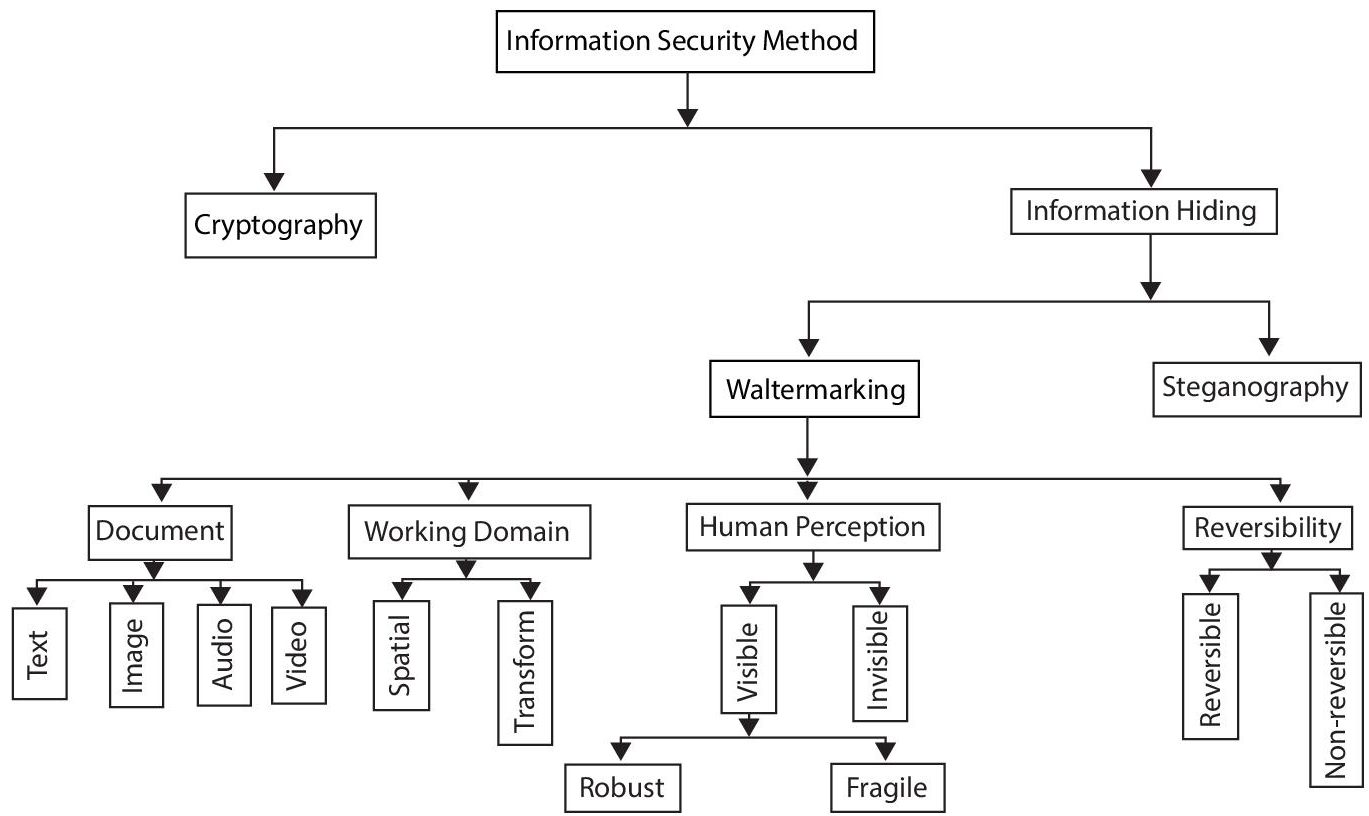
Figure 3.1 Classification of information hiding methods.
In Steganography, the expected recipient can only recognize the presence of hidden information. However; most users can’t even detect the presence of a message, which hinders its use in multimedia-based applications. In steganography, the message and watermark need to be uncorrelated to each other. However, in watermarking-based encryption technique message and watermark may or may not be correlated to each other.
The watermark embedding approach used in steganography and watermarking method makes the two technques different. In watermarking technique, the embedded watermark may be visible or not but in steganography technique the watermark is always invisible. Figure 3.2 highlights the main features of three techniques – steganography, cryptography and watermarking. Among these three, watermarking is the most widely used in multimedia-based applications, for copyright protection or copyright authentication.
Imperceptibility and robustness are the two key parameters that decide the performance of the digital watermarking algorithm. A trade-off between the two parameters needs to be maintained as these are interrelated. There are numerous approaches proposed in the literature that address this issue. However, there is no unique digital watermarking method available that provides security against all possible threats to multimedia data [6, 7].
