Understanding stakeholders’ real concerns is critical to successful software development. Concerns come from various sources and can be about different aspects of the system. Use cases provide a single technique to describe what the system must do to address these concerns. We distinguish between two major categories of use cases: application and infrastructure use cases. Application use cases describe how users interact with the system to perform the desired functionality. Infrastructure use cases describe what the system does to add qualities such as usability, reliability, performance, and supportability to each step of an application use case.
If you want to build the correct system, you have to get the requirements correct. This does not necessarily mean thick and huge volumes of documents. You must understand the motivation behind the stated requirements—the stakeholders’ concerns. And that is paramount. If you ever feel that stakeholders keep on changing their requirements, ask yourself these questions: do you have a good feel for the stakeholders’ concerns, and do you share their vision of the desired system? Even if your answer is yes, you must continually validate your understanding with them.
In addition, you have to understand stakeholder priorities. Not all concerns are created equal. Some are more important than others. The priority determines which requirements have to be developed before others and how their development will be spread across the project schedule. If things do not turn out well, you know which requirements can be dropped out, and your stakeholders can still get an acceptable, albeit incomplete, functionality.
The whole idea of requirements is about nailing down the problem that the system is intended to solve. You must be able to elicit and explore the root problem with the stakeholders. You must understand the business domain; you must walk through the business scenarios with the stakeholders; you must identify key desirable features of the system with them. You frequently do these activities in parallel, and the goal is to draw out the stakeholders’ real needs.
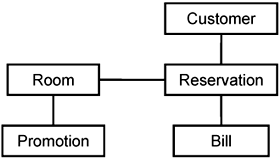
It is an important stakeholder concern that the system correctly and accurately captures the problem domain. This can be effectively achieved through classes. When being introduced into a new problem domain, you need to quickly grasp its essential concepts that distinguish this new problem domain from another. Classes are excellent tools for you to describe such concepts. For example, if you are ever required to build a hotel management system, you need to understand what constitutes such concepts as Room, Promotion, Reservation, Customer, and Bill. Even if you have built such a system for Hotel Chain ABC, the terms used by Hotel Chain XYZ might be different. It is extremely important that you clarify these concepts. You can capture them in a glossary. You can most certainly depict them visually as classes through a class diagram such as that shown in Figure 7-1, which further shows the relationships between these classes.
Finding these classes constitutes what is known as domain modeling, or business object modeling [Jacobson et al. 1994]. You go through the essential business scenarios that your system will be supporting to identify what information the system needs to keep track of or manipulate. Such information will be modeled as domain classes. It is usually sufficient to identify the essential attributes and relationships between these classes. At this point, you are merely capturing the essential concepts and their relationships. You should not go into too much detail as if you were doing data modeling in database design. You will do that later.
Stakeholders and project sponsors normally justify the need for a new system or an enhancement by emphasizing the benefits and payoffs of specific features. Features are high-level statements of desired system capability, which can either be in terms of functionality (i.e., what the system can do) or some other quality attribute (performance, security, etc.). There are many ways to come up with the features for a system. You can conduct some brainstorming with the stakeholders; you can look at the problems they are facing; you can walk through the business process with them; and so on. But whichever method you use, you end up with a list of key features for the system. As an example, Listing 7-1 itemizes the key features of the Hotel Management System.
Example 7-1. Key Features of Hotel Management System
A customer can make a reservation for a hotel room.
Counter staffs can check in and check out customers.
Hotel management can define standard room rates and promotional offers when room rates are reduced for limited periods.
Members can accumulate loyalty points and use them for any payment.
There will be a waiting list in case the rooms are fully reserved.
Different types of customer (individual, corporate, members) must be handled.
The room reservation can be over different channels, such as through agents, Internet, or via phone.
The system will store all records in a relational database.
For audit purposes, all transactions in the system have to be logged.
Only authorized personnel can perform their functions.
To promote ease of use, the system will track the users’ preferences and use them as default.
All retrieval of records should take no longer than 2 seconds.
Listing 7-1 gives us, in concise terms, an overview of the system’s requirements. However, it definitely does not constitute all the requirements for the system. Listing 7-1 is still a long way from that. From the perspective of the developer, the features are still open to many interpretations, and different acceptance criteria can be proposed for each one. Additional work is necessary to clarify what each feature means. One way to find out more about these features is to refine them one by one, resulting in a long requirement list. But if you do this, you end up with loose bits of information.
