One of the hottest technologies of late is Blockchain. But what exactly is a blockchain? And how does it actually work? In this chapter, we will explore the concept of blockchain, how the concept was conceived, and what problems it aimed to solve. By the end of this chapter, the idea and motivation behind blockchain would be crystal clear.
Tip
For the clearly impatient – A blockchain is a digital transaction of records that’s arranged in chunks of data called blocks. These blocks link with one another through a cryptographic validation known as a hashing function. Linked together, these blocks form an unbroken chain – a blockchain. A blockchain is programmed to record not only financial transactions but virtually everything of value. Another name for blockchain is distributed ledger.
Hold on tight, as I’m going to discuss a lot of concepts in this chapter. But if you follow along closely, you’ll understand the concepts of blockchain and be on your way to creating some really creative applications on the Ethereum blockchain in the upcoming chapters!
Tip
Ethereum is an open-source public blockchain that is similar to the Bitcoin network. Besides offering a cryptocurrency known as Ether (which is similar to Bitcoin), the main difference between Bitcoin and itself is that it offers a programming platform on top of the blockchain, called Smart Contract. This book focuses on the Ethereum blockchain and Smart Contract.
Motivations Behind Blockchain
Most people have heard of cryptocurrencies, or at least, Bitcoin.
Note
The technology behind cryptocurrencies is blockchain.
To understand why we need cryptocurrencies, you have to first start with understanding a fundamental concept – trust. Today, any asset of value or transaction is recorded by a third party, such as bank, government, or company. We trust banks won’t steal our money, and they are regulated by the government. And even If the banks fail, it is backed by the government. We also trust our credit card companies – sellers trust credit card companies to pay them the money, and buyers trust credit card companies to settle any disputes with the sellers.
Placement of Trusts
All these boil down to one key concept – placement of trust . And that is, we place our trust on a central body. Think about it, in our everyday life, we place our trusts on banks, and we place our trusts on our governments.
Even for simple mundane day-to-day activities, we place our trusts in central bodies. For example, when you go to the library to borrow a book, you trust that the library would maintain a proper record of the books that you have borrowed and returned.
The key theme is that we trust institutions but don’t trust each other. We trust our government, banks, even our library, but we just don’t trust each other. As an example, consider the following scenario. Imagine you work at a cafe, and someone walks up to you and offers you a US ten-dollar bill for two cups of coffee. And another person who offers to pay you for the two cups of coffee using a handwritten note saying he owes you ten dollars. Which one would you trust? The answer is pretty obvious, isn’t it? Naturally you would trust the US ten-dollar bill, as opposed to the handwritten note. This is because you understand that using the ten-dollar bill, you can use it elsewhere to exchange for other goods or services, and that it is backed by the US government. In contract, the handwritten note is not backed by anyone else (except perhaps the person who wrote it), and hence it has literally no value.

Currencies from two countries
Would you accept the currencies as shown in the figure? Here, you have two different currencies – one from Venezuela and one from Zimbabwe. In this case, the first thing you consider is whether these currencies are widely accepted and also your trust in these governments . You might have read from the news about the hyperinflation in these two countries, and that these currencies might not retain its value over time.
And so, would you accept these currencies as payment?
Trust Issues
Earlier on, I mentioned that people trust institutions and don’t trust each other. But even established economies can fail, such as in the case of the financial crisis of the United States in 2007–2008. Investment bank Lehman Brothers collapsed in September 2008 because of the subprime mortgage market. So, if banks from established economies can collapse, how can people in less developed countries trust their banks and governments? Even if the banks are trusted, your deposits may be monitored by the government, and they could arrest you based on your transactions.
As we have seen in the example in the previous section, there are times when people don’t trust institutions, especially if the political situation in that country is not stable.
All these discussions bring us to the next key issue – even though people trust institutions, institutions can still fail. And when people lose trust in institutions, people turn to cryptocurrencies . In the next section, we will discuss how we can solve the trust issues using decentralization, a fundamental concept behind cryptocurrency.
Solving Trust Issues Using Decentralization
Now that you have seen the challenges of trust – who to trust and who not to trust, it is now time to consider a way to solve the trust issues. In particular, blockchain uses decentralization to solve the trust issue.
In order to understand decentralization, let’s use a very simple example that is based on our daily lives.
Example of Decentralization
To understand how decentralization solves the trust issue, let’s consider a real-life example.

Sharing DVDs among a group of people
The first thing they need to do is to have someone keep track of the whereabouts of each DVD. Of course, the easiest is for each person to keep track of what they have borrowed and what they have lent, but since people inherently do not trust each other, this approach is not very popular among the three persons.
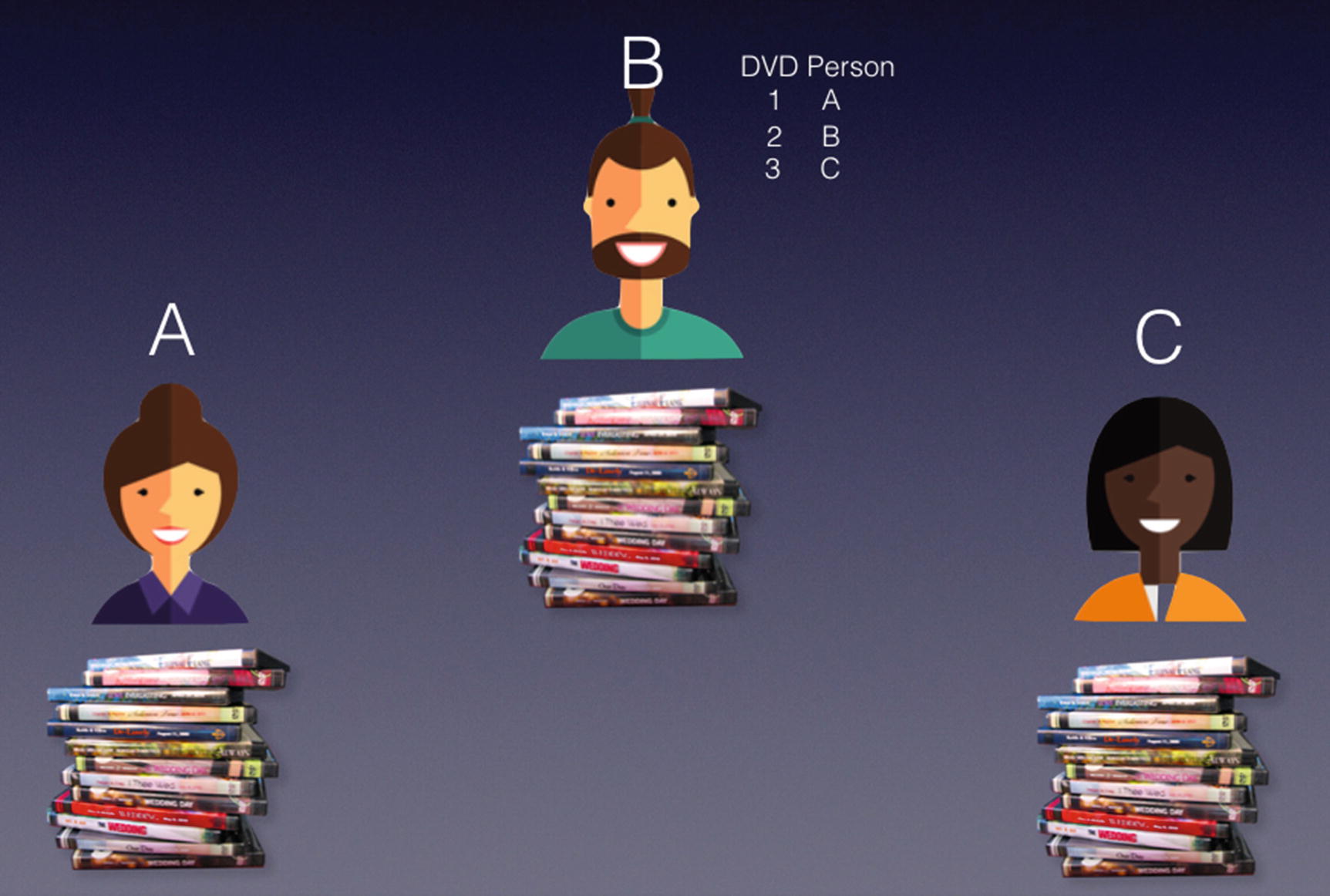
Appointing a particular person to keep the records
This way, there is a central body to keep track of the whereabouts of each DVD. But wait, isn’t this the problem with centralization? What happens if B is not trustworthy? Turns out that B has the habit of stealing DVDs, and he in fact could easily modify the ledger to erase the record of DVDs that he has borrowed. So, there must be a better way.
