1
M2M in 5G Cellular Networks: Challenges, Proposed Solutions, and Future Directions
Kiran Ahuja1* and Indu Bala2
1Department of Electronics and Communication Engineering, DAV Institute of Engineering and Technology, Jalandhar, India
2School of Electronics and Electrical Engineering Lovely Professional University, Phagwara, Punjab, India
Abstract
Fifth-generation wireless networks (5G) are defined to meet the requirements of high data rates for thousands of users, synchronized connections for vast wireless sensor networks, improved coverage area, efficient signal processing, low latency and enhanced network spectrum as compared to the fourth-generation wireless networks (4G). These networks were initially envisioned for efficient and fast mobile networks along with converged fiber-wireless networks. However, with the explosion of smart devices and emerging multimedia applications the need to roll out 5G networks to meet the demands both at the consumer and business end became necessary. Therefore, to create a network with faster speed, the 5G networks have initiated a new basis for communication, which consists of the Internet of Things (IoT) and Machine-to-Machine communication (M2M). The IoT and M2M have been able to overcome the major limitations of 5G to initiate multiple-hop networks, making available high data rates to peers between several base stations and thereby reducing costs and initiating reliable security standards. Such a major deviation from the conventional design to involve large networks to support massive access by machine-type devices (MTDs) sets special technical challenges for M2M. This chapter offers an outline of the main issues raised by the M2M vision along with a survey of the common approaches proposed in the literature to enable the coexistence of M2M devices and the challenges which need to be investigated.
Keywords: Machine-to-Machine, Internet of Things (IoTs), 5G
1.1 Introduction
Every five years or so, enormous changes occur in cellular networks with the already existing generation networks in order to fix the faults of its predecessor networks. The 4G network was needed to make consuming data less of an unpleasant experience. However, it had its flaws, which were fixed by the emergence of 5G, which created a big change in the mobile networks. With the ever-growing count of wireless users, telecom technologies continued to develop speedily, supporting the growth of service capacity and coverage to fulfill user demand for higher data. But the concerning issue with current network standards is a serious lack of bandwidth which limits support of higher data networks. Due to this issue, radio spectrums on which the 4G networks operate are overcrowded and thereby are predicted to increase mobile traffic between 2010 and 2020 [1]. This being one of the major challenges, the telecom businesses are depending on 5G as an existence investor considering growing marketplace overthrow via internet groups. Attempts are being made via the telecom companies to outline 5G technological know-how that gives record transmission velocity of 10 gigabytes over the air [2], latency in the order of 1ms [3] and IoT units which run on a battery lasting for up to 10 years [4, 10].
In contrast to the 5G network, the contemporary vision of communication systems in the new business areas like car–satellite communications, home automation, health security remote controlling, smart cities, Mobile POS, etc., require complete automated communication without human intervention. Such a novel form of communication is referred to as M2M communications. M2M visualizes a scenario where equipment on both sides have tens or hundreds of antennas or even more that renders better data rates for users with efficient energy and spectrum. It serves as the key element in the emerging of Internet of Things and Smart City models [5] and [6], which are planned to provide solutions to present and upcoming socioeconomic necessities for tracking and monitoring services, as well as for novel applications and advanced business setups [7].
The basic idea of M2M is to enable direct communication between users and the devices without the occupancy of the core network elements which requires offloading of the networks thereby exploiting the physical proximities of the terminals. Even with the call for such solutions, the potential of M2M can be set free only if the connectivity of the Machine-type Devices (MTDs) is probable everywhere without employing additional devices and without (or with minimal) configuration. In this point of fact, the ideal situation should be such where the MTDs are ready to be connected with the rest of the world by placing it in the favorable position. Figure 1.1 describes the ways of connectivity in the M2M communication with three cases.
With specific instances of M2M connectivity new applications with international offerings are connecting a number of kinds of embedded Wi-Fi machines/devices to create an unexpectedly developing IoT which guarantees to expand boom and income possibilities for modern-day carriers in the facet of waning margins in hooked up strains of business. Including the IoT applications, the M2M links the networks in many ways, providing an optimal form of connectivity with the Machine-Type Communications (MTCs), enabling: faraway industrial manage structures (ICS); security metering monitoring of transportation; third-party video streaming and gaming content; voice signaling; e-healthcare emergency monitoring and metering; domestic and industrial automation and a lot more. Figure 1.2 indicates a range of functions of the M2M conversation at a variety of grounds of growing a big ad hoc network permitting close by units to connect.
Unfortunately, due to the massive accesses and high user demands the technologies that are supposed to carry out MTC are somewhat not capable to meet the demands for ubiquitous coverage of M2M communications. This ubiquitous access offered by satellite connections has prohibitive costs, posing major challenges when used in indoor environments. This therefore calls for the radio technologies which are capable of making available extensive coverage area with low power consumption and reduced cost. At the same time operation of such a new infrastructure network at a diverse scale makes it an economically challenging task, thus making it necessary to add the MTC devices in the services of the existing communication networks.

Figure 1.1 Cases for M2M connectivity. (a) Basic M2M connectivity, (b) M2M in which a single application shares information with of group of similar devices, and (c) M2M communication using the gateway device [8].

Figure 1.2 Applications of M2M communications [9].