A more effective approach is to walk through the use of the system and uncover how the features are put into effect. This is a better approach because it puts the features in the context of the system operation. This is what use-case modeling is all about. The remainder of this chapter describes how to map these features to use cases. We also describe how to explore and uncover requirements surrounding these features and how to capture them through use cases. Through use cases, you clarify stakeholders’ concerns about the system’s functionality and quality.
Most analysts distinguish between two kinds of requirements: functional requirements (FRs) and nonfunctional requirements (NFRs). Typically, functional requirements refer to what users can do with the system, whereas nonfunctional requirements usually refer to qualities of the system. Features 1 through 7 in Listing 7-1 are usually considered functional requirements; whereas features 8 through 13 are considered nonfunctional, or at least cross-functional: that is, they apply to all the functions in features 1 through 7.
Today, most practitioners model functional requirements with use cases, but they tend to leave nonfunctional requirements out of use-case modeling. However, use cases are applicable to nonfunctional requirements too. So long as a requirement requires some observable response to be programmed into the system, you can apply use cases. Always ask yourself, is there something the system must do to meet a particular requirement? If the answer is yes, then use cases can be applied because use cases help you capture desired system behaviors. Also ask if there is a way to test the system for conformance to the requirement. As long as you can define a test, you can indeed define a use case for it. After all, a use case is a set of test cases. Basically, each scenario in the use case is a preliminary test case. To complete the test case, you need to add test data. Making use cases/test cases upfront has been popularized through test-first-design techniques.
Nonfunctional requirements usually need the support of some underlying infrastructure mechanisms. For example, feature 12 needs some infrastructure mechanism to track user inputs. Feature 13 requires an infrastructure mechanism to utilize some form of caching to meet the 2-second response time requirement. So, these nonfunctional requirements do impose some behaviors on the infrastructure. You can most certainly model these infrastructure mechanisms with use cases. To distinguish such use cases from others, we call them infrastructure use cases. We call the others application use cases. Infrastructure use cases deal with infrastructure concerns, and application use cases deal with application concerns.
Most of you are familiar with writing application use cases. Here, we recommend that you specify the use cases for infrastructure mechanisms as well. The advantages for doing so are many. It helps the development team understand how the infrastructure mechanism will be used. Too frequently, we find that infrastructure mechanisms are poorly described. There might be a bunch of diagrams that attempt to describe the realization of the infrastructure mechanism, but they generally describe only the basic use of it. How exceptions and variations are handled is usually either not considered or poorly described. This leads to obscure defects in the system. You apply the same technique as you do with application use cases to explore the different scenarios that each infrastructure mechanism has to handle. There will be basic and alternate flows and so on in infrastructure use-case specifications just as in typical use-case specifications. We discuss how to model such infrastructure use cases later in this chapter.
Let us look at how you can distinguish application use cases from functional requirements. Features 1 to 5 are functional features and describe what users can do with the system; they lead to the identification of use cases for our system. But since features are rarely complete, we often supplement the identification of use cases by first identifying who the actors for the system are and what they are using the system for. Each use of the system is described through use cases.
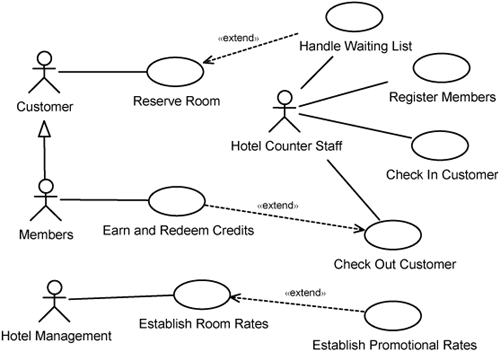
A first attempt at identifying use cases that address features 1 to 5 is depicted in Figure 7-2.
Most, if not all, businesses exist for two groups of people: customers who need some products and services, and business owners who believe they can earn some money from the customers. The rest of the folks in the business are workers; they are there to do their jobs and get paid. In our Hotel Management System, the actors that have been explicitly identified are:
Customers (and members)
Hotel counter staff
Hotel management
The goal of customers is to reserve rooms and stay there happily for a period of time. In our system, our stakeholders (the business owners) want the customer to reserve rooms over the Internet and thus broaden the hotel’s sales channel. Counter staff help customers check in and out of their rooms. Of course, counter staff must collect payment from the customers when they check out. The hotel management specifies the room rates and specials, but a frequent scenario is defining promotional offers when rooms are offered at a discount. As an attempt to capture more customers, the hotel offers a loyalty program whereby members can earn and redeem credits. Credits are earned when the member makes payment on a 10 to 1 ratio—that is, for every 10 dollars spent, the member earns one credit, which is equivalent to 1 dollar. Credits can be used to make subsequent payments. To participate in this program, the customer has to register through the counter staff. The stakeholder indicates the need for a waiting list as well.