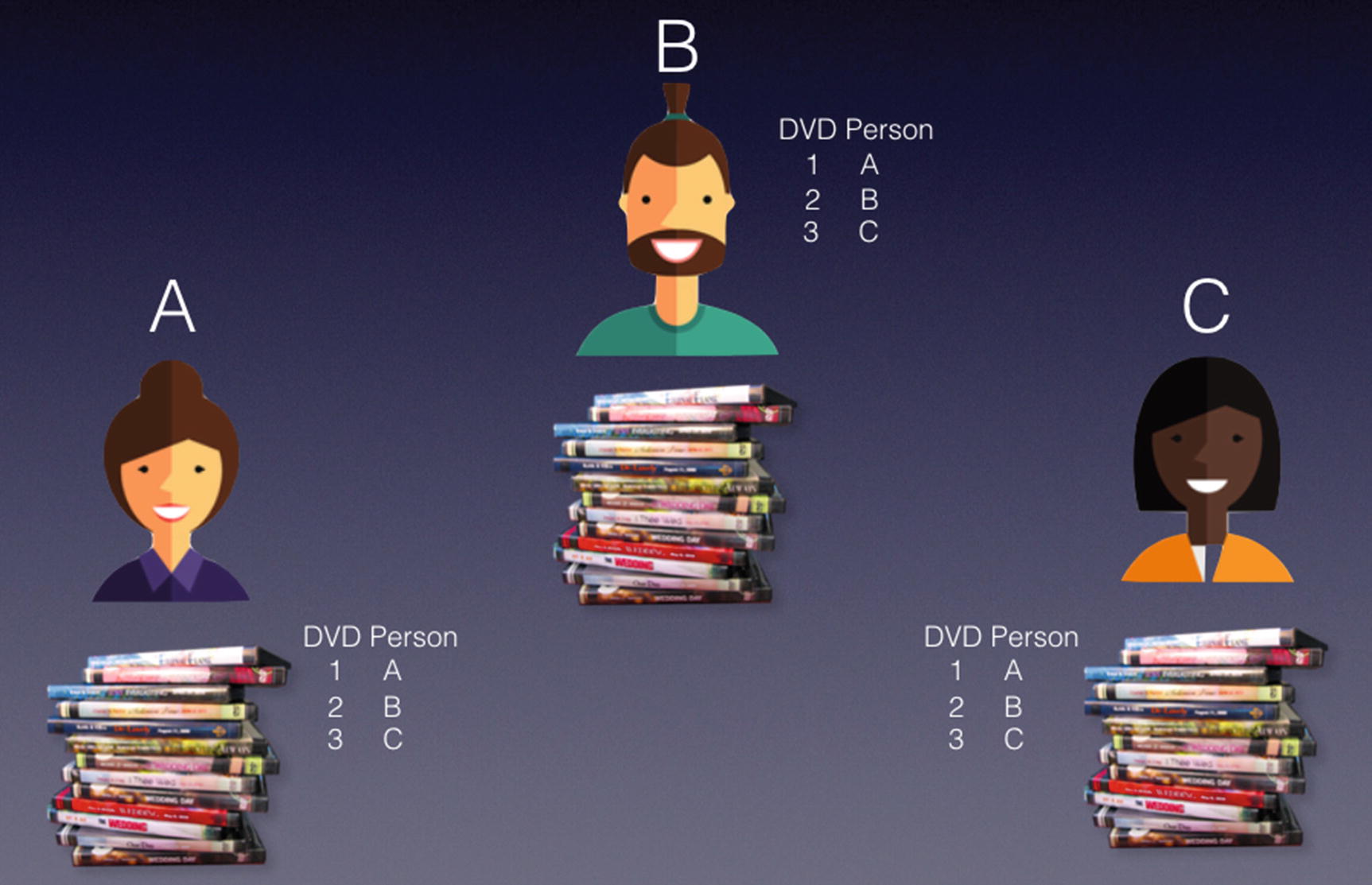
Getting everyone to keep the records
We say that the record keeping is now decentralized! We now have three persons holding the same ledger. But wait a minute. What if A and C conspire to change the records together so that they can steal the DVDs from B? Since majority wins, as long as there is more than 50% of the people with the same records, the others would have to listen to the majority. And because there are only three persons in this scenario, it is extremely easy to get more than 50% of the people to conspire.
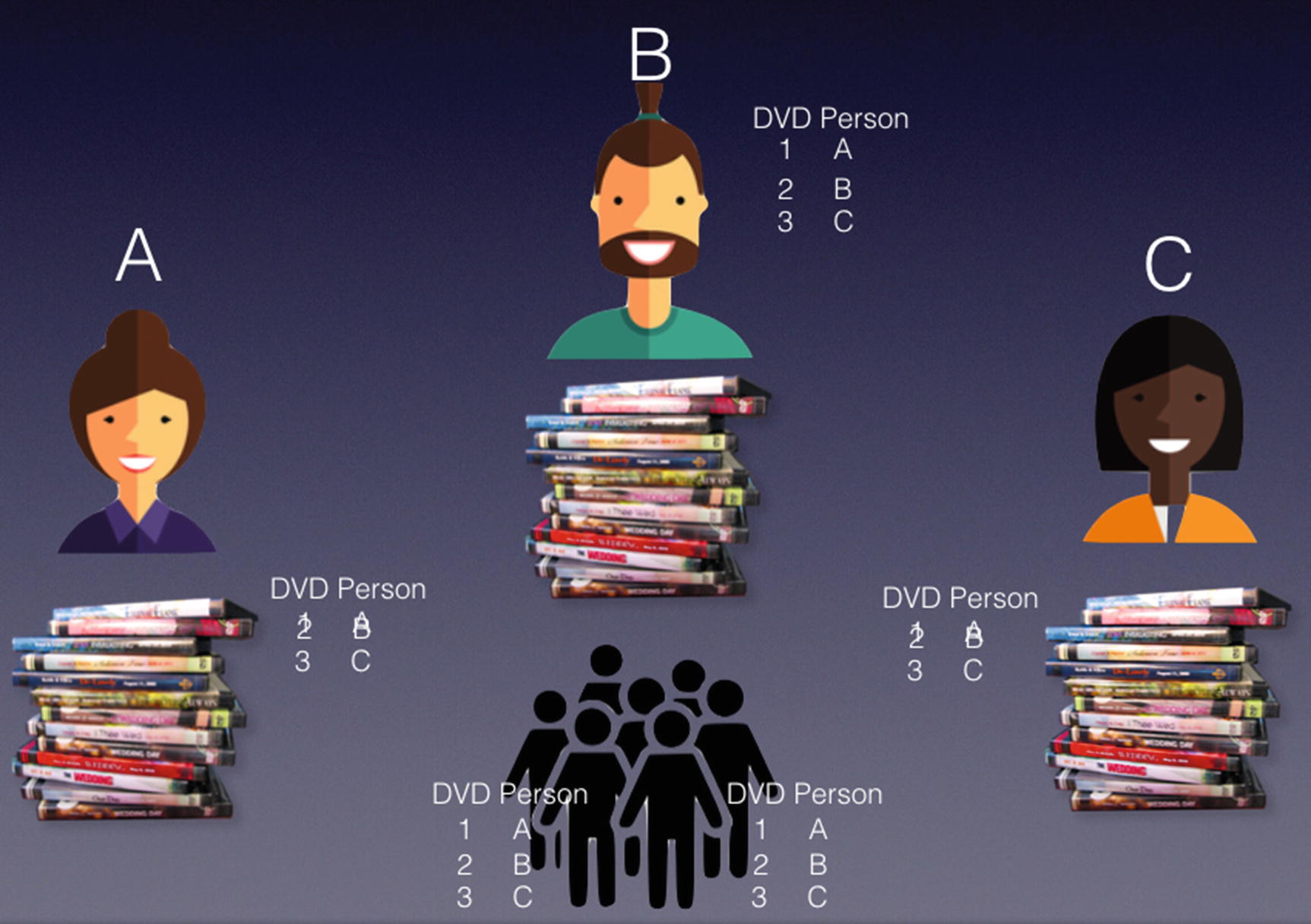
Getting a group of unrelated people to help keep the records
This way, it makes it more difficult for one party to alter the records on the ledger, and that in order to alter a record, it would need to involve a number of people altering the record all at the same time, which is a time-consuming affair. And this is the key idea behind distributed ledger, or commonly known as blockchain.
