Identity and access management (IAM) is the process of authenticating and authorizing security principles. Enterprises should govern and configure identity and access management to make sure that services, applications, users, and groups have correct access to data.
Azure Active Directory is an enterprise identity service that provides single sign-on (SSO) , multifactor authentication (MFA) , and conditional access to protect against security attacks.
Identity protocols and application types
Azure Active Directory security model
Active directory federation services
Azure AD Application Proxy
Azure AD B2B and B2C for external partners
PIM Azure AD Identity protection hybrid implementation
Single sign-on with Azure AD
Identity Protocol and Application Types
Microsoft Azure has an identity platform that allows developers to build different types of applications for various business needs. They can create single page applications, web applications, mobile apps, and services.
Single Page Applications
In recent years, web applications have become more popular and so advanced that developers can create sophisticated client applications. These client-side applications are also known as single sided page applications (SPA) .
Let’s look at how to create, configure, and use Azure AD applications to use the data returned from Microsoft Graph with the OAuth 2.0 protocol.
Modern web applications are written in languages like Vue, React, and Angular. The easiest way to use Microsoft Identity for authentication purposes is to obtain access tokens to authorize requests and secure endpoints.

A screenshot displays the Azure active recovery page. The page includes an overview, preview features, and diagnosis, solve problems and manage options. In the manage option, app registration is selected.
Azure AD app registration

A screenshot represents the configure single page application, which contains redirect U R ls, front channel logout U R L, and grant type of Azure A D S P A.
Azure AD single page app configuration
Web Apps with Sign In and API Calling
Developers can use Microsoft Identity to add authentication to a web app and require users to sign in to the web application. Once users are signed in and the user grants consent, the web application will obtain a token from Azure AD and use it to request data from the web APIs . In the second phase, you can enable the application to call the web API on behalf of the single sign-on users.

A screenshot depicts the application client, which contains authorization request, grant, access token, and protected resource as well as user, service A P I of the authorization server, and resource server.
OAuth 2.0 Flow
As shown in Figure 2-3, the application client will create an authorization request to the user or resource owner. Once the resource owner receives the request, it will grant authorization. Clients then accept the authorization using the service API, which will then generate an access token . Based on the access token, the service provider will protect the resource and serve the client request.
The next step is to create a server-side web application that will allow users to sign in and grant the app permission to act on behalf of the end user.

The six model diagrams represent the azure services such as create resource, resource groups, azure A D privileged, log analytics workspaces, azure active directory, and Microsoft sentinel.
Azure Active Directory

A screenshot represents the overview containing preview features, diagnose and solve problems, manage include users, groups, external identities, roles and administrators, and administrative units.
Azure Active Directory app registration

A screenshot represents the overview, diagnose and solve problems, new registration, endpoints, troubleshooting, all, owned, and deleted applications of azure active directory new app registration.
Azure Active Directory new app registration

A flow diagram represents the user, email and password, client I D, secret, username, password, scopes, i d token, access token, refresh token, and link of the authentication flow.
Authentication flow
Authorization server : The Microsoft Identity platform, also known as IdP or the identity provider, handles the end user information, related access, and the relationship between the requestor and server for the authentication flow . The server generates the security tokens to grant, deny, or revoke access to the resources.
Client: In OAuth, clients are generally end users or applications that request access to a protected resource. Clients can be end users or an applications that are requesting access to the resource.
Resource owner : In the authentication flow, the resource owner is typically an end user that owns the protected resources and data on your behalf. For example, if you want to get information from the Azure Active Directory using the Graph API, you can create a service principal in Azure AD with the required permissions to call the graph API to find the relevant information. See Figure 2-8.

A model diagram represents the azure active directory, which contains M S I, function app, Microsoft graph, get access token, and G E T or groups of azure A D graph A P I.
Azure AD Graph API
Resource server : The resource server provides access to the resource’s own data. It is a web API that relies on authorization to perform the authentication from bearer tokens that are issued by the authorization server . This grants the required access to the resources.
Access tokens : Access tokens are generated and issued by the authorization server to the client application. These access tokens contain the permissions that clients have requested to access the specific resources. See Figure 2-9.

