11
CloudIoT-Driven Healthcare: Review, Architecture, Security Implications, and Open Research Issues
Junaid Latief Shah1*, Heena Farooq Bhat2 and Asif Iqbal Khan3
1Department of Information Technology, Sri Pratap College, Cluster University Srinagar, J&K, India
2Department of IT & SS, University of Kashmir, Srinagar, J&K, India
3Department of Computer Science, Jamia Millia Islamia University, New Delhi, India
Abstract
The blending of Cloud Computing and IoT or CloudIoT provides an efficient paradigm to connect varied medical resources and dispense efficient, reliable, agile, and intelligent healthcare services to the patients with chronic illness. With CloudIoT, healthcare systems have been augmented with ubiquitous health monitoring and critical care services. The popularity of CloudIoT-driven healthcare applications has only surged in today’s world due to minimal cost implications and pervasive feature of sensor-based computing. Since IoT devices have constrained storage and processing power, as such are unable to provide efficient e-health facilities and process or store humongous volume of collected medical data. Thus, integrating IoT with Cloud provides a seamless platform for bridging the gap among dissimilar objects and regulating escalating resource requirements in healthcare sector. Although CloudIoT architecture contributes toward effective patient care, yet it is challenging, given the issue of reliability and security of the patient information. The framework also lacks an established and secure healthcare architecture. The CloudIoT involves disparate networks through which sensitive medical data gets transacted. This data could be abused by malicious users and pervasive healthcare service operations could be rendered ineffective. The healthcare systems require robust security in order to avoid data tampering and privacy of user data is not compromised.
In this chapter, we survey the available CloudIoT papers and showcase overall scenario on CloudIoT-driven healthcare services. The chapter contemplates discussion on background elements that drive CloudIoT-health paradigm and discusses various security protocols and enabling technologies powering CloudIoT-health platform. We also present a conceptual healthcare monitoring architecture that takes into account diverse tasks which include data analysis, communication, and computation involving cloud storage. A use case scenario is also presented that recognizes various elements that underpin and convert IoT data and transmit it to cloud. Also, we highlight design considerations for the architecture. The chapter discusses security loopholes inherent in IoT architecture and the Cloud platform. The chapter also elaborates discussion on various security countermeasures that have been proposed in literature highlighting their strengths and limitations. Also, a discussion on possible defense measures has been provided. Finally, the chapter culminates by underlining some burning research problems and security issues that need to be addressed for seamless healthcare services.
Keywords: Cloud, IoT, sensor, RFID, CloudIoT
11.1 Introduction
The Internet of Things (IoT) points to small interconnected objects that communicate data using internet autonomously without any human intervention. These objects use sensor communication that generates data at an exponential rate and arduous to manage, given the constrained computational power and data services embedded in these devices [3, 6]. To vanquish this, blending of Cloud into IoT, also referred to as CloudIoT, proves to be panacea for enabling transmission between varied dissimilar devices and managing exponential data generation rate [42, 138]. CloudIoT model allows flawless service deployment and application access hinged on various cloud supported models [3, 39]. As depicted in Figure 11.1, the seamless integration of two heterogeneous technologies has allowed for the design of rational and well-organized healthcare monitoring systems, surveillance systems, environment monitoring, smart city, smart homes, intelligent energy management systems, etc. [3, 66].
The recent times have seen a surge in aged population globally resulting in serious health ailments which, in turn, increases hospitalization and clinical care cost for people around the world [7, 95, 137]. Periodic health checks and monitoring play a significant role in minimizing healthcare costs and enhancing Ambient Assisted Living for elder people having chronic ailments [24, 35]. Traditional healthcare setup is quite monotonous and inappropriate which does not scale up to the current demand of our hospitals and healthcare institutions [8, 10]. The increase in ageing population has driven the necessity for designing coherent and structured healthcare systems which aim to minimize clinical costs and load on healthcare institutions and, in turn, improve the quality of life for older people [9].
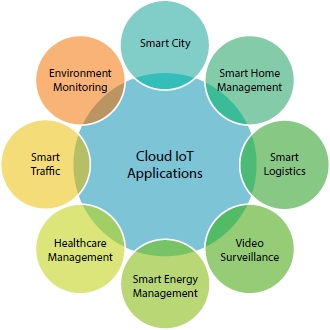
Figure 11.1 CloudIoT applications.
The CloudIoT framework enables varied IoT services to interconnect and transact information within the network for yielding robust healthcare solutions [98, 136]. There are number of factors and issues that drive further research work in this area, some of which include increase in aged people globally, rise in chronic and high-risk diseases, and soaring increase in daily health system [98]. The application of CloudIoT in health systems can augment medical infrastructure and can significantly improve patient healthcare with resolute and tenacious innovation [9, 42]. The implementation of CloudIoT system offers flexibility for patients to carry on with their usual business and day-to-day work while medical practitioners are tracking their activities in the background and providing them with expert advice and consultation [98]. With profound rise in chronic and severe health ailments, the application of enabling technologies like CloudIoT play a vital part in diagnosis and treatment that notably influences hospital costs and healthcare budget of average people [5, 60, 106].
To assist common people and ease daily life of patients having chronic medical ailments, the idea of ambient-based living has developed gradually with time [13, 14]. The application of CloudIoT in healthcare has supplemented diverse range of application which include deployment of wireless sensor network for collecting patient data, communication of data to the cloud, processing and data analytics, Artificial Intelligence-based services and application rendering [102, 130, 135]. One among the novel concepts of employing CloudIoT in health-based system is its ubiquitous nature of dispensing clinical services that have minimum service deployment costs associated with it [42, 86]. However, with ubiquitous nature and exponential data generation rate, healthcare systems demand high-end data storage systems with mining and analytics [150]. The cloud offers a robust system to serve the need and facilitate secure healthcare data transaction with concealing implementation part from the end system [28]. Also, it grants autonomy with respect to data transfer and storage and allows mobile devices of users to receive health updates and analysis [92]. The CloudIoT framework is being adopted on a global scale in order to collaborate and connect geographically separated medical infrastructures and also provide ubiquitous, scalable and economical healthcare solutions to patient community [1, 11, 116]. Implementation of CloudIoT framework in healthcare includes integration and collaboration of various state-of-the-art technologies, mobile apps, sensor nodes, and end users that transact and communicate information as one integrated system to analyze, track, and monitor data [14, 49]. Majority of CloudIoT healthcare models have three primary components. These include wearable body sensors and devices for data perception, communication device for real-time updates including data transfer to warehouse and cloud-based archival space for data inference and processing including mining [42, 104]. A large number of wearable body sensors including implantable clinical bio-markers are readily available in stores that carry out minute and precise data collection [133]. Majority of these sensors record vital patient data that helps in prior disease diagnosis and timely delivery of associated medical treatment [64, 121]. Some bio-sensors record electrocardiography (ECG) data of patients which gets transmitted to persistent storage in the cloud via wireless medium such as internet. The medical data is then studied and analyzed and relevant actions are undertaken [48, 51, 77]. The models can also include backend clinical care systems that continuously monitor and pull out information from the cloud storage [40].
The cloud also offers medical practitioners and health experts, on-demand and seamless access to varied range of data including E-Medical Records (EMRs), doctor recommendations, and laboratory test results aggregated from heterogeneous sources [45, 141]. Handling chronic health cases and ailments such as asthma and diabetes and follow up drug regimens can be done automatically, as the system can notify healthcare team in case of disparate or follow up appointments [2, 133]. The CloudIoT model also offers tools for data analysis that will update medical or clinical experts to observe and keep record of people at any time period [41, 96, 130].
Old age care and monitoring using CloudIoT has permitted aged persons to have an individualistic and vibrant quality of life [64, 121]. Providing timely and ubiquities medical attention to the aged people is one of the arduous tasks. CloudIoT-driven healthcare has been instrumental in alerting patients of their periodic medical attention and scheduled medication [49]. The CloudIoT platform also supports critical care applications that sense emergency situations so that real-time decisions could be taken with respect to providing healthcare facilities [71].
Although CloudIoT model augments healthcare framework substantially, its technical and implementation bottlenecks impede the vision of its expeditious and structured development [49, 141]. The CloudIoT model suffers inherent security challenges and privacy issues that compromise the validity of medical data [3]. Using CloudIoT infrastructure, sensitive, and personal patient data gets transacted over unsecured networks which could be abused by malevolent users raising concerns regarding its security and privacy [41, 145]. Ensuring security means protection and safeguarding IoT and Cloud infrastructure including applications from malicious intrusions [120]. For example, if the network layer in IoT gets compromised, then the attacker can gain control over the entire IoT network and leverage attack on other devices via the compromised node. Similarly, if the cloud fails to authenticate access to its interface, then the sensitive data might get leaked and exposed. In general, the devices that maintain online presence are susceptible to attacks from malevolent users [122]. A report from International Data Corporation points that by the year 2020, more than 200 million devices will be internet ready and most of these devices will be easy target for attackers. The attacks which include Denial of Service, harmful Trojans, and Worms would be mostly directed toward home appliances [82]. A study by Hewlett Packard (HP) indicates that about 70% of IoT devices are susceptible to attacks. As per recent analysis by HP, about 90% of Internet-enabled devices collected at least some minimal user information via the device product, cloud, or some mobile application. This personal user information is vulnerable to abuse and unauthorized access by attackers. This will, in turn, question the confidentiality and integrity of the personal data. As such, users will be hesitant to embrace this new technology paradigm [75, 82].
As of today, Machine-to-Machine (M2M), sensor networks, and Human-to-Machine (H2M) systems have become intrinsic components of CloudIoT-based healthcare framework; as such, security issues associated with sensor, M2M, and H2M continue to be persistent in CloudIoT platform with Internet Protocol (IP) being the underlying connectivity protocol [108]. Thus, entire CloudIoT health architecture needs to be protected from threats that may obstruct the rendered services as well as challenge the integrity, privacy, and authenticity of data. Since CloudIoT involves interconnection of heterogeneous networks, it automatically inherits the security flaws present in conventional computer networks [49, 138]. The limited computational resources in sensor objects further add to the complexity because the traditional security solutions cannot be applied. Therefore, extensive research has to be carried to provide seamless and robust security solutions for the CloudIoT platform [49, 75]. A majority of these security solutions are applied either at distinct IoT layers or Cloud, whereas other solutions dispense end-to-end (E2E) security for CloudIoT. For example, a recent survey research carried by authors in [4, 17] segregate security threats into four categories: application, communication, architecture, and data. This segregation of security threats is different from traditional layered network architecture. Also, threats for hardware, network, and application components are briefly discussed. Similar to this research, another survey in [57] elaborates discussion on security protocols for IoT and analyzes its security issues. The security issues highlighted in [37, 117] consider and contrast various key management frameworks and encryption algorithms. In [3, 6, 152], the authors present a holistic comparison of intrusion detection systems. Authors in [124] present a survey and debate on contributions dispensing confidentiality, security, authentication, and user privacy for IoT along with the security for intermediate layers. The authors also highlight on trust management, authentication issues, data privacy, and security of the network. A survey highlighting privacy preserving mechanisms for IoT has presented in [100]. In [157], the researchers pinpoint various security threats and their possible solutions for CloudIoT platform. The authors discuss user identity and privacy, sensor object compromise, and key exchange security implications for CloudIoT. A similar survey carried by authors in [5, 154] discuss vital security threats related to object identity, access authentication, user privacy, and demand for light weight encryption mechanisms.
In contrast to the existing work found in the literature, we follow the research methodology as depicted in Figure 11.2.
Our main significant contribution in this chapter is summarized as follows:
Figure 11.2 Research methodology.
- – Discussion on background elements that drive CloudIoT-health integration.
- – Review of security protocols and enabling technologies powering CloudIoT-health platform.
- – Presents a conceptual architecture for healthcare monitoring system. The architecture includes a real-life model that presents actors and flow of data that achieve transformation IoT data to cloud platform. Also, we highlight some architectural design considerations of the platform.
- – Summarizes and highlights various security vulnerabilities hampering seamless IoT model including issues persistent in the Cloud platform.
- – Holistic vision on varied security countermeasures that have been proposed in literature highlighting their strengths and limitations. Also, a discussion on possible defense measures has been provided.
- – Underlines some open research issues and security implications that demand robust solutions for seamless healthcare services.
The segregation of the other sections of this chapter is as follows:
Section 11.2 points out the background elements that drive the CloudIoT health paradigm and highlights underlying reason for their seamless integration. Section 11.3 elaborates discussion on security protocols and various enabling technologies for CloudIoT healthcare. Section 11.4 presents a conceptual architecture for healthcare monitoring system and includes a real-life model that presents actors and flow of data. Also, a brief overview on design elements has been provided. Section 11.5 presents various security vulnerabilities associated with IoT architecture including issues persistent in the Cloud platform. Section 11.6 points out security countermeasures that have been proposed in literature highlighting their strengths and limitations. Also, a discussion on possible defense measures has been provided. Section 11.7 presents some open research issues and security challenges impeding development of a secure framework for CloudIoT health paradigm. Section 11.8 presents discussion and analysis. Finally, Section 11.9 concludes the chapter.
11.2 Background Elements
The CloudIoT platform serves remote healthcare monitoring applications and offers flexible services to patients having chronic health situations and disabilities [139]. Implementing health monitoring with Cloud and IoT assists in early disease diagnosis, and as such, feasible healthcare options could be made available to ascertain patient comfort and easement [102].
The “Internet of Things (IoT)” offers a computational platform to healthcare architecture where healthcare objects are deployed with sensors, tiny microchips having data transmission capability and state-of-the-art communication protocols for interfacing and interacting with communication network including the physical environment [49, 110, 129]. IoT-driven healthcare systems include disparate sensor network that perceive, monitor, and collect information from the surroundings and transmit this information in real time to the cloud warehouse using internet as the medium [43, 66]. This helps in archiving, analytics, and mining of large data volumes and trigger alert signals and message events. The IoT-driven health system dispenses a seamless data production service that allows medical information extraction from a remote system using internet as underlying medium [26]. Thus, IoT-driven health system has played a pivotal role in enhancing ambient medical service with vigorous surveillance and minimal costs [9].
The IoT in itself involves heterogeneous devices that transmit data over the network using diverse interconnecting protocols [3]. “Things” represent small sensor objects that have the capability to interact with similar devices over the network. For communication, these devices use standards such as “Bluetooth” and “Zigbee” that have small data signaling radius and minimal power gobbling features [144]. The IoT has led to the genesis of personalized Healthcare by recording medical history of each patient in the backend database [33]. As pervasive healthcare systems are not so common, several health complications go unnoticed in traditional healthcare models [24]. The IoT-based healthcare tries to bridge this gap by implementing active health surveillance and analytics of medical data [150]. IoT platform dispenses countless solutions for managing healthcare; however, the feasible one hinges on limitations and requirements of a particular implementation [66, 141]. The feasible layout aids in designing seamless and economical healthcare model that supplements existing medical infrastructure, hospital systems, and online patient check [10, 130]. As an example, to monitor patients physically in hospitals over a period of time, we utilize services of healthcare workers. However, IoT eliminates such liability by providing ubiquitous patient monitoring systems wherein sensors, control nodes, and cloud platform work in conjunction and transmit data wirelessly to medical team [139].
Even though the emergence of IoT-based healthcare has only increased in recent years, however no formal or precise architecture is yet originated for the concept framework. As illustrated in Figure 11.3, the fundamental architecture of IoT is partitioned into four layered hierarchy: “Perception or Physical layer”, “Network or Transport layer”, “Middleware layer”, and “Application or Service layer”. Each level in the hierarchy carries out a predefined function and offers service to the layer above it.
The first layer, i.e., perception or physical layer, consists of tiny physical sensors, “RFID”-based objects, actuators, etc. The basic function performed at this level is to perceive, monitor and record data and communicate this data to a predetermined destination system. The second layer, i.e., network layer, is assigned the task of transmission of collected information to a remote destination. The third layer, i.e., middleware layer, acts as an intermediary connecting the network interface and application and offers diverse analytical processes. The topmost layer, i.e., application layer, provides application interface and control panel to the user.
Although IoT is applied in varied application areas ranging from online health surveillance, smart e-healthcare, smart living, autonomous traffic system, and environment surveillance; however, these applications produce humongous volume of data that entail for pliable network infrastructure that can underpin such high traffic volumes [30, 153]. As already discussed, that IoT-based systems have limited space, thus it is not feasible to archive this data locally. IoT devices have inherent constrained computational power which degrades its performing capabilities [104, 105]. Earlier solution was to migrate data and computation to server computers which were stocked with requisite processing infrastructure. But, this process had some limitations [20, 126]. First, processing applications and archiving data on mainframe computers was a cumbersome process and costly. Second, in case the mainframe computers failed, the whole system would shut which was not desirable. Therefore, shifting data and computation to Cloud data center seems to be a robust solution [30, 104]. The Cloud offers a flexible, on-request, and supple infrastructure for health-based system hosting and dispenses accessibility to vast computational infrastructures that are connected to each other [39]. These computational platforms provide substantial power, software and storage space that succors limited IoT resources, hence assisting in ubiquitous computing. In cloud processing, the data is usually stored on remote warehouse server and computation including processing are delivered as a service to the users, thus eliminating cumbersome management functions from its client users [105, 144]. Integration of two varied technologies, i.e., IoT and Cloud, will dispense structured computation and energy management, and for designing intelligent clinical services [31, 49]. The Cloud platform can handle delay sensitivity as well as provide service as per request to applications in a secure and agile setup. There are several reasons that favor adaptation of Cloud infrastructure for IoT in healthcare perspective. These include being cost effective, definitive and performance, agile and flexible, scalability, and state-of-the-art security [39, 144].