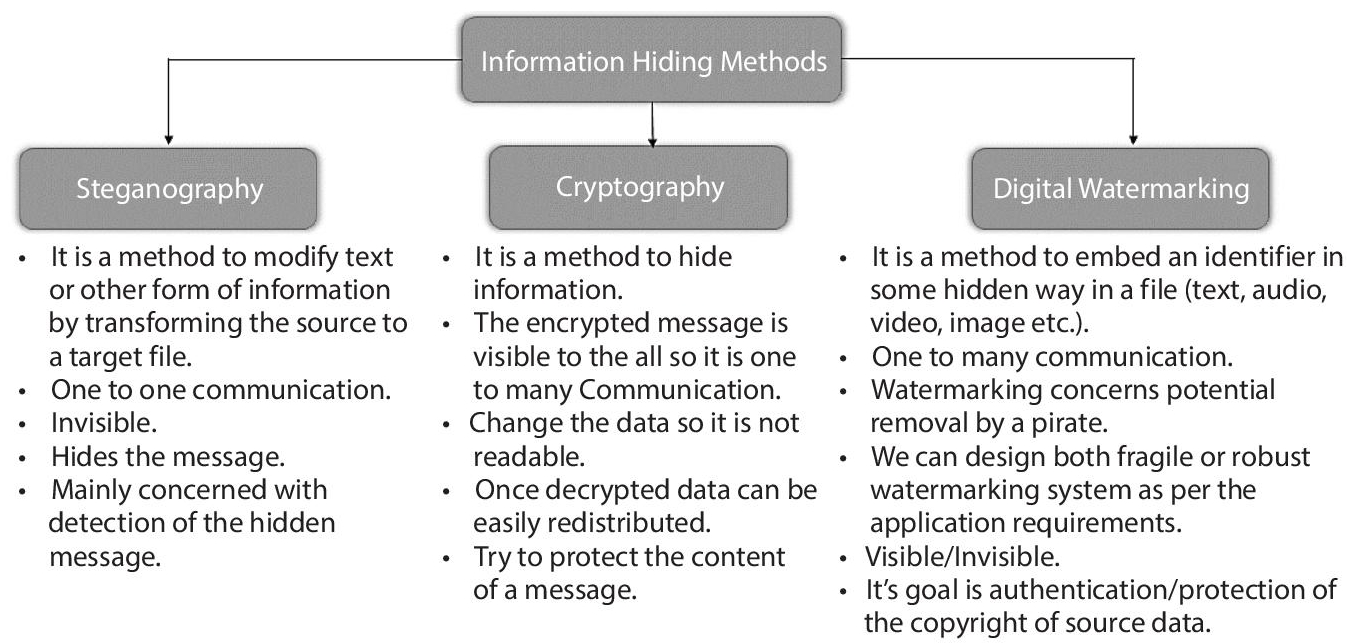
Figure 3.2 Difference between steganography, cryptography, and digital watermarking.
3.2 Literature Review
A watermark can be embedded in an image either in spatial domain or in transform domain. The pixel values of the host image are directly altered in watermarking in spatial domain but the only advantage is that it is very simple to implement and provides high data capacity. In this technique, security can be enhanced by embedding a watermark multiple times that will help the survival of the watermark in case of attacks. However, spatial domain techniques of watermarking suffer from image processing attacks like compression, rotation, etc. [1, 14].
Another way of embedding a watermark is transform domain. In this technique, host image and watermarked image are transformed in frequency domain, followed by embedding watermark coefficients in the host image keeping in view the human visual system (HVS). Transform domain techniques have shown better robustness and imperceptibility compared to spatial domain techniques [8–10].
Various transformation techniques like Discrete Fourier Transform (DFT) [10], Discrete Cosine Transform (DCT) [11], Discrete Wavelet Transform (DWT) [12, 13], fractional Fourier Transform (FrFT) [14], Discrete fractional Cosine transform (DFrCT) [15], some linear algebra transform methods such as singular value decomposition (SVD) [16], and QR decomposition [17], are executed to accomplish improved imperceptibility and robustness in digital watermarking [18–24].
I.J. Cox (1997) [1] has given a DCT-based non-blind digital watermarking algorithm. C.T. Hsu et al. (1998) [25] suggested a multi-resolution watermarking algorithm that uses sub-band DWT coefficients of the host image and watermark images. The algorithm showed good robustness and imperceptibility for common image processing attacks but suffered with geometric attacks.
C.T. Hsu et al. (1999) [16] proposed an algorithm in which the middle-frequency DCT coefficients are explored for embedding the watermark without affecting the low-frequency coefficients.
Wen-Nung Lie et al. (2000) [26] proposed a robust algorithm that gives better performance for different geometric and non-geometric attacks by calculating coefficients DCT inserting watermark coefficients in its middle band and also during the extraction of watermark the host image is not required. When compared with [27] it showed that the algoritm is computationally expensive and couldn’t sustain cropping attacks.
M. Barni et al. (2001) [28] developed an algorithm that is based on a pixel-wise masking model which uses HVS properties to improve watermark indistinctness and robustness. Pixel by pixel masking is performed to compute the local brightness and texture; however, only this information is not at all sufficient for brightness or texture calculation.
W.C. Chu (2003) [18] proposed a subsampling technique that used random perturbation of DCT coefficients that belong to various sub-images. It’s a blind watermarking algorithm. The algorithm shows good performance, better robustness compared to re-watermarking, collusion attacks, noise addition and high pass filtering; however, it suffers compression attacks.
S.U. Liyun et al. (2006) [29] proposed Fuzzy c-means-based adaptive image watermarking algorithm for classifying image blocks into two categories. To fine-tune the power of the watermark frequency masking technique is used. The algorithm showed good performance against various image processing attacks.