A model diagram depicts a client with a refresh and an access token to the A U T H server, as well as a client with a protected resource and an access token to the resource server of web app access tokens.
Access tokens
ID tokens : They are used by the authorization server . When the end users or clients try to sign in, the server will gather basic information about the users to serve the client requests. See Figure 2-10.

The two model diagrams of the I D token depict assert the user s identity or user I D, and the access token represent the optional, to retrieve consented user info.
ID tokens
Refresh tokens : End users and clients use refresh tokens to request new access tokens or ID tokens from the authorization servers . See Figure 2-11.

A model diagram represents the client, authorization server, resource server, refresh token, access token, and protected resource of refresh tokens.
Refresh tokens
Azure Active Directory Security Model
Azure Active Directory plays a very important role in defining the strategy of identity and access management . It helps scale the solution, save on costs, and improve the overall security. Organizations must use a combination of on-premises and cloud-only accounts so that users can access both types of accounts. Managing users, applications, and access on both on-premises and on cloud has major challenges.
Password hash synchronization
Passthrough authentication
Federation
- 1.
Make strong credentials.
- 2.
Reduce areas to attack.
- 3.
Automate the threat response.
- 4.
Use cloud intelligence.
- 5.
Enable self-service.

A screenshot represents the secure score for identity is 40.34 percent, comparison, score history for 7 days, improvement actions, score impact, and user impact of azure A D identity score.
Azure AD identity score
Measure identity security posture
Identify and list security improvements
Measure the success of your security improvements
Let’s now look at the best security practices for Azure AD in detail.
Make Strong Credentials
There are various types of attacks happening that impact your software applications. They can include phishing attacks, consent phishing, and password-based attacks.

A circular model depicts the Azure A D conditional access, which contains I F, THEN, allow access require M F A, force password reset, deny access, limit access, privileged user, user and session risk.
Azure AD security defaults

A screenshot indicates password protection, custom banned passwords enforce custom list is yes or no, enable password protection on windows server active directory is yes or no, and mode of enforced and audit.
Azure AD password protection
Global banned password list
- Custom banned password list
Brand names
Product names
Locations such cities and headquarters
Company-specific internal terms
Abbreviations

A screenshot indicates password protection, custom banned passwords enforce custom list is yes or no, enable password protection on windows server active directory is yes or no, and mode of enforced and audit.
Azure AD password expiration policy