Blockchain As a Distributed Ledger
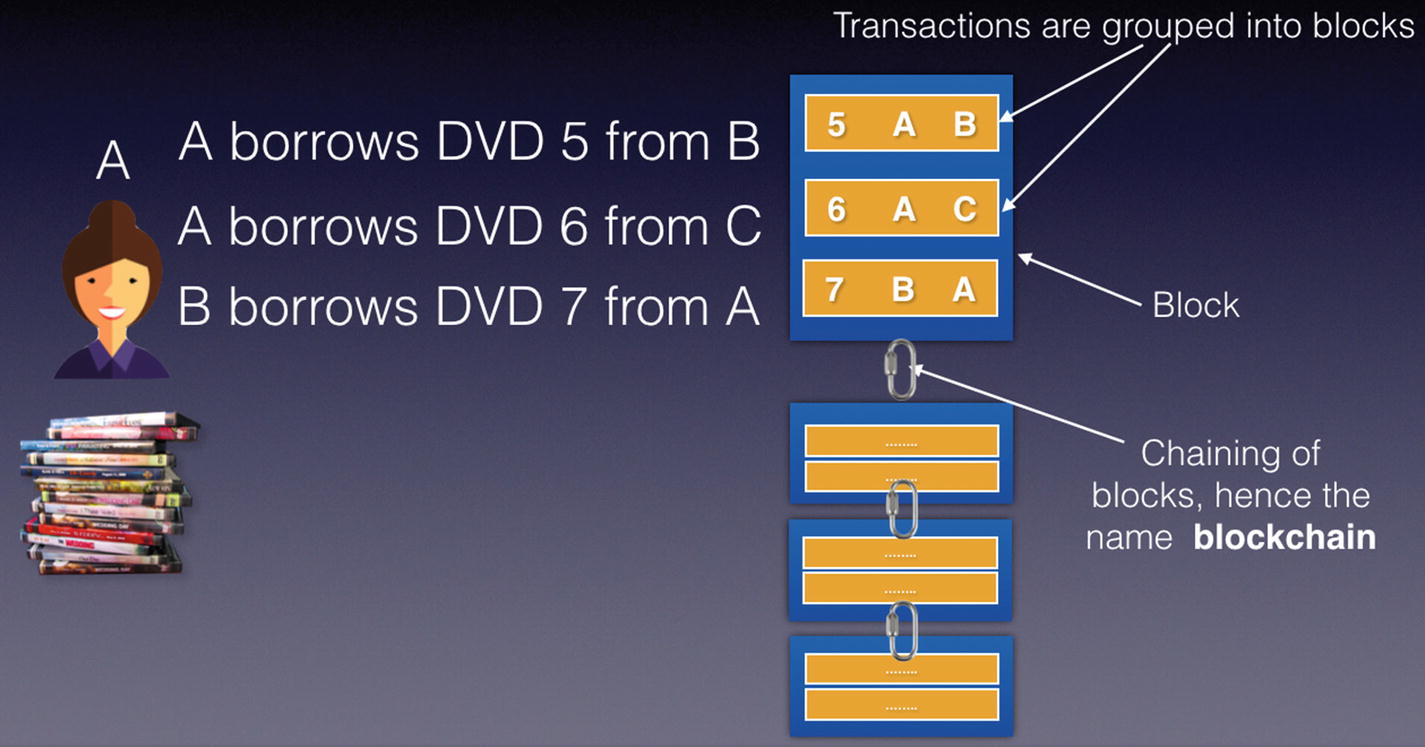
Transactions form a block, and then blocks are then chained
Centralized databases and institutions work when there is trust in the system of law, governments, regulatory bodies, and people.
A decentralized database built on the blockchain removes the need for the trust in a central body.
A blockchain can be used for anything of value, not just currencies.
How Blockchain Works
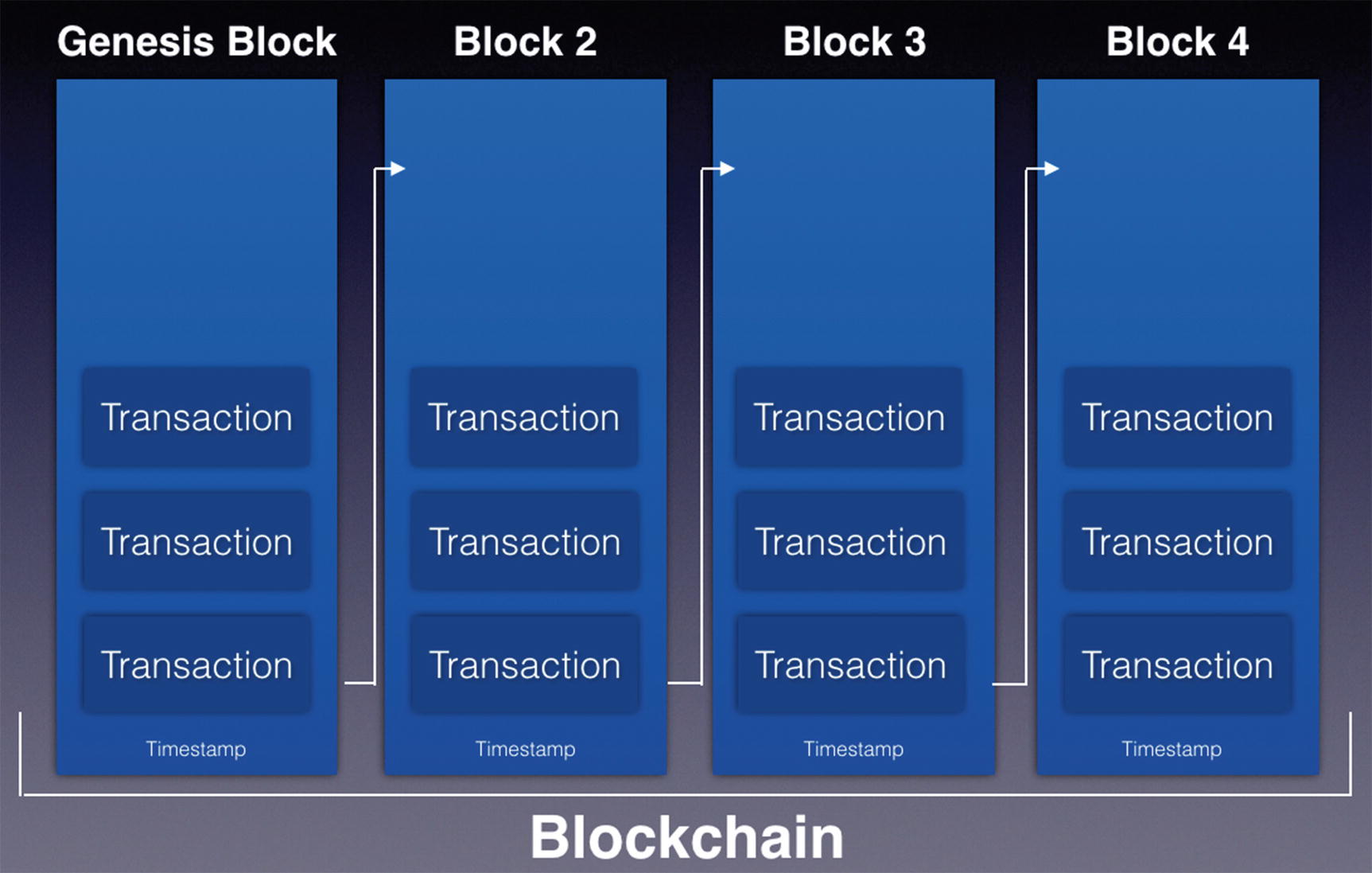
Every blockchain has a beginning block known as the genesis block
The blocks are connected to each other cryptographically, the details in which we will discuss in the sections ahead. The first block in a blockchain is known as the genesis block .