V.S. Verma (2013) [30, 31] has suggested an algorithm in which the difference between LWT coefficients is taken. Then randomly scrambling of CH3 sub-block sub-bands is done, followed by insertion of watermark into the obtained largest coefficients. This algorithm showed good robustness for different geometric and non-geometric attacks and also better visible quality in comparison to algorithms using the same methodology [32–35].
Singh et al. (2014) [36] proposed a new multi-transform-based robust watermarking scheme. The host image is transformed by applying DWT and HH sub-band is obtained, followed by DCT and then SVD to obtain the watermarked image. This algorithm used multiple transformations on the host imagemaking it complex. Ahmad et al. (2014) [37] proposed a three-level 2D DWT watermarking algorithm and in this LL sub-band coefficients obtained by applying DWT to watermark image and the host image are used in the watermark embedding process. Algorithms performed well against various geometic attcaks at the cost of increased complexity.
Rahman and Rabbi (2015) [38] proposed a watermarking algorithm for colored images that used DWT and SVD. Vaidya and Mouli (2015) [39] presented an adaptive watermarking algorithm that explored B&K methods to estimate the scaling factor. Simulation results showed the superiority of the proposed algorithm compared to similar algorithms in [40, 41].
Jamal et al. (2016) [42] proposed a substitution box-based semi-fragile watermarking technique. DFT has been used to decompose the host image and a chaotic map is used to embed the watermark.
A histogram-based robust image watermarking algorithm has been proposed in [43, 44]. The feature points from the color image are extracted using the probability density-based features. Algorithm showed better performance when compared with other similar algorithms in [45–48].
Lei et al. (2017) [49] proposed a robust watermarking technique that combines multiple watermarks while embedding. Singh et al. (2017) [51] pooled different transformation methods – Contourlet Transform, Redundant DWT and SVD to embed the watermark and showed better robustness and imperceptibility compared to other similar methods like [50, 52, 53].
Amini (2017) designed a blind watermark decoder by using HMM [54]. Substantial improvements in robustness have been shown compared to similar techniques offered in literature [55, 56]. Issue of FPP of SVD has been addressed by Makbol et al. (2018) [57] and he considered existing DWT-SVD and RDWT-SVD algorithms but with FPP.
Zhou et al. (2018) [58] proposed DWT, DCT and DFRNT based watermarking algorithm which is extremely secure. A DWT and encryption based watermarking algorithm for copyright protection of images has been proposed by Ambadekar et al. (2018) [59]. Recently, Artificial Neural Network and Machine learning based algorithms [60–66] have been suggested to improve the performance of conventional watermarking algorithms. The grouping of watermarking techniques, metrics for analyzing the performance of the digital images has also been presented.
3.3 Design Issues
There are certain design issues [11] in Digital watermarking systems such as robustness against various attack situations, distortion and visual quality, working domain, Human Visual System (HVS), a balance between imperceptibility, robustness, computational cost, etc. These issues are discussed in detail below.
3.3.1 Robustness Against Various Attack Conditions
The attackers in a digital watermarking system can be classified as a Passive attacker and an active attacker. The passive attacker doesn’t harm the watermarked image directly; instead, he just detects the presence or absence of the watermark. However, the active attacker will extract the watermark and will try to alter or destroy the watermark. So, the active attacker can alter the copyright over the watermarked image. In actual scenarios, the transmitted watermarked image travels through wired or wireless channels, and in this course, it faces several image processing or geometric attacks [10]. Figure 3.3 shows the possible cracking of the watermarking system by passive and active attackers. It has been observed that most of the available watermarking methods are resistant to compression, filtering, and some other conventional image processing attacks but they lag in providing enough robustness against geometric attacks.

Figure 3.3 Breaking watermarking system by possible attackers.
Hence, it becomes an important issue to design a watermarking system that can provide robustness against geometric attacks as well. Along with robustness, it is also very important to make the watermark secure against unauthorized detection and hence alteration.
3.3.2 Distortion and Visual Quality
The visual quality of the host image is directly affected upon insertion of the watermark. The distortions introduced during the watermark insertion process and due to the intentional/unintentional attacks across the channel are generally asymmetric in nature, hence there is a wide range of Peak Signal to Noise Ratio (PSNR). It helps in evaluation of imperceptibility offered by any watermarking scheme. Hence the imperceptibility of the watermarked image is proportional to the PSNR attained.
3.3.3 Working Domain
The most significant bit (MSB) and least significant bit (LSB) are the two most widely adopted spatial domain watermarking methods. Figure 3.4 showcases a sample of insertion of watermark bits over the host image, the generation of watermarked bits, and finally, the major changes introduced extracted watermarking bits using the LSB-based watermarking method in the spatial domain [67]. The major advantage of LSB-based watermarking schemes over MSB-based watermarking schemes is that the LSB watermarking introduces less distortion as compared to MSB watermarking schemes. Spatial domain watermarking methods are computationally less expensive and easy to implement but these methods offer much less robustness against the imposed attacks, low imperceptibility, and less security to the watermark as compared to the transform domain watermarking methods. In transform domain methods, instead of modifying the pixels directly, the watermark is inserted on the transformed coefficients of the host image.

Figure 3.4 An example of LSB Spatial Domain Watermarking [69].