A model diagram represents the password, multiplicator authentication, and logged in of M F A.
Multifactor authentication
Microsoft also provides recommendations for selecting passwords.
Resisting Common Attacks
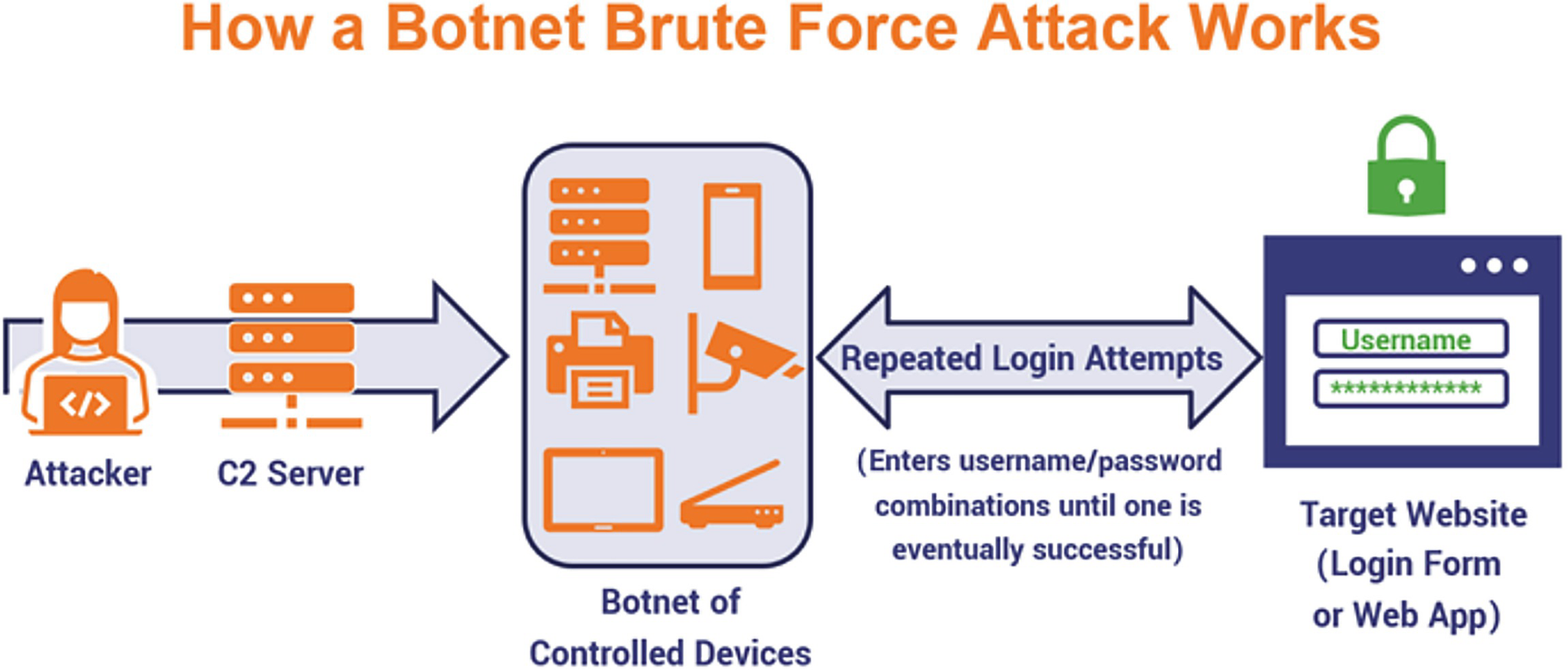
A model diagram depicts the operation of a botnet brute force attack, which includes an attacker, a C 2 server, a botnet of controlled devices, repeated login attempts, and the target website.
Brute force attack
Restrict successful attacks : Resisting a hacker’s attack is about restricting access to a specific service and limiting damage when the user password is stolen. For example, social networking credentials won’t make your bank account vulnerable . Figure 2-18 shows some common cybersecurity attacks .

The six model diagrams represent the malware, D D o S, phishing, S Q L injection attacks, cross site scripting, or X S S, botnets of common cyber security attacks.
Common cybersecurity attacks
Understand human nature: It is very important to understand human nature because the research shows that every rule set on the users will result in better password quality.
- 1.
Go to the Microsoft 365 Admin Center and click the Security and Privacy tab.
- 2.
Select the password expiration policy.
- 3.
If you don’t allow users to set/change passwords , uncheck the box to Set Passwords to Never Expire.
- 4.
Set the password expiration date. Choose a number of days from 14 to 730. See Figure 2-19.