Consumer attitude to usage of internet is altering due to the alteration in the tendencies. Such user demands can only be fulfilled by the widespread mobile network supporting the M2M communication offering higher efficiency, security and robustness. Current standards being designed to provide access to only a small count of devices are likely unable to cope with the expected growth in the traffic of the M2M communication networks, thereby becoming a major challenge for the 5G networks [8]. Due to this reason the major focus is to enforce the M2M services as shown in Figure 1.2, which involve myriad devices generating efficient periodic transmissions of short data, predicted to play a major role in the future networks.
This chapter surveys the major challenges presented to the wireless cellular network standards by the massive M2M services. Section 1.2 is the literature survey giving the current standards for enabling the M2M services. Section 1.3 addresses in greater detail the challenge of the same with their proposed solutions to fill the gaps in the future to fully support M2M. Section 1.4 concludes this chapter with the final reconsiderations.
1.2 Literature Survey
Researchers have predicted that more than a billion devices will connect with the M2M communications through mobile networks by 2020. Statistics show that the world cellular site visitors will experience increase around 70% with 26% smartphones accountable for 88% of whole cell facts visitors [9]. The current 4G mobile structures fail to aid this huge scale of information utilization when you consider that they had been in the beginning deliberate to keep up to 600 RCC related customers per cell [10, 11]. Relatively M2M communications and IoTs subsidize thousands of linked devices in a one cell. This makes the aforementioned essential to support the standards to enable the M2M communications.
The authors in [12] differentiated the M2M communications from mobile Human-based (H2H) because the H2H traffic (browsing, file transferring, video streaming) cannot be directly applied to the M2M [12, 13], mentioning the M2M traffic direction as uplink whereas the H2H traffic direction as downlink. The M2M applications duty-cycled with short connection would promise fast access to the M2M network, resolving major traffic problems in the M2M communications due to H2H traffic.
Due to increased H2H and M2M traffic, the Wi-Fi communications can’t chorus from dealing with the new challenges of radio spectrum congestion. In [14], the authors surveyed to provide complete investigation of the M2M fading channels in coordinated and cooperative networks under the propagation conditions of the line-of-sight (LOS) and non-line-of-sight (NLOS). The survey evaluated the performance of dual-hope-relay-systems with equal gain combining which improved the overall system performance of LOS components in the transmitting links [14]. Apart from the radio spectrum congestion, current research studies defined the problems faced by means of M2M gadgets such as channel instabilities [13–15] and noise acquaint with coordination uncertainties in the media access. Researchers explained that this unreliable processing and transmissions in the communication medium leads to data loss causing a major M2M failure, thereby stating reliability as an unresolved challenge for the M2M standards [16].
Also, with the rapid rise in the number of wireless users there is a notable increase in the concurrent accesses, making simultaneous access increase, causing extra packet collisions due to interference resulting in data loss. Thus, maximizing the uplink channel and optimizing the radio aid allocation elevated the overall performance with environment friendly Quality of Service (QoS). Along with dependable QoS, M2M units are designed in such a way that they are normally less expensive and small in dimension with energy, bandwidth and different storage constraints to communication. The networks on which these M2M units work provide extensive insurance areas with excessive statistics charges and diminished latency, however, in spite of the certain advantages. There are many more challenges to the M2M networks which have been specified in [15, 17]. The study in [18] testified that the M2M traffic in the presence of 4G traffic is not to be considered negligible, hence degrading the performance of the 4G networks in terms of QoS. Thus, the operation of M2M has to be seamless, i.e., besides human intervention stopping occasional physical attacks [15, 16, 19, 20]. This attainable success of the M2M functions overcoming all these challenges can promise to extend the miscellany and wide variety of the units to be related and the visitors in the upcoming years. So, the present research is focusing on enhancing the overall performance and the performance of the system, both in phases of energy consumption, affectivity or delay.
Moreover, further improvements supporting the M2M communications have been stated by the authors in [21] analyzing sensor-to-gateway communications in terms of delay and energy efficiency in wireless M2M introducing the contention-based MAC protocols. The study defined the use of gateways in the wireless M2M network driving a large number of devices that regularly wake their radio interfaces to the gateway carrying out high data rates with low latency. This use of gateways is supposed to reduce the number of devices to be accessed, thereby making the transmission less complex and reducing interference with increased efficiency.
Other authors in [22] have explained the idea of Clone-to-Clone (C2C) to solve the issues obstructing the development of the next generation applications by reducing the traffic, recovering overall network performances and mitigating the power consumption of the devices. The concept of Energy Efficient and Reliable (EER) and Green Allocation with Zone Algorithm (GAZA) to achieve overall power and energy efficiency, for reliable M2M communication has also been stated in [23].
With the sudden advancements in user-supported communication including E-health, security and surveillance, industrial and energy, one of the crucial areas in need of the M2M devices’ communication is the intelligent transportation systems (ITS). The key component of ITS, the Vehicular Ad Hoc Networks (VANETS), are created and connected by the mobile and hoc networks (MANETS) for the impulsive creation of the wireless networks for data sharing. Emphasis on the same has been made to define the M2M vehicular networking with the standardization of communication interfaces as a major challenge with high mobility and variability of components [24]. Furthermore, the data aggregation strategies which can be delivered for channel get admission to enhancements in M2M communications for mobile networks, mentioning the use of prolong to enhance uplink transmission affectivity, has been described in [25]. In addition to this, the world extend would reduce with the acceleration in quantity of the M2M devices. An extra scheme being cited to decrease extend or to acquire greater power and energy consumption affectivity is the transmission scheduling method [26]. The overview of the already existing scheduled airliners as relays between ground devices and satellites offering a new M2M infrastructure has been discussed in [27].
