2
Issues and Challenges Related to Privacy and Security in Healthcare Using IoT, Fog, and Cloud Computing
Hritu Raj, Mohit Kumar, Prashant Kumar*, Amritpal Singh and Om Prakash Verma
Dr. BR Ambedkar National Institute of Technology Jalandhar (Punjab), India
Abstract
In today’s era, the IoT (Internet of Things) introduced a new way to create a bond between devices and humans for enhancing and making life quite easy. The main purpose of attraction toward improving the healthcare industry with the latest technology is because IoT has proven great opportunity in smart offices, warehouses, smart homes, etc. So, IoT can also improve the healthcare industry very well. The healthcare sensor generates health-related data like blood pressure, blood glucose, blood temperature, ECG, and much more. These devices produce very large amounts of data, which need to be processed, filtered, and stored securely and efficiently. In this paper, we will discuss the complete architecture with various challenges and security risks of the next-generation healthcare industry with healthcare IoT sensor and fog computing. This paper also consists of some methodology used in various research papers to address the security and privacy related in IoT, fog, and cloud computing environment.
Keywords: Internet of Things, healthcare, fog computing, cloud computing, security, privacy
2.1 Introduction
IoT (Internet of Things) is very trending system consists of a variety of sensors, networking devices, microcomputer or microprocessor, optimized software, and different objects. To exchange data among each other, IoT devices, computers servers, and even cloud for data processing Apat et al. [24]. The demand of IoT devices is increasing day by day, and this will create a large opportunity for the IoT industry and researchers. Figure 2.1 illustrates healthcare using IoT. From the last few years, the sensor industry has evolved from making tiny sensors like photodetectors, temperature sensors, and hall sensors to more advanced sensors like blood glucose sensor, oxygen saturation level sensor, and ECG. With integration of fog computing and cloud, it facilitates the disease prediction of certain kinds and can get future insights of different diseases. The IoT system comprises various things like wearable IoT sensors, adaptive network interfaces, and optimized software integration module to cloud. Sensors are used to collect health-related data of sick patient with devices like oximeter for measuring oxygen saturation percentage in blood, blood pressure meter for measuring systolic blood pressure as well as diastolic blood pressure in arteries, blood glucose meter for measuring concentration of blood glucose using tiny drop of blood taken from human body, weight sensor for periodic measurement of patient weight for further analysis, and temperature sensor for monitoring real-time body temperature data.
Fall detection sensor for detection of accidental fall is using accelerometer and gyroscope and more advanced sensors like ECG for measuring electrical heart activity at rest. Adaptive networking interface provides support for a large number of networking protocols to easily integrate with different networking devices and software with enhanced algorithms to process health-related data efficiently and accurately Multag et al. [25]. There are a number of other uses of IoT devices. There are, like in fitness, a variety of fitness trackers available in the market for measuring daily activity like heart rate, sleep time, and running and walking time and also provide an interface for calling and messaging from right to the wrist. Companies offering these types of devices are Apple, Samsung, Fitbit, Xiaomi, etc. Next use of IoT devices is in smart homes, where the smart home Ghosh et al. [31], consists of a variety of a smart sensors like smart lock for keyless entry in car and homes, photo-director for turning garden light on at night and off at the day, sensor for detecting movement in room and triggering alarm when an intrusion happens, wireless camera with internet access to remotely monitor home and other premises, smart thermostat for controlling temperature according to human need, and smart fire alarm system for triggering alarm when a thing catches fire; IoT sensors can also be used in smart traffic management system for monitoring vehicle tracking on roads and switching traffic light according to traffic need. IoT sensors can also be used in warehouses for tracking workers activities. The increasing demand of smart devices in various fields creates huge amount of data and these data falls under various risk and challenges, if does not handled properly (especially health-related data). Patient data generated by smart heath sensors are very sensitive and critical, and management of these data is quite challenging Alihamidi et al. [32]. Every healthcare system must be provided security mechanism to handle five major factors in data handling: availability, integrity, confidentiality, authentication, and non-repudiation.

