Organizations typically focus on building applications and data-driven software to harvest value from their data. To create secure and reliable applications, setting up an infrastructure is a must. Security configurations must be done correctly in order to ensure that the applications function correctly, without any vulnerabilities or security concerns.
The previous chapter explored the infrastructure security patterns and discussed how to set up public cloud resources.
Physical security
Built-in Azure security controls
Azure Tenant Security
Container security
Securing Azure resources
Physical Security
When you use public cloud platforms like Azure, the Microsoft Azure team has to secure the data centers and resources used in the background for the IaaS, PaaS, and SaaS services.
These data centers and resources should comply with industry standards to maintain the security and reliability of the application. Managing and maintaining these data centers and resources is handled by the Microsoft operations staff in the background, so customers can continue their work without the headaches of configuration, management, and maintenance.

An illustration of the Azure regions worldwide with a cloud background. Microsoft Azure has a large number of regions across the world represented in a circular diagrammatic network.
Azure regions worldwide
Azure regions are organized into geographies. This ensures that the data residency and the compliance requirements are honored with respect to the geography and the regions. These geographies are also fault tolerant, in case of any failures in the region, with dedicated infrastructure.
Each Azure region consists of availability zones. Availability zones are physical, separate locations within an Azure region. Each availability zone consists of multiple data centers with cooling, networking, and compute capabilities.

A model depicts data residency boundary for regions 1 and 2, which includes availability zone 1, 2, and 3.
Azure regions and availability zone
Physical security reviews : For a public cloud, you have to periodically perform a physical security review to address the Azure security requirements. End users don’t have physical access to the Azure services and data centers where the Azure resources reside.
Data bearing devices : Microsoft uses best practices and various industry standard procedures to handle the data-bearing devices. There might be various hard drives that can’t be wiped.
Compliance : The Microsoft Azure infrastructure also has a set of international compliance standards, such as ISO 27001,HIPAA, SOC 1, and SOC 2.
Let’s explore in detail the built-in Azure security controls.
Built-in Azure Security Controls
While using a public cloud service , it is very important for enterprise organizations to know about the shared responsibility between the cloud customer and the public cloud offerings. Public clouds have three types of services: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Responsibility for these services differs based on the type of service you choose.
Data
Endpoints
Account
Access management
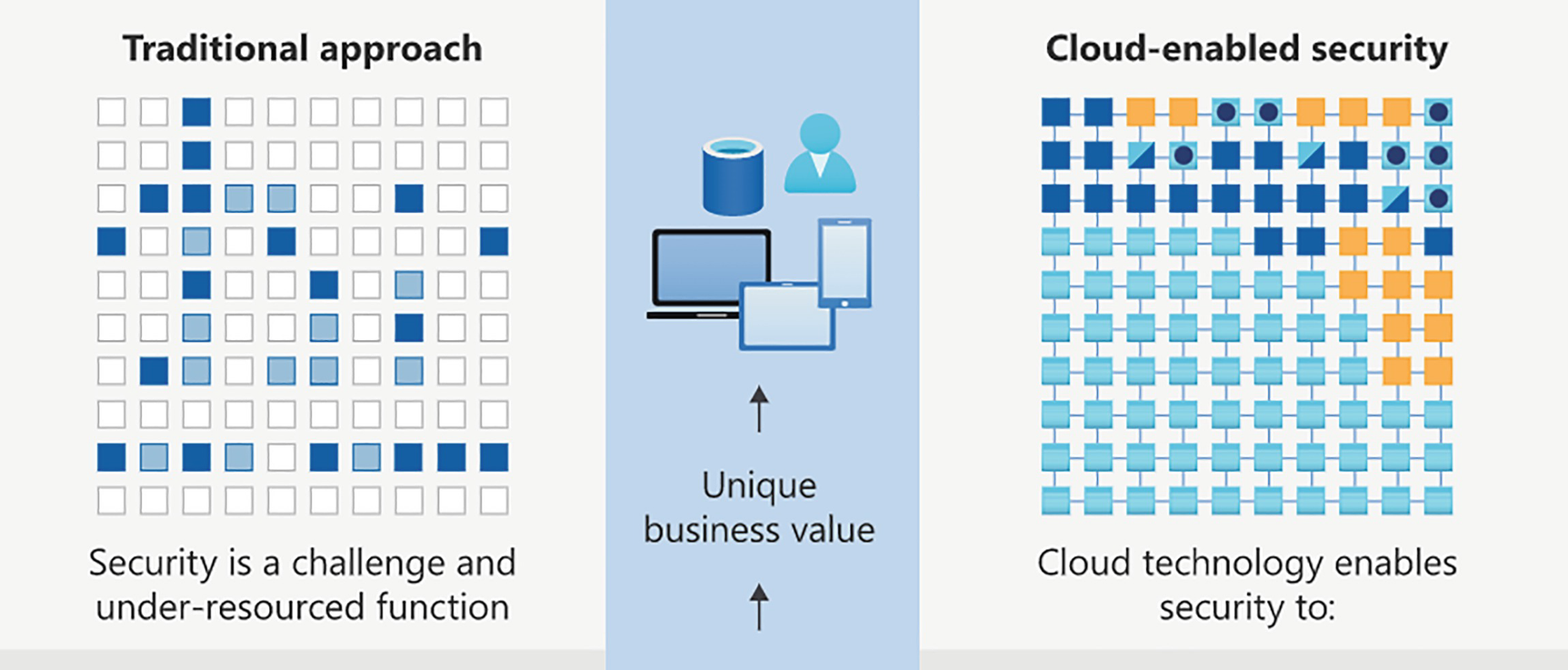
Three models depict the traditional approach to security as a challenge and under-resourced function, unique business value, and cloud-enabled security with cloud technology enabled with security.
Shared responsibility: traditional vs cloud
Azure platform : With the Azure cloud platform , you can select from a range of operating systems, programming languages, frameworks, databases, and tools. See Figure 4-4.