M2M communications cannot be reliable if the mobility, delay patterns and most specifically energy efficiency is not met [16]. This is usually at the time of using radio technologies for communications due to lower available bandwidth, higher link failure, and higher energy consumption. Finally, the future works will likely be to combine a range of strategies (transmission scheduling schemes, data aggregation, gateways) to minimize the quantity of indispensable records to be transmitted. Managing security and privacy in such a vivid network (M2M) obviously requires good attention, making M2M communications more efficient.
Summarizing the current M2M standards that have supported to enable the M2M communications, the next section describes the challenges which need to be overcome along with their proposed solutions.
1.3 Survey Challenges and Proposed Solutions of M2M
With the explosion of M2M and IoT applications, large tech companies are jumping on board with devices ranging from wearable to beacon modules. There are many considerations which need to be taken into account for the deployment of M2M and IoT technologies. So it becomes mandatory to study the challenges and the interference from each aspect, from cost and power to long-term product life cycle of the M2M devices. The challenges to enable the M2M communications include small-sized data transmissions supported by larger value of devices after regular and irregular intervals; high reliability, low latency and low energy consuming mobile profiles assuring that regular H2H traffic is not disturbed by the M2M traffic.
1.3.1 PARCH Overload Problem
The Random Access Channel (RACH) process is one of the key challenges [28] for M2M. This is because of the traffic load caused by a rapid rush of myriad M2M devices trying to access the base station at the same time. According to the latest M2M traffic surveys, approximately 3.2 billion cellular-based M2M devices are expected to join the network in 2024 [29] making Quality of Service (QoS) provisioning an important challenge [30] for the M2M communications.
The rush to access Physical Random Access Channel (PRACH) resources are likely to debase the M2M services. The enormous access calls by M2M devices burden the PRACH, resulting in access delay and failure rate. This traffic load can be reduced by multiplying the number of access devices scheduled per frame, but this further introduces a new challenge of reduced capacity for the devices. Thereafter, it becomes important to deduce schemes to overcome this overload problem. The author in [10] has forwarded various methods which include the isolation of the M2M and Human-2-Human (H2H) services by simply splitting the two or by making the two services share the same resource, giving them a combined name of Hybrid schemes. Apart from this, there are various other approaches that have been put forward to offset PRACH overload [31].
- Pull-based scheme: This is a central scheme which permits the MTDs to access the PRACH paged by the eNode (eNB) [31] keeping an account of the network load conditions to prevent overloading problems. With this approach the network channels can be managed having regular traffic patterns using a single server. However, being managed by a single M2M server the scheme cannot deal with unexpected flow of MTD access requests.
- Resource separation: The Resource separation scheme provides the simplest and most instant way to protect H2H devices from the risk of collisions due to diverse MTC requests by assigning orthogonal PRACH resources to H2H and M2M devices. The separation of resources can be done either by splitting the H2H and MTC devices into groups, or by simply allocating them different RA time/frequency slots [31]. To get a better effect, coupling with mechanisms which dynamically shift the resources among the two classes in accordance to the required access request rates is mandatory.
- Back-off tuning: Another scheme to clear the congestion caused by the traffic of requests in a smooth way is by assigning the back-off intervals to the MTDs which fail the transmission in RACH procedures [31]. Though the collisions between H2H and M2M devices can be improved efficiently, due to instability issues initialized by the ALOHA-like mechanisms this scheme is really not effective when dealing with stationary MTDs massive access.
- Access Class Barring (ACB): The above stated back-off tuning mechanism is a generalization of the Access Class Barring (ACB) method. The ABC scheme has each class allotted with an access probability with a barrier time [31] making it possible to define several access classes with dissimilar access probabilities. The access of the device is debarred, making the device wait for a random back-off time when the Message transmitted in the RA slot is larger than the access probability factor. Another scheme of Extended Access Barring (EAB) was projected that can withstand longer access delays [31], hence barring the device without the need of any new access class. This technique makes it possible for the MTDs to mitigate the massive access issue by simply labeling them as an EAB device. Thus ACB can prove to be quite useful in avoiding the overload problem but only with respect to longer access delays for the MTDs, whereas it fails in the case of contention-based access events like fire alarms due to power failures or any other unexpected event which require short time intervals.
- Self-Optimizing Overload Control (SOOC): In [28] the authors presented a complex scheme, i.e., SOOC, to offset PRACH overload by simply merging the pull-based, back-off, ACB, including the resource separation scheme. The primary feature of this scheme is the implementation of the control loop to collect information for overload examining at every RA cycle. Basically, the device enters the overload control mode and the classical p-persistent mechanism is applied for the regulation of RA cycles when it is not able to receive an access grant at the first attempt. Also, to differentiate between time-tolerant MTDs and time-sensitive MTDs, two access classes, namely low access priority and high access priority have been added in this scheme for the M2M devices. Though handling high traffic loads can be attained using this scheme the author in [28] has not provided enough evidence relating to the performance of this scheme.