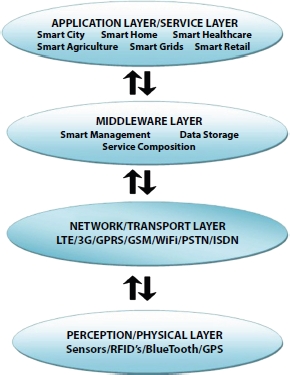
Figure 11.3 IoT layered architecture.
Adaptation of Cloud in clinical health dispenses a vital part in minimizing medical investment costs, augmenting people’s ambient life and enhances services that push for new technology-based insights [42]. The Cloud system allows healthcare data to be pervasive and as such can be retrieved given any location with no time constraints [136]. The cloud also grants seamless authentication to healthcare workers and practitioners to a vast database of medical information collected from disparate data origins that include medical records, laboratory test reports, test results, prescription of doctors, and health insurance data [51, 121]. This data could be utilized across systems for flawless policy making, precise diagnosis and cure, fixing appointment with doctors, etc. [53]. The cloud provides innovative data analytics that will assist healthcare workers and medical professionals to monitor patients from a remote location precisely and accurately [30]. A number of Information Technology giants such as “Microsoft”, “Google”, and “Amazon” are offering innovative solutions in healthcare domain and provide service platforms that integrate with relevant stakeholders to design economical medical solutions [116]. For instance, Microsoft-powered Health-Vault is a web-based personalized EHR developed by Microsoft to store and manage healthcare and patient information. Similarly, Google Fit developed by Google is a health-tracking platform that stores biological data of its end-user in the cloud. The cloud platform provides four unique characteristics that segregate it from conventional computing methods [3]. First, it furnishes an “on-request working model” that permits a user to access drive space and computation on server according to his flexibility. Second, it dispenses a “large network access” by granting access to variety of devices such as smart phones, hand-held tablets, laptops, and also workstations. Third, it “aggregates diverse data sources” and integrates them to develop a huge repository of resources that are available on demand to users. Fourth, it advocates “agility” of computing infrastructure that allows a server to calibrate to user service as per request and demand.
As depicted in Figure 11.4, the Cloud interface provides interface to the users at three different hierarchies: “Infrastructure Level (IaaS)”, “Software Level (SaaS)”, and “Platform Level (PaaS)”.
The IaaS offers a web platform to its users such as computing infrastructure that involve server computer, storage, and internetworking devices that are provided on demand. The leased infrastructure is extensible which is determined by user requirements and demand. The SaaS platform provides flawless entry to cloud interface and data-warehouse on lease. The implanting, augmentation, and amendments to software are handled by the SaaS interface. The “PaaS” dispenses a consistent software architecture and control interface to the client user.
As shown in Figure 11.5, the Cloud also offers different deployment platforms, i.e., public, private, and community cloud which provide abstraction of services at three different levels.
The cloud framework warrants that end user application performance is maintained in the platform [111]. For instance, when number of client requests that want to access the cloud platform increase, the cloud must automatically elevate and expand its processing capabilities to satisfy each and every request. Again when number of client requests decreases, the cloud must autonomously fine-tune its capacity to adjust the change.

Figure 11.4 Interface services.
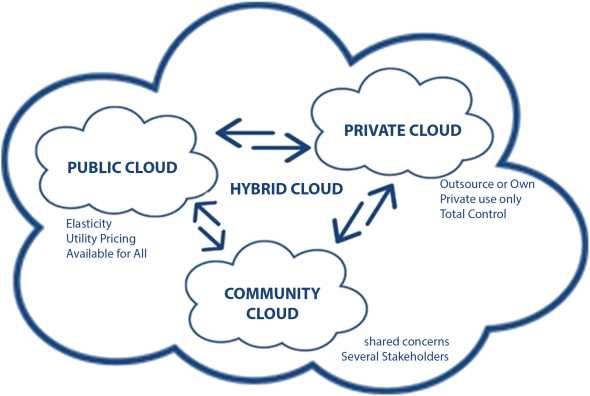
Figure 11.5 Deployment services.
Thus, implementation and adoption of CloudIoT seems to offer a coherent solution that is pliable, secure, less complex, and economical [81, 90].
However, with countless agile services offered by CloudIoT platform, the integration of two heterogeneous technologies is a challenging task [35]. The amalgamation process should take into consideration, problems that pertain to economy and cost viewpoint of internet service providers [25]. Also, CloudIoT platform must ensure reliable and secure communication and storage of data [39, 69]. The CloudIoT transacts private and sensitive medical data over its platform, as such is vulnerable to security threats from malicious users [79]. The problem becomes more complex in the scenario involving hybrid clouds. The main focal point on safety measures should be on ensuring that integrity, authentication, access, and isolation of data are maintained [94, 141].
11.2.1 Security Comparison Between Traditional and IoT Networks
It is evident from research that challenges and security issues of IoT and traditional networks vary in various aspects [63, 120]. The IoT involves RFID-based objects and nodes having constrained resources such as minimal CPU speeds and, often, objects are battery powered while as traditional networks such as internet is composed of high-end PCs, servers, smart phones, and tablet computers having abundant resources. Thus, traditional internet can support complex combination of security algorithms irrespective of resource usage and consumption [38, 115]. While as in case of IoT, lightweight algorithms having minimal resource usage that balance between security and computational power need to be implemented. The conventional cryptographic encryption algorithms demand swift computations, so it is not feasible to directly port them to IoT devices [79].
The IoT nodes communicate through slower and insecure wireless medium which is susceptible to data theft, privacy violation and node compromise. In comparison to this, traditional internet involves communication through faster wired medium such as optical fiber which is more secure and reliable. Even in case of wireless communication, the setup is built on top of complex and secure protocols which are not usually feasible with resource constrained IoT nodes. Additionally, IoT devices employ minimal data-rate radio technology for communication across the network. Thus, conventional security policies do not apply to IoT-enabled devices directly due to low-throughput transmission media implications [25].
Although internet consists of heterogeneous devices, but with the abstraction support provided by the operating system, the devices are able to share a common data format across multiple platforms. In case of IoT nodes, no such operating system or common data format exists. The nodes have embedded programs that vary with different chip hardware resulting in heterogeneous data contents and formats.
Table 11.1 shows typical feature difference between IoT and conventional networks.
Table 11.1 Feature contrast between IoT and conventional networks.
| Characteristic | IoT | Conventional network |
| Power | Constrained power | Unbounded |
| Setup | Mobile and flexible | Static |
| Framework | Self-organized (ad hoc) | Established standard, hierarchical |
| Communication range | Short distance transmission | Long-distance transmission |
| Routing | Random and dynamically build | End-to-end connection |
| Packet delivery mode | Cooperative, DTN type, and need incentive mechanism to stimulate | Optimized packet delivery |
11.3 Secure Protocols and Enabling Technologies for CloudIoT Healthcare Applications
The development of smart and interconnected objects entail for standard and robust secure communication protocols [38]. The IP engineered by Internet Engineering Task Force (IETF) is the standard delivery mechanism of Internet and is also used as a standard for interoperability of smart objects. As IPv4 addresses have exhausted completely, thus next-generation protocol, i.e., IPv6, seems to be a potential solution for enabling smart device communication [18, 115]. The protocol stack which CloudIoT will implement will be identical to the already deployed traditional internet in order to ensure interoperability and heterogeneous communications between devices. Thus, for seamless integration, security protocols that are developed for standard internet can be reused (or augmented in some cases) for smart device communication in a heterogeneous environment [63, 65].
11.3.1 Security Protocols
Internet Protocol Security (IPsec): At IoT’s network layer, a device can exchange data securely by implementing IPsec in its communications. IPsec forms an integral component in IPv6 as a part of extension header while as in IPv4; it was added as an additional feature in order to augment its security and encryption. The principal objectives accomplished by employing IPsec in smart object communication over an unsecure network are the data integrity, confidentiality, authentication, and protection against replay attacks. The IPsec offers two protocols for achieving security. These are Authentication Header (AH) and Encapsulating Security Protocol (ESP). Both of these standards are implemented as a part of extension headers in IPv6.
Transport Layer Security (TLS): To protect data exchange at transport layer, the TLS protocol is employed. TLS dispenses secure communication via object-based authentication and key interchange. TLS is commonly used for data encryption at the IoT application layer between the IoT applications and the backend server. The encryption can also be extended to other services such as short message communication and VoIP.
Secure Socket Layer (SSL): SSL protocol uses certificates that ensure security, integrity and protect identity of IoT devices. Although there are different varieties of SSL certificates but all use asymmetric encryption to protect the data communication between two sensor objects.
11.3.2 Enabling Technologies
RFID: RFID is the short form for “Radio-Frequency Identification”. In this communication technology, digital data which are concealed in RFID tags are detected by RFID reader using radio signal. RFID technology is analogous to bar-coding in which tag data is detected by a node and is then archived in data warehouse. In fact, RFID provides several merits over other devices that implement bar-code tracking software. The most significant advantage being that RFID tag data identification does not entail for line-of-sight communication. Using Automatic Identification and Data Capture (AIDC) methods, RFID automatically identifies objects, captures information, and stores that data directly into database without any human intervention. The base architecture of an RFID system consists of three main integral elements which include an RFID label, reader, and a communication media. The tags or smart labels consist of a microchip and an antenna to communicate data to the RFID reader. The reader transforms radio signals into readable data format which is then sent through a communication medium to an end computer system where data is archived in a database. In contrast with other available techniques, RFID offers optimized scanning, reliability, reuse, huge storage, non–line-of-sight communication, security, etc. Thus, RFID is an optimal choice to be used at IoT perception layer in order to identify, track and exchange data between objects in real time.
“Constrained Application Protocol (CoAP)”: CoAP is a messaging standard hinged on REST (Representational State Transfer) architecture designed for low power and computationally constrained devices in order to operate in an IoT environment [19, 29]. CoAP is developed by IETF core working team and is enumerated as RFC 7252. CoAP was designed to enable M2M communication between constrained devices and networks having low bandwidth and availability. As most IoT nodes are resource constrained, HTTP cannot be operated in such an environment owing to its complexity. To vanquish the challenge, CoAP has evolved as an alternative to HTTP operations in an IoT network. The CoAP protocol underpins features such as group communication including push notifications, communication with HTTP, resource identification, and security [145].
Wireless Sensor Network (WSN): A WSN form an integral part of an IoT network. A WSN is a network of sensor devices that can transmit the monitored information through wireless links. The data gets transferred using multiple nodes which are further connected to other sensor networks via gateway. The sensor network typically consists of a single base station and a set of wireless nodes which are used to scan and monitor the status of devices and transmit this status data to the base station or sink nodes. The WSN connects the line between virtual world and physical world and dispenses features such as scalability, robust reconfiguration, minimized cost, and minimal energy consumption. Both RFID and WSN are employed for data collection in IoT; however, the RFID is mainly operated for object tracking, while as WSN is mainly used for the sensing of real-world physical parameters inherent in the neighboring environment.
IEEE 802.15.4: The IEEE 802.15.4 is a protocol designed by IEEE 802.15 working scientists which expounds the working of low-rate wireless personal area networks (LR-WPANs). The protocol identifies the physical and the Media Access Control (MAC) layer for wireless personal area networks (WPANs). This standard underpins protocols such as Zigbee, 6LoWPAN, MiWi, and Wireless-HART, each of which further define the upper layers of the standard. The IEEE 802.15.4 standard aims to dispense minimal rate connections in personal area networks with minimal cost and power consumption. IEEE 802.15.4 protocol stack is analogous to the layers of OSI model wherein each layer implements a predefined function and lower layers pass the data and control information to the upper layers.
6LoWPAN: 6LoWPAN standard aims to carry IPv6 datagram’s with IEEE 802.15.4–based communication networks. The protocol dispenses E2E IPv6 connectivity, thereby providing direct communication with varied networks including internet. 6LoWPAN employs header compression technique for IPv6 datagram’s that are motivated by constrained space offered by 802.15.4 frames to encapsulate IPv6 data packets. The encoding formats for compression are defined by 6LoWPAN itself due to the fact that certain fields are implicitly available to all network nodes or can be implied from MAC layer. 6LoWPAN offers number of advantages such as minimal packet size, low power, and optimized bandwidth utilization.
Zigbee: Zigbee is a wireless protocol hinged on open standards designed to bridge requirements of low-cost and optimized energy IoT networks. This protocol works on IEEE 802.15.4 physical radio guidelines and using unlicensed bands such as 2.4 GHz, 900 MHz and 868 MHz. The Zigbee technology focuses on short-term communication utilizing low power and energy and dispensing high reliability and security. Similar to TCP/IP model, Zigbee operates using five layers which are physical layer, the MAC layer, the data transmission layer, the networking layer, and the user interface/application layer. For network configuration, Zigbee supports topologies such as Star and Mesh.
Z-Wave: Z-wave is wireless communication technology commonly used in designing smart home networks thereby permitting the smart devices to communicate and interact with each other and also interchange control messages and data. With duplex communication and data acknowledgement system, the Z-Wave protocol standard eases out power consumption issues and delivers low-cost wireless networking. Thus, offering a low-power and long-range alternate solution to Wi-Fi and Bluetooth. One important thing to note in Z-wave network is that only 232 nodes (slaves), all having routing capacity can be connected at a time which are managed by a controller node. The controller is also responsible for updating routing table which is stored in the memory of each slave. Although both Zigbee and Z-wave provide short range wireless data communication, however they differ in the frequency band in which they operate. The Zigbee operates at 2.4-Ghz frequency band in the physical layer while as Z wave frequency band is less than 1 Ghz.
MQTT: Based on publish/subscribe method, MQTT is a short message standard which is employed for acquiring sensed data on deployed sensors and further transmission of this data to the server. MQTT is primarily designed for networks suffering from low bandwidth and latency. MQTT finds implementation at various platform levels and thus plays a substantial role in connecting IoT with the global internet.
Extensible Messaging and Presence Protocol (XMPP): Hinged on XML streaming protocols, XMPP is an instant messaging protocol. Due to inherited features from XML, XMPP dispenses greater extensibility, addressing and security features. The protocol can also be employed for applications such as multi user chatting and voice including video streaming. XMPP protocol supports three main functional components: client, server, and gateway and also inter communication between them. With XMPP integrated in IoT, object to object communication is possible based on XML supported text messages.
Data Distribution Service (DDS): The DDS protocol is a publish/subscribe-based standard underpinning highly effective device-to-device communication and suitable for constrained IoT communication. Designed by Object-Manage-Group (OMG), the protocol is highly data dependent and supports multicasting to achieve perceivable quality of service and reliability. Table 11.2 lists the characteristics of various enabling protocols and technologies.
Table 11.2 Characteristics of various enabling protocols and technologies.
| Protocol | Spectrum | Transmission rate | Range |
| RFID | LF (126–135 kHz) HF (13.58 MHz) UHF (432, 860–960 MHz) | Upto 424 kbps | >10 cm |
| NFC | 13.58 Mhz | Upto 424 kbps | <20 cm |
| Bluetooth | 2.4–2.5 GHz | Upto 2.1 Mbps | ~10 m |
| BLE | 2.4–2.5 GHz | Upto 1 Mbps | ~10 m |
| Zigbee | 915 MHz/2.4 GHz | 20 kbps–256 kbps | ~10 m |
| UWB | 3.1 GHz–10.6 GHz | > 100 Mbps | ~80 m |
| Wi-Fi | 2.4 GHz–6 GHz | Upto 2.4 Gbps | ~100 m |
| Wi-Max | 2 GHz–11 GHz | 100 Mbps | ~100 m |
| CDMA/EDGE | 896 MHz | Upto 2 Mbps | ~100 m |
| 6LoWPAN | 816/915 MHz–2.4 GHz | 250 kbps | ~100 m |
11.4 CloudIoT Health System Framework
CloudIoT-driven healthcare services can be designed by amalgamation and blending together of varied tools that employ wireless medium for communication and implement sensor network for perceiving and sensing data from the environment [49, 102]. This data undergoes analysis and is archived for storage on cloud [39]. To demonstrate smart healthcare process, the idea can be implemented by a conceptual architecture framework also referred to as CloudIoT Health architecture [31, 133]. The architectural framework as depicted in Figure 11.6 supports three layers that implements various services that involve data perception or acquisition, data communication or transmission, and Cloud-assisted archival or storage. The perception or acquisition layers aggregates information which include various physiological and biological measure of people and communicates this information remotely to cloud platform for archival processing and storage.
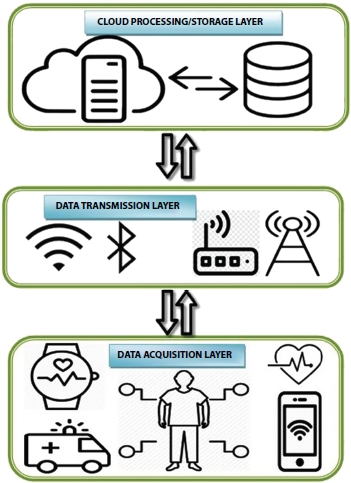
Figure 11.6 CloudIoT health architecture.
