The recipe describes how to access an internal machine using Microsoft's Remote Desktop Protocol (RDP).
The purpose of this recipe is to demonstrate a typical firewall task from start to finish. The following example will demonstrate how to remote into an internal machine from anywhere on the Internet. Doing so requires the configuration of the following features, which have all been covered in recipes preceding this point in the book:
- DHCP Server
- DHCP static mappings
- DNS Forwarder
- Aliases
- NAT port forwarding
- Firewall rules
- Schedules
- Let's connect a computer to our network.
- Browse to Status | DHCP Leases to find the newly added computer. Click the "plus" button to assign a new static mapping for the device:
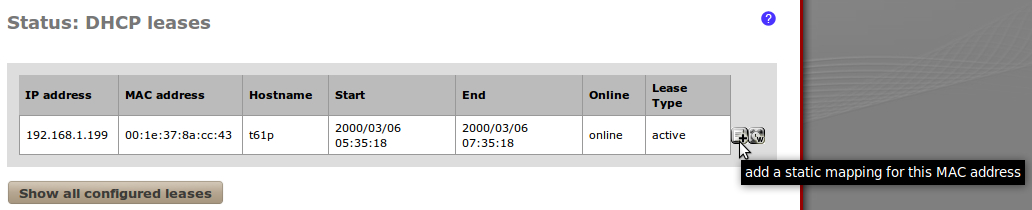
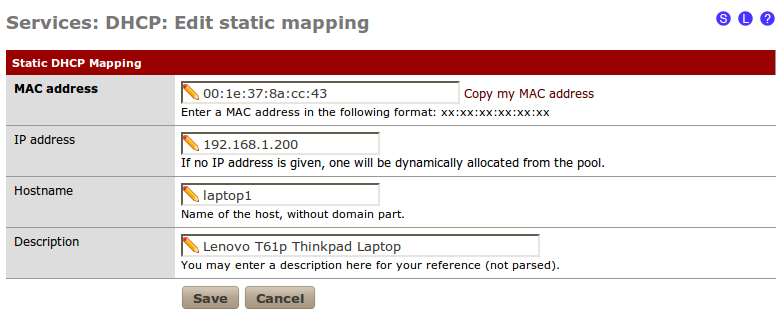
- Let's assign it a static IP address of 192.168.1.200 and call it laptop1:
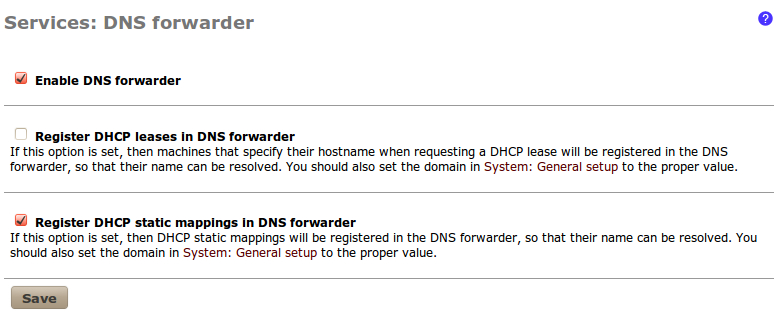
- Let's make sure our DNS Forwarder is configured to automatically serve static mappings at Services | DNS Forwarder, so that we can easily reference our laptop computer by name:
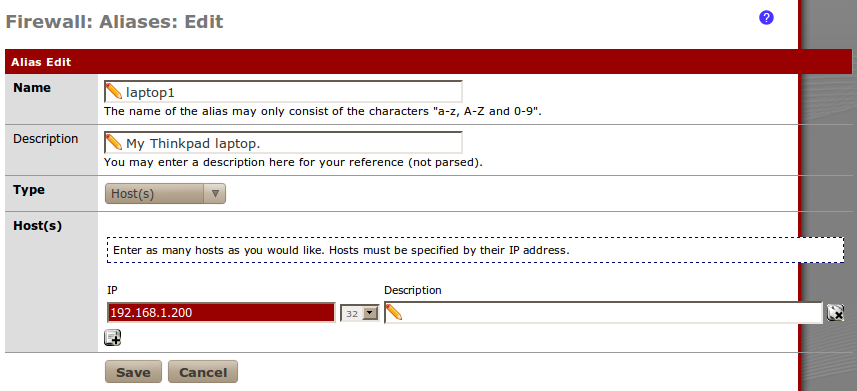
- Let's create an alias to be used when referencing this machine within pfSense from Firewall | Aliases:
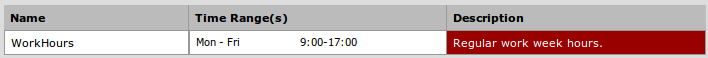
- Let's create a schedule at Firewall | Schedules so that remote access is only enabled while we're at work, since that's when we intend to use it. Also, we can rest a little easier that it's not susceptible to attack while we're sleeping:
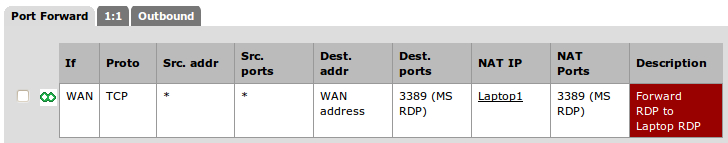
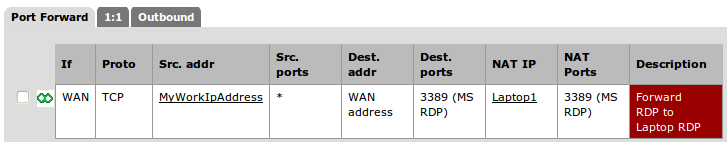
- Let's create a NAT rule to forward all remote desktop (RDP) requests to our laptop from Firewall | NAT. From researching on "remote desktop protocol" on the Internet, we know we are dealing with TCP port 3389 (PfSense includes a predefined MS RDP port because it's so common):