- Bulk MTC signaling scheme: Another scheme in [32] provided a further solution to overload problems by enabling bulk MTC signal handling stating lack of mechanisms while handling overheads generated from collective MTDs. This overhead can be reduced at the Base Station by making use of bulk processing (collecting signal data coming from MTDs before accelerating them to the core network). As an illustration for this scheme, consider a group of MTDs which are triggered to send Tracking Area Update (TAU) where the Base Station has to wait for a default timeout interval or awaiting the time it has gathered enough information to forward a message towards the Mobility Management Entity (MME). Since the MTDs are linked to the same MME, the TAU messages are going to be different on the MME Temporary Mobile Subscriber Identity (M-TMSI). A situation where an average of 20 TAU msg/sec with a period of 10 s, 200 TAU messages can be combined in a single 1211 bytes/msg in contrast to which an individual message would acquire up to 4500 bytes of space. Hence the approach in this scheme can reduce the intensity of traffic produced by large channel access.
1.3.2 Inefficient Radio Resource Utilization and Allocation
The existing cellular standards are not capable of handling large number of devices with small small-sized payloads, leading to network congestion. This makes it important for the existing mobile networks to be amended for supporting diverse M2M devices ensuring efficient allocation and utilization of the radio resources. Hence, novel methods are introduced to manage the overload issues such as back-off adjustment, M2M prioritization, etc. In radio access network and existing networks need to be improved to guide various M2M gadgets in the future [19]. The reality is that cell radio sources are narrowly accessible and an environment-friendly operation of such radio resources for M2M desires would be guaranteed. This environment-friendly utilization of confined radio assets has to be executed or the overall performance of M2M will probably degrade. Therefore, this theme needs vital attention to keep away from the congestion troubles in the M2M offerings effectively. Figure 1.3 suggests the instance of the useful resource allocation in present-day cell guidelines that are neither meant successfully to manipulate small statistics contents nor can take care of myriad gadgets concurrently [23].
Figure 1.3 Radio resource allocation in existing mobile standards [23].
The main issue in the case of dissimilar traffic is the management of interference, which needs a complex resource partitioning mechanism. A coordinated radio resource allocation is being enabled by partitioning among different devices which reduces the congestion problems to some extent. A number of scheduling algorithms were proposed by authors to estimate the performance in terms of throughput and equality between the mobile users [27]. Figure 1.4 represents the resource scheduling mechanism which supports M2M communication.
The aforementioned proposed approaches consisting of the self-organizing mechanisms with minimal phone transmitting strength to make use of frequency reuse patterns offer a solution for interference as properly as most useful frequency reuse [28]. To guide the M2M traffic [29] different scheduling schemes have been additionally advised which think about the community environments as properly as delay limitations, maximizing the count of sustained units per cell. Henceforth, performances of the aforementioned mechanisms are fairly favorable at the stake of immoderate signaling overhead [30] which will be the one of the most tedious issues in the future too.

Figure 1.4 Resource scheduling supports M2M communication [28].
1.3.3 M2M Random Access Challenges
Non-wired access might also be dependent totally on restricted wireless networks (ZigBee, Wi-Fi, etc.) or inclusive range cell networks (GSM, GPRS, UMTS, and LTE). Even though wired access strategies are extra regular in originating much less prolonging and supplying greater throughput, these methods honestly are no longer appropriate for all M2M purposes which are brought about by using elements such as mobility, scarcity of scalability and price competence. Hence these are the instances where non-wired networks play a necessary part. The different non-wired admittance is employed for constrained vary hyperlinks which are now not expensive, accessible, and consume much less energy. However, these hyperlinks are inappropriate for M2M communications because of low statistics rates, excessive interference, weaker security, and much lower mobility.
- Quality of Service: Interference is probable to take region so the M2M and H2H site visitors contest for PRACH resources. Though, the overall performance of H2H visitors ought to now not be affected; therefore M2M/MTC visitors have to meet QoS. Also, most promising decision of transmission mode is need of appropriate QoS which must have small delays mainly in emergency and greater data charges, e.g., surveillance applications.
- Cognitive M2M communications: Primary challenge is constantly growing signaling overhead due to the fact of giant consumer connectivity with M2M units per cellphone inflicting bandwidth issues. This bandwidth trouble on the other hand should be resolved via common strategies, i.e., by growing the range of eNBs. Another associated difficult project is the interference in the middle of the MTC and non-MTC units which ought to be extended with the aid of centralized coordination; however, this will increase the common complexity. Thus, the exceptional ideal approach would be imposing allotted supply administration which may additionally become what may be useful for lowering the interference between positive gadgets [33]. Furthermore, a higher thinking for a significant range of gadgets to join per mobile, i.e., the random get entry to mechanisms building the MTC and non-MTC expedients to section the similar restricted radio spectrum has been provided.
- Collective (Group-based) M2M communication: The main challenge for this mechanism is to allocate slots where group-based conversation performs a vital function [34]. Its major goal for this mechanism is to reduce the signal blockading on air interface. Additionally, in order to limit the community blockading risks, the energy intake of gadgets can additionally be deduced. The truth is that machines require send/receive statistics to/from a neighboring factor the place grouping of the MTC gadgets needs exclusive attention. The requirement of the logical/physical attribute primarily based on QoS and extra MTC traffic elements [35] for such a kind of conversation enabling the M2M.
1.3.4 Clustering Techniques
Various clustering techniques making allowance for priorities and delay restrictions to handle massive access have been introduced supporting the maximum number of devices to be connected in the M2M network. Figure 1.5 is an example of the clustering technique in the M2M networks.