11.4.1 Data Perception/Acquisition
This layer composes of deployed sensor network which include perception or wearable data acquisition things which perceive, measure, and store healthcare information of patients. These wearable devices track and sense critical patient parameters including temperature, blood pressure, and heart rate and record this data remotely in a backend database [96]. This recorded data is heterogeneous in nature and varies across diverse patient groups and cases. For instance, in heart disease patients, measuring ECG data, saturation of O2, and pulse rate points to one of the basic components in the diagnosis of any heart related disease symptoms [44]. Similarly, for diabetic patients, measuring blood sugar levels periodically is very important. For applications that support the idea of ambient-based living or AAL in old people, monitoring and tracking their activities repeatedly is required [36]. Many application programs underpinning AAL are equipped with accelerometers and gyroscopic sensors that aid in medical data collection and tracking [121]. These sensors are usually classified into two categories: invasive and non-invasive sensors. Invasive sensors are permanently installed inside the patient’s body and usually have better performance than non-invasive sensors due to the fact that they are in close proximity with the patient’s body. However, these are not usually preferred by the elderly patients due to discomfort unless the issue is complex and severe in nature [5, 56]. In comparison, non-invasive sensors are usually preferred and are wearable on hand, forearm or any other body part of the patient. Some sensor-based application use actuators for generation of alerts if they sense or record any change with respect to physiological parameters of the patient [131]. The research community has been actively engaged in the design and development of intelligent body sensors which broaden the application area of CloudIoT-driven healthcare framework [101]. These body sensors generate massive volumes of data that require substantial amount of storage. One of the key considerations for the design of data acquisition layer is the cost implication, energy utilization and data transmission capacity of the network. The body sensor network design needs to be ad hoc, light, agile, and flexible in nature for accommodating any change [10, 103].
11.4.2 Data Transmission/Communication
The data communication level facilitates transmission of medical data to remote databases for archival storage [66]. The layer also provides seamless access to the vast collected data available in the cloud repositories [151]. This layer is assigned the task of communication of collected medical data of patient confidentially to an end healthcare data server. The data transmission occurs at the local as well as the global level. For local communication and for activities that involve monitoring and scanning the environment, wireless communication protocols such as Bluetooth and Zigbee are implemented. These protocols facilitate transmission between the data perception level and concentrator [12, 53, 125]. The wireless protocol such as Bluetooth is used for short range transmission having an working frequency as 2.4 GHz and offers a lost cost solution with economical energy consumption [125]. A similar communication standard like Zigbee protocol which is although not so popular as Bluetooth offers decent and reliable transmission of data. The alternate transmission standards employed at this level include RFID-based communication, “Near Field communication” (NFC), and “Ultra-Wide Bandwidth” (UWB) communication. RFID supports duplex mode of data transmission involving RFID tag and reader. In long-distance transmission, the information available in the concentrator is forwarded using the Wi-Fi or mobile data internet to the Cloud or Healthcare Organization (HCO) for long-term storage [23, 88]. The mobile data protocols such as 4G and LTE are utilized in varied health surveillance and communication devices. The data communication layer also underpins low-power hardware devices which include Arduino and Rasberry Pi that underpin IoT service deployment environment. These applications involve varied data crunching tasks that run on devices such as mobile phones, tablet computers, and microcontroller-based devices [49].
11.4.3 Cloud Storage and Warehouse
The CloudIoT-driven healthcare devices link heterogeneous things that transact considerable volume of bio-medical data and thus entail for efficient storage space and mechanism [148]. The Cloud processing layer involves three basic functionalities which include archival data storage, processing, or computation on stored data and finally analysis or mining data for information [85]. The Cloud service providers including “Google Cloud”, “OpenIoT”, “Amazon”, “Thing-Wrox”, and “GENI” provide an excellent interface for long-term storage of patient’s biomedical information and provides an interface to healthcare professionals to access this data pervasively for mining and data analytics. The data analytics helps the medical practitioners in better disease diagnosis and prediction and thus helps realize the concept of smart e-healthcare including generating alerts and notifications [31]. In addition, this layer also provides various data visualization tools which enable physicians to present and conceptualize data in a given format.
11.4.4 Data Flow in Healthcare Architecture – A Conceptual Framework
Connecting technology with healthcare is an important challenging area of research and development [27]. Though this area has seen technological surge in recent years, however, planning and decision making process of medicos still counts on manual and traditional record system [13, 102]. To achieve an optimal, reliable, and secure healthcare framework is a daunting and challenging task [14]. The transaction of medical data is restricted between the health department and its subsidiaries. The other entities in the system such as clinical doctors, patients, HCO, and laboratories have no provision for sharing or access to this data. The CloudIoT health provides an underlying platform for guiding healthcare system to focus their resources on augmenting patient care by efficacious disease monitoring, timely diagnosis and cost effective treatment [150]. The CloudIoT improves traditional healthcare system by employing bio-sensors and RFID-enabled devices [40]. These devices and sensors enable real-time patient tracking, identification, diagnosis, and treatment and also in some cases, dispensing of medical supplies and drug management [133]. The CloudIoT-driven healthcare effectively connects patients, sensor objects, and network and checks for optimal medical waste management [30]. Recent advances in low-power devices have enabled the design of pervasive health framework [43, 62]. In healthcare, sensor networks have been replaced by a novel idea known as Wireless Body Area Networks (WBAN) that realizes the concept of e-health [24]. A WBAN integrates number of sensor devices for health surveillance which measure health parameters and report medical status of patient. The CloudIoT-driven health supports diverse services such as e-prescription system, “Electronic Health Records” (EHC), “Personal Health Records” (PHC), data analytics and decision systems, and drug recommendation system. These applications cater to varied stake holders which include patients, medical teams such as doctors, testing laboratories, and chemists across diverse interfaces offering a range of services [116].
To understand the working of a typical CloudIoT-driven healthcare system, let us consider a use case scenario as shown in Figure 11.7.
The figure depicts various entities and identifies actors involved in the healthcare system and illustrates the data transaction among the processes. For instance, the patient can wear a body sensor that monitors and collects biomedical data. These bio-medical sensors are deployed either as invasive or non-invasive implants on a human body. These sensors can also be placed as an ornament or also placed inside patient’s clothing including footwear. These sensors work autonomously and are proficient enough to sense, monitor and record physiological parameters and transmit them over a wireless medium to backend database or cloud. The biomedical sensors are also equipped with GPS facility which enables them to track patients location and precisely determine their physiological and activity state, i.e., whether a patient is walking, sitting, running, or doing some other physical work. This collected data is then uploaded for archival storage in the cloud and can be accessed via an Electronic Health Record system (EHR). The EHR is maintained separately for each patient, which can be accessed ubiquitously and pervasively from any given location. This EHR is further shared among the medical team and clinical experts seeking their opinion as well as analysis. The medical team such as surgeons, doctors, and lab technicians access EHR and dispense prompt and timely patient treatment. The lab professionals would store MRI scans, X-Rays, and serum reports in cloud database or EHR after proper consent and permission from the patient. This EHR could be shared via cloud platform with other medical experts across the globe for their expert opinion and diagnosis, and hence, the patient could benefit with their prompt suggestions with shorter turnaround time period. Further, the clinical professionals can suggest certain drugs and emergency medicines which should be readily stocked at the pharmacy warehouses. The pharmacist can beforehand make those drugs available so that any shortage in future could be avoided. Additionally, the pharmacist can study the medical profile of a patient available to him via EHR for any allergic reactions, before he recommends or issues any drug to the patient. In the same way, the hospitals and nursing care institutions dealing with an exigency case such as accident can check patient’s blood group, medical history and other pre-conditions before operating with any medical treatment. All this sensitive information would be available pervasively via EHR stored on the cloud and can be accessed from anywhere across geographical boundaries. Using CloudIoT healthcare system, e-health record of patient which includes medical history, serum sample reports, body scans, and information regarding allergic reactions can be available in digital format and can be accessed in a ubiquitous manner under secure authentication policies, thus implementing the idea of smart health management system.
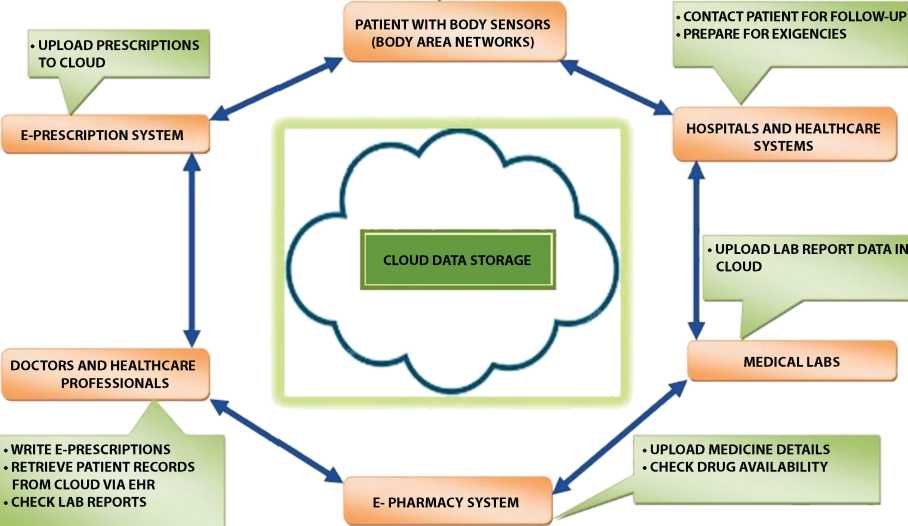
Figure 11.7 Conceptual healthcare scenario.
11.4.5 Design Considerations
The wearable things that monitor and archive patient’s bio-medical data consist of low-power sensors, small microcontroller chip, and a data transmission [26]. However, putting on bio-medical sensors by patients pose quite limitations on the overall design of bio-medical sensors [41, 122]. As an example, the sensors need to be light, minimal in dimension, and should not pose any hindrance to physical mobility of patient. The patient’s should feel comfortable while wearing these devices and should not affect their daily work routine. One of the critical design considerations is regarding the energy efficiency of the sensor. These sensors are usually battery powered and thus have limited operational working capacity [30]. Though sensor batteries are recharged or replaced, however the prototype should guarantee that no information is deleted during idle transition periods. The sensor design must ensure that they are able to work for extended time periods without any downtime or idleness [126].
Nowadays, research has focused on designing low-power sensors that can augment the working lifespan of the wearable sensor devices [101]. One of the feasible steps toward achieving this would be to harness other sources of power such as solar energy [103].
A similar feasible approach involves designing programmed intelligent sleep procedures for sensing nodes [31]. The programmed routines would force the sensor device to go into inactive stage when no perception task occurs during particular time period. If an external event occurs in the environment, the sensor would be triggered automatically to work again. Additionally, the sensor devices can be turned on/off based on relative importance of a task, its usage and patient’s current health status. As an example, in particular cases, when power usage is severely limited and health status of person requires working of only one particular bio-sensor, the other sensor devices attached with the patient could be turned off or put into sleep mode to conserve energy and increase working lifespan [127].
As data transmission consumes considerable energy, the limited battery power in sensors also entails for the design and usage of low energy consumption protocols. One of the efficient protocols for low-power communication is Zigbee using IEEE 802.15.4 which is usually utilized in “Low Rate Wide Personal Area Networks (LR-WPANs)”. This protocol supports communication between sensors that operate in the radius of 10 mts (10m). The Zigbee standard underpins reliable fully connected networking with optimal power usage.
Bluetooth Low Energy (BLE) is another wireless communication standard protocol that operates with minimal power and enables short range sensor communication [125]. BLE works in the similar fashion as traditional Bluetooth standard (IEEE 802.15.1), however augments the overall communication efficiency by enforcing programmed sleep routines to optimize power usage. BLE achieves reasonable accuracy with precision.
To further optimize communication, “IPv6 over Low Power Wireless Personal Area Networks” or 6LoWPAN is currently employed to achieve seamless data transmission in energy constrained devices [31]. 6LoWPAN breaks down IPv6 datagram’s in smaller fragments which are put as a payload in restricted IEEE 802.15.4 frame in order to achieve network connectivity.
The limited battery life also proves to be a bottleneck in determining data quality aggregated by a particular sensing node. The sensors need minimal power threshold to operate, however, if the system fails to maintain the minimal power threshold, then the sensor device may malfunction.
The sensor devices are capable of recording data efficiently and accurately when proximity with the patient’s body is close [127, 141]. Most of the sensors available today are non-invasive sensors that with greater accuracy and precision [15, 32, 80].
One of the essential considerations for designing an efficient healthcare system is to offload and migrate complex computations and processing from sensor nodes to the cloud platform [136]. Cloud platform provides substantial computational processing and humongous warehouse capacity that increments the limited sensor resources, thus dispensing optimal interface for ubiquitous communication [3]. The processing capabilities of Cloud can further be augmented by implementing the concept of Fog computing. The Fog layer offers a feasible interface for low latency in real-time and sensitive services like healthcare. The Fog also acts as an intermediate component for performing complex operations before actually moving the data to the cloud.
An essential and sensitive design consideration for healthcare framework is the ability to maintain confidentiality of patient and ensure safe and reliable information storage in Cloud [94, 112]. When sensitive medical data is transacted in the CloudIoT environment, robust security and efficient privacy procedures need to be operated so that no information is openly susceptible to abuse by malicious users. The data needs to be protected from unauthorized and illegitimate access. This implies applying feasible authentication and authorization policies and firewall rules that secure access to the data [39]. To encrypt data, light weight and low-power consumption cryptographic algorithms like Elliptic curve cryptography (ECC) should be applied.
11.5 Security Challenges and Vulnerabilities
Amalgamation of Cloud and IoT underpins framework of interconnected objects supporting varied range of services which include efficient healthcare systems, tracking patient remotely, concept of smart metropolis and homes, self-regulating traffic systems, industrial waste management, environment surveillance, as well as how these objects transact information with each other [59, 119, 120]. Some of these application areas of CloudIoT are listed in Table 11.3. The Cloud offers an excellent service and backup platform for IoT objects and sustains seamless access to shared resources which include processing, data storage, application interoperability, data analytics, and knowledge extraction features [54, 105]. Although adoption of CloudIoT framework in healthcare sector seems to be instrumental, however there has been minimal consideration with respect to its security implications [72, 124]. If data breach and security loopholes are there, then the healthcare framework would be rendered ineffective and sensitive patient data could be abused by malicious users [102]. Integrating Cloud and IoT will make the issue more compounded and will expose hidden security flaws making billions of interconnected sensor objects vulnerable. As such, the security drawbacks will negate the benefits of CloudIoT [113]. Given the widespread deployment of infrastructure and cost implications, it is also not optimal that sensor devices should be re-organized and changed periodically. The rudimentary security framework needs to be profound and sustainable from the core to work for an extended time period.
Table 11.3 CloudIoT application areas.
| Application area | Common examples |
| Smart Home | Intrusion detection systems, smart alarm system, motion detection |
| Smart Healthcare | Remote patient monitoring, drug regimen alerts |
| Smart Ecosystem | Pollution alerts, tree fire detection, UV radiation monitoring |
| Smart Agriculture | Meteorological updates, remote farmer assistance, greenhouse emissions monitoring |
| Smart City | Traffic updates, smart lighting, automated parking systems |
| Smart Industry | Energy management, assembly line monitoring, quality checking, and packaging |
11.5.1 Security Characteristics and Objectives
The CloudIoT enables information communication between interconnected sensor objects and remote systems to attain certain predefined objectives. For a secure communication in hostile scenarios, it is quite evident that security principles such as confidentiality, authenticity, privacy need to be protected [113, 115]. However, with limited security infrastructure and constrained resources, the models demand restructuring of existing security tools and algorithms to achieve perceptible security goals [22, 124]. The security framework should be imposed in CloudIoT throughout its developmental and working lifecycle [62]. Some of the secure principles that need to be practiced include the following:
- – All installed software on CloudIoT platform should be authentic and robust.
- – The initialization of IoT devices should be authenticated with the network servers before the device starts data perception and transmission.
- – There should be periodic security updates on CloudIoT devices in order to plug security loopholes; however the process should not consume additional network bandwidth.
The following security parameters as depicted in Figure 11.8 need to be safeguarded for secure transmission between IoT and Cloud platform.
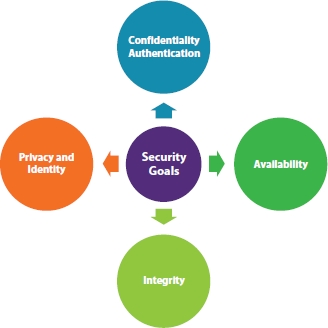
Figure 11.8 CloudIoT security goals.
11.5.1.1 Confidentiality
The confidentiality feature corroborates that data is accessible only to authenticated users and cannot be sniffed or eavesdropped. The collected data from the environment using sensor devices should not leak confidential information to the neighboring nodes and safeguard it from any illegal access. To enforce confidentiality, use of cryptographic techniques and secure key exchange mechanisms is highly recommended [62]. The confidentiality principle should also ensure how the data is managed in a hostile environment.