The use cases Reserve Room, Check In Customer, Check Out Customer, and Establish Room Rates are core use cases.
The use case Earn and Redeem Credits is an extension of the check-out use case to permit payment by loyalty credits earned by previous payments. A prerequisite for using loyalty credits is that the customer be registered as a member. This is provided by the Register Members use case.
The Establish Promotional Rates use case is an extension of the Establish Room Rates use case. The key difference between promotional rates is that they are time-limited, whereas room rates remain fairly constant.
The use cases and their relationships in Figure 7-2 are by no means complete. They represent an initial understanding of the system’s requirements. As you proceed through the project, the use-case model gets updated.
Once you have identified the use cases for the system, you have in effect separated the different concerns for a system from the actor or user perspective. Now you can explore the concerns of each use case in greater detail. For each use case, there are many flows of events, each describing how a particular variation is handled through that use case. It is important to have a systematic way to explore variations. Otherwise, you risk missing key requirements of a system. To avoid this risk, you have to identify variables for your system or for each use case. Some of these variables may be critical concerns to your stakeholders. In our example Hotel Management System, they are so important that they appear in the key feature list in Listing 7-1. Features 6 and 7 identify two variables, Customer Types and Reservation Channels. Each variable may take on different values. You may have values for the Customer Types variables such as individual customer, corporate customer, registered customers, and customers from an affiliate hotel. You may have values for different Reservation Channels such as through an agent, a telephone (i.e., an interactive voice response unit), or the Internet. Customer Types and Reservations Channels are not the only variables: as yet another example, you can have a variable for reservation schemes with values such as a single period reservation, reservation over multiple time periods, recurring reservations, and so on.
Identifying variables and their values is important because they help you to understand the complexity of the system you are developing. They identify the universe of your requirements gathering effort—that is, your project scope. Forgetting to deal with a variable or a variable value has negative consequences on the completeness of requirements. Thus, it is important to identify them early in the project.
The domain model shown in Figure 7-1 is quite useful in identifying the variables. The domain class itself and the attributes of the domain class and associations between domain classes are all candidates of use-case variability.
Use-case variables will likely affect multiple use cases. For example, most of the use cases identified earlier in Figure 7-2 will be affected by the Customer Type variable; thus, you might have scenarios describing how corporate customers reserve room, check in, check out, and use their loyalty credits, and those customers may be given higher priorities on the waiting list. In other words, the variables crosscut use cases, and you might consider them “aspects of use cases” (see Sidebar 7-1).
The handling of each variable value tends to be use-case-specific. Hence, while the variables may cut across use cases, it is better to leave them within the use cases and describe how to handle them as alternate flows. In fact, use-case variables help you organize your alternate flows. You can have one section per use-case variable, and within each of these sections, describe how each variable value is handled. This organization is shown in Listing 7-2.
Example 7-2. Organizing Alternate Flows with Use-Case Variables
Basic Flow
The use case begins when an individual customer wishes to make a reservation for a single period over the Internet.
1. . . .
2. . . .
3. . . .
Alternate Flows
Customer Types
Corporate Customer
Reservation Periods
Multiple Periods
Reservation Channels
Agent Reservation
Phone Reservation
There are two ways to describe the basic flow, either generically and independent of each use-case variable or using a default value. Listing 7-2, shows the use of default values in the basic flow. It assumes that the customer is an individual customer, the reservation is for a single time period, and the reservation is made over the Internet. The variations to this default case are handled in the alternate flows, which are organized according to the use-case variables.
When describing the handling of each variable, you walk through the basic flow and identify steps or points that are affected by that variable. You consolidate these points (which we call variability points) as sort of an introduction for that variable. So, each variable becomes a subsection within the alternate flows. Within this subsection, you describe how each variation is handled as an alternate flow. Organizing use-case specifications in this way makes reading use-case specifications a lot easier. This is much better than merely producing a long list of alternate flows. It facilitates reviewing the use case for completeness. It also facilitates the subsequent transition to analysis and design.