Figure 1.5 Clustering mechanism [36].
- Clustering Mechanism in M2M Devices: In a clustering mechanism all devices in a network are associated with one or more groups on the basis of their geographical location with regard to the QoS requirements [34]. The clustering scheme is, however, beneficial in minimizing the energy consumption for MTDs [36] which reduces the risk of network collisions. Another scheme which has been proposed is the dynamic radio resource allocation in which an eNB allocates PRACH resources among the MTDs on the basis of PRACH traffic load in that particular network [37], hence enabling this clustering mechanism.
- Energy efficient clustering of MTDs: Another way to control the network cognition is by appointing nodes to the Base Station known as cluster-heads which can limit the number of requests at the Base Station. The risk of cognition due to massive access could also be reduced by selecting the coordinators which can again help in reduced power and energy consumption. More schemes for this massive access management and power efficiency are combined by the author in [36] where the author has forwarded the idea of N MTDs, which are employed in a single cell centered at the Base Station maximizing the energy efficiency of the MTDs.
- QoS-based clustering technique: Clustering is being used as an effective remedy for the massive assignment of large number of MTDs having small transmission and distinct QoS requirement to a radio resource [34, 38]. In this the devices are grouped depending upon their arrival rates, which helps in forming clusters of the devices having similar QoS requirements proving to provide efficient power and energy consumption.
1.3.5 QoS Provisioning for M2M Communications
QoS provisioning is the most important requirement of a telecommunication system. It is an arrangement of service-linked chores related to the facility supplier to provide a desirable service to the consumer [39]. It is a challenging situation for the operators/service providers on the grounds that M2M functions cover a huge range of tasks relying upon data/packet size, precedence of the tasks, delay, and mobility demands. Also, some of the examples which contain M2M traffic like emergency alerting, unintentional and/or integral e-healthcare information, are extend touchy and demand strict precedence, which makes it essential for the M2M site visitors no longer to create much delay. By the emergency alerting techniques, the site visitors generated by applying point of sale terminals claim low priority; as a result it should be referred to that smart metering, tracking and monitoring home equipment create constant site visitors outlines, thinking about low priority site visitors but with higher information charge necessities. Table 1.1 provides information relating the class types of QoS for M2M communications.
| Parameters | Type 0 | Type 1 | Type 2 | Type 3 | Type 4 |
|---|---|---|---|---|---|
| Purpose | Health Security Remote Control & Maintenance | IP Multimedia Subsystem & Wireless Point on Sale (POS) | Video Streaming, Video Signaling | Home Automation | Security Metering Tracking |
| Features | High Reliability & Access Priority | High Security & Privacy | Access Priority & Low Latency | Increased Security | Low Error Rate |
| Traffic Type | Random | Random | Random | Random | Regular |
| Real Time | Real Time | ||||
| Priority | High | Low | Low | Low | Low |
| Mobility | Low | Low | Low | No | Low |
1.3.6 Less Cost and Low Power Device Requirements
The technical issues are summarized in [43]; an ambiguity that operators want to tackle is how to charge the user for M2M services. A primary M2M machine claims low rate and low energy usage. Moreover, the gadgets that act as transmitters for different customers utilize their personal sources such as battery, data storage and bandwidth, which insist on essential pricing models to be considered to encourage users to take part in such communication. It is predictable that M2M equipments/devices will be used for a lengthier time period, which will indirectly end up a difficult chore for component agencies as well as for the facility suppliers. Additionally, because of longer inter-arrival instances users ought to deplete usually time in their slothful state. This idle state is essentially a short energy usage state in which gadgets commonly save battery while keeping them in sleeping modeor wake up at particular instances to take a look at machine statistics (SI) replace [44]. Therefore, the key idea is to mend the battery epoch to average the endeavor of the slothful mode which can be without problems sustained the use of the paging cycles which ought to now not be regular. This is due to the motive that the gadgets have to be in lively mode only if there is any information to transmit. Table 1.2 shows optimization of the low price and low power for environment-friendly M2M communications. Thereafter these devised mechanisms result in low power devices which themselves help in a way to reduce the cost of the services.
Table 1.2 Optimization of low-cost and low-power M2M devices [43, 45, 46].
| Parameters | Category -0 | Category-1 | Category- 4 | |
|---|---|---|---|---|
| Release | Release 12 | Release 8 | Release 8 | Release 13 |
| Downlink Peak Rate | 1 Mbps | 10 Mbps | 15 Mbps | ~200 Mbps |
| Uplink Peak Rate | 1 Mbps | 5 Mbps | 50 Mbps | ~200 Mbps |
| Bandwidth | 20 MHz | 20 MHz | 20 MHz | 1.4MHz |
| Mode | Half Duplex | Full Duplex | Full Duplex | Half Duplex |
| Complexity | 50% | 100% | 125% | 25% |
| Transmitting Power Rate | 23dBm | 23dBm | 23dBm | ~20dBm |
1.3.7 Security and Privacy
M2M security is majorly emphasised in consumer characteristics and their communications which consist of authority, integrity, authenticity and secrecy. Therefore, to enable client acceptance the privateness of M2M is vital [47]. Diverse sectors such as e-health, smart metering, industrial and energy, transportation logistics, etc., can also have special private necessities which have to be viewed at the initial stages of the designing.