11.5.1.2 Integrity
The integrity principle warrants that data is tamper resistant and can withstand interference from malicious users during the transmission. The integrity features guarantees that accurate data which is also reliable is obtained by the intended destination. To ensure data integrity, robust security algorithms and cryptographic procedures should be operated in data communication and transmission.
11.5.1.3 Availability
This principle guarantees data of sensor devices is read only by authentic users whenever it is demanded. The sensor devices in internetwork involve real-time information transmission with minute delays. Non-availability of data would result is undesirable delays which will impact the performance of the sensor network. The most common threat to data availability is the denial-of-service attack that aims to render computational processing and resources inaccessible to its legitimate clients. To avert such issues, enhanced techniques such as secured and intelligent routing protocols need be employed into the network.
11.5.1.4 Identification and Authentication
The identification principle warrants that unauthorized objects or services should not get access to the network. The authentication, in turn, ensures that valid and legitimate data is transacted in the CloudIoT network. Due to diverse nature of Cloud and IoT, verifying and validating each and every object is quite cumbersome process [118]. The process should however be optimal, mutual and feasible so that only legitimate device transacts information in the network.
11.5.1.5 Privacy
The privacy principle warrants restricted information access and control to legitimate users. Contrary to confidentiality that utilizes encryption and cryptographic standards to avoid tampering of information, the privacy principle ensures limited authorization and limited operations over data. The privacy is one of the dominant components in data communication due to the fact that considerable number of devices and users transact sensitive information over an unsecured sensor network.
11.5.1.6 Light Weight Solutions
This feature is required due to underlying computational and processing power limitation imposed by CloudIoT platform. As sensor devices have constrained resources, the algorithms that run on these devices should be optimal without involving complex cryptographic procedures. The algorithms should be in tune with processing capabilities of the sensor nodes.
11.5.1.7 Heterogeneity
The objects in CloudIoT framework are intrinsically heterogeneous in nature with varying potential and complexities. These objects use diverse platforms and operating frequencies to support M2M and H2M communications. CloudIoT framework acts as a bridge between different heterogeneous components and networks. Thus, the protocols and algorithms must be developed keeping the dynamic nature of the technology in mind.
11.5.1.8 Policies
The standard policies must be in place to ascertain that data is organized, secured, and communicated in an optimal fashion. The current strategies applied for computer and network security may not suffice for CloudIoT framework due to its dynamic and heterogeneous characteristic nature.
11.5.2 Security Vulnerabilities
Security loopholes inherent in CloudIoT model involve problems in IoT sensor network including those immanent in the Cloud platform [12]. This section first highlights security vulnerabilities ingrained at each level of IoT model and thereafter draws attention toward vulnerabilities inherent in Cloud architecture. Figure 11.9 depicts list of CloudIoT vulnerabilities.
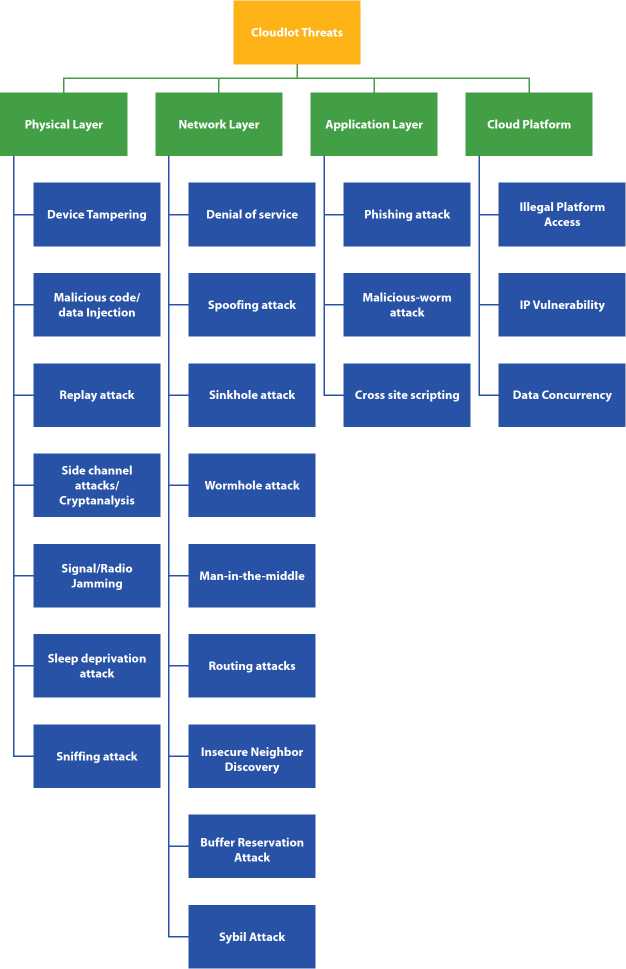
Figure 11.9 List of CloudIoT threats.
11.5.2.1 IoT Threats and Vulnerabilities
The IoT layered architecture is susceptible to disparate set of vulnerabilities from abusive users [12, 97]. These attacks are primarily classified as active or passive attacks depending on their source of origin which can be external or from inside the network. An active attack directly disrupts the normal operation of the service and is more minacious in nature. The passive attack works in stealth mode and monitors the network operations covertly [8, 62]. With large adoption rate of IoT, smart objects are vulnerable to security risks. Each layer of IoT should be secured in a way such that no data gets lost or modified in the network [22]. The IoT level wise elaborate security analysis is presented below.
11.5.2.1.1 Perception Level Threats
The principal function of this layer is to sense the physical environment, as such most of the attacks in this layer are directed toward altering or fiddling the captured data by malicious users. Some of the common attacks and threats in this layer are as follows:
“Node Hijacking Attack”: The layer mostly comprises of sensors and RFID’s which remains the prime focus for attackers whose aim is to cause physical damage to the hardware [155]. If a malicious user is successful in compromising the security of the physical deployed sensor object, then the sensitive information such as encryption and authentication keys becomes vulnerable to abuse. Also, to forge authentication with IoT network, the sensor object can copy vital information parameters from a compromised node. The attackers can also tamper software routines of sensor nodes by injecting malicious scripts and thus alter and downgrade its normal working operations.
“Replay Attacks”: The attackers can manipulate trust via replay attacks and redirect critical data to inappropriate and malicious user systems [93].
“Eavesdropping”: Eavesdropping is one of the common attacks leveraged by attackers in a wireless environment such as internet. In this attack vector, the malicious user transmits push notification to users using a compromised sensor node which enables it to collect sensitive private data.
“Sniffing Attacks”: The attackers can sniff the network by placing malicious sensor objects in the vicinity of legitimate IoT devices in order to capture sensitive information. This leads to user identification, tracking, and profiling covertly by malicious nodes.
“Data Noise”: The data transmission over unsecured wireless networks may contain noise and the data might be corrupted. Such incomplete information could be fatal especially in such scenarios where the working of IoT devices is hinged on reliability of available data.
“Sleep Deprivation attacks”: These attacks are aimed at draining the limited battery resources of sensor nodes. The sensor batteries need to work in optimal way in order to operate for longer time periods. As such, the nodes may go into sleep mode in case of no sensing activity at a given point in time. The sleep deprivation attack tampers programmed sleep routines so that sensors work continuously resulting in energy drainage and sensor anomaly [23].
“Jamming Signals”: The attackers deliberatively relay jamming or blocking signals that interfere with otherwise normal wireless signals [59]. These jamming or interference signals induce noise and deliberately disrupt normal communication between sensor nodes and backend data center.
11.5.2.1.2 Network Level Threats
This layer is heavily vulnerable to security leak as all the data aggregated with sensors gets communicated through this layer. This layer supports combination of traditional internet-based protocols and those that are unique to IoT. Therefore, this layer is open to both traditional TCP/IP network layer threats as well as threats that are unique to IoT architecture. Most of the security countermeasures aim at providing accessibility to the network infrastructure [88]. The security framework considers maintaining node integrity and privacy and ensures that authentic and reliable data is transmitted over the internetwork. A summary of common threats is listed below.
“Denial-of-Service (DoS) Attack”: The main aim of this vulnerability is to make computational infrastructure unavailable to the legitimate user. In this attack, the sensor objects or devices are flooded with illegitimate data traffic which they cannot process or handle simultaneously. This leads to device shutdown and disrupts network operation. There are various types of DoS attacks which include bandwidth wastage, overloading processors with massive computations, encumber memory and storage. Common countermeasures employed for mitigating such attacks include applying strong firewall strategies and gateway rules.
“Gateway Attacks”: The main focus of these attacks is to break down communication between sensor nodes and internet infrastructure. These are different class of DoS or routing attacks that redirect erroneous information from internet toward deployed sensors. Thus, impeding the normal working operation of these nodes.
“Storage Attacks”: A large volume of sensitive user data needs to be stored on Cloud data center which is vulnerable to abuse unless protected by strong cryptographic encryption algorithms. The attackers can replicate the data and cause data redundancy leading to wastage of storage space.
“IP Spoofing”: This class of attacks is segregated in two classes: Address concealing and RFID tag tampering. In both classes, the attack destination is the backend control of IoT system. The attacks specifically aim to transfer malicious code across the network [88].
“Black Hole Vulnerability”: In this vulnerability, network traffic gets altered and performance downgrades because malicious node drops some data packets. This results in information loss because the collected data does not reach the intended base station. Additionally, other attacks that attract traffic toward the victim node are “Illegal node access attack”, “Sybil Attack”, “Sink Hole attack”, and “Worm Hole attack”.
“Routing Attacks”: In this attack, the main aim of the adversary is to tamper the routing policy including routing protocols and generate routing loop. This leads to network congestion and increased packet loss rate [23].
11.5.2.1.3 Application Level treats
This is the topmost layer in the IoT network. This layer provides a platform for running client applications; therefore, most of the threats in this layer are directed toward shutting down applications. The main of the attacker is to inject software bugs in the program code that sets off the application to malfunction. There is no standard security protocol designed yet for IoT; therefore, these security vulnerabilities demand robust and substantial solutions. As disparate applications access application layer platform, therefore homogeneity of security architecture would be an arduous task. The common application level security threats are as follows:
“Malicious code attack”: Also known as code injection attack, the vulnerability aims to breach security of the system and inject malicious code in the application program code. For example, a malicious worm could spread over the internet and attach itself to the embedded operating system of IoT node, thereby compromising its operation.
“Node Application Tampering”: The attackers exploit vulnerability in sensor nodes and install malicious code. Failing to secure the sensor node would result in sensor malfunction and incorrect data collection. For example, malfunctioned temperature sensor would always display fixed temperature reading. Also, a compromised smart camera will record and display outdated pictures. Similar to this, in a scenario such as smart meter which transmits data utilization to the backend for real-time billing must be protected. The sensor devices should thus be robust and tamper resistant
“Failure to update security software”: Although not a security threat, the inability to update security software on sensor devices can lead to catastrophic situations. For example, in case of real-time systems such as nuclear reactors, the failure to update security algorithms leaves the system vulnerable to disaster like situations.
11.5.2.2 Cloud-Based Threats
The vulnerabilities inherent in conventional cloud-based devices are also present in the CloudIoT platform; in fact the amalgamation of two disparate platforms will induce more complex security vulnerabilities that entail for robust solutions [58]. Most of the IoT devices demand computation and require storage space on the cloud platform. This necessitates ensuring that privacy and confidentiality of data is maintained. The cloud must also block unauthorized access to the data and strong encryption should be in place to ensure data abstraction [132]. As cloud platform is pervasive, the IoT objects access this platform via different networking protocols which are susceptible to various attack vectors like “Man-in-the-Middle attack”, Eavesdropping, and “Denial-of-Service” attack [23].
Additionally to above, the Cloud suffers vulnerabilities owing its characteristic features.
According to NIST [92], the Cloud platform offers five unique characteristics. These include on-demand service, pervasive access to devices, pooling of resources, agility, and metered service. However, these characteristics invite vulnerabilities which are listed below:
Illegal platform access: As cloud supports on-demand service feature, it offers its management platform to varied number of users. As such, the probability that malicious users could access the platform is higher than the traditional systems which are monitored by only few administrators.
IP vulnerability: The ubiquitous nature of Cloud allows access to its platform using standard internet protocols. However, most of these network protocols have inherent vulnerabilities like man-in-the-middle attacks, session hijacking vulnerabilities, leaving the communication infrastructure as un-trusted and unsecure.
Table 11.4 Summary of CloudIoT threats and vulnerabilities.
| Vulnerability | Description | Mitigation | References | |
| “Perception layer” | “Device Tampering” | Control the working sensor device by physical damage or tampering its software code. | Physically checking the damaged site and monitoring malevolent code. | [12, 17,39] |
| “Malicious code/data Insertion” | Inserting vulnerable code into software program of sensor device to alter its normal behavior. | Practicing secure code writing including code testing procedures need to be designed and developed. | [46] | |
| “Replay vulnerability” | Forging authentication keys to obtain trust of sensor node. | Ensuring robust timestamp methods in digital authentication of keys | [17] | |
| “Side channel abuse/cryptanalysis” | Using normal-text/coded text, read cryptographic keys illegally. | Efficient and safe key development and encryption protocols need to be enforced. | [20, 70] | |
| “Radio jamming” | Mixing unwanted signal or radio waves to tamper and fiddle with wireless communication. | Intelligent noise reduction procedures and regenerating original needs to be designed. | [78, 88] | |
| “Sleep mode tampering” | Imposing sensor node shutdown by fiddling with their normal sleep procedures so that they up and continuously running all the time even when not required. | Exploit alternate sources of energy like wind, solar. Practicing secure code writing including code testing procedures need to be designed and developed. | [23, 22] | |
| “Sniffing attack” | The attackers sniff RFID-based wireless communication and extracts sensitive data like password thereby making the system open to exploit. | Ensure encrypted communication in the network. Use of asymmetric key cryptography is recommended. | [17, 22,39] | |
|
“Network layer” | “Denial of service” | Redirecting large volume of traffic on target system to make it work erratically and abnormally. | Developing secure firewall structure and packet inspection protocols in network devices. | [17,39] |
| “Spoofing abuse” | Conceals identification (IP or RFID spoofing) of genuine nodes to obtain unauthorized authentication. | Developing efficient and advanced access control standards and authentication algorithms. | [25, 70] | |
| “Sinkhole abuse” | To take over routing of information, the target node announces abnormal or unusual power/computation capacity. | Developing encrypted routing protocols and limited access to data forwarding nodes. | [57, 88, 109] | |
| “Wormhole attack” | Targets a routing protocol in which a packet or individual bits of a packet are captured at one location, transferred to another location and then replayed at some different location. | Developing encrypted routing protocols and limited access to data forwarding nodes. | [57, 88] | |
| “Man-in-the-middle” | The abusive node substitutes itself between two target nodes or systems. Spoofs their identity and obtains illegal access to data covertly. | Developing efficient and advanced access control standards and authentication algorithms. Practicing secure code writing including code testing procedures need to be designed and developed. | [70, 78] | |
| “Routing attacks” | Idea of this vulnerability is to create routing loops that causes massive network congestion. | Developing encrypted routing protocols and limited access to data forwarding nodes. | [57, 63] | |
| “Insecure neighbor discovery” | IP Address Spoofing | Employ light weight cryptographic procedures for authentication | [23,63] | |
| “Buffer reservation attack” | Blockage of Re-assembly Buffer | Split buffer approach requiring complete transmission of fragments | [70, 78] | |
| “Sybil attack” | Attack results in privacy violation, spamming and unreliable broadcast from fake spoofed nodes | Analyze user behavior and keep record of trusted/un-trusted nodes. | [70, 78] | |
| “Application layer” | “Web phishing” | Aim is to extract authentication information that includes passwords/usernames by spamming network with mails and fake pages. | Practicing secure code writing including code testing procedures need to be designed and developed. Creating awareness within web developer community. | [23, 120] |
| “Worm attack” | Spam’s the IoT network with Worms, Viruses and selfreplicating Trojans etc. Maliciously deletes sensitive data. | Developing secure firewall structure and packet inspection protocols in network devices. | [57, 62] | |
| “XSS attacks” | To gain access to authentication information including cryptographic passwords by inserting applications with malicious code. | Practicing secure code writing including code testing procedures need to be designed and developed. | [62, 70] | |
|
Cloud platform | Illegal platform access | Attackers access the cloud platform illegally and perform malicious operation. | Ensure strong authorization and authentication measures. | [47, 49] |
| IP vulnerability | Vulnerabilities persistent with standard IP model also exist within the Cloud. | Employing stripped and lighter versions of security protocols such as IPsec, SSL, and Https. | [23,30] | |
| Data concurrency | Attacker leverages simultaneously operations on the interface. | Ensure Concurrency control measures. | [42, 58] |
Data recovery issues: The Cloud platform allows resource pooling and rapid agility that allows computational resources to be assigned to multiple users at different intervals of time. However, it might happen that data written by the current user might be recovered by a different user accessing the same platform. This results in data privacy leakage and theft.
Tampering data usage: Every service rendered by the Cloud platform such as storage, processing or platform access is measured with metering capability with active user accounts. Based on the data usage, bills are generated and processed including payment. However, malicious user could play with the interface and cause data manipulation as well as billing evasion.