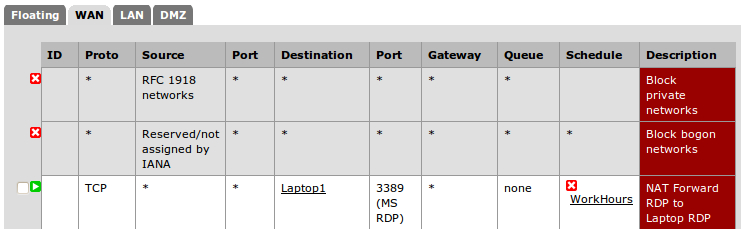
- Next, we need to add our schedule to the firewall rule that was automatically created from Firewall | Rules:
- Save all changes.
- Apply all changes, if necessary.
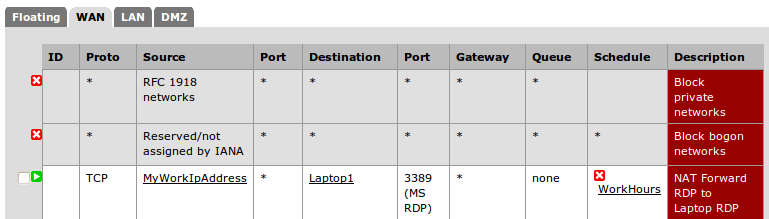
Our NAT rule forwards all RDP requests to our laptop. The NAT rule is always enabled. Our firewall rule allows anyone to remote into our laptop, but only during work hours (Monday-Friday, 9am-5pm). At the time of writing this book, it's Sunday at 4 pm; so you can see the rule is correctly disabled.
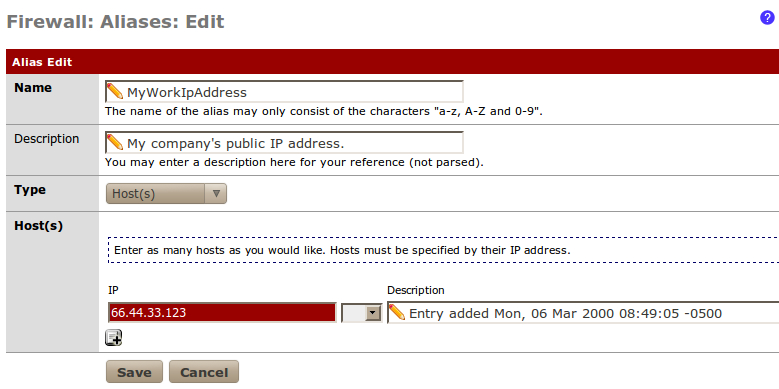
If we really wanted to tighten security, we could restrict external access to only our IP address at work. We would first create an alias for our office's IP address:
Then we would modify our firewall rule to only apply to requests coming from our company's IP address (remember, traffic that doesn't match any rules is blocked by default). Now, with pfSense's Filter Rule Association, we won't be able to modify the Source of our firewall rule directly.
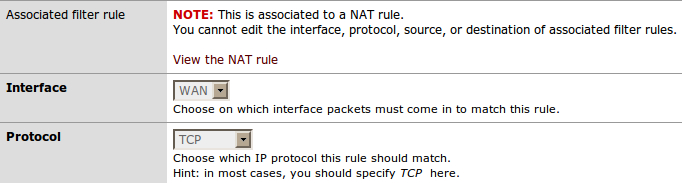
So, we'll modify the NAT rule instead. From Source, click the Advanced option and specify the alias for our company's public IP address.
Then we'll double check if those changes have propagated down to our firewall rule, which they have:
- The Configuring DHCP servers recipe in Chapter 2, Essential Services
- The Creating static DHCP mappings recipe in Chapter 2, Essential Services
- The Configuring dynamic DNS recipe in Chapter 2, Essential Services
- The Creating an alias recipe
- The Creating a NAT port forward rule recipe
- The Creating a firewall rule recipe
- The Creating a schedule recipe