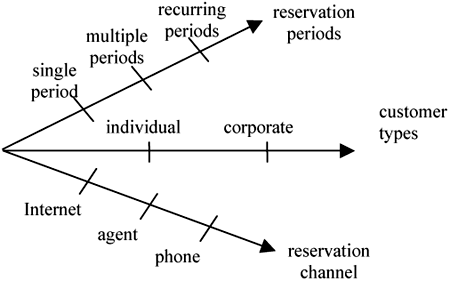
When helping the stakeholders to describe how they intend the variations to be handled, you can use a diagram similar to Figure 7-3. The figure presents the variables on each axis, and the markings on each axis represent a particular value.
Using Figure 7-3, you can ask whether the use-case variables are independent of each other. For example, how different reservation channels are handled is independent of the other two variables in the figure. Customer types and reservation periods may have some relationships. For example, only a corporate customer can make reservations over recurring periods, or there may be different pricing between customer types and reservation periods. When there is interplay between use-case variables, you need to supplement your use-case specifications with tables and matrices to summarize how they are handled.
It is not always possible to describe precisely how the variables are handled through use cases. In such cases, you might want to postpone this to analysis or even just list them as test cases.
If the handling of each variable is generic across use cases, you may want to factor them into a generalized use case. In this way, you avoid being repetitive in your use-case specifications.
Sometimes, how variations are dealt with is dependent on the customer site (e.g., for Hotel Chain ABC or Hotel Chain XYZ). In this case, you may wish to describe them in a separate extension use case containing a number of extension flows that describe the desired behaviors to meet the needs of that customer site.
Identifying these variables is extremely important if you want to build an extensible system because the system will likely be extended on the basis of these variables. For the Hotel Management System example, you might wish to introduce a new customer type, a new reservation scheme, a new reservation channel, and so forth. We discuss how you can design your system to be extensible in Part 4 of the book, specifically in Chapter 13, “Separating Functional Requirements with Application Extension Use Cases.”
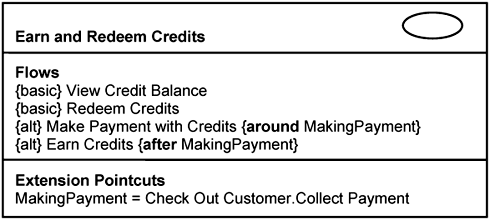
Our use-case model survey in Figure 7-2 shows several extension use cases. Some of these extension use cases are what we call concrete use cases—they can be instantiated separately from the use cases that they extend. Examples are the Handle Waiting List and the Earn and Redeem Credits use cases. We discussed the Handle Waiting List use case in Chapter 6, “Structuring Use Cases.” In this chapter, we discuss the Earn and Redeem Credits use case. Figure 7-4 provides a visual representation of this use case. With this use case, a customer can view the credit she has accumulated. She can also purchase reward items with the credits. These are achieved through the basic flows listed in Figure 7-4.
A customer’s credits can be accumulated only when she makes payment for hotel facilities. This is achieved through the extension flow Earn Credits. The customer can also use credits to pay for the hotel facilities she uses. This is achieved through the extension flow Make Payment with Credits. Recall that extension flows are alternate flows that execute in the context of separate use case—the base use case. The base use case is identified through an extension pointcut. The Earn and Redeem Credits use case has an extension pointcut named MakingPayment. It is used in both extension flows and it is defined to refer to the extension point Collect Payment in the Check Out Customer use case.
As you can see, an extension use case itself can be modeled relatively independently from the use case it extends. Its basic flows are separate from the Check Out Customer use case. The extension flows can be described by referencing to MakingPayment pointcut as an indirect reference to some extension point in another use cases.
The details of the extend relationship between the base and extension use cases needs coordination between the authors of the respective use cases. The interface between the extension and the base use case is expressed in terms of extension pointcuts and extension points. So, there is some coordination between the authors of both use cases to define them (i.e., extension pointcuts and extension points). There are basically two methods of coordination. In the first method, the author of the extension use case lists the pointcuts he or she needs. The author of the base provides a suitable extension point. This is exemplified by the Earn and Redeem Credits use case. You want to provide this loyalty credit capability, and you determine where in which use case additional behaviors are required. In the second method, the author of the base provides a list of extension points. This is useful when you want to handle variations in the base use case, as discussed in the previous section. You can also combine both methods. Once you have clarified the interface between the base and extension use case, both authors can work on them separately.