Note
Every blockchain has a genesis block.
So, the next important questions is – how do you chain the blocks together?
Chaining the Blocks
Before we discuss how blocks in a blockchain are chained together, we have to discuss a key concept in blockchain – hashing. A hash function is a function that maps data of arbitrary size to data of fixed size. By altering a single character in the original string, the resultant hash value is totally different from the previous one. Most importantly, observe that a single change in the original message results in a completely different hash, making it difficult to know that the two original messages are similar.
It is deterministic – the same message always results in the same hash.
It is a one-way process – when you hash a string, it is computationally hard to reverse a hash to its original message.
It is collision resistant – it is hard to find two different input messages that hash to the same hash.
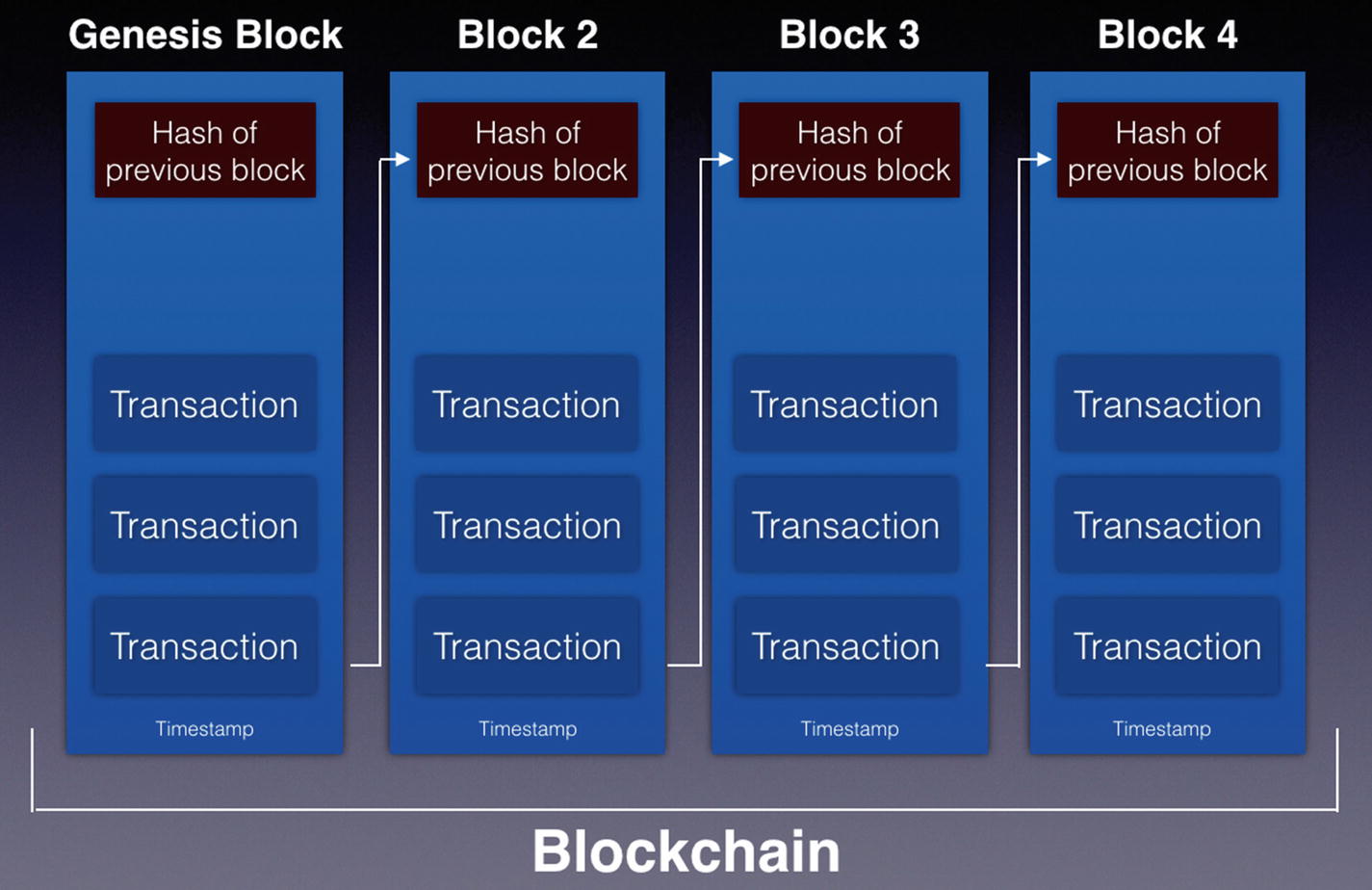
Chaining the blocks with hashes
Observe that when hashing the content of a block, the hash of the previous block is hashed together with the transactions. However, do take note that this is a simplification of what is in a block. Later on, we will dive into the details of a block and see exactly how transactions are represented in a block.
Storing the hash of the previous block in the current block assures the integrity of the transactions in the previous block. Any modifications to the transaction(s) within a block causes the hash in the next block to be invalidated, and it also affects the subsequent blocks in the blockchain. If a hacker wants to modify a transaction, not only must he modify the transaction in a block but all other subsequent blocks in the blockchain. In addition, he needs to synchronize the changes to all other computers on the network, which is a computationally expensive task to do. Hence, data stored in the blockchain is immutable, for they are hard to change once the block they are in is added to the blockchain.
Up to this point, you have a high-level overview of what constitutes a blockchain and how the blocks are chained together. In the next section, you will understand the next important topic in blockchain – mining.
Mining
Whenever you talk about blockchain or cryptocurrencies, there is always one term that comes up – mining. In this section, you will learn what is mining, and what goes on behind the scene.
Mining is the process of adding blocks to a blockchain. In a blockchain network, such as the Bitcoin or Ethereum network, there are different types of computers known as nodes. Computers on a blockchain that add blocks to the blockchain are known as miner nodes (or mining nodes, or more simply miners).
We will talk about the different types of nodes later on in this course, but for now, we want to talk about a particular type of node, known as the miner node . The role of the miner node is to add blocks to the blockchain.
But how are blocks added?