Figure 2.1 Healthcare using IoT.
2.2 Related Works
A paper proposed by Sun et al. [1] named “Security and Privacy in the Medical Internet of Things: A Review” was published in March 2018. In this paper, various security issues are discussed about health-related data which are traveling over the internet. Their main focus was data usability, integrity, and auditing.
They also talked about different existing techniques available like encryption and access control.
A survey paper by Zhang et al. [2] on “Security-Aware Measurement in Software-Defined Networking (SDN)” consists of SDN basic architecture, issue in security, performance analysis, bandwidth analysis, topologies, and future scope.
A paper named “Privacy-Preserving and Multifunctional Health Data Aggregation With Fault Tolerance for Cloud Assisted WBANs” written by Han et al. [3] discusses privacy preserving technique in wireless body area networks.
Abuwardih et al. [5] presented a paper on privacy preserving in healthcare data; in this paper, they discussed various types of attacks and privacy issues related to patient data. They also proposed some architectures and procedures to handle different type of attacks related to patient data. The paper was named “Privacy Preserving Data Mining on Published Data in Healthcare”, and it was proposed in 2016.
Anwar et al. [6] proposed a paper in 2015 named “Anytime Anywhere Access to Secure Privacy-Aware Healthcare Services: Issues Approaches and Challenges”; this paper consists of various approaches and challenges arises in healthcare industry for providing anytime and anywhere access of health-related resources. In this paper, they have shown approaches that are currently available and also discussed different policies made by government for information and technologies–related and international data–related security issues. The issues are generated by human, machine, and some other factors. All the security-related concern is discussed in detailed manner.
Rahman et al. [18] published a paper in ICOST (International Conference on Smart Homes and Health Telematics) naming “Inclusive Society: Health and Wellbeing in the Community and Care at Home”. In this paper, they have proposed a generic model “PriGen” for securing patient health-related data with the help of cloud storage. PriGen facilitates access of patient health-related data without involvement of any other party from the cloud as well as hiding highly sensitive data. PriGen uses homomorphic function for encryption of data that needs very high security and which is critical. This algorithm preserves the highly sensitive health-related personal data in public cloud environment and maintains confidentiality of the patient data.
Bindahman et al. [19] proposed a paper in 2011 ICIEIS (Informatics Engineering and Information Science: International Conference) in which they talked about general concept of privacy problem related to patient health data. They discussed various available security measures and its performance comparison related to healthcare data. Based on that, they also suggested some techniques for those security-related problems.
Next is the paper written by Dubovitskaya et al. [20] entitled “ICT Systems Security and Privacy Protection: 30th IFIP TC 11 International Conference SEC 2015”. In this paper, they have discussed various problems in building of health-related database for heterogeneous environment, where data are coming from various sources of different network environment of different hospitals. The integration of data comes from different locations. They introduced scaling and securing techniques for patient e-health data. They have used an algorithm called RSDB (Representative Protein Sequence Database) for collecting patient data efficiently and securely that are coming from various sources.
A paper by Idoga et al. [22] has discussed different issues related to privacy in the application e-healthcare environment.
2.3 Architecture
In this section, we will discuss three-layer architecture of next-generation healthcare industry with smart sensors, fog node, and cloud computing. The new healthcare industry will change the way hospital staff or doctors treat the patient. This IoT-driven healthcare industry will get highly efficient environment at very low cost, which decreases the workload and increases the throughput. The layered architecture will do different tasks at different layer. The three layers are device layer, fog layer, and cloud layer as shown in Figure 2.2.
2.3.1 Device Layer
At this layer, a very large number of smart sensors are involved, which are gathering tons of health-related data in near real-time. Any patient or healthcare specialist can access these data using any web-enabled device like phone, tablet, or computers. What they require is a secure and stable communication protocol to next layer in this case (fog layer). There is various communication are available for the wireless sensor nodes for communication within each other or propagating information to next layer. But selection of best protocol from the pool of various protocols is a tedious task. There are some protocols which are widely adopted for some general data transfer tasks are Low-Energy Bluetooth and High-Fidelity Wi-Fi.