The indirect reference from the extension pointcut to the actual execution point (the use-case step) in the base use case prevents changes in the base use case to propagate to the extension use case. If at any time the base use case gets modified, it is up to the base author to ensure that the extension point still points to a correct point in the base use case.
Let us now look at how you deal with nonfunctional requirements. Some nonfunctional requirements, such as authorization and transaction management, can be refined and kept separate as infrastructure use cases. As you will see shortly, these can be modeled as extensions to application use cases.
There are also other kinds of nonfunctional requirements that deal with system wide qualities such as performance and reliability. These system wide concerns are described simply as declarative statements during requirements. There are usually several key infrastructure use cases that are used to achieve these qualities, and you need to consider the sum of these infrastructure use cases to determine whether these qualities are met.
We again use the feature list for our Hotel Management System in Listing 7-1 for discussion. Features 8 to 13 are the nonfunctional requirements. To reiterate, these features are:
8. The system has to be Web-enabled.
9. The system will store all records in a relational database.
10. For audit purposes, all transactions in the system have to be logged.
11. Only authorized personnel can perform their functions.
12. To promote ease of use, the system will track the users’ preferences and use them as default.
13. All retrieval of records should take no longer than 2 seconds.
These features affect all use cases identified earlier. If you take a closer look at the features listed above, you find that they affect each step of an application use case. For feature 8, every step in an application use case produces a Web page. For feature 9, each step in an application use case has access to the database. For feature 10, the action at each step is recorded. For feature 11, each step must ensure that the actor instance has sufficient privileges. For feature 12, each step attempts to profile the actor inputs. Finally, for feature 13, each step of an application use case should take no longer than 2 seconds.
As you can see, the features listed above are qualities of the system that are required for each step of an application use case. We call each step of a use case a use-case transaction. It is an actor request-system response pair—the actor does something, the system responds in return. Since the features require additional processing within the basic use-case transaction, you can model them as extensions to this basic transaction.
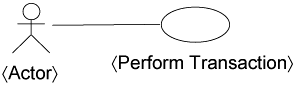
You can model the basic transaction through a 〈Perform Transaction〉 use case, as shown in Figure 7-5. This use case is a pattern—a template bounded to each step of an application use case. We use the angle brackets, 〈 〉, to indicate that both the Actor and the 〈Perform Transaction〉 use cases are parameterized elements.
The 〈Perform Transaction〉 use case collates the infrastructure requirements for the system. This is exemplified in Listing 7-3.
Example 7-3. Use-Case Specification: 〈Perform Transaction〉
Basic Flow
The use case begins when an actor instance performs a transaction to view the values of an entity instance.
The system prompts the actor instance to identify the desired entity instance.
The actor instance enters the values and submits his request.
The system retrieves the entity instance from its data store and displays its values.
The use case terminates.
Alternate Flows
A1. Access Control
If in step 3 of the basic flow the request requires authorization, the system checks the actor instance’s access rights.
If the actor instance does not have access rights, the request is rejected. The use case terminates.
Otherwise, the use case proceeds.
A2. User Preference
In step 1 of the basic flow, if prior preference is defined, the system retrieves the preference and uses those values as defaults for the actor instance’s request. The use case resumes.
In step 2 of the basic flow, if the user indicates that the submitted values will be used as defaults, the system stores the values as the user’s preference.
A3. Logging
In step 2 of the basic flow, the request has to be logged; the system stores the submitted request into the log database.
Special Requirements
All retrieval of records should take no longer than 2 seconds.
The basic flow in Listing 7-3 usually looks simple. The complexity of the 〈Perform Transaction〉 use case lies in the variations it needs to handle, as exemplified by the alternate flows.
We show only three alternate flows in Listing 7-3. In reality, there can be quite a large number of alternate flows, and an experienced architect will want to explore them and track their implementation. The 〈Perform Transaction〉 use case provides a convenient place to document these variations and the context in which they occur. If the 〈Perform Transaction〉 use case needs to deal with too many variations, you can factor out the different concerns into separate extension use cases, as we demonstrate in the next section.