Table 11.4 lists the summary of various CloudIoT threats and vulnerabilities.
11.6 Security Countermeasures and Considerations
11.6.1 Security Countermeasures
For seamless integration of two disparate technologies, i.e., Cloud and IoT, the security framework should cover both these platforms. However, this security framework should ensure that principles of authentication, integrity and confidentiality are not violated. In this section, we discuss research highlighting security vulnerability awareness and various security counter measures that handle varied security threats.
11.6.1.1 Security Awareness and Survey
Authors in [156] address the security issues inherent at each IoT layer with some given security countermeasures. However, the security solution includes encryption only at the perception layer. Also, the authors do not reference to any specific evaluation framework that will evaluate the specified security measures.
Researchers in [128] present a generalized overview of IoT and Cloud with special reference to security issues inherent in both the technologies. Their work integrates the two technologies in order to study their common features and examine the benefits. The paper also presents the challenges associated with the amalgamation of Cloud with IoT and concludes that for seamless integration, the security issues must be resolved and reduced to minimum. The paper presents two cryptographic algorithms, AES and RSA, which authors claim can aid in the integration of IoT and Cloud; however, there is no mention of other lightweight cryptographic algorithms such as ECC, TEA, DESL, and LEA. These lightweight algorithms perform optimally well in constrained IoT environment.
In [118], authors provide short summary of security and privacy challenges and conclude that privacy and data integrity are fundamental security principles with respect of IoT and Cloud. The authors also argue that ensuring and warranting confidentiality comes under the prime reasons responsible for flawless CloudIoT operation. Similar work has been showcased in [132], where the authors highlight IoT implementation, security challenges and open issues.
In [70], the authors present a survey of IoT security framework and analyzed its various security aspects. The work presents a systematic summary of IoT security requirements as well as issues. The authors also highlight attack platforms, issues and temporal measures that must be taken into account while securing IoT network. The paper also elaborates discussion on various research issues including directions for future work.
11.6.1.2 Security Architecture and Framework
Diverse solutions with regard to IoT security architecture and applications are available in the literature. We summarize some of them briefly here [57, 61].
Authors in [72] present security architecture of IoT and discusses security vulnerabilities at each IoT layer along with potential solutions. The paper also contemplates discussion on key enabling technologies at each layer of IoT and presents their comparative analysis. The paper also presents a typical security comparison between IoT and Traditional networks and concludes that IoT system security needs to be augmented as they work with constrained and limited security resources. The paper however does not mention any technique to evaluate the proposed security architecture. Also, paper fails to provide any future directions for their research.
In [34], authors present an IoT security framework that highlight security loopholes in conventional IoT networks. The architecture includes black software defined networks (SDNs) including a Key Management System which ensures confidentiality, privacy, integrity, and optimal key distribution. However, presented architecture fails to sustain a full SDN implementation owing to limited power in IoT environment. This leaves IoT nodes susceptible to serious security threats such as node capturing, eavesdropping, and tampering. The framework also suffers from decreased network performance and complex data forwarding.
In [16], authors recommend a SDN as a potential remedy to tackle the vulnerability issues in IoT. SDN concept elevates the network performance and lowers hardware usage and also dispenses a robust security and privacy in comparison with traditional networks. The paper also outlines the architectural design of SDN and its suitability for IoT and ad hoc networks. The paper however does not evaluate the performance empirically and the concept is only a theoretical one.
Authors in [140] introduce SDN architecture for designing IoT applications that remove non-agile security setup of traditional networks. The motivation for the adoption of SDN was development of network OS that will assist administrators in containing various IoT threats and take control of the system. However, scalability and reliability are some limitations of SDNs. The SDNs also suffer from poor packet handling performance that leads to delays and DoS attacks. Similar work has been reported in [15].
In [52], researchers propose a new SDN architecture also called SDN domain using border controllers. The researchers explain the role of SDN in interconnecting heterogeneous IoT devices, augmentation of domain security and distribution of security rules. However, researchers fail in addressing the issue of securing legitimate as well as illegitimate traffic including enterprise security.
In [67], authors present a lightweight validation and authorization security model for low-power devices. However, the model has not been combined into limited IoT setup for authenticity including authorization and for determining different techniques that evaluate its accuracy.
11.6.1.3 Key Management
In [4], authors propose a lightweight and E2E key exchange standard. This standard is hinged on integration of various IoT security elements to develop a secure transmission path for low-power objects. The protocol ensures data confidentiality and authentication during the transmission process. However, the protocol delegates complex cryptographic procedures to third party applications. The protocol also fails to highlight tradeoff between communication cost and tally of third party applications.
Authors in [99] present a security toolbox for designing control architecture for IoT objects. The toolbox provides a fundamental base for development of various IoT engineering tools and components that address security and privacy requirements of IoT. The control framework also supports and augments inter network security management and interoperability. The imitation of their technique is that authors fail to present a roadmap on deploying security and privacy vision for objects working in dynamic environments. The other limitation is that data integrity is not warranted.
In [87], authors propose PKI-based system that entails route encryption between the source and destination and employing key value for security and decryption of data. However, the concept is only theoretical with no formal evaluation and performance analysis.
11.6.1.4 Authentication
A varied range of algorithms have been proposed overtime for enforcing authentication on IoT devices in a CloudIoT environment.
For example, in [147], the researchers proposed an augmented authentication system for IoT devices. Their work is an improvement of the work done by researchers in [114]. The approach includes three principal components: addition of backup devices for control operation against each terminal device, addition of monitor devices for tracking and monitoring terminal devices, and addition of push alarm system for generating notification and alerts for unsuccessful authentications. However, this authentication system has not been tested empirically as no significant results have been presented.
To supplement authentication in IoT, researchers in [155] designed a novel IoT authentication technique for mutual identity. Their work proposes “Asymmetric Mutual Authentication Solution” that works across platforms and sink node hinged on “Secure Hash Algorithm”, feature selection, and “Elliptic Curve Cryptography”. Though researchers assert enhanced security having minimal computational and transmission cost, the conception is only hypothetical with no experimental backing and evaluation.
The work in [107] proposes two phase certificate-based authentication protocol that permits IoT devices as well as control stations to authenticate with each other. The system allows a secure connection to be established so that data is transmitted securely via a certificate authority. The protocol takes into consideration resource constraints of sensor nodes as well as scalability, reliability and heterogeneity factor of the network. The technique dispenses complete security and authentication mechanism at application level. However, the protocol fails to provide security against node capture attacks. The authors claim that protocol should use beacon message technique to avert damage due to node capture attack.
In [91], authors present “Identity Authentication and Capability based Access Control” (IACAC) model for IoT. The model presents a combined method of authenticating and authorization for IoT sensor objects and guarantees security against network layer attacks such as DoS. The security protocol verification tool is used for evaluation. The evaluation summary is mostly encouraging. However, this model does not altogether avert DoS attacks but reduces their frequency of happening substantially by permitting one ID periodically.
Authors in [143] propose one time cipher technique for ID authentication which is based on request-reply technique. In this cipher, the two end systems who have to undergo communication agree to a pre shared matrix. A user generates key from this matrix and sends encrypted message along with key and timestamp value. The communication between two parties is validated by this time stamp value. However, application of this method is very complex in a diverse IoT environment.
In [149], authors introduce a novel authentication and access control method. The technique achieves mutual authentication connecting the sensor objects and user by establishing a session key hinged on ECC. To realize agile access control to resources of legitimate users, the technique uses Attribute-based Access Control (ABAC). However, this technique solves resource limitation of only perception layer of IoT. Also, the authors further declare that ABAC policy requires further research and studies.
The work in [89] proposes authentication as well as access control in IoT devices in order to fix flaws related to security and integrity. In their proposed work, the user requires to seek permission from the Registration Authority (RA) for accessing a device which is granted after proper authentication. The technique is however flawed because if the RA is itself compromised, the whole network gets insecure.
11.6.1.5 Trust
In [146], authors focused their attention on item-layer access control for inter-node security and proposed an architecture for mutual trust in data transaction between varied computer system in IoT. The framework maintains trust using two methods: key creation and token. The proposed framework enables devices in IoT to verify the right owner and take a decision on whether a requesting node is allowed to perform certain actions to its system. The proposed framework is however theoretical and no experimental evaluation has been done by the authors.
For securing IoT communication, authors in [134] designed an augmented ant colony protocol for deciding trust level of devices in IoT. Trust is an important factor in determining reliability, security, and privacy of data that gets communicated over the network. The prominence of a node is used for deciding the trust level of a node and is calculated depending upon advance interaction of the node with rest of devices.
11.6.1.6 Cryptography
In [142], authors carry an in-depth performance evaluation of Attribute-Based Encryption (ABE), i.e., a public key encryption technique used for preserving privacy and enables access control including key management. The authors quantify two prime categories of ABE’s, i.e., Key-Policy Attribute-Based Encryption (KP-ABE) and Ciphertext-Policy Attribute-Based Encryption (CP-ABE) on various mobile devices and laptops. The results highlight various practical issues of ABE such as requirement of computing resources in heterogeneous environment, cost benefits of ABE, and best case scenario for implementation of ABE in IoT. However, implementation of ABE on devices with limited computing power needs further investigation.
In [73], a secure mutual authentication protocol has been proposed for IoT and Cloud. The proposed protocol provides mutual authentication in addition to security. The technique employs ECC-based encryption which offers robust security in addition to being light weight with smaller key size. The protocol has been formally verified using AVISPA tool and the results are promising.
11.6.1.7 Device Security
In [11], authors propose a security approach that protects devices instead of data. The technique ensures security of devices which use RFID for communication with one another. However, this technique cannot be generalized for other wireless protocols such as Bluetooth, Zigbee which are also used in sensor communication. Also, the technique has not been evaluated empirically.
The main sensing devices at the IoT perception layer are RFID’s and tiny sensors. As already discussed, these objects have limited computational power and as such use of traditional encryption algorithms is neither feasible nor recommended.
To tackle this issue, authors in [83] present a distinct validation approach for “RFID” tags. The approach employs XOR-based cryptography instead of heavy cryptographic algorithms. The technique is not complex and warrants mutual authentication in traditional RFID system. The technique is however limited to RFID communication only.
11.6.1.8 Identity Management
In [68], the Identity Framework Management technique has been presented that attempts to resolve the problem related with data authentication and processes between the cloud platform and underlying communication devices. The system proposes having an identity manager that performs the role of authentication and forwarding of data to the service manager that guides and affirms the implementation of the service. The framework however does not mention the required protocols that will implement the proposed architecture.
11.6.1.9 Risk-Based Security/Risk Assessment
Another adaptive security approach for smart IoT proposed by authors in [7] is based on Game Theory which involves employing simulated strategies by computers to build decisions for detection and avoidance of attacks. The approach takes into consideration the reliability and risk factors associated with the attacks. The framework however needs further studies and research for development of prototype models for predicting and estimating risks.
11.6.1.10 Block Chain-Based Security
In [78], authors highlight block chain technology for dispensing security in IoT. The block chain stands for a distributed, decentralized and immutable database registry that essentially controls and secures IoT objects. The underlying technology for block chain are cryptographic encryption algorithms, digital signatures and one way has functions that guarantee data integrity and access control. The authors have highlighted various block chain characteristics which are empirical for IoT protection and security.
11.6.1.11 Automata-Based Security
In [55], the authors suggest an automata-driven intrusion alert technique for diverse IoT environment. The technique uses labeled transition extension and can th wart three types of attacks which include jamming attack, replay attack, and spoofing attacks. The intrusion detection system offers a robust mechanism for ensuring IoT network security as all the traffic originating from or leaving the network is monitored.
Table 11.5 Overview of proposed security counter measures.
| Security countermeasure | Suggested work | Advantage | Limitations | Reference |
| Authentication | Enhanced mutual authentication model of IoT | Includes three principal components: addition of backup devices for control operation against each terminal device, addition of monitor devices for tracking and monitor terminal devices, and addition of push alarm system for generating notification and alerts for unsuccessful authentications. | This authentication system has not been tested empirically as no significant results have been presented. | [147] |
| Mutual identity authentication technique | Includes feature extraction involving hash functions. Avoids Collision attacks. Lightweight Improved Security using ECC. | Concept is only hypothetical and theoretical with no experimental backing and evaluation. | [155] | |
| Two-phase certificate-based authentication protocol |
Permits authentication between IoT devices and control. Allows data transmission securely via a certificate authority. Takes into account resource constraints as well as scalability reliability and heterogeneity factor of the network. | This protocol fails to avert node capture attacks. | [107] | |
| Identity Authentication and Capabilitybased Access Control |
Uses public key technique for authentication. Congruent with lightweight communication such as 4G, 3G, and Bluetooth. Averts man-in-the-middle vulnerability by employing timestamp. | The model fails averting DoS attacks completely but reduces their frequency of happening substantially by permitting one ID periodically. | [91] | |
| One-time one cipher methodbased on request-reply mechanism for ID authentication | Dynamic variable cipher operated with the help of pre-shared matrix. Two devices transact by certifying key and Timestamp value. | Application of this method is very complex in a diverse IoT environment. | [143] | |
| Efficient authentication and access control scheme for perception layer of internet of things | The technique achieves mutual authentication between the user and sensor objects by establishing a session key hinged on ECC. Uses Attribute-based Access Control (ABAC) to realize agile access control to resources of legitimate users. |
The Attribute-based Access Control policy requires further research and studies. Solves resource limitation of only perception layer of IoT. | [149] | |
| Authentication and access control in the internet of things | Claims to solve security and Integrity issues in IoT via a central registration authority. | Technique is flawed because if the registration authority is itself compromised, the whole network gets insecure. | [89] | |
|
Architecture and Framework | Security of the Internet of Things: perspectives and challenges |
Presents security architecture for IoT. Discusses security vulnerabilities for IoT layers along with potential solutions. Highlights key enabling technologies at each layer of IoT | Fails to mention any technique for evaluating the proposed security architecture. | [72] |
| Secure IoT architecture for Smart Cities | Presents a secure IoT architecture that includes black software defined networks (SDNs) including a Key Management System. Claims to ensure confidentiality, privacy, integrity and optimal key distribution. | Architecture fails to sustain a full SDN implementation owing to limited power in IoT environment. Architecture also suffers from decreased network efficiency and complex routing. | [34] | |
| Software defined network | Present software defined network (SDN) as a potential solution to tackle the security issues in IoT. Outlines the architectural design of SDN and its suitability ad hoc networks like IoT. | Does not evaluate the performance empirically and the concept is only a theoretical one. | [16] | |
| Software defined network | Present SDN architecture for designing IoT applications that remove non-agile security setup of traditional networks. Assists administrators in containing various IoT threats and take control of the system. | Suffers from scalability and reliability. SDNs also have poor packet handling performance that leads to delays and DoS attacks. | [140] | |
| SDN-based security architecture | Propose a novel SDN architecture called SDN domain using border controllers. Interconnects heterogeneous IoT devices, augmentation of domain security and distribution of security rules. | Fails in addressing the issue of securing legitimate as well as illegitimate traffic including enterprise security. | [52] | |
| Secure access framework | A Lightweight validation and authorization security model for low-power devices. | The model has not been integrated into constrained IoT setup for authenticity and authorization and for determining different techniques that evaluate its accuracy. | [67] | |
| Key management | End-to-End secure key management protocol | Presents a lightweight and end-to-end key management standard. Ensures data confidentiality and authentication during the transmission process. | Delegates complex cryptographic procedures to third party applications. Fails to highlight tradeoff between communication cost and count of third party applications. | [4] |
| SecKit: a modelbased security toolkit |
Presents a security toolkit for designing a control framework for the IoT objects. Provides a fundamental base for development of various IoT engineering tools and components that address security and privacy requirements of IoT. Supports and augments inter domain security management and interoperability. | Fails to provide a roadmap on deploying security and privacy solutions for objects working in dynamic environments. Also data integrity is not warranted. | [99] | |
| PKI-based Protocol | Proposes PKI-based system that entails route encryption between the source and destination and employing key value for security and decryption of data. | The concept is only theoretical with no formal evaluation and performance analysis. | [87] | |
|
Trust | Item-level access control framework for inter-system security | For inter-system security, it offers item-level access control. Proposes a framework for mutual trust in data transaction among varied information system in IoT. | The proposed framework is however theoretical and no experimental evaluation has been done by the authors. | [146] |
| Trust-based privacy | An augmented ant colony procedure for deciding trust values of devices in IoT. Determines reliability, security and privacy of data that gets communicated over the network. Uses previous reputation of node | [134] | ||
| Cryptography | Performance evaluation of attribute-based encryption | Evaluates performance of Attribute-Based Encryption (ABE) for preserving privacy and enables access control including key management. Highlights practical issues of ABE such as requirement of computing resources in heterogeneous environment, cost benefits of ABE and best case scenario for implementation of ABE in IoT. | Implementation of ABE on devices with limited computing power needs further investigation | [142] |
| Secure authentication scheme | Proposes a secure mutual authentication protocol for IoT and Cloud. Employs ECC-based encryption. | [73] | ||
|
Device security | Security in the Context of Internet of Things | Proposes a security approach that protects devices instead of data. Ensures security of devices which use RFID for communication. | Technique cannot be generalized for other wireless protocols such as Bluetooth, Zigbee.Technique is not evaluated empirically. | [11] |
| Lightweight authentication protocol for internet of things | Present a distinct validation technique for “RFID” tags that employs XOR-based encryption instead of heavy cryptographic algorithms. Guarantees mutual authentication in a traditional RFID system without harboring any complexity. | Technique is however limited to RFID communication only. | [83] | |
| Identity management | Identity management framework for cloud-based internet of things |
Presents Identity Framework Management technique. Claims to resolve data authentication problem and processes between the cloud platform and underlying communication devices. | Framework does not mention the required protocols that will implement the proposed framework. | [68] |
| Risk-Based Security/Risk Assessment | Risk-based adaptive security for smart IoT | Security approach for smart is based on Game Theory. Takes into consideration the reliability and risk factors associated with the attacks. | The framework needs further studies and research for development of prototype models for predicting and estimating risks. | [7] |
| Block chain-based Security | Block Chain Review | Highlights block chain technology for dispensing security in IoT. Highlights various block chain features that are empirical for IoT security. | Block chain systems are susceptible to Security threats. Hashing power of miner can be compromised. | [78] |
| Automata-based Security | Automata-based intrusion detection method for IoT | Presents automata-driven intrusion detection for IoT. Uses labeled transition extension and can thwart three types of attacks which include jamming attack, replay attack and spoofing attacks. | Needs Standardization of protocol. Needs further empirical research. | [55] |
| Security Awareness & Survey | IoT Survey | Addresses the security challenges inherent at every IoT level having some given security countermeasures. | Includes encryption only at the perception layer. No reference to any specific evaluation framework that will evaluate the specified security measures. | [156] |
| Secure integration of IoT and cloud computing |
Present an overview of IoT and Cloud with special reference to inherent security issues. Work integrates the two technologies in order to study their common features and examine the benefits. Presents challenges associated with the amalgamation of IoT and Cloud. | No mention of other optimal lightweight cryptographic algorithms such as ECC, TEA, DESL, and LEA. | [128] | |
| Security and Privacy in Distributed IoT | Provide brief summary of security and privacy challenges with respect to IoT and Cloud. | [118] | ||
| Security Analysis of IoT | Highlights a survey of IoT security framework and analyzes its various security aspects. | [70] |
A number of solutions that focus on CloudIoT security are available in existing research; however, most of them emphasize on preserving confidentiality, integrity, privacy, and enforcing authentication. The demand for providing robust security architecture is one of the open issues in research today. Table 11.5 lists the summary of various security counter measures.