An illustration of the physical security system functions in the Azure platform. It includes three levels, detect, delay, and respond.
Azure platform security
Azure Resource Manager : With Azure Resource Manager, you can work with resources to deploy, update, and delete all resources in the application. See Figure 4-5.

A model depicts Azure portal, PowerShell, C L I, and R E S clients for S D Ks with respect to Azure Resource Manager with authentication and also includes a data store, web app, virtual machine, service management, and other services.
Azure Resource Manager
Application Insight: With Application Insight , you can monitor applications when they are running as well as during testing and deployment. You can create charts and tables to find out more about how responsive the application is or to determine the overall performance of the application. See Figure 4-6.
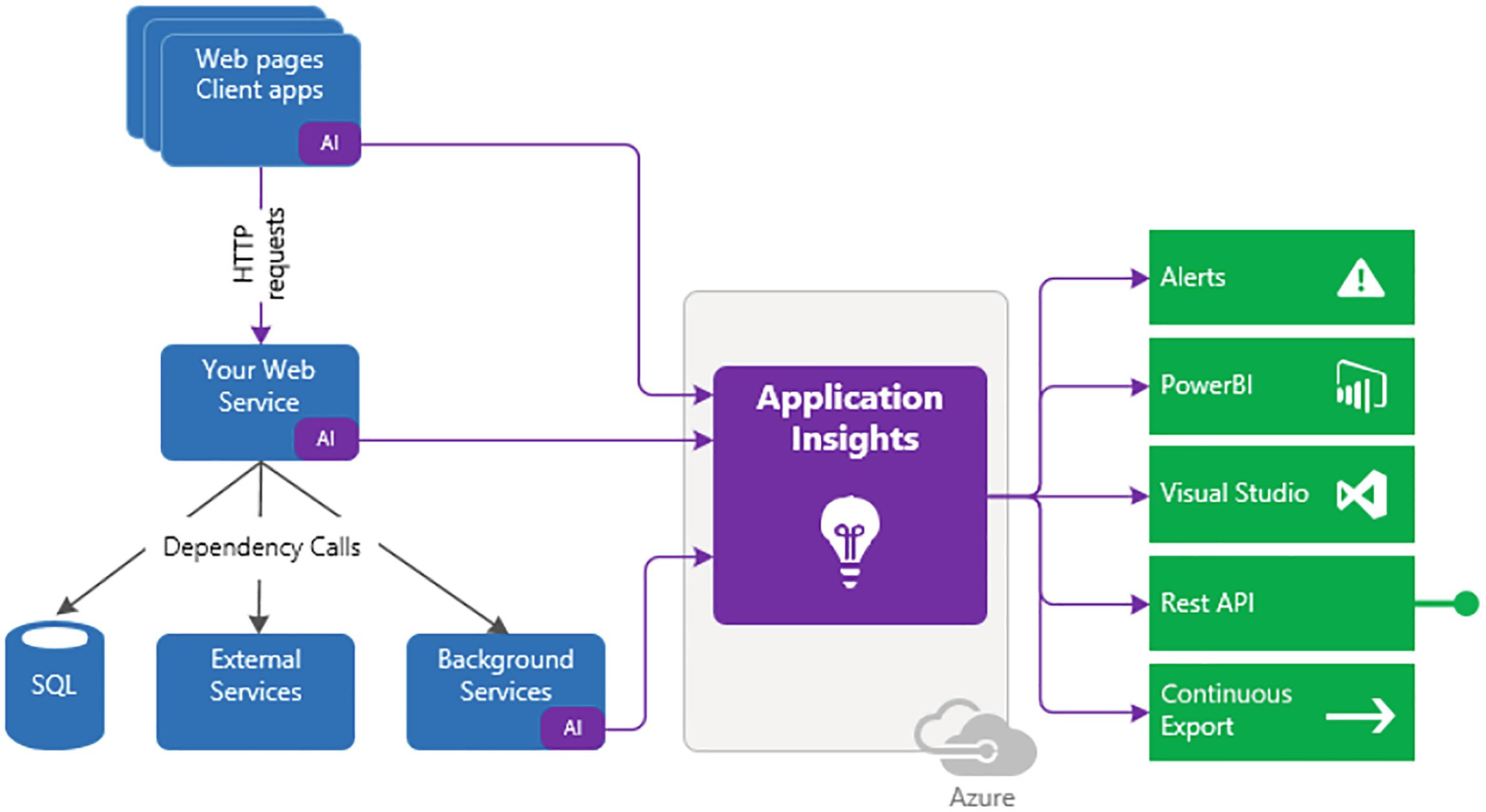
A model depicts web pages, client apps, web service, S Q L, external services, and background services leads to application insights that result in alerts, power, visual studio, rest A P I, and continuous export.
Application Insight
Azure Monitor Logs : These provide an IT management solution for on-premises as well as other cloud providers like AWS, Azure, and so on. They can be used to perform security as well as forensic logs. See Figure 4-7.

A model represents windows agent of event log result to event data, the event I D, event level, event log, rendered description, and event records in the event table.
Azure Monitor Logs