Due to the fusion of diverse heterogeneous networks, M2M communications are required to address all the threats while communicating with different network-based communications criteria. Even then, it is never to be supposed that M2M haven’t prompted new threats. These are prone to be amplified the present ones within the M2M environment and these threats will also cause money losses and in addition to this cause a threat to human lives indirectly. M2M devices are mainly deployed in amicable locations and probably work for prolonged periods. Therefore, numerous physical attacks will pretense alongside the devices. The following are major categories of attacks in case of M2M, pictorially shown in Figure 1.6, and their probable solutions are shown in Figure 1.7.
It is the most required feature of any communication system that personal information must not be disclosed at any cost. Otherwise, it can create a huge loss either in terms of personal assets or corporate ones. In M2M, it is important to accomplish the obligation of secrecy due to the existence of smart things, which indirectly create a threat of mishandling of technology. The massive number of smart things creates a gigantic challenging concern to preserve the seclusion of private data. One of the criteria is to launch a third-party reliable security association, which will be responsible for endorsement distribution. Conversely, if there are a huge number of M2M devices with different applications, this scheme appears to be too pricy to be applied. Due to this constraint, a lightweight cryptography technique is preferred in M2M communications. Asymmetric and symmetric keys authentication can also be applicable in a variety of deployment situations of M2M communications.
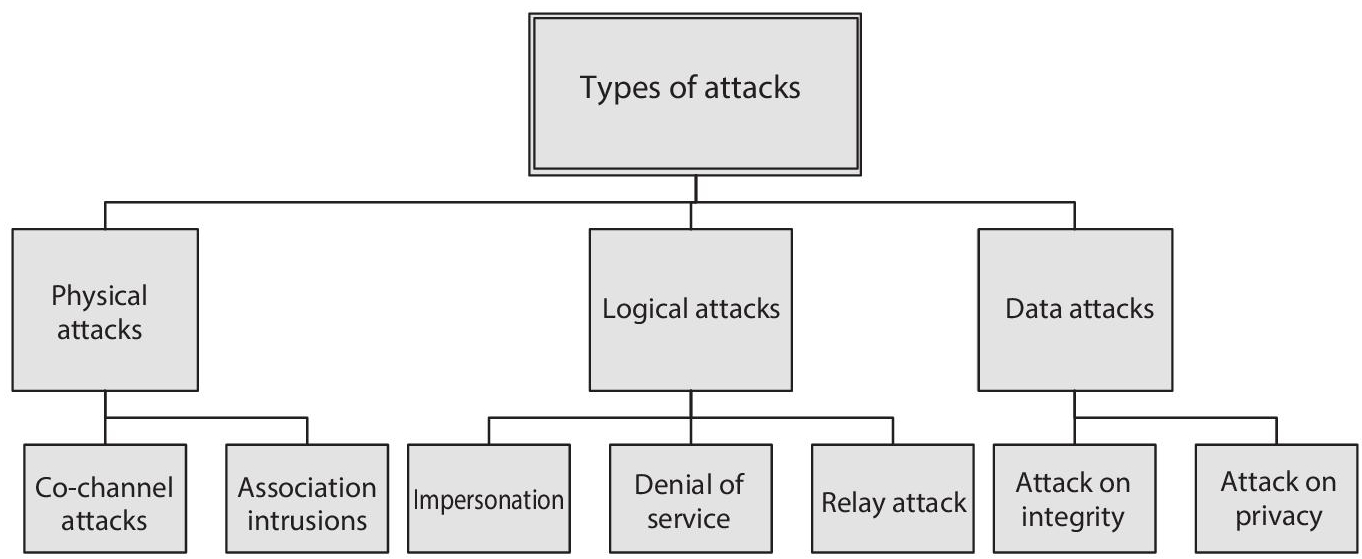
Figure 1.6 Represents the diverse types of attacks likely to occur while M2M communication.

Figure 1.7 Probable solutions for M2M security issues.
1.4 Conclusion
The current cellular systems have not been planned to support the M2M networks; however, these systems are capable of supplying the present-day demands and the user approaches for the M2M services. Furthermore, if the M2M market is able to fulfill the demands of the user and networks these technologies will hit the present networks with the biggest change. The evolution of the M2M applications in future is more likely to rely upon a mix of proprietary technologies, clearly intended for MTD connectivity. Considering that M2M devices and applications remain equipped for a long time with minimum intervention and maintenance, the M2M architectures is most likely to last for many years to come, and will be finally absorbed via 5G, that are concentrating greater to dominate non-cellular technologies which are in basic terms advocated for the future M2M services. Mobile M2M communications are being targeted due to their functionality in a number of purposes like healthcare, transport structures or telemetry and additionally due to the surfacing of IoT. A major challenge confronted by way of cell M2M networks is to help limitless units with smaller payloads inflicting inefficient use of PRBs (Physical Resource Blocks) and for this reason resulting in immoderate signaling overhead and an elevated chance of community jamming. Future work will center extra attention on enhancement of overall performance, each in terms of useful resource utilization effectively and delay. In addition, appropriate traffic and models with precise battery lifetime need to be worked upon for coming near applications. Methods for improving overall performance have to provide for all the probabilities, such as analytical modeling, device stage simulations, and hybrid techniques. Besides this, the most vital software is inspected for much less strength consumption including operations of battery-driven units in the scenarios; the place there is both no energy supply or restricted direct strength supply which can help in electricity management in M2M conversation networks.