The 〈Perform Transaction〉 use case is a convenient place to model the behavior required to meet nonfunctional requirements of the system. There are nonfunctional requirements that describe the system-level qualities such as that the response time should not exceed 2 seconds (see feature 13). For the time being, you model and express them using declarative statements in the special requirements section of the 〈Perform Transaction〉 use case. This is shown in the Special Requirements section of Listing 7-3.
The 〈Perform Transaction〉 use case is crucial to the architect. It is from this use case that she describes how infrastructure mechanisms are introduced. Expect that there will be different kinds of transactions, some involving the retrieval and displaying of an entity instance, some involving displaying a list of entity instances, and so on. In order for you to systematically extend them, you need to consider the different kinds of transactions that may occur. The use-case-specification technique itself offers a convenient way to describe the different kinds of transactions you have to handle. During analysis, design, and implementation, the realization of the 〈Perform Transaction〉 use case becomes a pattern that is applied to the realization of each application use-case step. Thus, the 〈Perform Transaction〉 use case also helps achieve consistency during analysis, design, and implementation.
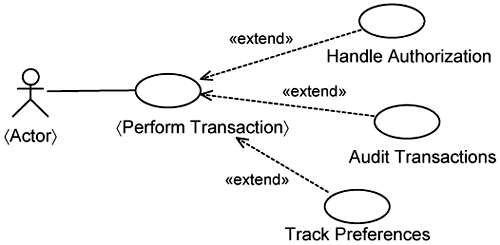
As you explore more variants of the basic flow in the 〈Perform Transaction〉 use case, it will start to grow. For complex systems with many infrastructure considerations, a single 〈Perform Transaction〉 use case will be too large and difficult to manage. You can factor out different alternate flows from the 〈Perform Transaction〉 use case into extension flows in separate extension use cases when they represent a separate, nonfunctional concern. This is depicted in Figure 7-6. These extension use cases—Handle Authorization, Audit Transaction, and Track Preferences—are infrastructure use cases.
Accordingly, you need to identify extension points in the 〈Perform Transaction〉 use case and define pointcuts for each infrastructure use case in Figure 7-6. Treating infrastructure use cases as extensions of the 〈Perform Transaction〉 use case offers many advantages. It helps you visualize the context of infrastructure mechanisms. It serves as a base from which you identify extension points systematically.
From an application standpoint, the 〈Perform Transaction〉 use case serves as a template for realizing each individual use-case transaction. It greatly improves the consistency in naming conventions, structuring, and so on. This makes specifying extension points and extension pointcuts a lot easier.
Now that you have identified the infrastructure use cases, you can describe them individually. Like application use cases, infrastructure use cases frequently have basic flows. The basic flows can be for several purposes:
They can be used to set the conditions for the extension flows. For example, to check authorization, an extension flow must be able to determine which actor is submitting a request.
They can be used to view the information collected by the extension flows. For example, in the Audit Transaction use case, you can view and analyze the logs collected from other use cases.
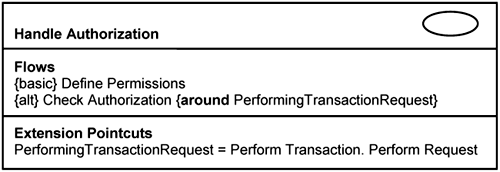
As an example, Figure 7-7 depicts the Handle Authorization use case. It has basic flows for the actors to define access permissions. This information is used to check if the actor is authorized to perform any transaction that arises through any application use cases.
The Check Authorization extension flow executes in the context of some base use-case flows. If the actor has no authorization to perform that request, this extension flow displays some message or notification of possible violations to interested parties.
In Figure 7-7, there is an extension pointcut, PerformingTransactionRequest, which is mapped to the Perform Request extension point in the 〈Perform Transaction〉 use case. This means that you need to identify the extension point in the base 〈Perform Transaction〉 use case. This can be mapped to step 3 of the basic flow in Listing 7-3. However, you need not always define extension points exactly during use-case modeling. The textual description used in use-case specifications is imprecise, and often it is more fruitful to define them during analysis and design. During use-case modeling, you just need to know the existence of the pointcut and roughly where it points to.
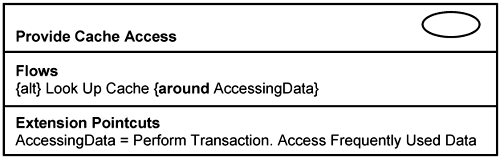
Not all infrastructure use cases are as visible to the users as Handling Authorization, Tracking Preference, and Auditing Transactions, as we described earlier. A number of infrastructure use cases work in the background. For example, to meet the 2-second response, you may have an infrastructure mechanism to describe how you Provide Cache Access of frequently accessed data, as depicted in Figure 7-8.