Azure Advisor : This is a personalized cloud service within Azure that’s used to determine and optimize the security, cost, and performance of your cloud workload. Azure advisor uses configurations and telemetry to improve overall security, performance, reliability, and cost of applications as well services. See Figure 4-8.
A screenshot represents the cost management, which includes cost analysis, cost alerts, budgets, insights, alerts, metrics, logs, and recommendation status is active.
Azure Advisor recommendations
As shown in Figure 4-9, you can look into the cost, security, reliability, and performance as well as operational excellence recommendations from Azure Advisor.

A screenshot represents the overview and advisor score of cost, security, reliability, operational excellence, performance, and all recommendations.
Azure Advisor Recommendations categories

A screenshot depicts advisor security, which includes a search button, feedback, download as C S V, download as P D F, and tries the new.
Azure Advisor security recommendations
Web application firewall (WAF) : With a web application firewall, you can protect your web applications from common attacks such as SQL injection, cross-site scripting (XSS), and session hijacking. It also helps enterprise organizations follow layered security approaches to make the application more secure and safe. Azure web application firewall on Azure application gateway provides protection from the web applications using the common security vulnerabilities. They target the attacks happening on the cloud resources and act based on the core rule set from the open web application security project. It operates as an application delivery control and provides a Transport Layer security layer, which was earlier known as the secure socket layer . This includes policy management and E2E TLS support. See Figure 4-11.