Broadcasting Transactions
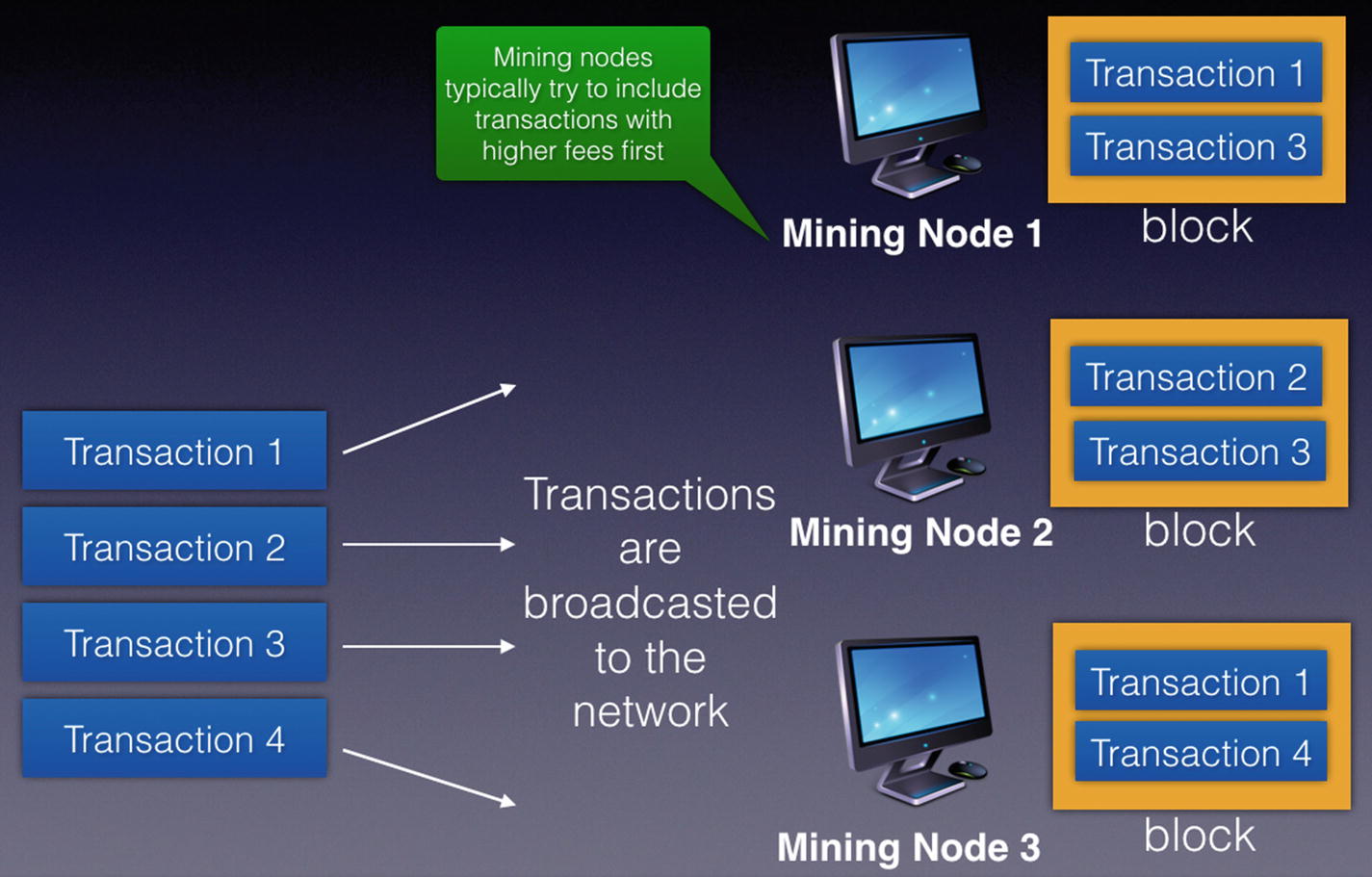
Transactions are broadcasted to mining nodes, which then assemble them into blocks to be mined
Each mining node may receive them at different times. As a node receives transactions, it will try to include them in a block. Observe that each node is free to include whatever transactions they want in a block. In practice, which transactions get included in a block depends on a number of factors, such as transaction fees, transaction size, order of arrival, and so on.
At this point, transactions that are included in a block but which are not yet added to the blockchain are known as unconfirmed transactions. Once a block is filled with transactions, a node will attempt to add the block to the blockchain.
Now here comes the problem – with so many miners out there, who gets to add the block to the blockchain first?
The Mining Process
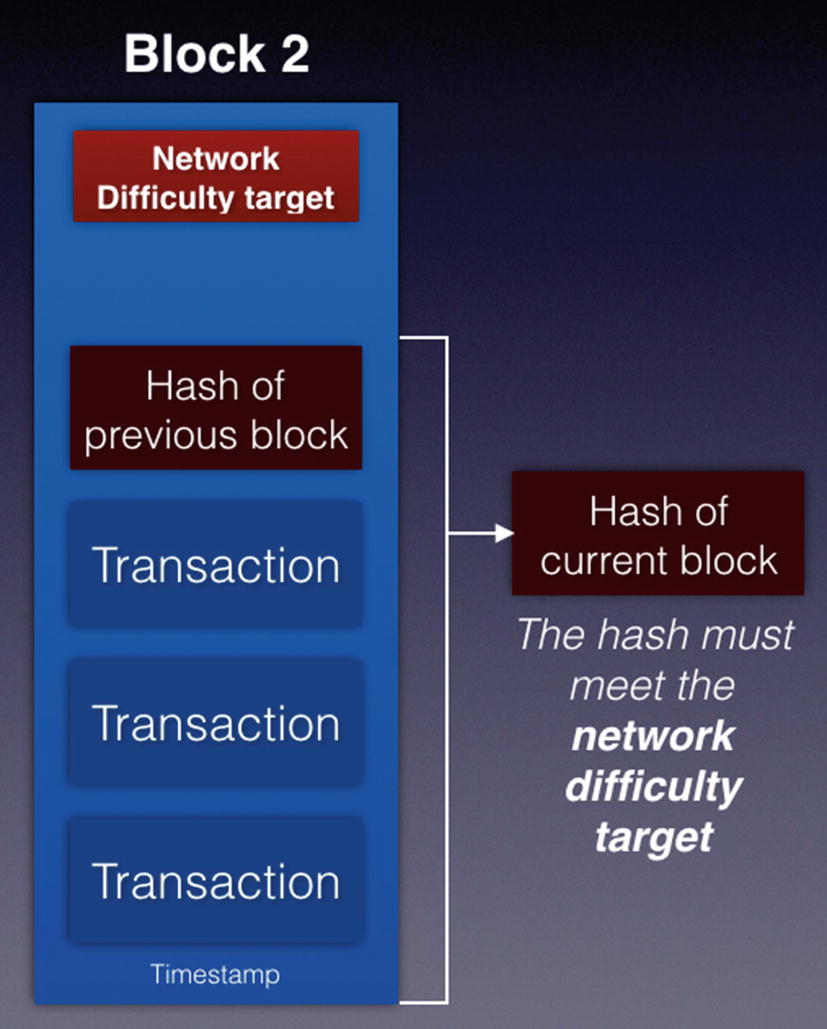
Hashing the block to meet the network difficulty target
In order to successfully add a block to the blockchain, a miner would hash the content of a block and check that the hash meets the criteria set by the difficulty target. For example, the resultant hash must start with five zeros and so on.
As more miners join the network, the difficultly level increases, for example, the hash must now start with six zeros and so on. This allows the blocks to be added to the blockchain at a consistent rate.
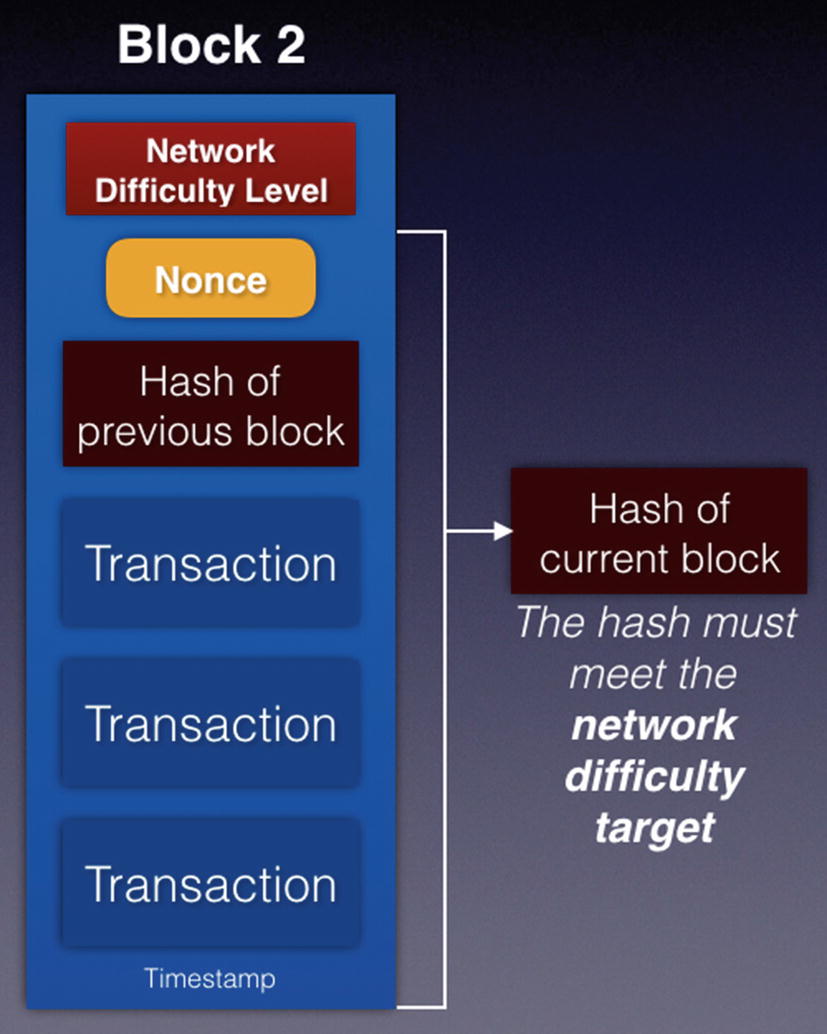
Adding a nonce to change the content of the block in order to meet the network difficulty target
The first miner who meets the target gets to claim the rewards and adds the block to the blockchain. It will broadcast the block to other nodes so that they can verify the claim and stop working on their current work of mining their own blocks. The miners would drop their current work, and the process of mining a new block starts all over again. The transactions that were not included in the block that was successfully mined will be added to the next block to be mined.