This use case has an extension flow that looks up a local cache to see if the requested data is available in the cache. If it is available, it returns the data in the cache. Otherwise, it reads from a back-end data store, updates the cache, and returns the data to the requestor.
In Figure 7-8, there is an extension pointcut, AccessingData, which corresponds to Access Frequently Used Data in the 〈Perform Transaction〉 use case. The question is then, What are the frequently used data? This answer will not be found in the 〈Perform Transaction〉 use case. Instead, it will be found in application use cases such as Reserve Room and Check In Customer that use the 〈Perform Transaction〉 as a template. In these application use cases, you can have a special requirements section that lists the frequently accessed data. For example, room rates can be a frequently accessed data.
You may be wondering why stakeholders may be interested in such low-level infrastructure use cases. There can be several possible reasons. First, the local cache might be on the end user’s machine and may have security implications. The cache may contain valuable information that needs protection and cannot be stored in a local cache. This means that cached access is not a viable option. In addition, the end user’s machine may impose size limitations on the cache. The stakeholder may also be interested in how frequently the cache gets refreshed so that the end user may have access to up-to-date data.
The level of detail you need to get into for these infrastructure use cases is very much dependent on what the stakeholder is concerned with. But please do not assume that they are not interested in such infrastructure details at all. Today’s IT departments are usually concerned about such things. They will be more than happy to tell you their infrastructure concerns. Nevertheless, the description of the infrastructure use cases must be refined during analysis when more details are available.
As you have seen, infrastructure use cases are excellent tools for expressing concerns about underlying infrastructure support. Infrastructure use cases help you keep infrastructure services separate. However, not all nonfunctional requirements can be kept separate this way. You will encounter requirements on the overall system characteristics. An example is feature 13. It requires that each step of an application use case should take no longer than 2 seconds. Although you indeed have an infrastructure use case, Provide Cache Access, to help improve response time, it is not enough. To ascertain whether each use-case step indeed takes 2 seconds or less, you must consider a combination of use cases. Recall that infrastructure use cases extend application use cases at each application use-case step. You need to sum up the time taken by each infrastructure use case to determine the total time taken. The use-case diagram in 7-6 tells you which infrastructure use cases you need to sum up. You add up the time spent in Handling Authorization, Auditing Transactions, and Tracking Preferences. If there are potential bottlenecks, you use the Provide Cache Access to improve the response time.
The summing up of response times can be performed by inspection. But to be certain about whether the response time can be met, you need to run some tests. Yes, you need to execute the system. With iterative development, you get an executable early in the project and you can verify the quality of your system. Once you have the test results, you can determine what additional infrastructure use cases you need.
To reiterate, understanding stakeholder concerns is extremely important to building the correct system. Many failures in software development are attributed to poor understanding of requirements. In these situations, you normally find stakeholders and developers walking along different paths and speaking with different assumptions and terms of reference. Both seem to be unable to get their ideas across. For a project to be successful, there needs to be a common vision of what the system must do. With use cases, you can get that common understanding.
There are various types of requirements. Some are functional, some are nonfunctional. But so long as they impose behaviors on the system, use cases will be applicable. You have application use cases to deal with application concerns and infrastructure use cases to deal with infrastructure concerns. Thus, with use cases, you have a common way of modeling crosscutting concerns.
We have stressed the importance of exploring the variations your system needs to handle and a means to describe them. This applies to all kinds of use cases. It is important that you identify such variables and their values early in the project. Otherwise, you miss key requirements and get a rude shock about the perceived scope of the requirements. How these variables are handled can be described with use cases, or they can be postponed to analysis when you refine the use cases.
This chapter introduced the 〈Perform Transaction〉 use case. It describes a pattern for how each step of an application use case is conducted. It provides the context for you to generically describe where infrastructure use cases extend application use cases. As you will see in the subsequent chapters, this 〈Perform Transaction〉 use case is crucial to describe concerns regarding the distribution of the system into different processing nodes, concerns regarding the execution platform, and in fact a wide range of concerns about the architecture in general. Thus, as an architect, you need to pay special attention to this use case.