A model diagram represents the azure web application firewall, which includes an application gateway through valid requests to site 1 and site 2.
Azure Web Application Firewall
A layered security architecture incorporates the pros and cons of various security products. With layered security, you can put multiple security controls into the IT environment. A fundamental component of layered security is the perimeter of defense for traffic from the network. The Azure app service environment provides an isolated runtime environment that’s deployed in the Azure Virtual Network . The major goal is to hide the API backends from Internet access. With Azure Virtual Network, you can also use Network Security Groups (NSGs) to allow or deny inbound or outbound traffic to and from the website and web application. You can also use private endpoints to restrict public access to the same.

A layered security architecture depicts mission-critical assets, data security, application security, endpoint security, network, perimeter security, and the human layer.
Layered security architecture
Let’s now look at the Azure Tenant Security concepts.
Azure Tenant Security

A text document represents the azure A D tenant boundary, which includes directory, administration, configuration, Microsoft services, apps, and object options.
Layered security architecture
With the Azure Tenant Security solution, you can scale efficiently and use less overhead to get the same level of visibility. It is also designed to accelerate migration to Azure security offerings such as Policy, Security Center, Management Groups, and Azure Resource graphs. .
- 1.
Download the PowerShell script from GitHub at:
https://github.com/azsk/AzTS-docs/blob/main/TemplateFiles/DeploymentFiles.zip?raw=1
- 2.
Open the folder in Windows Explorer and then open the ExecutionScript.ps file using the PowerShell IDE. See Figure 4-14.

A text document depicts the deployment script, which includes this P C, downloads, deployment files opened tabs.
Deployment script
- 3.
Now, change the information for $TenantId. You can get the information from the Azure Active Directory. See Figure 4-15.

A text document depicts the azure active directory, which includes this P C, downloads, deployment files opened tabs.
Azure Active Directory
- 4.
Once the details are up to date, execute the script that will create the Azure services, as shown in Figure 4-16.
A text document depicts the azure services tenant security, which includes this P C, downloads, deployment files opened tabs.
Azure services
- 5.
Even though the services have been created, when you open the web app, the data is still blank . Be sure to execute this PowerShell command:
- 6.
Once that command is executed, it will open the web page shown in Figure 4-17.

A webpage of the Azure tenant security with lists of files. The page is opened once the Powershell command is executed.
Azure Tenant Security
Azure Tenant Security can be used to obtain visibility of cloud subscriptions across multiple subscriptions in the organization. It is a DevOps kit that helps you move closer to the implementation of cloud security compliance on the Azure platform.
Scan multiple subscriptions with a central scan tool in a cheaper and more timely manner
Auto-scale without any external constraints
Speed up the effort of native features
Enable incremental transition to the controls for custom code
Let’s take a quick tour of container security.
Container Security

A model diagram depicts the K 8 security checklist with three dots at the top and five checkboxes with dotted lines.
K8 security checklist
Enable Kubernetes with role-based access control (RBAC) : With RBAC, you can define permissions and determine who can access the Kubernetes API and related permissions at a granular level. Kubernetes combines the authorization controllers so it is better to disable the legacy attribute based access control. It is advisable to avoid granting cluster-level permission, even during troubleshooting. See Figure 4-19.

A model diagram depicts role-based admin control from users to the permissions granted.
Role-based access control
Keep Kubernetes up to date : As it is open source, Kubernetes has many contributors. Thus, it is important to stay up to date with the latest version, considering the security vulnerabilities and related updates.
Integrate Kubernetes with third-party authentication: You can integrate Kubernetes with third-party tools, such as GitHub, for authentication. These tools provide additional security features like multifactor authentication, and so on.
Limit direct access to the Kubernetes nodes: Limit SSH access to the Kubernetes nodes to avoid the risk of unauthorized access. You can also use Kubernetes authorized plugins to control user access to these resources.
Set up administrative boundaries: You can create a Kubernetes namespace to partition the resources into logical groups. Resources created in one namespace won’t be accessible to another namespace. You can even create policies to separate access between the namespaces.
Enable network isolation: Running multiple applications on a Kubernetes cluster runs the risk of one application interfering with another. Therefore, network isolation is important to ensure containers can only communicate with appropriate containers. See Figure 4-20.