Rewards For Miners
In the case of Bitcoin, the block reward initially was 50 BTC and will halve every 210,000 blocks. At the time of writing, the block reward is currently at 12.5 BTC, and it will eventually be reduced to 0 after 64 halving events. For Ethereum, the reward for mining a block is currently 2 ETH (Ether).
Blocks Adding Rates
For Bitcoin, the network adjusts the difficulty of the puzzles so that a new block is being mined roughly every 10 minutes. For Ethereum, a block is mined approximately every 14 seconds.
Proof of Work
The process in which blocks are mined and added to the blockchain is known as the Proof of Work (PoW). It is difficult to produce the proof but very easy to validate. A good example of Proof of Work is cracking a combination lock – it takes a lot of time to find the right combination, but it is easy to verify once the combination is found.
Proof of Work uses tremendous computing resources – GPUs are required, while CPU speed is not important. It also uses a lot of electricity, because miners are doing the same work repeatedly – find the nonce to meet the network difficulty for the block.
A common question is why you need to use a powerful GPU instead of CPU for mining? Well, as a simple comparison, a CPU core can execute 4 32-bit instructions per clock, whereas a GPU like the Radeon HD 5970 can execute 3200 32-bit instructions per clock. In short, the CPU excels at doing complex manipulations to a small set of data , whereas the GPU excels at doing simple manipulations to a large set of data. And since mining is all about performing hashing and finding the nonce, it is a highly repetitive task, something that GPU excels in.
Tip
When a miner has successfully mined a block, he earns mining fees as well as transaction fees. That’s what keeps miners motivated to invest in mining rigs and keep them running 24/7, thereby incurring substantial electricity bills.
Immutability of Blockchains
In a blockchain, each block is chained to its previous block through the use of a cryptographic hash. A block’s identity changes if the parent’s identity changes. This in turn causes the current block’s children to change, which affects the grandchildren, and so on. A change to a block forces a recalculation of all subsequent blocks, which requires enormous computation power. This makes the blockchain immutable, a key feature of cryptocurrencies like Bitcoin and Ethereum.
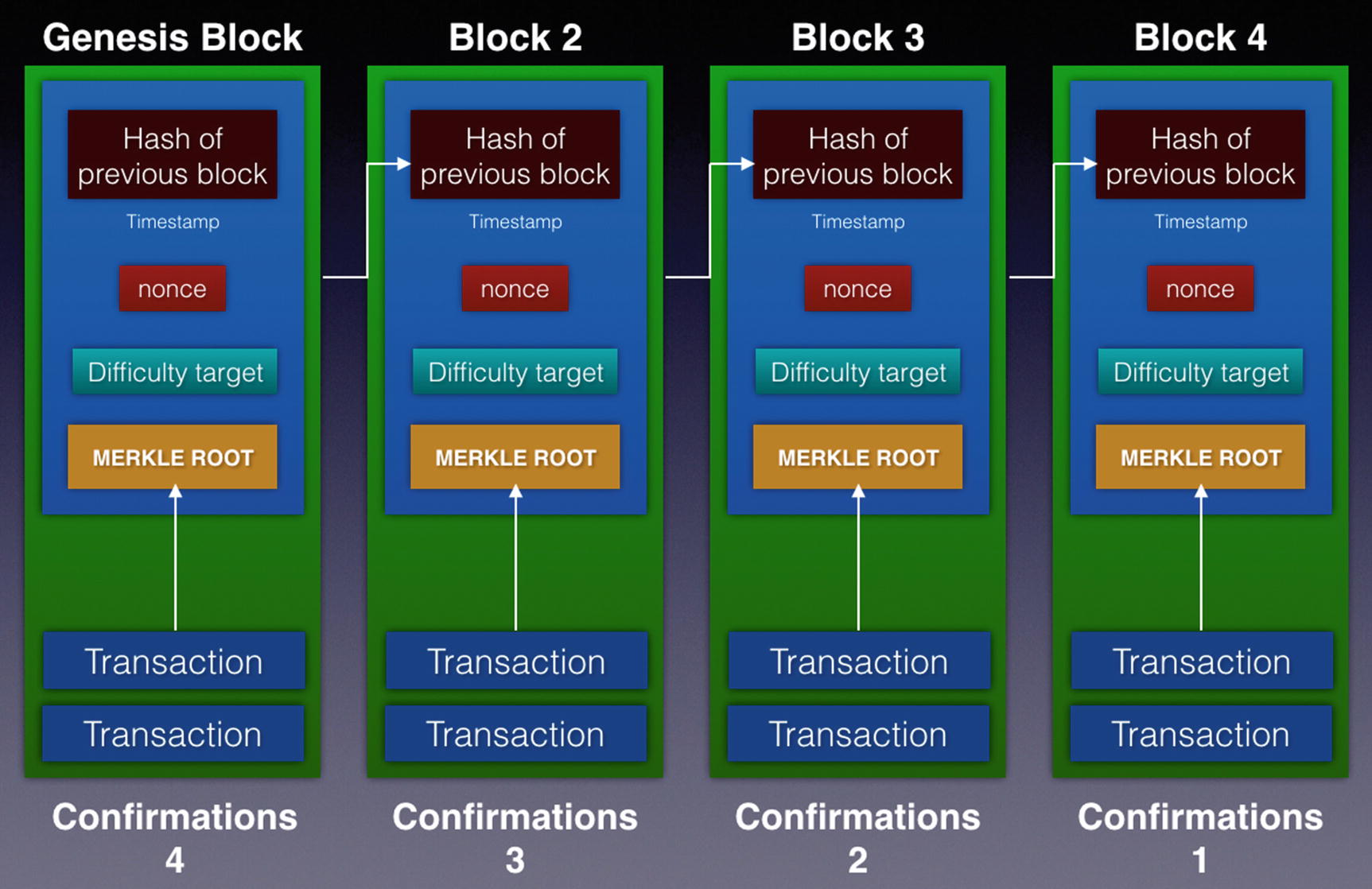
Confirmations of blocks in a blockchain
Tip
In general, once a block has six or more confirmations, it’s deemed infeasible for it to be reversed. Therefore, the data stored in the blockchain is immutable.