A flowchart of the key steps of a brute force attack. It includes an attacker, a guess list of username and password combinations, and repeats login attempts until one is successful and successful credential validation.
Password expiration policy
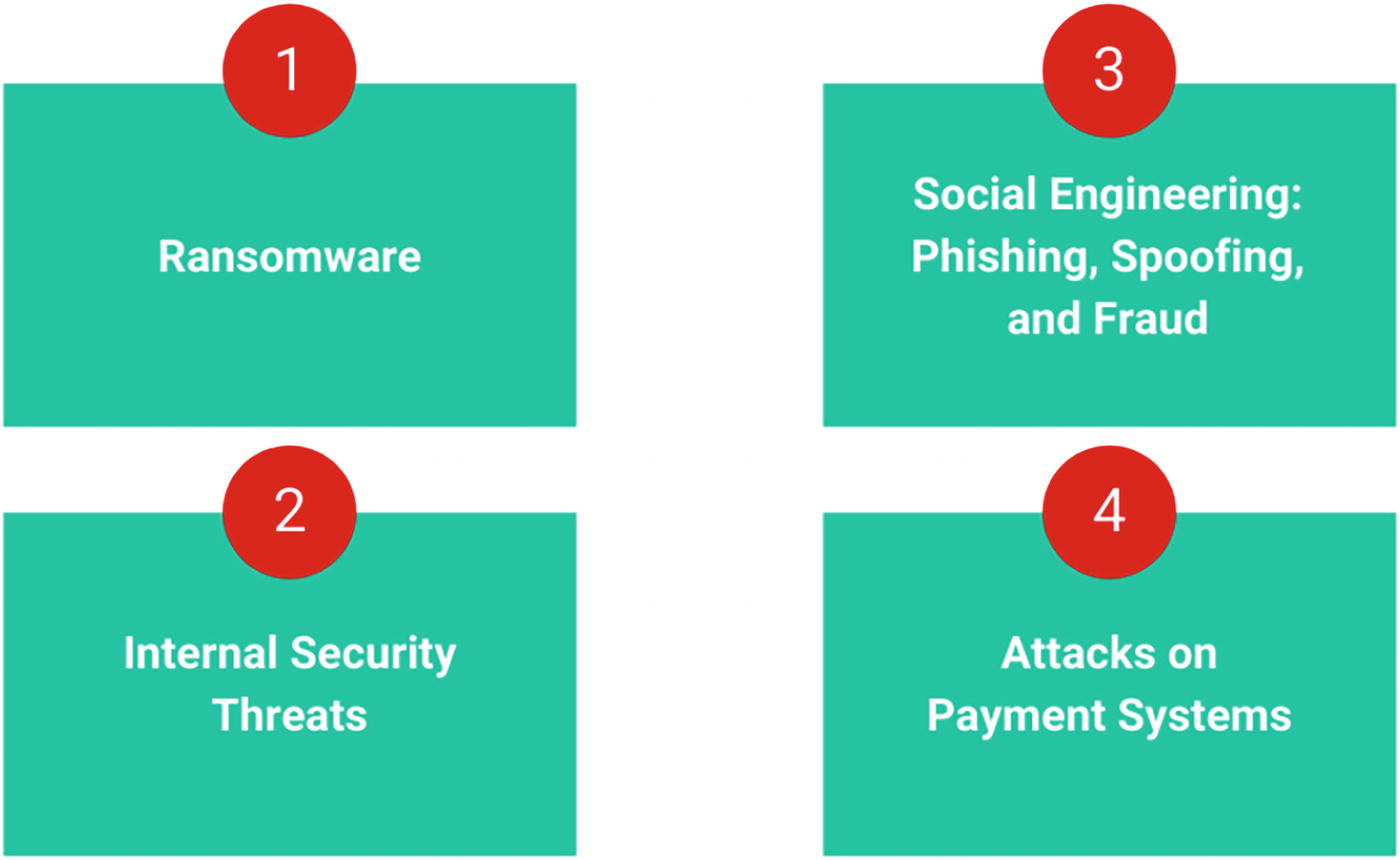
An illustration of password hash synchronization. It includes four types, ransomware, internal security threats, social engineering with phishing, spoofing, and frauds, and attacks on payment systems.
Azure AD Password hash synchronization
Active Directory Federation Services
Active Directory Federation Service is a simplified, secured identity federation . Federation mainly consists of a collection of domains with well-established trust between the entities. It can also include a collection of organizations that have established trust to share information and connections.

A model diagram represents the active directory and A D F S, on premises, azure active directory, L O B apps, office 365, and S a a S apps of azure A D federation service.
Azure AD federation service

The two model diagrams represent the on premises active directory, A D F S, azure A D connect D C 1 on the left and azure active directory on the right.
On-premises Azure AD federation service
Password hash synchronization with seamless single sign-on (SSO)
Passthrough authentication with seamless single sign-on (SSO)
Federated SSO
Federation with PingFederate
- Cloud authentication : Azure AD handles the authentication process using the cloud to sign in to the application. There are two options for cloud authentication:
- Password hash synchronization : Enables users to use the username and password that end users are using on the on-premises server without deploying any additional information. See Figure 2-23.

An illustration of password hash synchronization. It includes an on-premises active directory, password sync, and azure active directory with the user on premise sign on and cloud sign on.
Figure 2-23Azure AD with password hash sync
- Passthrough authentication : This option is similar to password hash sync, but it provides simple password validation using the on-premises software with strong security and compliance. See Figure 2-24.