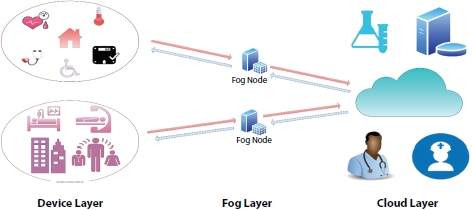
Figure 2.2 Three-layer architecture.
Low-Energy Bluetooth is good for beacon type signal and where power constrains matter too much or battery is irreplaceable (like in heart pacemaker). On the other hand, Wi-Fi is used where long-range and high-data rate required (like transferring raw ECG data).
2.3.2 Fog Layer
This layer consists of high-end processors, large and high-speed data storage, and Network Interface Card for communication over internet. The patient health data are very critical data a normal considerable amount of latency can cost lives, example of such type of data is Myocardial Infarction where latency of seconds can cause serious damage Singh et al. [26]. So, we cannot rely only on cloud for data processing and analyzing critical time sensitive data. In handling these types of data, we require analysis, processing, and storage as close as possible to the devices where data is generated Badidi et al. [23]. Thus, need of fog computing arises here, and it processes, analyzes, and stores (for further use) health-related data which is very time-sensitive in nature Kraemer et al. [28]. This layer also filters, compresses high volume raw data, and passes to next layer (cloud computing layer) for big data analytics purposes.
2.3.3 Cloud Layer
The cloud layer integrates data from various fog nodes and does analysis using deep learning, generates pattern, and gets future insights for the disease prediction. The cloud layer provides various connectivity protocols to address variety of users across the world Akintoye et al. [27]. The fog node across different geographical areas uses different communication channel like optical fibers, twisted pair, co-axial cable, satellite communication, and sometimes LTE. The cloud provides best data management techniques to health-related user for better management of large amount of patient data. The cloud healthcare system incorporates set of rules through which it can analyze patterns and can trigger alarm when any risky pattern detected. The cloud layer uptime should be as high as possible (very near to 100%). So, it can always be there for help when ever any request arises from persons involved in healthcare institutions.
2.4 Issues and Challenges
Integration of IoT and fog computing can take the healthcare industry to the next level. The smart health sensors of wearable IoT devices stays with the patient all the time and it monitors patient heart rate, blood pressure, body temperature, blood glucose, oxygen saturation, and much more in real time and passes these whole data to the fog node for the processing and storage and then to the cloud for deep learning Khan et al. [29]. All this data plays an important role in the healthcare industry. So, it should be protected from various threats and vulnerabilities. There are a number of security challenges that we should care about. Generally, the patient care industry invests very less amount of money on privacy and security of healthcare data. But in a smart healthcare system, security and privacy plays a very important role Hamid et al. [30]. The data produced by medical e-health sensors are very large and very sensitive. These data also contain patient private information. The patient data can be hampered on different stages like in data gathering from sensors and transfer it to fog nodes and sometimes on clouds also.
Some of the data risks that should be taken into account are integrity of data, authenticity of data, and auditing of data and private data of patients. Various mechanisms are shown in Table 2.1.
Integrity of Patient Data: It refers to availability of the same data in the whole system without change. Or you can say no modification in data throughout its life cycle. This means accuracy of data should not be tempered. There should be no unintentional change in data. Any intention should reflect immediately in the whole system. The main purpose of maintaining integrity is to ensure accuracy and reliability of the health data. Integrity can be sub-categorized in four categories: integrity defined by user, integrity of reference, integrity of various domains, and integrity of data entity.
Usability of Patient Information: Information usability refers to no unauthorized access of patient data generated or stored by smart healthcare systems. The use of deep learning on patient data can generate unique patterns and provide different solutions. The data generated by the system also comes at data privacy risks. The little bit of unwanted modification in data can cause serious issues.