11.6.2 Security Considerations
Given the fact that collaboration of IoT and Cloud, i.e., two varied technological platforms will outpour security issues considerably, thus impregnable defense policies are required for averting threats [22, 23].
While designing the security for CloudIoT platform, the security of entire whole system should be taken into consideration [109]. The security setup however cannot be built by simply deploying solutions at each layer of the architecture together. Different CloudIoT applications such as smart home, traffic management, and intelligent healthcare entail for diverse heterogeneous security solutions [25, 65]. For example, for intelligent traffic management and smart healthcare, data privacy is of utmost importance [66]. However, for applications such as smart city and smart environment monitoring, data authenticity needs to be ensured [24]. This implies that every applications demands different level of security to be enforced. Applying security at only one level will not cater to the security requirements at other levels. For example, if a system has weak security applied at the application level, no matter how much strong security we implement at the lower levels (such as perception level); the system would still be insecure. Thus, we need to design a system that provides cross layer security and helps integrate the system as one entity [111]. The security systems should be designed keeping cross layer heterogeneous integration in mind [69, 121].
The security framework should also take into consideration security challenges in IoT as well as those inherent in Cloud platform [22, 97]. As an example, in order to avoid illegal access to a sensor node, strong authentication measures should be put into place. Also, strong cryptographic encryption should be practiced to guarantee data confidentiality. To ensure this, advanced encryption algorithms such as ECC should be practiced. This should be coupled with efficient key exchange policies [124]. As IoT sensor nodes are driven by batteries, thus to maximize their working time period, efficient power utilization mechanism like programmed sleep procedures should be executed so that nodes do not drain the limited battery power. Additionally, other renewable sources of power generation for IoT such as solar energy should be harnessed. Table 11.6 lists the various energy drainage factors of sensor nodes along with their potential solutions. To check for physical damage to sensor objects, it is recommended that periodic watch and monitoring needs to be implemented at remote deployed site. To prevent network-based attacks like DoS and DDoS, the optimal policy could be firewall implementation and access methods. The security at the network layer can be viewed from two perspectives: wireless and wired security. To ensure security via both communication mediums, development of authentication protocols and key management is one of the essential components. Protocols such as SSL/TLS need to be employed to encrypt the communication link. Additionally, for IP security, IPsec-enabled communication needs to be practiced. This will ensure that data authenticity, confidentiality and integrity are maintained at each layer. Before establishing a new network, guest access and default passwords should be disabled and cleared immediately in routers and gateways. Ensuring periodic password changes, applying strong passwords with alphanumeric characters and numbers should be practiced. For mitigating replay attacks, synchronized timestamp techniques should be practiced. In general, it is recommended that cryptographic algorithms that dispense E2E security need to be implemented. It would ensure that data authenticity, integrity and genuineness is maintained [124]. To protect security threats at the Application layer, the mitigation policy would be writing secure programming algorithm and implement malicious script identification procedures. For sanitizing vulnerable scripts, code rewrite techniques should be implemented.
Table 11.6 Node energy drainage factors and solutions.
| Energy drainage factor | Description | Potential solutions |
| Idle Listening | Node listening to an idle channel in order to receive possible traffic (data) | Nodes should implement energy saving procedures and programmed sleep routines. |
| Packet collision | Node receives more than one packet at the same time lead to packet discarding or retransmission |
Packet Firewall and Filtering mechanism should be implemented. Node Input should be throttled. |
| Overhearing | Node receives packets that are destined to other nodes | Efficient packet addressing needs to be done. Packet encryption for ensuring privacy of data. |
| Control packet overhead | A minimal number of control packets should be used to make a data transmission | Periodic transmission of data packets. Longer time interval between packet transmissions. |
| Over-emitting | A message is transmitted when the destination node is not ready | Handshaking and acknowledge mechanism between nodes should be implemented. Use of Sync packets before transmission is recommended |
To secure data at the cloud platform, client access should be authenticated and authorized with no room for illegitimate access. The fundamental step toward this is to ascertain that only legitimate users get access to critical information perceived by sensor objects. The entails demand for defining the required physical identity and platform access policies. Any client nodes trying to access cloud should first identity and authenticate itself with the platform. Once authenticated, access may be given; however, the access may be restricted depending upon the user and mode of operation desired. Since cloud offers pervasive access to the users, the security professionals need to implement concurrency control measures so that data is not corrupted and redundancy operations could be avoided. Also, to ensure data security, approaches like multimedia compression, image stenography and compression, water marking, cryptography, and session timers should be practiced [123].
To track cybercrimes aimed at CloudIoT platform, the efficient solution would be to log every action on the cloud platform. This logged record can be checked in future to detect for any anomaly. Logging also enables the cyber forensic investigators to check and ascertain which operation went wrong so that it can be rectified. The Cloud as well as IoT are two completely different heterogeneous interfaces, and thus, to dispense optimal level of security is a daunting job for security researchers.
11.7 Open Research Issues and Security Challenges
It is an established fact that CloudIoT dispenses convenience and user comfort in our everyday life; however, majority of CloudIoT working components such as low-cost sensor and communication chips are designed without considering security [72, 97]. If successful malicious attack is executed successfully, then the CloudIoT system would lie insecure with loss of private sensitive information and critical damage to the infrastructure. The problem becomes more convoluted with the integration of IoT and Cloud platforms [63].
The CloudIoT security involves security of the entire system rather than the security of single individual layer or cloud. The CloudIoT treats entire system as an integrated framework for a cross platform security solution. To secure CloudIoT systems, heterogeneous security architectures need to be designed to allow blending of varied data generated from disparate sources [62, 63].
The CloudIoT platform has witnessed exponential surge nowadays in the areas such as healthcare monitoring, telemedicine, environment surveillance, and pollution control. Some researchers are also of the opinion that connected things will surge near to 26 billion by the year 2020 [84]. However, its security challenges and issues must be addressed to facilitate its unbounded growth. Listed below are some of the open areas for research that aim to make the platform robust and secure.
11.7.1 Security Architecture
The CloudIoT integrates varied objects, platforms and standards to realize certain goals. However, to fuse smaller micro frameworks for designing a larger framework entails for following well defined standards. The CloudIoT security framework demands data models and standard security protocols that underpin diverse range of devices, platforms and operating systems [76].
As CloudIoT security threats vary from application to application, so are their specific solutions. Different applications demand diverse solutions and security requirements. Thus, single security framework cannot provide solution to all application contexts [78]. However, what is required is to design an abstract security architecture that features similarities among the applications till a concrete security model comes up. This model hides the differences between different applications and offers an interface that highlights similarities.
11.7.2 Resource Constraints
The constrained power of sensor devices are the major bottlenecks in designing a vibrant and powerful security system for CloudIoT [109]. In contrast to traditional security systems, the cryptographic and encryption systems need to scale down and work with minimal features for working under these limitations. In addition to this, resource limitation also causes minimal broadcast or multicast of keys and certificates, access control and authentication as well as intelligent communication and storage of data that consumes less power.
However, this demands revamping of existing protocols and employing light weight cryptographic encryption algorithms such as ECC. The focus should also be on exploring and harvesting alternate energy sources such as solar power [74]. The applications computational and security requirements can also be broken down into several levels. Each level runs a different set of algorithms which have different energy requirements. In this way, some levels would consume less power while some need to be optimized.
11.7.3 Heterogeneous Data and Devices
The CloudIoT systems generate humongous volumes of data also known as big data. Research should focus on developing ways and techniques for efficiently handling this massive data volume [45]. Also, secure protocols and algorithms need to be developed that can effectively protect this data and comprehensive security solution is put into place. Also, multilayer and cross platform security framework needs to be employed for heterogeneous devices ranging from low-power sensors to high-end server systems. The security framework should be dynamic and should adapt itself to the existing resources.
11.7.4 Protocol Interoperability
To develop a global standard security framework for CloudIoT, the protocols functioning at various layers of IoT as well as Cloud need to interoperate and communicate with each other [115]. This entails designing conversion routines and dialog controllers. However, the interoperability design should take into consideration the architectural limitations and constraints. With heterogeneous networks such as CloudIoT, the security framework becomes vulnerable to a single point of failure [12]. Most of the data in the network gets transacted through a central controller node. If that node is compromised, then the security of entire network is at stake. It is thus required to introduce some amount of redundancy in the network while maintaining and balancing reliability and cost.
11.7.5 Trust Management and Governance
The level of compatibility in the network and flexible expansion capacity of a sensor device helps it to decide other trustworthy nodes in the network. This decision can be quite challenging because it is arduous to distinguish between a genuine and a rogue node in a pervasive and wireless environment such as CloudIoT. The IoT device must also not reveal identity to adversary that could prove fatal to the system. What is required is a robust and pliable authorization mechanism that performs identity management and grants access to the legitimate devices in the network. However, the identity management should be properly encrypted because the process is susceptible to interception by malicious users which can leverage man-in-the-middle attack and imperil entire CloudIoT architecture [9].
The actual security and control of the CloudIoT network is determined by the degree of governance. The security of the network and level of governance are directly proportional. If more control and monitoring mechanisms can be employed, then the network would become more secure. This implies that if every data transaction in the network is monitored, then any malicious activity would get easily detected and tracked. However, the amount of monitoring and surveillance should be balanced as it should not amount to the level of nuisance and uneasiness for user’s privacy.
11.7.6 Fault Tolerance
The CloudIoT systems and objects should possess a certain degree of fault tolerance and self-repairing ability. These defense mechanisms should allow the device to recover from any possible damage on its own if the threat is not so severe. Different options are available for a device; for example, one way would be to report in case of intrusion to the central controller node or backend server. Another approach could be to lock sensitive operations and shutdown the entire system. However, there has to be a balance so that normal working of the node is not hampered. The decision depends upon the conditions and level of severity of the threat. In some other scenarios, complex approaches may be required.
11.7.7 Next-Generation 5G Protocol
For fully exploiting the potential of CloudIoT platform, Ipv4 will shortfall and lack behind in assigning IP address to each and every connected device. This is the prime reason for the genesis of Ipv6 which has 3.4 x 1038 addresses; enough to cater every connected device on earth. However, such a large address space and connected devices will generate large volumes of data that can draw network congestion and delay. Also, substantial bandwidth is required to support seamless access to internet for connected devices. The new generation communication protocol, i.e., 5G is expected to provide speeds of up to 800 Gbps. When compared with 4G which offers speed up to 1,000 Mbps, 5G is expected to efficiently manage traffic generated by connected devices in CloudIoT network. The 5G network is also expected to facilitate Ipv4 to Ipv6 migration by implementing inherent framework translation. The 5G security and implementation is one of the hot areas of research today and must be extensively studied [109]. The adoption of 5G network will completely realize the concept of CloudIoT.
11.8 Discussion and Analysis
Amalgamation of two diverse technology frameworks demands interconnectivity and transaction of data among heterogeneous networks. These heterogeneous networks need to be flexible and unrestricted and should support divergent data and services [39].
The security architecture of CloudIoT framework may be augmented by “privacy by design” method in which holistic view of security and privacy concerns of the entire system is addressed at the design and implementation time. To design security framework, enhanced security protocols, cryptographic methods, and algorithms should be employed which take into consideration constrained computing resources of connected devices [21].
The security architecture should also provide solution to the issue of fault tolerance and hardware failure which is quite common in these devices [109]. The CloudIoT security framework should feature detection of spurious and compromised data including protection of data identity [3].
The devices in CloudIoT network produce exponential data that need to be managed, processed and transmitted [12]. In an optimal system, the management of data is primarily handled by the Cloud platform. Thus, the security of this generated data depends upon the security framework implemented in the Cloud platform by the service providers. The security of data on the Cloud platform depends upon the secure allocation/re-allocation of resources from one virtual machine to another and safeguarding the virtualization process. The security of data on Cloud platform is often compromised by malevolent traffic exchanged between the virtual machines. This is usually avoided by monitoring the traffic and installing firewall systems between the virtual machines. Another approach is to separate and isolate varied virtual machine classes from one another. In addition to these, the attacks on CloudIoT platform may be launched by hostile users who upload malicious data with the intension of performing illegal operations. These threats are usually averted by anomaly detection systems that can distinguish between normal and abnormal behavior.
Thus, enforcing security and privacy on the platform is of supreme importance. This requires implementing cryptographic encryptions that abstract and authenticate communication data. Also, unauthorized access to the platform must be restricted. Ensuring robust security and reliability will be a major success factor in adopting and deployment of this technology.
The efficient solution could also be a tangible and robust security system that will encapsulate and abstract user information and safeguard confidentiality [94]. Such systems in particular, for delay-sensitive services like healthcare also entail for designing minimal energy gobbling efficient devices. Though number of power-saving architecture have been designed over a period of time, majority of them handle operation of IoT and Cloud asynchronously. Designing power efficient and reliable CloudIoT architecture can ameliorate sensor operational time which, in turn, can improve functionality of operational devices. To vanquish delay sensitivity and power utilization, operation of Fog computing technology significantly minimizes the data flow on cloud and additionally offers localized storage for IoT [3, 95]. As privacy issues are involved in healthcare data, the regional bindings and guidelines do not allow these to be transacted beyond the framework of healthcare application portals. Thus, Fog-based computation proves to be a flawless solution as it drives the complexity and processing nearer to the healthcare service providers [3, 97]. This leads to minimal latency, lower power consumption, data security, and privacy as well as ideal bandwidth consumption.
The CloudIoT involves amalgamation of disparate heterogeneous networks which raise certain compatibility issues. However, it is expected that by efficient key management and implementing routing protocols, the incompatibilities will be negated.
11.9 Conclusion
The evolutionary growth of CloudIoT platform has become the intrinsic factor for developing robust and organized healthcare applications that influence our daily life. The adoption of CloudIoT in healthcare is influenced by demand for robust processing architectures, humongous data storage, high performance networks, and resource availability. The Cloud platform also seems to be a panacea for several limitations such as resource constraints immanent within the IoT network. A wide majority of healthcare research literature has discussed the role of Cloud and IoT separately, highlighting their architecture and applications; however, shortfall from comprehensive and elaborate security issue examination. To bridge this gap, this chapter reviews CloudIoT literature and presents an overall insight on CloudIoT-driven healthcare services. In this chapter, we presented a brief background highlighting composition of CloudIoT platform and its enabling technologies. We also introduced a conceptual architecture for healthcare monitoring system which included a use case scenario depicting the actual data flow in a smart healthcare system. The chapter also tried to highlight various security vulnerabilities affecting IoT and cloud platform. These vulnerabilities demand efficient security architectures so that user data privacy is maintained. We also made an attempt to underline some open research issues and security challenges that can further motivate our research in this domain.
References
1. Aazam, M. and Huh, E.N., Fog computing and smart gateway based communication for cloud of things, in: 2014 International Conference on Future Internet of Things and Cloud, 2014, August, IEEE, pp. 464–470.