Blockchain in More Detail
A block header
The list of transactions
The hash of the previous block
Timestamp
Merkle root
Nonce
Network difficulty target
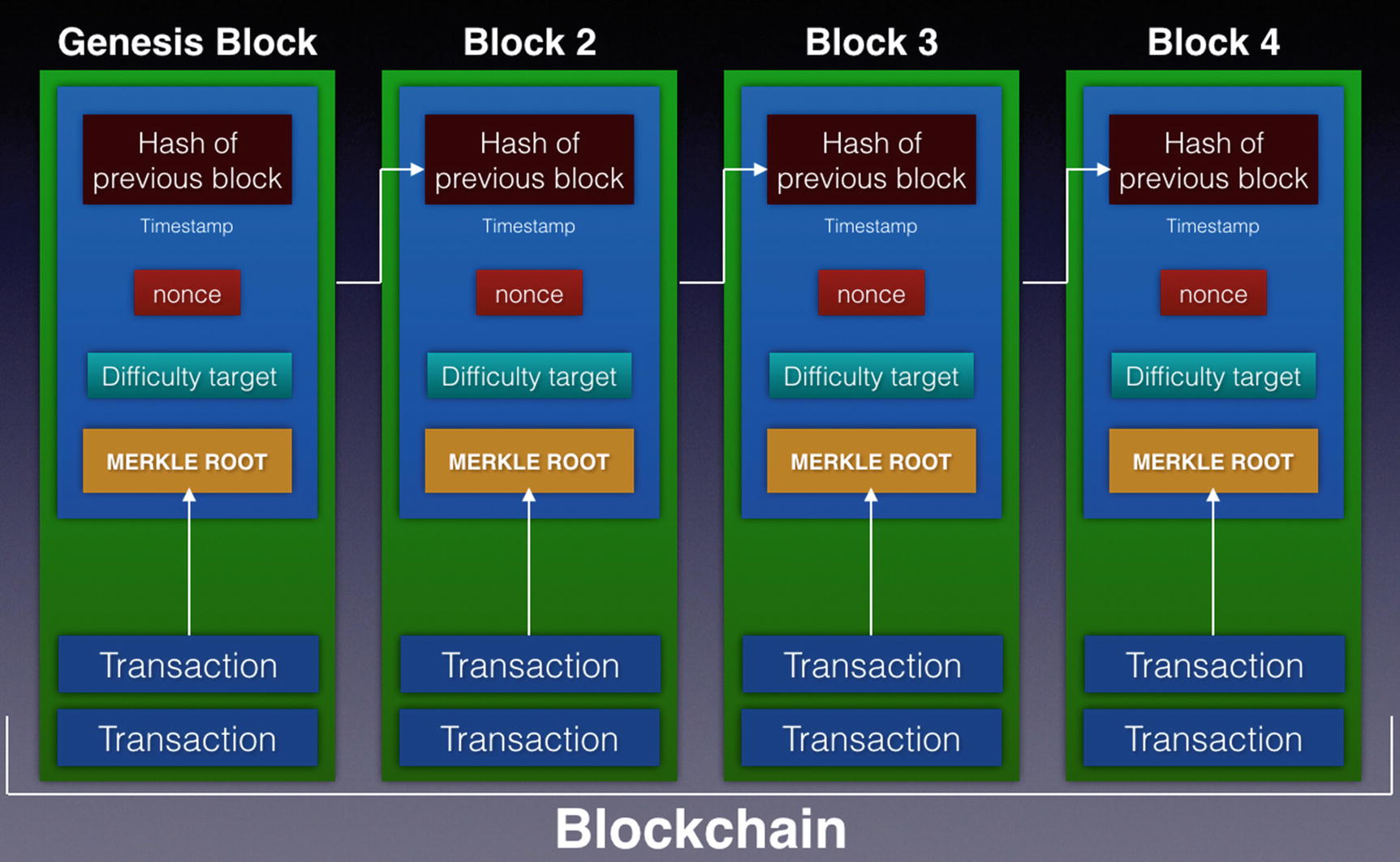
A block contains the block header, which in turns contains the Merkle root of the transactions
Types of Nodes
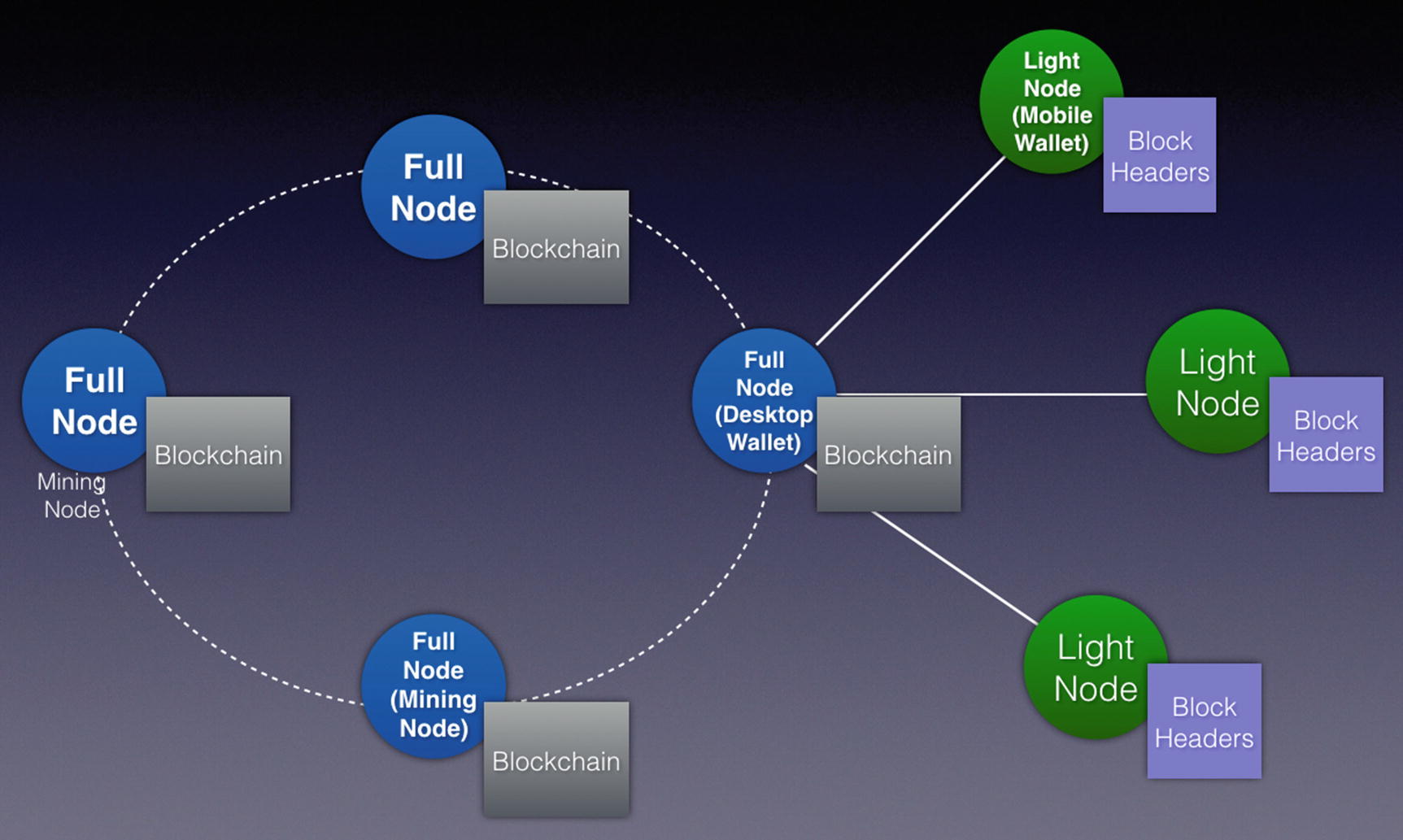
Different types of nodes in a blockchain network
As we mentioned in our earlier sections, computers connected to the blockchain network are known as nodes. We have discussed the role of mining nodes, whose key responsibility is to gather transactions into blocks and then try to add the block to the blockchain by finding the nonce that satisfies the network difficulty. Mining nodes are also known as full nodes .
Tip
Note that full nodes are not necessarily mining nodes. However, mining nodes need to be a full node.
The purpose of a full node is to ensure the integrity of the blockchain and people running full nodes do not get rewards. On the other hand, mining nodes are rewarded when they add a block to the blockchain.
An example of a full node is a desktop wallet, which allows users to perform transaction using the cryptocurrency.
Each full node has a copy of the entire blockchain. Full nodes also validate every block and transactions presented to it.
Besides full nodes, there are also light nodes. Light nodes help to verify transactions using a method called simplified payment verification (SPV). SPV allows a node to verify if a transaction has been included in a block, without needing to download the entire blockchain. Using SPV, light nodes connect to full nodes and transmit transactions to the full nodes for verifications.
Light nodes only need to store the block headers of all the blocks in the blockchain. An example of a light node is a mobile wallet, such as the Coinbase mobile app for iOS and Android. Using a mobile wallet, a user can perform transactions on the mobile device.
Note
Desktop wallets can be full node or light node.
- Full node
Maintains a complete copy of the blockchain
Able to verify all transactions since the beginning
Verifies a newly created block and add it to the blockchain
- Visit the following sites to see the current number of full nodes for the following blockchains:
Bitcoin – https://bitnodes.earn.com
Ethereum – www.ethernodes.org/network/1
- Mining node (must be a full node)
Works on a problem (finding the nonce)
- Light node (e.g., wallets)
Maintains the headers of the blockchain
Uses SPV to verify if a transaction is present and valid in a block
Finally, let’s now see the use of representing the transactions as a Merkle root in the block header in the next section.