Audition of Healthcare Data: Access of healthcare devices needs to be auditioned properly for monitoring of various mechanisms and techniques for identifying unwanted patterns. The integration of cloud computing resources may also create some trouble in security concerns because the cloud providers generally are usually unreliable in case of privacy terms. So, it requires a good audition procedure, the audition procedure consists of records used in operation, the service provider (in this case the cloud provider) and the user which is involved in patient care.
Privacy of Patient: Privacy of users plays a very important role in any digital technology. In the e-health system, patient information is the most valuable resource. So, we need to be very careful in keeping data safe. The patient data can be divided into two kinds: general records and the critical personal information. General records do not require any good privacy like name, age, sex, height, weight, and color. But critical personal information needs special attention in terms of security and privacy [21]. Critical information includes genetic info data, allergy from some kind medicine, addiction to drugs, certain kinds of infections, color blindness data, fertility information, sexual orientation, and some others. This information needs to be encrypted before storing and sending it to the cloud.
Table 2.1 Security and privacy mechanism prosed in some papers.
| Paper | Techniques | Domain | Characteristic |
| [4] | Machine Learning | Smart Healthcare Health Decision | Support System |
| [7] | Attribute Based-Encryption | Personal Healthcare | Encrypting Personal Healthcare Records |
| [8] | Ciphertext Policy Attribute Based-Encryption | Wireless Network for Healthcare Sensors | Preserving integrity and confidentiality of health-related data |
| [9] | Attribute Based-Encryption | Patient Data sharing | Resolving key escrow problem |
| [10] | KMS | e-health systems | Lightweight end to end key management |
| [11] | IoT sensors based on Cloud | Senior citizen health data management | Providing medical assistance to elder people |
| [12] | Ciphertext Policy Attribute Based-Encryption | Encrypted cloud data | Resolving APKS problem in Cloud computing |
| [13] | m2-ABKS | Encrypted e-health data | Authorized access of records and collusion attacks are addressed |
| [14] | Laplace guided KR | Image Compression | Achieving high compression ratio with low computational cost |
| [15] | PASStree | Matching of string | Providing good string matching without privacy hampering |
| [16] | Authentication techniques | Patient Supervision | Promising patient’s privacy while preserving confidentiality of system |
| [17] | Homomorphic Encryption | Privacy of Data | Preserving privacy of data generated by IoT devices |
There are some threats available related to security and privacy.
Fake Identity Attack: In this, attacker can create false identity of authorized persons in the system and can do certain things like changing the entries and deleting some important records; attackers can also downgrade the system performance by consuming system resources unnecessarily.
Data Tampering Attack: In this, attacker can tamper health-related data by changing, editing, manipulating, and destroying.
Spamming: In this attack, fake data of patients is created and flooded in the system which induces unnecessary entry in data tables which leads to inaccurate results.
Denial-of-Service Attack: In this, attacker creates a large number of fake packets to flood the network, and then, the system engages in fulfilling the request generated by the fake packets and denies the request generated by genuine packets. This results in poor system performance and uptime. Eavesdropping: In this, attackers take access of the communication channel and start snooping the packet traveling in that channel. If a very strong encryption technique is not applied, then it is very easy for attackers to read and understand those data.
Location Privacy: In this, attacker can gain live location access of the patient, generated form the wearable IoT devices attached to the patient or the mobile phone.
Usages Privacy: In this, attacker can gain usage information of the patient or the person involved in the healthcare to find the useful and predict some sensitive information.
2.5 Conclusion
Technological advancement in the healthcare industry is increasing rapidly, and a variety of wearable devices are available for gathering health-related patient data. Data gathered from these smart devices are very huge.
The high volume of important data invites attackers to steal and manipulate it. To maintain integrity, security and privacy of health-related data. In this paper we have discussed architecture of the next generation healthcare system with latest available IoT devices, use of fog computing for local processing and storing, then for pattern recognition sends it to the cloud. Here, deep learning and data mining are done on that data. There are many security privacy issues, and challenges are there that need to be addressed very carefully.