3.3.4 Human Visual System (HVS)
The visual quality or the imperceptibility parameter in the digital image watermarking methods can be achieved by exploiting the features of the HVS while designing the watermarking system. It has been observed that the multi-resolution property of Discrete Wavelet Transform (DWT) makes it similar to HVS [68]. Hence, where the imperceptibility parameter is an important parameter in a watermarking system DWT is preferred.
3.3.5 The Trade-Off between Robustness and Imperceptibility
It is desired that the designed watermarking system should be capable of providing high imperceptibility, robustness towards the attacks, high fidelity, and security [70, 71]. The watermarking system should be able to insert a maximum capacity watermark without severe deterioration in the imperceptibility of the host image and ensure removal of watermark from the host image shouldn’t be easy. The fundamental issue in the design of a digital image watermarking system is to achieve a balance between imperceptibility and robustness because these parameters conflict with each other.
3.3.6 Computational Cost
Computational cost or time complexity is another major aspect of digital image watermarking. The designed watermarking scheme should be able to execute efficiently by consuming minimum execution time. To maintain a balance between robustness and imperceptibility various available GA or optimization techniques can be used. But these optimization methods take much execution time, hence designing a computationally efficient digital watermarking method is a very important design issue [71].
3.4 A Secure Grayscale Image Watermarking Based on DWT-SVD
In this section, a grayscale image watermarking method using DWT-SVD is explained. While designing this watermarking method the design issues such as security of the watermark from any unauthorized detection, high robustness, and high imperceptibility are taken care of.
Watermark Insertion Process
Let an image I[x, y] be the original grayscale host image. The watermark image is a grayscale image of size M x N. the low frequencies of the host image has been extracted by using 2 level RDWT and the SVD has been applied over those low frequencies. The flowchart of the algorithm has been depicted in Figure 3.5 and the steps involved in the implementation of this algorithm are as discussed below.
The steps involved in the watermark insertion process:
- Insert the encryption key.
- 2 level DWT decomposition is applied over the original host image to extract all the four sub-bands LL, LH, HL, and HH.
- SVD is applied over the LL sub-band to extract S, U, and V matrices from the LL sub-band of the host image.
- Take the S matrix obtained in step 2 for the watermark insertion process.
- 2 level DWT decomposition is applied over the original watermark image to extract LL, LH, HL, and HH sub-band.
- SVD has been applied over the LL sub-band to extract S, U, and V matrices from the LL sub-band of the watermark image.
- Take the S matrix obtained in step 5 for the watermark insertion process.
- Select the position in the S matrix of the host image.
- Apply watermark insertion algorithm. The resultant image would be the watermarked image.
- Apply image processing attacks over the watermarked image.
The steps involved in the watermark extraction process are as follows:
- Check the encryption key. If the key matches go to step 2 of the extraction process, else flash the message “Not an authorized user”.
- Over the distorted watermarked image obtained from step 8, apply the watermark extraction process.
- Retrieve the watermark from step 1 of the extraction process.
- Compare the extracted watermark with the original watermark.
- Calculate SSIM for the comparison of the step above. This comparison defines the robustness of this algorithm.

Figure 3.5 The flowchart of proposed algorithm.
3.5 Experimental Results
The simulation results with their analysis and comparison with the state-of-the-art methods are demonstrated in this section. The efficiency of this proposed method in terms of robustness and imperceptibility is evaluated with the help of standard IQA parameters such as PSNR and NC. PSNR has been used to define the offered imperceptibility whereas NC defines the robustness of the offered method. All the simulations are performed over Intel(R) Core i7-4600U CPU @ 2.10GHz Windows 10 with 8 GB RAM in MATLAB 2017 Platform. Haar wavelet is used to extract the features to achieve imperceptibility in the watermarking system. Standard test images Cameraman and Lena in .tiff format are used as the original host images and the letter A image in .tiff is used as the watermark. Figure 3.6 depicts the host and watermark image used in the experimental study for the analysis of the proposed method. The cameraman and Lena image both are 256X256 whereas the watermark image is of the size 64X64.
The watermarked host images (Cameraman and Lena) without attack, along with their extracted watermark and attained values of PSNR and NC are presented in Figure 3.7. It is evident for this figure that PSNR value of 52.78 and 54.82 is achieved for the Cameraman and Lena image, respectively, which shows that the imperceptibility offered by this proposed method is quite high when the watermarked image is not attacked.
To validate the proposed watermarking method both the host images are exposed to attacks blurring, cropping, the addition of Gaussian noise, resize, salt & pepper noise, rotation, and sharpening. The effect of imposed attacks on Lena image is shown in the first column of Figure 3.8; the second and third column of this figure show the extracted watermark from the attacked watermarked image and the value of NC, respectively. The value of NC determines the robustness of this method. It can be seen that a very high value of NC (above 0.90) is achieved for the attacks Gaussian noise, salt & pepper noise, resize, and sharpening, and for the attacks cropping and rotation NC value is 0.8922 and 0.8843 which is also practically feasible to provide robustness. However, this proposed method is not able to attain a high NC for the rotation attack. For rotation attack, the value of NC is 0.6970.

Figure 3.6 (a) Original host image Cameraman, (b) Original host image Lena, and (c) watermark image.