Merkle Tree and Merkle Root
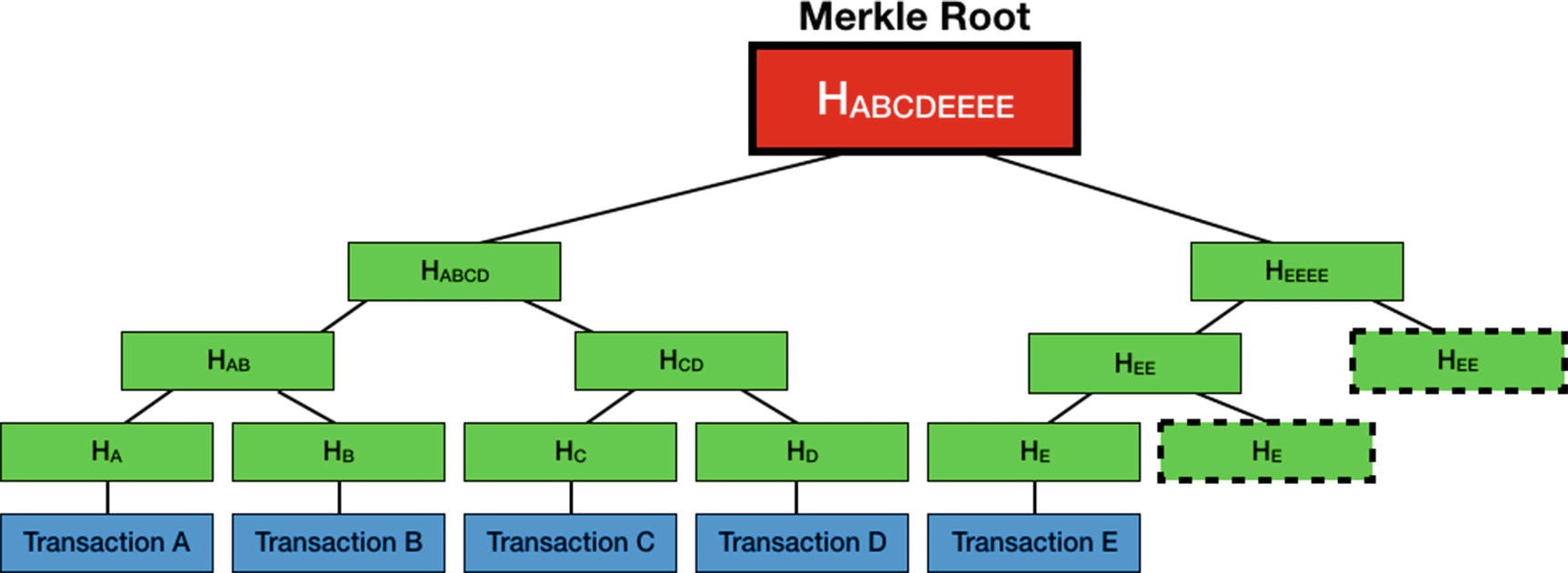
How the Merkle root is derived from the Merkle tree
As you can see from the figure, each transaction is hashed. The hash of each transaction is hashed together with the hash of another node. For example, the hash of transaction A (HA) is combined with the hash of transaction B (HB) and hashed to derive HAB. This process is repeated until there’s only one resultant hash. This final hash is known as the Merkle root. In the preceding example, because HE doesn’t have another node to pair with, it’s hashed with itself. The same applies to HEE.
The Merkle root is stored in the block header, and the rest of the transactions are stored in the block as a Merkle tree. In the earlier discussion, I mentioned about full nodes. Full nodes download the entire blockchain, and there’s another type of node (known as light nodes) that downloads only the blockchain headers. Because light nodes don’t download the entire blockchain, they’re easier to maintain and run. Using a method called simplified payment verifications (SPV), a light node can query a full node to verify a transaction. Examples of light nodes are cryptographic wallets.
Uses of Merkle Tree and the Merkle Root
The light node queries a full node for the following hashes: HD, HAB, and HEEEE (see Figure 1-16).
Because the light node can compute HC, it can then compute HCD with HD supplied.
With HAB supplied, it can now compute HABCD.
With HEEEE supplied, it can now compute HABCDEEEE (which is the Merkle root).
Because the light node has the Merkle root of the block, it can now check to see if the two Merkle roots match. If they match, the transaction is verified.
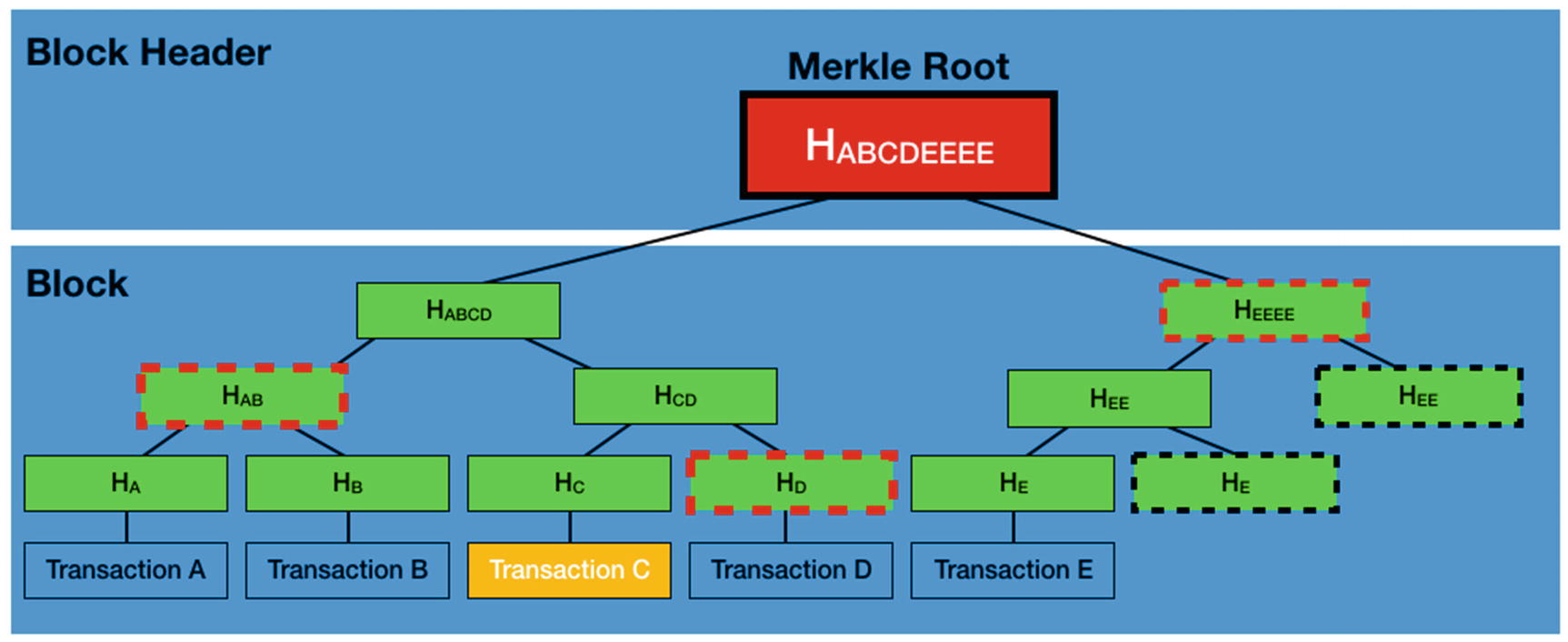
How the Merkle tree and Merkle root are used to validate a transaction
As you can see from this simple example, to verify a single transaction out of five transactions, only three hashes need to be retrieved from the full node. Mathematically, for n transactions in a block, it takes log2n hashes to verify that a transaction is in a block . For example, if there are 1024 transactions in a block, a light node only needs to request ten hashes to verify the existence of a transaction in the block.
Summary
In this chapter, you have learned about the motivations behind blockchain and the problems that it aims to solve. You also had a chance to know how blocks are added to the blockchain through a process known as mining. In the next chapter, you will learn how to build your own blockchain using Python so that you can see and understand the inner workings of a blockchain.
