Besides teaching you how to use the Kali Linux tools for your ethical hacking endeavors, in previous chapters I have tried to touch on some related topics too. Specifically, I have given you an overview of security trends, networking, anonymity, Python, the information assurance model, hashes and passwords, and more. This has all been so that you can take your hacking skills to a higher level than merely learning a few automated tools.
In this chapter, you will learn even more. I’ll cover some classic and modern encryption techniques. This topic belongs to the world of cryptography, so you can consider this chapter as your first step toward a more complex world of computer security.
Cryptography is a big topic to cover, especially in a single chapter. It has three major components to it: computer science, electrical engineering, and algorithms. A good knowledge of physics and mathematics is also important if you want to approach this topic seriously. However, as a penetration tester, you just need some basic knowledge about what cryptography is, how it works, and why it is so important in the age of digital transformation.
Nature and Perspective
As a penetration tester, you need to deal with the secrets of your clients. Specifically, you need to make the client’s system foolproof so that it protects all its secrets such as passwords. Cryptography has been created to keep secrets protected in a manner that does not allow unauthorized people to view the information. Cryptography ensures that private information can safely travel across networks such as the Internet, is inherently insecure. At its core, cryptography deals with encrypting data by generating secret keys. These keys are called symmetric when they are used for performing bulk data encryption. They are called asymmetric when the keys are used for transferring a secret key to a system to match the pair.
A digital certificate is a good example of cryptography.
Let’s view a certificate to try to understand how it is formatted. Each certificate has fields that contain many things such as version, serial number, validity, algorithm ID, public key information and algorithm, and so on.
Let’s open an e-mail account in Mozilla Firefox, which requires a login. Log in, go to the Tools menu, and click the Page Info submenu.