Figure 3.7 (a) Watermarked Cameraman image and extracted watermark when non-attacked, with PSNR and NC value (b), Watermarked Lena image and extracted watermark when non-attacked, with PSNR and NC value.
After analyzing the efficiency of the proposed technique in terms of robustness and imperceptibility, finally, the efficacy of the recently proposed method is evaluated by equating this method with other state-of-the-art methods [59 and 60]. The comparison results are presented in Tables 3.1 and 3.2, and the summary of this comparison is as discussed below:
Firstly, Table 3.1 shows that the PSNR value obtained by using the proposed method is higher than the techniques offered in [59, 60]. For the Cameraman image these methods can attain a PSNR value of 41.57 dB, whereas our proposed method is attaining the value of PSNR as, 52.78 dB for the same cameraman image. This improvement in attained PSNR from [59] hold for the Lena image as well. We have achieved a PSNR value of 54.82 dB for the Lena image, which is a significant improvement in PSNR from [59 and 60].
Secondly, we can observe from Table 3.2 that the NC values obtained using the proposed method are higher than the methods listed in [10] against the image processing attacks. In this table the NC values for the non-attacked watermarked image (for both Cameraman and Lena image) and the same watermarked image when exposed to various attacks like blurring, cropping, the addition of Gaussian noise, salt & pepper noise, resize, sharpening, and rotation is tabulated. Column 1 lists the state of the watermarked attack, i.e., whether unattacked or intentionally/unintentionally attacked. Column 2 lists the NC value for the Cameraman image using the method proposed in [7]. The NC values for the Lena image for the proposed methods in [10] is demonstrated in column 3 of this table. Columns 4 and 5 show the NC values of the Cameraman and Lena image obtained using the recently proposed method. From this table, it is evident that a high NC value for extracted watermark is obtained by using our proposed method.


Figure 3.8 (a) Blurring attack on Lena image, (b) cropping attack on Lena image, (c) addition of Gaussian noise i Lena image.
Table 3.1 PSNR values for the Cameraman and Lena image.
| The result obtained by the approach presented in [59 and 60] | The result obtained by the approach presented in [59 and 60] | Proposed method | Proposed method |
|---|---|---|---|
| Cameraman | Lena | Cameraman | Lena |
| 41.57 | 45.9 | 52.78 | 54.82 |
Table 3.2 NC values for the Camraman and Lena image.
| The result obtained by the approach in [3, 13] | The result obtained by the approach in [3, 13] | Proposed method | Proposed method | |
|---|---|---|---|---|
| Images/ Attacks | Cameraman | Lena | Cameraman | Lena |
| No Attack | 0.9990 | 0.9845 | 0.9999 | 0.9983 |
| Blurring | 0.6108 | 0.6658 | 0.6576 | 0.6970 |
| Cropping | 0.7140 | 0.6672 | 0.9441 | 0.8922 |
| Gaussian Noise | 0.9929 | 0.9702 | 0.9579 | 0.9921 |
| Salt & Pepper Noise | 0.8918 | 0.8726 | 0.9640 | 0.9401 |
| Resize | 0.7466 | 0.7713 | 0.9640 | 0.9401 |
| Sharpening | 0.7942 | 0.7741 | 0.8657 | 0.8843 |
| Rotation | 0.9636 | 0.9517 | 0.9737 | 0.9744 |
It is evident from Table 3.2 that high NC and hence high robustness can be achieved using this proposed method. This is due to the following reasons:
- We have selected low-frequency coefficients for the watermark insertion procedure which provide high resistance towards the image processing attacks.
- The presence of energy preservation property makes the low-frequency coefficients more tolerant against any image distortion.
- The inclusion of a security key enhances the security of the watermark against unauthorized detection.
The PSNR and NC plots are demonstrated in Figures 3.9 and 3.10, respectively.
![Schematic illustration of PSNR values for the results obtained by the method proposed in [7, 10] and our proposed method.](https://imgdetail.ebookreading.net/2023/10/9781119777144/9781119777144__9781119777144__files__images__c03_image_17_4.jpg)
Figure 3.9 PSNR values for the results obtained by the method proposed in [7, 10] and our proposed method.
![Schematic illustration of PSNR values for the results obtained by the method proposed in [7, 10] and our proposed method.](https://imgdetail.ebookreading.net/2023/10/9781119777144/9781119777144__9781119777144__files__images__c03_image_17_6.jpg)
Figure 3.10 PSNR values for the results obtained by the method proposed in [7, 10] and our proposed method.
3.6 Conclusion
In this chapter, a novel grayscale image watermarking method in the hybrid domain using DWT and SVD hybridization is presented. This proposed method is highly secure against the unauthorized watermark extraction attempted by any Active attacker. Using the Haar wavelet decomposition in DWT we have extracted the low-frequency coefficients for the watermark embedding process. The watermark insertion over the low-frequency coefficients makes this proposed method robust against most of the image processing attacks. The watermark is inserted over the S coefficients extracted from these low-frequency coefficients, which makes this method more robust. The locations for the watermark insertion from these S coefficients are selected based upon the security key. Experimental analysis of the proposed methods and comparison with two state-of-the-art methods showcased that the proposed scheme offers better imperceptibility and robustness against the image processing attacks such as blurring, cropping, the addition of Gaussian noise, resize, salt & pepper noise, rotation, and sharpening.