2. Aazam, M. and Huh, E.N., Fog computing: The cloud-iot/ioe middleware paradigm. IEEE Potentials, 35, 3, 40–44, 2016.
3. Aazam, M., Huh, E.N., St-Hilaire, M., Lung, C.H., Lambadaris, I., Cloud of things: integration of IoT with cloud computing, in: Robots and Sensor Clouds, pp. 77–94, Springer, Cham, 2016.
4. Abdmeziem, M.R. and Tandjaoui, D., An end-to-end secure key management protocol for e-health applications. Comput. Electr. Eng., 44, 184–197, 2015.
5. AbdulGhaffar, A., Mostafa, S.M., Alsaleh, A., Sheltami, T., Shakshuki, E.M., Internet of things based multiple disease monitoring and health improvement system. J. Ambient Intell. Hum. Comput., 11, 3, 1021–1029, 2020.
6. Abduvaliyev, A., Pathan, A.S.K., Zhou, J., Roman, R., Wong, W.C., On the vital areas of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutorials, 15, 3, 1223–1237, 2013.
7. Abie, H. and Balasingham, I., Risk-based adaptive security for smart IoT in eHealth, in: Proceedings of the 7th International Conference on Body Area Networks, pp. 269–275, 2012, February.
8. Abomhara, M. and Koien, G.M., Security and privacy in the Internet of Things: Current status and open issues, in: 2014 international conference on privacy and security in mobile systems (PRISMS), IEEE, pp. 1–8, 2014 May.
9. Aceto, G., Persico, V., Pescapé, A., Industry 4.0 and Health: Internet of Things, Big Data, and Cloud Computing for Healthcare 4.0. J. Ind. Inf. Integr., 18, 100129, 2020.
10. Adhikary, T., Jana, A.D., Chakrabarty, A., Jana, S.K., The Internet of Things (IoT) Augmentation in Healthcare: An Application Analytics, in: International Conference on Intelligent Computing and Communication Technologies, Springer, Singapore, pp. 576–583, 2019, January.
11. Aggarwal, R. and Das, M.L., RFID Security in the Context of” Internet of Things, in: Proceedings of the First International Conference on Security of Internet of Things, pp. 51–56, 2012, August.
12. Ahemd, M.M., Shah, M.A., Wahid, A., IoT security: A layered approach for attacks & defenses, in: 2017 International Conference on Communication Technologies (ComTech), IEEE, pp. 104–110, 2017, April.
13. Ahmed, M.U., Banaee, H., Rafael-Palou, X., Loutfi, A., Intelligent healthcare services to support health monitoring of elderly, in: International Internet of Things Summit, Springer, Cham, pp. 178–186, 2014, October.
14. Ahmed, M.U., Björkman, M., Causevic, A., Fotouhi, H., Lindén, M., An overview on the internet of things for health monitoring systems, in: International Internet of Things Summit, Springer, Cham, pp. 429–436, 2015, October.
15. Akhunzada, A., Gani, A., Anuar, N.B., Abdelaziz, A., Khan, M.K., Hayat, A., Khan, S.U., Secure and dependable software defined networks. J. Netw. Comput. Appl., 61, 199–221, 2016.
16. Al Shuhaimi, F., Jose, M., Singh, A.V., Software defined network as solution to overcome security challenges in IoT, in: 2016 5th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions)(ICRITO), IEEE, pp. 491–496, 2016, September.
17. Alaba, F.A., Othman, M., Hashem, I.A.T., Alotaibi, F., Internet of Things security: A survey. J. Netw. Comput. Appl., 88, 10–28, 2017.
18. Alampalayam, S. and Kumar, A., An adaptive and predictive security model for mobile ad hoc networks. Wirel. Pers. Commun., 29, 3–4, 263–281, 2004.
19. Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., Ayyash, M., Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutorials, 17, 4, 2347–2376, 2015.
20. Al-Hayajneh, A., Bhuiyan, Z.A., McAndrew, I., Improving Internet of Things (IoT) Security with Software-Defined Networking (SDN). Computers, 9, 1, 8, 2020.
21. Alohali, B.A., Vassilakis, V.G., Moscholios, I.D., Logothetis, M.D., A secure scheme for group communication of wireless IoT devices, in: 2018 11th International Symposium on Communication Systems, Networks & Digital Signal Processing (CSNDSP), IEEE, pp. 1–6 2018, July,.
22. Alsaidi, A. and Kausar, F., Security attacks and countermeasures on cloud assisted IoT applications, in: 2018 IEEE International Conference on Smart Cloud (SmartCloud), IEEE, pp. 213–217, 2018, September.
23. Andrea, I., Chrysostomou, C., Hadjichristofi, G., Internet of Things: Security vulnerabilities and challenges, in: 2015 IEEE Symposium on Computers and Communication (ISCC), IEEE, pp. 180–187, 2015, July.
24. Ansari, S., Aslam, T., Poncela, J., Otero, P, Ansari, A., Internet of Things-Based Healthcare Applications, in: IoT Architectures, Models, and Platforms for Smart City Applications, USA, pp. 1–28, IGI Global, 2020.
25. Atlam, H.F., Hemdan, E.E.D., Alenezi, A., Alassafi, M.O., Wills, G.B., Internet of Things Forensics: A Review. Internet Things, 11, 100220, 2020.
26. Azimi, I., Rahmani, A.M., Liljeberg, P, Tenhunen, H., Internet of things for remote elderly monitoring: a study from user-centered perspective. J. Ambient Intell. Hum. Comput., 8, 2, 273–289, 2017.
27. Basanta, H., Huang, Y.P, Lee, T.T., Intuitive IoT-based H2U healthcare system for elderly people, in: 2016 IEEE 13th International Conference on Networking, Sensing, and Control (ICNSC), IEEE, pp. 1–6, 2016, April.
28. Bonomi, F., Milito, R., Zhu, J., Addepalli, S., Fog computing and its role in the internet of things, in: Proceedings of the first edition of the MCC workshop on Mobile cloud computing, ACM, pp. 13–16, 2012, August.
29. Bormann, C., Castellani, A.P, Shelby, Z., Coap: An application protocol for billions of tiny internet nodes. IEEE Internet Comput., 16, 2, 62–67, 2012.
30. Botta, A., De Donato, W, Persico, V., Pescapé, A., Integration of cloud computing and internet of things: a survey. Future Gener. Comput. Syst., 56, 684700, 2016.
31. Bui, N. and Zorzi, M., Healthcare applications: a solution based on the internet of things, in: Proceedings of the 4th international symposium on applied sciences in biomedical and communication technologies, ACM, p. 131, 2011, October.
32. Capkun, S., Buttyán, L., Hubaux, J.P, Self-organized public-key management for mobile ad hoc networks. IEEE Trans. Mob. Comput., 1, 52–64, 2003.
33. Catarinucci, L., De Donno, D., Mainetti, L., Palano, L., Patrono, L., Stefanizzi, M.L., Tarricone, L., An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J., 2, 6, 515–526, 2015.
34. Chakrabarty, S. and Engels, D.W., A secure IoT architecture for Smart Cities, in: 2016 13th IEEE annual consumer communications & networking conference (CCNC), IEEE, pp. 812–813, 2016, January.
35. Chen, S., Xu, H., Liu, D., Hu, B., Wang, H., A vision of IoT: Applications, challenges, and opportunities with china perspective. IEEE Internet Things J., 1, 4, 349–359, 2014.
36. Cheng, Y., Jiang, C., Shi, J., A Fall detection system based on SensorTag and Windows 10 IoT core, in: 2015 International Conference on Mechanical Science and Engineering, Atlantis Press, 2016, March.
37. Cirani, S., Ferrari, G., Veltri, L., Enforcing security mechanisms in the IP-based internet of things: An algorithmic overview. Algorithms, 6, 2, 197226, 2013.
38. Colakovic, A. and Hadzialic, M., Internet of Things (IoT): A review of enabling technologies, challenges, and open research issues. Comput. Networks, 144, 17–39, 2018.
39. Cook, A., Robinson, M., Ferrag, M.A., Maglaras, L.A., He, Y., Jones, K., Janicke, H., Internet of cloud: Security and privacy issues, in: Cloud Computing for Optimization: Foundations, Applications, and Challenges, pp. 271–301, Springer, Cham, 2018.
40. Dang, L.M., Piran, M., Han, D., Min, K., Moon, H., A survey on internet of things and cloud computing for healthcare. Electronics, 8, 7, 768, 2019.
41. Darshan, K.R. and Anandakumar, K.R., A comprehensive review on usage of Internet of Things (IoT) in healthcare system, in: 2015 International Conference on Emerging Research in Electronics, Computer Science and Technology (ICERECT), IEEE, pp. 132–136, 2015, December.
42. Darwish, A., Hassanien, A.E., Elhoseny, M., Sangaiah, A.K., Muhammad, K., The impact of the hybrid platform of internet of things and cloud computing on healthcare systems: Opportunities, challenges, and open problems. J. Ambient Intell. Hum. Comput., 10, 1–16, 2017.
43. Datta, S.K., Bonnet, C., Gyrard, A., Da Costa, R.P.F., Boudaoud, K., Applying Internet of Things for personalized healthcare in smart homes, in: 2015 24th Wireless and Optical Communication Conference (WOCC), IEEE, pp. 164169, 2015, October.
44. De Capua, C., Meduri, A., Morello, R., A smart ECG measurement system based on web-service-oriented architecture for telemedicine applications. IEEE Trans. Instrum. Meas., 59, 10, 2530–2538, 2010.
45. Dhanvijay, M.M. and Patil, S.C., Internet of Things: A survey of enabling technologies in healthcare and its applications, Computer Networks, Amsterdam, The Netherlands, 2019.
46. Dhillon, P.K. and Kalra, S., Multi-factor user authentication scheme for IoT-based healthcare services. J. Reliab. Intell. Environ., 4, 3, 141–160, 2018.
47. Díaz, M., Martín, C., Rubio, B., State-of-the-art, challenges, and open issues in the integration of Internet of things and cloud computing. J. Netw. Comput. Appl., 67, 99–117, 2016.
48. Dierckx, R., Pellicori, P., Cleland, J.G.F., Clark, A.L., Telemonitoring in heart failure: Big Brother watching over you. Heart Fail. Rev., 20, 1, 107–116, 2015.
49. Din, I.U., Almogren, A., Guizani, M., Zuair, M., A decade of Internet of Things: Analysis in the light of healthcare applications. IEEE Access, 7, 89967–89979, 2019.
50. Distefano, S., Merlino, G., Puliafito, A., Enabling the cloud of things, in: 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, IEEE, pp. 858–863, 2012, July.
51. Fanucci, L., Saponara, S., Bacchillone, T., Donati, M., Barba, P., Sánchez-Tato, I., Carmona, C., Sensing devices and sensor signal processing for remote monitoring of vital signs in CHF patients. IEEE Trans. Instrum. Meas., 62, 3, 553–569, 2012.
52. Flauzac, O., Gonzalez Santamaría, C.J., Nolot, F., New security architecture for IoT network, Procedia Computer Science, Elsevier, 52, 1028–1033, 2015.
53. Fortino, G., Parisi, D., Pirrone, V., Di Fatta, G., BodyCloud: A SaaS approach for community body sensor networks. Future Gener. Comput. Syst., 35, 62-79, 2014.
54. Fox, A., Griffith, R., Joseph, A., Katz, R., Konwinski, A., Lee, G., Stoica, I., Above the clouds: A berkeley view of cloud computing. Dept. Electrical Eng. and Comput. Sciences, University of California, Berkeley, Rep. UCB/EECS, 28(13), Technical Report No is UCB/EECS-2009-28. 2017, 1–13, February 10, 2009.
55. Fu, Y., Yan, Z., Cao, J., Koné, O., Cao, X., An automata based intrusion detection method for internet of things. Mob. Inf. Syst., 2017, pp. 1–13, 2017.
56. Gasparrini, S., Cippitelli, E., Spinsante, S., Gambi, E., A depth-based fall detection system using a Kinect® sensor. Sensors, 14, 2, 2756–2775, 2014.
57. Granjal, J., Monteiro, E., Silva, J.S., Security for the internet of things: a survey of existing protocols and open research issues. IEEE Commun. Surv. Tutorials, 17, 3, 1294–1312, 2015.
58. Grobauer, B., Walloschek, T., Stocker, E., Understanding cloud computing vulnerabilities. IEEE Secur. Privacy, 9, 2, 50–57, 2010.
59. Gubbi, J., Buyya, R., Marusic, S., Palaniswami, M., Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst., 29, 7, 1645–1660, 2013.
60. Gund, A., Ekman, I., Lindecrantz, K., Sjoqvist, B.A., Staaf, E.L., Thorneskold, N., Design evaluation of a home-based telecare system for chronic heart failure patients, in: 2008 30th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, IEEE, pp. 5851–5854, 2008, August.
61. Guo, J., Chen, R., Tsai, J.J., A survey of trust computation models for service management in internet of things systems. Comput. Commun., 97, 1–14, 2017.
62. Gupta, P., Agrawal, D., Chhabra, J., Dhir, P.K., IoT based smart healthcare kit, in: 2016 International Conference on Computational Techniques in Information and Communication Technologies (ICCTICT), IEEE, pp. 237242,2016, March.
63. Hamad, S.A., Sheng, Q.Z., Zhang, W.E., Nepal, S., Realizing an Internet of Secure Things: A Survey on Issues and Enabling Technologies. IEEE Commun. Surv. Tutorials, 22, 2, 1372–1391, 2020.
64. Harper, S., Ageing Societies: Myths, in: Challenges and Opportunities, p. 116, 2006.
65. Hassan, Q.F. (Ed.), Internet of Things A to Z: technologies and applications, John Wiley & Sons, New Jersey, USA, 2018.
66. He, D., Ye, R., Chan, S., Guizani, M., Xu, Y., Privacy in the Internet of Things for smart healthcare. IEEE Commun. Mag., 56, 4, 38–44, 2018.
67. Hernández-Ramos, J.L., Moreno, M.V., Bernabé, J.B., Carrillo, D.G., Skarmeta, A.F., SAFIR: Secure access framework for IoT-enabled services on smart buildings. J. Comput. Syst. Sci., 81, 8, 1452–1463, 2015.
68. Horrow, S. and Sardana, A., Identity management framework for cloud based internet of things, in: Proceedings of the First International Conference on Security of Internet of Things, pp. 200–203, 2012, August.
69. Hosenkhan, M.R. and Pattanayak, B.K., Security Issues in Internet of Things (IoT): A Comprehensive Review, in: New Paradigm in Decision Science and Management, pp. 359–369, Springer, Singapore, 2020.
70. Hossain, M.M., Fotouhi, M., Hasan, R., Towards an analysis of security issues, challenges, and open problems in the internet of things, in: 2015 IEEE World Congress on Services, IEEE, pp. 21–28, 2015, June.
71. Jimenez, F. and Torres, R., Building an IoT-aware healthcare monitoring system, in: 2015 34th International Conference of the Chilean Computer Science Society (SCCC), IEEE, pp. 1–4, 2015, November.
72. Jing, Q., Vasilakos, A.V, Wan, J., Lu, J., Qiu, D., Security of the Internet of Things: perspectives and challenges. Wirel. Netw., 20, 8, 2481–2501, 2014.
73. Kalra, S. and Sood, S.K., Secure authentication scheme for IoT and cloud servers. Pervasive Mob. Comput., 24, 210–223, 2015.
74. Kamalinejad, P., Mahapatra, C., Sheng, Z., Mirabbasi, S., Leung, V.C., Guan, Y.L., Wireless energy harvesting for the Internet of Things. IEEE Commun. Mag., 53, 6, 102–108, 2015.
75. Kanuparthi, A., Karri, R., Addepalli, S., Hardware and embedded security in the context of internet of things, in: Proceedings of the 2013 ACM workshop on Security, privacy & dependability for cyber vehicles, pp. 61–64, 2013, November.
76. Karmakar, K.K., Varadharajan, V., Nepal, S., Tupakula, U., SDN Enabled Secure IoT Architecture, in: 2019 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), IEEE, pp. 581–585, 2019, April.
77. Karthikeyan, S., Devi, K.V., Valarmathi, K., Internet of Things: Hospice appliances monitoring and control system, in: 2015 Online International Conference on Green Engineering and Technologies (IC-GET), IEEE, pp. 1–6, 2015, November).
78. Khan, M.A. and Salah, K., IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst., 82, 395–411, 2018.
79. Khursheeed, F., Sami-Ud-Din, M., Sumra, I.A., Safder, M., A Review of Security Machanism in internet of Things (IoT), in: 2020 3rd International Conference on Advancements in Computational Sciences (ICACS), IEEE, pp. 1–9, 2020, February.
80. Kim, D.H., Ghaffari, R., Lu, N., Rogers, J.A., Flexible and stretchable electronics for biointegrated devices. Annu. Rev. Biomed. Eng., 14, 113–128, 2012.
81. Kovatsch, M., Mayer, S., Ostermaier, B., Moving application logic from the firmware to the cloud: Towards the thin server architecture for the internet of things, in: 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, IEEE, pp. 751–756, 2012, July.