References
1. Sun, W., Cai, Z., Li, Y., Liu, F., Fang, S., Wang, G., Security and Privacy in the Medical Internet of Things: A Review. Secur. Commun. Netw., 2018, 9, 2018.
2. Zhang, H., Cai, Z., Liu, Q. et al., A survey on security-aware measurement in SDN. Secur. Commun. Netw., 2018, 2018. https://doi.org/10.1155/2018/2459154.
3. Han, S., Zhao, S., Li, Q., Ju, C.-H., Zhou, W., PPM-HDA: privacy-preserving and multifunctional health data aggregation with fault tolerance. IEEE Trans. Inf. Forensics Secur., 11, 9, 1940–1955, 2016.
4. Yin, H. et al., Smart Healthcare. Found. Trends R Electron. Des. Autom., 1, 1–67, 2018.
5. Abuwardih, L.A., Shatnawi, W., Aleroud, A., Privacy preserving data mining on published data in healthcare: A survey. 1–6, 2016. https://ieeexplore.ieee.org/document/7549444
6. Anwar, M., Joshi, J., Tan, J., Anytime anywhere access to secure privacy-aware healthcare services: Issues approaches and challenges. Health Policy Technol., 4, 4, 299–311, 2015.
7. Lounis, A., Hadjidj, A., Bouabdallah, A., Challal, Y., Secure medical architecture on the cloud using wireless sensor networks for emergency management, in: Proceedings of the 2013 IEEE 8th International Conference on Broadband, Wireless Computing, Communication and Applications, BWCCA 2013, pp. 248–252, October 2013.
8. Lounis, A., Hadjidj, A., Bouabdallah, A., Challal, Y., Healing on the cloud: secure cloud architecture for medical wireless sensor networks. Future Gener. Comput. Syst., 55, 266–277, 2016.
9. Li, M., Yu, S., Zheng, Y., Scalable and secure sharing of personal health records in cloud computing using attributebased encryption. IEEE Trans. Parallel Distrib. Syst., 24, 1, 131–143, 2012.
10. Abdmeziem, M.R. and Tandjaoui, D., A cooperative end to end key management scheme for e-health applications in the context of internet of things, in: Ad-hoc Networks and Wireless, pp. 35–46, Springer, Berlin Heidelberg, 2014.
11. Hu, J.-X., Chen, C.-L., Fan, C.-L., Wang, K.-H., An intelligent and secure health monitoring scheme using IoT sensor based on cloud computing. J. Sens., 2017, Article ID 3734764, 11 pages, 2017.
12. Li, M., Yu, S., Cao, N., Lou, W., Authorized private keyword search over encrypted data in cloud computing, in: Proceedings of the 31st International Conference on Distributed Computing Systems (ICDCS ‘11), IEEE, Minneapolis, Minn, USA, pp. 383–392, July, 2011.
13. Miao, Y., Ma, J., Liu, X., Wei, F., Liu, Z., Wang, X.A., m2-ABKS: attributebased multi-keyword search over encrypted personal health records in multi-owner setting. J. Med. Syst., 40, 11, 246, 2016. https://link.springer.com/article/10.1007/s10916-016-0617-z
14. Song, C., Lin, X., Shen, X. et al., Kernel regression based encrypted images compression for e-healthcare systems, in: Proceedings of the International Conference on Wireless Communications and Signal Processing, pp. 1–6, 2013.
15. Bezawada, B., Liu, A.X., Jayaraman, B., Wang, A.L., Li, R., Privacy Preserving String Matching for Cloud Computing, in: Proceedings of the 35th IEEE International Conference on Distributed Computing Systems, ICDCS ‘15, pp. 609–618, July 2015.
16. Li, C.-T., Lee, C.-C., Weng, C.-Y., A secure cloud-assisted wireless body area network in mobile emergency medical care system. J. Med. Syst., 40, 5, 1–15, 2016.