The proposed method in this work is semi-blind because, during the watermark extraction process, we require the original watermark image. As the proposed method offers high performance in terms of robustness and imperceptibility along with enhancement in the security of the watermark, this method can be used for digital watermarking applications where copyright protection, copy protection, and ownership assertion are foremost required.
References
- 1. Cox, I. J., Kilian, J., Leighton, F. T., & Shamoon, T. (1997). Secure spread spectrum watermarking for multimedia. IEEE Transactions on Image Processing, 6(12), 1673-1687.
- 2. Kutter, M., & Petitcolas, F. A. (1999, April). Fair benchmark for image watermarking systems. In Security and Watermarking of Multimedia Contents (Vol. 3657, pp. 226-239). International Society for Optics and Photonics.
- 3. Cox, I. J., & Miller, M. L. (2002). The first 50 years of electronic watermarking. EURASIP Journal on Advances in Signal Processing, 2002(2), 1-7.
- 4. Cox, I. J., Miller, M. L., Bloom, J. A., & Honsinger, C. (2002). Digital Watermarking (Vol. 53). San Francisco: Morgan Kaufmann.
- 5. Mishra, S., Mahapatra, A., & Mishra, P. (2013). A survey on digital watermarking techniques. International Journal of Computer Science and Information Technologies, 4(3), 451-456.
- 6. Kadian, P., Arora, S. M., & Arora, N. (2021). Robust Digital Watermarking Techniques for Copyright Protection of Digital Data: A Survey. Wireless Personal Communications, 1-25.
- 7. Kadian, P., Arora, N., & Arora, S. M. (2019, March). Performance Evaluation of Robust Watermarking Using DWT-SVD and RDWT-SVD. In 2019 6th International Conference on Signal Processing and Integrated Networks (SPIN) (pp. 987-991). IEEE.
- 8. Kadian, P., Arora, N., & Arora, S. M. (2019). A Highly Secure and Robust Copyright Protection Method for Grayscale Images using DWT-SVD. In International Journal of Recent Technology and Engineering, 8(3), 7284-7288.
- 9. Kadian, P., Arora, N., & Arora, S. M. (2019). Role of scaling factor in Digital watermarking. In International Journal of Innovative Technology and Exploring Engineering, 8 (11), 1658-1669.
- 10. Poonam, Arora, S. M. (2018). A DWT-SVD based robust digital watermarking for digital images. In Procedia Computer Science, 132, 1441-1448.
- 11. Kadian, P., Arora, V., & Arora, S. M. (2020, July). Robust Watermarking Schemes for Copyright Protection of Digital Data: A Survey. In 2nd International Conference on Emerging Technologies in Data Mining and Information Security (IEMIS 2020). Springer.
- 12. Roy, S., & Pal, A. K. (2018). An SVD based location specific robust color image watermarking scheme using RDWT and Arnold scrambling. Wireless Personal Communications, 98(2), 2223-2250.
- 13. alias Sathya, S. P., & Ramakrishnan, S. (2018). Fibonacci based key frame selection and scrambling for video watermarking in DWT–SVD domain. Wireless Personal Communications, 102(2), 2011-2031.
- 14. Jiansheng, M., Sukang, L., & Xiaomei, T. (2009). A digital watermarking algorithm based on DCT and DWT. In Proceedings. The 2009 International Symposium on Web Information Systems and Applications (WISA 2009) (p. 104). Academy publisher.
- 15. Mishra, A., Jain, A., Narwaria, M., & Agarwal, C. (2011). An experimental study into objective quality assessment of watermarked images. International Journal of Image Processing, 5(2), 199-219.
- 16. Hsu, C. T., & Wu, J. L. (1999). Hidden digital watermarks in images. IEEE Transactions on Image Processing, 8(1), 58-68.
- 17. Singh, D., Choudhary, N., & Agrawal, M. (2012). Spatial and Frequency Domain for Grey level Digital Images. Special Issue of International Journal of Computer Applications (0975–8887) on Communication Security (4), 16-20.
- 18. Chu, W. C. (2003). DCT-based image watermarking using subsampling. IEEE Transactions on Multimedia, 5(1), 34-38.
- 19. Yavuz, E., & Telatar, Z. (2006, September). SVD adapted DCT domain DC subband image watermarking against watermark ambiguity. In International Workshop on Multimedia Content Representation, Classification and Security (pp. 66-73). Springer, Berlin, Heidelberg.
- 20. Eyadat, M., & Vasikarla, S. (2005). Performance evaluation of an incorporated DCT block-based watermarking algorithm with human visual system model. Pattern Recognition Letters, 26(10), 1405-1411.
- 21. Rioul, O., & Duhamel, P. (1992). Fast algorithms for discrete and continuous wavelet transforms. IEEE Transactions on Information Theory, 38(2), 569-586.
- 22. Wang, X. Y., Yang, H. Y., & Fu, Z. K. (2010). A new wavelet-based image denoising using undecimated discrete wavelet transform and least squares support vector machine. Expert Systems with Applications, 37(10), 7040-7049.
- 23. Daubechies, I., & Sweldens, W. (1998). Factoring wavelet transforms into lifting steps. Journal of Fourier Analysis and Applications, 4(3), 247-269.