Future scope: The spectrum of the cellular networks nonetheless continues to be a paucity resource; consequently there is an urge to graph out new thoughts for new site visitors types so as to successfully use the bandwidth. Finally, for efficient, optimized and reliable communication all the above-stated challenges need to be worked upon, including the challenges for complete the end users right from regulation of organizations, companies of network tools and consumer devices, network operatives, to the application sources.
References
- 1. Chin, Woon Hau, Zhong Fan, and Russell Haines. “Emerging technologies and research challenges for 5G wireless networks.” IEEE Wireless Communications 21, no. 2 (2014): 106-112.
- 2. “Journey to 5G: Singtel partners with Ericsson to ready 4G LTE network for Internet of Things”, www.Ericsson.com. Press Release, Feb. 21, 2016.
- 3. “5G Vision: 100 Billion connections, 1 ms Latency, and 10 Gbps Throughput” 5G Vision: 100 Billion connections, 1 ms Latency, and 10 Gbps Throughput”, www.huawei.com.
- 4. Intelligence, G. S. M. A. “Understanding 5G: Perspectives on future technological advancements in mobile.” White paper (2014): 1-26.
- 5. Zanella, Andrea, Nicola Bui, Angelo Castellani, Lorenzo Vangelista, and Michele Zorzi, “Internet of things for smart cities.” IEEE Internet of Things Journal 1, no. 1 (2014): 22-32.
- 6. Zhou Z., Chang Z., Liao H., “Energy-Efficient M2M Communications in for Industrial Automation,” In: Green Internet of Things (IoT): Energy Efficiency Perspective, Wireless Networks, Springer, Cham. (2021).
- 7. P. Bellavista, G. Cardone, A. Corradi, L. Foschini, “Convergence of MANET and WSN in IoT urban scenarios”, IEEE Sens. J., vol. 13, no. 10, pp. 3558-3567 (Oct. 2013).
- 8. Aschenbrenner, Doris, “Human Robot Interaction Concepts for Human Supervisory Control and Telemaintenance Applications in an Industry 4.0 Environment,” Thesis, 2017/06/20.
- 9. Prasad R., Rohokale V. (2020) Internet of Things (IoT) and Machine to Machine (M2M) Communication. In: Cyber Security: The Lifeline of Information and Communication Technology. Springer Series in Wireless Technology, Springer, Cham, Print ISBN 978-3-030-31702-7.
- 10. H. Holma, A. Toskala, J. Reunanen, “LTE small cell optimization: 3GPP evolution to Release 13”, John Wiley & Sons, Ltd. (2015).
- 11. Huawei Technologies Co, “eLTE2.2 DBS3900 LTE configuration principles” (2014).
- 12. Laya, A.; Alonso, L.; Alonso-Zarate, J., “Is the Random Access Channel of LTE and LTE Suitable for M2M Communications? A Survey of Alternatives”, IEEE Commun. Surv. Tutor., 16, 4–16, (2014).
- 13. Lien, S.Y.; Chen, K.C.; Lin, Y., “Toward ubiquitous massive accesses in 3GPP machine-to-machine communications”. IEEE Commun. Mag., 49, 66–74 (2011).
- 14. BatoolTalha, “Mobile-to-Mobile Cooperative Communication Systems: Channel Modelling and System Performance Analysis”, LAP Lambert Academic Publishing (2011-07-29).
- 15. Zhang, Y.; Yu, R.; Xie, S.; Yao, W.; Xiao, Y.; Guizani, M,”Home M2M networks: Architectures, standards, and QoS improvement”. IEEE Commun. Mag., 49, 44–52, (2011).
- 16. Lu, R.; Li, X.; Liang, X.; Shen, X.; Lin, X. GRS, “The green, reliability, and security of Emerging machine to machine communications”, IEEE Commun. Mag., 49, 28–35, (2011).
- 17. Hernández, Elaine Cubillas, Caridad Anías Calderón, and Tatiana Delgado Fernández. “M2M Architecture for environmental monitoring in real time.” ITECKNE 18, no. 1 (2021).
- 18. Marwat, S.; Potsch, T.; Zaki, Y.; Weerawardane, T.; Gorg, C. “Addressing the Challenges of E-Healthcare in Future Mobile Networks”. Lect. Notes Computer. Sci. (2013).
- 19. Wu, G.; Talwar, S.; Johnsson, K.; Himayat, N.; Johnson, K.,“M2M: From mobile to Embedded internet”. IEEE Commun. Mag., 49, 36–43 (2011).
- 20. Booysen, M.; Gilmore, J.; Zeadally, S.; Rooyen, G., “Machine-to-Machine (M2m) Communications in Vehicular Networks”. KSII Trans. Internet Inf. Syst., 6,529–546, (2012).
- 21. Vazquez Gallego, F.; Alonso-Zarate, J.; Alonso, L., “Energy and delay analysis of contention resolution mechanisms for machine-to-machine networks based on low-power WiFi”, Browse conference publications (2013).
- 22. E. Ortiz-Guerra, M. O. Rojas, S. Montejo-Sánchez, R. D. Souza, C. A. Azurdia-Meza and S. Céspedes, “On MAC Protocols Performance for M2M Communications,” IEEE Colombian Conference on Communications and Computing (COLCOM), Cali, Colombia, pp. 1-5, 2020.