A flow diagram represents the L D A P client with L D A P bind to open L D A P with S A S l to saslauthd with L D A P search, L D A P bind to the active directory of Azure A D.
Figure 2-24Azure AD with passthrough authentication
As shown in Figure 2-24, with passthrough authentication , it will create a secure channel to Azure Active Directory. Once the secure channel is established, public and private keys are generated using Azure AD and then you can establish the connection to Azure SQL DB. Once the connection is established, certificates are issued.
Federated authentication : With this federation authentication, you can hand over the authentication process to a separate, trusted authentication system, such as AD FS. See Figure 2-25.

A model diagram depicts federated authentication, which includes workflow, an identity provider with trust and a secure token, or an X M L file to a service provider, and a user
Azure AD federated authentication

A screenshot represents the additional tasks, such as a view current configuration, change user sign in, refresh directory schema configuration staging mode, and verify A D F S login.
Azure AD Connect additional tasks
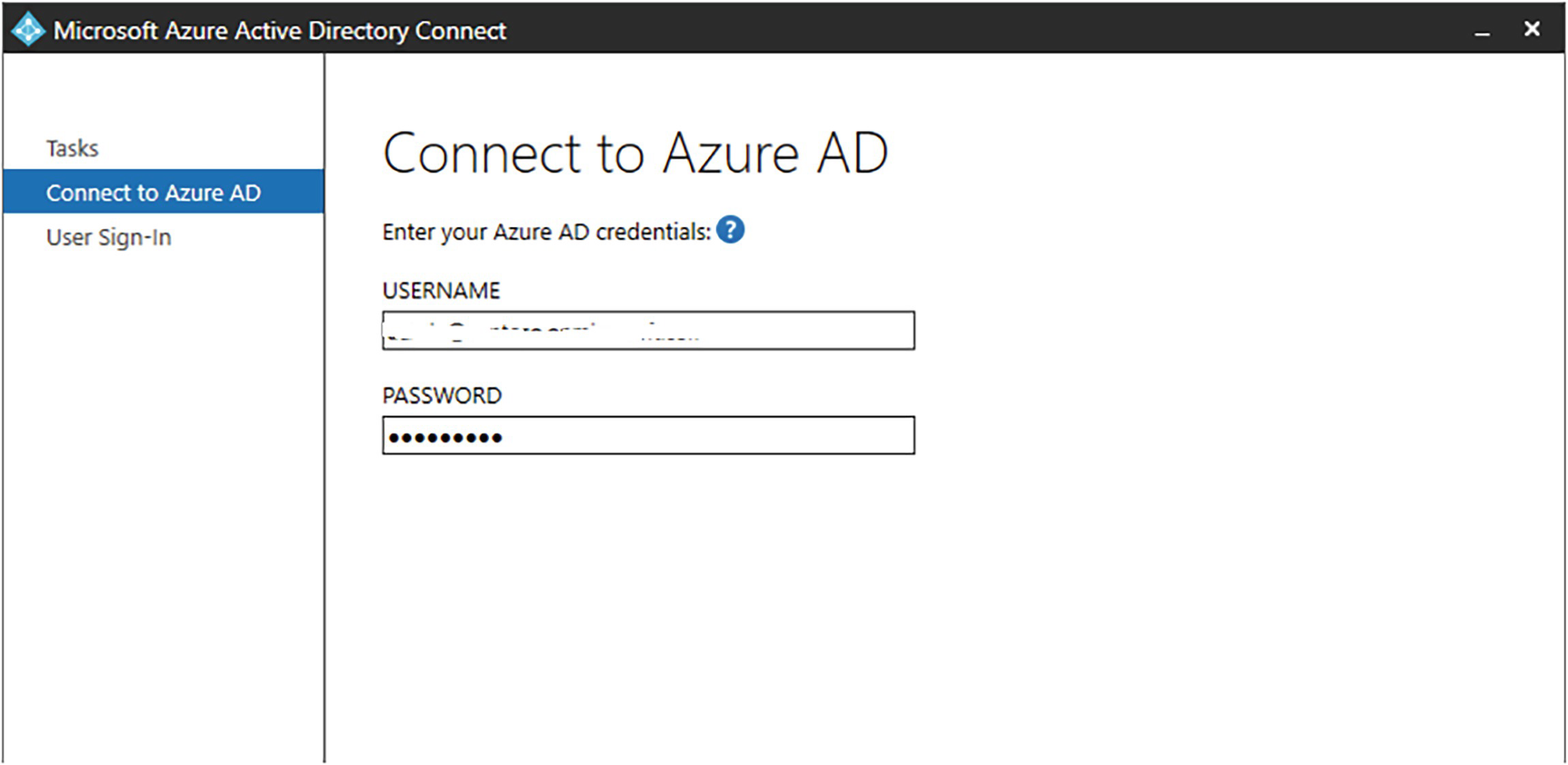
A screenshot represents the tasks, connect to azure A D, and user sign in, which contains entering your azure A D credentials in the below username and password boxes.
Connect to Azure AD