A model diagram depicts the K 8 network isolation, which includes two teams, a platform team, and a product team with various companies x, y, and various services.
K8 network isolation
Enable security context for pods and containers: While designing containers and pods, it is advised to configure the security context for the pods, containers, and volumes. You can define security context properties in the YAML format. See Figure 4-21.

A model diagram depicts the node, pod, volume, containerized app, and node process enclosed in a hexagonal structure.
Node, pod, volume and node process
Enable Kubernetes cluster logging: Enable logging for all cluster-related activities. You can also integrate the output of cluster logs with tools like Google Stackdriver logging or ElasticSearch.
Secure secrets: Kubernetes cluster secrets contain sensitive information such as passwords, tokens, and SSH keys. Kubernetes supports encryption to ensure communication between the API servers is protected with TLS/SSL. It is also recommended to frequently rotate secrets to make it harder for attackers to gain unauthorized access to the cluster.
Protect etcd with TLS, firewalls, and encryption: etcd stores the state of the cluster and confidential information in the form of secrets. It contains all the confidential information and is the highest-value target for attackers. If unauthorized users get access to etcd, the entire cluster is vulnerable to security attacks. See Figure 4-22.

A model diagram represents the e t c d multi-Tenant, which contains clusters 1, 2, and N of e t c d container security.
etcd
Set up process whitelisting: Whitelisting is an effective way of identifying unexpected running processes. For this, you first need to understand the overall application behavior over a period of time. Then, use this pattern/list to whitelist the workload to the Kubernetes cluster . It is also difficult to do runtime analysis at the process level, but there are various solutions available in the market that minimize the overhead.
Lock Kubelet: Kubelet is basically an agent that runs on each cluster node that interacts with the container runtime to launch the pods. Various configuration options are available to lock Kubelet to improve the overall security of the cluster.
Disable anonymous access with --anonymous-auth=false: Unauthenticated requests won’t be able to access the cluster and they will get an error response.
Set --authorization mode: It is recommended to set the value for this variable to AlwaysAllow to verify that requests are authorized.
Set --read-only-port=0: This configuration will enable read-only ports to prevent anonymous users from accessing information about running workloads.
Let’s now look at how to secure Azure resources.
Securing Azure Resources
When you use a public cloud like Azure, deploying services and components is very easy and flexible. Before deploying the cloud application in the production environment, you have to make sure that the application follows the checklist for all the operational security requirements.
Azure Role-Based Access Control (RBAC) : Azure has various built-in roles to provide end users with the required permissions to the users, groups, or service principles. See Figure 4-23.

A model diagram represents the sales as a customer database, finance as payroll, and engineering as the codebase of the role-based access control.
Role-based access control
Data storage : In order to access and authenticate the data stored in the storage account, you can use the shared access signature (SAS) . See Figure 4-24.

A model diagram depicts the data storage schema of Microsoft Azure Storage.
Data storage
You can also use the TLS (Transport Layer Encryption) with HTTPS for Azure File shares. You can also use client-side encryption to secure the data sent to the storage accounts. This can be controlled with encryption keys. For Azure Virtual machines, you use Azure disk encryption to store the data. You can use the Storage Service Encryption to encrypt the data stored on the disk and data files.
Using the Azure storage analytics , we can monitor the authorization type based on the storage account keys or shared access signature. See Figure 4-25.

A flow diagram depicts disk encryption. which includes disk encryption, managed disks, active directory, and Azure key vault.
Disk Encryption with SSE
Identity and Access Management : The first step is to sync your on-premises active directory with Azure Active Directory. You can also use single sign-on to enable access to the SaaS applications based on the accounts in Azure. You can also enable multifactor authentication for users to make authentication and authorization more secure. Using Azure AD premium, you can actively monitor suspicious activities. See Figure 4-26.
Instead of using personal accounts, developers can use applications like Microsoft software development lifecycle.

A model diagram depicts access management, which includes authentication, authorization, user management, and a central user repository.
Identity and access management
Conclusion
This chapter explored how cloud providers use and manage public security of their infrastructure. In addition to this, you also took an in-depth tour of the built-in security controls available on the Microsoft Azure cloud. You also learned about Azure Tenant Security, with a step-by-step guide, and learned how to follow best practices to improve container security. Finally, you explored the security controls available in Azure’s services and resources.