Certificate Viewer window in Mozilla Firefox

Algorithm details in the Certificate Viewer window

Certificate information in Internet Explorer on Windows 10
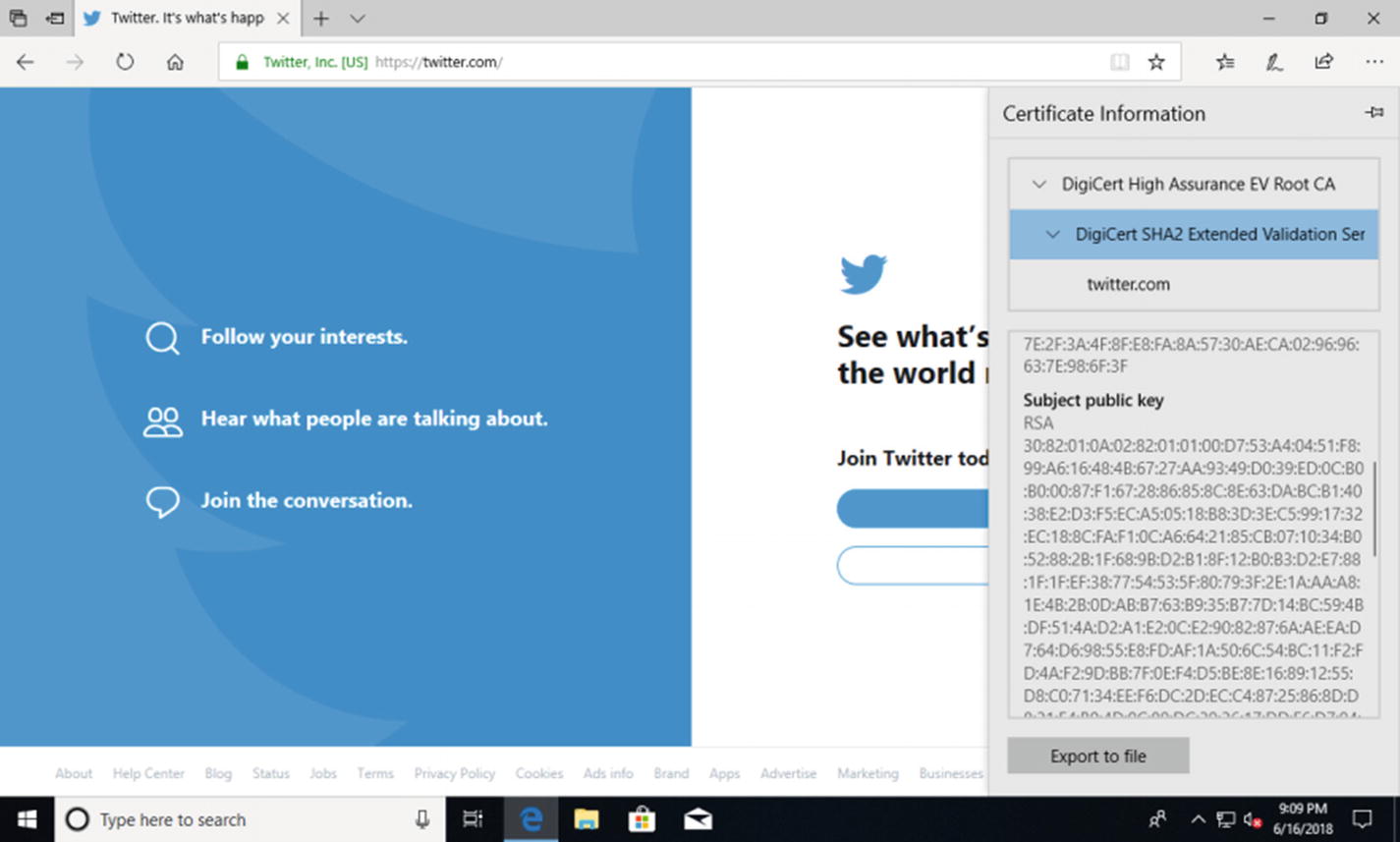
Public key in in Internet Explorer
In the previous chapter, you learned that encryption is a two-way function; it matches public and private keys, and when they match, it decrypts the mangled data.
In the previous figures, you saw the public key of Twitter, and it has been incorporated into the SSL certificate and shared with clients, which could be a browser, mobile device, or another server. The whole structure of an SSL certificate consists of private and public keys.
In Figure 14-1, you saw a certificate after logging into an e-mail account in Mozilla Firefox. Your private key is stored on the Mozilla server. This private key is one-half the private and public key pair used in that digital certificate.
You may ask who has issued this certificate. Who is the authority? Why is it needed?
As an example, you know that each U.S. state issues a unique authentication ID (it could be a voter’s ID or driver’s license). In such cases, the state is the certificate authority, in other words, a trusted third party that is trusted to validate your identity. You cannot make this ID at home! Certificate authorities play the same type of role. They are third-party organizations that provide notarization services for digital certificates.
Now let’s see the specifics of cryptography.
Models of the Cryptography System
Early cryptographers used to encrypt data using ciphers. A cipher encrypts a message by altering the characters. Inside the cipher text is the original plain text. Each cipher follows specific rules, and anyone who knows the rules of the cipher can decrypt the cipher text.
The word cryptography originally comes from a combination of the Greek words krytos, which means secret, and graphein, which means writing.
Early cryptography ensured nonrepudiation, which was discussed in Chapter 11. This ensures that the written messages could be sent to their intended recipients. The encryption technique used at that time was based on a simple principle; the messages were transformed in such a way that they became unreadable.
In the early days, substitution ciphers were used. These types of ciphers encoded messages, and certain letters were always substituted by other letters. For example, Caesar’s cipher, named after Julius Caesar, used a substitution cipher. It replaced each letter with a letter that is a specified number of positions to its right or left in the alphabet. In Caesar’s cipher, the word hello would be ebiil. The first letter h has been replaced by a letter that is three positions to its left, which is e.
By 1920, one-time pads (OTPs) and rotor machines came into existence. An OTP is unbreakable because plain text is paired with a random secret key. A rotor machine is an electromechanical cipher machine.
Symmetric-key cryptography : A good example of symmetric-key cryptography is session key because it uses a single key to both encrypt and decrypt the data. In symmetric-key cryptography, the sender and the recipient must have access to the same key.
Asymmetric-key cryptography : In asymmetric-key cryptography, two keys are used; one is the public key, and the other is a private key. You have seen this type in the digital certificate examples. In asymmetric-key cryptography, the sender and the recipient have a different set of public-key and private-key pairs. Therefore, it is much more difficult to break this type of cryptography.
Let’s try to understand this in detail. When you use multiple systems and try to share the key using symmetric-key cryptography, each system should use a secure channel. Why? This is because the sender and the recipient use the same key. If the channel is not secure, it can be stolen. In multiple systems, you cannot guarantee that. One link could be vulnerable. The only advantage of symmetric-key cryptography is that it is fast. So, it is custom to use asymmetric-key cryptography whenever possible.
Asymmetric-key cryptography was created while keeping those shortcomings in mind. In an insecure network such as the Internet, it is important to keep the secret key secure. For that reason, asymmetric-key encryption started using two related keys known as the key pair. For example, while using an e-mail or banking service, you have two keys; one is public, and the other is private (that you only) know. The recipient has the same public key and their own private key (that only the recipient knows). In both cases, this pair should match. A cracker would have to know both keys to read the encrypted data, which is more difficult than obtaining just one key.
There are several mathematical methods that are used to establish the relationship between the two keys in asymmetric-key cryptography. Factorization of prime numbers or discrete logarithms may be used by cryptographers.
To summarize, in symmetric-key cryptography, encryption and decryption use the same key. In asymmetric-key cryptography, the encryption and decryption keys are different. Cryptography is secure, but there is always an overhead because the algorithms can be computation intensive, requiring large numbers and complex mathematical operations. In addition, there is always a design challenge: how can you make an algorithm small but powerful and secure at the same time? Performance and speed are big issues.
You will learn more about the design challenges of cryptography in the next section, which discusses the types of attacks on encrypted messages.
Types of Attacks on Encrypted Messages
An attacker or a packet sniffer might study the side channels. Side channels comprise many things, such as the pattern of power consumption and the radiation of the devices that are used by the sender and the recipient. The attacker might study the execution time of the algorithm and guess what type of encryption algorithm is being used.
In addition, there could be vulnerabilities either in the cipher or in the protocol. The key management could be vulnerable. In cipher text-only attacks, the attacker obtains several encrypted messages first. Next, the attacker studies the patterns of the encryption algorithm. The attacker also does statistical analysis. In this case, the attacker does not have the associated plain text.
In a plain-text attack, the attacker already has some of the plain text of the messages and some of the cipher text of one or more messages. This type of attack can be used when portions of the plain-text messages fall into attacker’s hand.
In another type of plain-text attack, the attacker has only the plain-text messages. The attacker can encrypt them and analyze the cipher text to discover the key. Another type of attack may happen when the attacker has only the cipher text; in such cases, the attacker decrypts the cipher text and tries to find the key. Finally, there is brute-force attack, where an attacker may try all possible combinations of keys or passwords. However, this is time-consuming and costly.
Keeping all possible attacks in mind, cryptographers always face challenges when they design ciphers. There are trade-offs between security, speed, and side channel attacks.
You have three diversified interests here. You want to write an algorithm that is small and fast, but you want to protect it from side channel attacks; further, to enhance security, you must make the algorithm computationally intensive using large numbers. So, a trade-off between implementation and security is always present.