A screenshot depicts the user sign in, which contains select the sign on method, password synchronization, pass through authentication, federation with A D F S, do not configure, and enable single sign on.
Connect to Azure AD
Azure AD Application Proxy

A model diagram represents azure A D application proxy which contains an active directory, H R apps, S a a s apps, cloud hosted apps, and on premises and web apps.
Azure AD Application Proxy
Simple to use: End users can access on-premises applications the same way using Microsoft 365 and other SaaS applications with Azure AD.
Secure: On-premises applications can use Azure’s authorization control and security analytics. For example, an on-premises application can use conditional access and two-step verification or multifactor authentication to make it more secure. Application Proxy doesn’t require an open, inbound connection using the firewall.
Cost-effective: You don’t have to change the network infrastructure or install any additional software in order to use Azure AD Application Proxy.
Azure AD Application Proxy is a feature of Azure AD that accesses on-premises web applications from a remote desktop/client. It includes Application Proxy, which runs in the cloud, and the Application Proxy connector , which runs on the on-premises server.
Access to the applications from the Remote Desktop Gateway
Rich client apps with the Microsoft Authentication Library
Web applications using header access
Application Proxy is recommended for giving remote users access to internal resources. It replaces the need for a VPN or reverse proxy and it is not needed by the internal users of the corporate world or an enterprise company.
Figure 2-29 shows Azure AD and Application Proxy working together to provide a single sign-on to on-premises applications .

A model diagram represents the H T T P S, publish to D N S open firewall, multi factor authentication, azure active directory, work account, internet, on premises, and azure A D app proxy connector.
Azure AD Application Proxy with conditional access
Application Proxy Service: It runs in the cloud.
Application Proxy Connector: It runs on the on-premises server.
This service and connector interact to securely transmit the user sign-on tokens from Azure AD to the web application.
It handles web application using Windows authentication for form-based access
It supports applications protected by Remote Desktop Gateway
It provides remote users with access to an internal resource without using the reverse proxy or virtual private network. Azure AD Application Proxy is only available with a premium license. See Figure 2-31.

A flow diagram represents the user, azure active directory, D M Z contains connector with apps 1, 2, and 3 of on premises of azure A D application proxy.
Azure AD Application Proxy with on-premises
- 1.
Once users have access to the application using the endpoint, Application Proxy directs them to the Active Directory sign-in page. When the conditional access policies are enabled, it will check for the conditions and comply with the security requirements.
- 2.
If the sign-in is successful, Azure Active Directory will transfer the AD token to the client’s device.
- 3.
The client will then transfer the token to Application Proxy and access the token's security principal.
- 4.
Application Proxy then sends the request to the Application Proxy connector .
- 5.
Connectors then carry out authentication steps, which will then send the requests to the application's internal endpoint and forward the request to the application.
- 6.
Connectors then forward the application’s server response to Application Proxy.
- 7.
Application Proxy then transfers the server’s response to the user.
Exploring Azure AD B2B and B2C for External Partners

A model diagram represents the azure A D B 2 B, which contains PowerShell, graph A P I in that Microsoft azure and azure active directory.
Azure AD B2B
- 1.
The end user will receive an email with the link to accept the invitation.
- 2.
Authentication will happen at the right place once you click the link.
- 3.
A trust relationship is established in the background without any configuration.
- 4.
The entered credentials will be saved in a guest directory.
- 5.
Access control is then managed in a host directory.
Personal email invitation: Access packages (Individuals apply for access using an automated verification process.)
Self-service user flows: Bulk invite via CSV upload.