- 23. Shyam Sundar Prasad, Chanakya Kumar, “A Methodology for an Efficient and Reliable M2M Communication”, International Journal of Soft Computing and Engineering (IJSCE) ISSN: 2231-2307, Volume 3, Issue 4 (September 2013).
- 24. M.J. Booysen1, J.S. Gilmore1, S. Zeadally2 and G.J.van Rooyen1, “Machine-to-Machine (M2M) Communications in Vehicular Networks” (2 Jan 2012).
- 25. Lo, A.; Law, Y.; Jacobsson, M., “A cellular-centric service architecture for machine-to-machine (M2M) communications”. IEEE Wirel. Commun. 20, 143-151 (2013).
- 26. Yunoki, S.; Takada, M.; Liu, C., “Experimental results of remote energy monitoring system via cellular network in China”, In Proceedings of the SICE Annual Conference (SICE), Akita, Japan. 20–23, pp. 948–954 (August 2012).
- 27. Plass, S.; Berioli, M.; Hermenier, R., “Concept for an M2M communications infrastructure via airliners”, in Proceedings of the 2012 Future Network Mobile Summit (FutureNetw), Berlin, Germany, pp. 1–8 (4–6, July 2012).
- 28. Lo, Anthony, Yee Wei Law, Martin Jacobsson, and Michal Kucharzak, “Enhanced LTE-advanced random-access mechanism for massive machine-to-machine (M2M) communications.” in 27th World Wireless Research Forum (WWRF) Meeting, vol. 2011. Düsseldorf, Germany, 2011.
- 29. “M2M device connection forcast”, www.machinetomachinemagazine.com.
- 30. “Mobile and wireless communications Enablers for Twenty-twenty (2020)” Information Society, Novel radio link concepts and state of the art analysis, www.metis2020.com.
- 31. 3GPP, “Study on RAN Improvements for Machine-type Communications”, Technical Report, 3GPP TR 37.868 V11.0.0, (2011).
- 32. T. Taleb, A. Kunz, “Machine type communications in 3GPP networks: potential, challenges, and solutions”, IEEE Commun Mag., vol. 50, 3, 178-184 (March 2012).
- 33. Y Zhang, R Yu, M Nekovee, Y Liu, S Xie, S Gjessing, “Cognitive machine-to-machine communications: visions and potentials for the smart grid”, IEEE Netw. 26(3), 6–13 (2012).
- 34. S Lien, K Chen, Y Lin, “Toward ubiquitous massive accesses in 3GPP machine-to-machine communications”, IEEE Commun. Mag. 49(4), 66–74 (2011).
- 35. H Safdar, N Fisal, R Ullah, W Maqbool, F Asraf, Z Khalid, AS Khan,:, “Resource allocation for uplink M2M communication: a game theory approach”, IEEE Symposium on Wireless Technology and Applications (ISWTA). IEEE, Kuching, Malaysia, pp. 48–52 (2013).
- 36. P. Andres-Maldonado, P. Ameigeiras, J. Prados-Garzon, J. J. Ramos-Munoz and J. M. Lopez-Soler, “Reduced M2M signaling communications in 3GPP LTE and future 5G cellular networks,” 2016 Wireless Days (WD), Toulouse, 2016, pp. 1-3.
- 37. M Hasan, E Hossain, “Random access for machine-to-Machine communication in LTE-Advanced networks: issues and approaches”, IEEE Commun. Mag. 51(6), 86–93 (2013).
- 38. S.-Y. Lien, K.-C. Chen. “Massive Access Management for QoS Guarantees in 3GPP Machine-to-Machine Communications”, IEEE Comm. Letters, Issue No. 09, vol. 23, pp 1752-1761, Sept. 2012.
- 39. International Telecommunication Union Telecommunications (ITU-T), Definitions of terms related to quality of service (2008), www.itu.int.
- 40. R Liu, W Wu, H Zhu, D Yang, “M2M-oriented QoS categorization in cellular network,” in Proceedings of 7th IEEE International Conference on Networking And Mobile Computing (WiCOM). IET, Beijing, China, pp. 1–5, (2011).
- 41. “Machine to Machine (M2M) Evaluation” Methodology Document (EMD) Broadband Wireless Access Working Group (2010).
- 42. C Anton-Haro, M Dohler, “Machine-to-Machine (M2M) Communications: Architecture, Performance and Applications.” (2015).
- 43. Mehmood, Y., Görg, C., Muehleisen, M. et al. Mobile M2M communication architectures, upcoming challenges, applications, and future directions. J Wireless Com Network, pp. 250, 2015.
- 44. Le, Nam Tuan, Mohammad Arif Hossain, Amirul Islam, Do-yun Kim, Young-June Choi, and Yeong Min Jang. “Survey of promising technologies for 5G networks.” Mobile information systems, 2016.
- 45. Dighriri, Mohammed, Ali Saeed Dayem Alfoudi, Gyu Myoung Lee, and Thar Baker. “Data traffic model in machine to machine communications over 5G network slicing,” in IEEE 9th International Conference on Developments in eSystems Engineering (DeSE), pp. 239-244, 2016.
- 46. G Velev, “M2M applications and 3GPP cellular networks,” (NEC Laboratories Europe, (2014). www.docbox.etsi.org.
- 47. QUALCOMM, LTEMTC, “Optimizing LTE-Advanced for machine-type-communications”, 2014.
Note
- *Corresponding author: [email protected]