- 24. Verma, V. S., & Jha, R. K. (2015). Improved watermarking technique based on significant difference of lifting wavelet coefficients. Signal, Image and Video Processing, 9(6), 1443-1450.
- 25. Hsu, C. T., & Wu, J. L. (1998). Multiresolution watermarking for digital images. IEEE Transactions on Circuits and Systems II: Analog and Digital Signal Processing, 45(8), 1097-1101.
- 26. Lie, W. N., Lin, G. S., Wu, C. L., & Wang, T. C. (2000, May). Robust image watermarking on the DCT domain. In 2000 IEEE International Symposium on Circuits and Systems (ISCAS) (Vol. 1, pp. 228-231). IEEE.
- 27. Hernandez, J. R., Amado, M., & Perez-Gonzalez, F. (2000). DCT-domain watermarking techniques for still images: Detector performance analysis and a new structure. IEEE Transactions on Image Processing, 9(1), 55-68.
- 28. Barni, M., Bartolini, F., & Piva, A. (2001). Improved wavelet-based watermarking through pixel-wise masking. IEEE Transactions on Image Processing, 10(5), 783-791.
- 29. Liyun, S., Hong, M. A., & Shifu, T. (2006). Adaptive image digital watermarking with DCT and FCM. Wuhan University Journal of Natural Sciences, 11(6), 1657-1660.
- 30. Verma, V. S., & Jha, R. K. (2015). Improved watermarking technique based on significant difference of lifting wavelet coefficients. Signal, Image and Video Processing, 9(6), 1443-1450.
- 31. Li, E., Liang, H., & Niu, X. (2006, June). Blind image watermarking scheme based on wavelet tree quantization robust to geometric attacks. In 2006 6th World Congress on Intelligent Control and Automation (Vol. 2, pp. 10256-10260). IEEE.
- 32. Lin, W. H., Horng, S. J., Kao, T. W., Fan, P., Lee, C. L., & Pan, Y. (2008). An efficient watermarking method based on significant difference of wavelet coefficient quantization. IEEE Transactions on Multimedia, 10(5), 746-757.
- 33. Byun, K., Lee, S., & Kim, H. (2005, December). A watermarking method using quantization and statistical characteristics of wavelet transform. In Sixth International Conference on Parallel and Distributed Computing Applications and Technologies (PDCAT’05) (pp. 689-693). IEEE.
- 34. Phadikar, A., Maity, S. P., & Kundu, M. K. (2008, December). Quantization based data hiding scheme for efficient quality access control of images using DWT via lifting. In 2008 Sixth Indian Conference on Computer Vision, Graphics & Image Processing (pp. 265-272). IEEE.
- 35. Santhi, V., & Arulmozhivarman, P. (2013). Hadamard transform based adaptive visible/invisible watermarking scheme for digital images. Journal of Information Security and Applications, 18(4), 167-179.
- 36. Singh, A. K., Dave, M., & Mohan, A. (2014). Hybrid technique for robust and imperceptible dual watermarking using error correcting codes for application in telemedicine. International Journal of Electronic Security and Digital Forensics, 6(4), 285-305.
- 37. Ahmad, A., Sinha, G. R., & Kashyap, N. (2014). 3-Level DWT Image Watermarking Against Frequency and Geometrical Attacks. International Journal of Computer Network & Information Security, 6(12).
- 38. Rahman, M. A., & Rabbi, M. F. (2015). DWT-SVD based new watermarking idea in RGB color space. International Journal of Signal Processing, Image Processing and Pattern Recognition, 8(6), 193-198.
- 39. Vaidya, S. P., & Mouli, P. C. (2015). Adaptive digital watermarking for copyright protection of digital images in wavelet domain. Procedia Computer Science, 58, 233-240.
- 40. Wu, H. T., & Huang, J. (2012). Reversible image watermarking on prediction errors by efficient histogram modification. Signal Processing, 92(12), 3000-3009.
- 41. Peng, F., Li, X., & Yang, B. (2012). Adaptive reversible data hiding scheme based on integer transform. Signal Processing, 92(1), 54-62.
- 42. Jamal, S. S., Khan, M. U., & Shah, T. (2016). A watermarking technique with chaotic fractional S-box transformation. Wireless Personal Communications, 90(4), 2033-2049.
- 43. Anees, A. (2015). An image encryption scheme based on Lorenz system for low profile applications. 3D Research, 6(3), 1-10.
- 44. Pan-Pan, N., Xiang-Yang, W., Yu-Nan, L., & Hong-Ying, Y. (2017). A robust color image watermarking using local invariant significant bitplane histogram. Multimedia Tools and Applications, 76(3), 3403-3433.
- 45. Wang, X. Y., Niu, P. P., Yang, H. Y., & Chen, L. L. (2012). Affine invariant image watermarking using intensity probability density-based Harris Laplace detector. Journal of Visual Communication and Image Representation, 23(6), 892-907.
- 46. Gao, X., Deng, C., Li, X., & Tao, D. (2010). Geometric distortion insensitive image watermarking in affine covariant regions. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 40(3), 278-286.
- 47. Seo, J. S., & Yoo, C. D. (2006). Image watermarking based on invariant regions of scale-space representation. IEEE Transactions on Signal Processing, 54(4), 1537-1549.