A flow diagram represents the authentication experience, azure active directory, client, your website, and back office of azure A D B 2 C.
Azure AD B2C

The five model diagram represents the azure A D B 2 C flow which contains accept our T and C s, prove who you are, set up a password, set up M F A, and access your documents.
Azure AD B2C flow
To make this possible, Azure AD B2C needs to verify the customer’s identity using an API call.
PIM Azure AD Identity Protection Hybrid Implementation

The two triangles depict your directory and home directory, which contain resources, member users, and external users.
Azure AD Privileged Identity Management
Enables just-in time access to Azure AD and resources
Assigns timely access to resources using the start and end data
Requires additional approval to activate the roles
Uses multifactor authentication to activate the roles
Conducts access reviews for user roles
Exports the audit history for the internal and external audit

The six model diagrams depict the just in time access, workflow, justification, and notification, conduct access reviews, enforce M F A for role activation, and prevent removal of the last active global.
Just-in time access
Attackers or end users who perform brute force attacks on the entire system and find a way to steal information
Unauthorized users being able to access data and resources by deleting, updating, or inserting data

The three model diagrams represent the account administrator, service administrator, and co administrators of azure A D P I M roles.
Azure AD PIM roles
Account administrators
Service administrators
Co-administrators
Eligible roles: This is the type of role assignment where the end user needs to perform actions to activate and use the role. Once the actions are completed, the role types change from eligible to active. Once users are eligible for the role, they can activate the role using a privileged activity. See Figure 2-38.

A screenshot represents my roles, azure resources, eligible, active, and expired assignments, and eligible assignments containing role, resource, resource type, and membership.
Azure AD privileged
Active roles: Role assignment that doesn’t require users to perform an action using privileged roles. See Figure 2-39.

A screenshot represents my roles, azure resources, eligible, active, and expired assignments, and active assignments containing role, resource type, membership, and condition.
Azure AD PIM active assignments
Let’s now look at the license requirements for users.
PIM Admin