17. Gong, T., Huang, H., Li, P., Zhang, K., Jiang, H., A Medical Healthcare System for Privacy Protection Based on IoT, in: Proceedings of the 7th International Symposium on Parallel Architectures, Algorithms, and Programming, PAAP ‘15, pp. 217–222, December 2015.
18. Rahman, F., Ahamed, S., II, Yang, J.-J., Wang, Q., nclusive Society: Health and Wellbeing in the Community and Care at Home. 11th International Conference on Smart Homes and Health Telematics ICOST 2013, June 19–21, 2013.
19. Bindahman, S. and Zakaria, N., Informatics Engineering and Information Science. International Conference ICIEIS 2011, November 14–16, 2011.
20. Dubovitskaya, A., Urovi, V., Vasirani, M., Aberer, K., ICT Systems Security and Privacy Protection. 30th IFIP TC 11 International Conference SEC 2015, May 26-28, 2015.
21. Farahani, B., Firouzi, F., Chang, V., Badaroglu, M., Constant, N., Mankodiya, K. , Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare. Future Gener. Comput. Syst., 78, Part 2, 2018. https://digitalcommons.uri.edu/ele_facpubs/79
22. Idoga, P.E., Agoyi, M., Coker-Farrell, E.Y., Ekeoma, O.L., Review of security issues in e-Healthcare and solutions. 2016 HONET-ICT, Nicosia, pp. 118121, 2016.
23. Badidi, E. and Moumane, K., Enhancing the Processing of Healthcare Data Streams using Fog Computing. 2019 IEEE Symposium on Computers and Communications (ISCC), Barcelona, Spain, pp. 1113–1118, 2019.
24. Apat, H.K., Bhaisare, K., Sahoo, B., Maiti, P., Energy Efficient Resource Management in Fog Computing Supported Medical Cyber-Physical System. 2020 International Conference on Computer Science, Engineering and Applications (ICCSEA), Gunupur, India, pp. 1–6, 2020.
25. Mutlag, A.A., Ghani, M.K.A., Arunkumar, N., Mohammed, M.A., Mohd, O., Enabling technologies for fog computing in healthcare IoT systems. Future Gener. Comput. Syst., 90, 62–78, 2019.
26. Singh, S., Bansal, A., Sandhu, R., Sidhu, J., Fog computing and IoT based healthcare support service for dengue fever. Int. J. Pervasive Comput. Commun., 14, 2, 197–207, Jun. 2018.
27. Akintoye, S.B., Bagula, A.B., Isafiade, O.E., Djemaiel, Y., Boudriga, N., Data Model for Cloud Computing Environment. e-Infrastructure and e-Services for Developing Countries. AFRICOMM 2018. Lecture Notes of the Institute for Computer Sciences Social Informatics and Telecommunications Engineering, vol. 275, 2019.
28. Kraemer, F.A., Braten, A.E., Tamkittikhun, N., Palma, D., Fog Computing in Healthcare-A Review and Discussion. IEEE Access, 5, 9206–9222, 2017.
29. Khan, S., Parkinson, S., Qin, Y., Fog computing security: a review of current applications and security solutions. J. Cloud Comput., 6, 1, 19, 2017.
30. Al Hamid, H.A., Rahman, Sk Md M., Shamim Hossain, M., Almogren, A., Alamri, A., A Security Model for Preserving the Privacy of Medical Big Data in a Healthcare Cloud Using a Fog Computing Facility With Pairing-Based Cryptography. IEEE Access, 5, 22313–22328, 2017.
31. Ghosh, A.M., Halder, D., Hossain, S.A., Remote health monitoring system through iot. 2016 International Conference on Informatics Electronics and Vision (ICIEV), pp. 921–926, 2016.
32. Alihamidi, I., Ait Madi, A., Addaim, A., Proposed Architecture of e-health IoT. 2019 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, pp. 1–7, 2019.
- *Corresponding author: [email protected]