- 48. Chen, C. H., Tang, Y. L., Wang, C. P., & Hsieh, W. S. (2014). A robust watermarking algorithm based on salient image features. Optik, 125(3), 1134-1140.
- 49. Lei, B., Zhao, X., Lei, H., Ni, D., Chen, S., Zhou, F., & Wang, T. (2019). Multipurpose watermarking scheme via intelligent method and chaotic map. Multimedia Tools and Applications, 78(19), 27085-27107.
- 50. Cao, X., Fu, Z., & Sun, X. (2016). A privacy-preserving outsourcing data storage scheme with fragile digital watermarking-based data auditing. Journal of Electrical and Computer Engineering, 2016.
- 51. Singh, A. K. (2017). Improved hybrid algorithm for robust and imperceptible multiple watermarking using digital images. Multimedia Tools and Applications, 76(6), 8881-8900.
- 52. Rosiyadi, D., Horng, S. J., Fan, P., Wang, X., Khan, M. K., & Pan, Y. (2011). Copyright protection for e-government document images. IEEE MultiMedia, 19(3), 62-73.
- 53. Singh, S., Rathore, V. S., Singh, R., & Singh, M. K. (2017). Hybrid semi-blind image watermarking in redundant wavelet domain. Multimedia Tools and Applications, 76(18), 19113-19137.
- 54. Amini, M., Ahmad, M. O., & Swamy, M. N. S. (2017). Digital watermark extraction in wavelet domain using hidden Markov model. Multimedia Tools and Applications, 76(3), 3731-3749.
- 55. Kalantari, N. K., & Ahadi, S. M. (2010). A logarithmic quantization index modulation for perceptually better data hiding. IEEE Transactions on Image Processing, 19(6), 1504-1517.
- 56. Nezhadarya, E., Wang, Z. J., & Ward, R. K. (2011). Robust image watermarking based on multiscale gradient direction quantization. IEEE Transactions on Information Forensics and Security, 6(4), 1200-1213.
- 57. Makbol, N. M., Khoo, B. E., & Rassem, T. H. (2018). Security analyses of false positive problem for the SVD-based hybrid digital image watermarking techniques in the wavelet transform domain. Multimedia Tools and Applications, 77(20), 26845-26879.
- 58. Zhou, N. R., Hou, W. M. X., Wen, R. H., & Zou, W. P. (2018). Imperceptible digital watermarking scheme in multiple transform domains. Multimedia Tools and Applications, 77(23), 30251-30267.
- 59. Ambadekar, S. P., Jain, J., & Khanapuri, J. (2019). Digital image watermarking through encryption and DWT for copyright protection. In Recent Trends in Signal and Image Processing (pp. 187-195). Springer, Singapore.
- 60. Yu, P. T., Tsai, H. H., & Lin, J. S. (2001). Digital watermarking based on neural networks for color images. Signal Processing, 81(3), 663-671.
- 61. Zhenfei, W., Guangqun, Z., & Nengchao, W. (2006). Digital watermarking algorithm based on wavelet transform and neural network. Wuhan University Journal of Natural Sciences, 11(6), 1667-1670.
- 62. Xu, X. Q., Wen, X. B., Li, Y. Q., & Quan, J. J. (2007, August). A new watermarking approach based on neural network in wavelet domain. In International Conference on Intelligent Computing (pp. 1-6). Springer, Berlin, Heidelberg.
- 63. Huang, S., Zhang, W., Feng, W., & Yang, H. (2008, June). Blind watermarking scheme based on neural network. In 2008 7th World Congress on Intelligent Control and Automation (pp. 5985-5989). IEEE.
- 64. Ramamurthy, N., & Varadarajan, S. (2012). The robust digital image watermarking scheme with back propagation neural network in DWT domain. Procedia Engineering, 38, 3769-3778.
- 65. Mun, S. M., Nam, S. H., Jang, H. U., Kim, D., & Lee, H. K. (2017). A robust blind watermarking using convolutional neural network. arXiv preprint arXiv:1704.03248.
- 66. Liu, J. X., Wen, X. B., Yuan, L. M., & Xu, H. X. (2017). A robust approach of watermarking in contourlet domain based on probabilistic neural network. Multimedia Tools and Applications, 76(22), 24009-24026.
- 67. Mohammed, G. N., Yasin, A., & Zeki, A. M. (2014, March). Robust image watermarking based on dual intermediate significant bit (DISB). In 2014 6th International Conference on Computer Science and Information Technology (CSIT) (pp. 18-22). IEEE.
- 68. Cui, L., & Li, W. (2010). Adaptive multiwavelet-based watermarking through JPW masking. IEEE Transactions on Image Processing, 20(4), 1047-1060.
- 69. http://hdl.handle.net/10603/82341.
- 70. K. Ramanjaneyulu, K. Rajarajeswari, “Wavelet-based oblivious image watermarking scheme using genetic algorithm”, IET Image Processing, Vol.6, Iss.4, pp. 364373, 2012.
- 71. Lai, C. C., Ko, C. H., & Yeh, C. H. (2012, July). An adaptive SVD-based watermarking scheme based on genetic algorithm. In 2012 International Conference on Machine Learning and Cybernetics (Vol. 4, pp. 1546-1551). IEEE.
Note
- *Correspponding author: [email protected]