A flow diagram depicts the azure A D P I M admin, which contains eligible members, requests to activate a specific role, approve the user, become a full member of the role, and removed from a role at expiration time.
Azure AD PIM admin
Approvers
These are users who have the authority to approve or deny the role assignment requests using the PIM.
Access Reviewers
These users have been assigned the role to perform access reviews of the privileged role assignments to the users via PIM-eligible roles.
Single Sign-on with Azure AD
The Azure Active Directory single sign-on (SSO) feature allows users to sign in automatically when their corporate devices are connected to the enterprise corporate network. Once single sign-on is enabled for Azure AD, it allows users to sign in without entering their passwords and usernames.
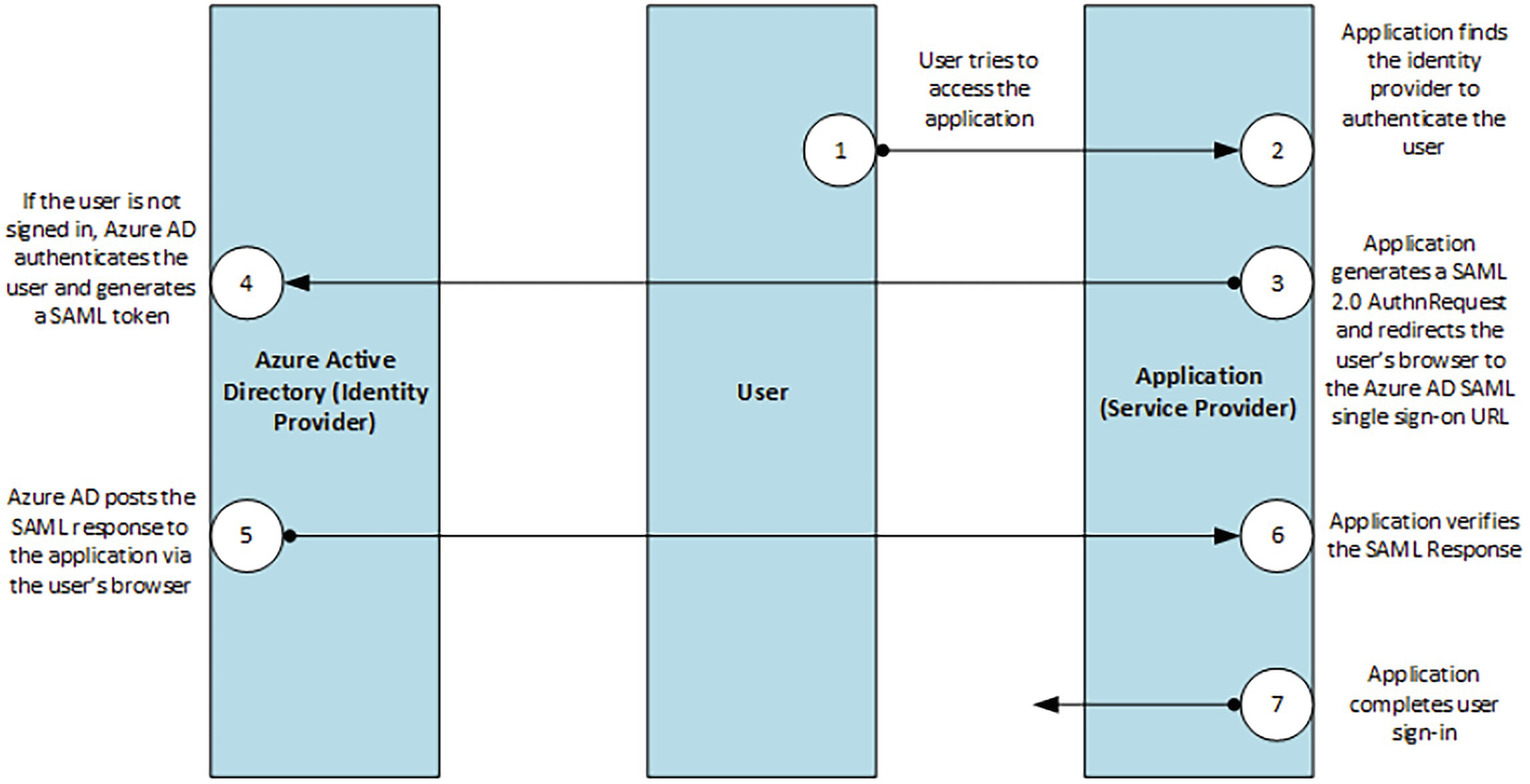
A model diagram depicts the single sign on S A M K protocol labeled as 1 through 7, which is the user tries to access the application, service provider, user, and azure active directory.
Single sign-on SAML protocol
SAML 2.0 sends authentication requests and responses to Azure AD using SSO. The cloud service uses HTTP redirection to pass the element to Azure AD. Azure AD then uses HTTP post binding to respond to the cloud service.
- 1.
Log in to the Microsoft Portal using the following URL: https://portal.azure.com .
- 2.
Click the Azure Active Directory and select Manage Applications under the Manage tab. See Figure 2-42.

A screenshot represents the azure service, which contains create a resource, azure active directory, azure A D privileged, resource groups, log analytics workspaces, and recent resources.
Azure Active Directory
- 3.
Click New Application and choose Create the Enterprise Application. See Figure 2-43.

A screenshot of the enterprise applications of azure active directory contains new applications, refresh, preview info, applications found in that name, object and application I D, the home page, and enterprise applications.
Azure Active Directory - Enterprise Applications
- 4.
Open the enterprise application. From there, you can configure the application based on the required settings . See Figure 2-44.

A screenshot represents the enterprise applications, which contains an overview, new application, refresh, download, manage, and search by application name or object I D.
Azure Active Directory - Create Enterprise Applications
Conclusion
This chapter explored various identity protocols and their application types. You also learned about the Azure Active Directory security model and explored the Active Directory federation service and Azure AD Application Proxy, which is used to connect cloud applications with on-premises applications. You also learned about Azure AD B2B and B2C, which are for external partners using Azure AD. The chapter also quickly walked through the PIM implementation and its features using Azure AD and a hybrid implementation. In the end, you explored the single sign-on implementation using Azure AD.