82. Krishnan, D. and Mallya, A., A Survey on Security Attacks in Internet of Things and Challenges in Existing Countermeasures, in: Proceedings of International Conference on Wireless Communication, Springer, Singapore, pp. 463–469, 2020.
83. Lee, J.Y., Lin, W.C., Huang, Y.H., A lightweight authentication protocol for internet of things, in: 2014 International Symposium on Next-Generation Electronics (ISNE), IEEE, pp. 1–2, 2014, May.
84. Leo, M., Battisti, F., Carli, M., Neri, A., A federated architecture approach for Internet of Things security, in: 2014 Euro Med Telco Conference (EMTC), IEEE, pp. 1–5, 2014, November.
85. Li, N. and Mahalik, N.P., A big data and cloud computing specification, standards and architecture: agricultural and food informatics. Int. J. Inf. Commun. Technol., 14, 2, 159–174, 2019.
86. Li, S., Da Xu, L., Zhao, S., The internet of things: a survey. Inform. Syst. Front., 17, 2, 243–259, 2015.
87. Li, Z., Yin, X., Geng, Z., Zhang, H., Li, P., Sun, Y., Li, L., Research on PKI-like Protocol for the Internet of Things, in: 2013 Fifth International Conference on Measuring Technology and Mechatronics Automation, IEEE, pp. 915–918, 2013, January.
88. Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H., Zhao, W., A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J., 4, 5, 1125–1142, 2017.
89. Liu, J., Xiao, Y., Chen, C.P., Authentication and access control in the internet of things, in: 2012 32nd International Conference on Distributed Computing Systems Workshops, IEEE, pp. 588–592, 2012, June.
90. Liu, W., Zhao, X., Xiao, J., Wu, Y., Automatic vehicle classification instrument based on multiple sensor information fusion, in: Third International Conference on Information Technology and Applications (ICITA’05), vol. 1, IEEE, pp. 379–382, 2005, July.
91. Mahalle, P.N., Anggorojati, B., Prasad, N.R., Prasad, R., Identity authentication and capability based access control (iacac) for the internet of things. J. Cyber Secur. Mobil., 1, 4, 309–348, 2013.
92. Mell, P. and Grance, T., The NIST definition of cloud computing, Computer Security Division, Information Technology Laboratory, National Institute of Standards and Technology, Gaithersburg, USA, 2011.
93. Mo, Y. and Sinopoli, B., Secure control against replay attacks, in: 2009 47th annual Allerton conference on communication, control, and computing (Allerton), IEEE, pp. 911–918, 2009, September.
94. Moosavi, S.R., Gia, T.N., Nigussie, E., Rahmani, A.M., Virtanen, S., Tenhunen, H., Isoaho, J., End-to-end security scheme for mobility enabled healthcare Internet of Things. Future Gener. Comput. Syst., 64, 108–124, 2016.
95. Mutlag, A.A., Ghani, M.K.A., Arunkumar, N.A., Mohamed, M.A., Mohd, O., Enabling technologies for fog computing in healthcare IoT systems. Future Gener. Comput. Syst., 90, 62–78, 2019.
96. Namahoot, C.S., Brückner, M., Nuntawong, C., Mobile Diagnosis System with Emergency Telecare in Thailand (MOD-SET). Proc. Comput. Sci., 69, 86–95, 2015.
97. Nawir, M., Amir, A., Yaakob, N., Lynn, O.B., Internet of Things (IoT): Taxonomy of security attacks, in: 2016 3rd International Conference on Electronic Design (ICED), IEEE, pp. 321–326, 2016, August.
98. Neagu, G., Preda, §., Stanciu, A., Florian, V., A Cloud-IoT based sensing service for health monitoring, in: 2017 E-Health and Bioengineering Conference (EHB), IEEE, pp. 53–56, 2017, June.
99. Neisse, R., Steri, G., Fovino, I.N., Baldini, G., SecKit: a model-based security toolkit for the internet of things. Comput. Secur., 54, 60–76, 2015.
100. Oleshchuk, V., Internet of things and privacy preserving technologies, in: 2009 1st International Conference on Wireless Communication, Vehicular Technology, Information Theory and Aerospace & Electronic Systems Technology, IEEE, pp. 336–340, 2009, May.
101. Olorode, O. and Nourani, M., Reducing leakage power in wearable medical devices using memory nap controller, in: 2014 IEEE Dallas Circuits and Systems Conference (DCAS), IEEE, pp. 1–4, 2014, October.
102. Panchatcharam, P. and Vivekanandan, S., Internet of things (IoT) in healthcare-smart health and surveillance, architectures, security analysis and data transfer: a review. Int. J. Software Innov. (IJSI), 7, 2, 21–40, 2019.
103. Park, C., Chou, P.H., Bai, Y., Matthews, R., Hibbs, A., An ultra-wearable, wireless, low power ECG monitoring system, in: 2006 IEEE biomedical circuits and systems conference, IEEE, pp. 241–244, 2006, November.
104. Parwekar, P., From internet of things towards cloud of things, in: 2011 2nd International Conference on Computer and Communication Technology (ICCCT-2011), IEEE, pp. 329–333, 2011, September.
105. Patel, C. and Doshi, N., Internet of Things: A Review on Major Challenges and Applications, in: Reliability and Risk Assessment in Engineering, pp. 427437, Springer, Singapore, 2020.
106. Pollonini, L., Rajan, N.O., Xu, S., Madala, S., Dacso, C.C., A novel handheld device for use in remote patient monitoring of heart failure patients—Design and preliminary validation on healthy subjects. J. Med. Syst., 36, 2, 653–659, 2012.
107. Porambage, P., Schmitt, C., Kumar, P., Gurtov, A., Ylianttila, M., Two-phase authentication protocol for wireless sensor networks in distributed IoT applications, in: 2014 IEEE Wireless Communications and Networking Conference (WCNC), Ieee, pp. 2728–2733, 2014, April.
108. Qadri, Y.A., Nauman, A., Zikria, Y.B., Vasilakos, A.V., Kim, S.W., The Future of Healthcare Internet of Things: A Survey of Emerging Technologies. IEEE Commun. Surv. Tutorials, 22, 2, 1121–1167 2020.
109. Rahimi, H., Zibaeenejad, A., Rajabzadeh, P., Safavi, A.A., on the Security of the 5G-IoT Architecture, in: Proceedings of the international conference on smart cities and internet of things, pp. 1–8, 2018, September.
110. Rao, B.P., Saluia, P., Sharma, N., Mittal, A., Sharma, S.V., Cloud computing for Internet of Things & sensing based applications, in: 2012 Sixth International Conference on Sensing Technology (ICST), IEEE, pp. 374–380, 2012, December.
111. Rath, M., Resource provision and QoS support with added security for client side applications in cloud computing. Int. J. Inf. Technol., 11, 2, 357–364, 2019.
112. Rathore, S., Kwon, B.W., Park, J.H., BlockSecIoTNet: Blockchain-based decentralized security architecture for IoT network. J. Netw. Comput. Appl., 143, 167–177, 2019.
113. Ray, P.P., Dash, D., Kumar, N., Sensors for internet of medical things: State-of-the-art, security and privacy issues, challenges and future directions. Comput. Commun., 160, 111–131, 2020.
114. Rhee, K., Kwak, J., Kim, S., Won, D., Challenge-response based RFID authentication protocol for distributed database environment, in: International Conference on Security in Pervasive Computing, Springer, Berlin, Heidelberg, pp. 70–84, 2005, April.
115. Rodrigues, J.J., Segundo, D.B.D.R., Junqueira, H.A., Sabino, M.H., Prince, R.M., Al-Muhtadi, J., De Albuquerque, V.H.C., Enabling technologies for the internet of health things. IEEE Access, 6, 13129–13141, 2018.
116. Rohatgi, D., Srivastava, S., Choudhary, S., Khatri, A., Kalra, V., Smart Healthcare Based on Internet of Things, in: International Conference on Application of Computing and Communication Technologies, 2018, March, Springer, Singapore, pp. 300–309.
117. Roman, R., Najera, P., Lopez, J., Securing the internet of things. Computer, 44, 9, 51–58, 2011.
118. Roman, R., Zhou, J., Lopez, J., On the features and challenges of security and privacy in distributed internet of things. Comput. Networks, 57, 10, 22662279, 2013.
119. Samarati, P., di Vimercati, S.D.C., Murugesan, S., Bojanova, I., Cloud security: Issues and concerns, in: Encyclopedia on cloud computing, pp. 1–14, 2016.
120. Sengupta, J., Ruj, S., Bit, S.D., A Comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl., 149, 102481, 2020.
121. Shah, S.T.U., Yar, H., Khan, I., Ikram, M., Khan, H., Internet of Things-Based Healthcare: Recent Advances and Challenges, in: Applications of Intelligent Technologies in Healthcare, pp. 153–162, Springer, Cham, 2019.
122. Sharma, A. and Sharma, R., A Review of Applications, Approaches, and Challenges in Internet of Things (IoT), in: Proceedings of ICRIC 2019, Springer, Cham, pp. 257–269, 2020.
123. Sharma, R., Nah, F.F.H., Sharma, K., Katta, T.S.S.S., Pang, N., Yong, A., Smart living for elderly: design and human-computer interaction considerations, in: International Conference on Human Aspects of IT for the Aged Population, 2016, July, Springer, Cham, pp. 112–122.
124. Sicari, S., Rizzardi, A., Grieco, L.A., Coen-Porisini, A., Security, privacy and trust in Internet of Things: The road ahead. Comput. Networks, 76, 146–164, 2015.
125. Siekkinen, M., Hiienkari, M., Nurminen, J.K., Nieminen, J., How low energy is bluetooth low energy? comparative measurements with zigbee/802.15. 4, in: 2012 IEEE wireless communications and networking conference workshops (WCNCW), 2012, April, IEEE, pp. 232–237.
126. Soliman, M., Abiodun, T., Hamouda, T., Zhou, J., Lung, C.H., Smart home: Integrating internet of things with web services and cloud computing, in: 2013 IEEE 5th international conference on cloud computing technology and science, 2013, December, vol. 2, IEEE, pp. 317–320).
127. Son, D., Lee, J., Qiao, S., Ghaffari, R., Kim, J., Lee, J.E., Yang, S., Multifunctional wearable devices for diagnosis and therapy of movement disorders. Nat. Nanotechnol., 9, 5, 397, 2014.
128. Stergiou, C., Psannis, K.E., Kim, B.G., Gupta, B., Secure integration of IoT and cloud computing. Future Gener. Comput. Syst., 78, 964–975, 2018.
129. Suciu, G., Vulpe, A., Halunga, S., Fratu, O., Todoran, G., Suciu, V., Smart cities built on resilient cloud computing and secure internet of things, in: 2013 19th International Conference on Control Systems and Computer Science, 2013, May, IEEE, pp. 513–518.
130. Suh, M.K., Chen, C.A., Woodbridge, J., Tu, M.K., Kim, J.I., Nahapetian, A., Sarrafzadeh, M., A remote patient monitoring system for congestive heart failure. J. Med. Syst., 35, 5, 1165–1179, 2011.
131. Suh, M.K., Evangelista, L.S., Chen, V., Hong, W.S., Macbeth, J., Nahapetian, A., Sarrafzadeh, M., WANDA B.: Weight and activity with blood pressure monitoring system for heart failure patients, in: 2010 IEEE International Symposium on” A World of Wireless, Mobile and Multimedia Networks”(WoWMoM), IEEE, pp. 1–6, 2010, June.
132. Suo, H., Wan, J., Zou, C., Liu, J., Security in the internet of things: a review, in: 2012 international conference on computer science and electronics engineering, vol. 3, IEEE, pp. 648–651, 2012, March.
133. Suresh, A., Udendhran, R., Balamurgan, M., Varatharajan, R., A novel internet of things framework integrated with real time monitoring for intelligent healthcare environment. J. Med. Syst., 43, 6, 165, 2019.
134. Suryani, V., Sulistyo, S., Widyawan, W., Trust-based privacy for Internet of Things. Int. J. Electr. Comput. Eng., 6, 5, 2396, 2016.
135. Tewari, A. and Gupta, B.B., Security, privacy and trust of different layers in Internet-of-Things (IoTs) framework. Future Gener. Comput. Syst., 108, 909920, 2020.
136. Tyagi, S., Agarwal, A., Maheshwari, P., A conceptual framework for IoT-based healthcare system using cloud computing, in: 2016 6th International Conference-Cloud System and Big Data Engineering (Confluence), IEEE, pp. 503–507, 2016, January.
137. Ullah, K., Shah, M.A., Zhang, S., Effective ways to use Internet of Things in the field of medical and smart healthcare, in: 2016 International Conference on Intelligent Systems Engineering (ICISE), IEEE, pp. 372–379, 2016, January.
138. Upadhyay, S., Kumar, S., Dutta, S., Srivastava, A.K., Mondal, A.K., Kaundal, V., A Comprehensive Review on the Issues Related to the Data Security of Internet of Things (IoT) Devices, in: Intelligent Communication, Control and Devices, pp. 727–734, Springer, Singapore, 2020.
139. Usak, M., Kubiatko, M., Shabbir, M.S., Viktorovna Dudnik, O., Jermsittiparsert, K., Rajabion, L., Healthcare service delivery based on the Internet of things: A systematic and comprehensive study. Int. J. Commun. Syst., 33, 2, e4179, 2020.
140. Valdivieso Caraguay, Á. L., Benito Peral, A., Barona Lopez, L.I., García Villalba, L.J., SDN: Evolution and opportunities in the development IoT applications. Int. J. Distrib. Sens. Netw., 10, 5, 735142, 2014.
141. Velte, A.T., Velte, T.J., Elsenpeter, R.C., Elsenpeter, R.C., Cloud computing: a practical approach, p. 44, McGraw-Hill, New York, 2010.
142. Wang, X., Zhang, J., Schooler, E.M., Ion, M., Performance evaluation of attribute-based encryption: Toward data privacy in the IoT, in: 2014 IEEE International Conference on Communications (ICC), IEEE, pp. 725–730, 2014, June.
143. Wen, Q., Dong, X., Zhang, R., Application of dynamic variable cipher security certificate in internet of things, in: 2012 IEEE 2nd International Conference on Cloud Computing and Intelligence Systems, vol. 3, IEEE, pp. 1062–1066, 2012, October.
144. Wu, M., Lu, T.J., Ling, F.Y., Sun, J., Du, H.Y., Research on the architecture of Internet of Things, in: 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), vol. 5, IEEE, pp. V5-484, 2010, August.
145. Xiaohui, X., Study on security problems and key technologies of the internet of things, in: 2013 International conference on computational and information sciences, IEEE, pp. 407–410, 2013, June.
146. Xie, Y. and Wang, D., An item-level access control framework for intersystem security in the internet of things, in: Applied mechanics and materials, Trans Tech Publications Ltd, Baech, Switzerland, vol. 548, pp. 1430–1432, 2014.
147. Yang, J.C., Hao, P.A.N.G., Zhang, X., Enhanced mutual authentication model of IoT. J. China Univ. Posts Telecommun., 20, 69–74, 2013.
148. Yassine, A., Singh, S., Hossain, M.S., Muhammad, G., IoT big data analytics for smart homes with fog and cloud computing. Future Gener. Comput. Syst., 91, 563–573, 2019.
149. Ye, N., Zhu, Y., Wang, R.C., Malekian, R., Lin, Q.M., An efficient authentication and access control scheme for perception layer of internet of things, Applied Mathematics and Information Sciences, 8, 1617–1624. 2014.
150. Yeole, A.S. and Kalbande, D.R., Use of internet of things (iot) in healthcare: A survey, in: Proceedings of the ACM Symposium on Women in Research 2016, ACM, pp. 71–76, 2016, March.
151. Yuriyama, M. and Kushida, T., Sensor-Cloud Infrastructure-Physical Sensor Management with Virtualized Sensors on Cloud Computing. NBiS, 10, 1–8, 2010.
152. Zarpeläo, B.B., Miani, R.S., Kawakani, C.T., de Alvarenga, S.C., A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl., 84, 25–37, 2017.
153. Zaslavsky, A., Perera, C., Georgakopoulos, D., Sensing as a service and big data. arXiv preprint arXiv:1301.0159, Proceedings of the International Conference on Advances in Cloud Computing (ACC), Bangalore, India, July, 2012, 2013.
154. Zhang, Z.K., Cho, M.C.Y., Wang, C.W., Hsu, C.W., Chen, C.K., Shieh, S., IoT security: ongoing challenges and research opportunities, in: 2014 IEEE 7th international conference on service-oriented computing and applications, IEEE, pp. 230–234, 2014, November.
155. Zhao, G., Si, X., Wang, J., Long, X., Hu, T., A novel mutual authentication scheme for Internet of Things, in: Proceedings of 2011 International Conference on Modelling, Identification and Control, IEEE, pp. 563–566, 2011, June.
156. Zhao, K. and Ge, L., A survey on the internet of things security, in: 2013 Ninth international conference on computational intelligence and security, IEEE, pp. 663–667, 2013, December.
157. Zhou, J., Cao, Z., Dong, X., Vasilakos, A.V., Security and privacy for cloudbased IoT: Challenges. IEEE Commun. Mag., 55, 1, 26–33, 2017.
- * Corresponding author: [email protected]
